5G Networks | Wireless Networks and Security
Added on 2022-09-15
11 Pages2788 Words27 Views
NETWORKING 0
Wireless networks and security
Wireless networks and security

NETWORKING 1
Table of Contents
Introduction......................................................................................................................... 2
Comparison of cellular networks......................................................................................... 2
Architecture of 5G............................................................................................................... 4
Identification and Analysis of 5G Attacks............................................................................5
DDOS attack..................................................................................................................... 6
MITM attack...................................................................................................................... 6
Phishing attack................................................................................................................. 6
SQLI attack....................................................................................................................... 6
Countermeasures for addressing attacks............................................................................6
Identification and Analysis of 5G limitation in-network coverage........................................7
Conclusion........................................................................................................................... 7
References.......................................................................................................................... 8
Table of Contents
Introduction......................................................................................................................... 2
Comparison of cellular networks......................................................................................... 2
Architecture of 5G............................................................................................................... 4
Identification and Analysis of 5G Attacks............................................................................5
DDOS attack..................................................................................................................... 6
MITM attack...................................................................................................................... 6
Phishing attack................................................................................................................. 6
SQLI attack....................................................................................................................... 6
Countermeasures for addressing attacks............................................................................6
Identification and Analysis of 5G limitation in-network coverage........................................7
Conclusion........................................................................................................................... 7
References.......................................................................................................................... 8

NETWORKING 2
Introduction
The use of communication technologies are growing rapidly and 5G is the latest
networking technology that provides large data rate and better services to the
consumers. 5G communication technology has the capability to provide higher system
capacity that can help users for performing data transmission in an effective manner. It is
an advanced version of 4G technology that can be used in the companies to enhance the
performance of communication networks and exchange data in less time [1]. This
investigation mainly focuses on the 5G networking technology and provides technical
aspects of 5G networks along with the security issues. It is observed that communication
networks require proper connections with the computing devices and the presence of
conflicts in the system may lead to data breach-related problems. It is suggested that this
research will provide in-depth analysis related to the 5G networks which can help the
readers and students for understanding technical aspects of 5G and enhance their skills
in the area of communication technology.
Comparison of cellular networks
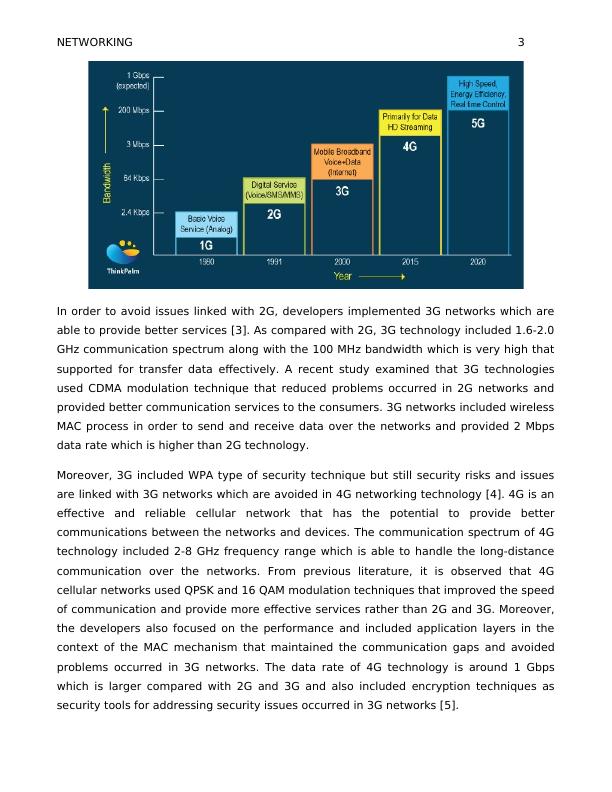
A cellular network is a kind of radio network which is mainly distributed over land areas
and each cell is served by one fixed transceiver called as the base station. There are
major five generations of cellular networks including 1G, 2G, 3G, 4G and 5G that help the
users for performing data transmission over the networks. In the case of 2G, the
developers used time division multiplexing technique which divided time into numbers of
sections. It is observed that 2G cellular network included MHz and GHz frequency rangers
in the communication spectrum and also provide 900 MHz bandwidth which is less for
performing wireless communication over the networks [2].
Moreover, such kind of communication technology utilized digital modulation technique
that provided better strengths of the transmitted signals and avoids errors from the
system. As compared with previous communication technology 2G provided 64 kbps data
rate which is less that cannot be used for long-distance communication. Moreover, 2G
involved less secured techniques due to which the consumers were suffered from security
threats and hacking related issues.
Figure: cellular networks [6]
Introduction
The use of communication technologies are growing rapidly and 5G is the latest
networking technology that provides large data rate and better services to the
consumers. 5G communication technology has the capability to provide higher system
capacity that can help users for performing data transmission in an effective manner. It is
an advanced version of 4G technology that can be used in the companies to enhance the
performance of communication networks and exchange data in less time [1]. This
investigation mainly focuses on the 5G networking technology and provides technical
aspects of 5G networks along with the security issues. It is observed that communication
networks require proper connections with the computing devices and the presence of
conflicts in the system may lead to data breach-related problems. It is suggested that this
research will provide in-depth analysis related to the 5G networks which can help the
readers and students for understanding technical aspects of 5G and enhance their skills
in the area of communication technology.
Comparison of cellular networks
A cellular network is a kind of radio network which is mainly distributed over land areas
and each cell is served by one fixed transceiver called as the base station. There are
major five generations of cellular networks including 1G, 2G, 3G, 4G and 5G that help the
users for performing data transmission over the networks. In the case of 2G, the
developers used time division multiplexing technique which divided time into numbers of
sections. It is observed that 2G cellular network included MHz and GHz frequency rangers
in the communication spectrum and also provide 900 MHz bandwidth which is less for
performing wireless communication over the networks [2].
Moreover, such kind of communication technology utilized digital modulation technique
that provided better strengths of the transmitted signals and avoids errors from the
system. As compared with previous communication technology 2G provided 64 kbps data
rate which is less that cannot be used for long-distance communication. Moreover, 2G
involved less secured techniques due to which the consumers were suffered from security
threats and hacking related issues.
Figure: cellular networks [6]

NETWORKING 3
In order to avoid issues linked with 2G, developers implemented 3G networks which are
able to provide better services [3]. As compared with 2G, 3G technology included 1.6-2.0
GHz communication spectrum along with the 100 MHz bandwidth which is very high that
supported for transfer data effectively. A recent study examined that 3G technologies
used CDMA modulation technique that reduced problems occurred in 2G networks and
provided better communication services to the consumers. 3G networks included wireless
MAC process in order to send and receive data over the networks and provided 2 Mbps
data rate which is higher than 2G technology.
Moreover, 3G included WPA type of security technique but still security risks and issues
are linked with 3G networks which are avoided in 4G networking technology [4]. 4G is an
effective and reliable cellular network that has the potential to provide better
communications between the networks and devices. The communication spectrum of 4G
technology included 2-8 GHz frequency range which is able to handle the long-distance
communication over the networks. From previous literature, it is observed that 4G
cellular networks used QPSK and 16 QAM modulation techniques that improved the speed
of communication and provide more effective services rather than 2G and 3G. Moreover,
the developers also focused on the performance and included application layers in the
context of the MAC mechanism that maintained the communication gaps and avoided
problems occurred in 3G networks. The data rate of 4G technology is around 1 Gbps
which is larger compared with 2G and 3G and also included encryption techniques as
security tools for addressing security issues occurred in 3G networks [5].
In order to avoid issues linked with 2G, developers implemented 3G networks which are
able to provide better services [3]. As compared with 2G, 3G technology included 1.6-2.0
GHz communication spectrum along with the 100 MHz bandwidth which is very high that
supported for transfer data effectively. A recent study examined that 3G technologies
used CDMA modulation technique that reduced problems occurred in 2G networks and
provided better communication services to the consumers. 3G networks included wireless
MAC process in order to send and receive data over the networks and provided 2 Mbps
data rate which is higher than 2G technology.
Moreover, 3G included WPA type of security technique but still security risks and issues
are linked with 3G networks which are avoided in 4G networking technology [4]. 4G is an
effective and reliable cellular network that has the potential to provide better
communications between the networks and devices. The communication spectrum of 4G
technology included 2-8 GHz frequency range which is able to handle the long-distance
communication over the networks. From previous literature, it is observed that 4G
cellular networks used QPSK and 16 QAM modulation techniques that improved the speed
of communication and provide more effective services rather than 2G and 3G. Moreover,
the developers also focused on the performance and included application layers in the
context of the MAC mechanism that maintained the communication gaps and avoided
problems occurred in 3G networks. The data rate of 4G technology is around 1 Gbps
which is larger compared with 2G and 3G and also included encryption techniques as
security tools for addressing security issues occurred in 3G networks [5].
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Wireless And Network Security Assignment 2022lg...
|10
|2527
|22
Wireless Network and Security Research Paper 2022lg...
|10
|2652
|20
Wireless Networks and Securitylg...
|11
|2619
|37
The wireless network and securitylg...
|10
|3158
|18
WIRELESS NETWORK AND SECURITY DISCUSSION 2022lg...
|12
|2964
|26
Network and the Security Case Study 2022lg...
|9
|2341
|36
