Network Designing and Technologies: A Case Study
VerifiedAdded on 2023/01/05
|14
|2750
|20
AI Summary
This article discusses the process of network designing and the technologies and components chosen for a hospital network. It also explores the efficiency in designing, testing tactics, and the methodology used in project planning.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Assesment
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
Network designing..................................................................................................................1
Technologies and Components chosen:.................................................................................2
Efficiency in designing:..........................................................................................................5
Testing and results:.................................................................................................................7
Refection of methodology used while project planning.........................................................9
CONCLUSION..............................................................................................................................10
References:.....................................................................................................................................11
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
Network designing..................................................................................................................1
Technologies and Components chosen:.................................................................................2
Efficiency in designing:..........................................................................................................5
Testing and results:.................................................................................................................7
Refection of methodology used while project planning.........................................................9
CONCLUSION..............................................................................................................................10
References:.....................................................................................................................................11


INTRODUCTION
Network is defined as a computer network where a set of systems uses group of common
protocols through digital interconnections for the aim of sharing various resources like hardware,
software and network devices which are located and provided by the nodes of the network
(Network, 2020). The following discussions is based on networking design, explanation of
technologies and the chosen components, justification of efficiency in designing network, testing
tactics and resulting the same and finally the conclusion of methodology used while planning the
scenarios.
MAIN BODY
Network designing
Completion is finally done on all the details, now the implementation of networking is to
be done. Due to COVID-19, there is a requirement of full health safety, so the expansion is
highly needed in the network. The expansion and implementation of networking geography can
give the hospital a better merit and refinement to the hospital's good speed of internet
connections and most importantly the data security (Ahn and Jeong, 2018). Complete design that
was initially done is figured below:
1
Network is defined as a computer network where a set of systems uses group of common
protocols through digital interconnections for the aim of sharing various resources like hardware,
software and network devices which are located and provided by the nodes of the network
(Network, 2020). The following discussions is based on networking design, explanation of
technologies and the chosen components, justification of efficiency in designing network, testing
tactics and resulting the same and finally the conclusion of methodology used while planning the
scenarios.
MAIN BODY
Network designing
Completion is finally done on all the details, now the implementation of networking is to
be done. Due to COVID-19, there is a requirement of full health safety, so the expansion is
highly needed in the network. The expansion and implementation of networking geography can
give the hospital a better merit and refinement to the hospital's good speed of internet
connections and most importantly the data security (Ahn and Jeong, 2018). Complete design that
was initially done is figured below:
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
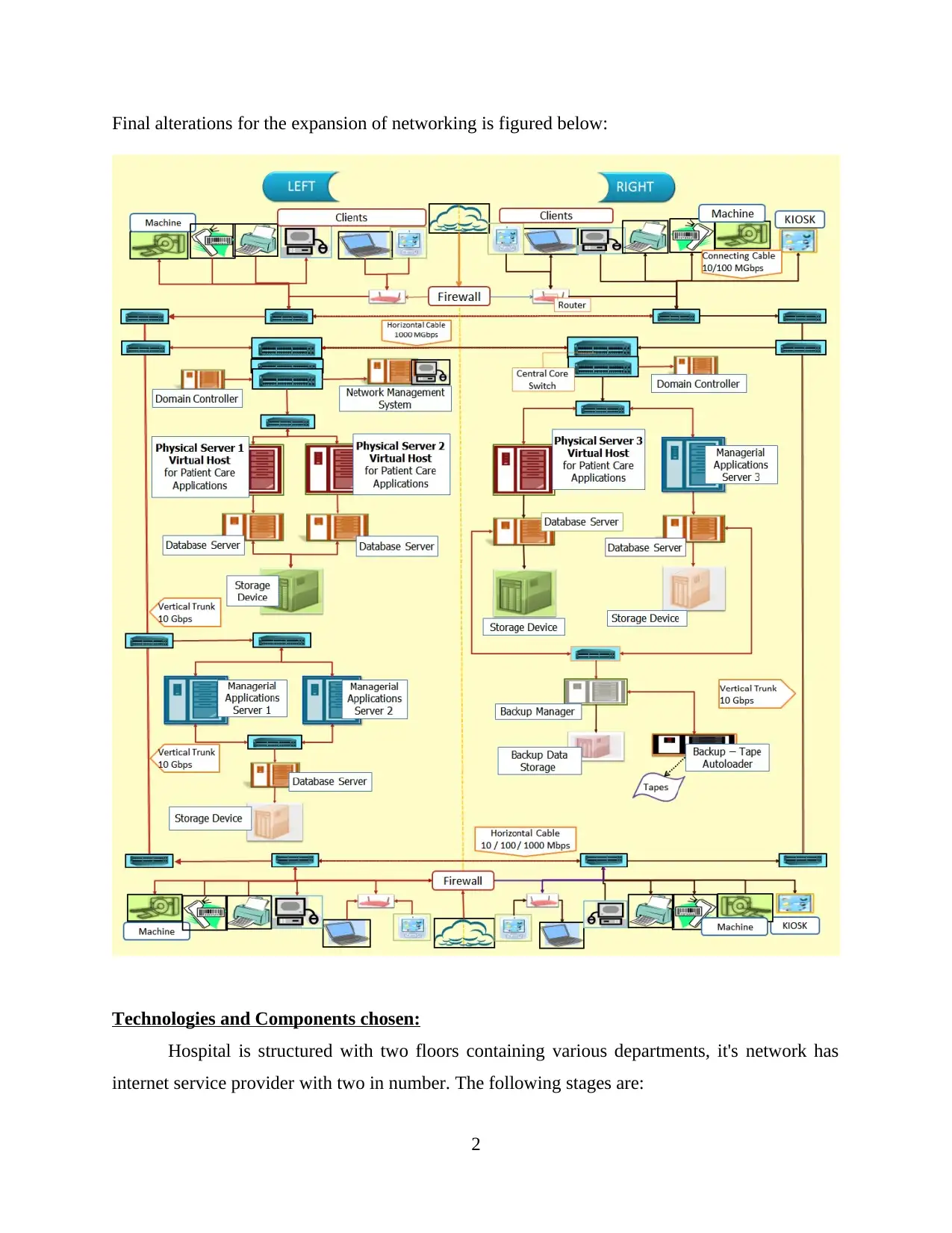
Final alterations for the expansion of networking is figured below:
Technologies and Components chosen:
Hospital is structured with two floors containing various departments, it's network has
internet service provider with two in number. The following stages are:
2
Technologies and Components chosen:
Hospital is structured with two floors containing various departments, it's network has
internet service provider with two in number. The following stages are:
2

There is a connection of ISP through which proxy server is connected to firewall
followed by router.
Servers are interconnected with the switches which are Cisco catalyst 2960 48 ports.
Cisco 2005 consist excellent features like ACL and better security. 2960 Cisco switches
also contains copper and fibre gigabit Ethernet uplink.
Switches one and two are connected with firewall. Cost effective sonic firewall has been
chosen here for the healthcare security. It is considered as high security firewall because
it can easily detect various types of malware, moreover minimum time taken by it to
prevent the next attacks by viruses and block them.
There is an intermediate between core switches and access switches which is Fibre optic
solutions which are majorly connected to the distribution switches one and two
(Boholano, 2017).
Servers included in this are web, application, storage, file, print, PACS and HIS servers.
Switches one, two, three, four, five and six are connected through IP phones and
desktops.
Components used here: Virtualisation: Virtual machines are generated through virtual machine ware workstation
pro fifteen software. DHCP server, active directory and domain controller is intalled in
virtual machines in windows 2012. Generation of local domain is 'nimmy.local'. DHCP Server: It stands for Dynamic Host Configuration Protocol, After it's
configuration, it is observed that IP addresses are assigned automatically with efficiency
for the various networks elements like IT, engineering and biomedical components that
are connected to the network of hospital. Groups and network users: Hospital has assigned every single desktop to each worker
working there with individual user account consisting username and password to log in to
their systems. Some user accounts are the member of single user groups and some are the
part of two or more user groups like security group or distribution (Comer, 2018). Directory server of file structure and rights of network user: All the departments in
hospital are having their own individual folders containing working details. Only
department members are having rights to access those files and folders. There are
3
followed by router.
Servers are interconnected with the switches which are Cisco catalyst 2960 48 ports.
Cisco 2005 consist excellent features like ACL and better security. 2960 Cisco switches
also contains copper and fibre gigabit Ethernet uplink.
Switches one and two are connected with firewall. Cost effective sonic firewall has been
chosen here for the healthcare security. It is considered as high security firewall because
it can easily detect various types of malware, moreover minimum time taken by it to
prevent the next attacks by viruses and block them.
There is an intermediate between core switches and access switches which is Fibre optic
solutions which are majorly connected to the distribution switches one and two
(Boholano, 2017).
Servers included in this are web, application, storage, file, print, PACS and HIS servers.
Switches one, two, three, four, five and six are connected through IP phones and
desktops.
Components used here: Virtualisation: Virtual machines are generated through virtual machine ware workstation
pro fifteen software. DHCP server, active directory and domain controller is intalled in
virtual machines in windows 2012. Generation of local domain is 'nimmy.local'. DHCP Server: It stands for Dynamic Host Configuration Protocol, After it's
configuration, it is observed that IP addresses are assigned automatically with efficiency
for the various networks elements like IT, engineering and biomedical components that
are connected to the network of hospital. Groups and network users: Hospital has assigned every single desktop to each worker
working there with individual user account consisting username and password to log in to
their systems. Some user accounts are the member of single user groups and some are the
part of two or more user groups like security group or distribution (Comer, 2018). Directory server of file structure and rights of network user: All the departments in
hospital are having their own individual folders containing working details. Only
department members are having rights to access those files and folders. There are
3
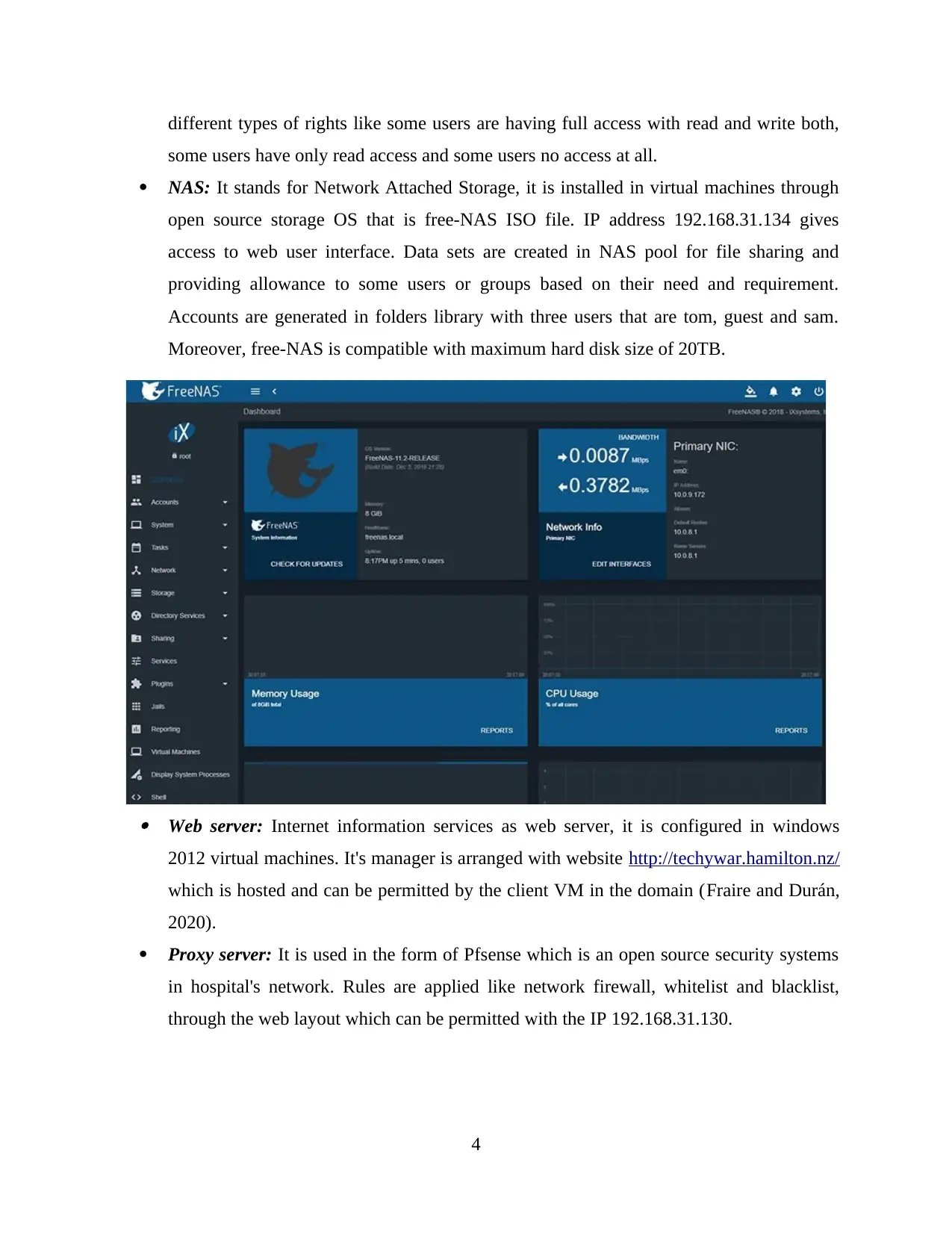
different types of rights like some users are having full access with read and write both,
some users have only read access and some users no access at all.
NAS: It stands for Network Attached Storage, it is installed in virtual machines through
open source storage OS that is free-NAS ISO file. IP address 192.168.31.134 gives
access to web user interface. Data sets are created in NAS pool for file sharing and
providing allowance to some users or groups based on their need and requirement.
Accounts are generated in folders library with three users that are tom, guest and sam.
Moreover, free-NAS is compatible with maximum hard disk size of 20TB.
Web server: Internet information services as web server, it is configured in windows
2012 virtual machines. It's manager is arranged with website http://techywar.hamilton.nz/
which is hosted and can be permitted by the client VM in the domain (Fraire and Durán,
2020).
Proxy server: It is used in the form of Pfsense which is an open source security systems
in hospital's network. Rules are applied like network firewall, whitelist and blacklist,
through the web layout which can be permitted with the IP 192.168.31.130.
4
some users have only read access and some users no access at all.
NAS: It stands for Network Attached Storage, it is installed in virtual machines through
open source storage OS that is free-NAS ISO file. IP address 192.168.31.134 gives
access to web user interface. Data sets are created in NAS pool for file sharing and
providing allowance to some users or groups based on their need and requirement.
Accounts are generated in folders library with three users that are tom, guest and sam.
Moreover, free-NAS is compatible with maximum hard disk size of 20TB.
Web server: Internet information services as web server, it is configured in windows
2012 virtual machines. It's manager is arranged with website http://techywar.hamilton.nz/
which is hosted and can be permitted by the client VM in the domain (Fraire and Durán,
2020).
Proxy server: It is used in the form of Pfsense which is an open source security systems
in hospital's network. Rules are applied like network firewall, whitelist and blacklist,
through the web layout which can be permitted with the IP 192.168.31.130.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Efficiency in designing:
There are many factors included to attain a cost-effective designing of network said by
Smith 2001. Those factors must be checked because it is not scanned properly can result in
excessive expenses and execution which can be highly useless. Efficient expense can be
5
There are many factors included to attain a cost-effective designing of network said by
Smith 2001. Those factors must be checked because it is not scanned properly can result in
excessive expenses and execution which can be highly useless. Efficient expense can be
5

achieved by SAS which are scalability, availability and security are the necessary components in
designing of network. All the delays, security, verification in the framework must be recognised
and scanned under feasibility criteria. They are generally:
After using the log in account of a user, make sure that it must be log out so that any
other user don't make a use of that logged in account positively or negatively.
It is important that not to share username and password to any other user for security
purpose (Li, Ota and Dong, 2018).
Log in password must be authenticated so that any other user could not look into it in any
way.
Make sure that there should not be unauthorised permission to files in a system.
Virus can attack to the system if unsecure sited are accessed in any way.
This is important to ensure that giving data to outsiders can be the great threat of data
security until and unless hospital does not give any allowance to the user. This is to ensure that unapproved software should not be installed I the hospital's systems
as it can affect the network security which can be unsafe for the staff and customers
details.
Meeting of the user needs and requirements:
The delay in network in occupied times is holding back the care of the patient and the
complaints are received by senior staff regarding the delayed revert of the HIS(Hospital
Information System). This is due to the lack of bandwidth in a hospital. The application like
gynaecology, radiology and many more utilizes a good range of bandwidth during imaging and
scanning, they placed in all the department of various types. Moreover, different sectors of the
hospital is requiring the advanced technological components for the betterment of the patient's
care and hospital's services. This can create a more load on the networking part, so to sort out
this problem, ISP is needed which is a larger bandwidth network. The information and data that
are to be navigated among the clinics is always private and should never be attained by any
unauthorised user or group of staffs. Therefore, medical records are having data privacy and
security which are of most important that can be enhanced by this framework. They are seeing to
utilize encrypted data for the security of patient's private information (Meishar-Tal and Pieterse,
2017).
6
designing of network. All the delays, security, verification in the framework must be recognised
and scanned under feasibility criteria. They are generally:
After using the log in account of a user, make sure that it must be log out so that any
other user don't make a use of that logged in account positively or negatively.
It is important that not to share username and password to any other user for security
purpose (Li, Ota and Dong, 2018).
Log in password must be authenticated so that any other user could not look into it in any
way.
Make sure that there should not be unauthorised permission to files in a system.
Virus can attack to the system if unsecure sited are accessed in any way.
This is important to ensure that giving data to outsiders can be the great threat of data
security until and unless hospital does not give any allowance to the user. This is to ensure that unapproved software should not be installed I the hospital's systems
as it can affect the network security which can be unsafe for the staff and customers
details.
Meeting of the user needs and requirements:
The delay in network in occupied times is holding back the care of the patient and the
complaints are received by senior staff regarding the delayed revert of the HIS(Hospital
Information System). This is due to the lack of bandwidth in a hospital. The application like
gynaecology, radiology and many more utilizes a good range of bandwidth during imaging and
scanning, they placed in all the department of various types. Moreover, different sectors of the
hospital is requiring the advanced technological components for the betterment of the patient's
care and hospital's services. This can create a more load on the networking part, so to sort out
this problem, ISP is needed which is a larger bandwidth network. The information and data that
are to be navigated among the clinics is always private and should never be attained by any
unauthorised user or group of staffs. Therefore, medical records are having data privacy and
security which are of most important that can be enhanced by this framework. They are seeing to
utilize encrypted data for the security of patient's private information (Meishar-Tal and Pieterse,
2017).
6

Testing and results:
DHCP Server
Testing: It's addresses are instinctive by the client's systems attached in the organization's
internal domain. The extent is provided in the bandwidth of 192.168.1.2 – 192.168.1.100.
Specified router and domain name system are provided as 192.168.1.1. IP addresses in the span
of 192.168.1.20 – 192.168.1.30 are kept out in the DHCP because it can be allotted inertly.
Result: Pass
Domain Controller
Testing: The devices in the hospital are connected to the internal domain and can call out the
domain as nimmy.local.
Result: Pass
File structure, server and rights of user: Several network sector's folders are generated
through which the individual teammates can have permissions like modify access, read
only and full access. For example, in medical folder only medicines can have allowance.
No other sector workforce can have permission to access their data and information
(Nikulchev, Ilin, Bubnov and Mateshuk, 2017).
Testing: By calling out the server of the file
Result: Call out successful: Pass
7
DHCP Server
Testing: It's addresses are instinctive by the client's systems attached in the organization's
internal domain. The extent is provided in the bandwidth of 192.168.1.2 – 192.168.1.100.
Specified router and domain name system are provided as 192.168.1.1. IP addresses in the span
of 192.168.1.20 – 192.168.1.30 are kept out in the DHCP because it can be allotted inertly.
Result: Pass
Domain Controller
Testing: The devices in the hospital are connected to the internal domain and can call out the
domain as nimmy.local.
Result: Pass
File structure, server and rights of user: Several network sector's folders are generated
through which the individual teammates can have permissions like modify access, read
only and full access. For example, in medical folder only medicines can have allowance.
No other sector workforce can have permission to access their data and information
(Nikulchev, Ilin, Bubnov and Mateshuk, 2017).
Testing: By calling out the server of the file
Result: Call out successful: Pass
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
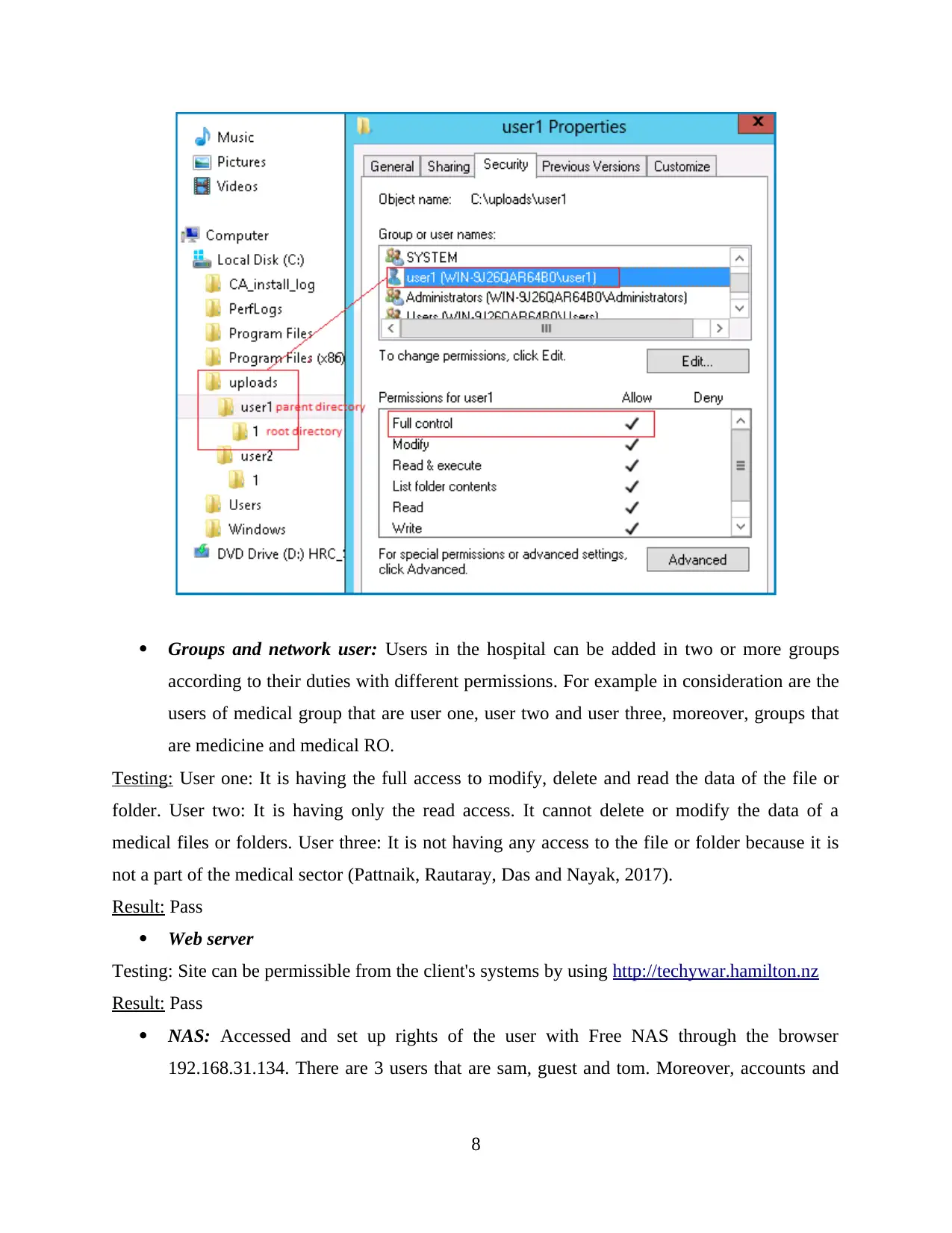
Groups and network user: Users in the hospital can be added in two or more groups
according to their duties with different permissions. For example in consideration are the
users of medical group that are user one, user two and user three, moreover, groups that
are medicine and medical RO.
Testing: User one: It is having the full access to modify, delete and read the data of the file or
folder. User two: It is having only the read access. It cannot delete or modify the data of a
medical files or folders. User three: It is not having any access to the file or folder because it is
not a part of the medical sector (Pattnaik, Rautaray, Das and Nayak, 2017).
Result: Pass
Web server
Testing: Site can be permissible from the client's systems by using http://techywar.hamilton.nz
Result: Pass
NAS: Accessed and set up rights of the user with Free NAS through the browser
192.168.31.134. There are 3 users that are sam, guest and tom. Moreover, accounts and
8
according to their duties with different permissions. For example in consideration are the
users of medical group that are user one, user two and user three, moreover, groups that
are medicine and medical RO.
Testing: User one: It is having the full access to modify, delete and read the data of the file or
folder. User two: It is having only the read access. It cannot delete or modify the data of a
medical files or folders. User three: It is not having any access to the file or folder because it is
not a part of the medical sector (Pattnaik, Rautaray, Das and Nayak, 2017).
Result: Pass
Web server
Testing: Site can be permissible from the client's systems by using http://techywar.hamilton.nz
Result: Pass
NAS: Accessed and set up rights of the user with Free NAS through the browser
192.168.31.134. There are 3 users that are sam, guest and tom. Moreover, accounts and
8

media teams with accordance to allowance are generated. There are several add ons data
information are generated through rights of user permissions.
Testing: Client drive can save the user data through dataset. Sam is having only access to read in
accounts file or folder with hard drive of size 20GB whereas Tom is not having any access such.
It is having full permission for the media library file or folder whereas Sam is having a only read
access for the same. Guest is having full rights to access the file or folder (Pooch, 2018).
Result: Pass
Proxy server
Testing: Internet access for client: WAN adaptor is used by the client to access the web browser.
Working traffic graphs: Proxy is used by client to access the websites. Configurations of proxy
server were facing issues while whitelisting and blacklisting of sites has been a difficult errors
for sites..
Result: Pass
Hence, according to the results, although the proxy servers were not working effectively or
efficiently, there has been a usage of firewalls to prevent the network of hospital from hackers.
Choking of unauthorized sites by whitelisting or blacklisting them were also managed by the
advanced version of Sonic wall. Moreover, malware problems were recognised at ease, and
finally the network of IT was fixed after the fixation of proxy servers were done (Yan and
McKeown, 2017).
Refection of methodology used while project planning
The selection of the project ideology is graceful because it is the kind practice for the
environment of hospital as it assist in looping of development procedure. In this representation,
testing actions are at the same time with development part. This procedure allows adaptation
among managers, engineers and customers. There is a group of four members. Since because of
COVID-19, campuses are closed and there are classes through online sessions with Zoom app.
Division of project is equally among all the members like 1st member is responsible for virtual
machines, clients and domain controller. 2nd member is responsible to ensure that network users
or teams, file sever and network storage with framework and rights of the user. The 3rd and 4th
members is responsible for DHCP, proxy and web servers. The work is to be achieved are
tracked through a zoom, Trello and many more. This was helpful because every body was
knowing about each other's work and updating regarding the tasks which are accomplished
9
information are generated through rights of user permissions.
Testing: Client drive can save the user data through dataset. Sam is having only access to read in
accounts file or folder with hard drive of size 20GB whereas Tom is not having any access such.
It is having full permission for the media library file or folder whereas Sam is having a only read
access for the same. Guest is having full rights to access the file or folder (Pooch, 2018).
Result: Pass
Proxy server
Testing: Internet access for client: WAN adaptor is used by the client to access the web browser.
Working traffic graphs: Proxy is used by client to access the websites. Configurations of proxy
server were facing issues while whitelisting and blacklisting of sites has been a difficult errors
for sites..
Result: Pass
Hence, according to the results, although the proxy servers were not working effectively or
efficiently, there has been a usage of firewalls to prevent the network of hospital from hackers.
Choking of unauthorized sites by whitelisting or blacklisting them were also managed by the
advanced version of Sonic wall. Moreover, malware problems were recognised at ease, and
finally the network of IT was fixed after the fixation of proxy servers were done (Yan and
McKeown, 2017).
Refection of methodology used while project planning
The selection of the project ideology is graceful because it is the kind practice for the
environment of hospital as it assist in looping of development procedure. In this representation,
testing actions are at the same time with development part. This procedure allows adaptation
among managers, engineers and customers. There is a group of four members. Since because of
COVID-19, campuses are closed and there are classes through online sessions with Zoom app.
Division of project is equally among all the members like 1st member is responsible for virtual
machines, clients and domain controller. 2nd member is responsible to ensure that network users
or teams, file sever and network storage with framework and rights of the user. The 3rd and 4th
members is responsible for DHCP, proxy and web servers. The work is to be achieved are
tracked through a zoom, Trello and many more. This was helpful because every body was
knowing about each other's work and updating regarding the tasks which are accomplished
9

trough software or physically. Web connection of one of the group members was improperly
working. So there were problems while working with him as of poor web connection because it
cannot manage 2 VMs at the same time. Therefore, divisions of portions has to be done to assist
him and accomplish the project with full effectiveness and efficiently.
CONCLUSION
Success of the project went like this: Firstly planned to use Linux but for the time being
it was found problematic to utilise as it was not having feature of user friendly type. Therefore,
later on, windows server is being used. There was a learning outcomes in a project except proxy
servers. Because some issues were found with proxy arrangements, because of the Sonic wall,
the project was safe from hackers. The completion of the project is more easier with a great team
and with appropriate communication among the members. There were brainstorming and group
discussions to share and contribute with the innovative and creative ideas.
10
working. So there were problems while working with him as of poor web connection because it
cannot manage 2 VMs at the same time. Therefore, divisions of portions has to be done to assist
him and accomplish the project with full effectiveness and efficiently.
CONCLUSION
Success of the project went like this: Firstly planned to use Linux but for the time being
it was found problematic to utilise as it was not having feature of user friendly type. Therefore,
later on, windows server is being used. There was a learning outcomes in a project except proxy
servers. Because some issues were found with proxy arrangements, because of the Sonic wall,
the project was safe from hackers. The completion of the project is more easier with a great team
and with appropriate communication among the members. There were brainstorming and group
discussions to share and contribute with the innovative and creative ideas.
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References:
Books and Journals:
Ahn, D.J. and Jeong, J., 2018. A PMIPv6-based user mobility pattern scheme for SDN-defined
smart factory networking. Procedia computer science, 134, pp.235-242.
Boholano, H., 2017. Smart social networking: 21st century teaching and learning
skills. Research in Pedagogy. 7(1). pp.21-29.
Comer, D.E., 2018. The Internet book: everything you need to know about computer networking
and how the Internet works. CRC Press.
Fraire, J.A. and Durán, J.E., 2020. Revising Computer Science Networking Hands-On Courses
in the Context of the Future Internet. IEEE Transactions on Education.
Li, H., Ota, K. and Dong, M., 2018. ECCN: Orchestration of edge-centric computing and
content-centric networking in the 5G radio access network. IEEE Wireless
Communications. 25(3). pp.88-93.
Meishar-Tal, H. and Pieterse, E., 2017. Why do academics use academic social networking
sites?. International Review of Research in Open and Distributed Learning. 18(1). pp.1-
22.
Nikulchev, E., Ilin, D., Bubnov, G. and Mateshuk, E., 2017. Scalable service for predictive
learning based on the professional social networking sites. International Journal of
Advanced Computer Science and Applications. 8(5).
Pattnaik, P.K., Rautaray, S.S., Das, H. and Nayak, J., 2017. Progress in computing, analytics and
networking. Proceedings of ICCAN, 710.
Pooch, U.W., 2018. Telecommunications and Networking. CRC Press.
Yan, L. and McKeown, N., 2017. Learning networking by reproducing research results. ACM
SIGCOMM Computer Communication Review. 47(2). pp.19-26.
Online:
Network. 2020. Available through <https://www.techopedia.com/definition/5537/network>./
11
Books and Journals:
Ahn, D.J. and Jeong, J., 2018. A PMIPv6-based user mobility pattern scheme for SDN-defined
smart factory networking. Procedia computer science, 134, pp.235-242.
Boholano, H., 2017. Smart social networking: 21st century teaching and learning
skills. Research in Pedagogy. 7(1). pp.21-29.
Comer, D.E., 2018. The Internet book: everything you need to know about computer networking
and how the Internet works. CRC Press.
Fraire, J.A. and Durán, J.E., 2020. Revising Computer Science Networking Hands-On Courses
in the Context of the Future Internet. IEEE Transactions on Education.
Li, H., Ota, K. and Dong, M., 2018. ECCN: Orchestration of edge-centric computing and
content-centric networking in the 5G radio access network. IEEE Wireless
Communications. 25(3). pp.88-93.
Meishar-Tal, H. and Pieterse, E., 2017. Why do academics use academic social networking
sites?. International Review of Research in Open and Distributed Learning. 18(1). pp.1-
22.
Nikulchev, E., Ilin, D., Bubnov, G. and Mateshuk, E., 2017. Scalable service for predictive
learning based on the professional social networking sites. International Journal of
Advanced Computer Science and Applications. 8(5).
Pattnaik, P.K., Rautaray, S.S., Das, H. and Nayak, J., 2017. Progress in computing, analytics and
networking. Proceedings of ICCAN, 710.
Pooch, U.W., 2018. Telecommunications and Networking. CRC Press.
Yan, L. and McKeown, N., 2017. Learning networking by reproducing research results. ACM
SIGCOMM Computer Communication Review. 47(2). pp.19-26.
Online:
Network. 2020. Available through <https://www.techopedia.com/definition/5537/network>./
11
1 out of 14
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)





