Comprehensive Cybersecurity Analysis and Solutions for ZP Company
VerifiedAdded on 2024/05/30
|12
|2673
|184
Report
AI Summary
This report identifies and analyzes critical cybersecurity issues affecting ZP Company, including a lack of understanding of asset risks, confusing compliance with security, BYOD policy vulnerabilities, funding and resource constraints, and the absence of a recovery plan. The consequences of these issues include potential cyber threats, data breaches, financial losses, and reputational damage. The proposed solutions involve implementing a comprehensive cybersecurity policy that includes hazard awareness, security controls, policy development, secure network infrastructure, vendor risk management, and intrusion detection. The report advocates for recovery and backup technology as a cost-effective approach for data management and security. Ultimately, the report emphasizes the importance of investing in cybersecurity systems and expertise to protect the company's data and maintain its reputation.

Computer Security - Assignment 2
Student Name
Student Number
Student Name
Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction...........................................................................................................................................2
Cyber security Issue...............................................................................................................................3
Why is cyber security “Top 8” issue in network?...............................................................................3
Consequences....................................................................................................................................5
Proposed solution to address the issue.............................................................................................7
Why selected approach is good than other alternative approaches.................................................8
Cost analysis......................................................................................................................................9
Summary.............................................................................................................................................10
References...........................................................................................................................................11
1
Introduction...........................................................................................................................................2
Cyber security Issue...............................................................................................................................3
Why is cyber security “Top 8” issue in network?...............................................................................3
Consequences....................................................................................................................................5
Proposed solution to address the issue.............................................................................................7
Why selected approach is good than other alternative approaches.................................................8
Cost analysis......................................................................................................................................9
Summary.............................................................................................................................................10
References...........................................................................................................................................11
1

Introduction
The cybersecurity consists of techniques, controls, and processes designed to protect data, systems
and ZP Company networks from cybercrimes and cyber-attacks. The cybercrimes and cyber-attacks
causes damage and disrupt the whole database of ZP Company and harm its reputation. The
reputation of the ZP Company is also on the risk of damage due to such activities.
Efficient cybersecurity:
Decrease the chances of cyber-attacks and cybercrimes to the organization.
Helps in keeping data secure and in-tact
Helps in maintaining secrecy
Reduces chances of leakage of important information
Protects from unauthorized exploitation of systems
Even though all the organizations these days tend to have a cybersecurity system but most of them
face cyber threats on a regular basis. The reasons for the same are that they do not have an efficient
or a well-maintained cybersecurity system. Many small or medium-sized organizations don’t even
realize the risk that they are at and are vulnerable to many mistakes that can lead them to huge
losses (Zhang, 2015).
2
The cybersecurity consists of techniques, controls, and processes designed to protect data, systems
and ZP Company networks from cybercrimes and cyber-attacks. The cybercrimes and cyber-attacks
causes damage and disrupt the whole database of ZP Company and harm its reputation. The
reputation of the ZP Company is also on the risk of damage due to such activities.
Efficient cybersecurity:
Decrease the chances of cyber-attacks and cybercrimes to the organization.
Helps in keeping data secure and in-tact
Helps in maintaining secrecy
Reduces chances of leakage of important information
Protects from unauthorized exploitation of systems
Even though all the organizations these days tend to have a cybersecurity system but most of them
face cyber threats on a regular basis. The reasons for the same are that they do not have an efficient
or a well-maintained cybersecurity system. Many small or medium-sized organizations don’t even
realize the risk that they are at and are vulnerable to many mistakes that can lead them to huge
losses (Zhang, 2015).
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
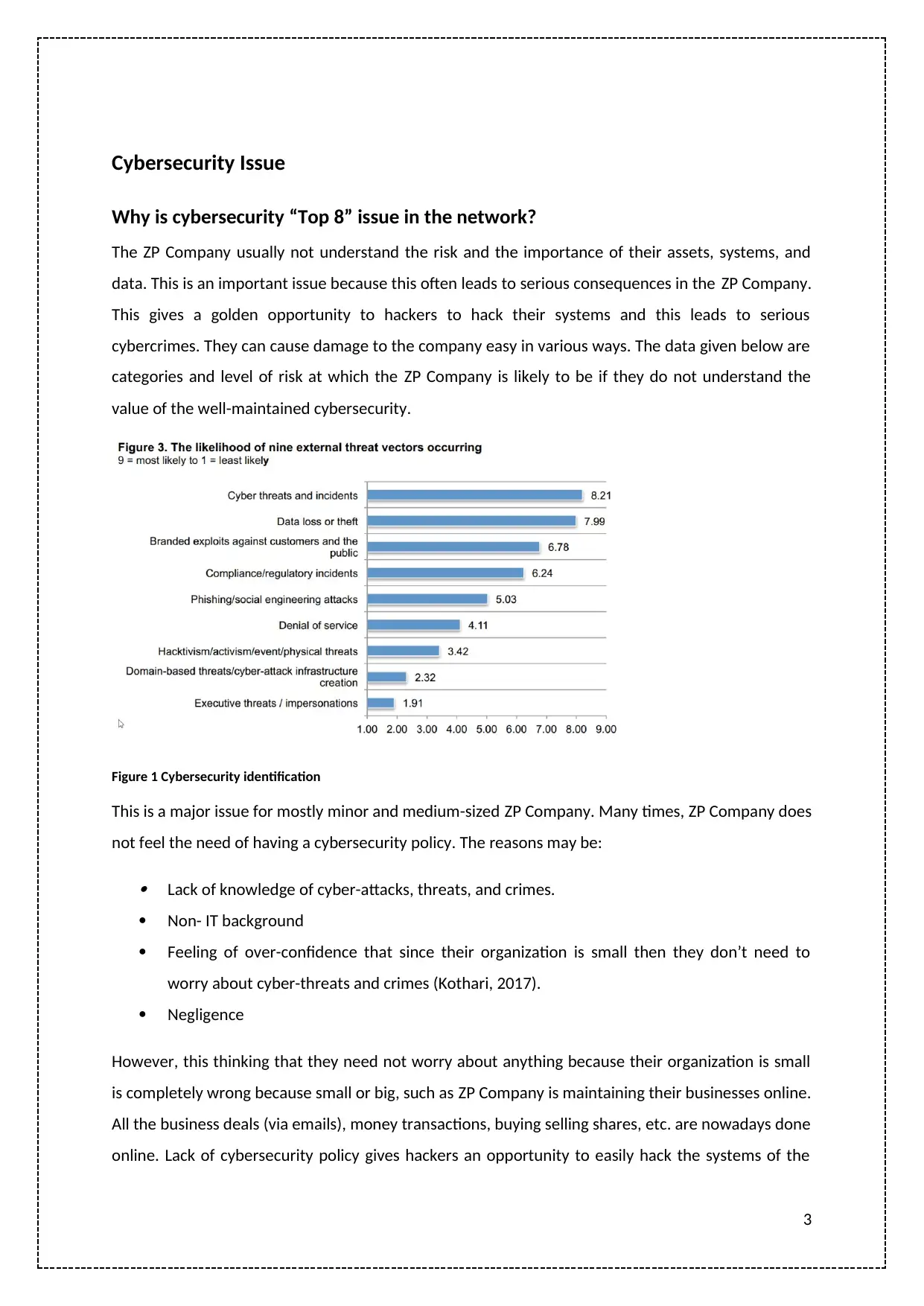
Cybersecurity Issue
Why is cybersecurity “Top 8” issue in the network?
The ZP Company usually not understand the risk and the importance of their assets, systems, and
data. This is an important issue because this often leads to serious consequences in the ZP Company.
This gives a golden opportunity to hackers to hack their systems and this leads to serious
cybercrimes. They can cause damage to the company easy in various ways. The data given below are
categories and level of risk at which the ZP Company is likely to be if they do not understand the
value of the well-maintained cybersecurity.
Figure 1 Cybersecurity identification
This is a major issue for mostly minor and medium-sized ZP Company. Many times, ZP Company does
not feel the need of having a cybersecurity policy. The reasons may be:
Lack of knowledge of cyber-attacks, threats, and crimes.
Non- IT background
Feeling of over-confidence that since their organization is small then they don’t need to
worry about cyber-threats and crimes (Kothari, 2017).
Negligence
However, this thinking that they need not worry about anything because their organization is small
is completely wrong because small or big, such as ZP Company is maintaining their businesses online.
All the business deals (via emails), money transactions, buying selling shares, etc. are nowadays done
online. Lack of cybersecurity policy gives hackers an opportunity to easily hack the systems of the
3
Why is cybersecurity “Top 8” issue in the network?
The ZP Company usually not understand the risk and the importance of their assets, systems, and
data. This is an important issue because this often leads to serious consequences in the ZP Company.
This gives a golden opportunity to hackers to hack their systems and this leads to serious
cybercrimes. They can cause damage to the company easy in various ways. The data given below are
categories and level of risk at which the ZP Company is likely to be if they do not understand the
value of the well-maintained cybersecurity.
Figure 1 Cybersecurity identification
This is a major issue for mostly minor and medium-sized ZP Company. Many times, ZP Company does
not feel the need of having a cybersecurity policy. The reasons may be:
Lack of knowledge of cyber-attacks, threats, and crimes.
Non- IT background
Feeling of over-confidence that since their organization is small then they don’t need to
worry about cyber-threats and crimes (Kothari, 2017).
Negligence
However, this thinking that they need not worry about anything because their organization is small
is completely wrong because small or big, such as ZP Company is maintaining their businesses online.
All the business deals (via emails), money transactions, buying selling shares, etc. are nowadays done
online. Lack of cybersecurity policy gives hackers an opportunity to easily hack the systems of the
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

companies. The external attacks lead to major financial losses and threaten the image of the
company. Confusing compliance with cyber security is a major cyber security issue. This is a major
risk that businesses deal with these days. They often confuse compliance with cyber security. They
think that compliance and cyber security is one and the same thing. However, ensure compliance
with the rules of the company is not equivalent to the protection of the company against cyber-
attacks. This leads to cyber-attacks and threats because the company is not paying attention to their
cyber security at all. The company, in this case, is living in a disbelieve that they have no worry to
deal with cyber security issues because they think compliance and cyber securities are one and the
same thing. The hackers and cyber criminals wait for such kind of opportunities and take advantage
of this situation. This leads to huge financial damage to the company, leakage of valuable
information and also leads to damage to the image of the company in the market (Chindipha, 2015).
Bring your own device policy (BYOD)
Bring your own device policy is a flexibility that if a company gives to its employees that implies that
the employees are free to use their own devices such as laptops, pen-drives, etc. in the office. This
may give them relaxation and better working conditions to work in but this is also a huge threat to
cyber security.
The company that follows such methodology may have to face the following consequences:
Mobile security breach
Heavy burden on IT sources
Increased security budgets
The measures that the company can adopt to avoid such consequences:
Make few necessary changes in the BYOD policy and limiting the number of devices that the
employee can use in the office which are his own.
Proper guidelines and instructions for employees who want to enjoy BYOD.
Better security of data and emphasis on password protection.
The capital investment required in this case is on the buying and installing of better and efficient
information security systems and hiring professionals to conduct this job (Ghosh, 2013).
Funding, talent and resources constraints
Funding, talent, and resources are major issues which result in good or bad cyber security of a
company.
It is quite obvious that if ZP Company is sufficient enough and has adequate funds, it will able to
higher specialists and install the best of information security software in order to maintain cyber
4
company. Confusing compliance with cyber security is a major cyber security issue. This is a major
risk that businesses deal with these days. They often confuse compliance with cyber security. They
think that compliance and cyber security is one and the same thing. However, ensure compliance
with the rules of the company is not equivalent to the protection of the company against cyber-
attacks. This leads to cyber-attacks and threats because the company is not paying attention to their
cyber security at all. The company, in this case, is living in a disbelieve that they have no worry to
deal with cyber security issues because they think compliance and cyber securities are one and the
same thing. The hackers and cyber criminals wait for such kind of opportunities and take advantage
of this situation. This leads to huge financial damage to the company, leakage of valuable
information and also leads to damage to the image of the company in the market (Chindipha, 2015).
Bring your own device policy (BYOD)
Bring your own device policy is a flexibility that if a company gives to its employees that implies that
the employees are free to use their own devices such as laptops, pen-drives, etc. in the office. This
may give them relaxation and better working conditions to work in but this is also a huge threat to
cyber security.
The company that follows such methodology may have to face the following consequences:
Mobile security breach
Heavy burden on IT sources
Increased security budgets
The measures that the company can adopt to avoid such consequences:
Make few necessary changes in the BYOD policy and limiting the number of devices that the
employee can use in the office which are his own.
Proper guidelines and instructions for employees who want to enjoy BYOD.
Better security of data and emphasis on password protection.
The capital investment required in this case is on the buying and installing of better and efficient
information security systems and hiring professionals to conduct this job (Ghosh, 2013).
Funding, talent and resources constraints
Funding, talent, and resources are major issues which result in good or bad cyber security of a
company.
It is quite obvious that if ZP Company is sufficient enough and has adequate funds, it will able to
higher specialists and install the best of information security software in order to maintain cyber
4

security and keep its data safe. However on the other hand if that ZP Company is sufficient enough
then these possibilities are low and this means that their cyber security system would not be as good
and efficient as the others.
The consequences that they may face are:
Cyber threats and attacks
Breaching of important information
The bad image in the market
The measure in this situation that company can take is to set reasonable expectations for this
purpose and allot resources that the company can afford.
This measure is better than any other measure because in this way there would not be any extra
financial burden on the ZP Company and adjustments could I made with the available resources only
(Rao, 2002).
Lack of a recovery plan
Lack of a recovery plan is a major cyber security issue that a company faces if it does not have it. ZP
Company needs to have a well-developed recovery plan to recover essential data that has been lost
due to cyber-attack. A recovery plan includes ways by which ZP Company can prevent itself from the
cyber-attack and minimize the damage.
Lack of recovery plan leads to:
Increased cyber threats and attacks
Loss of data completely
Huge financial losses
Therefore, the ZP Company needs to have a proper recovery plan in order to protect themselves
from any cybercrime or attack. A proper recovery plan means:
Protection of essential data
Backup for uncalled incidents such as accidentally deleting important data or clearance of
data due to some error (Pearson, 2011)
Consequences
The ZP printing organization first need to understand the issue properly and then they
should work in the direction.
5
then these possibilities are low and this means that their cyber security system would not be as good
and efficient as the others.
The consequences that they may face are:
Cyber threats and attacks
Breaching of important information
The bad image in the market
The measure in this situation that company can take is to set reasonable expectations for this
purpose and allot resources that the company can afford.
This measure is better than any other measure because in this way there would not be any extra
financial burden on the ZP Company and adjustments could I made with the available resources only
(Rao, 2002).
Lack of a recovery plan
Lack of a recovery plan is a major cyber security issue that a company faces if it does not have it. ZP
Company needs to have a well-developed recovery plan to recover essential data that has been lost
due to cyber-attack. A recovery plan includes ways by which ZP Company can prevent itself from the
cyber-attack and minimize the damage.
Lack of recovery plan leads to:
Increased cyber threats and attacks
Loss of data completely
Huge financial losses
Therefore, the ZP Company needs to have a proper recovery plan in order to protect themselves
from any cybercrime or attack. A proper recovery plan means:
Protection of essential data
Backup for uncalled incidents such as accidentally deleting important data or clearance of
data due to some error (Pearson, 2011)
Consequences
The ZP printing organization first need to understand the issue properly and then they
should work in the direction.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In order to improve the cyber security of ZP organization they can hire professionals who will
regularly check and maintain their security system and can help the ZP organization out
when it faces any kind of cyber threat or attack
The ZP Company should have strict guidelines that should be followed by each and every
employee.
Each and every employee should be aware of the cybercrimes and threats so that may
conduct their online transactions and work carefully.
The measures that companies can take in order to avoid such situations are:
The ZP Company need to understand the difference between compliance and cyber security
and should not confuse them.
The ZP Company can hire professionals for this job
The ZP Company can form well-defined policies differentiating between cyber security and
compliance. Maintaining a good code of conduct with their employees and appreciating
them for good work.
Installing more efficient cyber security systems in the ZP Company for protecting data.
Limiting the number of people who have important and confidential information about the
ZP Company which includes future plans, strategies, accounts of the company, etc.
Tracking potential threats within the ZP Company and confronting them. The ZP Company
may also take strict action against the employee (if found guilty) in order show an example
to other employees as well (Onken, 2007).
6
regularly check and maintain their security system and can help the ZP organization out
when it faces any kind of cyber threat or attack
The ZP Company should have strict guidelines that should be followed by each and every
employee.
Each and every employee should be aware of the cybercrimes and threats so that may
conduct their online transactions and work carefully.
The measures that companies can take in order to avoid such situations are:
The ZP Company need to understand the difference between compliance and cyber security
and should not confuse them.
The ZP Company can hire professionals for this job
The ZP Company can form well-defined policies differentiating between cyber security and
compliance. Maintaining a good code of conduct with their employees and appreciating
them for good work.
Installing more efficient cyber security systems in the ZP Company for protecting data.
Limiting the number of people who have important and confidential information about the
ZP Company which includes future plans, strategies, accounts of the company, etc.
Tracking potential threats within the ZP Company and confronting them. The ZP Company
may also take strict action against the employee (if found guilty) in order show an example
to other employees as well (Onken, 2007).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The proposed solution to address the issue
The ZP printing organization should do the following things as part proper cyber security policy:
Understand the hazards concerned with cyber security
Set up cyber security control
Develop procedures, policies and oversight processes
Secure information and networks of the company
Describe and hold risks related to the third parties and vendors
It should be able to sense any kind of unauthorized activity.
When it is purchasing any hardware, it should keep in mind whether the hardware is able to
support software updates or not and also how many.
It should regularly check and replace the devices that no longer support new software
updates. Maintaining a good code of conduct with their employees and appreciating them
for good work.
Installing more efficient cyber security systems in the company for protecting data.
Limiting the number of people who have important and confidential information about the
ZP Company which includes future plans, strategies, accounts of the company, etc.
Tracking potential threats within the company and confronting them. The company may also
take strict action against the employee (if found guilty) in order show an example to other
employees as well.
Here, various solutions are provided to manage or face the cyber security issue. With this given
point the ZP organization will be secure form the cyber security issue (Errission, 2010).
7
The ZP printing organization should do the following things as part proper cyber security policy:
Understand the hazards concerned with cyber security
Set up cyber security control
Develop procedures, policies and oversight processes
Secure information and networks of the company
Describe and hold risks related to the third parties and vendors
It should be able to sense any kind of unauthorized activity.
When it is purchasing any hardware, it should keep in mind whether the hardware is able to
support software updates or not and also how many.
It should regularly check and replace the devices that no longer support new software
updates. Maintaining a good code of conduct with their employees and appreciating them
for good work.
Installing more efficient cyber security systems in the company for protecting data.
Limiting the number of people who have important and confidential information about the
ZP Company which includes future plans, strategies, accounts of the company, etc.
Tracking potential threats within the company and confronting them. The company may also
take strict action against the employee (if found guilty) in order show an example to other
employees as well.
Here, various solutions are provided to manage or face the cyber security issue. With this given
point the ZP organization will be secure form the cyber security issue (Errission, 2010).
7

Why selected approach is good than other alternative approaches
In order to avoid risks, the managers of the companies should have access to the cyber security
system so that they can see how the data is flowing through the system and check by themselves
that there is no leakage of confidential data. A company needs to have a well-developed recovery
plan to recover essential data that has been lost due to cyber-attack. A recovery plan includes ways
by which a company can prevent itself from the cyber-attack and minimize the damage. The
company needs to have a proper recovery plan in order to protect themselves from any cybercrime
or attack. A proper recovery plan means:
Protection of essential data
Backup for uncalled incidents such as accidentally deleting important data or clearance of
data due to some error
There are several approaches to resolving the cyber security issue from the ZP printing organization
network. For solve this issue, I have selected Recovery and back up technology that easily manages
the data and secure the confidential information. If user or organization delete the data or because
of the cyber security issue the stored data is getting lost or crashed then this approach recover all
the confidential data. And this technology is not so costly for the small organization such as ZP
printing organization (Ralston, 2007).
8
In order to avoid risks, the managers of the companies should have access to the cyber security
system so that they can see how the data is flowing through the system and check by themselves
that there is no leakage of confidential data. A company needs to have a well-developed recovery
plan to recover essential data that has been lost due to cyber-attack. A recovery plan includes ways
by which a company can prevent itself from the cyber-attack and minimize the damage. The
company needs to have a proper recovery plan in order to protect themselves from any cybercrime
or attack. A proper recovery plan means:
Protection of essential data
Backup for uncalled incidents such as accidentally deleting important data or clearance of
data due to some error
There are several approaches to resolving the cyber security issue from the ZP printing organization
network. For solve this issue, I have selected Recovery and back up technology that easily manages
the data and secure the confidential information. If user or organization delete the data or because
of the cyber security issue the stored data is getting lost or crashed then this approach recover all
the confidential data. And this technology is not so costly for the small organization such as ZP
printing organization (Ralston, 2007).
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cost analysis
The cost related to this security issue is only the cost which will be put in the purchase and
installation of cyber security systems and for hiring cyber security professionals. Since there is a
variety of software available in the market according to the need and requirement of the company
so the price varies according. Also, since there is the number of cyber security professionals is still
very less that’s why their salary will definitely be high. Companies need to choose very carefully
according to their need and requirement. The cost related to this issue would mainly be on hiring
professionals to form a proper cyber security plan and to maintain it. This may mean that the
company will need to give them a considerate amount of money because their demand is high and
their number is less. For this issue, not much of the cost investment is required. The only cost
investment that will be required is in hiring professionals. The cost investment required in this case
is the cost that will be spent on replacing old and non-useful hardware devices and systems
(Stoneburner, 2002).
9
The cost related to this security issue is only the cost which will be put in the purchase and
installation of cyber security systems and for hiring cyber security professionals. Since there is a
variety of software available in the market according to the need and requirement of the company
so the price varies according. Also, since there is the number of cyber security professionals is still
very less that’s why their salary will definitely be high. Companies need to choose very carefully
according to their need and requirement. The cost related to this issue would mainly be on hiring
professionals to form a proper cyber security plan and to maintain it. This may mean that the
company will need to give them a considerate amount of money because their demand is high and
their number is less. For this issue, not much of the cost investment is required. The only cost
investment that will be required is in hiring professionals. The cost investment required in this case
is the cost that will be spent on replacing old and non-useful hardware devices and systems
(Stoneburner, 2002).
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Summary
In this report, we discussed the various cybersecurity issues that the companies and organizations
usually face, their consequences and measures to avoid such issues. We discussed the cost related
to improving such issues.
10
In this report, we discussed the various cybersecurity issues that the companies and organizations
usually face, their consequences and measures to avoid such issues. We discussed the cost related
to improving such issues.
10

References
Chindipha, S. D., & Irwin, B. (2015, November). Cyber Vulnerability Assessment: Case Study
of Malawi and Tanzania. In AFRICAN CYBER CITIZENSHIP CONFERENCE 2015 (ACCC2015) (p.
105).
Ericsson, G. N. (2010). Cyber security and power system communication—essential parts of a
smart grid infrastructure. IEEE Transactions on Power Delivery, 25(3), 1501-1507.
Ghosh, A., Gajar, P. K., & Rai, S. (2013). Bring your own device (BYOD): Security risks and
mitigating strategies. International Journal of Global Research in Computer Science (UGC
Approved Journal), 4(4), 62-70.
Kothari, B. P. V. (2017). Security Issues with Social Networking Sites.
Onken, S. J., Craig, C. M., Ridgway, P., Ralph, R. O., & Cook, J. A. (2007). An analysis of the
definitions and elements of recovery: A review of the literature. Psychiatric rehabilitation
journal, 31(1), 9.
Pearson, D. L., Hamilton, A. L., & Erwin, T. L. (2011). Recovery plan for the endangered
taxonomy profession. BioScience, 61(1), 58-63.
Ralston, P. A., Graham, J. H., & Hieb, J. L. (2007). Cyber security risk assessment for SCADA
and DCS networks. ISA Transactions, 46(4), 583-594.
Rao, H., & Drazin, R. (2002). Overcoming resource constraints on product innovation by
recruiting talent from rivals: A study of the mutual fund industry, 1986–1994. Academy of
Management Journal, 45(3), 491-507.
Stoneburner, G., Goguen, A. Y., & Feringa, A. (2002). Sp 800-30. Risk management guide for
information technology systems.
Zhang, S., Ou, X., & Caragea, D. (2015). Predicting cyber risks through national vulnerability
database. Information Security Journal: A Global Perspective, 24(4-6), 194-206.
11
Chindipha, S. D., & Irwin, B. (2015, November). Cyber Vulnerability Assessment: Case Study
of Malawi and Tanzania. In AFRICAN CYBER CITIZENSHIP CONFERENCE 2015 (ACCC2015) (p.
105).
Ericsson, G. N. (2010). Cyber security and power system communication—essential parts of a
smart grid infrastructure. IEEE Transactions on Power Delivery, 25(3), 1501-1507.
Ghosh, A., Gajar, P. K., & Rai, S. (2013). Bring your own device (BYOD): Security risks and
mitigating strategies. International Journal of Global Research in Computer Science (UGC
Approved Journal), 4(4), 62-70.
Kothari, B. P. V. (2017). Security Issues with Social Networking Sites.
Onken, S. J., Craig, C. M., Ridgway, P., Ralph, R. O., & Cook, J. A. (2007). An analysis of the
definitions and elements of recovery: A review of the literature. Psychiatric rehabilitation
journal, 31(1), 9.
Pearson, D. L., Hamilton, A. L., & Erwin, T. L. (2011). Recovery plan for the endangered
taxonomy profession. BioScience, 61(1), 58-63.
Ralston, P. A., Graham, J. H., & Hieb, J. L. (2007). Cyber security risk assessment for SCADA
and DCS networks. ISA Transactions, 46(4), 583-594.
Rao, H., & Drazin, R. (2002). Overcoming resource constraints on product innovation by
recruiting talent from rivals: A study of the mutual fund industry, 1986–1994. Academy of
Management Journal, 45(3), 491-507.
Stoneburner, G., Goguen, A. Y., & Feringa, A. (2002). Sp 800-30. Risk management guide for
information technology systems.
Zhang, S., Ou, X., & Caragea, D. (2015). Predicting cyber risks through national vulnerability
database. Information Security Journal: A Global Perspective, 24(4-6), 194-206.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





