ENISA's Satisfaction with Current State of IT Security
VerifiedAdded on 2019/11/12
|16
|3893
|157
Report
AI Summary
The European Union Agency for Network and Information Security (ENISA) has identified key points that form the basis of their Big Data security infrastructure. The report highlights the importance of trusted components at every level of the architecture to ensure data privacy. ENISA notes that big data security is a major threat due to the increase in information available from cloud servers, which hackers can exploit. The report also emphasizes the need for data productivity, filtering, and control accessibility to address the challenges of big data security. The study concludes that ENISA has a gap in their sensor data streams and recommends reconstructing security measures to mitigate identity fraud risks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: IT RISK MANAGEMENT
IT Risk Management
Name of the Student
Name of the University
Author Note
IT Risk Management
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
IT RISK MANAGEMENT
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................5
Question 3..................................................................................................................................6
Question 4..................................................................................................................................7
Question 5..................................................................................................................................9
References................................................................................................................................11
IT RISK MANAGEMENT
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................5
Question 3..................................................................................................................................6
Question 4..................................................................................................................................7
Question 5..................................................................................................................................9
References................................................................................................................................11

2
IT RISK MANAGEMENT
Introduction
The case study provides a brief overview of the big data threats that is associated with
the use of big data and its relative technology. The technology will have immense work in the
near future. ENSIA has elaborated on different topics, which are all connected to the use of
big data servers and the technology in modern day world. Hackers and threats are all over the
internet trying to grasp a moment to attack and steal data from the servers. The report
discusses about the different threats and the possible measures to follow to eliminate those
risks.
Question 1
Provide a brief overview of the case study and prepare a diagram for the ENISA Big Data
security infrastructure.
In the case study provided for this report ENISA, shows an elaborate discussion of the
threats that are related to the big data use in ENISA. The topic of discussion has gained
limelight in the recent years, which has forced the use of data storage methods and
information technology to have a serious role in different aspects of the society (Marinos,
2013). The aspect that is to be developed and changes for the developments of the
information technology and the use of Big Data analysis in the health security perspective,
food security and climate and other resources that is efficient in the mode of system
integration. The impact that of the big data analysis and threats has been approved by the
European Commission who have identified the approach to be in a strategic format of the use
of Big Data. This way the data is being stored is conceivable of the economic drive in the
system of the organization that is using the technology (Marinos, 2013). There has been
found to be escalation in the field of research and science that has always been in the top
IT RISK MANAGEMENT
Introduction
The case study provides a brief overview of the big data threats that is associated with
the use of big data and its relative technology. The technology will have immense work in the
near future. ENSIA has elaborated on different topics, which are all connected to the use of
big data servers and the technology in modern day world. Hackers and threats are all over the
internet trying to grasp a moment to attack and steal data from the servers. The report
discusses about the different threats and the possible measures to follow to eliminate those
risks.
Question 1
Provide a brief overview of the case study and prepare a diagram for the ENISA Big Data
security infrastructure.
In the case study provided for this report ENISA, shows an elaborate discussion of the
threats that are related to the big data use in ENISA. The topic of discussion has gained
limelight in the recent years, which has forced the use of data storage methods and
information technology to have a serious role in different aspects of the society (Marinos,
2013). The aspect that is to be developed and changes for the developments of the
information technology and the use of Big Data analysis in the health security perspective,
food security and climate and other resources that is efficient in the mode of system
integration. The impact that of the big data analysis and threats has been approved by the
European Commission who have identified the approach to be in a strategic format of the use
of Big Data. This way the data is being stored is conceivable of the economic drive in the
system of the organization that is using the technology (Marinos, 2013). There has been
found to be escalation in the field of research and science that has always been in the top

3
IT RISK MANAGEMENT
priority. This has forced different organizations around the world to launch different research
proposals for the better exploration of the prospect of use of Big Data in the field of cloud
computing and data analysis. There has been recent implementation of Big Data in the
department of military organizations. They have used the technology to help the soldiers to
assists them in fighting virtual and real terrorism. They collect information and data from
different sources in the internet, which has been marked as real field or as open source
programs (Marinos, Belmonte &Rekleitis, 2014). There is a use of highly novel and different
high technology modules for the implementation of Big Data with the help of different
Information and Communications Technology (ICT) systems. However, the increased use of
this technology of Big Data has prompted the hackers to launch different cyber-attacks and
data breach on the cloud servers. The increase of such attacks have increased the trend of
impactful and sophisticated. Due to the increase for usage of Big Data in business
organizations, the hackers get a positive edge in the process of developing a specialized
formative attack on the Big Data analysis. This form of technology also has capability to be
used in the form of a tool, which can be used to stop cyber-attacks by providing security and
privacy professionals who have the better insight of the incident and to be managed carefully.
ENISA provides the delivery of this area in the form of Threats Landscapes in the field of
Big Data analysis (Marinos, Belmonte &Rekleitis, 2014). The case study of the discussion
discuses about the form of architecture that is followed by ENISA in the domain of Big Data
analysis and threat taxonomy. The method, which is also, followed by ENISA and aslo the
gaps and the recommendation has been discussed.
The use of cloud computing has been depicted as a form of infrastructure layer which
has an implementation of Big Data system in ENISA. The infrastructure used by ENISA has
met all the requirements like cost effectiveness, elasticity and ability of the infrastructure to
IT RISK MANAGEMENT
priority. This has forced different organizations around the world to launch different research
proposals for the better exploration of the prospect of use of Big Data in the field of cloud
computing and data analysis. There has been recent implementation of Big Data in the
department of military organizations. They have used the technology to help the soldiers to
assists them in fighting virtual and real terrorism. They collect information and data from
different sources in the internet, which has been marked as real field or as open source
programs (Marinos, Belmonte &Rekleitis, 2014). There is a use of highly novel and different
high technology modules for the implementation of Big Data with the help of different
Information and Communications Technology (ICT) systems. However, the increased use of
this technology of Big Data has prompted the hackers to launch different cyber-attacks and
data breach on the cloud servers. The increase of such attacks have increased the trend of
impactful and sophisticated. Due to the increase for usage of Big Data in business
organizations, the hackers get a positive edge in the process of developing a specialized
formative attack on the Big Data analysis. This form of technology also has capability to be
used in the form of a tool, which can be used to stop cyber-attacks by providing security and
privacy professionals who have the better insight of the incident and to be managed carefully.
ENISA provides the delivery of this area in the form of Threats Landscapes in the field of
Big Data analysis (Marinos, Belmonte &Rekleitis, 2014). The case study of the discussion
discuses about the form of architecture that is followed by ENISA in the domain of Big Data
analysis and threat taxonomy. The method, which is also, followed by ENISA and aslo the
gaps and the recommendation has been discussed.
The use of cloud computing has been depicted as a form of infrastructure layer which
has an implementation of Big Data system in ENISA. The infrastructure used by ENISA has
met all the requirements like cost effectiveness, elasticity and ability of the infrastructure to
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
IT RISK MANAGEMENT
scale up and down from the original position (Marinos, Belmonte &Rekleitis, 2014). The
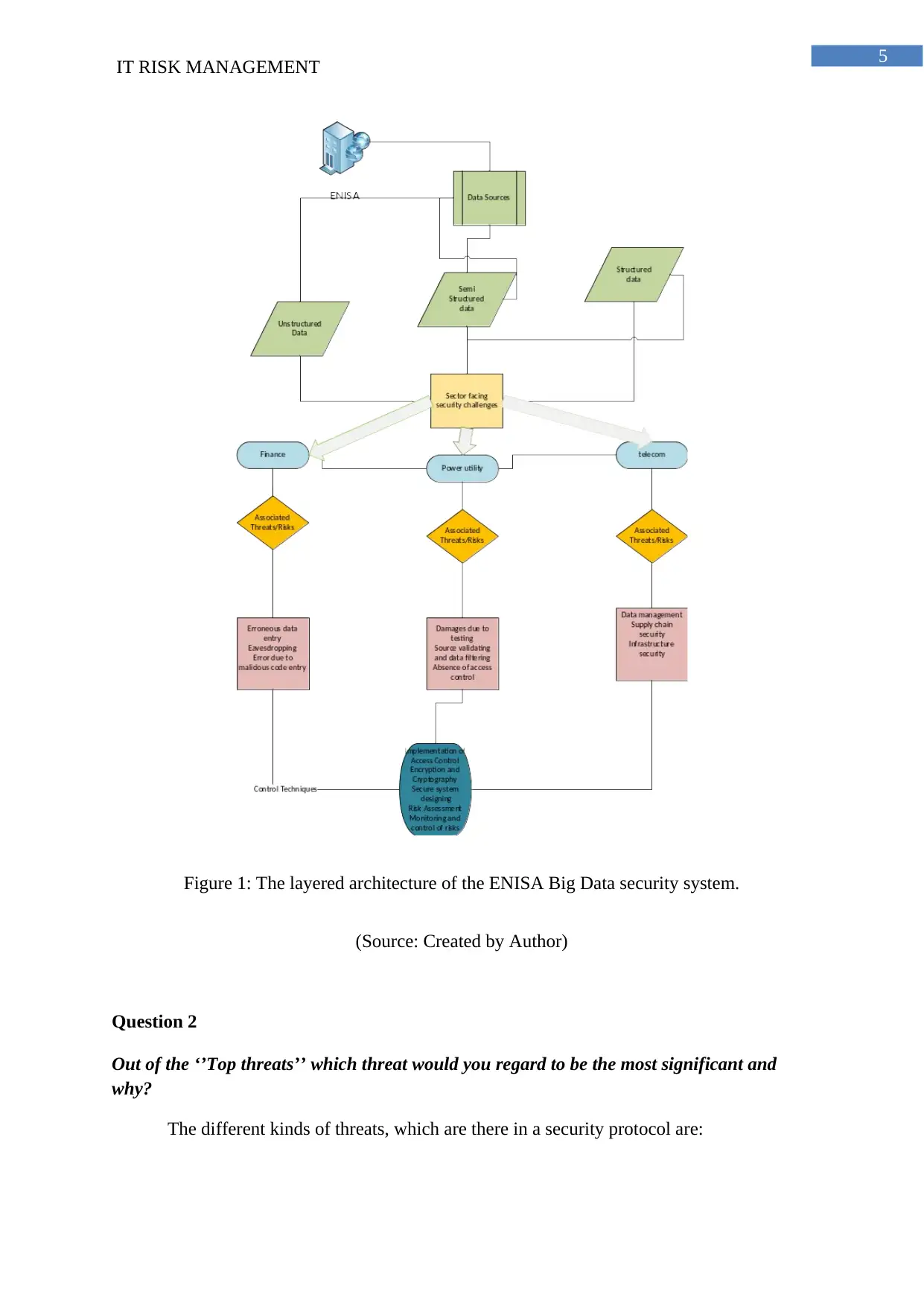
security infrastructure followed by ENISA is as follows:
Data source layer: The layer has a consistency of the data streaming property from the
sensors and distribute the data into different data sources to be organized into relational
database with semi structure and unstructured format of data (Barnard-Wills, 2014).
Process integration layer: The layer has the property of concerning with only the
important data, which is provided with preprocessing property to acquire data and then
get integrated into different datasets to form a structured format (Barnard-Wills, 2014).
Information storage layer: The data layer consists of a large variety of information. These
consists of RDF stores, NewSQL database, NoSQL and distributed file system, which has
the ability to control large data sets.
Computing and analytics model layer: The layer has the property of encapsulating
multiple data processing tools as MapReduce that uses the resources stored in the data
servers to produce data management analysis (Barnard-Wills, 2014).
Presentation layer: The layer helps in the visualization of the information with the help of
desktop visuals, web browsers and web services.
IT RISK MANAGEMENT
scale up and down from the original position (Marinos, Belmonte &Rekleitis, 2014). The
security infrastructure followed by ENISA is as follows:
Data source layer: The layer has a consistency of the data streaming property from the
sensors and distribute the data into different data sources to be organized into relational
database with semi structure and unstructured format of data (Barnard-Wills, 2014).
Process integration layer: The layer has the property of concerning with only the
important data, which is provided with preprocessing property to acquire data and then
get integrated into different datasets to form a structured format (Barnard-Wills, 2014).
Information storage layer: The data layer consists of a large variety of information. These
consists of RDF stores, NewSQL database, NoSQL and distributed file system, which has
the ability to control large data sets.
Computing and analytics model layer: The layer has the property of encapsulating
multiple data processing tools as MapReduce that uses the resources stored in the data
servers to produce data management analysis (Barnard-Wills, 2014).
Presentation layer: The layer helps in the visualization of the information with the help of
desktop visuals, web browsers and web services.
5
IT RISK MANAGEMENT
Figure 1: The layered architecture of the ENISA Big Data security system.
(Source: Created by Author)
Question 2
Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The different kinds of threats, which are there in a security protocol are:
IT RISK MANAGEMENT
Figure 1: The layered architecture of the ENISA Big Data security system.
(Source: Created by Author)
Question 2
Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The different kinds of threats, which are there in a security protocol are:

6
IT RISK MANAGEMENT
Threat Group: Eavesdropping, Hijacking and Interception
o Leaking of information due to error caused by human interaction.
o Web applications leaking information from history or cookies (Lévy-Bencheton et
al., 2015).
o Drawbacks in the implementation of the designing of the architecture of the data
servers
o Eavesdropping on the information exchange lines (Lévy-Bencheton et al., 2015).
Threat Group: Nefarious Abuse
o Distributed Denial of service (DDoS) attack
o Injection of malicious codes in to the network stream
o Use of systems and networks without proper authentication (Lévy-Bencheton et
al., 2015).
Threat Group: Legal
o Data breach which leads to the breaking of judicial laws
o Shortage of skills in the workforce leading to the breaking of laws (Cho et al.,
2016).
After studying the three threat groups, the most significant of the threats was found to
be the Nefarious Abuse. Since most of the work of the organization has to be done on the
internet or use the internet to complete the work. This means that the internet has to be the
topmost priority of the organization (Cho et al., 2016). However if the system and the
network is compromised by the hackers then the whole working of the organization will
break down. The attack in the form of DDoS attack will cause the network of the system to
get jammed with unrequired requests from garbage websites. The acknowledgements will
IT RISK MANAGEMENT
Threat Group: Eavesdropping, Hijacking and Interception
o Leaking of information due to error caused by human interaction.
o Web applications leaking information from history or cookies (Lévy-Bencheton et
al., 2015).
o Drawbacks in the implementation of the designing of the architecture of the data
servers
o Eavesdropping on the information exchange lines (Lévy-Bencheton et al., 2015).
Threat Group: Nefarious Abuse
o Distributed Denial of service (DDoS) attack
o Injection of malicious codes in to the network stream
o Use of systems and networks without proper authentication (Lévy-Bencheton et
al., 2015).
Threat Group: Legal
o Data breach which leads to the breaking of judicial laws
o Shortage of skills in the workforce leading to the breaking of laws (Cho et al.,
2016).
After studying the three threat groups, the most significant of the threats was found to
be the Nefarious Abuse. Since most of the work of the organization has to be done on the
internet or use the internet to complete the work. This means that the internet has to be the
topmost priority of the organization (Cho et al., 2016). However if the system and the
network is compromised by the hackers then the whole working of the organization will
break down. The attack in the form of DDoS attack will cause the network of the system to
get jammed with unrequired requests from garbage websites. The acknowledgements will
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT RISK MANAGEMENT
congestion of the whole network resulting in the breakdown of the network (Scott et al.,
2016).
Question 3
Identify and discuss the key Threat Agents. What could be done to minimize their impact
on the system? Based on the data provided, discuss the trends in threat probability.
From the case study of ENISA threat Landscape, a threat agent has been described as
“someone or something with decent capabilities, a clear intention to manifest a threat and a
record of past activities in this regard” (Barnard-Wills, Marinos & Portesi, 2014). Any
organization using the Big Data application should also know the threats that are new and
emerging in the current scenario. They should also have a clear idea of the group from which
the treat belongs. There are certain categories into which the threat agents have been divided.
There are mainly seven different threat agent’s category:
1. National states: This category of agents have the capability of having offensive cyber
security measures and use the system as an enterprise system (Scott et al., 2016).
2. Employees: many a times it has been seen that the employees wanting to leak the
company’s resources from inside the organization. The agents in this group includes the
operational staffs, employees and the contractors (Marinos, Belmonte &Rekleitis, 2014).
A prominent amount of knowledge is necessary for the agent to access the internal
information of the organization and leak them into the market.
3. Hacktivist: This is a group of hackers, who work with the sole mentality of proofing that
the organization is doing wrong in the world. They have the working criteria of going into
the network of the organization and stealing sensitive files to cause damage to the
organization. They target mainly high profile organizations where they use intelligent
agencies and military institutional information (Scott et al., 2016).
IT RISK MANAGEMENT
congestion of the whole network resulting in the breakdown of the network (Scott et al.,
2016).
Question 3
Identify and discuss the key Threat Agents. What could be done to minimize their impact
on the system? Based on the data provided, discuss the trends in threat probability.
From the case study of ENISA threat Landscape, a threat agent has been described as
“someone or something with decent capabilities, a clear intention to manifest a threat and a
record of past activities in this regard” (Barnard-Wills, Marinos & Portesi, 2014). Any
organization using the Big Data application should also know the threats that are new and
emerging in the current scenario. They should also have a clear idea of the group from which
the treat belongs. There are certain categories into which the threat agents have been divided.
There are mainly seven different threat agent’s category:
1. National states: This category of agents have the capability of having offensive cyber
security measures and use the system as an enterprise system (Scott et al., 2016).
2. Employees: many a times it has been seen that the employees wanting to leak the
company’s resources from inside the organization. The agents in this group includes the
operational staffs, employees and the contractors (Marinos, Belmonte &Rekleitis, 2014).
A prominent amount of knowledge is necessary for the agent to access the internal
information of the organization and leak them into the market.
3. Hacktivist: This is a group of hackers, who work with the sole mentality of proofing that
the organization is doing wrong in the world. They have the working criteria of going into
the network of the organization and stealing sensitive files to cause damage to the
organization. They target mainly high profile organizations where they use intelligent
agencies and military institutional information (Scott et al., 2016).

8
IT RISK MANAGEMENT
4. Script players: this group of agents use scripting language to inject malicious content into
the data stream of the organization to disable the network for a small amount of time
(Marinos, Belmonte &Rekleitis, 2014). They are mainly group of unskilled hackers trying
to gain a name in the dark web.
5. Cyber terrorists: this group of agents are mainly proceed with the mentality of either
political or religious. They mainly prefer to target energy production organizations, health
care facilities and telecommunication agencies. These type of complex organizations are
chosen because if they were rendered inactive then there would be rise in chaos in the
political environment of the country (Wang, Anokhin&Anderl, 2017).
6. Cyber criminals: this group of threat agent is generally hostile in nature. They have high
skill and mainly have the motto of financial gain. They work in groups in different levels:
local, national and international (Marinos, Belmonte &Rekleitis, 2014).
7. Corporations: this is the largest category in terms of percentage in the group of threat
agents. They engage in tactics and unethical values to gain the upper hand against the
organization. They gain advantage over their competitors in the market. They sort out the
main target threats that may ruin their work condition and thus goes forward with the use
of different tools to gain information of the target organization(Barnard-Wills,
Marinos&Portesi, 2014) . They have high engineering knowledge based expertise in the
field of hacking into the target organizations network.
Question 4
How could the ETL process be improved? Discuss.
The taxonomy of threat, which has been developed by the ENISA Threat Landscape
(ETL) Group. The group includes threats that are applicable to be used for the assets of
safeguarding the Big Data server. These can be improved in the following ways:
IT RISK MANAGEMENT
4. Script players: this group of agents use scripting language to inject malicious content into
the data stream of the organization to disable the network for a small amount of time
(Marinos, Belmonte &Rekleitis, 2014). They are mainly group of unskilled hackers trying
to gain a name in the dark web.
5. Cyber terrorists: this group of agents are mainly proceed with the mentality of either
political or religious. They mainly prefer to target energy production organizations, health
care facilities and telecommunication agencies. These type of complex organizations are
chosen because if they were rendered inactive then there would be rise in chaos in the
political environment of the country (Wang, Anokhin&Anderl, 2017).
6. Cyber criminals: this group of threat agent is generally hostile in nature. They have high
skill and mainly have the motto of financial gain. They work in groups in different levels:
local, national and international (Marinos, Belmonte &Rekleitis, 2014).
7. Corporations: this is the largest category in terms of percentage in the group of threat
agents. They engage in tactics and unethical values to gain the upper hand against the
organization. They gain advantage over their competitors in the market. They sort out the
main target threats that may ruin their work condition and thus goes forward with the use
of different tools to gain information of the target organization(Barnard-Wills,
Marinos&Portesi, 2014) . They have high engineering knowledge based expertise in the
field of hacking into the target organizations network.
Question 4
How could the ETL process be improved? Discuss.
The taxonomy of threat, which has been developed by the ENISA Threat Landscape
(ETL) Group. The group includes threats that are applicable to be used for the assets of
safeguarding the Big Data server. These can be improved in the following ways:

9
IT RISK MANAGEMENT
Tackling bottleneck: it is important for the organization to log all types of information
like time used, records accessed and the hardware used for the purpose. Checking of the
data at the end of the day will help in determination which process has been accessed by
whom. It is recommended that wherever the bottleneck may be it would be the best option
to dive into the code and find out the reason behind the unauthorized access(Brender&
Markov, 2013) .
Load Data Incrementally: the changes, which are loaded into the system between the
changing of the old and the new version should be compared up on full loading. Loading
the data incrementally will help in improving the ETL performance though the time taken
is more (Le Bray, Mayer &Aubert, 2016).
Partition large tables: to improve the data processing speed large relational databases can
be used for faster processing. This means that the large data sets are to be cut down into
smaller table so that the data analysis can be done easily. Each of the new partition has
separate indices table and an indices tree (Olesen, 2016). The use of indices table also
helps for switching of information between different tables easy and can be completed
using the meta data operation of the table.
Cut out extraneous data: it is always helpful to collect as much of data it is available.
Though, all kinds of data is not always necessary for operation performing during the
analysis of the dat. Much of the collected data is redundant and later discarded. If an
organization wants to have the best usage of the ETL service it is recommended to define
exactly the kinds of information that needs to be collected (Bugeja,
Jacobsson&Davidsson, 2017). It is always advisable to start collecting small and then
gradually increase the data set to form a monster set.
Cache the data: caching of the data that has been collected speeds up the working
procedure of the system as memory access can cause a huge delay in the working of the
IT RISK MANAGEMENT
Tackling bottleneck: it is important for the organization to log all types of information
like time used, records accessed and the hardware used for the purpose. Checking of the
data at the end of the day will help in determination which process has been accessed by
whom. It is recommended that wherever the bottleneck may be it would be the best option
to dive into the code and find out the reason behind the unauthorized access(Brender&
Markov, 2013) .
Load Data Incrementally: the changes, which are loaded into the system between the
changing of the old and the new version should be compared up on full loading. Loading
the data incrementally will help in improving the ETL performance though the time taken
is more (Le Bray, Mayer &Aubert, 2016).
Partition large tables: to improve the data processing speed large relational databases can
be used for faster processing. This means that the large data sets are to be cut down into
smaller table so that the data analysis can be done easily. Each of the new partition has
separate indices table and an indices tree (Olesen, 2016). The use of indices table also
helps for switching of information between different tables easy and can be completed
using the meta data operation of the table.
Cut out extraneous data: it is always helpful to collect as much of data it is available.
Though, all kinds of data is not always necessary for operation performing during the
analysis of the dat. Much of the collected data is redundant and later discarded. If an
organization wants to have the best usage of the ETL service it is recommended to define
exactly the kinds of information that needs to be collected (Bugeja,
Jacobsson&Davidsson, 2017). It is always advisable to start collecting small and then
gradually increase the data set to form a monster set.
Cache the data: caching of the data that has been collected speeds up the working
procedure of the system as memory access can cause a huge delay in the working of the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
IT RISK MANAGEMENT
process. It should also be kept in mind that there is a limited amount of memory available
for the caching of the information (Belmonte Martin et al., 2015).
Process in parallel: instead of processing the resources serially, the resources are
connected in parallel form so that the CPU is able to scale the process up. This is the best
solution available (Gorton, 2015).
Use Hadoop: an open source software by the name of Apache Hadoop includes the ability
of data distribution from large sets of data from different cluster of systems connected to
a common network. This is done by following simple programming models. The software
has the capability to scale from a single system to multiple systems, which may or may
not be connected to a single networking server (Rhee et al., 2013).
Question 5
To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or Why
not?
Form the case study of the report the following are the key points that is followed by
the ENISA Big Data security infrastructure:
From the application level to the network payer of the system there will always be an
inclusion of trusted components in the architecture.
It is important of an organization as big as ENISA to own their private infrastructure so
that they are able to implement the trusted structure on every level of the architecture.
The ENISA has explained that there would be an increase of information for the hacker to
access from the cloud servers. They will always have a chance of extracting and
exploiting private and confidential information (Lehto, 2015).
Due to the positioning of the big data security on the top of the list in terms of emerging
security measures it is spreading wildly among social technologies and other internet
subscriptions.
IT RISK MANAGEMENT
process. It should also be kept in mind that there is a limited amount of memory available
for the caching of the information (Belmonte Martin et al., 2015).
Process in parallel: instead of processing the resources serially, the resources are
connected in parallel form so that the CPU is able to scale the process up. This is the best
solution available (Gorton, 2015).
Use Hadoop: an open source software by the name of Apache Hadoop includes the ability
of data distribution from large sets of data from different cluster of systems connected to
a common network. This is done by following simple programming models. The software
has the capability to scale from a single system to multiple systems, which may or may
not be connected to a single networking server (Rhee et al., 2013).
Question 5
To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or Why
not?
Form the case study of the report the following are the key points that is followed by
the ENISA Big Data security infrastructure:
From the application level to the network payer of the system there will always be an
inclusion of trusted components in the architecture.
It is important of an organization as big as ENISA to own their private infrastructure so
that they are able to implement the trusted structure on every level of the architecture.
The ENISA has explained that there would be an increase of information for the hacker to
access from the cloud servers. They will always have a chance of extracting and
exploiting private and confidential information (Lehto, 2015).
Due to the positioning of the big data security on the top of the list in terms of emerging
security measures it is spreading wildly among social technologies and other internet
subscriptions.

11
IT RISK MANAGEMENT
The privacy of the big data is greatly compromised due to the exploitation of such huge
amount of data by using unauthorized access. However, in the case of advertisements the
threat level of big data security gets the addition of new vectors (Lehto, 2015).
There are several other kinds of challenging situations, which defines the identity of
the security system of the Big Data. These challenges should be provided with data
productivity, data filtering and control accessibility (Karchefsky& Rao, 2017). As discussed
by the ENISA there are many issues, which pertain to the domain of data controlling. This
procedure is beyond the power of the products in security information and in the form of
event management.
Form the case study and the research conducted in this report it can be said that
ENISA will be satisfied with the current scenario in their IT security. There is a gap in the
security measure of the sensor data streams (Lykou, 2016). During the process of identity
fraud, the collected information on the traffic would help in the process of facilitating the
process of intrusion of privacy by providing a strong root for the common techniques. In the
year 2009 ENISA had assessed their current risk and security protocol to gain the idea of the
safety protocol of their organization (Lévy-Bencheton et al., 2015). It has been found that the
primary risk form cloud computing has still not changed but a decision of reconstructing the
security measures has been put forward. Since then there has been inclusion of legal aspect of
data security of the cloud servers. There is a system which continuously monitors the system
for any breach in the data.
Conclusion
It can be concluded from the report that the threat based on the concept of bug data
has been in the system of network from a long time. However due to the recent up rise in the
use of the big data servers and similar technology the threat related to data security has
IT RISK MANAGEMENT
The privacy of the big data is greatly compromised due to the exploitation of such huge
amount of data by using unauthorized access. However, in the case of advertisements the
threat level of big data security gets the addition of new vectors (Lehto, 2015).
There are several other kinds of challenging situations, which defines the identity of
the security system of the Big Data. These challenges should be provided with data
productivity, data filtering and control accessibility (Karchefsky& Rao, 2017). As discussed
by the ENISA there are many issues, which pertain to the domain of data controlling. This
procedure is beyond the power of the products in security information and in the form of
event management.
Form the case study and the research conducted in this report it can be said that
ENISA will be satisfied with the current scenario in their IT security. There is a gap in the
security measure of the sensor data streams (Lykou, 2016). During the process of identity
fraud, the collected information on the traffic would help in the process of facilitating the
process of intrusion of privacy by providing a strong root for the common techniques. In the
year 2009 ENISA had assessed their current risk and security protocol to gain the idea of the
safety protocol of their organization (Lévy-Bencheton et al., 2015). It has been found that the
primary risk form cloud computing has still not changed but a decision of reconstructing the
security measures has been put forward. Since then there has been inclusion of legal aspect of
data security of the cloud servers. There is a system which continuously monitors the system
for any breach in the data.
Conclusion
It can be concluded from the report that the threat based on the concept of bug data
has been in the system of network from a long time. However due to the recent up rise in the
use of the big data servers and similar technology the threat related to data security has
12
IT RISK MANAGEMENT
increased. The main idea based upon which big data was created was to provide a storage
area for the huge amount of data being generated daily. The report has put forward the
detailed study of the ENISA case study to find the possible treats in the organization.
IT RISK MANAGEMENT
increased. The main idea based upon which big data was created was to provide a storage
area for the huge amount of data being generated daily. The report has put forward the
detailed study of the ENISA case study to find the possible treats in the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
IT RISK MANAGEMENT
References
Barnard-Wills, D. (2014). ENISA Threat Landscape and Good Practice Guide for Smart
Home and Converged Media. ENISA (The European Network and Information
Security Agency).
Barnard-Wills, D., Marinos, L., &Portesi, S. (2014). Threat landscape and good practice
guide for smart home and converged media. European Union Agency for Network
and Information Security, ENISA.
Belmonte Martin, A., Marinos, L., Rekleitis, E., Spanoudakis, G., &Petroulakis, N. E. (2015).
Threat Landscape and Good Practice Guide for Software Defined Networks/5G.
Brender, N., & Markov, I. (2013). Risk perception and risk management in cloud computing:
Results from a case study of Swiss companies. International journal of information
management, 33(5), 726-733.
Bugeja, J., Jacobsson, A., &Davidsson, P. (2017, March). An analysis of malicious threat
agents for the smart connected home. In Pervasive Computing and Communications
Workshops (PerCom Workshops), 2017 IEEE International Conference on (pp. 557-
562). IEEE.
Cho, H., Yoon, K., Choi, S., & Kim, Y. M. (2016). Automatic Binary Execution
Environment based on Real-machines for Intelligent Malware Analysis. KIISE
Transactions on Computing Practices, 22(3), 139-144.
Gorton, D. (2015). IncidentResponseSim: An agent-based simulation tool for risk
management of online Fraud. In Secure IT Systems (pp. 172-187). Springer, Cham.
IT RISK MANAGEMENT
References
Barnard-Wills, D. (2014). ENISA Threat Landscape and Good Practice Guide for Smart
Home and Converged Media. ENISA (The European Network and Information
Security Agency).
Barnard-Wills, D., Marinos, L., &Portesi, S. (2014). Threat landscape and good practice
guide for smart home and converged media. European Union Agency for Network
and Information Security, ENISA.
Belmonte Martin, A., Marinos, L., Rekleitis, E., Spanoudakis, G., &Petroulakis, N. E. (2015).
Threat Landscape and Good Practice Guide for Software Defined Networks/5G.
Brender, N., & Markov, I. (2013). Risk perception and risk management in cloud computing:
Results from a case study of Swiss companies. International journal of information
management, 33(5), 726-733.
Bugeja, J., Jacobsson, A., &Davidsson, P. (2017, March). An analysis of malicious threat
agents for the smart connected home. In Pervasive Computing and Communications
Workshops (PerCom Workshops), 2017 IEEE International Conference on (pp. 557-
562). IEEE.
Cho, H., Yoon, K., Choi, S., & Kim, Y. M. (2016). Automatic Binary Execution
Environment based on Real-machines for Intelligent Malware Analysis. KIISE
Transactions on Computing Practices, 22(3), 139-144.
Gorton, D. (2015). IncidentResponseSim: An agent-based simulation tool for risk
management of online Fraud. In Secure IT Systems (pp. 172-187). Springer, Cham.

14
IT RISK MANAGEMENT
Karchefsky, S., & Rao, H. R. (2017). Toward a Safer Tomorrow: Cybersecurity and Critical
Infrastructure. In The Palgrave Handbook of Managing Continuous Business
Transformation (pp. 335-352). Palgrave Macmillan UK.
Le Bray, Y., Mayer, N., &Aubert, J. (2016, April). Defining measurements for analyzing
information security risk reports in the telecommunications sector. In Proceedings of
the 31st Annual ACM Symposium on Applied Computing(pp. 2189-2194). ACM.
Lehto, M. (2015). Phenomena in the Cyber World. In Cyber Security: Analytics, Technology
and Automation (pp. 3-29). Springer International Publishing.
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., &Stumpf, J. (2015).
Threat landscape and good practice guide for internet infrastructure. Report, European
Union Agency for Network and Information Security (ENISA).
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., &Stumpf, J. (2015).
Threat landscape and good practice guide for internet infrastructure. Report, European
Union Agency for Network and Information Security (ENISA).
Lykou, G. (2016). Critical Infrastructure Protection: Protecting Public Welfare.
Marinos, L. (2013). ENISA Threat Landscape 2013: Overview of current and emerging
cyber-threats. Heraklion: European Union Agency for Network and Information
Security Publishing. doi, 10, 14231.
Marinos, L., Belmonte, A., &Rekleitis, E. (2014). ENISA Threat Landscape Report
2013. European Union Agency for Network and Information Security.
Marinos, L., Belmonte, A., &Rekleitis, E. (2014). ENISA Threat Landscape 2015. Heraklion,
Greece: ENISA. doi, 10, 061861.
IT RISK MANAGEMENT
Karchefsky, S., & Rao, H. R. (2017). Toward a Safer Tomorrow: Cybersecurity and Critical
Infrastructure. In The Palgrave Handbook of Managing Continuous Business
Transformation (pp. 335-352). Palgrave Macmillan UK.
Le Bray, Y., Mayer, N., &Aubert, J. (2016, April). Defining measurements for analyzing
information security risk reports in the telecommunications sector. In Proceedings of
the 31st Annual ACM Symposium on Applied Computing(pp. 2189-2194). ACM.
Lehto, M. (2015). Phenomena in the Cyber World. In Cyber Security: Analytics, Technology
and Automation (pp. 3-29). Springer International Publishing.
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., &Stumpf, J. (2015).
Threat landscape and good practice guide for internet infrastructure. Report, European
Union Agency for Network and Information Security (ENISA).
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., &Stumpf, J. (2015).
Threat landscape and good practice guide for internet infrastructure. Report, European
Union Agency for Network and Information Security (ENISA).
Lykou, G. (2016). Critical Infrastructure Protection: Protecting Public Welfare.
Marinos, L. (2013). ENISA Threat Landscape 2013: Overview of current and emerging
cyber-threats. Heraklion: European Union Agency for Network and Information
Security Publishing. doi, 10, 14231.
Marinos, L., Belmonte, A., &Rekleitis, E. (2014). ENISA Threat Landscape Report
2013. European Union Agency for Network and Information Security.
Marinos, L., Belmonte, A., &Rekleitis, E. (2014). ENISA Threat Landscape 2015. Heraklion,
Greece: ENISA. doi, 10, 061861.

15
IT RISK MANAGEMENT
Olesen, N. (2016). European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting
Cybercrime and Cyberterrorism (pp. 259-278). Springer International Publishing.
Rhee, K., Won, D., Jang, S. W., Chae, S., & Park, S. (2013). Threat modeling of a mobile
device management system for secure smart work. Electronic Commerce
Research, 13(3), 243-256.
Scott, K. (2016, November). Phobic Cartography: a Human-Centred, Communicative
Analysis of the Cyber Threat Landscape.
Wang, Y., Anokhin, O., &Anderl, R. (2017). Concept and use Case Driven Approach for
Mapping IT Security Requirements on System Assets and Processes in Industrie
4.0. Procedia CIRP, 63, 207-212.
IT RISK MANAGEMENT
Olesen, N. (2016). European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting
Cybercrime and Cyberterrorism (pp. 259-278). Springer International Publishing.
Rhee, K., Won, D., Jang, S. W., Chae, S., & Park, S. (2013). Threat modeling of a mobile
device management system for secure smart work. Electronic Commerce
Research, 13(3), 243-256.
Scott, K. (2016, November). Phobic Cartography: a Human-Centred, Communicative
Analysis of the Cyber Threat Landscape.
Wang, Y., Anokhin, O., &Anderl, R. (2017). Concept and use Case Driven Approach for
Mapping IT Security Requirements on System Assets and Processes in Industrie
4.0. Procedia CIRP, 63, 207-212.
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





