Implementing Client-Server Model in Linux: UDP, TCP, and DNS Server
VerifiedAdded on 2021/02/20
|17
|3904
|40
Report
AI Summary
This report provides a comprehensive overview of the client-server model within a Linux environment. It begins by introducing the fundamental concepts of client-server architecture, outlining the roles of clients and servers, and explaining the communication processes involved, including the OSI and TCP/IP models. The report delves into the specifics of process management within Linux, defining Process IDs (PIDs), Parent Process IDs (PPIDs), and the 'init' process, and compares the operations of parent and child processes. A significant portion of the report focuses on the practical implementation of a client-server model in Linux, exploring the features of Linux server configurations, and evaluating the roles of UDP and TCP protocols in network communication. The implementation of a DNS server using UDP and TCP is also discussed. Furthermore, the report addresses network security, evaluating network security protocols, analyzing the purpose and requirements of network security, and providing insights into the design and configuration of a secure network. The report concludes by summarizing the key findings and emphasizing the importance of understanding the client-server model and network security in modern computing environments.

Advance Computer Network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
Concept of the Server Client and processes...................................................................................1
1.1 Client Server environment and its communication process..................................................1
1.2 Definition of Process ID (PID), Parent process ID (PPID) and Init......................................3
1.3 Comparing the operations of the parent and child Processes................................................3
Create a Client server Model in Lynax system................................................................................4
2.1 The Features of Linux Server configuration..........................................................................4
2.2 Evaluating the concept of UDP and TCP Systems................................................................6
2.3 Implementing the DNS server in Linux using UDP and TCP...............................................8
Secure Network for a corporate network.........................................................................................9
3.1 Evaluation of the Network Security Protocol........................................................................9
3.2 Critically analyse the purpose and Requirements of Network Security..............................10
3.3 Design of a Secured network...............................................................................................11
3.4 Configuring the Network security for a Secure network.....................................................11
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................14
INTRODUCTION...........................................................................................................................1
Concept of the Server Client and processes...................................................................................1
1.1 Client Server environment and its communication process..................................................1
1.2 Definition of Process ID (PID), Parent process ID (PPID) and Init......................................3
1.3 Comparing the operations of the parent and child Processes................................................3
Create a Client server Model in Lynax system................................................................................4
2.1 The Features of Linux Server configuration..........................................................................4
2.2 Evaluating the concept of UDP and TCP Systems................................................................6
2.3 Implementing the DNS server in Linux using UDP and TCP...............................................8
Secure Network for a corporate network.........................................................................................9
3.1 Evaluation of the Network Security Protocol........................................................................9
3.2 Critically analyse the purpose and Requirements of Network Security..............................10
3.3 Design of a Secured network...............................................................................................11
3.4 Configuring the Network security for a Secure network.....................................................11
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................14

INTRODUCTION
Computer network can be defined as the connection of one or more computer systems in
order to share the data and information over the internet. Advanced computer network covers the
set of advanced topics in computer networks such as which covers the internet, social media,
cloud computing and various other high performance network centres. The study will be based
on the advanced and modern concepts in networking technologies. It will also help in developing
a clear understanding about the Client server relationship using various in a Lynax system which
can be established via UDP, TCP and Application layer.
In addition, this report will also helps in understanding features of the Lynax server
configurations. It will also explore about the User datagram Protocol which is used in
establishing Client server network architecture. It will also be able to develop the knowledge
about the Network Security protocols. Moreover, It helps in determining the purpose and
requirements of the secured network
Concept of the Server Client and processes
1.1 Client Server environment and its communication process
The Open System Interconnection Model (OSI model) helps in applying the concept
which derives the telecommunication facilities. It basically provides a model that assists an
application to communicate over the network. OSI model enables the data communication
between any two networked systems. It is composed of seven different types of layer r elated
functions (Besmer, 2018). In these each communication user or program is on a device in which
each layer is served by the layer above it and followed by the layer below it. Client Server model
allows the exchange of the data and information within the distributed environment so that it
allows the access of the server via multiple clients. There are Seven Layers in OSI model which
can be described below:
Application Model
This layer allows the intercommunication link between the user and server in the form of
interface. Also this provides the various different kinds of services such as mail facility, data
base management and accessibility of huge files to maintain the confidential data of the business
etc.
Presentation Model
1
Computer network can be defined as the connection of one or more computer systems in
order to share the data and information over the internet. Advanced computer network covers the
set of advanced topics in computer networks such as which covers the internet, social media,
cloud computing and various other high performance network centres. The study will be based
on the advanced and modern concepts in networking technologies. It will also help in developing
a clear understanding about the Client server relationship using various in a Lynax system which
can be established via UDP, TCP and Application layer.
In addition, this report will also helps in understanding features of the Lynax server
configurations. It will also explore about the User datagram Protocol which is used in
establishing Client server network architecture. It will also be able to develop the knowledge
about the Network Security protocols. Moreover, It helps in determining the purpose and
requirements of the secured network
Concept of the Server Client and processes
1.1 Client Server environment and its communication process
The Open System Interconnection Model (OSI model) helps in applying the concept
which derives the telecommunication facilities. It basically provides a model that assists an
application to communicate over the network. OSI model enables the data communication
between any two networked systems. It is composed of seven different types of layer r elated
functions (Besmer, 2018). In these each communication user or program is on a device in which
each layer is served by the layer above it and followed by the layer below it. Client Server model
allows the exchange of the data and information within the distributed environment so that it
allows the access of the server via multiple clients. There are Seven Layers in OSI model which
can be described below:
Application Model
This layer allows the intercommunication link between the user and server in the form of
interface. Also this provides the various different kinds of services such as mail facility, data
base management and accessibility of huge files to maintain the confidential data of the business
etc.
Presentation Model
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

It emphasis on syntax and semantics that are used during the transmission of the data and
information. It enables the translation, encryption, compression and encoding of the existing
form of data into another form.
Session Layer
This layer allows in synchronization in order to keep the communication within 2
systems. This layer is used to establish a session between them (Colin, Nakechbandi and
Mathieu, 2019). It includes services such as control Dialog box and Synchronisation.
Transport Layer
This layer helps in receiving the independent packets of data and this layer provides the
services such as connection control, segmentation, flow control, etc.
Network Layer
This layer allows the logical addressing which helps in locating the data and information
which has been sent via multiple packets. It translates logical address into physical MAC
addresses so that it allows the communication and interaction of multiple devices with each
other.
Data Link Layer
It connects the Physical layer and makes it free from the errors via masking methods.
This layer mainly includes the services such as framing, error, etc.
Physical Layer
It transmits the data into the binary format over transmission channel therefore this layer
mainly deals with the characteristics between the device and the transmission media. It includes
various services such as bits representation, line configuration, transmission mode, data rates etc.
There is one more model that is TCP/IP which helps in establishing a client server
model. It mainly consists of the four layers which are similar to the layers of the OSI model
(DMello, Foo and Reid, 2018). However, it differs from various things such are described below:
Internet protocol or Transmission control protocol is a client server model that is based
on the availability of the services via server according to the requests of the client.
Transmission control Protocol is a standard rule of IT whereas OSI is a conceptual
protocol.
TCP/IP consists of four layers which are common in OSI while the OSI is a seven layered
Model.
2
information. It enables the translation, encryption, compression and encoding of the existing
form of data into another form.
Session Layer
This layer allows in synchronization in order to keep the communication within 2
systems. This layer is used to establish a session between them (Colin, Nakechbandi and
Mathieu, 2019). It includes services such as control Dialog box and Synchronisation.
Transport Layer
This layer helps in receiving the independent packets of data and this layer provides the
services such as connection control, segmentation, flow control, etc.
Network Layer
This layer allows the logical addressing which helps in locating the data and information
which has been sent via multiple packets. It translates logical address into physical MAC
addresses so that it allows the communication and interaction of multiple devices with each
other.
Data Link Layer
It connects the Physical layer and makes it free from the errors via masking methods.
This layer mainly includes the services such as framing, error, etc.
Physical Layer
It transmits the data into the binary format over transmission channel therefore this layer
mainly deals with the characteristics between the device and the transmission media. It includes
various services such as bits representation, line configuration, transmission mode, data rates etc.
There is one more model that is TCP/IP which helps in establishing a client server
model. It mainly consists of the four layers which are similar to the layers of the OSI model
(DMello, Foo and Reid, 2018). However, it differs from various things such are described below:
Internet protocol or Transmission control protocol is a client server model that is based
on the availability of the services via server according to the requests of the client.
Transmission control Protocol is a standard rule of IT whereas OSI is a conceptual
protocol.
TCP/IP consists of four layers which are common in OSI while the OSI is a seven layered
Model.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Transmission control protocol and Internet protocol generally follows vertical approach
on the other hand, OSI follows horizontal approach.
TCP/IP is a Tangible whereas OSI model is conceptual or intangible.
TCP/IP generally follows TOP bottom approach and on the other hand, OSI follows
Bottom up approach.
1.2 Definition of Process ID (PID), Parent process ID (PPID) and Init.
It is normally defined as a Process identifier and it is basically a number which is
normally used by the Kernals of most of the Operating systems such as UNIX, macOS and
Microsoft Windows. It can be used to assign a unique ID to the process which is running into the
system.
In addition PPID is a unique processes ID, in which each process is allocated with one
parent process ID (PPID) and this helps in determining the currently started process. Basically
PPID is a PID of a process's parent. Sometimes, the processes go bad and users quit the program
in order to find the other intentions of it (Hosen, 2018). However, the program continues to use
the resources even after it is closed by the user. So such processes are called as Zombie process,
in simple words it can be termed as the process which is currently processing but it is actually
dead as its parent process does not exists in the system. Although, kill the parent process might
kill other children of the same parent process.
The process init is only the process that will always have the same PID weather it can be
any system or it can be any session but the PID is still 1.
1.3 Comparing the operations of the parent and child Processes
There are two ID numbers that are generally assigned to the UNIX process in order to
identify each process within the system such process can be considered as PID and PPID. Pid is
the small processes which Since LYNUX is a time shared Operating system, so the two
processes can be concurrently executed. In these type of OS the first process, init is created by
the Kernel at boot time and is never terminated until the system runs. Although, other parentless
processes may be launched in order to perform different daemon tasks. In some situation, it can
be obtained that some child processes are orphaned when its parent dies which can be further
adopted by the Init pro cess for the short period of time. In contrast, the child process gener ally
derived from the parent which can be invoked via Fork () function that is used to call the system.
3
on the other hand, OSI follows horizontal approach.
TCP/IP is a Tangible whereas OSI model is conceptual or intangible.
TCP/IP generally follows TOP bottom approach and on the other hand, OSI follows
Bottom up approach.
1.2 Definition of Process ID (PID), Parent process ID (PPID) and Init.
It is normally defined as a Process identifier and it is basically a number which is
normally used by the Kernals of most of the Operating systems such as UNIX, macOS and
Microsoft Windows. It can be used to assign a unique ID to the process which is running into the
system.
In addition PPID is a unique processes ID, in which each process is allocated with one
parent process ID (PPID) and this helps in determining the currently started process. Basically
PPID is a PID of a process's parent. Sometimes, the processes go bad and users quit the program
in order to find the other intentions of it (Hosen, 2018). However, the program continues to use
the resources even after it is closed by the user. So such processes are called as Zombie process,
in simple words it can be termed as the process which is currently processing but it is actually
dead as its parent process does not exists in the system. Although, kill the parent process might
kill other children of the same parent process.
The process init is only the process that will always have the same PID weather it can be
any system or it can be any session but the PID is still 1.
1.3 Comparing the operations of the parent and child Processes
There are two ID numbers that are generally assigned to the UNIX process in order to
identify each process within the system such process can be considered as PID and PPID. Pid is
the small processes which Since LYNUX is a time shared Operating system, so the two
processes can be concurrently executed. In these type of OS the first process, init is created by
the Kernel at boot time and is never terminated until the system runs. Although, other parentless
processes may be launched in order to perform different daemon tasks. In some situation, it can
be obtained that some child processes are orphaned when its parent dies which can be further
adopted by the Init pro cess for the short period of time. In contrast, the child process gener ally
derived from the parent which can be invoked via Fork () function that is used to call the system.
3

Where as child process is created as it's parents processes copy which inherits most of its
attributes.
For Example, the PPID is the PID of the Processes parent. So here, if the process 1 with a
PID of 208 starts a process named Process2, then the process2 will be given a unique PID that is
3250 and thus it will be given a unique PPID for that process 101. it can be termed as a parent
child process.
Create a Client server Model in Lynax system
2.1 The Features of Linux Server configuration
LINUX can be considered the fastest operating system because it is the latest version of
UNIX which allows the free Operating system services to the user as it is open to all and freely
provided. It design was based on the compatibility of the UNIX which provides quite similar
functions like UNIX operating system. There are commonly three types of components included
in the Linux Operating system such as Kernel, system Libraries and System Utilities. The Core
features of this Operating system allows the effective communication between software and
Hardware. Basic Features of the Linux server configuration are as follows:
System Libraries
Kernel
Kernel Module
4
attributes.
For Example, the PPID is the PID of the Processes parent. So here, if the process 1 with a
PID of 208 starts a process named Process2, then the process2 will be given a unique PID that is
3250 and thus it will be given a unique PPID for that process 101. it can be termed as a parent
child process.
Create a Client server Model in Lynax system
2.1 The Features of Linux Server configuration
LINUX can be considered the fastest operating system because it is the latest version of
UNIX which allows the free Operating system services to the user as it is open to all and freely
provided. It design was based on the compatibility of the UNIX which provides quite similar
functions like UNIX operating system. There are commonly three types of components included
in the Linux Operating system such as Kernel, system Libraries and System Utilities. The Core
features of this Operating system allows the effective communication between software and
Hardware. Basic Features of the Linux server configuration are as follows:
System Libraries
Kernel
Kernel Module
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
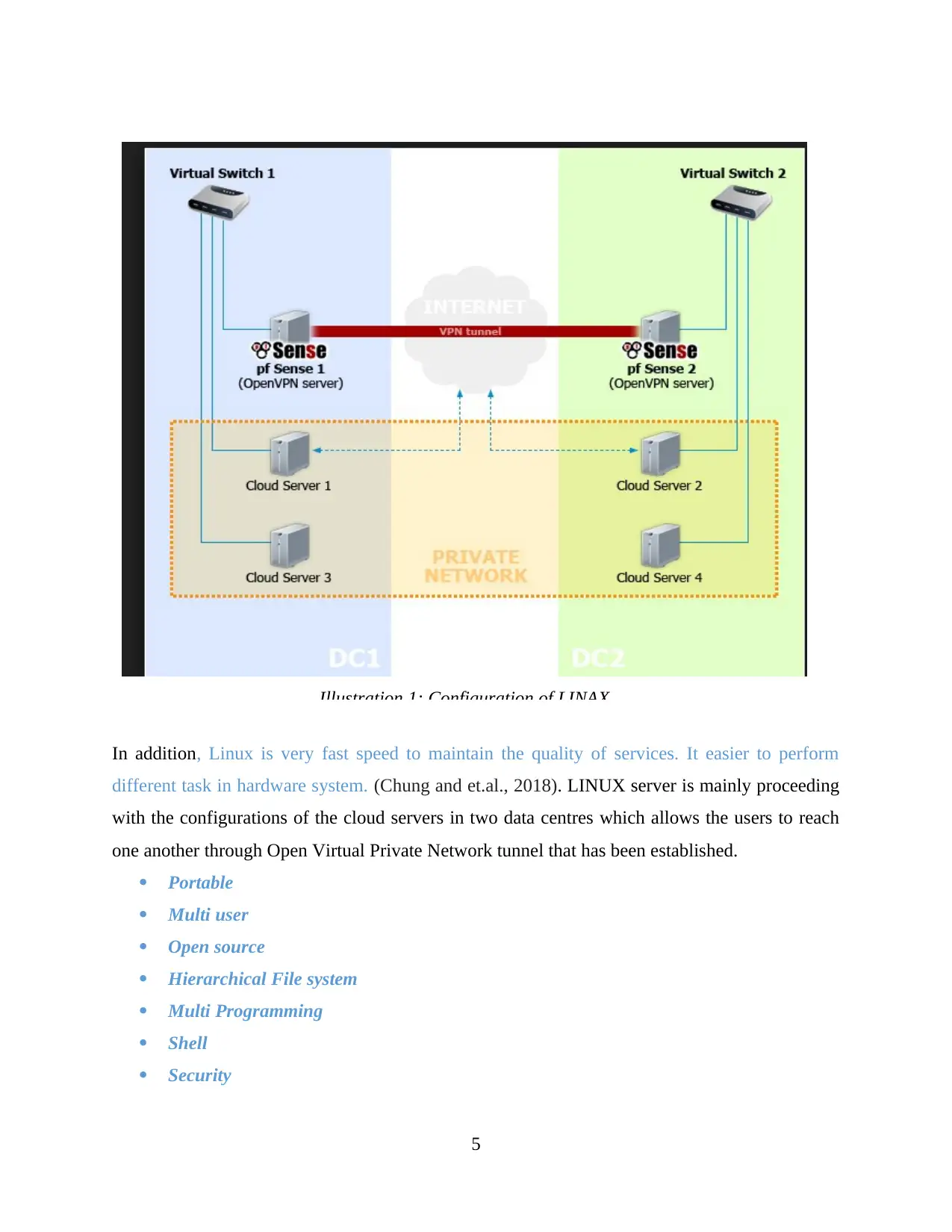
In addition, Linux is very fast speed to maintain the quality of services. It easier to perform
different task in hardware system. (Chung and et.al., 2018). LINUX server is mainly proceeding
with the configurations of the cloud servers in two data centres which allows the users to reach
one another through Open Virtual Private Network tunnel that has been established.
Portable
Multi user
Open source
Hierarchical File system
Multi Programming
Shell
Security
5
Illustration 1: Configuration of LINAX
different task in hardware system. (Chung and et.al., 2018). LINUX server is mainly proceeding
with the configurations of the cloud servers in two data centres which allows the users to reach
one another through Open Virtual Private Network tunnel that has been established.
Portable
Multi user
Open source
Hierarchical File system
Multi Programming
Shell
Security
5
Illustration 1: Configuration of LINAX
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
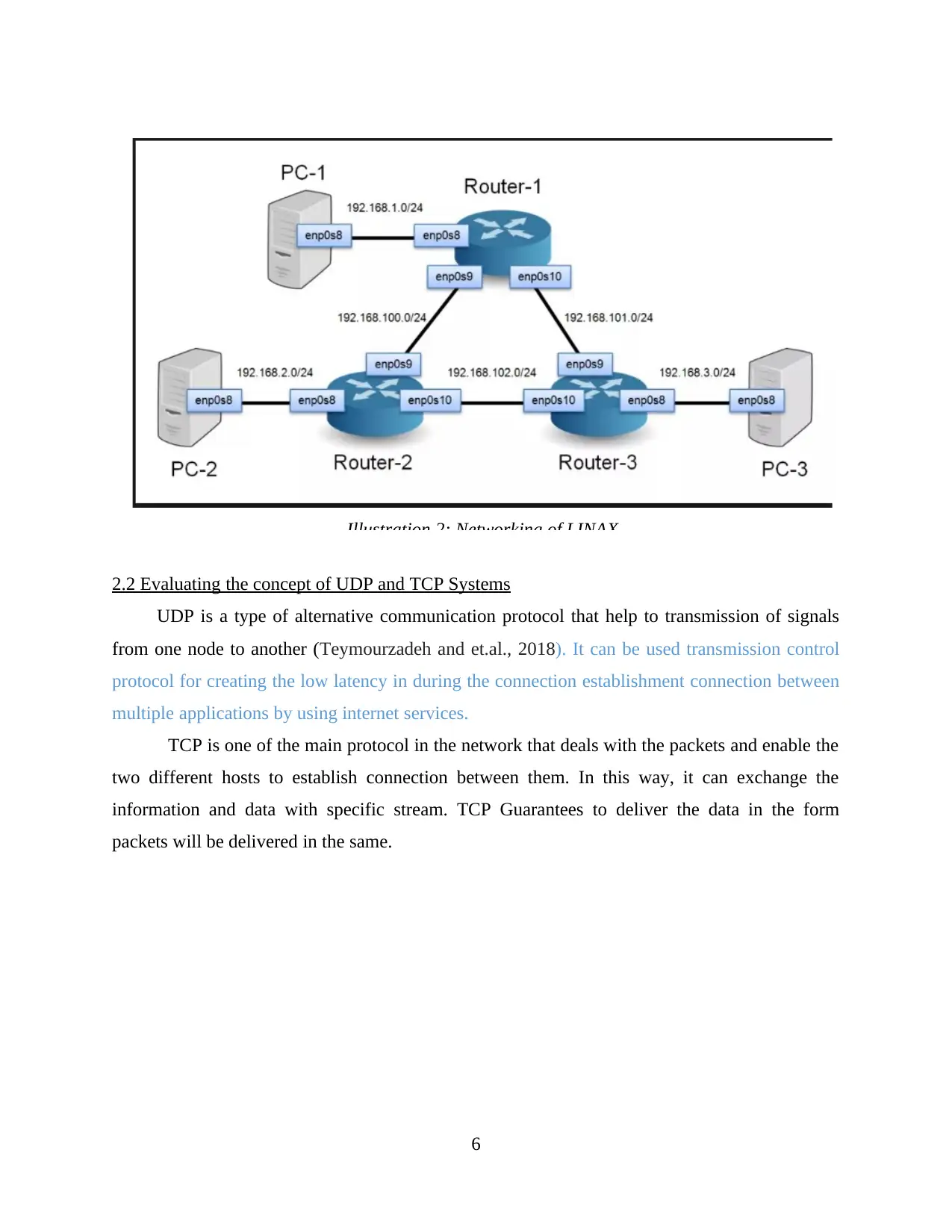
2.2 Evaluating the concept of UDP and TCP Systems
UDP is a type of alternative communication protocol that help to transmission of signals
from one node to another (Teymourzadeh and et.al., 2018). It can be used transmission control
protocol for creating the low latency in during the connection establishment connection between
multiple applications by using internet services.
TCP is one of the main protocol in the network that deals with the packets and enable the
two different hosts to establish connection between them. In this way, it can exchange the
information and data with specific stream. TCP Guarantees to deliver the data in the form
packets will be delivered in the same.
6
Illustration 2: Networking of LINAX
UDP is a type of alternative communication protocol that help to transmission of signals
from one node to another (Teymourzadeh and et.al., 2018). It can be used transmission control
protocol for creating the low latency in during the connection establishment connection between
multiple applications by using internet services.
TCP is one of the main protocol in the network that deals with the packets and enable the
two different hosts to establish connection between them. In this way, it can exchange the
information and data with specific stream. TCP Guarantees to deliver the data in the form
packets will be delivered in the same.
6
Illustration 2: Networking of LINAX
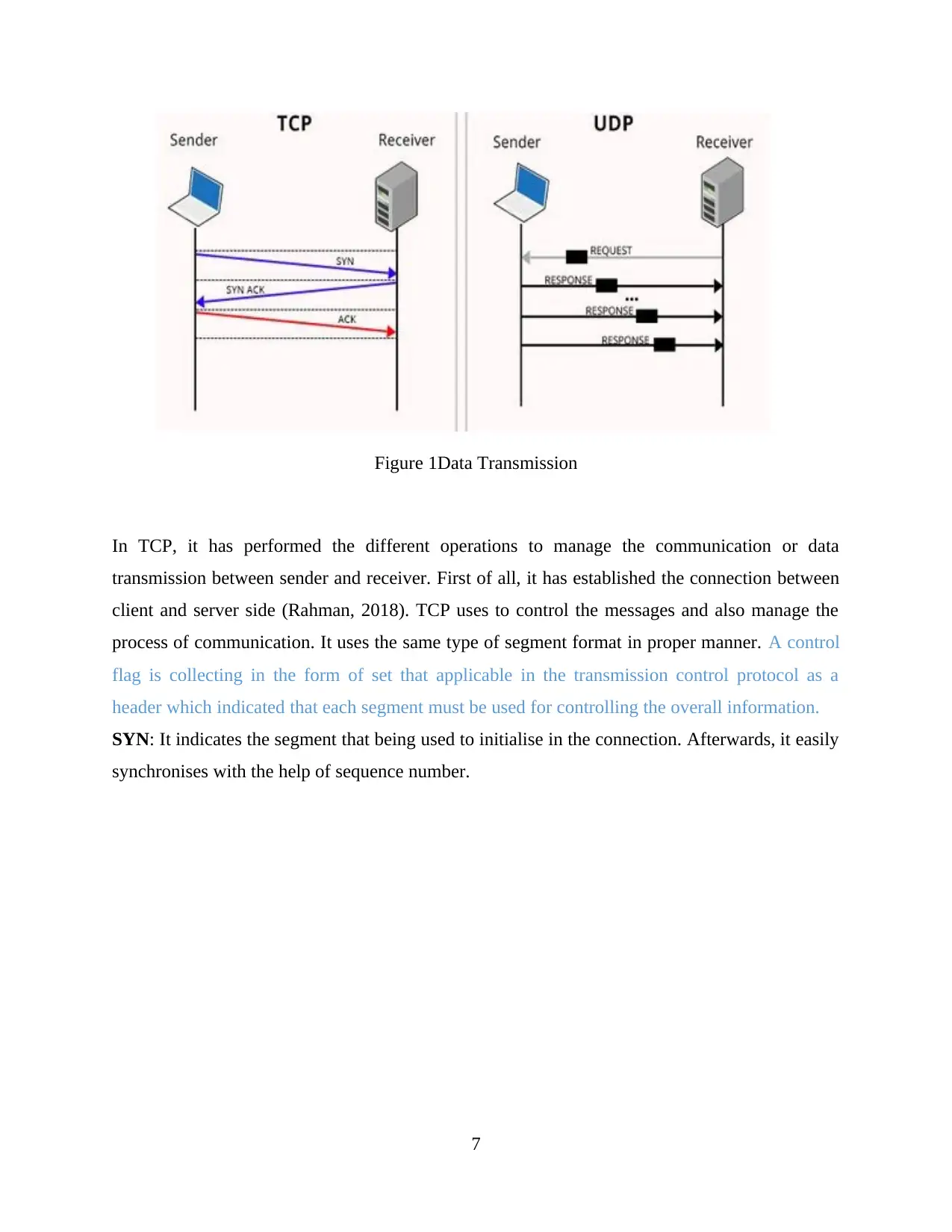
Figure 1Data Transmission
In TCP, it has performed the different operations to manage the communication or data
transmission between sender and receiver. First of all, it has established the connection between
client and server side (Rahman, 2018). TCP uses to control the messages and also manage the
process of communication. It uses the same type of segment format in proper manner. A control
flag is collecting in the form of set that applicable in the transmission control protocol as a
header which indicated that each segment must be used for controlling the overall information.
SYN: It indicates the segment that being used to initialise in the connection. Afterwards, it easily
synchronises with the help of sequence number.
7
In TCP, it has performed the different operations to manage the communication or data
transmission between sender and receiver. First of all, it has established the connection between
client and server side (Rahman, 2018). TCP uses to control the messages and also manage the
process of communication. It uses the same type of segment format in proper manner. A control
flag is collecting in the form of set that applicable in the transmission control protocol as a
header which indicated that each segment must be used for controlling the overall information.
SYN: It indicates the segment that being used to initialise in the connection. Afterwards, it easily
synchronises with the help of sequence number.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ACK: It indicated that the device is sending the data into the segment and conveying
acknowledgement for message it has received.
In UDP, it is based on the connectionless and unreliable transport protocol. It consists of
two ports server during data transmission to determine end points of client and server side.
Server send a request to the client related the data transmission; afterwards they were sending the
message of response to server side. In this way, it has created data transmission process between
two hosts. During UDP connection, client has been fixed the unique source number according to
the program and also started to create new connections.
2.3 Implementing the DNS server in Linux using UDP and TCP
DNS Server is primarily uses the both type of protocols such as UDP and TCP. UDP
useful for exchange the small information from one node to another with the help of TCP that
must exchange the information large than 513 bytes (Khorram and Baykan, 2018). DNS is
default uses the resolution services in Linux. However, when the internet was small and host
name resolution by using the file name of host under Linux.
DNS Implementation:
Unix system is basically used the Berkeley internet name domain which are typically use as
the non-active directory with the specific domain name solution. There are common steps to
implement the DNS server in Linux operating system.
First of all, it can be used the specific domain name like google.com into the browser by
using the operating systems of client side.
Client has needed to use the proper IP address where it helps to find the location of
domain name on the world.
The browser is sending the specific queries towards the Operating system.
It is configured every OS to identify the queries of Domain name system server. It is
generally used the network administrator to configure the DNS server. It is called as a
resolving name server.
The server was not aware about proper place of domain name but it does know about the
root server where it is located.
8
acknowledgement for message it has received.
In UDP, it is based on the connectionless and unreliable transport protocol. It consists of
two ports server during data transmission to determine end points of client and server side.
Server send a request to the client related the data transmission; afterwards they were sending the
message of response to server side. In this way, it has created data transmission process between
two hosts. During UDP connection, client has been fixed the unique source number according to
the program and also started to create new connections.
2.3 Implementing the DNS server in Linux using UDP and TCP
DNS Server is primarily uses the both type of protocols such as UDP and TCP. UDP
useful for exchange the small information from one node to another with the help of TCP that
must exchange the information large than 513 bytes (Khorram and Baykan, 2018). DNS is
default uses the resolution services in Linux. However, when the internet was small and host
name resolution by using the file name of host under Linux.
DNS Implementation:
Unix system is basically used the Berkeley internet name domain which are typically use as
the non-active directory with the specific domain name solution. There are common steps to
implement the DNS server in Linux operating system.
First of all, it can be used the specific domain name like google.com into the browser by
using the operating systems of client side.
Client has needed to use the proper IP address where it helps to find the location of
domain name on the world.
The browser is sending the specific queries towards the Operating system.
It is configured every OS to identify the queries of Domain name system server. It is
generally used the network administrator to configure the DNS server. It is called as a
resolving name server.
The server was not aware about proper place of domain name but it does know about the
root server where it is located.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
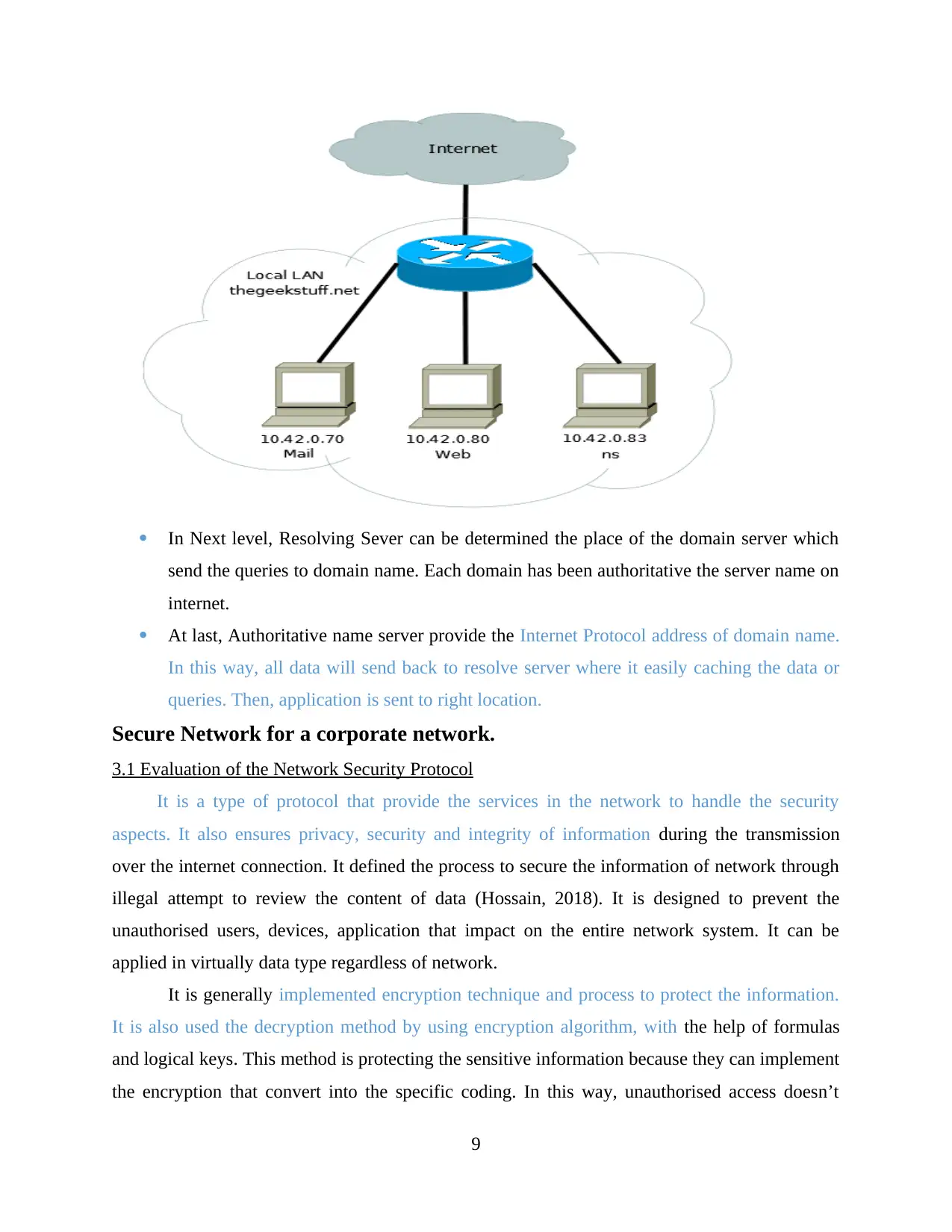
In Next level, Resolving Sever can be determined the place of the domain server which
send the queries to domain name. Each domain has been authoritative the server name on
internet.
At last, Authoritative name server provide the Internet Protocol address of domain name.
In this way, all data will send back to resolve server where it easily caching the data or
queries. Then, application is sent to right location.
Secure Network for a corporate network.
3.1 Evaluation of the Network Security Protocol
It is a type of protocol that provide the services in the network to handle the security
aspects. It also ensures privacy, security and integrity of information during the transmission
over the internet connection. It defined the process to secure the information of network through
illegal attempt to review the content of data (Hossain, 2018). It is designed to prevent the
unauthorised users, devices, application that impact on the entire network system. It can be
applied in virtually data type regardless of network.
It is generally implemented encryption technique and process to protect the information.
It is also used the decryption method by using encryption algorithm, with the help of formulas
and logical keys. This method is protecting the sensitive information because they can implement
the encryption that convert into the specific coding. In this way, unauthorised access doesn’t
9
send the queries to domain name. Each domain has been authoritative the server name on
internet.
At last, Authoritative name server provide the Internet Protocol address of domain name.
In this way, all data will send back to resolve server where it easily caching the data or
queries. Then, application is sent to right location.
Secure Network for a corporate network.
3.1 Evaluation of the Network Security Protocol
It is a type of protocol that provide the services in the network to handle the security
aspects. It also ensures privacy, security and integrity of information during the transmission
over the internet connection. It defined the process to secure the information of network through
illegal attempt to review the content of data (Hossain, 2018). It is designed to prevent the
unauthorised users, devices, application that impact on the entire network system. It can be
applied in virtually data type regardless of network.
It is generally implemented encryption technique and process to protect the information.
It is also used the decryption method by using encryption algorithm, with the help of formulas
and logical keys. This method is protecting the sensitive information because they can implement
the encryption that convert into the specific coding. In this way, unauthorised access doesn’t
9
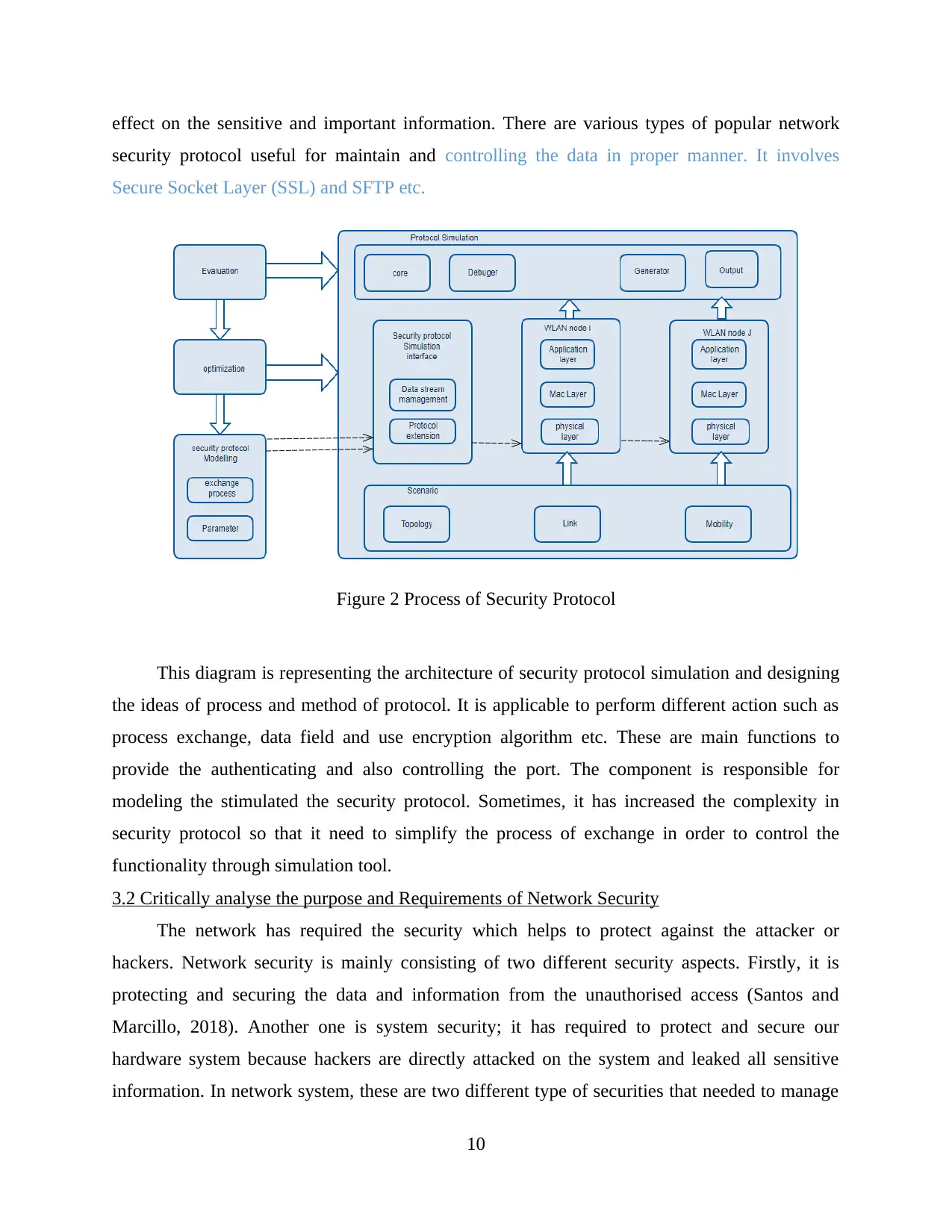
effect on the sensitive and important information. There are various types of popular network
security protocol useful for maintain and controlling the data in proper manner. It involves
Secure Socket Layer (SSL) and SFTP etc.
Figure 2 Process of Security Protocol
This diagram is representing the architecture of security protocol simulation and designing
the ideas of process and method of protocol. It is applicable to perform different action such as
process exchange, data field and use encryption algorithm etc. These are main functions to
provide the authenticating and also controlling the port. The component is responsible for
modeling the stimulated the security protocol. Sometimes, it has increased the complexity in
security protocol so that it need to simplify the process of exchange in order to control the
functionality through simulation tool.
3.2 Critically analyse the purpose and Requirements of Network Security
The network has required the security which helps to protect against the attacker or
hackers. Network security is mainly consisting of two different security aspects. Firstly, it is
protecting and securing the data and information from the unauthorised access (Santos and
Marcillo, 2018). Another one is system security; it has required to protect and secure our
hardware system because hackers are directly attacked on the system and leaked all sensitive
information. In network system, these are two different type of securities that needed to manage
10
security protocol useful for maintain and controlling the data in proper manner. It involves
Secure Socket Layer (SSL) and SFTP etc.
Figure 2 Process of Security Protocol
This diagram is representing the architecture of security protocol simulation and designing
the ideas of process and method of protocol. It is applicable to perform different action such as
process exchange, data field and use encryption algorithm etc. These are main functions to
provide the authenticating and also controlling the port. The component is responsible for
modeling the stimulated the security protocol. Sometimes, it has increased the complexity in
security protocol so that it need to simplify the process of exchange in order to control the
functionality through simulation tool.
3.2 Critically analyse the purpose and Requirements of Network Security
The network has required the security which helps to protect against the attacker or
hackers. Network security is mainly consisting of two different security aspects. Firstly, it is
protecting and securing the data and information from the unauthorised access (Santos and
Marcillo, 2018). Another one is system security; it has required to protect and secure our
hardware system because hackers are directly attacked on the system and leaked all sensitive
information. In network system, these are two different type of securities that needed to manage
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





