Report on WLAN Tools and Advanced Wireless Technologies in Detail
VerifiedAdded on 2023/06/05
|13
|2307
|368
Report
AI Summary
This report provides an overview of WLAN tools and advanced wireless technologies. It begins with an executive summary, followed by a detailed exploration of two WLAN sniffing tools: Wireshark and Network Miner. The report delves into the installation steps, features, advantages, and disadvantages of each tool, along with a comparison of their functionalities. The second part of the report examines various wireless technologies, including radio, cellular, WiFi, Femtocell, WiMax, 4G, and 3G, highlighting their strengths, weaknesses, and security aspects. The report concludes with a proposal for the best wireless technologies for organizational adoption. The report uses tables, figures and analysis to compare and contrast the tools and technologies discussed.

WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 1
WLAN TOOLS AND ADVANCED WIRELESS TECHNOLOGIES
Name
Instructor
Institution
Course
City
Date
WLAN TOOLS AND ADVANCED WIRELESS TECHNOLOGIES
Name
Instructor
Institution
Course
City
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 2
Table of Contents
Executive summary...................................................................................................................................2
Part A: WLAN Tools................................................................................................................................3
Introduction...........................................................................................................................................3
Report layout.........................................................................................................................................3
WLAN tools..........................................................................................................................................3
Wireshark...........................................................................................................................................3
Network Miner...................................................................................................................................7
Comparison models in functionalities of the two WLAN tools.......................................................11
Part B: Wireless Technologies................................................................................................................11
The types of wireless technologies......................................................................................................11
Proposal of the best wireless technologies..........................................................................................12
Conclusion...............................................................................................................................................12
References...............................................................................................................................................13
Table of Contents
Executive summary...................................................................................................................................2
Part A: WLAN Tools................................................................................................................................3
Introduction...........................................................................................................................................3
Report layout.........................................................................................................................................3
WLAN tools..........................................................................................................................................3
Wireshark...........................................................................................................................................3
Network Miner...................................................................................................................................7
Comparison models in functionalities of the two WLAN tools.......................................................11
Part B: Wireless Technologies................................................................................................................11
The types of wireless technologies......................................................................................................11
Proposal of the best wireless technologies..........................................................................................12
Conclusion...............................................................................................................................................12
References...............................................................................................................................................13

WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 3
Executive summary
This paper will contain two parts; the first part is a demo of two WLAN sniffing tools. Where a
description of the main features of the WLAN tools. This will include the level of complexity, the features of the
two tools, a discussion of the disadvantages and advantages, a comparison the models in functionalities of the
tools, and a summary of the report findings. The second part is summary of the recent wireless technologies
where the report will indicate strengthens, weaknesses, and some of the security issues with the wireless
technologies.
Part A: WLAN Tools
Introduction
One of the most frustrating and time-consuming tasks for IT administrators is network
troubleshooting. To avoid some of the unfortunate events in a network, packet sniffers developed WLAN
sniffing tools. There are the various WLAN sniffing tools example are Kismet, packet capture, Tcpdump,
NetworkMiner, and packet capture. This paper will concentrate on two types of tools which are wireshark and
Network Minder [1].
Report layout
The report is structured into two parts. The first will highlight the two best types of WLAN sniffing tools
which any organization needs to adopt. The second part will highlight the various types of wireless
technologies and propose the best types of technologies that organizations need to adopt
WLAN tools
Wireshark
WireShark is one of the open-source packet analyzer. The tool is widely used for network analysis,
communications protocol development, and network troubleshooting. Originally the tool was referred to as
Ethereal and later renamed WireShark in 2006 May due to trademark issues. Network engineers have
indicated that WireShark is a cross-platform using pcap to capture packets and also it uses Qt widget toolkit to
implement its user interface. The tool runs on Linux, Solaris, Micorsoft windows, and also runs of Linux.
The tool is one of the leading network traffic analyzer and it is very important for system
administrators and security professionals. The tool is a free source and it is considered as one of the best tools
for troubleshooting. Some of the issues that can help network engineers in troubleshooting include latency
issues, malicious activities, and dropped packets. Specifically the tool is used by network engineers to put the
organization network traffic under microscope; it provides tools to filter traffic and zoom in to find the root
cause of network problem. On the other hand the system administrators use the tool to identify any faulty on
Executive summary
This paper will contain two parts; the first part is a demo of two WLAN sniffing tools. Where a
description of the main features of the WLAN tools. This will include the level of complexity, the features of the
two tools, a discussion of the disadvantages and advantages, a comparison the models in functionalities of the
tools, and a summary of the report findings. The second part is summary of the recent wireless technologies
where the report will indicate strengthens, weaknesses, and some of the security issues with the wireless
technologies.
Part A: WLAN Tools
Introduction
One of the most frustrating and time-consuming tasks for IT administrators is network
troubleshooting. To avoid some of the unfortunate events in a network, packet sniffers developed WLAN
sniffing tools. There are the various WLAN sniffing tools example are Kismet, packet capture, Tcpdump,
NetworkMiner, and packet capture. This paper will concentrate on two types of tools which are wireshark and
Network Minder [1].
Report layout
The report is structured into two parts. The first will highlight the two best types of WLAN sniffing tools
which any organization needs to adopt. The second part will highlight the various types of wireless
technologies and propose the best types of technologies that organizations need to adopt
WLAN tools
Wireshark
WireShark is one of the open-source packet analyzer. The tool is widely used for network analysis,
communications protocol development, and network troubleshooting. Originally the tool was referred to as
Ethereal and later renamed WireShark in 2006 May due to trademark issues. Network engineers have
indicated that WireShark is a cross-platform using pcap to capture packets and also it uses Qt widget toolkit to
implement its user interface. The tool runs on Linux, Solaris, Micorsoft windows, and also runs of Linux.
The tool is one of the leading network traffic analyzer and it is very important for system
administrators and security professionals. The tool is a free source and it is considered as one of the best tools
for troubleshooting. Some of the issues that can help network engineers in troubleshooting include latency
issues, malicious activities, and dropped packets. Specifically the tool is used by network engineers to put the
organization network traffic under microscope; it provides tools to filter traffic and zoom in to find the root
cause of network problem. On the other hand the system administrators use the tool to identify any faulty on
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 4
network appliances which are dropping packets and any latency issues caused by those computers routing
network traffic halfway around the world or any form of hacking attempts and data exfiltration [2].
Level of complexity and installation steps
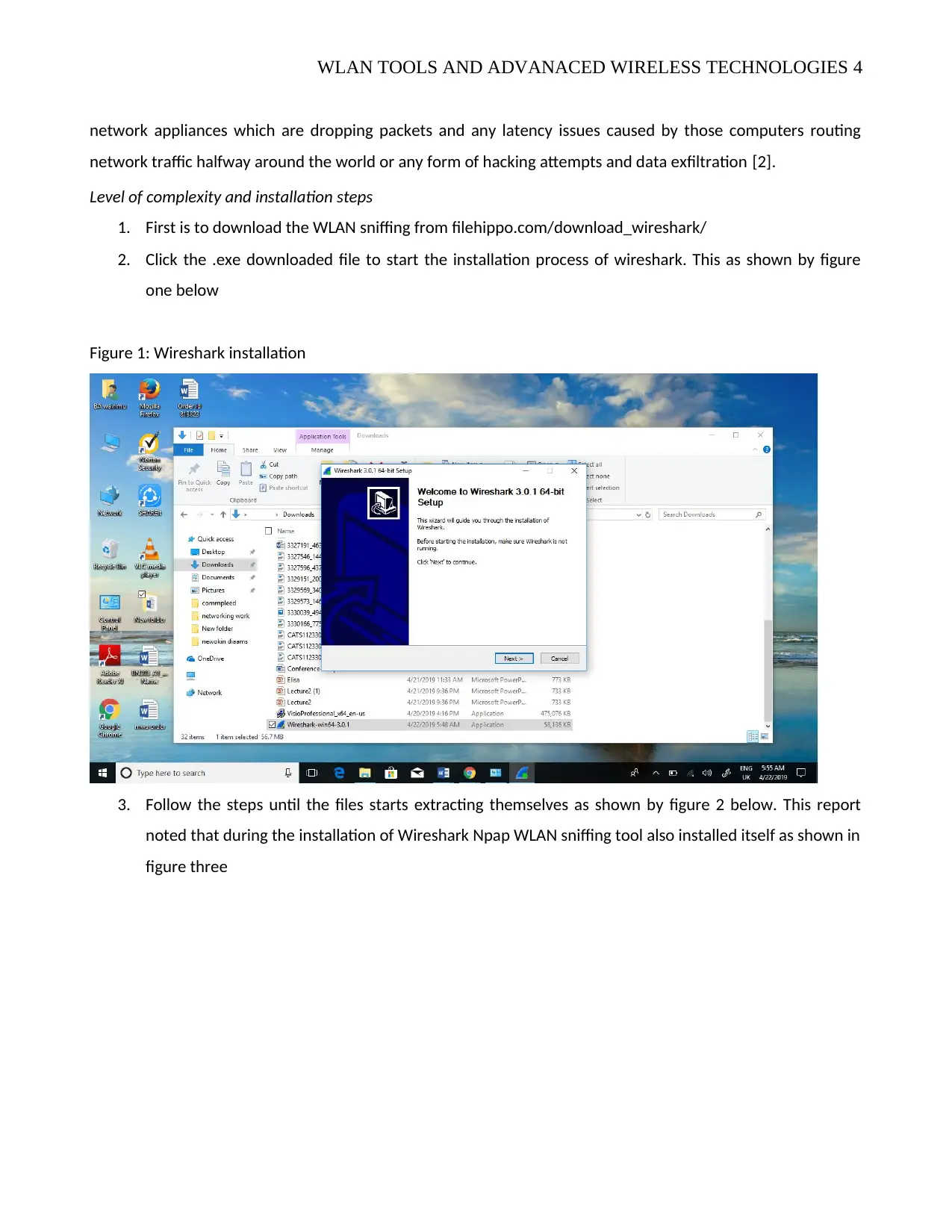
1. First is to download the WLAN sniffing from filehippo.com/download_wireshark/
2. Click the .exe downloaded file to start the installation process of wireshark. This as shown by figure
one below
Figure 1: Wireshark installation
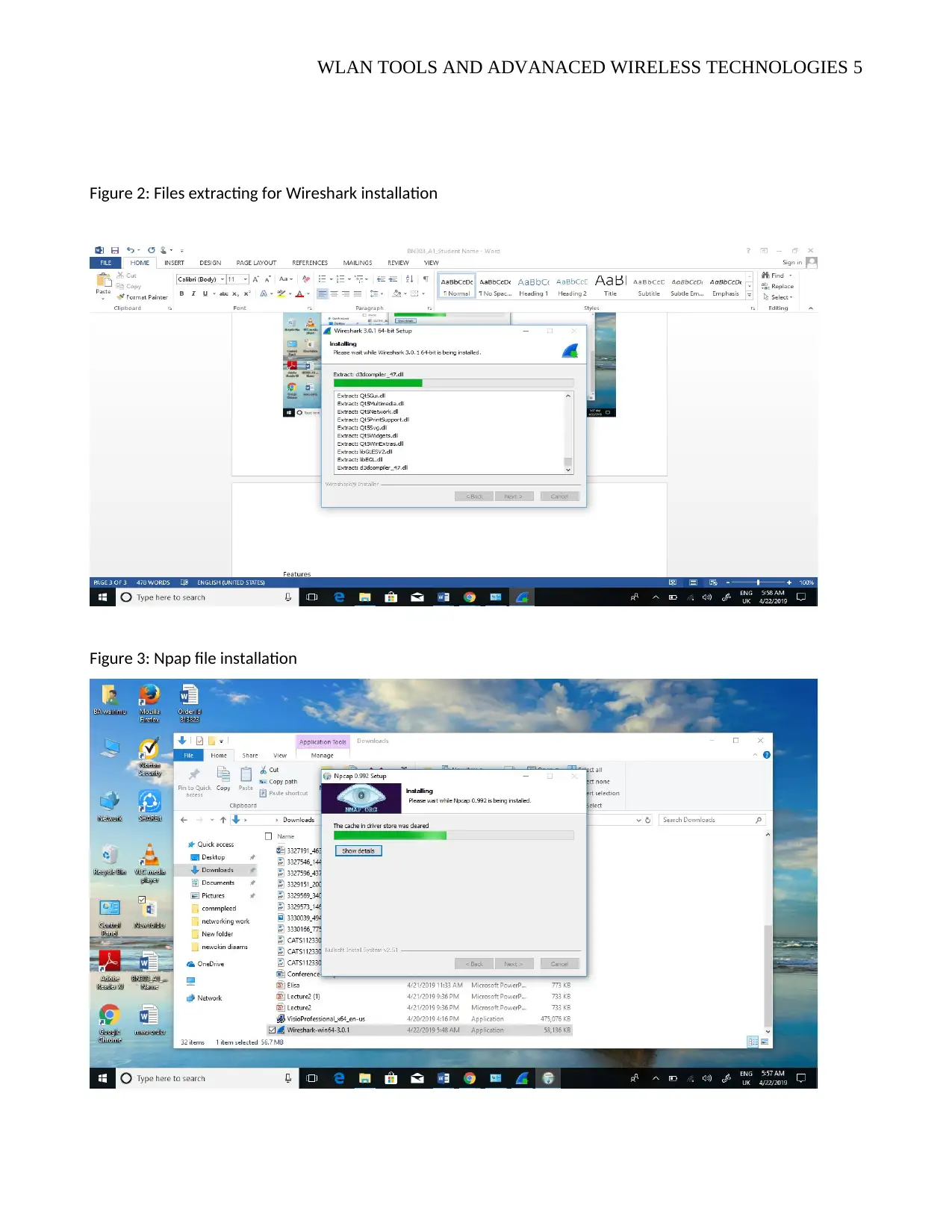
3. Follow the steps until the files starts extracting themselves as shown by figure 2 below. This report
noted that during the installation of Wireshark Npap WLAN sniffing tool also installed itself as shown in
figure three
network appliances which are dropping packets and any latency issues caused by those computers routing
network traffic halfway around the world or any form of hacking attempts and data exfiltration [2].
Level of complexity and installation steps
1. First is to download the WLAN sniffing from filehippo.com/download_wireshark/
2. Click the .exe downloaded file to start the installation process of wireshark. This as shown by figure
one below
Figure 1: Wireshark installation
3. Follow the steps until the files starts extracting themselves as shown by figure 2 below. This report
noted that during the installation of Wireshark Npap WLAN sniffing tool also installed itself as shown in
figure three
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 5
Figure 2: Files extracting for Wireshark installation
Figure 3: Npap file installation
Figure 2: Files extracting for Wireshark installation
Figure 3: Npap file installation
WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 6
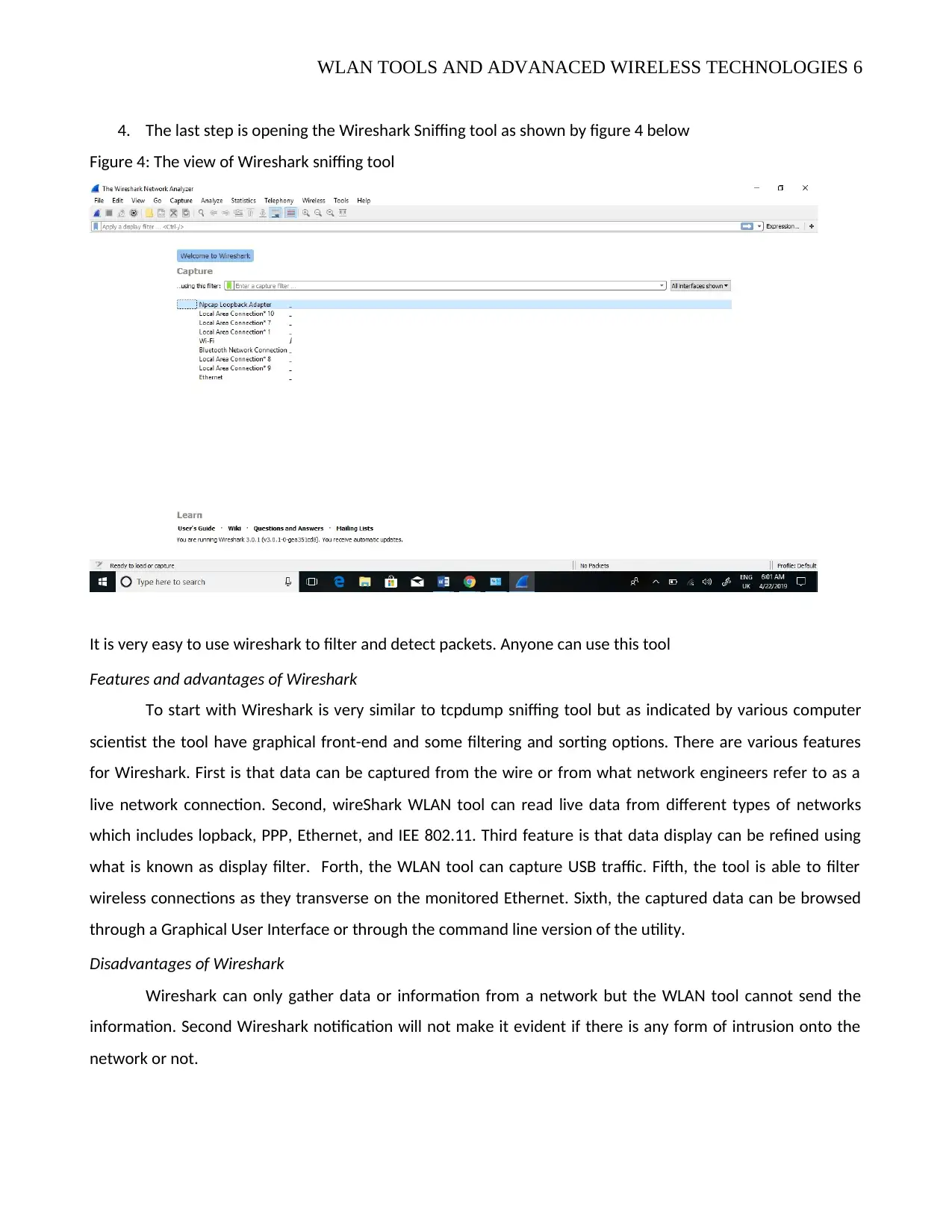
4. The last step is opening the Wireshark Sniffing tool as shown by figure 4 below
Figure 4: The view of Wireshark sniffing tool
It is very easy to use wireshark to filter and detect packets. Anyone can use this tool
Features and advantages of Wireshark
To start with Wireshark is very similar to tcpdump sniffing tool but as indicated by various computer
scientist the tool have graphical front-end and some filtering and sorting options. There are various features
for Wireshark. First is that data can be captured from the wire or from what network engineers refer to as a
live network connection. Second, wireShark WLAN tool can read live data from different types of networks
which includes lopback, PPP, Ethernet, and IEE 802.11. Third feature is that data display can be refined using
what is known as display filter. Forth, the WLAN tool can capture USB traffic. Fifth, the tool is able to filter
wireless connections as they transverse on the monitored Ethernet. Sixth, the captured data can be browsed
through a Graphical User Interface or through the command line version of the utility.
Disadvantages of Wireshark
Wireshark can only gather data or information from a network but the WLAN tool cannot send the
information. Second Wireshark notification will not make it evident if there is any form of intrusion onto the
network or not.
4. The last step is opening the Wireshark Sniffing tool as shown by figure 4 below
Figure 4: The view of Wireshark sniffing tool
It is very easy to use wireshark to filter and detect packets. Anyone can use this tool
Features and advantages of Wireshark
To start with Wireshark is very similar to tcpdump sniffing tool but as indicated by various computer
scientist the tool have graphical front-end and some filtering and sorting options. There are various features
for Wireshark. First is that data can be captured from the wire or from what network engineers refer to as a
live network connection. Second, wireShark WLAN tool can read live data from different types of networks
which includes lopback, PPP, Ethernet, and IEE 802.11. Third feature is that data display can be refined using
what is known as display filter. Forth, the WLAN tool can capture USB traffic. Fifth, the tool is able to filter
wireless connections as they transverse on the monitored Ethernet. Sixth, the captured data can be browsed
through a Graphical User Interface or through the command line version of the utility.
Disadvantages of Wireshark
Wireshark can only gather data or information from a network but the WLAN tool cannot send the
information. Second Wireshark notification will not make it evident if there is any form of intrusion onto the
network or not.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 7
Summary and findings
Wireshark WLAN sniffing tool is tool used by network engineers to intercept network traffic and
convert the binary traffic into a human-readable format. This in turn make it very easy for the network
engineers to identify what is crossing onto the network, how much of it, how much latency there is between
certain hops, and how frequent. Lastly, wireshark supports more than 2000 network protocols many of which
are esoteric, the modern security professional, or uncommon. The majority of packets on the organization
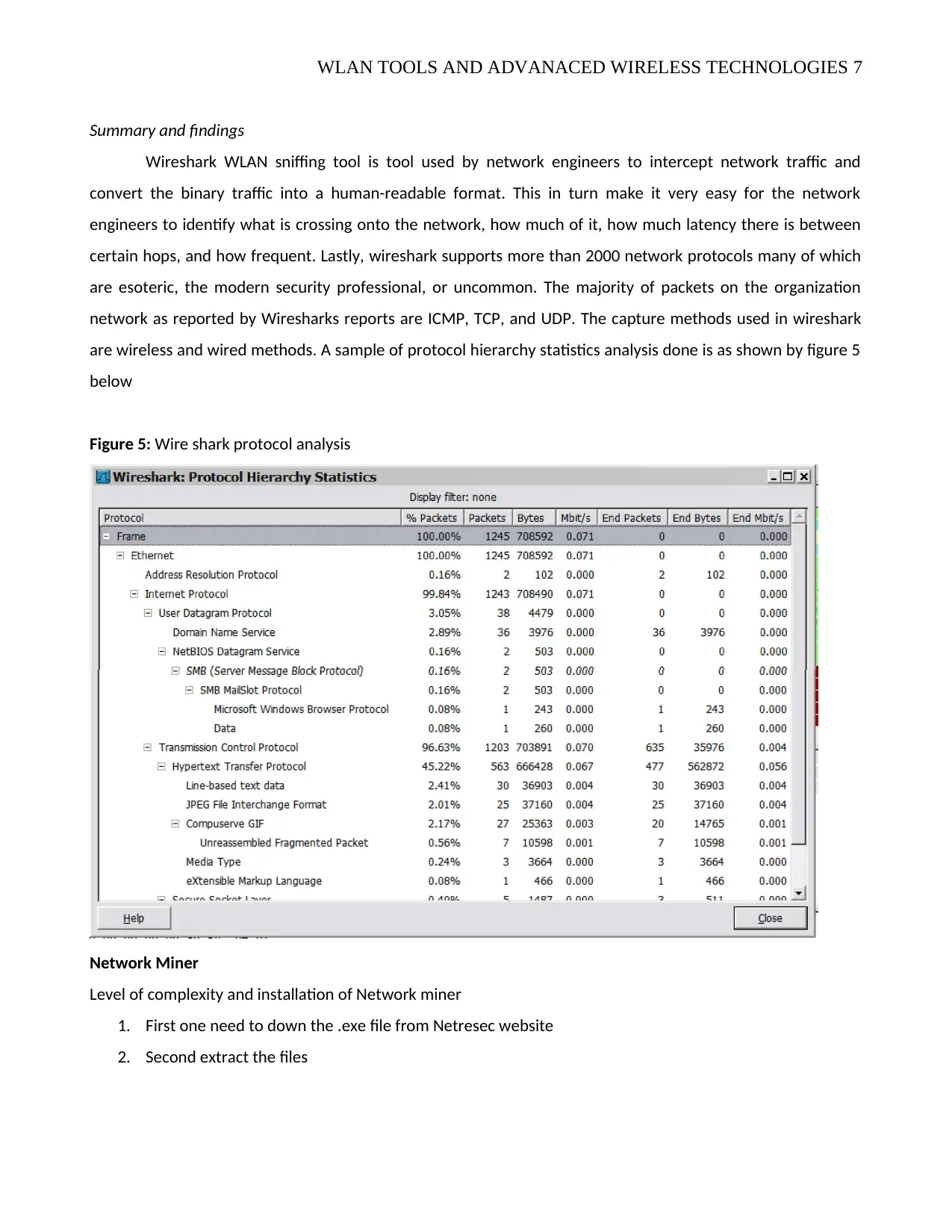
network as reported by Wiresharks reports are ICMP, TCP, and UDP. The capture methods used in wireshark
are wireless and wired methods. A sample of protocol hierarchy statistics analysis done is as shown by figure 5
below
Figure 5: Wire shark protocol analysis
Network Miner
Level of complexity and installation of Network miner
1. First one need to down the .exe file from Netresec website
2. Second extract the files
Summary and findings
Wireshark WLAN sniffing tool is tool used by network engineers to intercept network traffic and
convert the binary traffic into a human-readable format. This in turn make it very easy for the network
engineers to identify what is crossing onto the network, how much of it, how much latency there is between
certain hops, and how frequent. Lastly, wireshark supports more than 2000 network protocols many of which
are esoteric, the modern security professional, or uncommon. The majority of packets on the organization
network as reported by Wiresharks reports are ICMP, TCP, and UDP. The capture methods used in wireshark
are wireless and wired methods. A sample of protocol hierarchy statistics analysis done is as shown by figure 5
below
Figure 5: Wire shark protocol analysis
Network Miner
Level of complexity and installation of Network miner
1. First one need to down the .exe file from Netresec website
2. Second extract the files
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
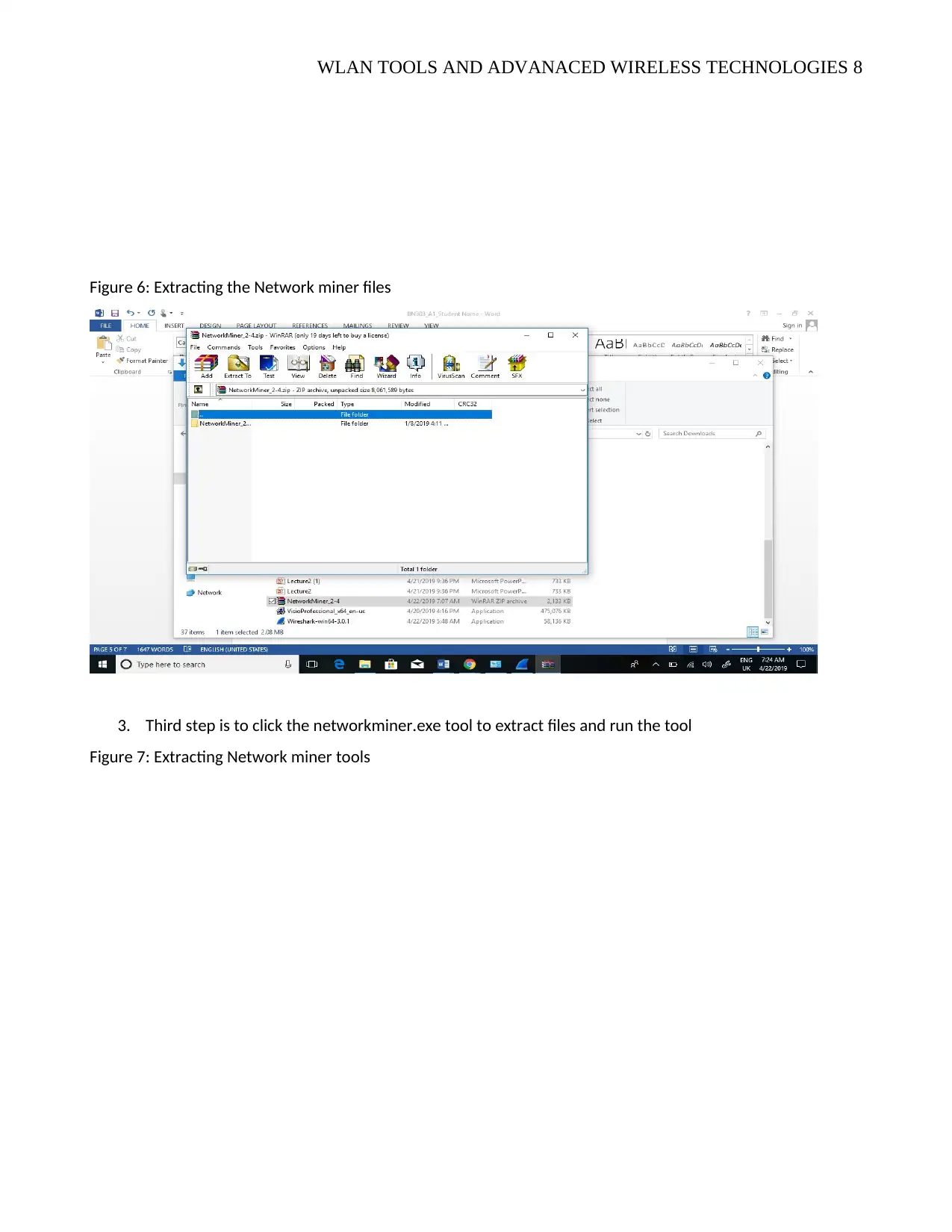
WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 8
Figure 6: Extracting the Network miner files
3. Third step is to click the networkminer.exe tool to extract files and run the tool
Figure 7: Extracting Network miner tools
Figure 6: Extracting the Network miner files
3. Third step is to click the networkminer.exe tool to extract files and run the tool
Figure 7: Extracting Network miner tools
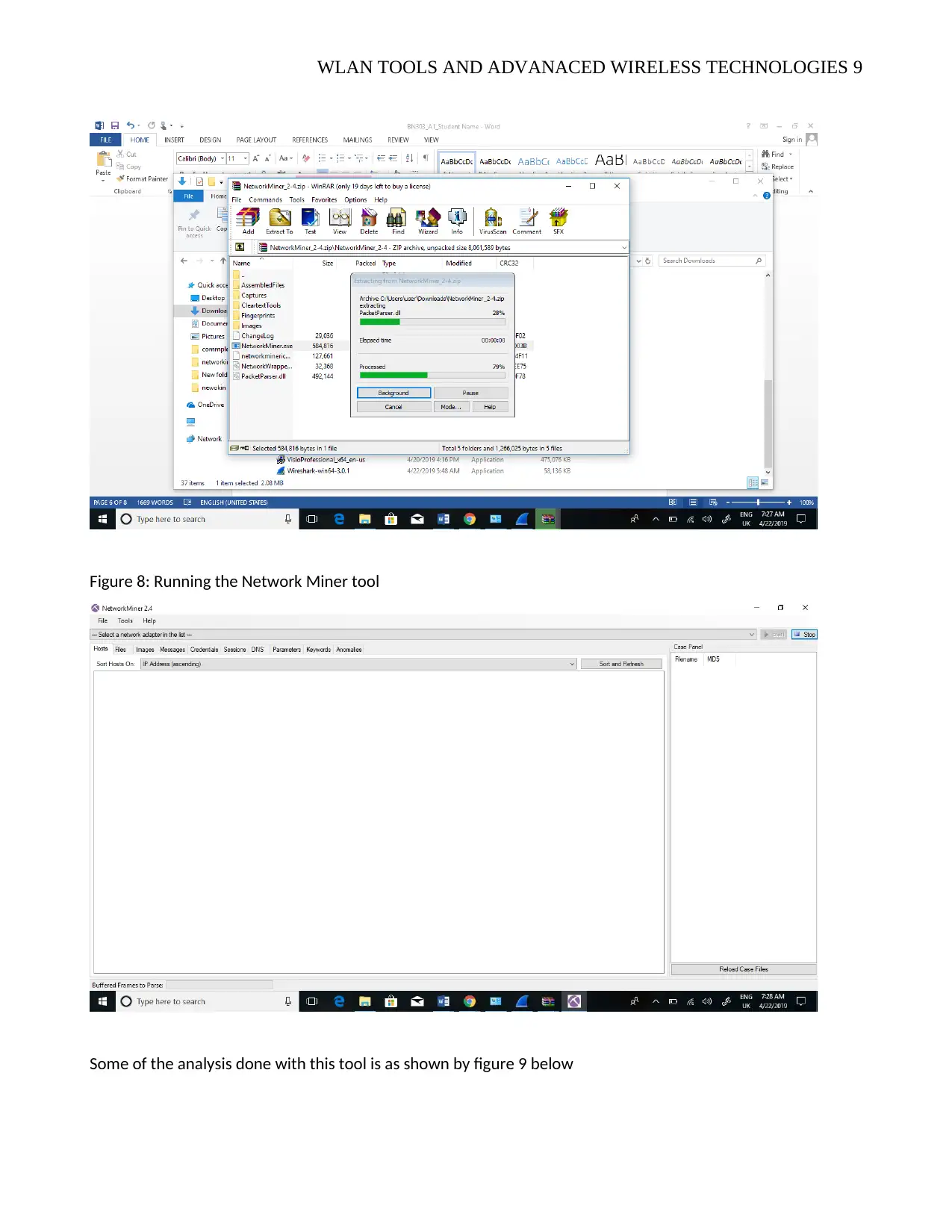
WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 9
Figure 8: Running the Network Miner tool
Some of the analysis done with this tool is as shown by figure 9 below
Figure 8: Running the Network Miner tool
Some of the analysis done with this tool is as shown by figure 9 below
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
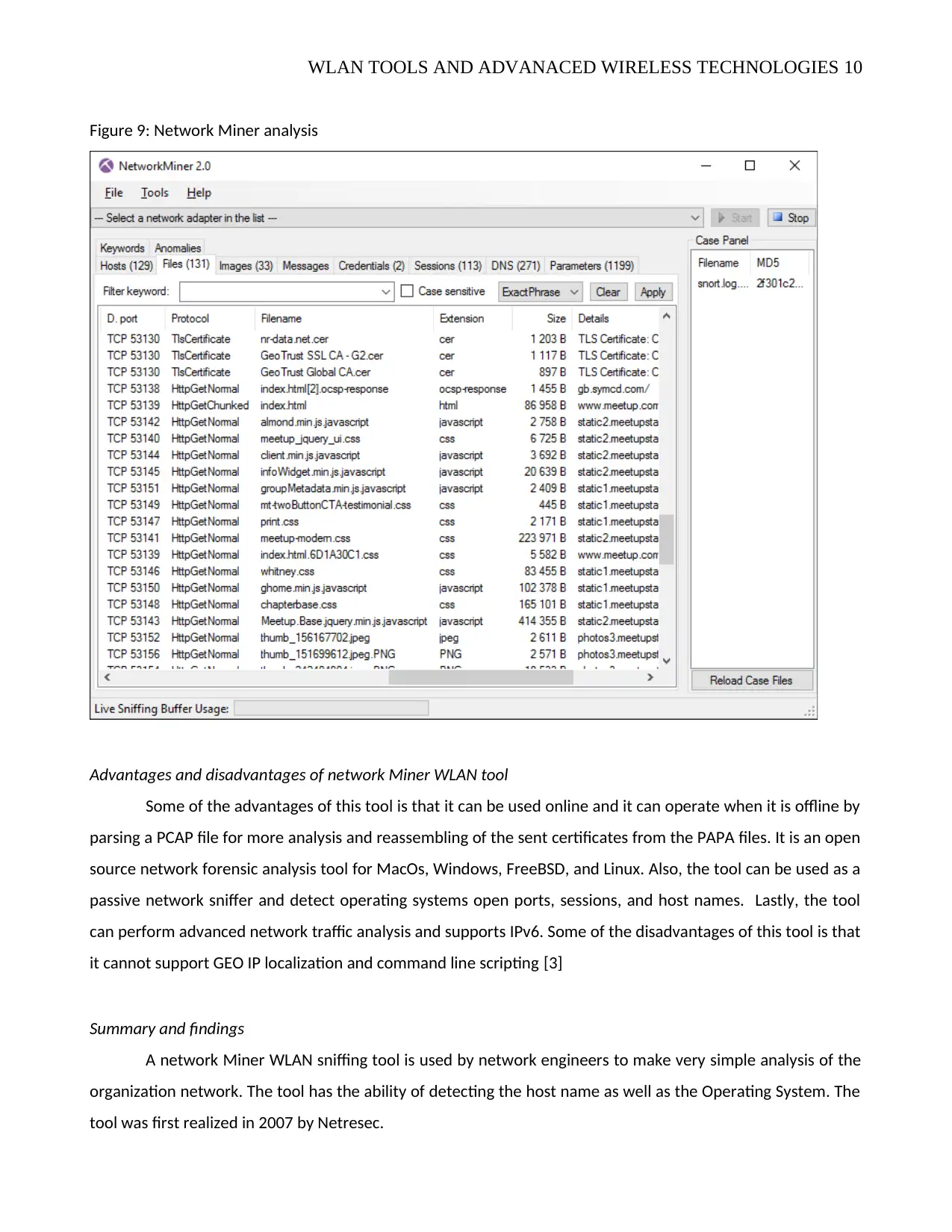
WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 10
Figure 9: Network Miner analysis
Advantages and disadvantages of network Miner WLAN tool
Some of the advantages of this tool is that it can be used online and it can operate when it is offline by
parsing a PCAP file for more analysis and reassembling of the sent certificates from the PAPA files. It is an open
source network forensic analysis tool for MacOs, Windows, FreeBSD, and Linux. Also, the tool can be used as a
passive network sniffer and detect operating systems open ports, sessions, and host names. Lastly, the tool
can perform advanced network traffic analysis and supports IPv6. Some of the disadvantages of this tool is that
it cannot support GEO IP localization and command line scripting [3]
Summary and findings
A network Miner WLAN sniffing tool is used by network engineers to make very simple analysis of the
organization network. The tool has the ability of detecting the host name as well as the Operating System. The
tool was first realized in 2007 by Netresec.
Figure 9: Network Miner analysis
Advantages and disadvantages of network Miner WLAN tool
Some of the advantages of this tool is that it can be used online and it can operate when it is offline by
parsing a PCAP file for more analysis and reassembling of the sent certificates from the PAPA files. It is an open
source network forensic analysis tool for MacOs, Windows, FreeBSD, and Linux. Also, the tool can be used as a
passive network sniffer and detect operating systems open ports, sessions, and host names. Lastly, the tool
can perform advanced network traffic analysis and supports IPv6. Some of the disadvantages of this tool is that
it cannot support GEO IP localization and command line scripting [3]
Summary and findings
A network Miner WLAN sniffing tool is used by network engineers to make very simple analysis of the
organization network. The tool has the ability of detecting the host name as well as the Operating System. The
tool was first realized in 2007 by Netresec.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
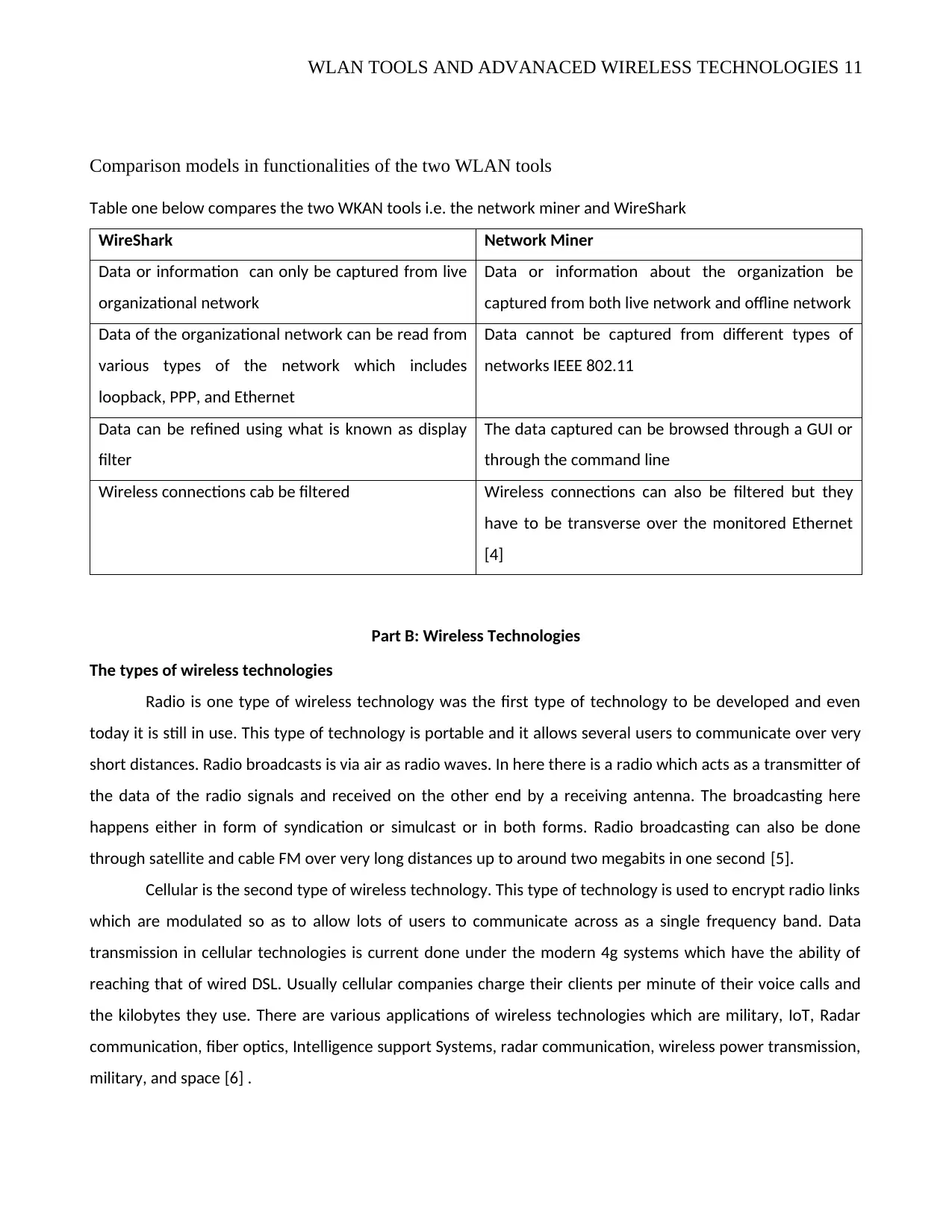
WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 11
Comparison models in functionalities of the two WLAN tools
Table one below compares the two WKAN tools i.e. the network miner and WireShark
WireShark Network Miner
Data or information can only be captured from live
organizational network
Data or information about the organization be
captured from both live network and offline network
Data of the organizational network can be read from
various types of the network which includes
loopback, PPP, and Ethernet
Data cannot be captured from different types of
networks IEEE 802.11
Data can be refined using what is known as display
filter
The data captured can be browsed through a GUI or
through the command line
Wireless connections cab be filtered Wireless connections can also be filtered but they
have to be transverse over the monitored Ethernet
[4]
Part B: Wireless Technologies
The types of wireless technologies
Radio is one type of wireless technology was the first type of technology to be developed and even
today it is still in use. This type of technology is portable and it allows several users to communicate over very
short distances. Radio broadcasts is via air as radio waves. In here there is a radio which acts as a transmitter of
the data of the radio signals and received on the other end by a receiving antenna. The broadcasting here
happens either in form of syndication or simulcast or in both forms. Radio broadcasting can also be done
through satellite and cable FM over very long distances up to around two megabits in one second [5].
Cellular is the second type of wireless technology. This type of technology is used to encrypt radio links
which are modulated so as to allow lots of users to communicate across as a single frequency band. Data
transmission in cellular technologies is current done under the modern 4g systems which have the ability of
reaching that of wired DSL. Usually cellular companies charge their clients per minute of their voice calls and
the kilobytes they use. There are various applications of wireless technologies which are military, IoT, Radar
communication, fiber optics, Intelligence support Systems, radar communication, wireless power transmission,
military, and space [6] .
Comparison models in functionalities of the two WLAN tools
Table one below compares the two WKAN tools i.e. the network miner and WireShark
WireShark Network Miner
Data or information can only be captured from live
organizational network
Data or information about the organization be
captured from both live network and offline network
Data of the organizational network can be read from
various types of the network which includes
loopback, PPP, and Ethernet
Data cannot be captured from different types of
networks IEEE 802.11
Data can be refined using what is known as display
filter
The data captured can be browsed through a GUI or
through the command line
Wireless connections cab be filtered Wireless connections can also be filtered but they
have to be transverse over the monitored Ethernet
[4]
Part B: Wireless Technologies
The types of wireless technologies
Radio is one type of wireless technology was the first type of technology to be developed and even
today it is still in use. This type of technology is portable and it allows several users to communicate over very
short distances. Radio broadcasts is via air as radio waves. In here there is a radio which acts as a transmitter of
the data of the radio signals and received on the other end by a receiving antenna. The broadcasting here
happens either in form of syndication or simulcast or in both forms. Radio broadcasting can also be done
through satellite and cable FM over very long distances up to around two megabits in one second [5].
Cellular is the second type of wireless technology. This type of technology is used to encrypt radio links
which are modulated so as to allow lots of users to communicate across as a single frequency band. Data
transmission in cellular technologies is current done under the modern 4g systems which have the ability of
reaching that of wired DSL. Usually cellular companies charge their clients per minute of their voice calls and
the kilobytes they use. There are various applications of wireless technologies which are military, IoT, Radar
communication, fiber optics, Intelligence support Systems, radar communication, wireless power transmission,
military, and space [6] .

WLAN TOOLS AND ADVANACED WIRELESS TECHNOLOGIES 12
Proposal of the best wireless technologies
The essential types of wireless technologies and the one which have been implemented by most of the
organizations are WiFi, Femtocell, WiMax, 4G, and 3G. This paper will go for these five types of technologies.
WiFi technology can be used by organizations to provide high speed internet connection without the use of
wires. Wi-Fi technology can be used in education, home, and in education industry. Femtocells is a small, low-
power cellular base station that resemble wireless routers. In addition the wireless technology can act as a
repeater for boosting signals. One of the reason as to why this paper has gone for this type of technology is
that it is very cheaper to install and it offers lots of advantages for both the end consumer and the operators.
In here the operator can benefit by providing an extended coverage which is near to the users at very low cost.
WiMax is a type of wireless technology which is based on the IEE 802.16 standard. Some of the reasons this
paper has gone for this type of technology is that it supports very high speed data and voice transfer over very
long distances. Second this type of technology has a very high network coverage as compared to WiFi
technology; even cellular like performance can be achieved with mobile wiMax. Lastly, this type of technology
is considered cheaper aand an alternative method for wired types of technologies or cable modems [7].
Conclusion
The two types of tools adopted in this report are Network Miner and Wireshark. As highlighted from
the report it is very easy to use the tools. Second the report has highlighted the different types of wireless
technologies but five types have been adopted and proposed for use by organizations.
References
[1] M.-T. Zhou, Y. Zhang and L. T. Yang, Wireless Technologies, New York: Springer Press, 2017.
[2] InformationResourcesManagementAssociation, Wireless Technologies, tools,and concepts, London:
Information Science Reference Press, 2014.
[3] R. Temple and J. Regnault, Wireless Network technologies, New York: Springer Press, 2018.
[4] M. D. Ciampa, CWSP guide to wireless security, Chicago: Springer Press, 2017.
Proposal of the best wireless technologies
The essential types of wireless technologies and the one which have been implemented by most of the
organizations are WiFi, Femtocell, WiMax, 4G, and 3G. This paper will go for these five types of technologies.
WiFi technology can be used by organizations to provide high speed internet connection without the use of
wires. Wi-Fi technology can be used in education, home, and in education industry. Femtocells is a small, low-
power cellular base station that resemble wireless routers. In addition the wireless technology can act as a
repeater for boosting signals. One of the reason as to why this paper has gone for this type of technology is
that it is very cheaper to install and it offers lots of advantages for both the end consumer and the operators.
In here the operator can benefit by providing an extended coverage which is near to the users at very low cost.
WiMax is a type of wireless technology which is based on the IEE 802.16 standard. Some of the reasons this
paper has gone for this type of technology is that it supports very high speed data and voice transfer over very
long distances. Second this type of technology has a very high network coverage as compared to WiFi
technology; even cellular like performance can be achieved with mobile wiMax. Lastly, this type of technology
is considered cheaper aand an alternative method for wired types of technologies or cable modems [7].
Conclusion
The two types of tools adopted in this report are Network Miner and Wireshark. As highlighted from
the report it is very easy to use the tools. Second the report has highlighted the different types of wireless
technologies but five types have been adopted and proposed for use by organizations.
References
[1] M.-T. Zhou, Y. Zhang and L. T. Yang, Wireless Technologies, New York: Springer Press, 2017.
[2] InformationResourcesManagementAssociation, Wireless Technologies, tools,and concepts, London:
Information Science Reference Press, 2014.
[3] R. Temple and J. Regnault, Wireless Network technologies, New York: Springer Press, 2018.
[4] M. D. Ciampa, CWSP guide to wireless security, Chicago: Springer Press, 2017.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




