Malicious Cyber Activities and Security Defences
Added on 2023-01-05
11 Pages3046 Words39 Views
Assessment 1

Table of Contents
INTRODUCTION...........................................................................................................................2
TASK 1............................................................................................................................................2
1. Identify and examine all types of the malicious cyber activities identified by ACSC and
summarize them in a table......................................................................................................2
2. Identification and categories assets, including all elements of an organisation’s system. .5
3. Create table to identifying and prioritising threats against each type of assets identified. 6
4. Analyse fundamental security principles with the mitigation strategies proposed by the
ACSC and demonstrate each recommended mitigation in relation to fundamental security
principle with justification......................................................................................................8
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11
INTRODUCTION...........................................................................................................................2
TASK 1............................................................................................................................................2
1. Identify and examine all types of the malicious cyber activities identified by ACSC and
summarize them in a table......................................................................................................2
2. Identification and categories assets, including all elements of an organisation’s system. .5
3. Create table to identifying and prioritising threats against each type of assets identified. 6
4. Analyse fundamental security principles with the mitigation strategies proposed by the
ACSC and demonstrate each recommended mitigation in relation to fundamental security
principle with justification......................................................................................................8
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11

INTRODUCTION
Internet is a global system which interconnects the computer network by using the
Internet Protocol Site so that communication can be made between device and network. The
technology era has made the individual dependent on the internet for all includes which have
severe consequences on the other side which is referred to as the cyber crimes. These have
gained a rapid increase in the last few years where people and organisations are subject to cyber
criminals. Cyber crimes refer to the activity which is criminal in nature where computer, c
network device and computer network is targeted by the individual or the organisations in order
to make money (Shah Jones and Choudrie, 2019). During the covid 19 time, this era is no more
an exceptional for these cyber crimes, rather there has been a rapid increase during this time.
This report shall cover the malicious cyber activities, identification and categories assets,
prioritising threats against each asset and the security defences based on fundamental security
principles and its analysis together with recommended mitigations.
TASK 1
1. Identify and examine all types of the malicious cyber activities identified by ACSC and
summarize them in a table
The malicious cyber activity is referred to as the activity that seeks to impair or
compromise the confidentiality, availability of information, integrity, communication or
information systems, virtual or physical infrastructure, networks that are controlled by the
computer (Siddiqui, Yadav and Husain, 2018). These are the external threats that infiltrate the
system with an aim to steal the information or damaging the software or hardware.
From the early 2020, March, there have been a major increase in malicious cyber crimes
in Australia as identified by the Australian Competition and Consumer Commission (ACCC) and
Australian Cyber Security Centre (ACSC). The following malicious cyber activities have been
spreading in the past few months from the time of Covid 19 which are discussed below-
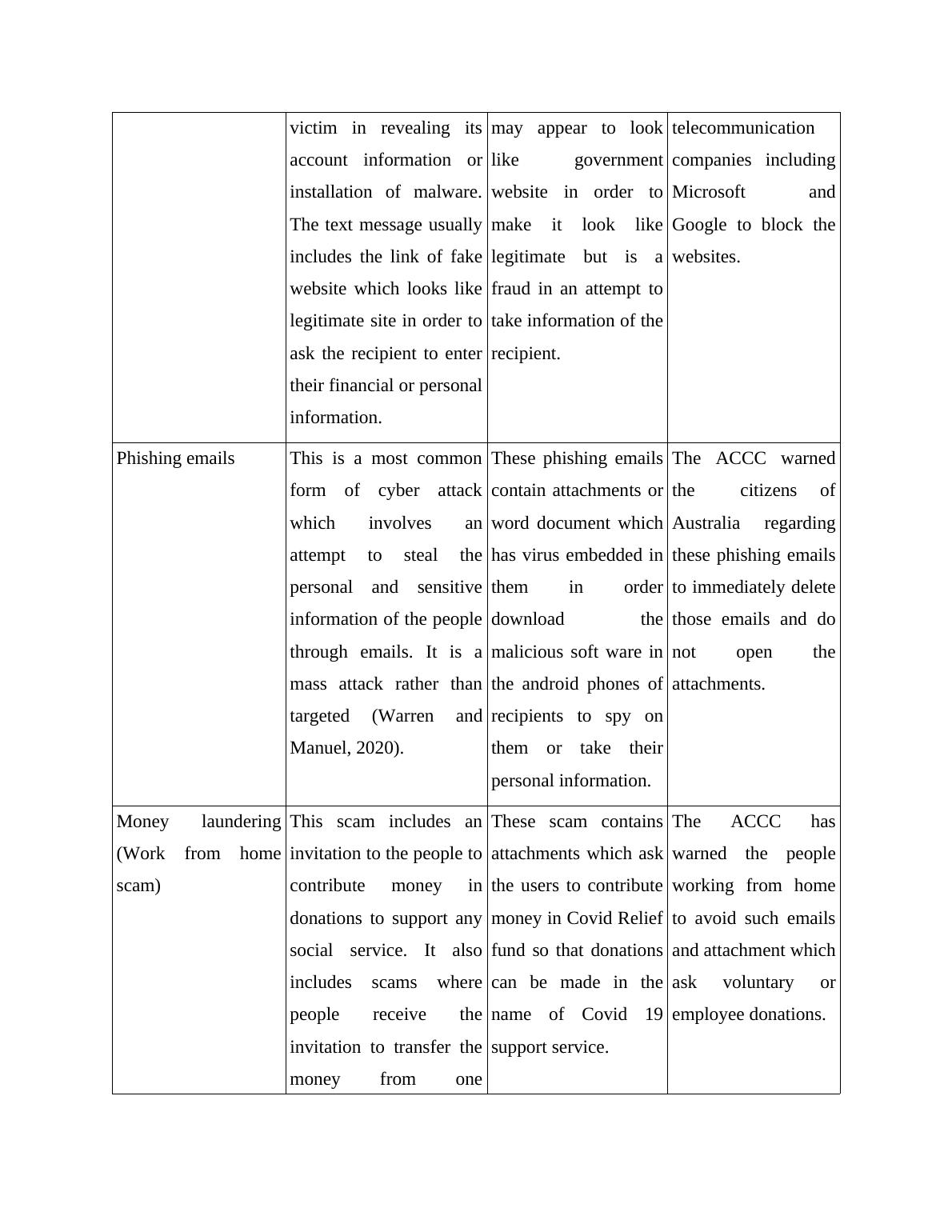
Cyber crime Description Impact What was done?
SMS Phishing It is an act which
involves text message
which tries to fraud the
This attack ask the
user to redirect them
to a website which
The Australia Cyber
Security Centra
reached six
Internet is a global system which interconnects the computer network by using the
Internet Protocol Site so that communication can be made between device and network. The
technology era has made the individual dependent on the internet for all includes which have
severe consequences on the other side which is referred to as the cyber crimes. These have
gained a rapid increase in the last few years where people and organisations are subject to cyber
criminals. Cyber crimes refer to the activity which is criminal in nature where computer, c
network device and computer network is targeted by the individual or the organisations in order
to make money (Shah Jones and Choudrie, 2019). During the covid 19 time, this era is no more
an exceptional for these cyber crimes, rather there has been a rapid increase during this time.
This report shall cover the malicious cyber activities, identification and categories assets,
prioritising threats against each asset and the security defences based on fundamental security
principles and its analysis together with recommended mitigations.
TASK 1
1. Identify and examine all types of the malicious cyber activities identified by ACSC and
summarize them in a table
The malicious cyber activity is referred to as the activity that seeks to impair or
compromise the confidentiality, availability of information, integrity, communication or
information systems, virtual or physical infrastructure, networks that are controlled by the
computer (Siddiqui, Yadav and Husain, 2018). These are the external threats that infiltrate the
system with an aim to steal the information or damaging the software or hardware.
From the early 2020, March, there have been a major increase in malicious cyber crimes
in Australia as identified by the Australian Competition and Consumer Commission (ACCC) and
Australian Cyber Security Centre (ACSC). The following malicious cyber activities have been
spreading in the past few months from the time of Covid 19 which are discussed below-
Cyber crime Description Impact What was done?
SMS Phishing It is an act which
involves text message
which tries to fraud the
This attack ask the
user to redirect them
to a website which
The Australia Cyber
Security Centra
reached six

victim in revealing its
account information or
installation of malware.
The text message usually
includes the link of fake
website which looks like
legitimate site in order to
ask the recipient to enter
their financial or personal
information.
may appear to look
like government
website in order to
make it look like
legitimate but is a
fraud in an attempt to
take information of the
recipient.
telecommunication
companies including
Microsoft and
Google to block the
websites.
Phishing emails This is a most common
form of cyber attack
which involves an
attempt to steal the
personal and sensitive
information of the people
through emails. It is a
mass attack rather than
targeted (Warren and
Manuel, 2020).
These phishing emails
contain attachments or
word document which
has virus embedded in
them in order
download the
malicious soft ware in
the android phones of
recipients to spy on
them or take their
personal information.
The ACCC warned
the citizens of
Australia regarding
these phishing emails
to immediately delete
those emails and do
not open the
attachments.
Money laundering
(Work from home
scam)
This scam includes an
invitation to the people to
contribute money in
donations to support any
social service. It also
includes scams where
people receive the
invitation to transfer the
money from one
These scam contains
attachments which ask
the users to contribute
money in Covid Relief
fund so that donations
can be made in the
name of Covid 19
support service.
The ACCC has
warned the people
working from home
to avoid such emails
and attachment which
ask voluntary or
employee donations.
account information or
installation of malware.
The text message usually
includes the link of fake
website which looks like
legitimate site in order to
ask the recipient to enter
their financial or personal
information.
may appear to look
like government
website in order to
make it look like
legitimate but is a
fraud in an attempt to
take information of the
recipient.
telecommunication
companies including
Microsoft and
Google to block the
websites.
Phishing emails This is a most common
form of cyber attack
which involves an
attempt to steal the
personal and sensitive
information of the people
through emails. It is a
mass attack rather than
targeted (Warren and
Manuel, 2020).
These phishing emails
contain attachments or
word document which
has virus embedded in
them in order
download the
malicious soft ware in
the android phones of
recipients to spy on
them or take their
personal information.
The ACCC warned
the citizens of
Australia regarding
these phishing emails
to immediately delete
those emails and do
not open the
attachments.
Money laundering
(Work from home
scam)
This scam includes an
invitation to the people to
contribute money in
donations to support any
social service. It also
includes scams where
people receive the
invitation to transfer the
money from one
These scam contains
attachments which ask
the users to contribute
money in Covid Relief
fund so that donations
can be made in the
name of Covid 19
support service.
The ACCC has
warned the people
working from home
to avoid such emails
and attachment which
ask voluntary or
employee donations.
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
IS Security and Risk Managementlg...
|12
|3177
|391
Threats Faced by Australian Health Sector Organizationslg...
|9
|2361
|75
IS Security and Risk Managementlg...
|13
|3313
|58
How to Recognize and Avoid Cybercrime in Australialg...
|10
|2834
|65
(solved) Essay on Cyber Issueslg...
|20
|4326
|169
The Assignment on Information Securitylg...
|12
|832
|36
