Accounting Definitions and Types of Controls
7 Pages2602 Words21 Views
Added on 2023-01-05
About This Document
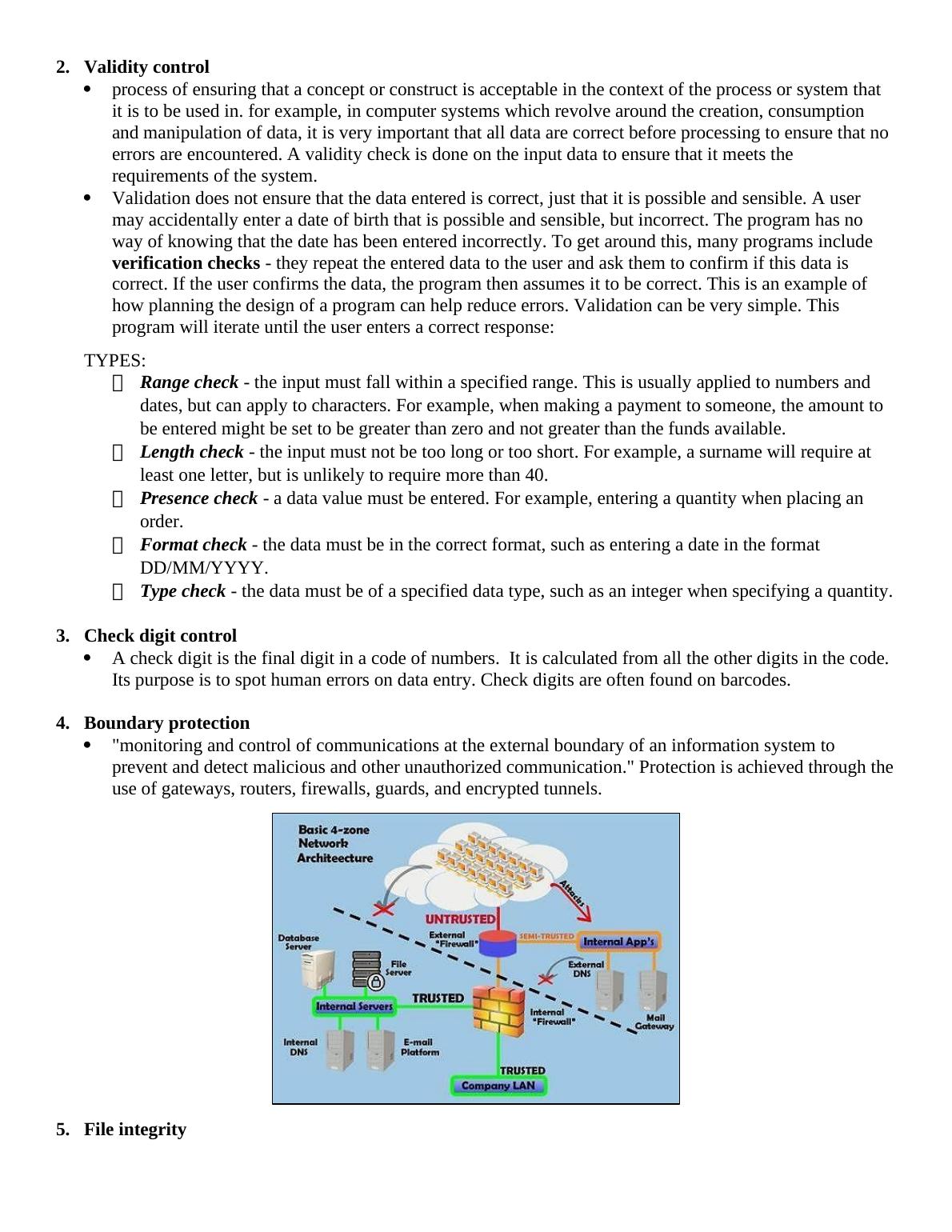
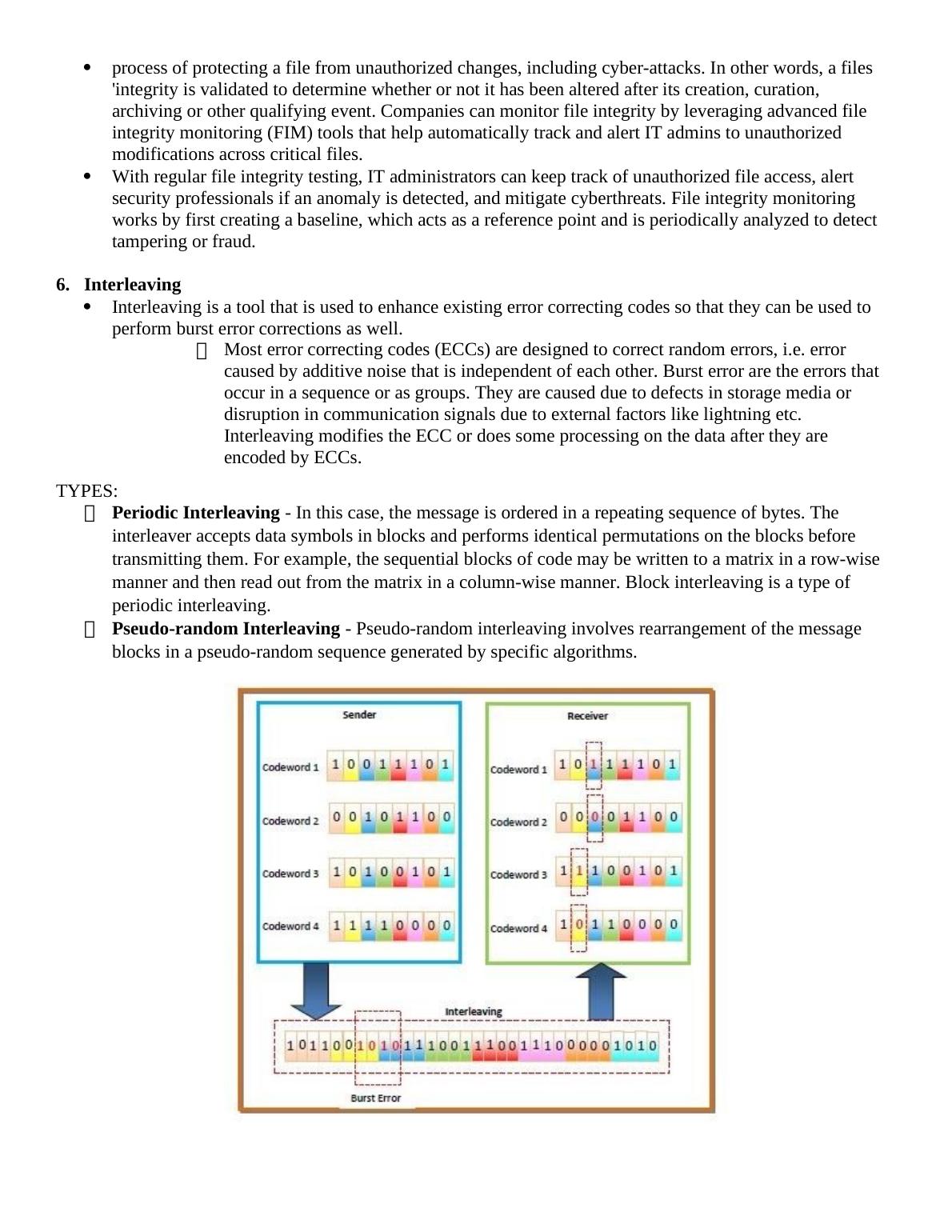
This document provides definitions and explanations of various accounting concepts, such as echo control, validity control, check digit control, and more. It also discusses different types of controls, including preventive, detective, and corrective controls. Additionally, it covers auditing through the computer and CAATs techniques. This information is relevant for students studying accounting and auditing.
Accounting Definitions and Types of Controls
Added on 2023-01-05
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
NIT5150 The Gym Membership Calculator (Doc)
|6
|638
|45
Developing a Command Line Text-Based User Interface for Memory Database
|13
|1316
|373
Programming Principles Document
|8
|493
|42
Employee Salary Calculator
|8
|1084
|42
Menu Of The SMS Program
|7
|537
|292
Fuel Management Software Solution for an Irish Airline
|2
|990
|389