Privacy Violation on Social Media: Factors, Ethics and Effectiveness of Policies
VerifiedAdded on 2019/09/22
|24
|8880
|98
Report
AI Summary
The study reveals that people use social media primarily for staying connected with areas/peoples of interest, expressing views and opinions, and spying on others. While some individuals use it to chat with friends or pass time, most users engage in activities that breach the privacy of others. The study also highlights the legal framework established to regulate social media use, but notes that authorities are often incompetent in resolving complaints related to privacy violation. Furthermore, the respondents express dissatisfaction with the resolution process, feeling that authorities take too long to address issues.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

An investigation on use of social media for violating privacy of others
Introduction
Overview
Project motivation
Project objectives
Objectives:
1. To find out the limits that individuals understand regarding their own privacy and other‘s privacy
while using social media.
2. To analyse the appropriateness of privacy standards for others in social media.
3. To determine the factors that influence individuals in violating privacy of others.
4. To study the ethical code of conduct or legal framework to regulate the use of social media in
violating privacy of others.
5. To investigate the effectiveness of the policies and standards in protecting the privacy of people
in context of social media.
Project scope
Literature Review
The world today is very fast moving and is extensively using the internet technology. In this current era,
the social networking has become very famous on the internet and all the people around the world use
it. The generation or the age group that use it most frequently is the young population and the
teenagers. They use this tool of social media and social networking for communicating with others and
for expressing themselves in front of others. There are many social networking sites that allow the users
to talk about each other’s common interests like they are able to share their photos, interests, job
details, and political views etc. on the websites. All the people who have access to the internet are able
to view each other’s posts and they are able to discuss with them whatever is going on in their external
environment. One of the most debated topics in today’s world is the privacy concerns that arise due to
the use of social media and the social networking. People have increased their participation in this area
dramatically. There are many researches in this area and many journals and articles have talked about
these concerns. Everyone talks about the increased privacy issues due to the use of social networking
sites and the increased number of crimes due to the use of these websites. The technology is not used
by the people in a proper way and some of them are not even aware of the privacy violations that
happen with them or they do to others on the social media. People don’t refrain themselves from
sharing private information on the websites that increases the risk to their privacy. When the people
Introduction
Overview
Project motivation
Project objectives
Objectives:
1. To find out the limits that individuals understand regarding their own privacy and other‘s privacy
while using social media.
2. To analyse the appropriateness of privacy standards for others in social media.
3. To determine the factors that influence individuals in violating privacy of others.
4. To study the ethical code of conduct or legal framework to regulate the use of social media in
violating privacy of others.
5. To investigate the effectiveness of the policies and standards in protecting the privacy of people
in context of social media.
Project scope
Literature Review
The world today is very fast moving and is extensively using the internet technology. In this current era,
the social networking has become very famous on the internet and all the people around the world use
it. The generation or the age group that use it most frequently is the young population and the
teenagers. They use this tool of social media and social networking for communicating with others and
for expressing themselves in front of others. There are many social networking sites that allow the users
to talk about each other’s common interests like they are able to share their photos, interests, job
details, and political views etc. on the websites. All the people who have access to the internet are able
to view each other’s posts and they are able to discuss with them whatever is going on in their external
environment. One of the most debated topics in today’s world is the privacy concerns that arise due to
the use of social media and the social networking. People have increased their participation in this area
dramatically. There are many researches in this area and many journals and articles have talked about
these concerns. Everyone talks about the increased privacy issues due to the use of social networking
sites and the increased number of crimes due to the use of these websites. The technology is not used
by the people in a proper way and some of them are not even aware of the privacy violations that
happen with them or they do to others on the social media. People don’t refrain themselves from
sharing private information on the websites that increases the risk to their privacy. When the people
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

share sensitive information on the social media, the concerns related to the privacy increases
automatically.
Definitions of privacy
Different people have defined privacy in different ways. There are many different types of privacy like
the personal privacy; information privacy etc. But the privacy related to the social media is the one that
is related to the information privacy. When an individual claims to control the terms under which
his/her personal information is used, disclosed or acquired, is called information privacy. The personal
information includes the information that an individual can identify. There are boundaries to privacy of
people too. One boundary is the disclosure boundary that enables a person to manage the issues
and .0tensions between the public and the private. Then another boundary is the identity boundary that
enables a person to manage the self-representation with particular audience. This means that the
behavior of people differ with different people. The way a person behaves in office may be different
from his behavior at home. The last boundary is the temporal boundary that helps a person in managing
his past actions and his expectations about the future. The behavior in this case may change with time.
The online privacy related to personal information
The protection of the personal information on social media is a big challenge in today’s world. The
website developers are also concerned about protecting the people’s privacy. There are many
researchers who have tried to find the reason behind this and they have also recommended ways to
protect the people. (Bae and Kim, 2010) have written a paper in which they have suggested that higher
levels of privacy could be achieved when the user or the concerned person is allowed to control his
settings related to privacy. Whenever any stranger is trying to contact the person, he should be able to
stop that stranger from contacting him and in the future too, the person should protect himself from
receiving any messages from that stranger. The authors of this particular paper have put emphasis on
designing a policy of privacy for the users of social media so that their personal information is
protected and the others are not able to misuse their information. The authors of the paper have also
tries to design one model for privacy using the agents of mobile.
It has been stated by (Dötzer, 2006) that if privacy is lost one time, it becomes very difficult to re-
establish that privacy and protect the personal rights in the future. Thus all kinds of communication
systems must have privacy protection installed especially the mobile systems. There are profile pages on
social media where the users practice self-representation and they interact with others and introduce
themselves. They trust the data that is placed on their profile pages like the name they show, the
pictures they share etc. the social media gives opportunity to people to share their information with
others and it also allows others to comment on the things that people share. The internet and social
media is so complex that the web privacy is automatically threatened.
The state of privacy is that condition which allows only limited access to the persons. There are some
rules and policies that the users utilize for achieving certain level of protection in their information.
There are rules made for protecting the privacy of people and they differ as per the requirements and
needs. For example, there is location privacy in which protection is given against the access to the
automatically.
Definitions of privacy
Different people have defined privacy in different ways. There are many different types of privacy like
the personal privacy; information privacy etc. But the privacy related to the social media is the one that
is related to the information privacy. When an individual claims to control the terms under which
his/her personal information is used, disclosed or acquired, is called information privacy. The personal
information includes the information that an individual can identify. There are boundaries to privacy of
people too. One boundary is the disclosure boundary that enables a person to manage the issues
and .0tensions between the public and the private. Then another boundary is the identity boundary that
enables a person to manage the self-representation with particular audience. This means that the
behavior of people differ with different people. The way a person behaves in office may be different
from his behavior at home. The last boundary is the temporal boundary that helps a person in managing
his past actions and his expectations about the future. The behavior in this case may change with time.
The online privacy related to personal information
The protection of the personal information on social media is a big challenge in today’s world. The
website developers are also concerned about protecting the people’s privacy. There are many
researchers who have tried to find the reason behind this and they have also recommended ways to
protect the people. (Bae and Kim, 2010) have written a paper in which they have suggested that higher
levels of privacy could be achieved when the user or the concerned person is allowed to control his
settings related to privacy. Whenever any stranger is trying to contact the person, he should be able to
stop that stranger from contacting him and in the future too, the person should protect himself from
receiving any messages from that stranger. The authors of this particular paper have put emphasis on
designing a policy of privacy for the users of social media so that their personal information is
protected and the others are not able to misuse their information. The authors of the paper have also
tries to design one model for privacy using the agents of mobile.
It has been stated by (Dötzer, 2006) that if privacy is lost one time, it becomes very difficult to re-
establish that privacy and protect the personal rights in the future. Thus all kinds of communication
systems must have privacy protection installed especially the mobile systems. There are profile pages on
social media where the users practice self-representation and they interact with others and introduce
themselves. They trust the data that is placed on their profile pages like the name they show, the
pictures they share etc. the social media gives opportunity to people to share their information with
others and it also allows others to comment on the things that people share. The internet and social
media is so complex that the web privacy is automatically threatened.
The state of privacy is that condition which allows only limited access to the persons. There are some
rules and policies that the users utilize for achieving certain level of protection in their information.
There are rules made for protecting the privacy of people and they differ as per the requirements and
needs. For example, there is location privacy in which protection is given against the access to the

location of the user. But if the inline privacy is considered, there is no rule or policy to restrict the
privacy breach online or on social media. There are just solutions that are being developed to protect
the privacy of people. Some of these solutions include the protective technologies, legislative support
and the social awareness. Among the protective technologies, the control is given to the access of the
information and it also demands strong authentication of the information before it can be used by
someone else. There protective technologies have been developed and they have been evolved with
time. The use of encryption is very common in these technologies and encryption helps in solving the
privacy related concerns in this. Then social awareness is used when the people are educated about the
risks of misuse of the personal information if the people give their personal information online like their
home address or their phone number. Finally, the privacy can be protected using legislation and the
agreements with the users can be clarified for protecting the personal information. Thus law or the legal
framework can be used for protecting the personal information of the people.
Online privacy risks
There are several risks surrounding the posting of personal information details on social networks.
These threats can be caused by hackers or spammers who obtain users’ personal information details.
Identity theft is one of the major risks that users face (Williams et al. 2009). Access to sensitive
information may also lead to terrorism risks, financial risks and physical or sexual extortion
(Gharibi&Shaabi 2012). Gao et al. (2011) discussed the common privacy breach attacks in online social
networks. First, users usually upload their personal information when they trust the service provider.
However, the provider can use these details for business purposes such as advertising. In addition, it is
not only the service providers who can see the users’ personal information. Some online social networks
provide users with policies to determine the list of authorized persons who can see their personal
information. These policies vary from one provider to another; some providers give users more flexibility
than others and some provide encryption for their data. The second privacy breach can be caused by the
user’s friends, who can share the user’s personal information details with others. Friends who have
access to the user’s personal information can copy and publish this information. The third breach is due
to spammers. When spammers see the user’s friend list, they can see other users’ personal information
by sending them a friend request, impersonating one of his/her friends by using the friend’s name or
picture. Lastly, breaches can be caused by third party applications installed by users. These applications
can be a threat to users, especially if they are not from a trusted provider. When the application
accesses the users’ personal information, others can obtain this information. Novak and Li (2012) also
claimed that privacy breaches can be caused by friends, applications, and exploitation of personal
information details by the service providers for advertising. The authors added that understanding
privacy settings is not enough to protect users, especially from friends and other online social network
users. Thus, social networking websites such as Facebook prioritize the development of tools to protect
privacy. This is manifested in the social network providers’ requests for new users to create new privacy
settings. However, some users do not realize the risk of leakage of personal information (Lee et al.
2011). Therefore, sensitive information such as home address and date of birth should not be published
online in order to avoid risks to online privacy. Increasing user awareness of these risks, providing a
privacy breach online or on social media. There are just solutions that are being developed to protect
the privacy of people. Some of these solutions include the protective technologies, legislative support
and the social awareness. Among the protective technologies, the control is given to the access of the
information and it also demands strong authentication of the information before it can be used by
someone else. There protective technologies have been developed and they have been evolved with
time. The use of encryption is very common in these technologies and encryption helps in solving the
privacy related concerns in this. Then social awareness is used when the people are educated about the
risks of misuse of the personal information if the people give their personal information online like their
home address or their phone number. Finally, the privacy can be protected using legislation and the
agreements with the users can be clarified for protecting the personal information. Thus law or the legal
framework can be used for protecting the personal information of the people.
Online privacy risks
There are several risks surrounding the posting of personal information details on social networks.
These threats can be caused by hackers or spammers who obtain users’ personal information details.
Identity theft is one of the major risks that users face (Williams et al. 2009). Access to sensitive
information may also lead to terrorism risks, financial risks and physical or sexual extortion
(Gharibi&Shaabi 2012). Gao et al. (2011) discussed the common privacy breach attacks in online social
networks. First, users usually upload their personal information when they trust the service provider.
However, the provider can use these details for business purposes such as advertising. In addition, it is
not only the service providers who can see the users’ personal information. Some online social networks
provide users with policies to determine the list of authorized persons who can see their personal
information. These policies vary from one provider to another; some providers give users more flexibility
than others and some provide encryption for their data. The second privacy breach can be caused by the
user’s friends, who can share the user’s personal information details with others. Friends who have
access to the user’s personal information can copy and publish this information. The third breach is due
to spammers. When spammers see the user’s friend list, they can see other users’ personal information
by sending them a friend request, impersonating one of his/her friends by using the friend’s name or
picture. Lastly, breaches can be caused by third party applications installed by users. These applications
can be a threat to users, especially if they are not from a trusted provider. When the application
accesses the users’ personal information, others can obtain this information. Novak and Li (2012) also
claimed that privacy breaches can be caused by friends, applications, and exploitation of personal
information details by the service providers for advertising. The authors added that understanding
privacy settings is not enough to protect users, especially from friends and other online social network
users. Thus, social networking websites such as Facebook prioritize the development of tools to protect
privacy. This is manifested in the social network providers’ requests for new users to create new privacy
settings. However, some users do not realize the risk of leakage of personal information (Lee et al.
2011). Therefore, sensitive information such as home address and date of birth should not be published
online in order to avoid risks to online privacy. Increasing user awareness of these risks, providing a

privacy management system for users to control their personal information details, and constantly
updating privacy policies can lead to a decline of these risks (Gharibi&Shaabi 2012).
In addition, O’Brien and Torres 2012 wrote an article named Social Networking and Online Privacy:
Facebook Users’ Perceptions. As a result, the researchers found that Facebook users are alert and
cautious when using the social networking sites. However, Facebook users are not completely informed
or aware of all activities concerning privacy on the social networking sites. Though, low trust levels to
date have not hindered activity on Facebook and membership continues to rise. Facebook users seem
willing to push aside trust issues to achieve social interaction. The importance of trust in a social
networking context is clearly questionable and perhaps different determinants for online activity exist in
different online environments. There are a number of barriers to trust in the online environment. These
barriers include perceived risk, website design and content, the user themselves and privacy concerns.
Privacy concerns are considered the greatest barrier of them all because ‘the internet, by design, lacks
unified provisions for identifying who communicates with whom; it lacks a well-designed identity
infrastructure’ (Leenes et al., 2008). Privacy concerns include online information collection techniques
such as cookie technology involving extreme surveillance. The use and analysis of data are also a
concern due to unethical merging and data mining practices to profile customers. The instant recording
and permanence of activity, loss of control and ownership of data also creates barriers to online activity
(Tavani, 2011). Social networking users claim to be concerned about risks to privacy, yet do little to
safeguard their information (Dwyer et al., 2007). Often users openly disclose detailed and personal
information on these networks, comfortable living a part of their lives online (Rosenblum, 2007).
However, Facebook has continually introduced new features and services including the Newsfeed,
Facebook Beacon, Facebook Advertisements and Facebook Platform, which subsequently lead to
changes in the privacy settings and the privacy policy (less privacy) (Fletcher, 2010). With each additional
expansion to the website has come a growing level of discontent and concern and a general feeling that
‘the company was eroding privacy and making substantial information public’ (Rothery, 2010).
Online privacy protection
Privacy settings, that allow the user to control the profile view and distribution of personal data, vary
across social networking websites, and there is no privacy standard for controlling the user’s personal
information settings. Although privacy settings should be chosen carefully, most online social network
providers have complex privacy settings (Novak & Li 2012). These complex privacy settings may cause
confusion among users (Gundecha, Barbier& Liu 2011). Different techniques have been designed to
increase personal information privacy protection. Williams et al. (2009) listed some steps for online
social network users to stay safe. These included: being aware of the risks of social networks, limiting
the posting of personal information details, and being careful when dealing with strangers online or
when reading any information from any sender. Most social networking sites have given their users
more authority to control privacy settings. Users of some social networking sites are now able to classify
their friend list into sub-lists, which allows some personal information details, such as birthday or
relationship status, to be visible to one sub-list and hidden from others. Fang et al. (2010) designed a
privacy recommendation wizard based on user inputs to help users classify their friend list into sub-lists.
The wizard gives the user two options: to allow the friends in their sub-list to see their personal
updating privacy policies can lead to a decline of these risks (Gharibi&Shaabi 2012).
In addition, O’Brien and Torres 2012 wrote an article named Social Networking and Online Privacy:
Facebook Users’ Perceptions. As a result, the researchers found that Facebook users are alert and
cautious when using the social networking sites. However, Facebook users are not completely informed
or aware of all activities concerning privacy on the social networking sites. Though, low trust levels to
date have not hindered activity on Facebook and membership continues to rise. Facebook users seem
willing to push aside trust issues to achieve social interaction. The importance of trust in a social
networking context is clearly questionable and perhaps different determinants for online activity exist in
different online environments. There are a number of barriers to trust in the online environment. These
barriers include perceived risk, website design and content, the user themselves and privacy concerns.
Privacy concerns are considered the greatest barrier of them all because ‘the internet, by design, lacks
unified provisions for identifying who communicates with whom; it lacks a well-designed identity
infrastructure’ (Leenes et al., 2008). Privacy concerns include online information collection techniques
such as cookie technology involving extreme surveillance. The use and analysis of data are also a
concern due to unethical merging and data mining practices to profile customers. The instant recording
and permanence of activity, loss of control and ownership of data also creates barriers to online activity
(Tavani, 2011). Social networking users claim to be concerned about risks to privacy, yet do little to
safeguard their information (Dwyer et al., 2007). Often users openly disclose detailed and personal
information on these networks, comfortable living a part of their lives online (Rosenblum, 2007).
However, Facebook has continually introduced new features and services including the Newsfeed,
Facebook Beacon, Facebook Advertisements and Facebook Platform, which subsequently lead to
changes in the privacy settings and the privacy policy (less privacy) (Fletcher, 2010). With each additional
expansion to the website has come a growing level of discontent and concern and a general feeling that
‘the company was eroding privacy and making substantial information public’ (Rothery, 2010).
Online privacy protection
Privacy settings, that allow the user to control the profile view and distribution of personal data, vary
across social networking websites, and there is no privacy standard for controlling the user’s personal
information settings. Although privacy settings should be chosen carefully, most online social network
providers have complex privacy settings (Novak & Li 2012). These complex privacy settings may cause
confusion among users (Gundecha, Barbier& Liu 2011). Different techniques have been designed to
increase personal information privacy protection. Williams et al. (2009) listed some steps for online
social network users to stay safe. These included: being aware of the risks of social networks, limiting
the posting of personal information details, and being careful when dealing with strangers online or
when reading any information from any sender. Most social networking sites have given their users
more authority to control privacy settings. Users of some social networking sites are now able to classify
their friend list into sub-lists, which allows some personal information details, such as birthday or
relationship status, to be visible to one sub-list and hidden from others. Fang et al. (2010) designed a
privacy recommendation wizard based on user inputs to help users classify their friend list into sub-lists.
The wizard gives the user two options: to allow the friends in their sub-list to see their personal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

information, or to deny them access to this information. Configuring privacy settings so that only friends
can see your posts is not enough to defend oneself from other attacks such as applications and
advertisements (Stutzman& Kramer-Duffield 2010). Lipford, Besmer and Watson (2008) found that
showing an example of privacy settings International Journal of Security, Privacy and Trust Management
( IJSPPRIVACY) vol 2, No 2, April 2013 6 will enable users to understand their privacy settings better. It
will also help them find out who can see their personal information. For instance, Facebook allows users
to see their profiles from their friends’ point of view; this allows users to see what personal information
their friends can see. This technique helps users understand privacy settings but does not provide
security to protect them from neighbourhood attacks or other types of attacks such as viruses or spam.
Fang and Lefevre (2010) designed a privacy wizard system to make it easier for users to control their
privacy settings. It was designed based on friends classification to groups and asking questions. It guides
users in choosing privacy settings for group or individual users by allowing the users to see or hide an
item. For example, if Alice is Bob’s friend, then Bob can identify which items of his profile Alice can see.
Bob can hide some details such as his date of birth and mobile number from Alice, and can do the same
for his other friends.
There has been some previous work attempting to apply nudging to computer security. For instance,
Brustoloni et al. developed security dialogs in which users were held accountable for their decisions to
open email attachments. Those who took unjustified risks could be “subject to a variety of sanctions,
such as being unable to use the application for increasing periods of time...” A user study found that
these dialogs resulted in significantly fewer unjustified risks [35]. An approach similar to nudging can be
found in persuasive computing, a sub-field of computer science concerned with systems intentionally
designed to “change a person’s attitude or behavior in a predetermined way” [37]. Persuasive
technologies have been applied in specific domains including computer security. For instance, Forget et
al. built a text password system that encourages users to create stronger text password [38]. A number
of mechanisms have been proposed to help users better protect their privacy in social media. Fang et al.
designed a privacy wizard that asks users to iterate over privacy settings for some of their friends. Based
on this information, a classifier could be built automatically to categorize the remaining friends [36].
Lipford et al. investigated interfaces for social network privacy controls, comparing compact settings in
the form of expandable grids to visual policies. They found that both alternatives were usable, but
different users appreciated them for different reasons [40]. While most previous work on privacy
protections for social media has focused on helping users adjust their settings up front, our work
employs tools that encourage real-time adjusprivacyents during or immediately following the
composition of a Facebook post.
can see your posts is not enough to defend oneself from other attacks such as applications and
advertisements (Stutzman& Kramer-Duffield 2010). Lipford, Besmer and Watson (2008) found that
showing an example of privacy settings International Journal of Security, Privacy and Trust Management
( IJSPPRIVACY) vol 2, No 2, April 2013 6 will enable users to understand their privacy settings better. It
will also help them find out who can see their personal information. For instance, Facebook allows users
to see their profiles from their friends’ point of view; this allows users to see what personal information
their friends can see. This technique helps users understand privacy settings but does not provide
security to protect them from neighbourhood attacks or other types of attacks such as viruses or spam.
Fang and Lefevre (2010) designed a privacy wizard system to make it easier for users to control their
privacy settings. It was designed based on friends classification to groups and asking questions. It guides
users in choosing privacy settings for group or individual users by allowing the users to see or hide an
item. For example, if Alice is Bob’s friend, then Bob can identify which items of his profile Alice can see.
Bob can hide some details such as his date of birth and mobile number from Alice, and can do the same
for his other friends.
There has been some previous work attempting to apply nudging to computer security. For instance,
Brustoloni et al. developed security dialogs in which users were held accountable for their decisions to
open email attachments. Those who took unjustified risks could be “subject to a variety of sanctions,
such as being unable to use the application for increasing periods of time...” A user study found that
these dialogs resulted in significantly fewer unjustified risks [35]. An approach similar to nudging can be
found in persuasive computing, a sub-field of computer science concerned with systems intentionally
designed to “change a person’s attitude or behavior in a predetermined way” [37]. Persuasive
technologies have been applied in specific domains including computer security. For instance, Forget et
al. built a text password system that encourages users to create stronger text password [38]. A number
of mechanisms have been proposed to help users better protect their privacy in social media. Fang et al.
designed a privacy wizard that asks users to iterate over privacy settings for some of their friends. Based
on this information, a classifier could be built automatically to categorize the remaining friends [36].
Lipford et al. investigated interfaces for social network privacy controls, comparing compact settings in
the form of expandable grids to visual policies. They found that both alternatives were usable, but
different users appreciated them for different reasons [40]. While most previous work on privacy
protections for social media has focused on helping users adjust their settings up front, our work
employs tools that encourage real-time adjusprivacyents during or immediately following the
composition of a Facebook post.

Research Methodology
Research Methods and Framework- quantitative and qualitative
Data generation methods- observation, questionnaires, documents, interviews
Data analysis
Research Analysis and Findings
Findings from quantitative sources
Why do you use social media?
To stay connected
with friends To stay connected
with areas/people of
interests like
celebrities, film
industry, political
industry etc.
To express my views,
opinions, thoughts,
knowledge about
some current issue
To spy in the lives of
others For passing time
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
10%
30% 30%
25%
5%
It is found in the research that the main reasons due to which people use social media are: 30% people
use it for staying connected with areas/people of interests like celebrities, film industry, and political
industry etc. and 30% people use it for expressing their views, opinions, thoughts, knowledge about
some current issue. Apart from this, there are 25% of the respondents who use social media for spying
Research Methods and Framework- quantitative and qualitative
Data generation methods- observation, questionnaires, documents, interviews
Data analysis
Research Analysis and Findings
Findings from quantitative sources
Why do you use social media?
To stay connected
with friends To stay connected
with areas/people of
interests like
celebrities, film
industry, political
industry etc.
To express my views,
opinions, thoughts,
knowledge about
some current issue
To spy in the lives of
others For passing time
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
10%
30% 30%
25%
5%
It is found in the research that the main reasons due to which people use social media are: 30% people
use it for staying connected with areas/people of interests like celebrities, film industry, and political
industry etc. and 30% people use it for expressing their views, opinions, thoughts, knowledge about
some current issue. Apart from this, there are 25% of the respondents who use social media for spying

in the lives of others, 10% use it for staying connected with their friends and only 5% use it for passing
their time.
How often people use the social media platform for posting something or for commenting on someone?
Everyday Many times in
a week Occasionally Very rarely Never
0%
10%
20%
30%
40%
50%
60%
33%
50%
10%
5% 2%
It is found in the research that 50% of the respondents in the study use the social media platform for
posting something or for commenting on someone many times in a week. 33% of the respondents in the
study use the social media platform for posting something or for commenting on someone every day.
Only 10% of the people under the study use it occasionally, 5% says that they use it very rarely and 2%
of them never use the social media platform for posting something or for commenting on someone.
Are you aware of the privacy settings of your social media accounts and its use?
their time.
How often people use the social media platform for posting something or for commenting on someone?
Everyday Many times in
a week Occasionally Very rarely Never
0%
10%
20%
30%
40%
50%
60%
33%
50%
10%
5% 2%
It is found in the research that 50% of the respondents in the study use the social media platform for
posting something or for commenting on someone many times in a week. 33% of the respondents in the
study use the social media platform for posting something or for commenting on someone every day.
Only 10% of the people under the study use it occasionally, 5% says that they use it very rarely and 2%
of them never use the social media platform for posting something or for commenting on someone.
Are you aware of the privacy settings of your social media accounts and its use?
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Yes No Not very sure
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
45%
25%
30%
It is found in the research that most of the people i.e. 45% of them are aware of the privacy settings of
their social media accounts and its use. 30% of them are not very sure about the privacy settings i.e.
they are not sure whether they are aware of the privacy settings of their social media accounts and its
use or not. 25% of the respondents are not at all aware of the privacy settings of their social media
accounts and its use.
Do you use the privacy settings in controlling and monitoring the posts you share or the people you
follow?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
30%
20%
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
45%
25%
30%
It is found in the research that most of the people i.e. 45% of them are aware of the privacy settings of
their social media accounts and its use. 30% of them are not very sure about the privacy settings i.e.
they are not sure whether they are aware of the privacy settings of their social media accounts and its
use or not. 25% of the respondents are not at all aware of the privacy settings of their social media
accounts and its use.
Do you use the privacy settings in controlling and monitoring the posts you share or the people you
follow?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
30%
20%

It is found that 50% of the people use privacy settings in controlling and monitoring the posts that they
share or the people they follow. 30% of the people do not use privacy settings in controlling and
monitoring the posts that they share or the people they follow. Only 20% of the people sometimes use
privacy settings in controlling and monitoring the posts that they share or the people they follow.
In what ways do you control the privacy related settings of your social media accounts?
0
0.1
0.2
0.3
0.4 40%
10%
20%
30%
It is found in the study that 40% of the people control the privacy related settings of their social media
accounts by adjusting the settings for controlling the other people’s access on their account and on the
things that they post or publish. 30% of the people just know how to control the privacy settings of their
social media accounts. 20% of them are not aware about the procedure to control the privacy settings of
their social media accounts. Only 10% of the people are aware about the privacy settings but they don’t
bother about controlling them.
When you use your social media accounts like the Facebook account or the Twitter account, do you
make your posts visible to all the users of internet?
share or the people they follow. 30% of the people do not use privacy settings in controlling and
monitoring the posts that they share or the people they follow. Only 20% of the people sometimes use
privacy settings in controlling and monitoring the posts that they share or the people they follow.
In what ways do you control the privacy related settings of your social media accounts?
0
0.1
0.2
0.3
0.4 40%
10%
20%
30%
It is found in the study that 40% of the people control the privacy related settings of their social media
accounts by adjusting the settings for controlling the other people’s access on their account and on the
things that they post or publish. 30% of the people just know how to control the privacy settings of their
social media accounts. 20% of them are not aware about the procedure to control the privacy settings of
their social media accounts. Only 10% of the people are aware about the privacy settings but they don’t
bother about controlling them.
When you use your social media accounts like the Facebook account or the Twitter account, do you
make your posts visible to all the users of internet?

Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
15%
35%
It is found that when people use their social media accounts like the Facebook account or the Twitter
account, 50% of them make their posts visible to all the users of internet, 35% of them sometimes make
their posts visible to all the users of internet and 15% of them does not make their posts visible to all the
users of internet.
Do you take permission of your friends, followers or anybody (about whom you share something or talk
something) before presenting them on social media?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
70%
5%
60%
35%
It is found that 60% of the people do not take permission of their friends, followers or anybody (about
whom they share something or talk something) before presenting them on social media. 35% of the
people sometimes take permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media and only 5% of them take
0%
10%
20%
30%
40%
50%
60%
50%
15%
35%
It is found that when people use their social media accounts like the Facebook account or the Twitter
account, 50% of them make their posts visible to all the users of internet, 35% of them sometimes make
their posts visible to all the users of internet and 15% of them does not make their posts visible to all the
users of internet.
Do you take permission of your friends, followers or anybody (about whom you share something or talk
something) before presenting them on social media?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
70%
5%
60%
35%
It is found that 60% of the people do not take permission of their friends, followers or anybody (about
whom they share something or talk something) before presenting them on social media. 35% of the
people sometimes take permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media and only 5% of them take
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

permission of their friends, followers or anybody (about whom they share something or talk something)
before presenting them on social media.
Do you think that you should take permission of your friends, followers or anybody (about whom you
share something or talk something) before presenting them on social media?
Yes No
0%
10%
20%
30%
40%
50%
60%
70%
40%
60%
It is found that 60% of the people do not feel the need to take permission of their friends, followers or
anybody (about whom they share something or talk something) before presenting them on social
media. But 40% of the people feel that they should take permission of their friends, followers or
anybody (about whom they share something or talk something) before presenting them on social
media.
When your friend/follower shares something about you or anybody else on the social media, do you or
that person has the ability to control it?
before presenting them on social media.
Do you think that you should take permission of your friends, followers or anybody (about whom you
share something or talk something) before presenting them on social media?
Yes No
0%
10%
20%
30%
40%
50%
60%
70%
40%
60%
It is found that 60% of the people do not feel the need to take permission of their friends, followers or
anybody (about whom they share something or talk something) before presenting them on social
media. But 40% of the people feel that they should take permission of their friends, followers or
anybody (about whom they share something or talk something) before presenting them on social
media.
When your friend/follower shares something about you or anybody else on the social media, do you or
that person has the ability to control it?

Yes No To an extent
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
30% 30%
40%
40% of the respondents say that when their friend/follower shares something about them or anybody
else on the social media, to an extent they ability to control it. 30% say that they have the ability to
control it and 30% say that they don’t have the ability to control it.
When your friend/follower shares something about you or anybody else on the social media, do you or
that person has the right to limit that post or report it or mark it as spam?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
20%
30%
It is found in the study that 50% of the people feel that they have the right to limit the post or report it
or mark it as spam when their friend/follower shares something about them or anybody else on the
social media. 30% of the people feel that they sometimes have the right to limit the post or report it or
mark it as spam when their friend/follower shares something about them or anybody else on the social
media. Only 20% of the respondents’ people feel that they do not have the right to limit the post or
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
30% 30%
40%
40% of the respondents say that when their friend/follower shares something about them or anybody
else on the social media, to an extent they ability to control it. 30% say that they have the ability to
control it and 30% say that they don’t have the ability to control it.
When your friend/follower shares something about you or anybody else on the social media, do you or
that person has the right to limit that post or report it or mark it as spam?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
20%
30%
It is found in the study that 50% of the people feel that they have the right to limit the post or report it
or mark it as spam when their friend/follower shares something about them or anybody else on the
social media. 30% of the people feel that they sometimes have the right to limit the post or report it or
mark it as spam when their friend/follower shares something about them or anybody else on the social
media. Only 20% of the respondents’ people feel that they do not have the right to limit the post or
report it or mark it as spam when their friend/follower shares something about them or anybody else on
the social media.
When your friend/follower shares something about you or anybody else on the social media, do you or
that person has the option to block that friend/follower?
Yes No
0%
10%
20%
30%
40%
50%
60%
70%
80%
90%
100%
90%
10%
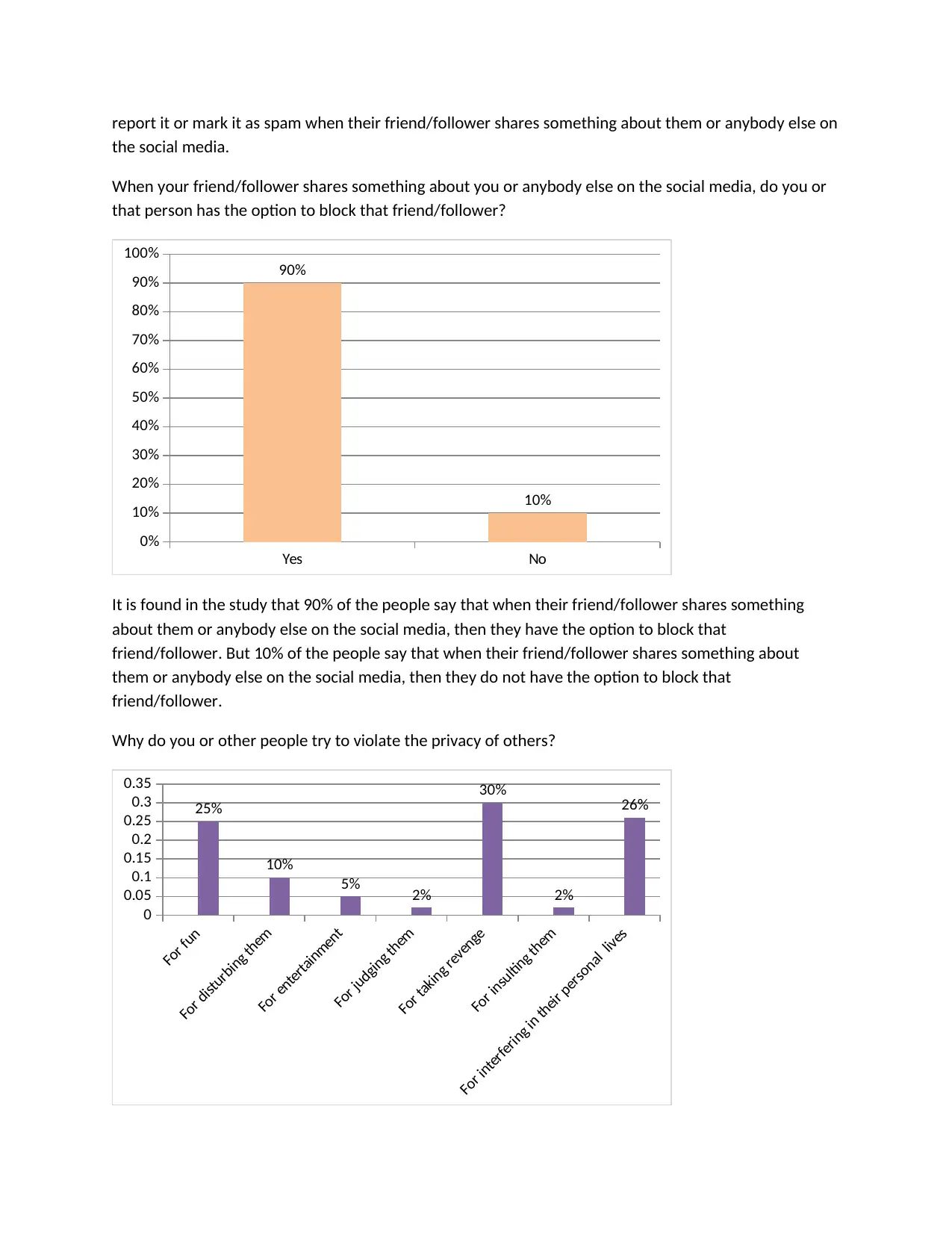
It is found in the study that 90% of the people say that when their friend/follower shares something
about them or anybody else on the social media, then they have the option to block that
friend/follower. But 10% of the people say that when their friend/follower shares something about
them or anybody else on the social media, then they do not have the option to block that
friend/follower.
Why do you or other people try to violate the privacy of others?
For fun
For disturbing them
For entertainment
For judging them
For taking revenge
For insulting them
For interfering in their personal lives
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
25%
10%
5% 2%
30%
2%
26%
the social media.
When your friend/follower shares something about you or anybody else on the social media, do you or
that person has the option to block that friend/follower?
Yes No
0%
10%
20%
30%
40%
50%
60%
70%
80%
90%
100%
90%
10%
It is found in the study that 90% of the people say that when their friend/follower shares something
about them or anybody else on the social media, then they have the option to block that
friend/follower. But 10% of the people say that when their friend/follower shares something about
them or anybody else on the social media, then they do not have the option to block that
friend/follower.
Why do you or other people try to violate the privacy of others?
For fun
For disturbing them
For entertainment
For judging them
For taking revenge
For insulting them
For interfering in their personal lives
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
25%
10%
5% 2%
30%
2%
26%
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
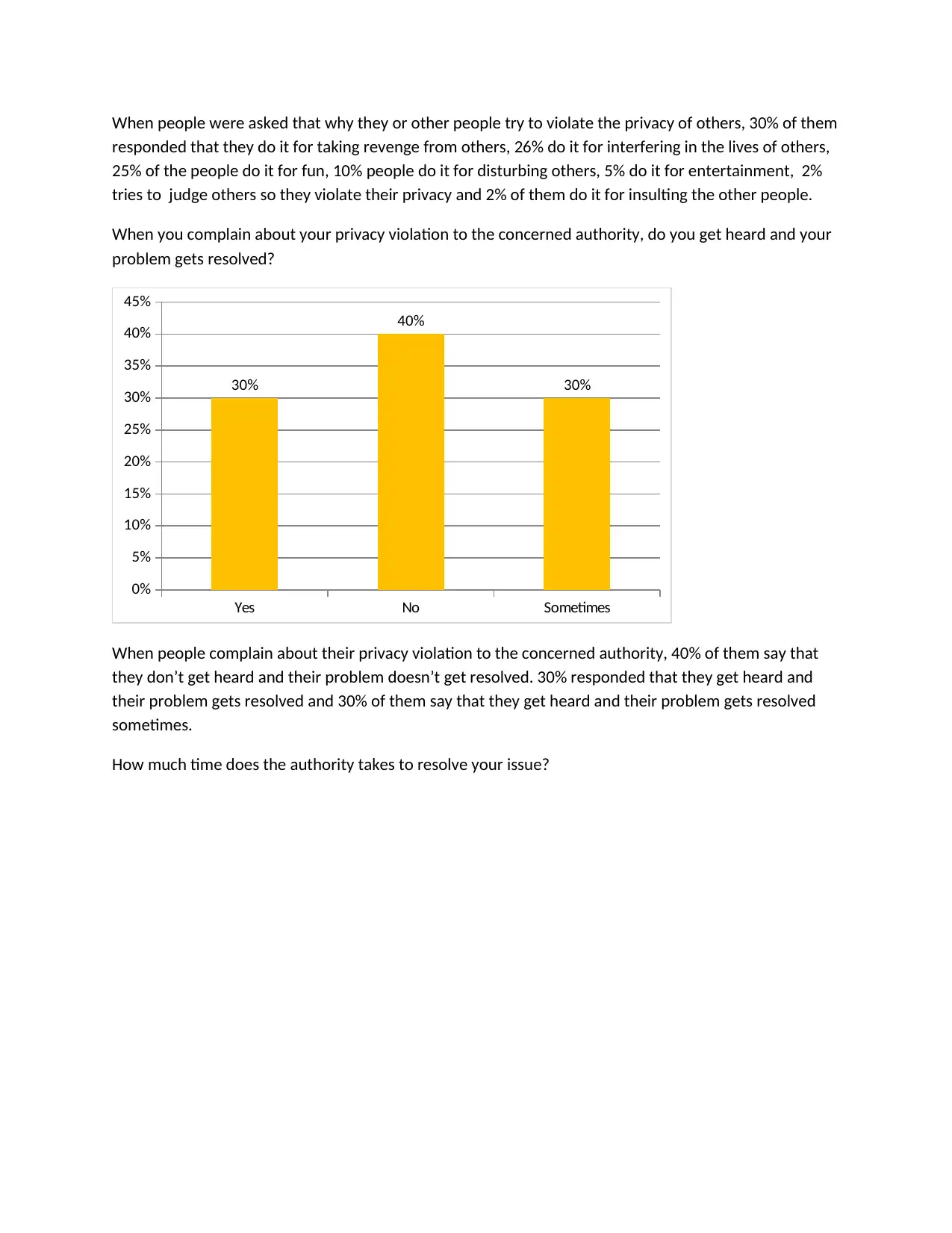
When people were asked that why they or other people try to violate the privacy of others, 30% of them
responded that they do it for taking revenge from others, 26% do it for interfering in the lives of others,
25% of the people do it for fun, 10% people do it for disturbing others, 5% do it for entertainment, 2%
tries to judge others so they violate their privacy and 2% of them do it for insulting the other people.
When you complain about your privacy violation to the concerned authority, do you get heard and your
problem gets resolved?
Yes No Sometimes
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
30%
40%
30%
When people complain about their privacy violation to the concerned authority, 40% of them say that
they don’t get heard and their problem doesn’t get resolved. 30% responded that they get heard and
their problem gets resolved and 30% of them say that they get heard and their problem gets resolved
sometimes.
How much time does the authority takes to resolve your issue?
responded that they do it for taking revenge from others, 26% do it for interfering in the lives of others,
25% of the people do it for fun, 10% people do it for disturbing others, 5% do it for entertainment, 2%
tries to judge others so they violate their privacy and 2% of them do it for insulting the other people.
When you complain about your privacy violation to the concerned authority, do you get heard and your
problem gets resolved?
Yes No Sometimes
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
30%
40%
30%
When people complain about their privacy violation to the concerned authority, 40% of them say that
they don’t get heard and their problem doesn’t get resolved. 30% responded that they get heard and
their problem gets resolved and 30% of them say that they get heard and their problem gets resolved
sometimes.
How much time does the authority takes to resolve your issue?

One day One week One month More than a
month
0%
10%
20%
30%
40%
50%
60%
2%
50%
20%
28%
It is found that 50% of the people say that it takes one week for the authority to resolve their issue, 28%
say that it takes more than a month week for the authority to resolve their issue, 20% say that it takes a
month for the authority to resolve their issue and only 2% say that it takes a day for the authority to
resolve their issue.
month
0%
10%
20%
30%
40%
50%
60%
2%
50%
20%
28%
It is found that 50% of the people say that it takes one week for the authority to resolve their issue, 28%
say that it takes more than a month week for the authority to resolve their issue, 20% say that it takes a
month for the authority to resolve their issue and only 2% say that it takes a day for the authority to
resolve their issue.

Findings from qualitative sources
Findings related to the ethical code of conduct or legal framework to regulate the use of social media
in violating privacy of others
There is a right in UK known as the ‘Right to Privacy’. This right gives the privacy rights against the
misuse of the information about the state and the private persons which is confidential. The rights given
in this right protects the people from all types of social media activities even the photographs posting,
no matter the information underlying it may be effectively commercial in nature. This right is not
mentioned in the constitution of UK, but it has incorporated the European Convention on Human Rights into its
national law, which provides for a limited right of respect towards an individual’s privacy and family life (Edwards,
2013). In social media, there are also laws related to protection of data and it enables people to get
protection from the information that is posted on the social media (Adelola, 2015).
The ‘Data Protection Act, 1998’ was enacted to take care of the personal information of the people that
was being processed. The personal information of the people is protected from being disclosed,
obtained, held and used (Council, 2015).
Conclusion and recommendations
Research analysis and results
1. The findings show that mainly, the people use social media for staying connected with areas/people
of interests like celebrities, film industry, and political industry etc. and for expressing their views,
opinions, thoughts, knowledge about some current issue. So, it can be analysed that people like to
look into the world around them and they like to know that what is happening in the industries
around them especially the film and political world. Also, they like to share their views on the
current issues because they have the freedom of speech and they want the world to know that
what are their opinions and views. They also encourage others to talk about the issues and give
their views so that they can hold a debate on a topic and talk about it in detail. It has also been
found that some people use social media for spying in the lives of others, they do this because they
like to comment on the life and instances of others. There were very few people who wanted to
stay connected with their friends and few of them used it for passing their time. This means that
people are not using media for their personal things like chatting with friends or for leisure; they are
just using it to peep in the lives of others and for interfering with their issues. Though this is not
incorrect in the sense that people should give their opinion and views if they feel something but
that should not lead to insulting someone or it should not breach the privacy of others. That is
considered unethical when people do this and they misuse the social media for breaching the
privacy of others.
2. The findings show that most of the respondents in the study use the social media platform for
posting something or for commenting on someone many times in a week. This shows that the
people are very active on the social media platforms and they use their social media accounts very
Findings related to the ethical code of conduct or legal framework to regulate the use of social media
in violating privacy of others
There is a right in UK known as the ‘Right to Privacy’. This right gives the privacy rights against the
misuse of the information about the state and the private persons which is confidential. The rights given
in this right protects the people from all types of social media activities even the photographs posting,
no matter the information underlying it may be effectively commercial in nature. This right is not
mentioned in the constitution of UK, but it has incorporated the European Convention on Human Rights into its
national law, which provides for a limited right of respect towards an individual’s privacy and family life (Edwards,
2013). In social media, there are also laws related to protection of data and it enables people to get
protection from the information that is posted on the social media (Adelola, 2015).
The ‘Data Protection Act, 1998’ was enacted to take care of the personal information of the people that
was being processed. The personal information of the people is protected from being disclosed,
obtained, held and used (Council, 2015).
Conclusion and recommendations
Research analysis and results
1. The findings show that mainly, the people use social media for staying connected with areas/people
of interests like celebrities, film industry, and political industry etc. and for expressing their views,
opinions, thoughts, knowledge about some current issue. So, it can be analysed that people like to
look into the world around them and they like to know that what is happening in the industries
around them especially the film and political world. Also, they like to share their views on the
current issues because they have the freedom of speech and they want the world to know that
what are their opinions and views. They also encourage others to talk about the issues and give
their views so that they can hold a debate on a topic and talk about it in detail. It has also been
found that some people use social media for spying in the lives of others, they do this because they
like to comment on the life and instances of others. There were very few people who wanted to
stay connected with their friends and few of them used it for passing their time. This means that
people are not using media for their personal things like chatting with friends or for leisure; they are
just using it to peep in the lives of others and for interfering with their issues. Though this is not
incorrect in the sense that people should give their opinion and views if they feel something but
that should not lead to insulting someone or it should not breach the privacy of others. That is
considered unethical when people do this and they misuse the social media for breaching the
privacy of others.
2. The findings show that most of the respondents in the study use the social media platform for
posting something or for commenting on someone many times in a week. This shows that the
people are very active on the social media platforms and they use their social media accounts very
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

extensively. Even there were people in large number who post something on the platform of social
media daily. This shows that social media has become very popular among the people and it is used
on regular basis by the people. The people comment on the social media sites in regular manner
and they like to talk on these websites very much. They have not set any limits of using social media
for themselves, they are using it as and when they feel to. There are very few people who are not
using social media on regular basis. One reason of this may be that they are of older generation
and they are not very tech savvy to use such things, or they may just not be interested to become
social.
3. The findings show that most of the people are aware of the privacy settings of their social media
accounts and its use. This means that they know about the privacy of social media accounts and
they know how to use it. The awareness about privacy settings is there in the people and they are
well-equipped to use it. There were few people who were not at all aware of the privacy settings of
their social media accounts and its use. This may be due to the reason that they were not properly
educated or may be because they were indulged in the breach of privacy of others so they never
bothered to learn about the privacy settings.
4. The findings show that most of the people use privacy settings in controlling and monitoring the
posts that they share or the people they follow. These are not indulged in violation of privacy of
others as they know how to limit the audience of their post. But there are many other people who
do not use privacy settings in controlling and monitoring the posts that they share or the people
they follow. They are the ones who don’t know their limits while using social media and they cause
privacy violation in social media accounts of others. They do something and others suffer due to
that, for example they share some post or photo and it is visible to everyone on the internet, so
there is risk to the privacy of others. There are other people also, who sometimes use privacy
settings in controlling and monitoring the posts that they share or the people they follow. This
shows that they use these settings only when they feel that some post is not for everyone on the
internet but these people may also cause a threat to the privacy of others.
5. The findings show that most of the people control the privacy related settings of their social media
accounts by adjusting the settings for controlling the other people’s access on their account and on
the things that they post or publish. This shows that they are concerned about their privacy a lot.
They don’t want others to peep in their personal lives and comment on what they share but this
does not confirm that they feel the same for the others too. There are other people too who don’t
care about the control on the privacy settings and they are not even aware about the settings.
6. The findings show that most of the people make their posts visible to all the users of internet. This
means that they have no limits on the use of social media. They are open to all the people and they
allow others to violate their privacy. They are very few people who do not do this.
7. There are many people in the study who do not take permission of their friends, followers or
anybody (about whom they share something or talk something) before presenting them on social
media. This shows that they are not concerned about their privacy and they don’t leave them
secured. They are giving others a chance to breach and violate the privacy of their friends and they
themselves are doing the same if they are not taking permission. Very few of them take permission
of their friends, followers or anybody (about whom they share something or talk something) before
media daily. This shows that social media has become very popular among the people and it is used
on regular basis by the people. The people comment on the social media sites in regular manner
and they like to talk on these websites very much. They have not set any limits of using social media
for themselves, they are using it as and when they feel to. There are very few people who are not
using social media on regular basis. One reason of this may be that they are of older generation
and they are not very tech savvy to use such things, or they may just not be interested to become
social.
3. The findings show that most of the people are aware of the privacy settings of their social media
accounts and its use. This means that they know about the privacy of social media accounts and
they know how to use it. The awareness about privacy settings is there in the people and they are
well-equipped to use it. There were few people who were not at all aware of the privacy settings of
their social media accounts and its use. This may be due to the reason that they were not properly
educated or may be because they were indulged in the breach of privacy of others so they never
bothered to learn about the privacy settings.
4. The findings show that most of the people use privacy settings in controlling and monitoring the
posts that they share or the people they follow. These are not indulged in violation of privacy of
others as they know how to limit the audience of their post. But there are many other people who
do not use privacy settings in controlling and monitoring the posts that they share or the people
they follow. They are the ones who don’t know their limits while using social media and they cause
privacy violation in social media accounts of others. They do something and others suffer due to
that, for example they share some post or photo and it is visible to everyone on the internet, so
there is risk to the privacy of others. There are other people also, who sometimes use privacy
settings in controlling and monitoring the posts that they share or the people they follow. This
shows that they use these settings only when they feel that some post is not for everyone on the
internet but these people may also cause a threat to the privacy of others.
5. The findings show that most of the people control the privacy related settings of their social media
accounts by adjusting the settings for controlling the other people’s access on their account and on
the things that they post or publish. This shows that they are concerned about their privacy a lot.
They don’t want others to peep in their personal lives and comment on what they share but this
does not confirm that they feel the same for the others too. There are other people too who don’t
care about the control on the privacy settings and they are not even aware about the settings.
6. The findings show that most of the people make their posts visible to all the users of internet. This
means that they have no limits on the use of social media. They are open to all the people and they
allow others to violate their privacy. They are very few people who do not do this.
7. There are many people in the study who do not take permission of their friends, followers or
anybody (about whom they share something or talk something) before presenting them on social
media. This shows that they are not concerned about their privacy and they don’t leave them
secured. They are giving others a chance to breach and violate the privacy of their friends and they
themselves are doing the same if they are not taking permission. Very few of them take permission
of their friends, followers or anybody (about whom they share something or talk something) before

presenting them on social media. These are the ones who are concerned about privacy violation
issues in social media but they are very limited in number.
8. Earlier it was found that people don’t take permission of their friends, followers or anybody (about
whom they share something or talk something) before presenting them on social media, but here it
is found that they don’t even feel the need to do so. Most of the people under this study do not feel
the need to take permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media. This shows that the level of
awareness among people is less and the concern about privacy issues is also less. Though there are
people who still feel that they should take permission of their friends, followers or anybody (about
whom they share something or talk something) before presenting them on social media. But these
are less in number than the former ones.
9. It is difficult for most of the people to control what their friend/follower shares something about
them or anybody else on the social media. This means that they have less control on their security.
It is very little that they can do to control their own privacy. Thus, there is a threat to privacy of
people. But few of the people also feel that they have the ability to control it and don’t have the
ability to control it. The people are not safe in the use of social media of they cannot control their
own privacy settings and the posts about them that others share.
10. The study shows that large number of the people feel that they have the right to limit the post or
report it or mark it as spam when their friend/follower shares something about them or anybody
else on the social media. This means that even if something is posted or written against them, they
can rectify it and remove it or they don’t like it or it breaches their privacy on social media. Others
said that they sometimes have the right which means that they cannot always limit what others
post because others may have not allowed us to look at their post but they have the right to post
anything about anyone. Few people also feel that they do not have the right to limit the post or
report it or mark it as spam when their friend/follower shares something about them or anybody
else on the social media. This is due to the same reason that they may not have the access to other
people’s accounts.
11. A positive thing that was found related to security on the social media is that most of the people,
almost 90% of the people say that when their friend/follower shares something about them or
anybody else on the social media, then they have the option to block that friend/follower. This
means that the people have the option to get secured from the person forever but it may happen
that the person violates the privacy by making a fake account or by any other means. So, still the
privacy may be violated due to use of social media.
12. The main factors due to which people violate other’s privacy is that they do it for taking revenge
from others, 26% do it for interfering in the lives of others, 25% of the people do it for fun, 10%
people do it for disturbing others, 5% do it for entertainment, 2% tries to judge others so they
violate their privacy and 2% of them do it for insulting the other people. This means that jealousy,
competition, and negative thoughts makes people violate others privacy and some people like to
know what others are doing and they are interested in disturbing their personal lives so they violate
their privacy. Some do it for fun as they find it funny to disturb others and bother them.
13. Most of the people find the authorities to be incompetent to resolve their issues. This may be due
to the fact they might have had a bad experience in the past and they might have complained it to
issues in social media but they are very limited in number.
8. Earlier it was found that people don’t take permission of their friends, followers or anybody (about
whom they share something or talk something) before presenting them on social media, but here it
is found that they don’t even feel the need to do so. Most of the people under this study do not feel
the need to take permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media. This shows that the level of
awareness among people is less and the concern about privacy issues is also less. Though there are
people who still feel that they should take permission of their friends, followers or anybody (about
whom they share something or talk something) before presenting them on social media. But these
are less in number than the former ones.
9. It is difficult for most of the people to control what their friend/follower shares something about
them or anybody else on the social media. This means that they have less control on their security.
It is very little that they can do to control their own privacy. Thus, there is a threat to privacy of
people. But few of the people also feel that they have the ability to control it and don’t have the
ability to control it. The people are not safe in the use of social media of they cannot control their
own privacy settings and the posts about them that others share.
10. The study shows that large number of the people feel that they have the right to limit the post or
report it or mark it as spam when their friend/follower shares something about them or anybody
else on the social media. This means that even if something is posted or written against them, they
can rectify it and remove it or they don’t like it or it breaches their privacy on social media. Others
said that they sometimes have the right which means that they cannot always limit what others
post because others may have not allowed us to look at their post but they have the right to post
anything about anyone. Few people also feel that they do not have the right to limit the post or
report it or mark it as spam when their friend/follower shares something about them or anybody
else on the social media. This is due to the same reason that they may not have the access to other
people’s accounts.
11. A positive thing that was found related to security on the social media is that most of the people,
almost 90% of the people say that when their friend/follower shares something about them or
anybody else on the social media, then they have the option to block that friend/follower. This
means that the people have the option to get secured from the person forever but it may happen
that the person violates the privacy by making a fake account or by any other means. So, still the
privacy may be violated due to use of social media.
12. The main factors due to which people violate other’s privacy is that they do it for taking revenge
from others, 26% do it for interfering in the lives of others, 25% of the people do it for fun, 10%
people do it for disturbing others, 5% do it for entertainment, 2% tries to judge others so they
violate their privacy and 2% of them do it for insulting the other people. This means that jealousy,
competition, and negative thoughts makes people violate others privacy and some people like to
know what others are doing and they are interested in disturbing their personal lives so they violate
their privacy. Some do it for fun as they find it funny to disturb others and bother them.
13. Most of the people find the authorities to be incompetent to resolve their issues. This may be due
to the fact they might have had a bad experience in the past and they might have complained it to

the authorities earlier but they were not heard. This shows that even if their privacy is violated, they
don’t get justice and resolution of the same. But there were few people too who were positive
about the resolution of their problems. This may be due to their experience was good in the past.
So, the people who got their issues resolved in the past found the authorities to be competent
enough to solve their problems and vice-versa.
14. The respondents say that the authorities take one week to resolve their issue, though the time
taken is not long but in some cases the issue might be urgent so in that case, one week is a long
time. The issue should get resolved as per the urgency of the work. But in some cases the
authorities even take a month to resolve their issue. This response was based on the experience of
the respondents.
15. Lastly, it has been found that the country has some laws, regulations, rights and legal framework to
protect the people from privacy violation in the social media. These have been used to regulate the
use of social media in violating privacy of others. But then also, there are issues in this area and the
people are not satisfied by the regulations etc. That is why they keep on complaining about such
issues and the authorities also get reports on such matters.
Conclusion
From the above discussion, it can be concluded that all the objectives of the study are satisfied in this
study in the following way:
The objective that “To find out the limits that individuals understand regarding their own privacy and
other‘s privacy while using social media” is fulfilled from the findings that most of the people are aware
of the privacy settings of their social media accounts and its use, they know about the privacy of social
media accounts and they know how to use it. Though, most of the people use privacy settings in
controlling and monitoring the posts that they share or the people they follow and they are not indulged
in violation of privacy of others as they know how to limit the audience of their post. But there are many
other people who do not use privacy settings in controlling and monitoring the posts that they share or
the people they follow. Majority of the people control the privacy related settings of their social media
accounts by adjusting the settings for controlling the other people’s access on their account and on the
things that they post or publish. This shows that they are concerned about their privacy a lot. Then,
most of the people make their posts visible to all the users of internet. This means that they have no
limits on the use of social media. There are many people in the study who do not take permission of
their friends, followers or anybody (about whom they share something or talk something) before
presenting them on social media. This shows that they are not concerned about their privacy and they
don’t leave them secured. They are giving others a chance to breach and violate the privacy of their
friends and they themselves are doing the same if they are not taking permission and that they don’t
even feel the need to do so. Briefly, the people have very less limits on the understanding of their
privacy and other’s privacy on social media.
The second objective “To analyse the appropriateness of privacy standards for others in social media” is
fulfilled from the findings that it is difficult for most of the people to control what their friend/follower
don’t get justice and resolution of the same. But there were few people too who were positive
about the resolution of their problems. This may be due to their experience was good in the past.
So, the people who got their issues resolved in the past found the authorities to be competent
enough to solve their problems and vice-versa.
14. The respondents say that the authorities take one week to resolve their issue, though the time
taken is not long but in some cases the issue might be urgent so in that case, one week is a long
time. The issue should get resolved as per the urgency of the work. But in some cases the
authorities even take a month to resolve their issue. This response was based on the experience of
the respondents.
15. Lastly, it has been found that the country has some laws, regulations, rights and legal framework to
protect the people from privacy violation in the social media. These have been used to regulate the
use of social media in violating privacy of others. But then also, there are issues in this area and the
people are not satisfied by the regulations etc. That is why they keep on complaining about such
issues and the authorities also get reports on such matters.
Conclusion
From the above discussion, it can be concluded that all the objectives of the study are satisfied in this
study in the following way:
The objective that “To find out the limits that individuals understand regarding their own privacy and
other‘s privacy while using social media” is fulfilled from the findings that most of the people are aware
of the privacy settings of their social media accounts and its use, they know about the privacy of social
media accounts and they know how to use it. Though, most of the people use privacy settings in
controlling and monitoring the posts that they share or the people they follow and they are not indulged
in violation of privacy of others as they know how to limit the audience of their post. But there are many
other people who do not use privacy settings in controlling and monitoring the posts that they share or
the people they follow. Majority of the people control the privacy related settings of their social media
accounts by adjusting the settings for controlling the other people’s access on their account and on the
things that they post or publish. This shows that they are concerned about their privacy a lot. Then,
most of the people make their posts visible to all the users of internet. This means that they have no
limits on the use of social media. There are many people in the study who do not take permission of
their friends, followers or anybody (about whom they share something or talk something) before
presenting them on social media. This shows that they are not concerned about their privacy and they
don’t leave them secured. They are giving others a chance to breach and violate the privacy of their
friends and they themselves are doing the same if they are not taking permission and that they don’t
even feel the need to do so. Briefly, the people have very less limits on the understanding of their
privacy and other’s privacy on social media.
The second objective “To analyse the appropriateness of privacy standards for others in social media” is
fulfilled from the findings that it is difficult for most of the people to control what their friend/follower
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

shares something about them or anybody else on the social media. This means that they have less
control on their security. The study shows that large number of the people feel that they have the right
to limit the post or report it or mark it as spam when their friend/follower shares something about them
or anybody else on the social media. This means that even if something is posted or written against
them, they can rectify it and remove it or they don’t like it or it breaches their privacy on social media.
90% of the people say that when their friend/follower shares something about them or anybody else on
the social media, then they have the option to block that friend/follower. This means that the people
have the option to get secured from the person forever but it may happen that the person violates the
privacy by making a fake account or by any other means. Briefly, the privacy standards are appropriate
as the online websites have given many privacy securities to the people but then also the standards are
capable of getting violated.
The third objective “To determine the factors that influence individuals in violating privacy of others” is
satisfied from the result that mainly, the people use social media for staying connected with
areas/people of interests like celebrities, film industry, and political industry etc. and for expressing their
views, opinions, thoughts, knowledge about some current issue. It has also been found that some
people use social media for spying in the lives of others, they do this because they like to comment on
the life and instances of others. There were very few people who wanted to stay connected with their
friends and few of them used it for passing their time. This means that people are not using media for
their personal things like chatting with friends or for leisure; they are just using it to peep in the lives of
others and for interfering with their issues. Though this is not incorrect in the sense that people should
give their opinion and views if they feel something but that should not lead to insulting someone or it
should not breach the privacy of others. That is considered unethical when people do this and they
misuse the social media for breaching the privacy of others. The main factors due to which people
violate other’s privacy is that they do it for taking revenge from others, 26% do it for interfering in the
lives of others, 25% of the people do it for fun, 10% people do it for disturbing others, 5% do it for
entertainment, 2% tries to judge others so they violate their privacy and 2% of them do it for insulting
the other people. This means that jealousy, competition, and negative thoughts makes people violate
others privacy and some people like to know what others are doing and they are interested in disturbing
their personal lives so they violate their privacy. Some do it for fun as they find it funny to disturb others
and bother them. Briefly, the reason for violating the privacy is that the people try to defame others by
disrespecting them and they do it for taking some kind of revenge from the.
The fourth objective “To study the ethical code of conduct or legal framework to regulate the use of
social media in violating privacy of others” is fulfilled from the result that the country has some laws,
regulations, rights and legal framework to protect the people from privacy violation in the social media.
These have been used to regulate the use of social media in violating privacy of others. But then also,
there are issues in this area and the people are not satisfied by the regulations etc. That is why they
keep on complaining about such issues and the authorities also get reports on such matters. Briefly, it
can be said that the legal framework is established for protecting people, but it is not much effective.
The last objective, “To investigate the effectiveness of the policies and standards in protecting the
privacy of people in context of social media” is satisfied from the findings that most of the people find
control on their security. The study shows that large number of the people feel that they have the right
to limit the post or report it or mark it as spam when their friend/follower shares something about them
or anybody else on the social media. This means that even if something is posted or written against
them, they can rectify it and remove it or they don’t like it or it breaches their privacy on social media.
90% of the people say that when their friend/follower shares something about them or anybody else on
the social media, then they have the option to block that friend/follower. This means that the people
have the option to get secured from the person forever but it may happen that the person violates the
privacy by making a fake account or by any other means. Briefly, the privacy standards are appropriate
as the online websites have given many privacy securities to the people but then also the standards are
capable of getting violated.
The third objective “To determine the factors that influence individuals in violating privacy of others” is
satisfied from the result that mainly, the people use social media for staying connected with
areas/people of interests like celebrities, film industry, and political industry etc. and for expressing their
views, opinions, thoughts, knowledge about some current issue. It has also been found that some
people use social media for spying in the lives of others, they do this because they like to comment on
the life and instances of others. There were very few people who wanted to stay connected with their
friends and few of them used it for passing their time. This means that people are not using media for
their personal things like chatting with friends or for leisure; they are just using it to peep in the lives of
others and for interfering with their issues. Though this is not incorrect in the sense that people should
give their opinion and views if they feel something but that should not lead to insulting someone or it
should not breach the privacy of others. That is considered unethical when people do this and they
misuse the social media for breaching the privacy of others. The main factors due to which people
violate other’s privacy is that they do it for taking revenge from others, 26% do it for interfering in the
lives of others, 25% of the people do it for fun, 10% people do it for disturbing others, 5% do it for
entertainment, 2% tries to judge others so they violate their privacy and 2% of them do it for insulting
the other people. This means that jealousy, competition, and negative thoughts makes people violate
others privacy and some people like to know what others are doing and they are interested in disturbing
their personal lives so they violate their privacy. Some do it for fun as they find it funny to disturb others
and bother them. Briefly, the reason for violating the privacy is that the people try to defame others by
disrespecting them and they do it for taking some kind of revenge from the.
The fourth objective “To study the ethical code of conduct or legal framework to regulate the use of
social media in violating privacy of others” is fulfilled from the result that the country has some laws,
regulations, rights and legal framework to protect the people from privacy violation in the social media.
These have been used to regulate the use of social media in violating privacy of others. But then also,
there are issues in this area and the people are not satisfied by the regulations etc. That is why they
keep on complaining about such issues and the authorities also get reports on such matters. Briefly, it
can be said that the legal framework is established for protecting people, but it is not much effective.
The last objective, “To investigate the effectiveness of the policies and standards in protecting the
privacy of people in context of social media” is satisfied from the findings that most of the people find

the authorities to be incompetent to resolve their issues. This may be due to the fact they might have
had a bad experience in the past and they might have complained it to the authorities earlier but they
were not heard. This shows that even if their privacy is violated, they don’t get justice and resolution of
the same. But there were few people too who were positive about the resolution of their problems. This
may be due to their experience was good in the past. So, the people who got their issues resolved in the
past found the authorities to be competent enough to solve their problems and vice-versa. The
respondents say that the authorities take one week to resolve their issue, though the time taken is not
long but in some cases the issue might be urgent so in that case, one week is a long time. The issue
should get resolved as per the urgency of the work. But in some cases the authorities even take a month
to resolve their issue. This response was based on the experience of the respondents. Briefly, it can be
said that people are not happy with the resolution of their privacy related complaints, they feel that
the time taken for resolving the issues by the authorities is very long.
had a bad experience in the past and they might have complained it to the authorities earlier but they
were not heard. This shows that even if their privacy is violated, they don’t get justice and resolution of
the same. But there were few people too who were positive about the resolution of their problems. This
may be due to their experience was good in the past. So, the people who got their issues resolved in the
past found the authorities to be competent enough to solve their problems and vice-versa. The
respondents say that the authorities take one week to resolve their issue, though the time taken is not
long but in some cases the issue might be urgent so in that case, one week is a long time. The issue
should get resolved as per the urgency of the work. But in some cases the authorities even take a month
to resolve their issue. This response was based on the experience of the respondents. Briefly, it can be
said that people are not happy with the resolution of their privacy related complaints, they feel that
the time taken for resolving the issues by the authorities is very long.

References
Appendices
Questionnaire
The responses will be used for academic purpose only and the identity of the respondents will be kept
confidential.
Name of respondent
Occupation
Age
Gender
1. Why do you use social media? Q3
a. To stay connected with friends
b. To stay connected with areas/people of interests like celebrities, film industry, political
industry etc.
c. To express my views, opinions, thoughts, knowledge about some current issue
d. To spy in the lives of others
e. For passing time
2. How often do you use the social media platform for posting something or for commenting on
someone?
a. Everyday
b. Many times in a week
c. Occasionally
d. Very rarely
e. Never
3. Are you aware of the privacy settings of your social media accounts and its use? Q1
a. Yes
b. No
c. Not very sure
4. Do you use the privacy settings in controlling and monitoring the posts you share or the people
you follow? Q1
a. Yes
b. No
c. Sometimes
5. In what ways do you control the privacy related settings of your social media accounts? Q1
a. The settings are adjusted for controlling the other people’s access on my account and on the
things that I post or publish.
b. I know about the settings related to privacy but I don’t bother about controlling them.
Appendices
Questionnaire
The responses will be used for academic purpose only and the identity of the respondents will be kept
confidential.
Name of respondent
Occupation
Age
Gender
1. Why do you use social media? Q3
a. To stay connected with friends
b. To stay connected with areas/people of interests like celebrities, film industry, political
industry etc.
c. To express my views, opinions, thoughts, knowledge about some current issue
d. To spy in the lives of others
e. For passing time
2. How often do you use the social media platform for posting something or for commenting on
someone?
a. Everyday
b. Many times in a week
c. Occasionally
d. Very rarely
e. Never
3. Are you aware of the privacy settings of your social media accounts and its use? Q1
a. Yes
b. No
c. Not very sure
4. Do you use the privacy settings in controlling and monitoring the posts you share or the people
you follow? Q1
a. Yes
b. No
c. Sometimes
5. In what ways do you control the privacy related settings of your social media accounts? Q1
a. The settings are adjusted for controlling the other people’s access on my account and on the
things that I post or publish.
b. I know about the settings related to privacy but I don’t bother about controlling them.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

c. I am not aware about the procedure to control the privacy settings of my social media
accounts.
d. I know how to control the privacy related settings of my social media accounts.
6. When you use your social media accounts like the Facebook account or the Twitter account, do
you make your posts visible to all the users of internet? Q1
a. Yes
b. No
c. Sometimes
7. Do you take permission of your friends, followers or anybody (about whom you share something
or talk something) before presenting them on social media? Q1
a. Yes
b. No
c. Sometimes
8. Do you think that you should take permission of your friends, followers or anybody (about
whom you share something or talk something) before presenting them on social media? Q1
a. Yes
b. No
9. When your friend/follower shares something about you or anybody else on the social media, do
you or that person has the ability to control it? Q2
a. Yes
b. No
c. To an extent
10. When your friend/follower shares something about you or anybody else on the social media, do
you or that person has the right to limit that post or report it or mark it as spam? Q2
a. Yes
b. No
c. Sometimes
11. When your friend/follower shares something about you or anybody else on the social media, do
you or that person has the option to block that friend/follower? Q2
a. Yes
b. No
12. Why do you or other people try to violate the privacy of others? Q3
a. For fun
b. For disturbing them
c. For entertainment
d. For judging them
e. For taking revenge
f. For insulting them
g. For interfering in their personal lives
13. When you complain about your privacy violation to the concerned authority, do you get heard
and your problem gets resolved? Q5
a. Yes
b. No
c. Sometimes
accounts.
d. I know how to control the privacy related settings of my social media accounts.
6. When you use your social media accounts like the Facebook account or the Twitter account, do
you make your posts visible to all the users of internet? Q1
a. Yes
b. No
c. Sometimes
7. Do you take permission of your friends, followers or anybody (about whom you share something
or talk something) before presenting them on social media? Q1
a. Yes
b. No
c. Sometimes
8. Do you think that you should take permission of your friends, followers or anybody (about
whom you share something or talk something) before presenting them on social media? Q1
a. Yes
b. No
9. When your friend/follower shares something about you or anybody else on the social media, do
you or that person has the ability to control it? Q2
a. Yes
b. No
c. To an extent
10. When your friend/follower shares something about you or anybody else on the social media, do
you or that person has the right to limit that post or report it or mark it as spam? Q2
a. Yes
b. No
c. Sometimes
11. When your friend/follower shares something about you or anybody else on the social media, do
you or that person has the option to block that friend/follower? Q2
a. Yes
b. No
12. Why do you or other people try to violate the privacy of others? Q3
a. For fun
b. For disturbing them
c. For entertainment
d. For judging them
e. For taking revenge
f. For insulting them
g. For interfering in their personal lives
13. When you complain about your privacy violation to the concerned authority, do you get heard
and your problem gets resolved? Q5
a. Yes
b. No
c. Sometimes

14. How much time does the authority takes to resolve your issue? Q5
a. One day
b. One week
c. One month
d. More than a month
a. One day
b. One week
c. One month
d. More than a month
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





