Xemba Translations: Project Performance and Risk Mitigation
VerifiedAdded on 2023/06/09
|8
|1774
|95
Project
AI Summary
This project analyzes the risks and performance metrics associated with Xemba Translations' expansion to telecommuting. The document begins with a risk assessment matrix, identifying potential legal, network, and malware threats, and proposes mitigation strategies such as encryption, security tools, and device tracking. Project performance is evaluated using metrics like Earned Value, Employee Satisfaction Score, and Return on Investment (ROI), with justifications provided for each. The project reveals that the project is on budget with a slight schedule variance, and addresses three key problems: schedule variation, employee dissatisfaction, and potential failure to achieve estimated benefits. Mitigation strategies include schedule analysis, conflict resolution, and cost-benefit analysis. The project concludes with a formal executive summary, reiterating the risks and mitigation strategies, emphasizing the importance of data encryption, advanced security tools, and regular device updates and audits to ensure the success of the telecommuting initiative. The project also highlights the importance of regular project reviews and audits.

Xemba Translations
Risk Assessment & Project Performance
Risk Assessment & Project Performance
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Xemba Translations
Table of Contents
Risk Assessment Matrix........................................................................................................................2
Project Performance Metrics.................................................................................................................4
Metrics for Project Performance & their Justification.......................................................................4
Earned Value.................................................................................................................................4
Employee Satisfaction Score.........................................................................................................4
Return on Investment (ROI)..........................................................................................................4
Interpretation of Project’s Current Performance................................................................................4
Three Problems & their Mitigation....................................................................................................4
Formal Executive Summary..................................................................................................................5
References.............................................................................................................................................7
1
Table of Contents
Risk Assessment Matrix........................................................................................................................2
Project Performance Metrics.................................................................................................................4
Metrics for Project Performance & their Justification.......................................................................4
Earned Value.................................................................................................................................4
Employee Satisfaction Score.........................................................................................................4
Return on Investment (ROI)..........................................................................................................4
Interpretation of Project’s Current Performance................................................................................4
Three Problems & their Mitigation....................................................................................................4
Formal Executive Summary..................................................................................................................5
References.............................................................................................................................................7
1
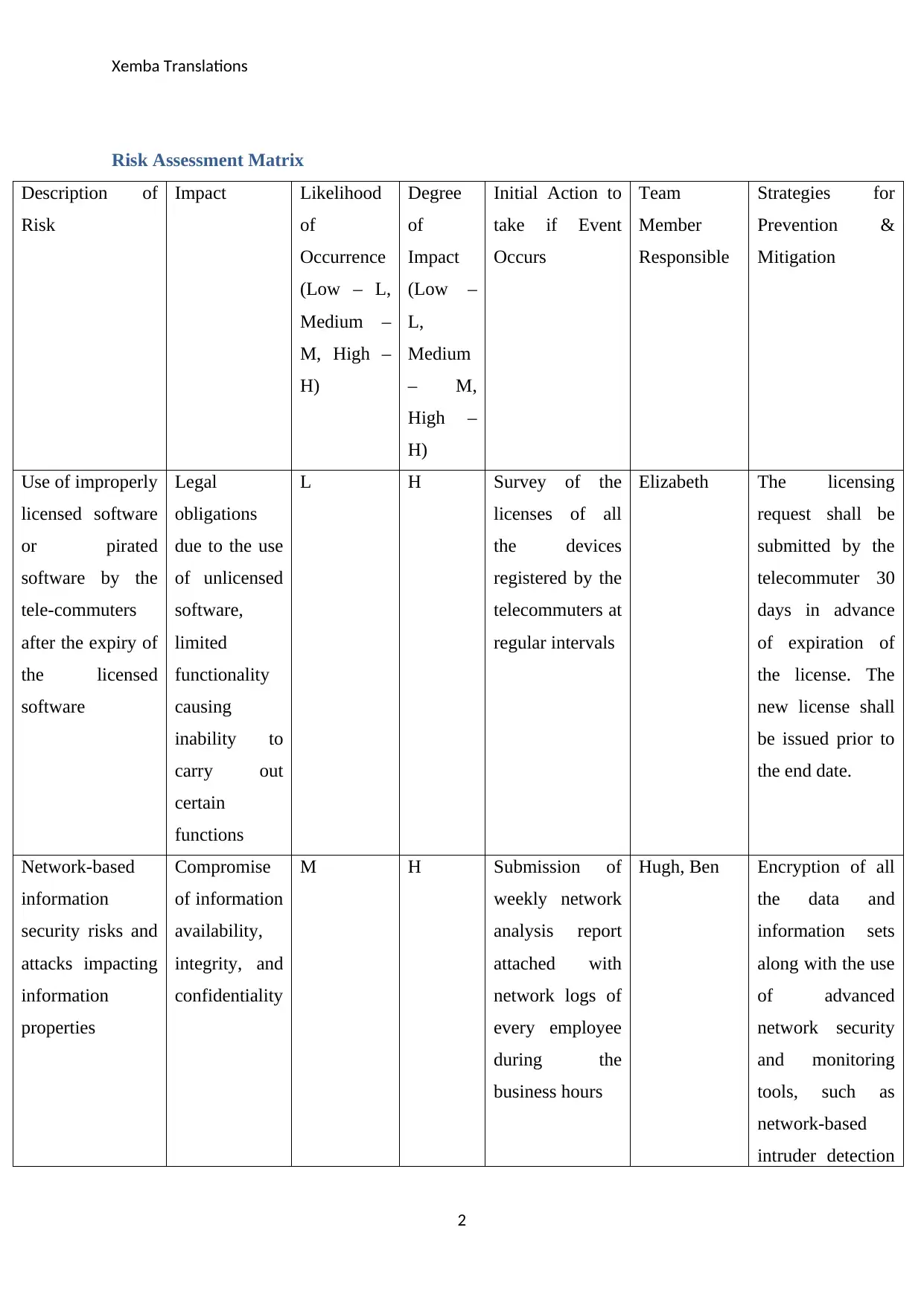
Xemba Translations
Risk Assessment Matrix
Description of
Risk
Impact Likelihood
of
Occurrence
(Low – L,
Medium –
M, High –
H)
Degree
of
Impact
(Low –
L,
Medium
– M,
High –
H)
Initial Action to
take if Event
Occurs
Team
Member
Responsible
Strategies for
Prevention &
Mitigation
Use of improperly
licensed software
or pirated
software by the
tele-commuters
after the expiry of
the licensed
software
Legal
obligations
due to the use
of unlicensed
software,
limited
functionality
causing
inability to
carry out
certain
functions
L H Survey of the
licenses of all
the devices
registered by the
telecommuters at
regular intervals
Elizabeth The licensing
request shall be
submitted by the
telecommuter 30
days in advance
of expiration of
the license. The
new license shall
be issued prior to
the end date.
Network-based
information
security risks and
attacks impacting
information
properties
Compromise
of information
availability,
integrity, and
confidentiality
M H Submission of
weekly network
analysis report
attached with
network logs of
every employee
during the
business hours
Hugh, Ben Encryption of all
the data and
information sets
along with the use
of advanced
network security
and monitoring
tools, such as
network-based
intruder detection
2
Risk Assessment Matrix
Description of
Risk
Impact Likelihood
of
Occurrence
(Low – L,
Medium –
M, High –
H)
Degree
of
Impact
(Low –
L,
Medium
– M,
High –
H)
Initial Action to
take if Event
Occurs
Team
Member
Responsible
Strategies for
Prevention &
Mitigation
Use of improperly
licensed software
or pirated
software by the
tele-commuters
after the expiry of
the licensed
software
Legal
obligations
due to the use
of unlicensed
software,
limited
functionality
causing
inability to
carry out
certain
functions
L H Survey of the
licenses of all
the devices
registered by the
telecommuters at
regular intervals
Elizabeth The licensing
request shall be
submitted by the
telecommuter 30
days in advance
of expiration of
the license. The
new license shall
be issued prior to
the end date.
Network-based
information
security risks and
attacks impacting
information
properties
Compromise
of information
availability,
integrity, and
confidentiality
M H Submission of
weekly network
analysis report
attached with
network logs of
every employee
during the
business hours
Hugh, Ben Encryption of all
the data and
information sets
along with the use
of advanced
network security
and monitoring
tools, such as
network-based
intruder detection
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
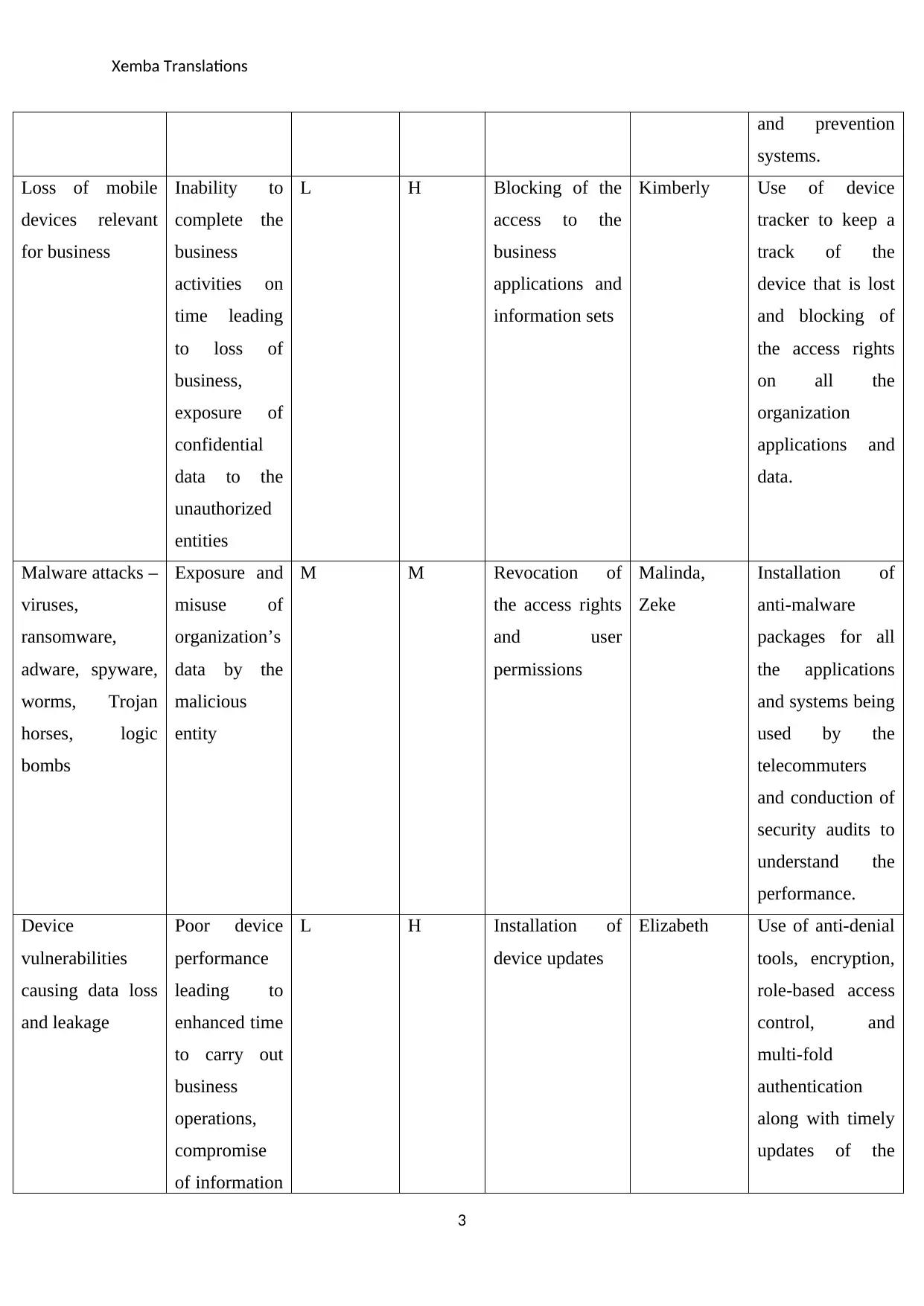
Xemba Translations
and prevention
systems.
Loss of mobile
devices relevant
for business
Inability to
complete the
business
activities on
time leading
to loss of
business,
exposure of
confidential
data to the
unauthorized
entities
L H Blocking of the
access to the
business
applications and
information sets
Kimberly Use of device
tracker to keep a
track of the
device that is lost
and blocking of
the access rights
on all the
organization
applications and
data.
Malware attacks –
viruses,
ransomware,
adware, spyware,
worms, Trojan
horses, logic
bombs
Exposure and
misuse of
organization’s
data by the
malicious
entity
M M Revocation of
the access rights
and user
permissions
Malinda,
Zeke
Installation of
anti-malware
packages for all
the applications
and systems being
used by the
telecommuters
and conduction of
security audits to
understand the
performance.
Device
vulnerabilities
causing data loss
and leakage
Poor device
performance
leading to
enhanced time
to carry out
business
operations,
compromise
of information
L H Installation of
device updates
Elizabeth Use of anti-denial
tools, encryption,
role-based access
control, and
multi-fold
authentication
along with timely
updates of the
3
and prevention
systems.
Loss of mobile
devices relevant
for business
Inability to
complete the
business
activities on
time leading
to loss of
business,
exposure of
confidential
data to the
unauthorized
entities
L H Blocking of the
access to the
business
applications and
information sets
Kimberly Use of device
tracker to keep a
track of the
device that is lost
and blocking of
the access rights
on all the
organization
applications and
data.
Malware attacks –
viruses,
ransomware,
adware, spyware,
worms, Trojan
horses, logic
bombs
Exposure and
misuse of
organization’s
data by the
malicious
entity
M M Revocation of
the access rights
and user
permissions
Malinda,
Zeke
Installation of
anti-malware
packages for all
the applications
and systems being
used by the
telecommuters
and conduction of
security audits to
understand the
performance.
Device
vulnerabilities
causing data loss
and leakage
Poor device
performance
leading to
enhanced time
to carry out
business
operations,
compromise
of information
L H Installation of
device updates
Elizabeth Use of anti-denial
tools, encryption,
role-based access
control, and
multi-fold
authentication
along with timely
updates of the
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Xemba Translations
security and
privacy
devices.
Project Performance Metrics
Metrics for Project Performance & their Justification
Earned Value
The work completed till a specified date and the budget at the time of completion is
calculated under this metrics. It is chosen as it will provide the cost variance and schedule
variance involved to take the necessary steps of action (Bryde, Unterhitzenberger & Joby,
2018).
Employee Satisfaction Score
Satisfied employees tend to show higher productivity levels as compared to the unsatisfied
employees. The metrics will show the satisfaction level of the telecommuters to make the
changes in the approach, if necessary.
Return on Investment (ROI)
The benefits shall be divided by the project costs to determine the ROI and it is a necessary
metrics as it showcases the benefits being achieved with the project.
Interpretation of Project’s Current Performance
As per the current situation of the project, the earned value of the project shows the project to
be on-budget. There is a slight variance in the schedule that is observed. The employee
satisfaction score for some is excellent while there are areas of improvement that are
highlighted and may be improved upon. The estimated ROI of the project is as per the
expectations (Sauermann, 2016).
Three Problems & their Mitigation
The first problem is schedule variation that may have an adverse impact on project delivery if
not handled and mitigated. It shall be mitigated by analysing the project progress and
developing a schedule for the remaining project activities.
The second problem identified is the reduced employee satisfaction for some of the
employees associated with the project. The root cause behind the same is the conflicts and
4
security and
privacy
devices.
Project Performance Metrics
Metrics for Project Performance & their Justification
Earned Value
The work completed till a specified date and the budget at the time of completion is
calculated under this metrics. It is chosen as it will provide the cost variance and schedule
variance involved to take the necessary steps of action (Bryde, Unterhitzenberger & Joby,
2018).
Employee Satisfaction Score
Satisfied employees tend to show higher productivity levels as compared to the unsatisfied
employees. The metrics will show the satisfaction level of the telecommuters to make the
changes in the approach, if necessary.
Return on Investment (ROI)
The benefits shall be divided by the project costs to determine the ROI and it is a necessary
metrics as it showcases the benefits being achieved with the project.
Interpretation of Project’s Current Performance
As per the current situation of the project, the earned value of the project shows the project to
be on-budget. There is a slight variance in the schedule that is observed. The employee
satisfaction score for some is excellent while there are areas of improvement that are
highlighted and may be improved upon. The estimated ROI of the project is as per the
expectations (Sauermann, 2016).
Three Problems & their Mitigation
The first problem is schedule variation that may have an adverse impact on project delivery if
not handled and mitigated. It shall be mitigated by analysing the project progress and
developing a schedule for the remaining project activities.
The second problem identified is the reduced employee satisfaction for some of the
employees associated with the project. The root cause behind the same is the conflicts and
4

Xemba Translations
disputes among the employees on project related issues. There shall be conflict resolution
activities and team building tasks organized for better team cohesion and performance (Chen,
Hou & Wu, 2016).
The third problem identified is inability to achieve the estimated project benefits that may
lead to limited profits or enhanced losses. There shall be cost-benefit analysis carried out
after regular intervals to mitigate the issue.
Formal Executive Summary
Xemba Translations has decided to enhance the number of telecommuters associated with the
organization to bring down the overall costs and enhance the organization performance.
There are several risks associated with the project and some of the primary risks involved are
the security risks and attacks. The telecommuters associated with the organization may make
use of their personal devices for carrying out organizational tasks and activities. The range of
these devices may include laptops, tablets, Smartphones, computer systems, and many others.
Also, the network connectivity used by the telecommuters may also vary as they may choose
public or private network connection to carry out the execution of the business activities. This
may bring up the network-related security risks, such as, denial of service attacks,
unauthorized network monitoring, man in the middle attacks, eavesdropping attacks, and
likewise. There are measures that shall be used to mitigate and avoid these attacks. The first
and the foremost step shall be to encrypt all of the data and information sets so that the
attacks may not have any impact on the information security and privacy. There are advanced
network security and control tools that have been released in the market and the same shall be
deployed for all the telecommuters. Network-based intrusion detection and prevention
systems along with network scanning tools shall be deployed (Webb, Maynard, Ahmad &
Shanks, 2014).
Another risk that may impact the business operations and performance is the malware attacks.
There are a wide range of malware being developed by the malicious entities, such as viruses,
worms, logic bombs, Trojan horses, ransomware, spyware, and adware. Anti-malware tools
and applications shall be deployed for all the employees to control and mitigate the risk.
There may also be device related risks and attacks that may come up. Most of the devices that
will be used by the telecommuters will be mobile devices and such devices have an enhanced
probability of getting stolen or lost (Taylor, 2015). The occurrence of such a risk will have
5
disputes among the employees on project related issues. There shall be conflict resolution
activities and team building tasks organized for better team cohesion and performance (Chen,
Hou & Wu, 2016).
The third problem identified is inability to achieve the estimated project benefits that may
lead to limited profits or enhanced losses. There shall be cost-benefit analysis carried out
after regular intervals to mitigate the issue.
Formal Executive Summary
Xemba Translations has decided to enhance the number of telecommuters associated with the
organization to bring down the overall costs and enhance the organization performance.
There are several risks associated with the project and some of the primary risks involved are
the security risks and attacks. The telecommuters associated with the organization may make
use of their personal devices for carrying out organizational tasks and activities. The range of
these devices may include laptops, tablets, Smartphones, computer systems, and many others.
Also, the network connectivity used by the telecommuters may also vary as they may choose
public or private network connection to carry out the execution of the business activities. This
may bring up the network-related security risks, such as, denial of service attacks,
unauthorized network monitoring, man in the middle attacks, eavesdropping attacks, and
likewise. There are measures that shall be used to mitigate and avoid these attacks. The first
and the foremost step shall be to encrypt all of the data and information sets so that the
attacks may not have any impact on the information security and privacy. There are advanced
network security and control tools that have been released in the market and the same shall be
deployed for all the telecommuters. Network-based intrusion detection and prevention
systems along with network scanning tools shall be deployed (Webb, Maynard, Ahmad &
Shanks, 2014).
Another risk that may impact the business operations and performance is the malware attacks.
There are a wide range of malware being developed by the malicious entities, such as viruses,
worms, logic bombs, Trojan horses, ransomware, spyware, and adware. Anti-malware tools
and applications shall be deployed for all the employees to control and mitigate the risk.
There may also be device related risks and attacks that may come up. Most of the devices that
will be used by the telecommuters will be mobile devices and such devices have an enhanced
probability of getting stolen or lost (Taylor, 2015). The occurrence of such a risk will have
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Xemba Translations
negative implications on the organization. Therefore, it shall be mitigated and controlled by
installing a device tracker on all the devices so that the device may be tracked if it gets lost.
The access rights and permissions to all the business applications shall also be revoked. The
devices used by the telecommuters may not be updated regularly that may bring up enhanced
device vulnerabilities. There must be regular updates launched for the devices and security
audits must also be carried out to avoid delay in the execution of the business operations
(Fazlida & Said, 2015).
There are also certain project-related risks that may come up during the project timeline. The
first problem that may come is schedule variation that may have an adverse impact on project
delivery if not handled and mitigated. It shall be mitigated by analysing the project progress
and developing a schedule for the remaining project activities (Pereira Silva & Miranda
Barros, 2016). The second problem identified is the reduced employee satisfaction for some
of the employees associated with the project. The root cause behind the same is the conflicts
and disputes among the employees on project related issues. There shall be conflict resolution
activities and team building tasks organized for better team cohesion and performance. The
third problem identified is inability to achieve the estimated project benefits that may lead to
limited profits or enhanced losses. There shall be cost-benefit analysis carried out after
regular intervals to mitigate the issue.
There shall also be project reviews and audits that shall be organized and carried out at
regular intervals.
6
negative implications on the organization. Therefore, it shall be mitigated and controlled by
installing a device tracker on all the devices so that the device may be tracked if it gets lost.
The access rights and permissions to all the business applications shall also be revoked. The
devices used by the telecommuters may not be updated regularly that may bring up enhanced
device vulnerabilities. There must be regular updates launched for the devices and security
audits must also be carried out to avoid delay in the execution of the business operations
(Fazlida & Said, 2015).
There are also certain project-related risks that may come up during the project timeline. The
first problem that may come is schedule variation that may have an adverse impact on project
delivery if not handled and mitigated. It shall be mitigated by analysing the project progress
and developing a schedule for the remaining project activities (Pereira Silva & Miranda
Barros, 2016). The second problem identified is the reduced employee satisfaction for some
of the employees associated with the project. The root cause behind the same is the conflicts
and disputes among the employees on project related issues. There shall be conflict resolution
activities and team building tasks organized for better team cohesion and performance. The
third problem identified is inability to achieve the estimated project benefits that may lead to
limited profits or enhanced losses. There shall be cost-benefit analysis carried out after
regular intervals to mitigate the issue.
There shall also be project reviews and audits that shall be organized and carried out at
regular intervals.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Xemba Translations
References
Bryde, D., Unterhitzenberger, C., & Joby, R. (2018). Conditions of success for earned value
analysis in projects. International Journal Of Project Management, 36(3), 474-484.
doi: 10.1016/j.ijproman.2017.12.002
Chen, A., Hou, Y., & Wu, I. (2016). Handling conflict at work – the impact of active and
agreeable conflict styles. International Journal Of Conflict Management, 27(1), 50-
61. doi: 10.1108/ijcma-10-2014-0076
Fazlida, M., & Said, J. (2015). Information Security: Risk, Governance and Implementation
Setback. Procedia Economics And Finance, 28, 243-248. doi: 10.1016/s2212-
5671(15)01106-5
Pereira Silva, M., & Miranda Barros, R. (2016). Earned Value Analysis Deployment in an
Enterprise Using BI Software. IEEE Latin America Transactions, 14(2), 907-912. doi:
10.1109/tla.2016.7437239
Sauermann, J. (2016). Performance measures and worker productivity. IZA World Of Labor.
doi: 10.15185/izawol.260
Taylor, R. (2015). Potential Problems with Information Security Risk Assessments.
Information Security Journal: A Global Perspective, 24(4-6), 177-184. doi:
10.1080/19393555.2015.1092620
Webb, J., Maynard, S., Ahmad, A., & Shanks, G. (2014). Information Security Risk
Management: An Intelligence-Driven Approach. Retrieved from
http://dx.doi.org/10.3127/ajis.v18i3.1096
7
References
Bryde, D., Unterhitzenberger, C., & Joby, R. (2018). Conditions of success for earned value
analysis in projects. International Journal Of Project Management, 36(3), 474-484.
doi: 10.1016/j.ijproman.2017.12.002
Chen, A., Hou, Y., & Wu, I. (2016). Handling conflict at work – the impact of active and
agreeable conflict styles. International Journal Of Conflict Management, 27(1), 50-
61. doi: 10.1108/ijcma-10-2014-0076
Fazlida, M., & Said, J. (2015). Information Security: Risk, Governance and Implementation
Setback. Procedia Economics And Finance, 28, 243-248. doi: 10.1016/s2212-
5671(15)01106-5
Pereira Silva, M., & Miranda Barros, R. (2016). Earned Value Analysis Deployment in an
Enterprise Using BI Software. IEEE Latin America Transactions, 14(2), 907-912. doi:
10.1109/tla.2016.7437239
Sauermann, J. (2016). Performance measures and worker productivity. IZA World Of Labor.
doi: 10.15185/izawol.260
Taylor, R. (2015). Potential Problems with Information Security Risk Assessments.
Information Security Journal: A Global Perspective, 24(4-6), 177-184. doi:
10.1080/19393555.2015.1092620
Webb, J., Maynard, S., Ahmad, A., & Shanks, G. (2014). Information Security Risk
Management: An Intelligence-Driven Approach. Retrieved from
http://dx.doi.org/10.3127/ajis.v18i3.1096
7
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





