Developing a Network Solution for uSoft.com
VerifiedAdded on 2023/04/24
|11
|3504
|119
AI Summary
The main aim of this paper is to develop a network solution for the uSoft.com as they need to connect two of their office branches for communication purpose. In this paper current network framework which is used by the organization is evaluated and various of issues in the current network framework has been assessed. Depending on the issues that has been determined solution has been determined for fulfilling the technical goals and business goals of the organization.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: DATA COMMUNICATION AND NETWORK
Data Communication and Network
Name of the Student
Name of the University
Author Note
Data Communication and Network
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1DATA COMMUNICATION AND NETWORK
Executive Summary:
The main aim of this paper is to develop a network solution for the uSoft.com as they need to
connect two of their office branches for communication purpose. In this paper current network
framework which is used by the organization is evaluated and various of issues in the current
network framework has been assessed. Depending on the issues that has been determined solution
has been determined for fulfilling the technical goals and business goals of the organization. In this
paper the security requirement of the organization has been assessed and for protecting the IT
assists of the uSoft.com from external agents and external agents. Also, this report has comprised
analysis of the structure of HQ of the organization for providing a proposal of physical and logical
network framework. This paper has also evaluated the building plan of the HQ of organization for
identifying the network device placement and development of the physical network topology to
ensure that network is able to meet the business requirement of the uSoft.com.
Executive Summary:
The main aim of this paper is to develop a network solution for the uSoft.com as they need to
connect two of their office branches for communication purpose. In this paper current network
framework which is used by the organization is evaluated and various of issues in the current
network framework has been assessed. Depending on the issues that has been determined solution
has been determined for fulfilling the technical goals and business goals of the organization. In this
paper the security requirement of the organization has been assessed and for protecting the IT
assists of the uSoft.com from external agents and external agents. Also, this report has comprised
analysis of the structure of HQ of the organization for providing a proposal of physical and logical
network framework. This paper has also evaluated the building plan of the HQ of organization for
identifying the network device placement and development of the physical network topology to
ensure that network is able to meet the business requirement of the uSoft.com.

2DATA COMMUNICATION AND NETWORK
Table of Contents
1. Introduction:......................................................................................................................................3
1.1 Goals............................................................................................................................................3
1.2 Purpose:.......................................................................................................................................3
1.3 Background and Scope:...............................................................................................................3
2. Organizational Description:...............................................................................................................4
3. Analysis of the user requirements:....................................................................................................4
3.1 Mobility Requirement:.................................................................................................................4
3.2 Security requirement:..................................................................................................................4
3.3 Bandwidth Requirement:.............................................................................................................4
3.4 Application Requirement:............................................................................................................4
3.5 Remote access requirement:.......................................................................................................4
3.6. Performance Requirement.........................................................................................................4
3.7. Quality of Service (QoS) Requirement........................................................................................5
3.8. VoIP Service Requirement..........................................................................................................5
4. Logical Design:...................................................................................................................................5
4.1 Security:.......................................................................................................................................5
4.2 Wireless Network:.......................................................................................................................5
4.3 Virtual LANs:................................................................................................................................5
5. IP Address Allocation Plan:................................................................................................................5
6. Logical Network Diagram:..................................................................................................................7
7. Physical Network Diagram:................................................................................................................7
8. Conclusion:........................................................................................................................................8
9. Bibliography:......................................................................................................................................9
Table of Contents
1. Introduction:......................................................................................................................................3
1.1 Goals............................................................................................................................................3
1.2 Purpose:.......................................................................................................................................3
1.3 Background and Scope:...............................................................................................................3
2. Organizational Description:...............................................................................................................4
3. Analysis of the user requirements:....................................................................................................4
3.1 Mobility Requirement:.................................................................................................................4
3.2 Security requirement:..................................................................................................................4
3.3 Bandwidth Requirement:.............................................................................................................4
3.4 Application Requirement:............................................................................................................4
3.5 Remote access requirement:.......................................................................................................4
3.6. Performance Requirement.........................................................................................................4
3.7. Quality of Service (QoS) Requirement........................................................................................5
3.8. VoIP Service Requirement..........................................................................................................5
4. Logical Design:...................................................................................................................................5
4.1 Security:.......................................................................................................................................5
4.2 Wireless Network:.......................................................................................................................5
4.3 Virtual LANs:................................................................................................................................5
5. IP Address Allocation Plan:................................................................................................................5
6. Logical Network Diagram:..................................................................................................................7
7. Physical Network Diagram:................................................................................................................7
8. Conclusion:........................................................................................................................................8
9. Bibliography:......................................................................................................................................9

3DATA COMMUNICATION AND NETWORK
1. Introduction:
1.1 Goals
The main business goals which are perused by the uSoft.com organization are discussed in
the below section.
Protection of various sensitive information within the organization and configuring the list of
access control for handling the access of the user to the servers of different department of
the organization.
Improvement of the wireless communication and the VoIP among all the departments of the
organization which will improve the performance of the current employees.
Network scalability improvement of the current network for allowing increased number
users to connect which will help in the growth of the company.
Configuring the network in such a way that performance will not be decreased with
increased number of users and other different types of risks must be mitigated such as jitter,
packet loss and contestation.
Configuring the access control list for communication management of the users for accessing
servers of different department of the organization.
Connecting different subnet wireless access point in such a way that the intruder will be able
to gain local network access.
1.2 Purpose:
The main purpose behind the development of this network is creating a network solution
that will consist a centralized management of data traffic flowing. This data flows from different of
sources to a specific destination address within the network. The successful data sending and data
receiving from the headquarters to the fellow branches of the organization will reduce the network
responding time. The network of the organization must be configured in such a way that the
employees will be connect with the organizational network from remote location. This will surely
improve the productivity of the employees. Also, the network must be configured in such way that
there is no error in the network configuration and no error will be occurring in the future cases.
Besides that user activity monitoring should be done in this type of system to ensure that the
resources are safe. Users can be monitored effectively by implementing a network security policy,
firewall and by implementing a DMZ.
1.3 Background and Scope:
The discussed network solution is in the development process for the uSoft.com
organization which is a private software development organization for biomedical solutions. This
organization is having a HQ which comprises of total 6 different departments in it. The main aim of
the organization behind developing this network solution expanding the organization with meeting
the technical and business goals of the organization. In the present situation the organization is
having total 102 numbers of employees in the department of software development. 92 employees
are working for designing the solution, 52 peoples are in sales department, 22 employees in human
resource department, 32 peoples in the financial department and 62 employees are serving in the
customer support department. The present network setup consists 1 server in each department of
human resource, finance and sales while the solution design department is having 2 severs and the
software development department is having total 3 servers installed the subnet of the network. In
this case some more numbers of IP addresses are kept in the reservation to support expansion
process of the organization that will help more employees to connect to each of the subnet which
are installed in the department of the organization.
1. Introduction:
1.1 Goals
The main business goals which are perused by the uSoft.com organization are discussed in
the below section.
Protection of various sensitive information within the organization and configuring the list of
access control for handling the access of the user to the servers of different department of
the organization.
Improvement of the wireless communication and the VoIP among all the departments of the
organization which will improve the performance of the current employees.
Network scalability improvement of the current network for allowing increased number
users to connect which will help in the growth of the company.
Configuring the network in such a way that performance will not be decreased with
increased number of users and other different types of risks must be mitigated such as jitter,
packet loss and contestation.
Configuring the access control list for communication management of the users for accessing
servers of different department of the organization.
Connecting different subnet wireless access point in such a way that the intruder will be able
to gain local network access.
1.2 Purpose:
The main purpose behind the development of this network is creating a network solution
that will consist a centralized management of data traffic flowing. This data flows from different of
sources to a specific destination address within the network. The successful data sending and data
receiving from the headquarters to the fellow branches of the organization will reduce the network
responding time. The network of the organization must be configured in such a way that the
employees will be connect with the organizational network from remote location. This will surely
improve the productivity of the employees. Also, the network must be configured in such way that
there is no error in the network configuration and no error will be occurring in the future cases.
Besides that user activity monitoring should be done in this type of system to ensure that the
resources are safe. Users can be monitored effectively by implementing a network security policy,
firewall and by implementing a DMZ.
1.3 Background and Scope:
The discussed network solution is in the development process for the uSoft.com
organization which is a private software development organization for biomedical solutions. This
organization is having a HQ which comprises of total 6 different departments in it. The main aim of
the organization behind developing this network solution expanding the organization with meeting
the technical and business goals of the organization. In the present situation the organization is
having total 102 numbers of employees in the department of software development. 92 employees
are working for designing the solution, 52 peoples are in sales department, 22 employees in human
resource department, 32 peoples in the financial department and 62 employees are serving in the
customer support department. The present network setup consists 1 server in each department of
human resource, finance and sales while the solution design department is having 2 severs and the
software development department is having total 3 servers installed the subnet of the network. In
this case some more numbers of IP addresses are kept in the reservation to support expansion
process of the organization that will help more employees to connect to each of the subnet which
are installed in the department of the organization.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4DATA COMMUNICATION AND NETWORK
2. Organizational Description:
The uSoft.com organization currently having two branches and both of them are located in
the region of Gold Coast. The organization aims for further expansion and for that they must
redesign the current network topology. The HQ of the organization consists total 6 departments
each of the department is separate floors. The organization is planning to allocate two floors to the
solution design department and due to that network of the organization must be redesigned.
3. Analysis of the user requirements:
The requirement of the user must be analysed in a proper way for developing a solution.
Hence, user requirement is analysed in this case on the basis of security, mobility, application,
remote access and bandwidth.
3.1 Mobility Requirement:
Mobility is required for the employees of the organization and for that wireless access points
should be installed in the organization so that peoples can connect wireless devices of them. The
servers which are installed in the organization must be reconfigured as RADUIS sever. Through this
server users will be able to access the organizational network from remote location. This will
increase productivity and efficiency of the employees of the organization.
3.2 Security requirement:
As per the security requirement the wireless access points must be secured from the
external agents. For securing this access point, different subnets can be created for every
department of the organization and encryption algorithm can be used. The routers of the
organization must be configured with an access control list which will secure the sensitive
information of the organization internally.
3.3 Bandwidth Requirement:
In this case initially required bandwidth for using various of application must be calculated.
As it need to be ensured every subnet of the organisation is having sufficient bandwidth, interface
must be divided and an efficient plan for cabling should be executed for interconnecting the network
devices.
3.4 Application Requirement:
The department of the solution design often need to run various of web development
software and tools for interface design purpose. In such of cases a proper efficient antivirus software
must be installed in the all of the host to avoid the spyware risks, virus risks and malware risks which
can negatively affect the network performance.
3.5 Remote access requirement:
The existing server of the organization need to be reconfigured with RADUIS protocol which
will help the employees of the organization to get access to organizational network independent of
geographic location. In such a way the productivity of the employees will be increased and the
organization will gain competitive advantage.
3.6. Performance Requirement
The network developed for the organization should be available to the users 24 *7 and the
destination address of the network can be reached via different paths. The network should provide
wireless access to the users connected in the network such that the BYOD policy of the organization
is fulfilled. The speed of the network should not get down if there is a sudden increase in the
number of users per subnet.
2. Organizational Description:
The uSoft.com organization currently having two branches and both of them are located in
the region of Gold Coast. The organization aims for further expansion and for that they must
redesign the current network topology. The HQ of the organization consists total 6 departments
each of the department is separate floors. The organization is planning to allocate two floors to the
solution design department and due to that network of the organization must be redesigned.
3. Analysis of the user requirements:
The requirement of the user must be analysed in a proper way for developing a solution.
Hence, user requirement is analysed in this case on the basis of security, mobility, application,
remote access and bandwidth.
3.1 Mobility Requirement:
Mobility is required for the employees of the organization and for that wireless access points
should be installed in the organization so that peoples can connect wireless devices of them. The
servers which are installed in the organization must be reconfigured as RADUIS sever. Through this
server users will be able to access the organizational network from remote location. This will
increase productivity and efficiency of the employees of the organization.
3.2 Security requirement:
As per the security requirement the wireless access points must be secured from the
external agents. For securing this access point, different subnets can be created for every
department of the organization and encryption algorithm can be used. The routers of the
organization must be configured with an access control list which will secure the sensitive
information of the organization internally.
3.3 Bandwidth Requirement:
In this case initially required bandwidth for using various of application must be calculated.
As it need to be ensured every subnet of the organisation is having sufficient bandwidth, interface
must be divided and an efficient plan for cabling should be executed for interconnecting the network
devices.
3.4 Application Requirement:
The department of the solution design often need to run various of web development
software and tools for interface design purpose. In such of cases a proper efficient antivirus software
must be installed in the all of the host to avoid the spyware risks, virus risks and malware risks which
can negatively affect the network performance.
3.5 Remote access requirement:
The existing server of the organization need to be reconfigured with RADUIS protocol which
will help the employees of the organization to get access to organizational network independent of
geographic location. In such a way the productivity of the employees will be increased and the
organization will gain competitive advantage.
3.6. Performance Requirement
The network developed for the organization should be available to the users 24 *7 and the
destination address of the network can be reached via different paths. The network should provide
wireless access to the users connected in the network such that the BYOD policy of the organization
is fulfilled. The speed of the network should not get down if there is a sudden increase in the
number of users per subnet.
5DATA COMMUNICATION AND NETWORK
3.7. Quality of Service (QoS) Requirement
The network developed for the organization should not have delay, jitter, packet loss and
specific measures should be taken for increasing the accuracy and eliminate the rate of error in the
network. The QoS for each of the application should be listed for management of different types of
traffic and examination of the capability of the current technology supporting the QoS metrics.
3.8. VoIP Service Requirement
There are different factors that helps in increasing the reliability of VoIP such as a reliable
internet connection and traffic filtering. The type of service required should be identified and the
quality should never be compromised since it can cause call drop and voice delay making the
network unusable.
4. Logical Design:
4.1 Security:
For the security purposes the network of the organization must be secured from external
threats and for that a DMZ zone need to be configured that will assist to install core network devices
and will limit the access of the users which will increase the security. Firewall need to be deployed in
this network which will manage the incoming and outgoing packets of the data and will enable
access control of users. A VPN also must be configured that will eliminate man in the middle attack.
4.2 Wireless Network:
A separate type of access point must be implemented for each of the department of the
organization. Also, it must be ensured that the wireless access points are installed in such a way that
it does not faces any type of obstruction. Also an efficient encryption must be implemented for
improving network security.
4.3 Virtual LANs:
It is very much important for the organization to ensure that any congestion is not present in
the current network. To ensure that a virtual LAN need to be implemented. The virtual LAN will also
ensure that the less number of data packets are broadcasted. Network management complexity is
also reduced by the implementation of the VLAN. The VLAN will also enforce the security policy of
the uSoft.com for different department of the organization.
5. IP Address Allocation Plan:
The HQ of the uSoft.com organization is using 172.16.123.0/22 IP address designing IP
address plan for the network solution configuration.
Subnet
Name
Neede
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Software
Developme
nt Data
102 172.16.120.12
8
/25 255.255.255.1
28
172.16.120.12
9 -
172.16.120.25
4
172.16.120.25
5
Software
Developme
nt Voice
102 172.16.120.0 /25 255.255.255.1
28
172.16.120.1 -
172.16.120.12
6
172.16.120.12
7
Software
Developme
nt Server
3 172.16.123.19
2
/29 255.255.255.2
48
172.16.123.19
3 -
172.16.123.19
8
172.16.123.19
9
Solution 92 172.16.121.12 /25 255.255.255.1 172.16.121.12 172.16.121.25
3.7. Quality of Service (QoS) Requirement
The network developed for the organization should not have delay, jitter, packet loss and
specific measures should be taken for increasing the accuracy and eliminate the rate of error in the
network. The QoS for each of the application should be listed for management of different types of
traffic and examination of the capability of the current technology supporting the QoS metrics.
3.8. VoIP Service Requirement
There are different factors that helps in increasing the reliability of VoIP such as a reliable
internet connection and traffic filtering. The type of service required should be identified and the
quality should never be compromised since it can cause call drop and voice delay making the
network unusable.
4. Logical Design:
4.1 Security:
For the security purposes the network of the organization must be secured from external
threats and for that a DMZ zone need to be configured that will assist to install core network devices
and will limit the access of the users which will increase the security. Firewall need to be deployed in
this network which will manage the incoming and outgoing packets of the data and will enable
access control of users. A VPN also must be configured that will eliminate man in the middle attack.
4.2 Wireless Network:
A separate type of access point must be implemented for each of the department of the
organization. Also, it must be ensured that the wireless access points are installed in such a way that
it does not faces any type of obstruction. Also an efficient encryption must be implemented for
improving network security.
4.3 Virtual LANs:
It is very much important for the organization to ensure that any congestion is not present in
the current network. To ensure that a virtual LAN need to be implemented. The virtual LAN will also
ensure that the less number of data packets are broadcasted. Network management complexity is
also reduced by the implementation of the VLAN. The VLAN will also enforce the security policy of
the uSoft.com for different department of the organization.
5. IP Address Allocation Plan:
The HQ of the uSoft.com organization is using 172.16.123.0/22 IP address designing IP
address plan for the network solution configuration.
Subnet
Name
Neede
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Software
Developme
nt Data
102 172.16.120.12
8
/25 255.255.255.1
28
172.16.120.12
9 -
172.16.120.25
4
172.16.120.25
5
Software
Developme
nt Voice
102 172.16.120.0 /25 255.255.255.1
28
172.16.120.1 -
172.16.120.12
6
172.16.120.12
7
Software
Developme
nt Server
3 172.16.123.19
2
/29 255.255.255.2
48
172.16.123.19
3 -
172.16.123.19
8
172.16.123.19
9
Solution 92 172.16.121.12 /25 255.255.255.1 172.16.121.12 172.16.121.25
6DATA COMMUNICATION AND NETWORK
Design Data 8 28 9 -
172.16.121.25
4
5
Solution
Design
Voice
92 172.16.121.0 /25 255.255.255.1
28
172.16.121.1 -
172.16.121.12
6
172.16.121.12
7
Solution
Design
Server
2 172.16.123.20
0
/30 255.255.255.2
52
172.16.123.20
1 -
172.16.123.20
2
172.16.123.20
3
Customer
Support
Data
62 172.16.122.64 /26 255.255.255.1
92
172.16.122.65
-
172.16.122.12
6
172.16.122.12
7
Customer
Support
Voice
62 172.16.122.0 /26 255.255.255.1
92
172.16.122.1 -
172.16.122.62
172.16.122.63
Customer
Support
Server
1 172.16.123.20
4
/30 255.255.255.2
52
172.16.123.20
5 -
172.16.123.20
6
172.16.123.20
7
Sales Data 52 172.16.122.19
2
/26 255.255.255.1
92
172.16.122.19
3 -
172.16.122.25
4
172.16.122.25
5
Sales Voice 52 172.16.122.12
8
/26 255.255.255.1
92
172.16.122.12
9 -
172.16.122.19
0
172.16.122.19
1
Sales Server 1 172.16.123.21
6
/30 255.255.255.2
52
172.16.123.21
7 -
172.16.123.21
8
172.16.123.21
9
Finance
Data
32 172.16.123.64 /26 255.255.255.1
92
172.16.123.65
-
172.16.123.12
6
172.16.123.12
7
Finance
Voice
32 172.16.123.0 /26 255.255.255.1
92
172.16.123.1 -
172.16.123.62
172.16.123.63
Finance
Server
1 172.16.123.20
8
/30 255.255.255.2
52
172.16.123.20
9 -
172.16.123.21
0
172.16.123.21
1
Human
Resource
Data
22 172.16.123.16
0
/27 255.255.255.2
24
172.16.123.16
1 -
172.16.123.19
0
172.16.123.19
1
Human
Resource
22 172.16.123.12
8
/27 255.255.255.2
24
172.16.123.12
9 -
172.16.123.15
Design Data 8 28 9 -
172.16.121.25
4
5
Solution
Design
Voice
92 172.16.121.0 /25 255.255.255.1
28
172.16.121.1 -
172.16.121.12
6
172.16.121.12
7
Solution
Design
Server
2 172.16.123.20
0
/30 255.255.255.2
52
172.16.123.20
1 -
172.16.123.20
2
172.16.123.20
3
Customer
Support
Data
62 172.16.122.64 /26 255.255.255.1
92
172.16.122.65
-
172.16.122.12
6
172.16.122.12
7
Customer
Support
Voice
62 172.16.122.0 /26 255.255.255.1
92
172.16.122.1 -
172.16.122.62
172.16.122.63
Customer
Support
Server
1 172.16.123.20
4
/30 255.255.255.2
52
172.16.123.20
5 -
172.16.123.20
6
172.16.123.20
7
Sales Data 52 172.16.122.19
2
/26 255.255.255.1
92
172.16.122.19
3 -
172.16.122.25
4
172.16.122.25
5
Sales Voice 52 172.16.122.12
8
/26 255.255.255.1
92
172.16.122.12
9 -
172.16.122.19
0
172.16.122.19
1
Sales Server 1 172.16.123.21
6
/30 255.255.255.2
52
172.16.123.21
7 -
172.16.123.21
8
172.16.123.21
9
Finance
Data
32 172.16.123.64 /26 255.255.255.1
92
172.16.123.65
-
172.16.123.12
6
172.16.123.12
7
Finance
Voice
32 172.16.123.0 /26 255.255.255.1
92
172.16.123.1 -
172.16.123.62
172.16.123.63
Finance
Server
1 172.16.123.20
8
/30 255.255.255.2
52
172.16.123.20
9 -
172.16.123.21
0
172.16.123.21
1
Human
Resource
Data
22 172.16.123.16
0
/27 255.255.255.2
24
172.16.123.16
1 -
172.16.123.19
0
172.16.123.19
1
Human
Resource
22 172.16.123.12
8
/27 255.255.255.2
24
172.16.123.12
9 -
172.16.123.15
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7DATA COMMUNICATION AND NETWORK
Voice 172.16.123.15
8
9
Human
Resource
Server
1 172.16.123.21
2
/30 255.255.255.2
52
172.16.123.21
3 -
172.16.123.21
4
172.16.123.21
5
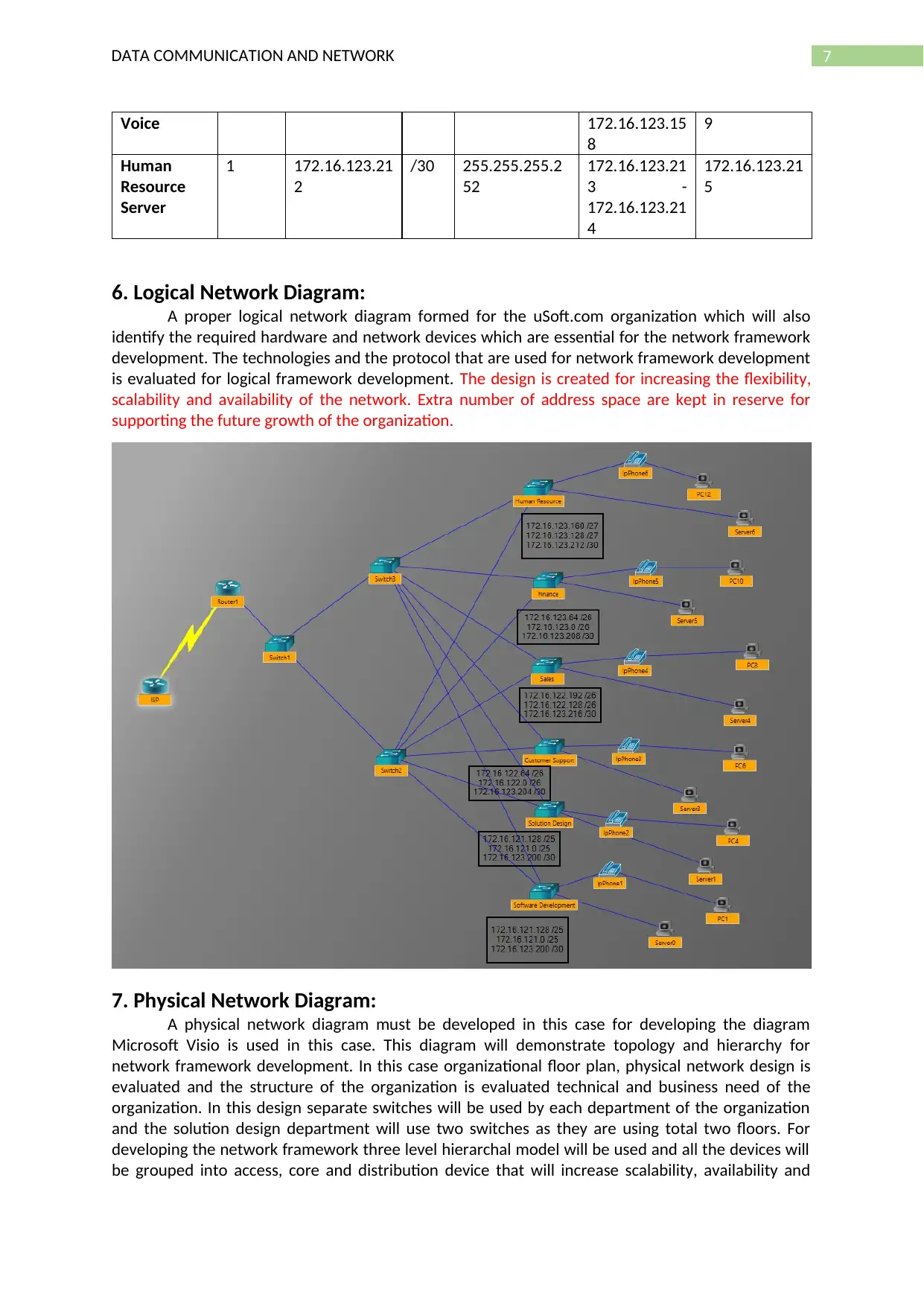
6. Logical Network Diagram:
A proper logical network diagram formed for the uSoft.com organization which will also
identify the required hardware and network devices which are essential for the network framework
development. The technologies and the protocol that are used for network framework development
is evaluated for logical framework development. The design is created for increasing the flexibility,
scalability and availability of the network. Extra number of address space are kept in reserve for
supporting the future growth of the organization.
7. Physical Network Diagram:
A physical network diagram must be developed in this case for developing the diagram
Microsoft Visio is used in this case. This diagram will demonstrate topology and hierarchy for
network framework development. In this case organizational floor plan, physical network design is
evaluated and the structure of the organization is evaluated technical and business need of the
organization. In this design separate switches will be used by each department of the organization
and the solution design department will use two switches as they are using total two floors. For
developing the network framework three level hierarchal model will be used and all the devices will
be grouped into access, core and distribution device that will increase scalability, availability and
Voice 172.16.123.15
8
9
Human
Resource
Server
1 172.16.123.21
2
/30 255.255.255.2
52
172.16.123.21
3 -
172.16.123.21
4
172.16.123.21
5
6. Logical Network Diagram:
A proper logical network diagram formed for the uSoft.com organization which will also
identify the required hardware and network devices which are essential for the network framework
development. The technologies and the protocol that are used for network framework development
is evaluated for logical framework development. The design is created for increasing the flexibility,
scalability and availability of the network. Extra number of address space are kept in reserve for
supporting the future growth of the organization.
7. Physical Network Diagram:
A physical network diagram must be developed in this case for developing the diagram
Microsoft Visio is used in this case. This diagram will demonstrate topology and hierarchy for
network framework development. In this case organizational floor plan, physical network design is
evaluated and the structure of the organization is evaluated technical and business need of the
organization. In this design separate switches will be used by each department of the organization
and the solution design department will use two switches as they are using total two floors. For
developing the network framework three level hierarchal model will be used and all the devices will
be grouped into access, core and distribution device that will increase scalability, availability and

8DATA COMMUNICATION AND NETWORK
redundancy of the network. This network design will assist in the future growth of the organization
will also minimize the management cost. Data traffic will be managed by the core router and a
firewall and a DMZ zone will be created to secure accessibility of the server for external and internal
user of the organisation.
8. Conclusion:
Form the above discussion it can be concluded that a new network framework is needed by
the uSoft.com organisation. Various of technologies are need to be considered in this case for
developing the assessed network. This network is designed to bring improvements in the
communication between various department of the organization. A subnet plan is developed in this
report and for that the total number of employees need to be determined in this case which has
been done properly. The above discussion also suggested that the VLAN is created for each of the
each present subnet of the organization according to the department of the organization. The
implementation of VLAN and VoIP will increase the network security. From the discussion it has been
determined that the voice chinned must be separated so that there no lag or call drop in the
organization. Accessibility of the network should be managed and users must be categorised as per
the service requirement of them and that will improve the network flexibility. This network solution
consists multiple of paths and has a remote access to different of parts of the organization. Also the
network must limit the access of the internal and external users.
redundancy of the network. This network design will assist in the future growth of the organization
will also minimize the management cost. Data traffic will be managed by the core router and a
firewall and a DMZ zone will be created to secure accessibility of the server for external and internal
user of the organisation.
8. Conclusion:
Form the above discussion it can be concluded that a new network framework is needed by
the uSoft.com organisation. Various of technologies are need to be considered in this case for
developing the assessed network. This network is designed to bring improvements in the
communication between various department of the organization. A subnet plan is developed in this
report and for that the total number of employees need to be determined in this case which has
been done properly. The above discussion also suggested that the VLAN is created for each of the
each present subnet of the organization according to the department of the organization. The
implementation of VLAN and VoIP will increase the network security. From the discussion it has been
determined that the voice chinned must be separated so that there no lag or call drop in the
organization. Accessibility of the network should be managed and users must be categorised as per
the service requirement of them and that will improve the network flexibility. This network solution
consists multiple of paths and has a remote access to different of parts of the organization. Also the
network must limit the access of the internal and external users.

9DATA COMMUNICATION AND NETWORK
9. Bibliography:
Da Cunha, F.D., Boukerche, A., Villas, L., Viana, A.C. and Loureiro, A.A., 2014. Data communication in
VANETs: a survey, challenges and applications (Doctoral dissertation, INRIA Saclay; INRIA).
Dong, X., Lin, H., Tan, R., Iyer, R.K. and Kalbarczyk, Z., 2015, April. Software-defined networking for
smart grid resilience: Opportunities and challenges. In Proceedings of the 1st ACM Workshop on
Cyber-Physical System Security (pp. 61-68). ACM.
Ghali, C., Tsudik, G. and Uzun, E., 2014. Network-layer trust in named-data networking. ACM
SIGCOMM Computer Communication Review, 44(5), pp.12-19.
Grassi, G., Pesavento, D., Pau, G., Vuyyuru, R., Wakikawa, R. and Zhang, L., 2014, April. VANET via
named data networking. In Computer Communications Workshops (INFOCOM WKSHPS), 2014 IEEE
Conference on (pp. 410-415). IEEE.
Haas, H., 2013. High-speed wireless networking using visible light. SPIE Newsroom, 10(2.1201304),
p.004773.
Jawhar, I., Mohamed, N., Al-Jaroodi, J., Agrawal, D.P. and Zhang, S., 2017. Communication and
networking of UAV-based systems: Classification and associated architectures. Journal of Network
and Computer Applications, 84, pp.93-108.
Katsaros, K., Chai, W., Wang, N., Pavlou, G., Bontius, H. and Paolone, M., 2014. Information-centric
networking for machine-to-machine data delivery: a case study in smart grid applications. IEEE
Network, 28(3), pp.58-64.
Kayastha, N., Niyato, D., Hossain, E. and Han, Z., 2014. Smart grid sensor data collection,
communication, and networking: a tutorial. Wireless communications and mobile computing, 14(11),
pp.1055-1087.
Li, J., Zhou, Y. and Lamont, L., 2013, December. Communication architectures and protocols for
networking unmanned aerial vehicles. In Globecom Workshops (GC Wkshps), 2013 IEEE (pp. 1415-
1420). IEEE.
Nunes, B.A.A., Mendonca, M., Nguyen, X.N., Obraczka, K. and Turletti, T., 2014. A survey of software-
defined networking: Past, present, and future of programmable networks. IEEE Communications
Surveys & Tutorials, 16(3), pp.1617-1634.
Puthal, D., Nepal, S., Ranjan, R. and Chen, J., 2016. Threats to networking cloud and edge
datacenters in the internet of things. IEEE Cloud Computing, 3(3), pp.64-71.
Sakano, T., Fadlullah, Z.M., Ngo, T., Nishiyama, H., Nakazawa, M., Adachi, F., Kato, N., Takahara, A.,
Kumagai, T., Kasahara, H. and Kurihara, S., 2013. Disaster-resilient networking: a new vision based on
movable and deployable resource units. IEEE Network, 27(4), pp.40-46.
Saxena, D., Raychoudhury, V., Suri, N., Becker, C. and Cao, J., 2016. Named data networking: a
survey. Computer Science Review, 19, pp.15-55.
Shang, W., Bannis, A., Liang, T., Wang, Z., Yu, Y., Afanasyev, A., Thompson, J., Burke, J., Zhang, B. and
Zhang, L., 2016, April. Named data networking of things. In Internet-of-Things Design and
Implementation (IoTDI), 2016 IEEE First International Conference on (pp. 117-128). IEEE.
Shang, W., Yu, Y., Droms, R. and Zhang, L., 2016. Challenges in IoT networking via TCP/IP
architecture. Technical Report NDN-0038. NDN Project.
9. Bibliography:
Da Cunha, F.D., Boukerche, A., Villas, L., Viana, A.C. and Loureiro, A.A., 2014. Data communication in
VANETs: a survey, challenges and applications (Doctoral dissertation, INRIA Saclay; INRIA).
Dong, X., Lin, H., Tan, R., Iyer, R.K. and Kalbarczyk, Z., 2015, April. Software-defined networking for
smart grid resilience: Opportunities and challenges. In Proceedings of the 1st ACM Workshop on
Cyber-Physical System Security (pp. 61-68). ACM.
Ghali, C., Tsudik, G. and Uzun, E., 2014. Network-layer trust in named-data networking. ACM
SIGCOMM Computer Communication Review, 44(5), pp.12-19.
Grassi, G., Pesavento, D., Pau, G., Vuyyuru, R., Wakikawa, R. and Zhang, L., 2014, April. VANET via
named data networking. In Computer Communications Workshops (INFOCOM WKSHPS), 2014 IEEE
Conference on (pp. 410-415). IEEE.
Haas, H., 2013. High-speed wireless networking using visible light. SPIE Newsroom, 10(2.1201304),
p.004773.
Jawhar, I., Mohamed, N., Al-Jaroodi, J., Agrawal, D.P. and Zhang, S., 2017. Communication and
networking of UAV-based systems: Classification and associated architectures. Journal of Network
and Computer Applications, 84, pp.93-108.
Katsaros, K., Chai, W., Wang, N., Pavlou, G., Bontius, H. and Paolone, M., 2014. Information-centric
networking for machine-to-machine data delivery: a case study in smart grid applications. IEEE
Network, 28(3), pp.58-64.
Kayastha, N., Niyato, D., Hossain, E. and Han, Z., 2014. Smart grid sensor data collection,
communication, and networking: a tutorial. Wireless communications and mobile computing, 14(11),
pp.1055-1087.
Li, J., Zhou, Y. and Lamont, L., 2013, December. Communication architectures and protocols for
networking unmanned aerial vehicles. In Globecom Workshops (GC Wkshps), 2013 IEEE (pp. 1415-
1420). IEEE.
Nunes, B.A.A., Mendonca, M., Nguyen, X.N., Obraczka, K. and Turletti, T., 2014. A survey of software-
defined networking: Past, present, and future of programmable networks. IEEE Communications
Surveys & Tutorials, 16(3), pp.1617-1634.
Puthal, D., Nepal, S., Ranjan, R. and Chen, J., 2016. Threats to networking cloud and edge
datacenters in the internet of things. IEEE Cloud Computing, 3(3), pp.64-71.
Sakano, T., Fadlullah, Z.M., Ngo, T., Nishiyama, H., Nakazawa, M., Adachi, F., Kato, N., Takahara, A.,
Kumagai, T., Kasahara, H. and Kurihara, S., 2013. Disaster-resilient networking: a new vision based on
movable and deployable resource units. IEEE Network, 27(4), pp.40-46.
Saxena, D., Raychoudhury, V., Suri, N., Becker, C. and Cao, J., 2016. Named data networking: a
survey. Computer Science Review, 19, pp.15-55.
Shang, W., Bannis, A., Liang, T., Wang, Z., Yu, Y., Afanasyev, A., Thompson, J., Burke, J., Zhang, B. and
Zhang, L., 2016, April. Named data networking of things. In Internet-of-Things Design and
Implementation (IoTDI), 2016 IEEE First International Conference on (pp. 117-128). IEEE.
Shang, W., Yu, Y., Droms, R. and Zhang, L., 2016. Challenges in IoT networking via TCP/IP
architecture. Technical Report NDN-0038. NDN Project.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10DATA COMMUNICATION AND NETWORK
Zhang, L., Afanasyev, A., Burke, J., Jacobson, V., Crowley, P., Papadopoulos, C., Wang, L. and Zhang,
B., 2014. Named data networking. ACM SIGCOMM Computer Communication Review, 44(3), pp.66-
73.
Zhao, Y., He, R., Chen, H., Zhang, J., Ji, Y., Zheng, H., Lin, Y. and Wang, X., 2014. Experimental
performance evaluation of software defined networking (SDN) based data communication networks
for large scale flexi-grid optical networks. Optics express, 22(8), pp.9538-9547.
Zhang, L., Afanasyev, A., Burke, J., Jacobson, V., Crowley, P., Papadopoulos, C., Wang, L. and Zhang,
B., 2014. Named data networking. ACM SIGCOMM Computer Communication Review, 44(3), pp.66-
73.
Zhao, Y., He, R., Chen, H., Zhang, J., Ji, Y., Zheng, H., Lin, Y. and Wang, X., 2014. Experimental
performance evaluation of software defined networking (SDN) based data communication networks
for large scale flexi-grid optical networks. Optics express, 22(8), pp.9538-9547.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





