Analysis, Editing, and Testing of Authentication Scripts with ZAP Tool
VerifiedAdded on 2022/08/28
|22
|2665
|15
Practical Assignment
AI Summary
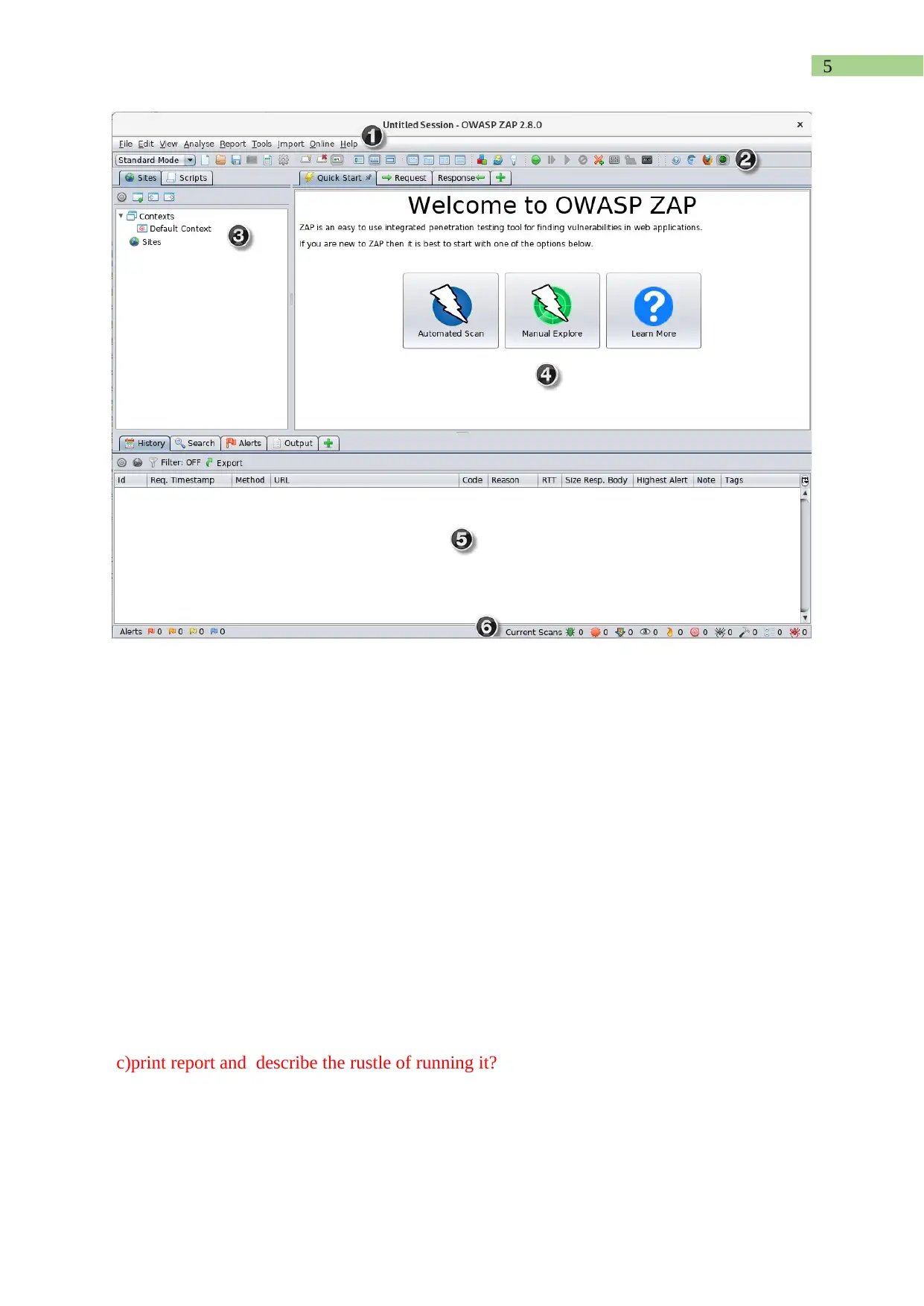
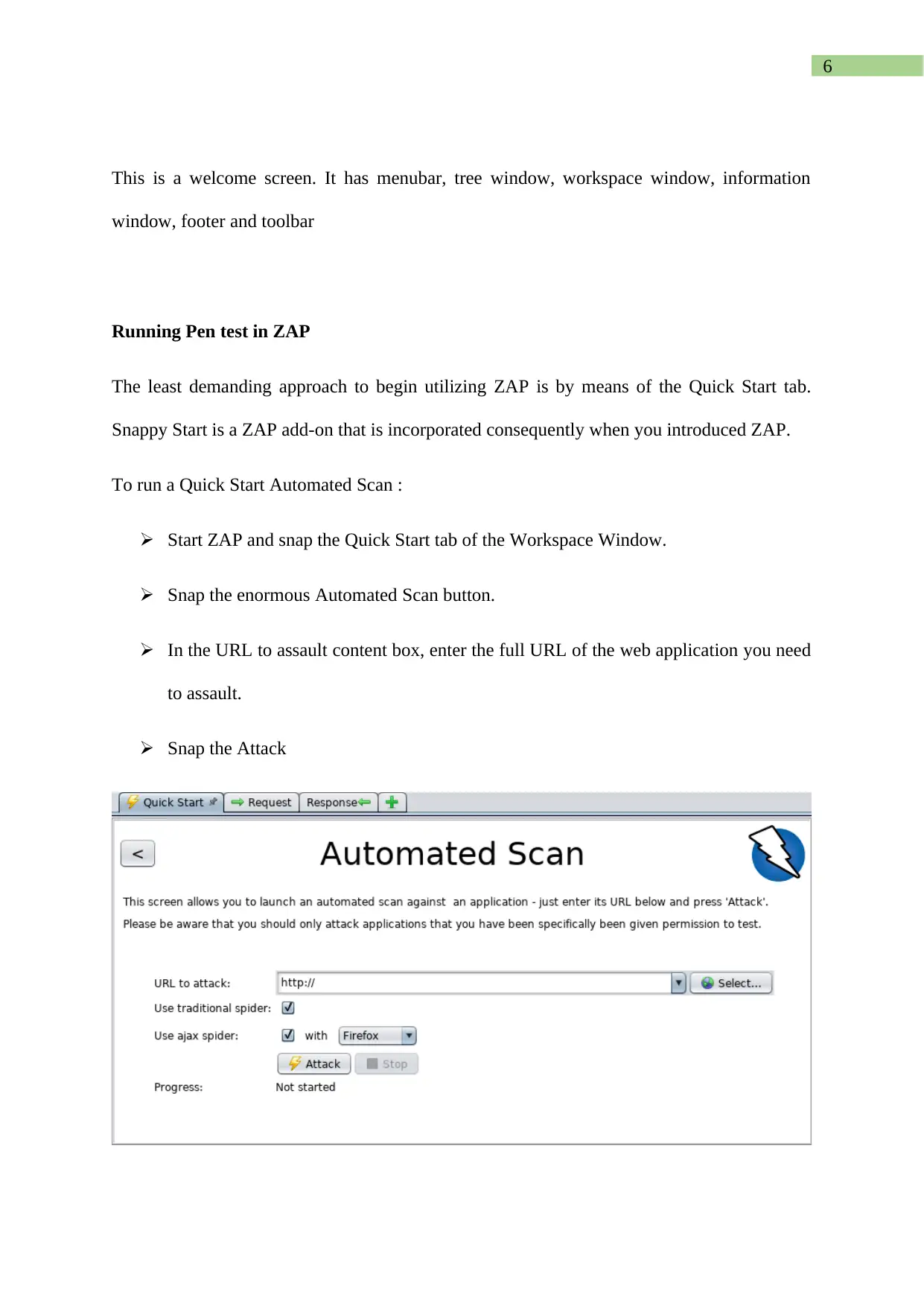
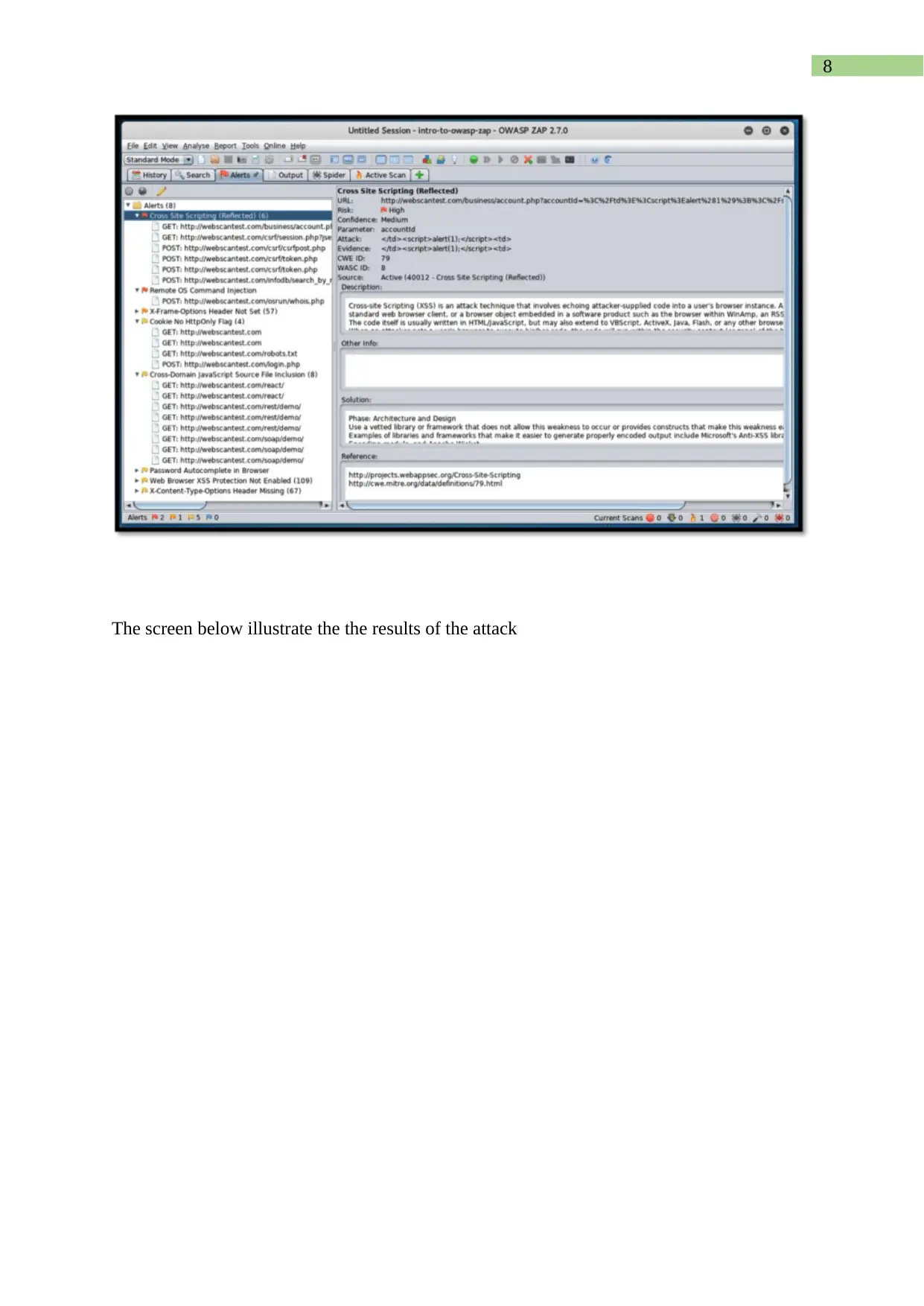
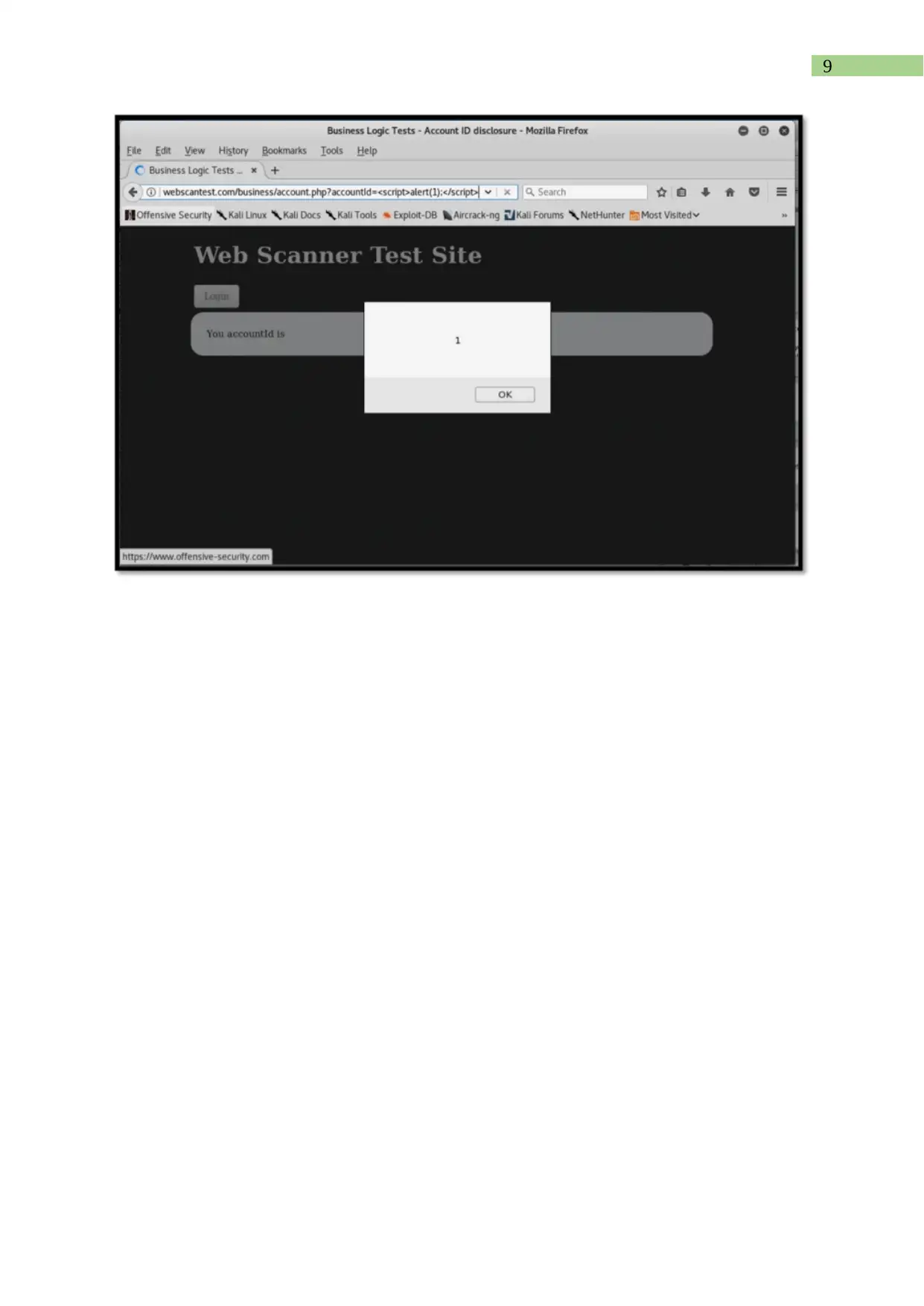
This assignment report details the analysis, editing, and testing of authentication scripts using the Zed Attack Proxy (ZAP) tool. It begins by identifying the script type as an authentication script and explains its purpose within a context. The report then guides the user through editing the script to accept username and password parameters, along with running the script on localhost using ZAP, including screenshots and descriptions for each step. The report also covers running a penetration test using ZAP, describes the interface, and explains the automated scan process, including how to print a report detailing the vulnerabilities found. Furthermore, the assignment explores the use of HTTP sender scripts to modify HTTP messages and identify potential vulnerabilities, emphasizing the use of breakpoints to intercept and alter data parameters. The report includes detailed steps for configuration, testing, and result interpretation, providing a comprehensive guide to web application security testing using ZAP.
1 out of 22







![[object Object]](/_next/static/media/star-bottom.7253800d.svg)