Analysis of Physical Security - Doc
VerifiedAdded on 2021/06/16
|11
|2360
|121
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Information Security
By
(Name)
(Course)
(Professor’s Name)
(Institution)
(State)
(Date)
Case project 4.2: Analysis of physical security.
By
(Name)
(Course)
(Professor’s Name)
(Institution)
(State)
(Date)
Case project 4.2: Analysis of physical security.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Introduction.
Physical security are hardware systems that detect and delay any malicious individuals or
activity from accessing and destroying computer systems1. These physical security systems
allow time for intervention by law enforcement such as guards. The levels of security systems
installed depend on the factors surrounding the protected devices such as fragility of the
system, sensitivity, data encryption and law enforcement response time.
Objectives.
To determine the level of physical security installed around the workplace’s computer lab.
To find out the strengths and weaknesses of the various aspects of the physical security.
Methodology.
Observations and note taking of the physical security systems around the computer facility.
Interviews were conducted to inquire about the levels of security installed and why.
Results.
The computer facility is located in the underground floor of the main office. The building
hosting the main offices and thus the computer facility is fenced with a high brick perimeter
wall with a barbed wire on the top to minimize the risk of intruders jumping over2.
The perimeter wall is gated. The gate is lockable with a strong padlock that is continually
locked and watched over by a security guard.
The room hosting the computers is locked using a guard controlled door.
There is a manual registry book to record all the entrances and exits into and out of the
computer facility, a responsibility of the guard to ensure that everyone accessing the room
signs the records book.
1 Mo, Y., Kim, T.H.J., Brancik, K., Dickinson, D., Lee, H., Perrig, A. and Sinopoli, B., 2012. Cyber–
physical security of a smart grid infrastructure. Proceedings of the IEEE, 100(1), pp.195-209.
2 Weingart, S.H., 2010, August. Physical security devices for computer subsystems: A survey of
attacks and defenses. In International Workshop on Cryptographic Hardware and Embedded
Systems (pp. 302-317). Springer, Berlin, Heidelberg.
Physical security are hardware systems that detect and delay any malicious individuals or
activity from accessing and destroying computer systems1. These physical security systems
allow time for intervention by law enforcement such as guards. The levels of security systems
installed depend on the factors surrounding the protected devices such as fragility of the
system, sensitivity, data encryption and law enforcement response time.
Objectives.
To determine the level of physical security installed around the workplace’s computer lab.
To find out the strengths and weaknesses of the various aspects of the physical security.
Methodology.
Observations and note taking of the physical security systems around the computer facility.
Interviews were conducted to inquire about the levels of security installed and why.
Results.
The computer facility is located in the underground floor of the main office. The building
hosting the main offices and thus the computer facility is fenced with a high brick perimeter
wall with a barbed wire on the top to minimize the risk of intruders jumping over2.
The perimeter wall is gated. The gate is lockable with a strong padlock that is continually
locked and watched over by a security guard.
The room hosting the computers is locked using a guard controlled door.
There is a manual registry book to record all the entrances and exits into and out of the
computer facility, a responsibility of the guard to ensure that everyone accessing the room
signs the records book.
1 Mo, Y., Kim, T.H.J., Brancik, K., Dickinson, D., Lee, H., Perrig, A. and Sinopoli, B., 2012. Cyber–
physical security of a smart grid infrastructure. Proceedings of the IEEE, 100(1), pp.195-209.
2 Weingart, S.H., 2010, August. Physical security devices for computer subsystems: A survey of
attacks and defenses. In International Workshop on Cryptographic Hardware and Embedded
Systems (pp. 302-317). Springer, Berlin, Heidelberg.

There are surveillance cameras in the building. One is located in the corridor leading to the
computer facility while the second is located in the room itself. The cameras offer a 360
degrees surveillance.
After going through the records book, the server computer is located on the right of the
building. There is no barrier protecting the server computer, the network cables nor the power
backup mains supply unit.
Discussions.
The strengths of the organization’s physical security system are the following:
I. Hardware locks are used to keep the gates and the doors locked at all times.
II. The server room is well protected in an underground chamber of a well fenced
building.
III. There are guards manning the server room with a high response time.
IV. The records book allows for authentication before accessing the server room.
V. The facility is under constant daytime surveillance by the video cameras.
The organization has set up a commendable physical security system. However, the following
are some of the noted shortcomings:
Individuals with malicious intent can easily bypass the manual logbook used for signing in or
out of the server room. A modern technology security authentication system is high
recommended such as a smartcard reader or biometric scan kit.
Vulnerable devices such as networking cables connected to the main server are not properly
protected and thus can allow capturing of data travelling to and from the server3.
Workstations connected to the main server, for example the computer at the receptionist desk
is not well secured and protected by any physical security system. It can allow a hacker to
access the server.
The surveillance cameras do not have a night-vision functionality and therefore function
poorly under low light.
3 Stallings, W., Brown, L., Bauer, M.D. and Bhattacharjee, A.K., 2012. Computer security: principles
and practice (pp. 978-0). Pearson Education.
computer facility while the second is located in the room itself. The cameras offer a 360
degrees surveillance.
After going through the records book, the server computer is located on the right of the
building. There is no barrier protecting the server computer, the network cables nor the power
backup mains supply unit.
Discussions.
The strengths of the organization’s physical security system are the following:
I. Hardware locks are used to keep the gates and the doors locked at all times.
II. The server room is well protected in an underground chamber of a well fenced
building.
III. There are guards manning the server room with a high response time.
IV. The records book allows for authentication before accessing the server room.
V. The facility is under constant daytime surveillance by the video cameras.
The organization has set up a commendable physical security system. However, the following
are some of the noted shortcomings:
Individuals with malicious intent can easily bypass the manual logbook used for signing in or
out of the server room. A modern technology security authentication system is high
recommended such as a smartcard reader or biometric scan kit.
Vulnerable devices such as networking cables connected to the main server are not properly
protected and thus can allow capturing of data travelling to and from the server3.
Workstations connected to the main server, for example the computer at the receptionist desk
is not well secured and protected by any physical security system. It can allow a hacker to
access the server.
The surveillance cameras do not have a night-vision functionality and therefore function
poorly under low light.
3 Stallings, W., Brown, L., Bauer, M.D. and Bhattacharjee, A.K., 2012. Computer security: principles
and practice (pp. 978-0). Pearson Education.
There are no tracking devices such as motion sensors in the hidden areas without a guard or
surveillance cameras. Such an area includes the direct way from the underground carpark.
Conclusion.
It is important to secure the computer and its peripheral devices to reduce the activity of
malicious individuals such as hackers and thus protect the data of the company. Such systems
need to be secure enough and complimented with human enforcement such as guards.
Case study 5.3: Blowfish.
Introduction.
Blowfish has never been hacked! Blowfish is an encryption algorithm that uses the
symmetrical cryptographic design to encrypt and protect data. Blowfish is a free user licence-
free application. In the encryption sequence, blowfish uses the same key for encryption and
decryption4.
Bluefish generates encryption keys that is very unique that converts the key that varies from
32 bits to 448 bits and tables into sub keys that can be to 4168 bytes in size.
Objectives.
To understand the functionality of blowfish.
To determine the strengths of blowfish.
To find out the weaknesses of blowfish as an encryption tool.
Methodology.
Secondary sources of data such as textbooks and the internet were used to develop the
knowledge on Blowfish.
Serial hack attempts were made on data encrypted using blowfish.
Results.
4 Schneier, B., 2009, December. Description of a new variable-length key, 64-bit block cipher
(Blowfish). In International Workshop on Fast Software Encryption (pp. 191-204). Springer, Berlin,
Heidelberg.
surveillance cameras. Such an area includes the direct way from the underground carpark.
Conclusion.
It is important to secure the computer and its peripheral devices to reduce the activity of
malicious individuals such as hackers and thus protect the data of the company. Such systems
need to be secure enough and complimented with human enforcement such as guards.
Case study 5.3: Blowfish.
Introduction.
Blowfish has never been hacked! Blowfish is an encryption algorithm that uses the
symmetrical cryptographic design to encrypt and protect data. Blowfish is a free user licence-
free application. In the encryption sequence, blowfish uses the same key for encryption and
decryption4.
Bluefish generates encryption keys that is very unique that converts the key that varies from
32 bits to 448 bits and tables into sub keys that can be to 4168 bytes in size.
Objectives.
To understand the functionality of blowfish.
To determine the strengths of blowfish.
To find out the weaknesses of blowfish as an encryption tool.
Methodology.
Secondary sources of data such as textbooks and the internet were used to develop the
knowledge on Blowfish.
Serial hack attempts were made on data encrypted using blowfish.
Results.
4 Schneier, B., 2009, December. Description of a new variable-length key, 64-bit block cipher
(Blowfish). In International Workshop on Fast Software Encryption (pp. 191-204). Springer, Berlin,
Heidelberg.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Blowfish data encryption is dived into two phases. The first phase is key generation. Using a
64-bit block size of 32 bits to 448 bits key lengths, the generated key is expanded into
subkeys arrays with a maximum of 4168 bytes5.
Blowfish uses the Feistel structure. This structure utilizes the 16 curved cryptogram and huge
key s - containers. The Feistel structure uses 32 bits. The procedure retains 2 important
assortments this includes 4 256 - entrance S - containers and 18 - entrance P- assortments
and. The S - containers takes the 8 - bit input then in return produces the 32-bit output.
Blowfish is used in different products which include password tools, backup software and e-
mail encryption tools. Examples of tools using the Blowfish encryption tool include;
a) Land-J Technology J-file, a database program.
b) Freedom which a web-browsing, chat and e-mail privacy tool manufactured by the
Zero-Knowledge.
c) AEdit, is word processor for the Windows platform that uses the text encryption
functionality.
The first and most notable strength of Blowfish is being the fastest block cipher. Another
strength is the fact that blowfish is freely available for use to the general public.
Most importantly is the ability of Blowfish to expand the 32 bits or 448 bits into subkeys to
increase the security of the encrypted data. With such a longer key, it becomes very difficult
to hack and get the key-value.
The Blowfish key generation process is automated and has slight changes in the way the sub
keys are generated thus it’s difficult for the hackers to figure out the key generation process.
The major drawbacks of Blowfish are:
The process of key expansion is quite slower making Blowfish not suitable for use in many
other applications that encryption keys are to change over time.
The management of the user’s unique keys generated by Blowfish become complicated when
the number of users increase.
Conclusion.
5 Thakur, J. and Kumar, N., 2011. DES, AES and Blowfish: Symmetric key cryptography algorithms
simulation based performance analysis. International journal of emerging technology and advanced
engineering, 1(2), pp.6-12.
64-bit block size of 32 bits to 448 bits key lengths, the generated key is expanded into
subkeys arrays with a maximum of 4168 bytes5.
Blowfish uses the Feistel structure. This structure utilizes the 16 curved cryptogram and huge
key s - containers. The Feistel structure uses 32 bits. The procedure retains 2 important
assortments this includes 4 256 - entrance S - containers and 18 - entrance P- assortments
and. The S - containers takes the 8 - bit input then in return produces the 32-bit output.
Blowfish is used in different products which include password tools, backup software and e-
mail encryption tools. Examples of tools using the Blowfish encryption tool include;
a) Land-J Technology J-file, a database program.
b) Freedom which a web-browsing, chat and e-mail privacy tool manufactured by the
Zero-Knowledge.
c) AEdit, is word processor for the Windows platform that uses the text encryption
functionality.
The first and most notable strength of Blowfish is being the fastest block cipher. Another
strength is the fact that blowfish is freely available for use to the general public.
Most importantly is the ability of Blowfish to expand the 32 bits or 448 bits into subkeys to
increase the security of the encrypted data. With such a longer key, it becomes very difficult
to hack and get the key-value.
The Blowfish key generation process is automated and has slight changes in the way the sub
keys are generated thus it’s difficult for the hackers to figure out the key generation process.
The major drawbacks of Blowfish are:
The process of key expansion is quite slower making Blowfish not suitable for use in many
other applications that encryption keys are to change over time.
The management of the user’s unique keys generated by Blowfish become complicated when
the number of users increase.
Conclusion.
5 Thakur, J. and Kumar, N., 2011. DES, AES and Blowfish: Symmetric key cryptography algorithms
simulation based performance analysis. International journal of emerging technology and advanced
engineering, 1(2), pp.6-12.

In applications where the key does not change often, Blowfish should be used. Such
applications include automatic file encryptions and communication links such as e-mails.
With the increase in the speed of the computer’s processors, Blowfish will be utilized even in
the programs that change encryption keys frequently.
Case project 6.5: TRANSPORT LAYER SECURITY protocol.
Introductions.
Transport layer protocol is a new security protocol that allows secure communications on the
internet between two computers, a server and a client computer in data transfer applications
such as web-browsing, e-mail and voice over IP. TLS follows after its predecessor secure
sockets layer protocol(SSL)6.
The transport layer security protocol is contained in the application layer of the OSI model.
The TLS allows for a handshake protocol that allows authentication between connected
computers7. This handshake protocol ensures encryption before data transfer from the server
to the client.
Objectives:
To identify the strengths of the TLS.
To determine the shortcomings of the Transport layer security protocol and find ways to
mitigate the risks.
Methodology:
secondary sources of data were used to determine the information on the TLS and knowledge
on the merits.
The security protocol was exposed to a series of benchmarking tests to identify the
shortcomings pf the feature.
Results.
6 Dierks, T., 2008. The transport layer security (TLS) protocol version 1.2.
7 Sengupta, S. and Ansari, N., New Jersey Institute of Technology, 2011. Sub-segment based
transport layer protocol for wireless medium. U.S. Patent 7,965,674.
applications include automatic file encryptions and communication links such as e-mails.
With the increase in the speed of the computer’s processors, Blowfish will be utilized even in
the programs that change encryption keys frequently.
Case project 6.5: TRANSPORT LAYER SECURITY protocol.
Introductions.
Transport layer protocol is a new security protocol that allows secure communications on the
internet between two computers, a server and a client computer in data transfer applications
such as web-browsing, e-mail and voice over IP. TLS follows after its predecessor secure
sockets layer protocol(SSL)6.
The transport layer security protocol is contained in the application layer of the OSI model.
The TLS allows for a handshake protocol that allows authentication between connected
computers7. This handshake protocol ensures encryption before data transfer from the server
to the client.
Objectives:
To identify the strengths of the TLS.
To determine the shortcomings of the Transport layer security protocol and find ways to
mitigate the risks.
Methodology:
secondary sources of data were used to determine the information on the TLS and knowledge
on the merits.
The security protocol was exposed to a series of benchmarking tests to identify the
shortcomings pf the feature.
Results.
6 Dierks, T., 2008. The transport layer security (TLS) protocol version 1.2.
7 Sengupta, S. and Ansari, N., New Jersey Institute of Technology, 2011. Sub-segment based
transport layer protocol for wireless medium. U.S. Patent 7,965,674.

Hashing for Message Authentication is incorporated in the transport layer security to provide
keyed authentication. This ensures that a data being transported over the open networks
cannot be altered.
The transport layer security uses the enhanced pseudorandom function to generate two
algorithms within the HMAS. This prevents data losses in case one of the algorithms is
changes or interfered with. A change to the second algorithm exposes the data being
transmitted to risks such as data losses and hacking8.
The use of Hashing for Message Authentication and enhanced pseudorandom function values
in the message provides a more secure authentication that does not allow other computers on
the same network to access the data being transmitted.
The TLS provides a certificate authentication between nodes that ensures consistency in the
data being transmitted.
However, the TLS has the following shortcoming.
The process of the TLS handshake between the server and the client guarantees a slower
performance in the communication process. This slow performance is also evident in the
reloading of web pages. The TLS does not allow data caching hence the slow
communication. To address this limitation, simple web pages should be used.
Conclusions.
Transport layer security protocol is the most efficient web based data encryption protocol.
Because attacks get better with time, the TLS protocol is designed to allow modifications and
additions of more algorithms to increase the security protocol.
Case project 7.2: UTM comparison.
Introduction.
Unified threat management are tools that combine networking and security features to
provide secure functionality for businesses. These applications provide the security features
of the network against phishing, ransomware and other cybercrimes. UMT system can be
either virtual, cloud-based or hardware appliances.
8 Bajpai, P., Jain, V.K. and Akella, A.S., EchoStar Technologies LLC, 2014. Method and node for
employing network connections over a connectionless transport layer protocol. U.S. Patent 8,750,112.
keyed authentication. This ensures that a data being transported over the open networks
cannot be altered.
The transport layer security uses the enhanced pseudorandom function to generate two
algorithms within the HMAS. This prevents data losses in case one of the algorithms is
changes or interfered with. A change to the second algorithm exposes the data being
transmitted to risks such as data losses and hacking8.
The use of Hashing for Message Authentication and enhanced pseudorandom function values
in the message provides a more secure authentication that does not allow other computers on
the same network to access the data being transmitted.
The TLS provides a certificate authentication between nodes that ensures consistency in the
data being transmitted.
However, the TLS has the following shortcoming.
The process of the TLS handshake between the server and the client guarantees a slower
performance in the communication process. This slow performance is also evident in the
reloading of web pages. The TLS does not allow data caching hence the slow
communication. To address this limitation, simple web pages should be used.
Conclusions.
Transport layer security protocol is the most efficient web based data encryption protocol.
Because attacks get better with time, the TLS protocol is designed to allow modifications and
additions of more algorithms to increase the security protocol.
Case project 7.2: UTM comparison.
Introduction.
Unified threat management are tools that combine networking and security features to
provide secure functionality for businesses. These applications provide the security features
of the network against phishing, ransomware and other cybercrimes. UMT system can be
either virtual, cloud-based or hardware appliances.
8 Bajpai, P., Jain, V.K. and Akella, A.S., EchoStar Technologies LLC, 2014. Method and node for
employing network connections over a connectionless transport layer protocol. U.S. Patent 8,750,112.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
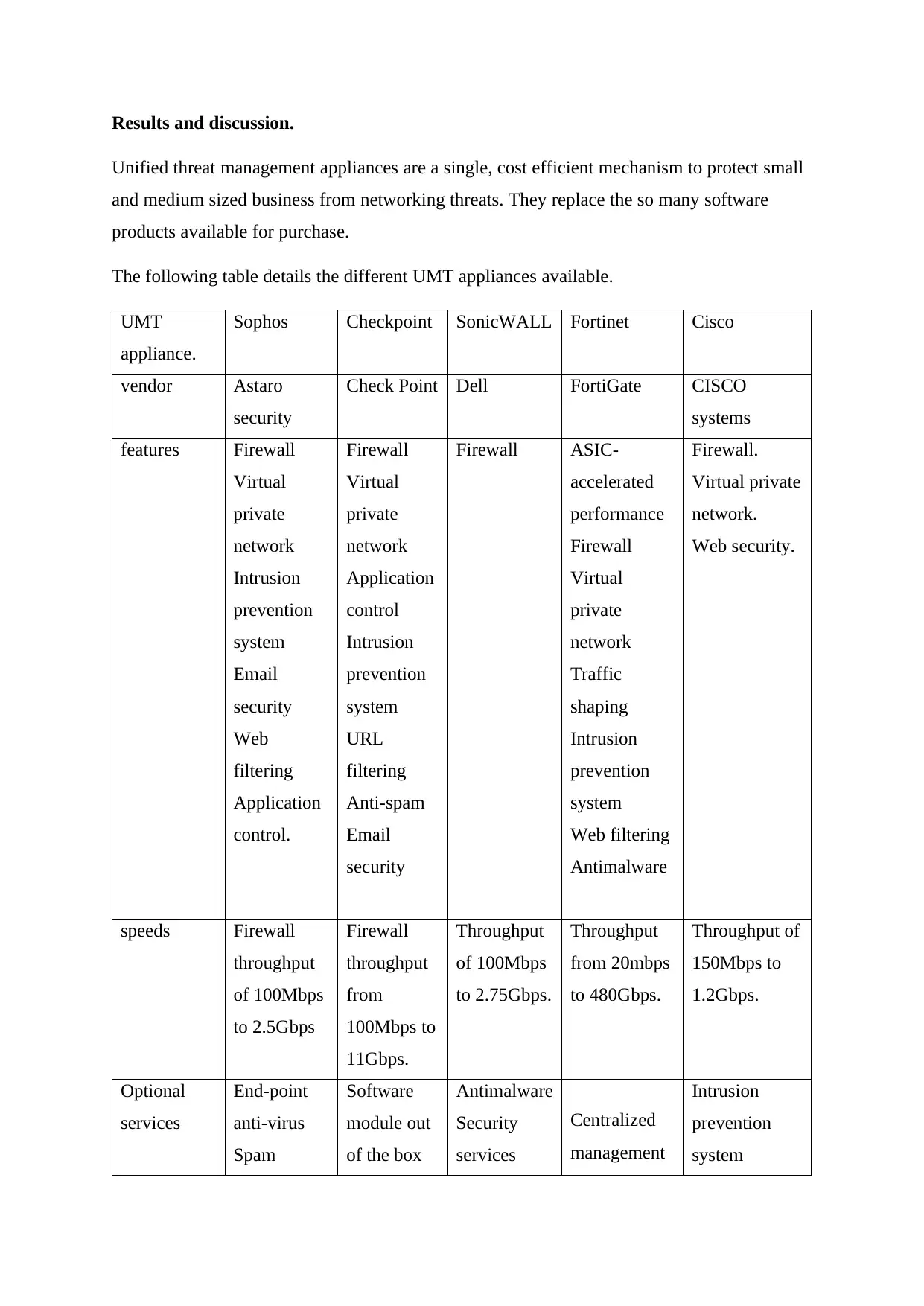
Results and discussion.
Unified threat management appliances are a single, cost efficient mechanism to protect small
and medium sized business from networking threats. They replace the so many software
products available for purchase.
The following table details the different UMT appliances available.
UMT
appliance.
Sophos Checkpoint SonicWALL Fortinet Cisco
vendor Astaro
security
Check Point Dell FortiGate CISCO
systems
features Firewall
Virtual
private
network
Intrusion
prevention
system
Email
security
Web
filtering
Application
control.
Firewall
Virtual
private
network
Application
control
Intrusion
prevention
system
URL
filtering
Anti-spam
Email
security
Firewall ASIC-
accelerated
performance
Firewall
Virtual
private
network
Traffic
shaping
Intrusion
prevention
system
Web filtering
Antimalware
Firewall.
Virtual private
network.
Web security.
speeds Firewall
throughput
of 100Mbps
to 2.5Gbps
Firewall
throughput
from
100Mbps to
11Gbps.
Throughput
of 100Mbps
to 2.75Gbps.
Throughput
from 20mbps
to 480Gbps.
Throughput of
150Mbps to
1.2Gbps.
Optional
services
End-point
anti-virus
Spam
Software
module out
of the box
Antimalware
Security
services
Centralized
management
Intrusion
prevention
system
Unified threat management appliances are a single, cost efficient mechanism to protect small
and medium sized business from networking threats. They replace the so many software
products available for purchase.
The following table details the different UMT appliances available.
UMT
appliance.
Sophos Checkpoint SonicWALL Fortinet Cisco
vendor Astaro
security
Check Point Dell FortiGate CISCO
systems
features Firewall
Virtual
private
network
Intrusion
prevention
system
security
Web
filtering
Application
control.
Firewall
Virtual
private
network
Application
control
Intrusion
prevention
system
URL
filtering
Anti-spam
security
Firewall ASIC-
accelerated
performance
Firewall
Virtual
private
network
Traffic
shaping
Intrusion
prevention
system
Web filtering
Antimalware
Firewall.
Virtual private
network.
Web security.
speeds Firewall
throughput
of 100Mbps
to 2.5Gbps
Firewall
throughput
from
100Mbps to
11Gbps.
Throughput
of 100Mbps
to 2.75Gbps.
Throughput
from 20mbps
to 480Gbps.
Throughput of
150Mbps to
1.2Gbps.
Optional
services
End-point
anti-virus
Spam
Software
module out
of the box
Antimalware
Security
services
Centralized
management
Intrusion
prevention
system
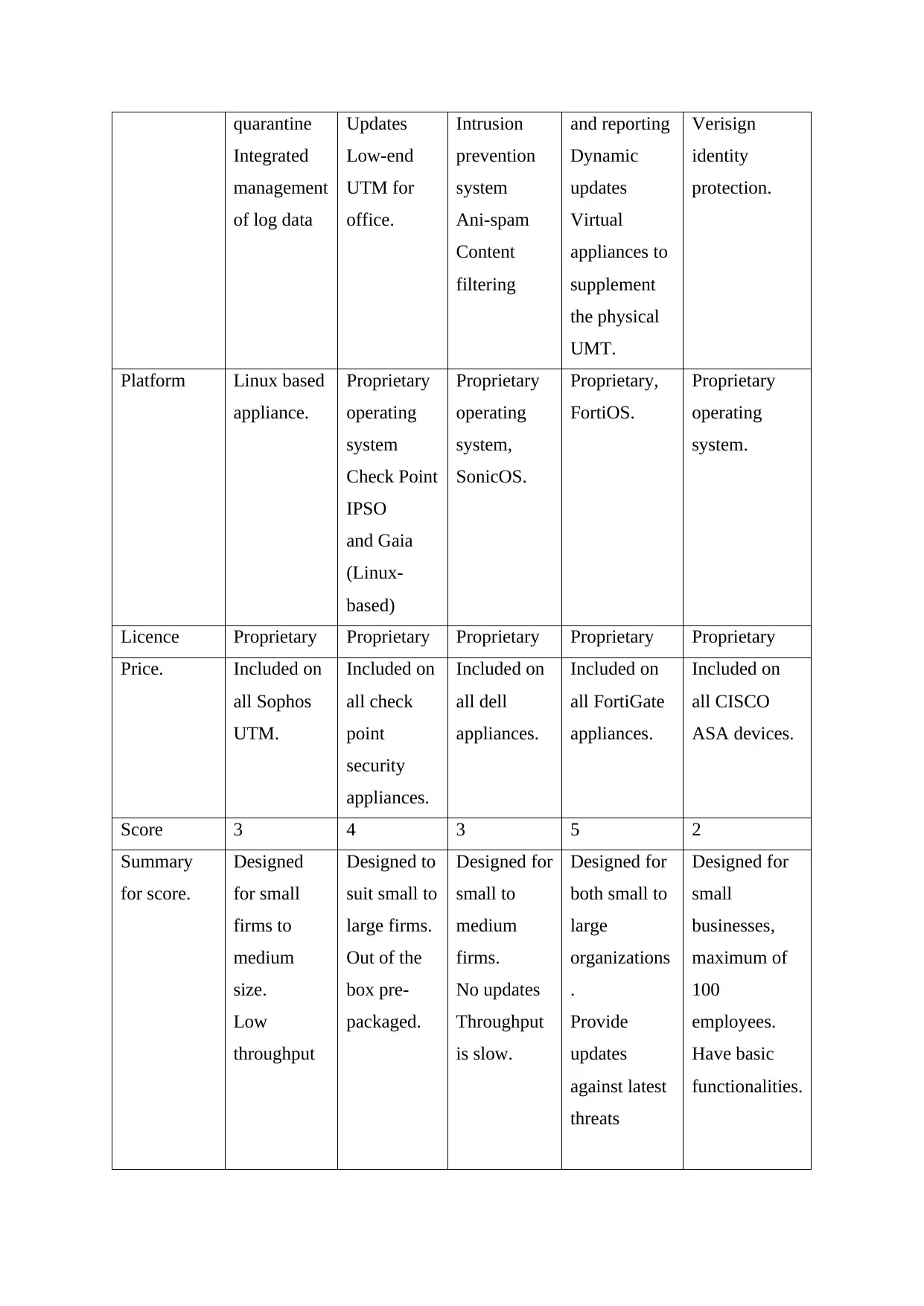
quarantine
Integrated
management
of log data
Updates
Low-end
UTM for
office.
Intrusion
prevention
system
Ani-spam
Content
filtering
and reporting
Dynamic
updates
Virtual
appliances to
supplement
the physical
UMT.
Verisign
identity
protection.
Platform Linux based
appliance.
Proprietary
operating
system
Check Point
IPSO
and Gaia
(Linux-
based)
Proprietary
operating
system,
SonicOS.
Proprietary,
FortiOS.
Proprietary
operating
system.
Licence Proprietary Proprietary Proprietary Proprietary Proprietary
Price. Included on
all Sophos
UTM.
Included on
all check
point
security
appliances.
Included on
all dell
appliances.
Included on
all FortiGate
appliances.
Included on
all CISCO
ASA devices.
Score 3 4 3 5 2
Summary
for score.
Designed
for small
firms to
medium
size.
Low
throughput
Designed to
suit small to
large firms.
Out of the
box pre-
packaged.
Designed for
small to
medium
firms.
No updates
Throughput
is slow.
Designed for
both small to
large
organizations
.
Provide
updates
against latest
threats
Designed for
small
businesses,
maximum of
100
employees.
Have basic
functionalities.
Integrated
management
of log data
Updates
Low-end
UTM for
office.
Intrusion
prevention
system
Ani-spam
Content
filtering
and reporting
Dynamic
updates
Virtual
appliances to
supplement
the physical
UMT.
Verisign
identity
protection.
Platform Linux based
appliance.
Proprietary
operating
system
Check Point
IPSO
and Gaia
(Linux-
based)
Proprietary
operating
system,
SonicOS.
Proprietary,
FortiOS.
Proprietary
operating
system.
Licence Proprietary Proprietary Proprietary Proprietary Proprietary
Price. Included on
all Sophos
UTM.
Included on
all check
point
security
appliances.
Included on
all dell
appliances.
Included on
all FortiGate
appliances.
Included on
all CISCO
ASA devices.
Score 3 4 3 5 2
Summary
for score.
Designed
for small
firms to
medium
size.
Low
throughput
Designed to
suit small to
large firms.
Out of the
box pre-
packaged.
Designed for
small to
medium
firms.
No updates
Throughput
is slow.
Designed for
both small to
large
organizations
.
Provide
updates
against latest
threats
Designed for
small
businesses,
maximum of
100
employees.
Have basic
functionalities.

Conclusion.
In the choice of the UMT appliance to use, various factors are used to decide what appliance
to purchase such as price, features, ease of deployment, speed and resources from the vendor.
Unified threat management appliances come in different packages, each suitable to the client
to enable them only pay for functionalities they are going to use. The list for the vendors
developing the unified threat management appliances is fairly friendly and therefore easy to
help the clients make a good choice.
In the choice of the UMT appliance to use, various factors are used to decide what appliance
to purchase such as price, features, ease of deployment, speed and resources from the vendor.
Unified threat management appliances come in different packages, each suitable to the client
to enable them only pay for functionalities they are going to use. The list for the vendors
developing the unified threat management appliances is fairly friendly and therefore easy to
help the clients make a good choice.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Bibliography
Schlyter, J. and Hoffman, P., 2012. The DNS-based authentication of named entities (DANE)
transport layer security (TLS) protocol: TLSA.
Schlyter, J. and Hoffman, P., 2012. The DNS-based authentication of named entities (DANE)
transport layer security (TLS) protocol: TLSA.
Funk, P. and Blake-Wilson, S., 2008. Extensible authentication protocol tunneled transport layer
security authenticated protocol version 0 (EAP-TTLSv0).
Igoe, K. and Solinas, J., 2009. AES Galois counter mode for the secure shell transport layer
protocol (No. RFC 5647).
Markham, T.R. and Heimerdinger, W., Honeywell International Inc, 2012. Physical security
management system. U.S. Patent 8,272,053.
Singh, A., Gopal, P.M., Bangalore, M.S. and Krishnan, R.S., Cisco Technology Inc, 2013. Physical
security triggered dynamic network authentication and authorization. U.S. Patent 8,549,584.
Wells, L.J., Camelio, J.A., Williams, C.B. and White, J., 2014. Cyber-physical security challenges in
manufacturing systems. Manufacturing Letters, 2(2), pp.74-77.
Schlyter, J. and Hoffman, P., 2012. The DNS-based authentication of named entities (DANE)
transport layer security (TLS) protocol: TLSA.
Schlyter, J. and Hoffman, P., 2012. The DNS-based authentication of named entities (DANE)
transport layer security (TLS) protocol: TLSA.
Funk, P. and Blake-Wilson, S., 2008. Extensible authentication protocol tunneled transport layer
security authenticated protocol version 0 (EAP-TTLSv0).
Igoe, K. and Solinas, J., 2009. AES Galois counter mode for the secure shell transport layer
protocol (No. RFC 5647).
Markham, T.R. and Heimerdinger, W., Honeywell International Inc, 2012. Physical security
management system. U.S. Patent 8,272,053.
Singh, A., Gopal, P.M., Bangalore, M.S. and Krishnan, R.S., Cisco Technology Inc, 2013. Physical
security triggered dynamic network authentication and authorization. U.S. Patent 8,549,584.
Wells, L.J., Camelio, J.A., Williams, C.B. and White, J., 2014. Cyber-physical security challenges in
manufacturing systems. Manufacturing Letters, 2(2), pp.74-77.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





