Anti-Virus and NMAP Scans
VerifiedAdded on 2023/06/01
|10
|1196
|286
AI Summary
This article discusses the use of Anti-Virus and NMAP Scans to secure networks. It explains how default Windows firewall and security settings can contribute to the inability to detect an attacker probing from inside the network. The article also explores the advantages and challenges of protecting cloud-hosted IaaS environments from malware and attacks. Finally, it provides tips for infrastructure administrators on how to use NMAP to monitor and control enterprise-grade networks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: ANTI VIRUS AND NMAP SCANS 1
Anti-Virus and NMAP Scans
Lucrecia V. Fuentes
CYB/205
November 5, 2018
Mr. Denis Brookers
Anti-Virus and NMAP Scans
Lucrecia V. Fuentes
CYB/205
November 5, 2018
Mr. Denis Brookers
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
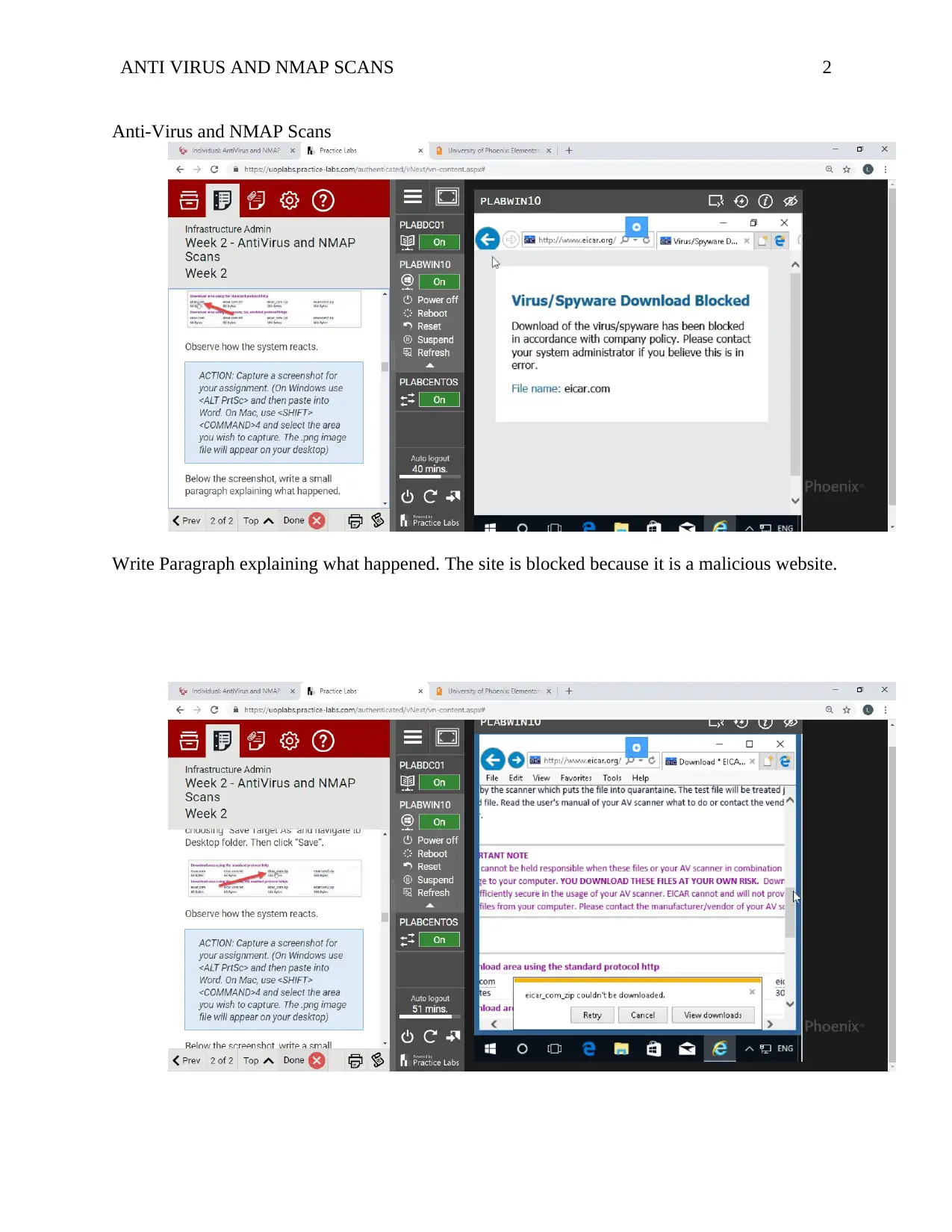
ANTI VIRUS AND NMAP SCANS 2
Anti-Virus and NMAP Scans
Write Paragraph explaining what happened. The site is blocked because it is a malicious website.
Anti-Virus and NMAP Scans
Write Paragraph explaining what happened. The site is blocked because it is a malicious website.
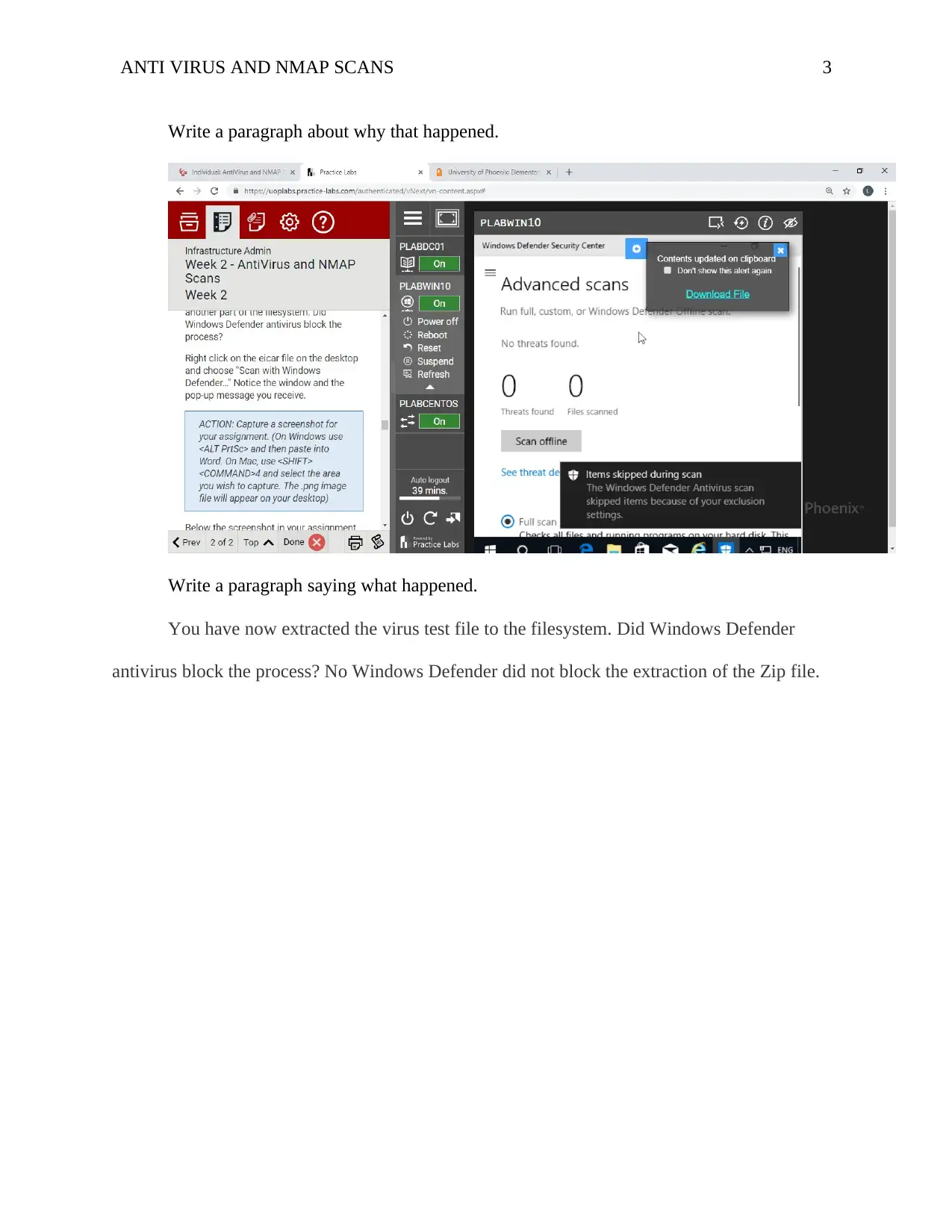
ANTI VIRUS AND NMAP SCANS 3
Write a paragraph about why that happened.
Write a paragraph saying what happened.
You have now extracted the virus test file to the filesystem. Did Windows Defender
antivirus block the process? No Windows Defender did not block the extraction of the Zip file.
Write a paragraph about why that happened.
Write a paragraph saying what happened.
You have now extracted the virus test file to the filesystem. Did Windows Defender
antivirus block the process? No Windows Defender did not block the extraction of the Zip file.
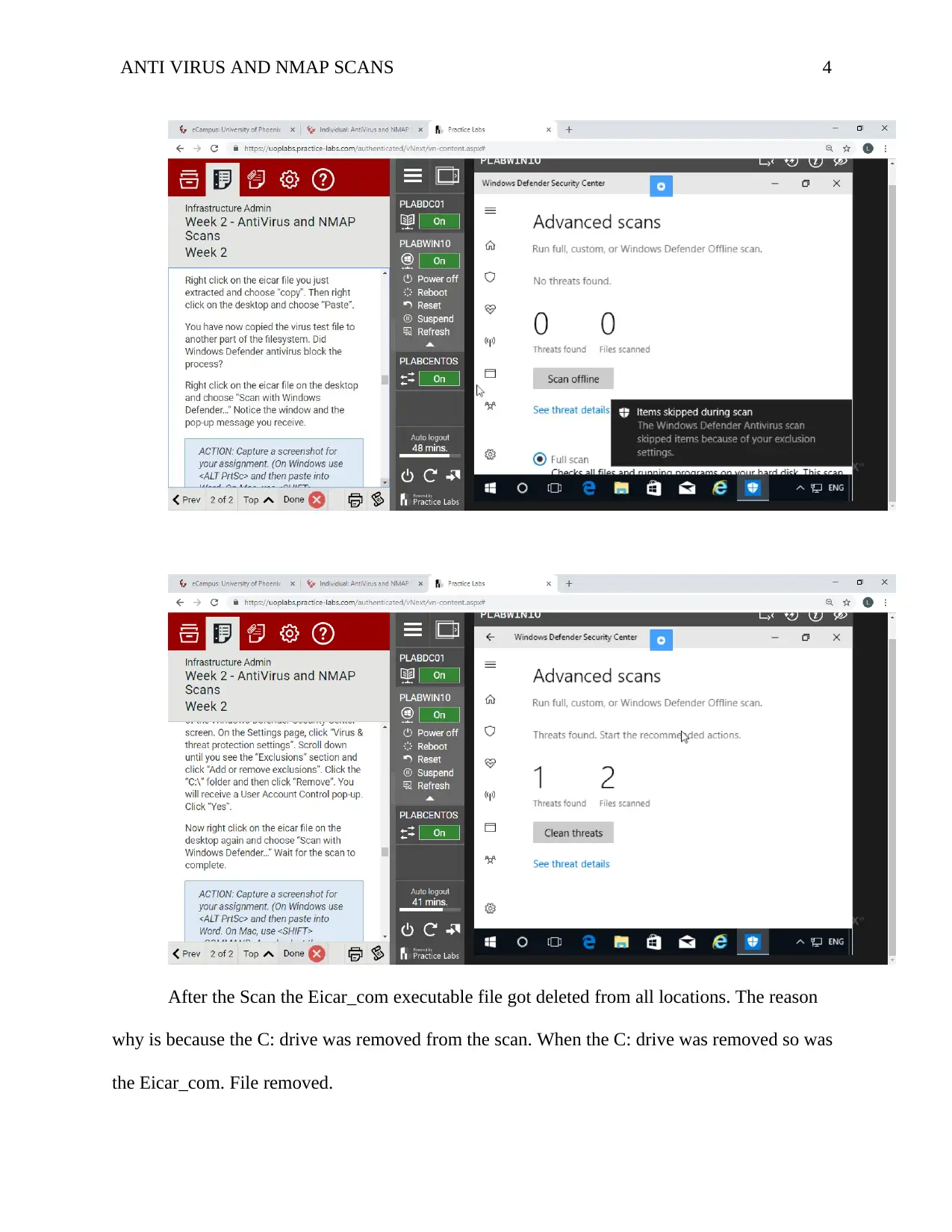
ANTI VIRUS AND NMAP SCANS 4
After the Scan the Eicar_com executable file got deleted from all locations. The reason
why is because the C: drive was removed from the scan. When the C: drive was removed so was
the Eicar_com. File removed.
After the Scan the Eicar_com executable file got deleted from all locations. The reason
why is because the C: drive was removed from the scan. When the C: drive was removed so was
the Eicar_com. File removed.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
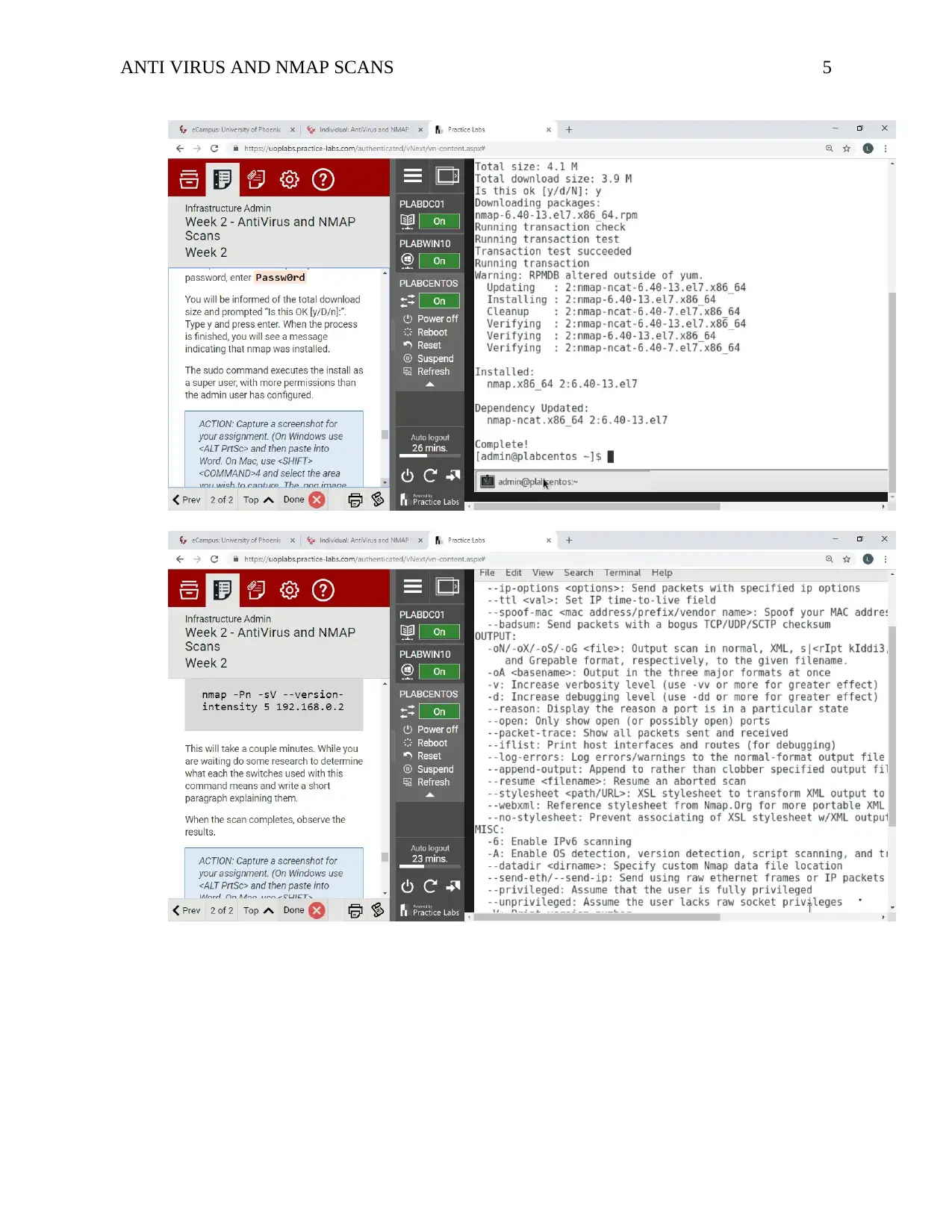
ANTI VIRUS AND NMAP SCANS 5
ANTI VIRUS AND NMAP SCANS 6
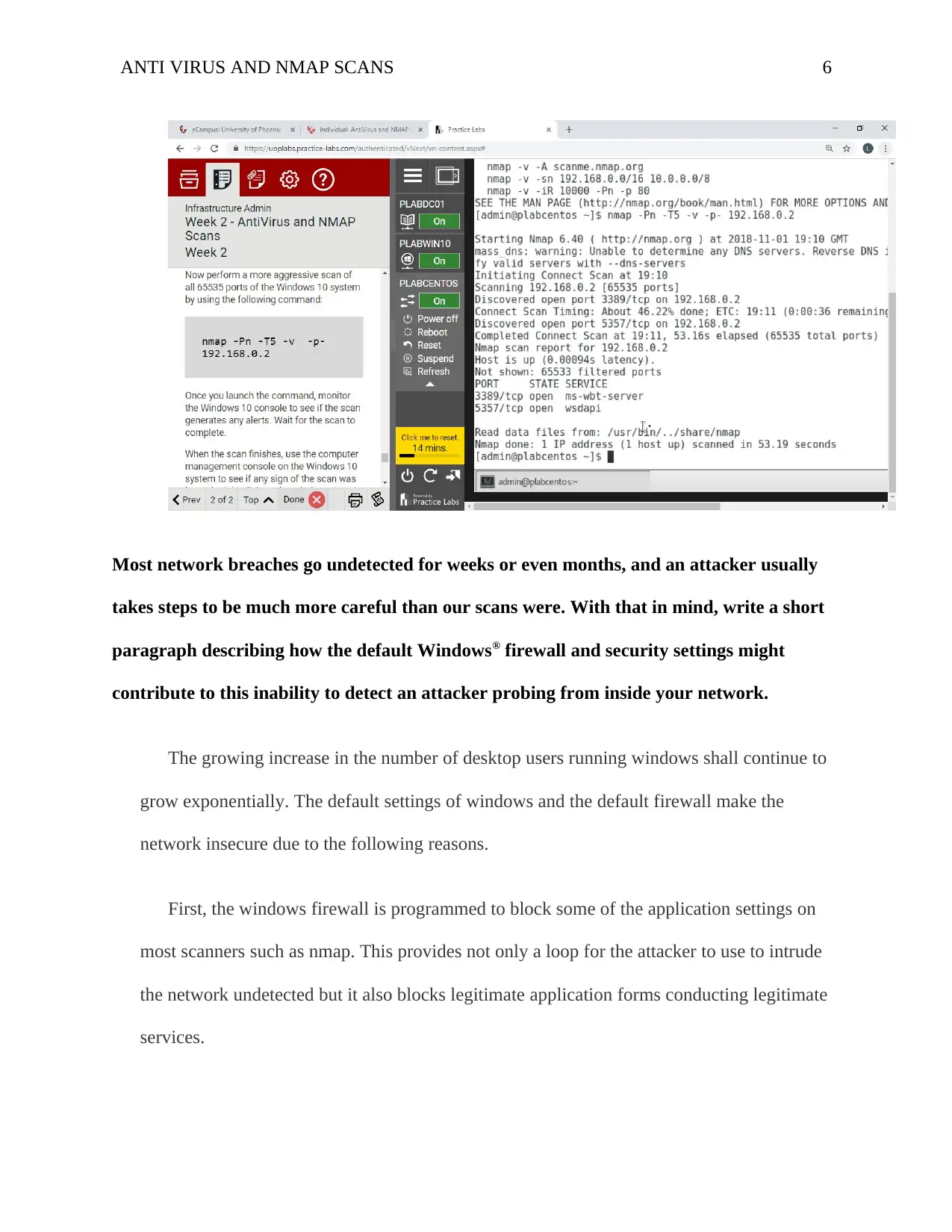
Most network breaches go undetected for weeks or even months, and an attacker usually
takes steps to be much more careful than our scans were. With that in mind, write a short
paragraph describing how the default Windows® firewall and security settings might
contribute to this inability to detect an attacker probing from inside your network.
The growing increase in the number of desktop users running windows shall continue to
grow exponentially. The default settings of windows and the default firewall make the
network insecure due to the following reasons.
First, the windows firewall is programmed to block some of the application settings on
most scanners such as nmap. This provides not only a loop for the attacker to use to intrude
the network undetected but it also blocks legitimate application forms conducting legitimate
services.
Most network breaches go undetected for weeks or even months, and an attacker usually
takes steps to be much more careful than our scans were. With that in mind, write a short
paragraph describing how the default Windows® firewall and security settings might
contribute to this inability to detect an attacker probing from inside your network.
The growing increase in the number of desktop users running windows shall continue to
grow exponentially. The default settings of windows and the default firewall make the
network insecure due to the following reasons.
First, the windows firewall is programmed to block some of the application settings on
most scanners such as nmap. This provides not only a loop for the attacker to use to intrude
the network undetected but it also blocks legitimate application forms conducting legitimate
services.

ANTI VIRUS AND NMAP SCANS 7
Secondly, the default firewall setting allows only blocking of inbound traffic and allows
the outbound traffic. This vulnerability can be exploited by an attacker who has gained
access from within the network and use the access to wreak havoc onto the operations of the
network. The difficult part is that the malicious traffic is amalgam with the legitimate traffic
and no rules exist to explicitly deny some outbound traffic.
Thirdly, the worst setting existing on any platform exist on windows where security
policies by default are weak making them easily bypassed by an insider job attack. Some
policies as simple as intrusion alerts are not enabled by default and requires an admin to
install third party software to provide the extra security control needed.
Last but not the least, the default permission for files and shares is unsecure as it gives
full access to the owner and everyone who has been shared the file. This can be used by an
attacker to launch attacks by sending malicious application to execute permission without
being noticed (Lyon, 2009).
This was just a single system on a local LAN. How much more complicated would this
process be for 100 computers? What about an enterprise with 10,000 computers on their
LAN/WAN?
The process process on 100 computers is generally the same as a single LAN however,
increasing the scope to 100000 computers on a WAN poses the complication of bypassing the
router security rules of to analyse remote computers. It theirfore needs a centralize security
focused server dedicated to scanning and monitoring of the network (Heninger, Durumeric,
Wustrow, & Halderman, 2012)
Secondly, the default firewall setting allows only blocking of inbound traffic and allows
the outbound traffic. This vulnerability can be exploited by an attacker who has gained
access from within the network and use the access to wreak havoc onto the operations of the
network. The difficult part is that the malicious traffic is amalgam with the legitimate traffic
and no rules exist to explicitly deny some outbound traffic.
Thirdly, the worst setting existing on any platform exist on windows where security
policies by default are weak making them easily bypassed by an insider job attack. Some
policies as simple as intrusion alerts are not enabled by default and requires an admin to
install third party software to provide the extra security control needed.
Last but not the least, the default permission for files and shares is unsecure as it gives
full access to the owner and everyone who has been shared the file. This can be used by an
attacker to launch attacks by sending malicious application to execute permission without
being noticed (Lyon, 2009).
This was just a single system on a local LAN. How much more complicated would this
process be for 100 computers? What about an enterprise with 10,000 computers on their
LAN/WAN?
The process process on 100 computers is generally the same as a single LAN however,
increasing the scope to 100000 computers on a WAN poses the complication of bypassing the
router security rules of to analyse remote computers. It theirfore needs a centralize security
focused server dedicated to scanning and monitoring of the network (Heninger, Durumeric,
Wustrow, & Halderman, 2012)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ANTI VIRUS AND NMAP SCANS 8
Consider a cloud-hosted Infrastructure as a Service (IaaS) environment with many new,
internet-accessible systems regularly being built and brought online. What advantages or
challenges might there be protecting such systems from malware and from attack?
The advantages is the centralized security protection where the server hosting the systems is
regularly checked for security vulnerabilities from a central point. However, different system has
different security settings hence it poses a challenge in providing a universally acceptable
security framework for the renting of the infrastructure by the cloud customer.
Finally, conclude this week's assignment with a page explaining how the same types of tools
demonstrated in this lab might be used by an infrastructure administrator to help secure
an environment.
Network monitoring is a key network administrator job as their key role is ensuring the
network is up and running. To do so, the admins need an automated approach to maintain
enterprise-grade networks with lots of end devices. This section explains how the admins can
employ nmap on enterprise-grade networks for successfully monitoring and control
First, the admin needs to set up a virtual machine which shall run the nmap. The platform
is solely the admins choice but would recommended Linux platform as the tools are equally
command line driven (Staniford, Hoagland, & McAlerney, 2002).
Once the installation is complete, the first step most probably is to scan the ports and
identify vulnerabilities associated with open ports. The command is as shown below,
Nmap –sP <target IP>
Consider a cloud-hosted Infrastructure as a Service (IaaS) environment with many new,
internet-accessible systems regularly being built and brought online. What advantages or
challenges might there be protecting such systems from malware and from attack?
The advantages is the centralized security protection where the server hosting the systems is
regularly checked for security vulnerabilities from a central point. However, different system has
different security settings hence it poses a challenge in providing a universally acceptable
security framework for the renting of the infrastructure by the cloud customer.
Finally, conclude this week's assignment with a page explaining how the same types of tools
demonstrated in this lab might be used by an infrastructure administrator to help secure
an environment.
Network monitoring is a key network administrator job as their key role is ensuring the
network is up and running. To do so, the admins need an automated approach to maintain
enterprise-grade networks with lots of end devices. This section explains how the admins can
employ nmap on enterprise-grade networks for successfully monitoring and control
First, the admin needs to set up a virtual machine which shall run the nmap. The platform
is solely the admins choice but would recommended Linux platform as the tools are equally
command line driven (Staniford, Hoagland, & McAlerney, 2002).
Once the installation is complete, the first step most probably is to scan the ports and
identify vulnerabilities associated with open ports. The command is as shown below,
Nmap –sP <target IP>

ANTI VIRUS AND NMAP SCANS 9
The nmap utility again can be used on an enterprise network to identify the key Operating
System being used by various end devices. The vulnerabilities on such Operating System can
be registered and used by the admin to harden the network by automating patches for the
same. To scan the operating system, the admin runs the following nmap command,
Nmpa -O
The admin can use the tool to identify vulnerabilities on the enterprise network by
conducting an attack on the network. His can be achieved by first cloning the nmap-vunners
from GitHub to be used in launching the attack.
To launch the attack, use the following command,
Nmpa –A --script vulners <IPrange>
The result will be a list of vulnerabilities within the network which the admin can fix
since the link to description n and documentation is given (Orebaugh & Pinkard, 2011).
The nmap utility again can be used on an enterprise network to identify the key Operating
System being used by various end devices. The vulnerabilities on such Operating System can
be registered and used by the admin to harden the network by automating patches for the
same. To scan the operating system, the admin runs the following nmap command,
Nmpa -O
The admin can use the tool to identify vulnerabilities on the enterprise network by
conducting an attack on the network. His can be achieved by first cloning the nmap-vunners
from GitHub to be used in launching the attack.
To launch the attack, use the following command,
Nmpa –A --script vulners <IPrange>
The result will be a list of vulnerabilities within the network which the admin can fix
since the link to description n and documentation is given (Orebaugh & Pinkard, 2011).

ANTI VIRUS AND NMAP SCANS 10
References
Heninger, N., Durumeric, Z., Wustrow, E., & Halderman, J. A. (2012). Mining Your Ps and Qs:
Detection of Widespread Weak Keys in Network Devices. In USENIX Security
Symposium (Vol. 8, p. 1).
Lyon, G. F. (2009). Nmap network scanning: The official Nmap project guide to network
discovery and security scanning. Insecure.
Orebaugh, A., & Pinkard, B. (2011). Nmap in the enterprise: your guide to network scanning.
Elsevier.
Staniford, S., Hoagland, J. A., & McAlerney, J. M. (2002). Practical automated detection of
stealthy portscans. Journal of Computer Security, 10(1–2), 105–136.
References
Heninger, N., Durumeric, Z., Wustrow, E., & Halderman, J. A. (2012). Mining Your Ps and Qs:
Detection of Widespread Weak Keys in Network Devices. In USENIX Security
Symposium (Vol. 8, p. 1).
Lyon, G. F. (2009). Nmap network scanning: The official Nmap project guide to network
discovery and security scanning. Insecure.
Orebaugh, A., & Pinkard, B. (2011). Nmap in the enterprise: your guide to network scanning.
Elsevier.
Staniford, S., Hoagland, J. A., & McAlerney, J. M. (2002). Practical automated detection of
stealthy portscans. Journal of Computer Security, 10(1–2), 105–136.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


