ITC595 Information Security Assessment 2: Security Fundamentals
VerifiedAdded on 2024/05/21
|10
|2391
|248
Homework Assignment
AI Summary
This ITC595 Information Security assessment solution delves into core security fundamentals, analyzing data integrity, confidentiality, and availability within the context of ATM transactions. It explores the impact of broken keys on PIN security and the limitations of manual brute-force attacks. The assessment further investigates the reluctance of clients to adopt biometrics, highlighting concerns around personal information intrusion, expense issues, and system shortcomings. It differentiates between false positives and false negatives in biometric systems, emphasizing scenarios where false negatives pose greater risks. Finally, the solution provides a step-by-step decryption of a transposition cipher using substitution techniques and Caesar ciphers to reveal the plaintext message: 'INCREASE THE PROCESS OR FREQUENCY'. Desklib offers a wide range of study resources, including solved assignments and past papers, to support students in their academic endeavors.

ITC595: Information security
Assessment 2
Security Fundamental
Student Name: Shaik Yousuf naseer
Student ID: 11585839
Assessment 2
Security Fundamental
Student Name: Shaik Yousuf naseer
Student ID: 11585839
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Shaik Yousuf naseer 11585839
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................2
Question 3..................................................................................................................................4
Question 4..................................................................................................................................5
Question 5..................................................................................................................................6
References..................................................................................................................................9
1
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................2
Question 3..................................................................................................................................4
Question 4..................................................................................................................................5
Question 5..................................................................................................................................6
References..................................................................................................................................9
1

Shaik Yousuf naseer 11585839
Question 1
Solution:
Integrity
It is the factor of security that needs to be achieved for securing information; it includes
accuracy of information over the network. While transferring the information over a
network; if the information is accessed and modified by the unauthorized person than the
data integrity is lost. While using ATM integrity is a must. Customers using ATM while
making transactions need a full integrity as if the amount transacted is altered than a
customer can suffer more additional charges (Peltier, 2010).
Degree of importance
Integrity is needed during ATM transactions because it directly affects the account
of a customer.
For example, if a customer has an account balance of $5500 and he withdraws
$1000. So the updated balance will be $4500; but accidentally in account $4300 gets
updated then this is a loss of integrity and affects the customer.
Confidentiality
It is similar to privacy that is if the information needs to be sent from A to B, and it
accidentally transferred to some C than it is the loss of confidentiality and it is needed to
maintain while transferring information. While the user is using ATM, customer needs a card
and it's PIN number so the PIN needs to be confidential to the individual customer only
Stallings (Brown, Bauer & Bhattacharjee, 2012).
Degree of importance
If the PIN number is unsecured while transaction than it can lead to a compromise in
the account. So the PIN number should be highly encrypted.
Availability
It means the resources should be available to the authorized users. If availability is lost it is
going to result in interrupts. The ATM machine should be 24*7 available to the customers
(Whitman & Mattord, 2011).
Degree of importance
It is important because it increases the growth of banks economic; therefore it is
necessary that ATM should be available and operational almost 24*7.
Question 2
2
Question 1
Solution:
Integrity
It is the factor of security that needs to be achieved for securing information; it includes
accuracy of information over the network. While transferring the information over a
network; if the information is accessed and modified by the unauthorized person than the
data integrity is lost. While using ATM integrity is a must. Customers using ATM while
making transactions need a full integrity as if the amount transacted is altered than a
customer can suffer more additional charges (Peltier, 2010).
Degree of importance
Integrity is needed during ATM transactions because it directly affects the account
of a customer.
For example, if a customer has an account balance of $5500 and he withdraws
$1000. So the updated balance will be $4500; but accidentally in account $4300 gets
updated then this is a loss of integrity and affects the customer.
Confidentiality
It is similar to privacy that is if the information needs to be sent from A to B, and it
accidentally transferred to some C than it is the loss of confidentiality and it is needed to
maintain while transferring information. While the user is using ATM, customer needs a card
and it's PIN number so the PIN needs to be confidential to the individual customer only
Stallings (Brown, Bauer & Bhattacharjee, 2012).
Degree of importance
If the PIN number is unsecured while transaction than it can lead to a compromise in
the account. So the PIN number should be highly encrypted.
Availability
It means the resources should be available to the authorized users. If availability is lost it is
going to result in interrupts. The ATM machine should be 24*7 available to the customers
(Whitman & Mattord, 2011).
Degree of importance
It is important because it increases the growth of banks economic; therefore it is
necessary that ATM should be available and operational almost 24*7.
Question 2
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Shaik Yousuf naseer 11585839
Solution:
For the PIN number, any combination of four digit number between 0-9 can be used
repeatedly.
Case1 (key 0 got broken)
Key 0 if broken, it will reduce the one option of combination (0 at all places of the PIN),
because if the first place of the PIN number is 0 than the PIN would become a 3-digit
number.
Number of digits after breaking a couple of keys is five (barring 0).
Now there are 5 ways of filling each place, as the repetition is permitted.
Possible combinations than thief need to make for reaching the correct PIN number are 54=
625.
Case2 (if key 0 isn’t broken)
On the off chance that 0 has not been broken by the thief than one combination will be
decreased.
Number of digits after breaking a couple of keys is five (counting 0).
Now there are 5 ways of filling each place, as the repetition is permitted.
Possible combinations than thief need to make for reaching the correct PIN number are (54-
1) = 624.
The arrangement is manual which is not possible as the ATM allows only three chances to
enter correct PIN. After the three incorrect PINs, the notification or alert message is sent
and the card is locked temporarily for some time.
3
Solution:
For the PIN number, any combination of four digit number between 0-9 can be used
repeatedly.
Case1 (key 0 got broken)
Key 0 if broken, it will reduce the one option of combination (0 at all places of the PIN),
because if the first place of the PIN number is 0 than the PIN would become a 3-digit
number.
Number of digits after breaking a couple of keys is five (barring 0).
Now there are 5 ways of filling each place, as the repetition is permitted.
Possible combinations than thief need to make for reaching the correct PIN number are 54=
625.
Case2 (if key 0 isn’t broken)
On the off chance that 0 has not been broken by the thief than one combination will be
decreased.
Number of digits after breaking a couple of keys is five (counting 0).
Now there are 5 ways of filling each place, as the repetition is permitted.
Possible combinations than thief need to make for reaching the correct PIN number are (54-
1) = 624.
The arrangement is manual which is not possible as the ATM allows only three chances to
enter correct PIN. After the three incorrect PINs, the notification or alert message is sent
and the card is locked temporarily for some time.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Shaik Yousuf naseer 11585839
Question 3
Solution:
Biometrics sensors are the machines based on the human body senses for the purpose of
authentication. The biometrics is reflected as a strong way of authentication till date. The
biometric contains features existing in all human body but is unique to each individual.
Some of the features are eyes, thumbprint, fingerprint through which information can be
accessed by authenticated persons (Jain, Nandakumar, & Ross, 2016).
Here are few ideas in light of which the clients don't want to utilize biometrics as validation
system.
1. Personal information intrusion: people fear to share their personal information on
the machines which are not trustable. It’s an outlook among individuals to not
believe on any machine with their personal information. However, the biometrics is
an important to individual recognizable proof and keeps data of one's citizenship in
government's record. The biometric machine allows two-stage verification to
generate trust among customers.
2. Expense issues: Installing any biometric validation packages can range up to
thousand. It isn't at all financially steady. It’s a one-time speculation. Along these
lines, the administration ought to give credits or set up a few plans or memberships
for the establishment and updating of the framework.
3. Have some shortcomings: Every framework has flaws or mistakes. Likewise, there’s a
man who has start-up his unique mark as confirmation. If any cut or burn occurs to
the person the machine doesn’t recognize the features and gives an authorization
error. In this way it causes issues.
Issues can be there if multiple biometrics is stored in multiple slots.
4
Question 3
Solution:
Biometrics sensors are the machines based on the human body senses for the purpose of
authentication. The biometrics is reflected as a strong way of authentication till date. The
biometric contains features existing in all human body but is unique to each individual.
Some of the features are eyes, thumbprint, fingerprint through which information can be
accessed by authenticated persons (Jain, Nandakumar, & Ross, 2016).
Here are few ideas in light of which the clients don't want to utilize biometrics as validation
system.
1. Personal information intrusion: people fear to share their personal information on
the machines which are not trustable. It’s an outlook among individuals to not
believe on any machine with their personal information. However, the biometrics is
an important to individual recognizable proof and keeps data of one's citizenship in
government's record. The biometric machine allows two-stage verification to
generate trust among customers.
2. Expense issues: Installing any biometric validation packages can range up to
thousand. It isn't at all financially steady. It’s a one-time speculation. Along these
lines, the administration ought to give credits or set up a few plans or memberships
for the establishment and updating of the framework.
3. Have some shortcomings: Every framework has flaws or mistakes. Likewise, there’s a
man who has start-up his unique mark as confirmation. If any cut or burn occurs to
the person the machine doesn’t recognize the features and gives an authorization
error. In this way it causes issues.
Issues can be there if multiple biometrics is stored in multiple slots.
4

Shaik Yousuf naseer 11585839
Question 4
Solution:
False positives
It is the situation or outcome of biometric machines when the machine accepts and gives
access to an invalid individual accident that is false acceptance. The false positive is a big
problem as it could affect the organization personal information including bank account
details and confidential data (Pereira, Kennedy & Viljoen, 2015).
False negatives
False negatives can be defined as the failed system that is when the machine is unsuccessful
in identifying the authorized client.
There could be numerous concerns where false negative is proved more serious than the
false positive;
Organization: There is a large information stored in the storage of an organization
that is biometrically protected from the unauthorized access. Likewise, if the
company server is down, and manager needs to access data stores for refurbishing
services and, company needs to recover services as fast as they can; because the
revenue of company is quickly decreasing, and the biometric machine fails to
identify manager, then this could lead to loss of economy in company.
Personal: The system sometimes fails to identify the authorized individual and the
important data or money gets stuck then it creates a problem for an individual.
Likewise, if an individual wants money urgently from his safe and has the biometric
machine that is not identifying the individual than it becomes an issue.
5
Question 4
Solution:
False positives
It is the situation or outcome of biometric machines when the machine accepts and gives
access to an invalid individual accident that is false acceptance. The false positive is a big
problem as it could affect the organization personal information including bank account
details and confidential data (Pereira, Kennedy & Viljoen, 2015).
False negatives
False negatives can be defined as the failed system that is when the machine is unsuccessful
in identifying the authorized client.
There could be numerous concerns where false negative is proved more serious than the
false positive;
Organization: There is a large information stored in the storage of an organization
that is biometrically protected from the unauthorized access. Likewise, if the
company server is down, and manager needs to access data stores for refurbishing
services and, company needs to recover services as fast as they can; because the
revenue of company is quickly decreasing, and the biometric machine fails to
identify manager, then this could lead to loss of economy in company.
Personal: The system sometimes fails to identify the authorized individual and the
important data or money gets stuck then it creates a problem for an individual.
Likewise, if an individual wants money urgently from his safe and has the biometric
machine that is not identifying the individual than it becomes an issue.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Shaik Yousuf naseer 11585839
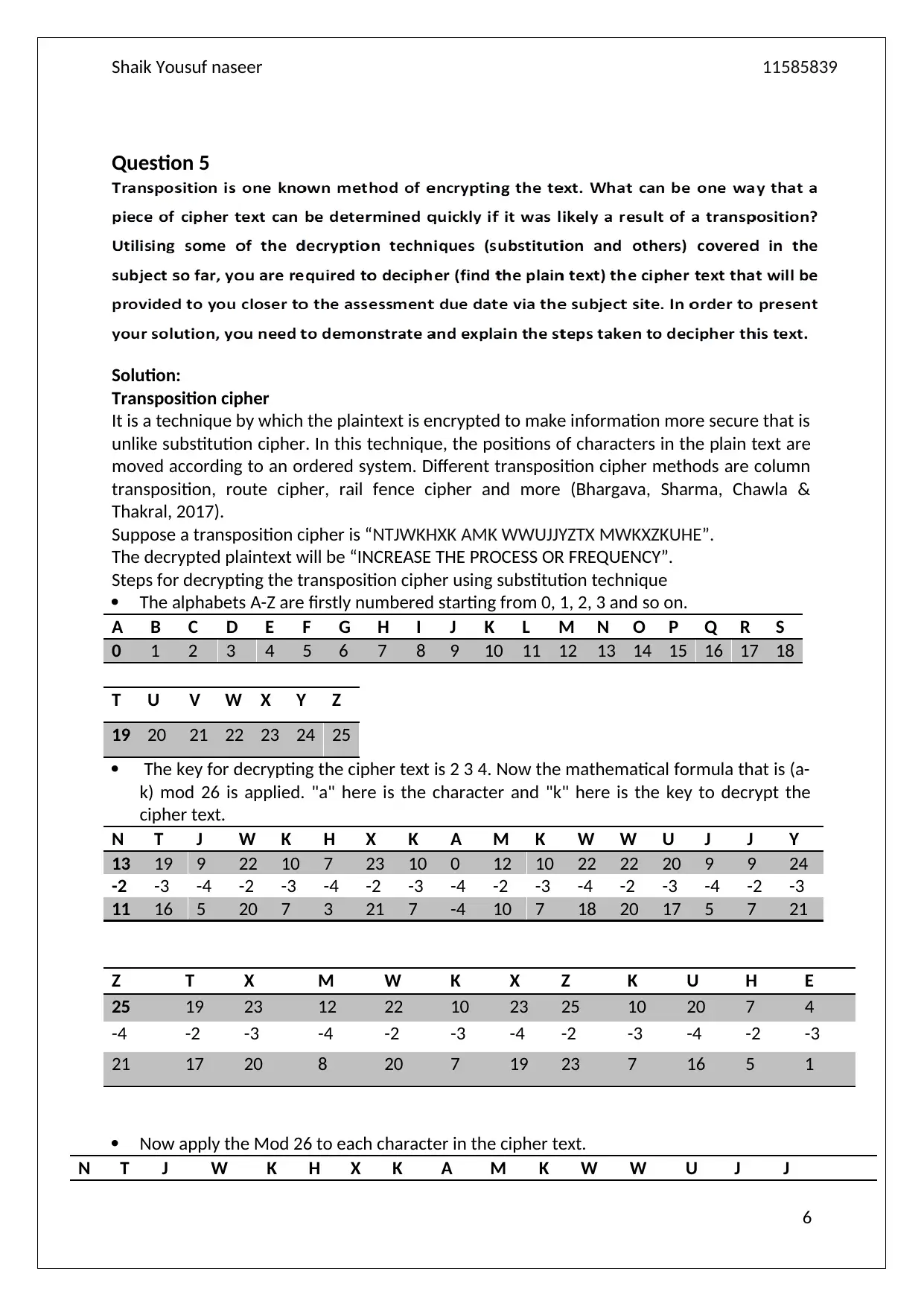
Question 5
Solution:
Transposition cipher
It is a technique by which the plaintext is encrypted to make information more secure that is
unlike substitution cipher. In this technique, the positions of characters in the plain text are
moved according to an ordered system. Different transposition cipher methods are column
transposition, route cipher, rail fence cipher and more (Bhargava, Sharma, Chawla &
Thakral, 2017).
Suppose a transposition cipher is “NTJWKHXK AMK WWUJJYZTX MWKXZKUHE”.
The decrypted plaintext will be “INCREASE THE PROCESS OR FREQUENCY”.
Steps for decrypting the transposition cipher using substitution technique
The alphabets A-Z are firstly numbered starting from 0, 1, 2, 3 and so on.
A B C D E F G H I J K L M N O P Q R S
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
T U V W X Y Z
19 20 21 22 23 24 25
The key for decrypting the cipher text is 2 3 4. Now the mathematical formula that is (a-
k) mod 26 is applied. "a" here is the character and "k" here is the key to decrypt the
cipher text.
N T J W K H X K A M K W W U J J Y
13 19 9 22 10 7 23 10 0 12 10 22 22 20 9 9 24
-2 -3 -4 -2 -3 -4 -2 -3 -4 -2 -3 -4 -2 -3 -4 -2 -3
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
Z T X M W K X Z K U H E
25 19 23 12 22 10 23 25 10 20 7 4
-4 -2 -3 -4 -2 -3 -4 -2 -3 -4 -2 -3
21 17 20 8 20 7 19 23 7 16 5 1
Now apply the Mod 26 to each character in the cipher text.
N T J W K H X K A M K W W U J J
6
Question 5
Solution:
Transposition cipher
It is a technique by which the plaintext is encrypted to make information more secure that is
unlike substitution cipher. In this technique, the positions of characters in the plain text are
moved according to an ordered system. Different transposition cipher methods are column
transposition, route cipher, rail fence cipher and more (Bhargava, Sharma, Chawla &
Thakral, 2017).
Suppose a transposition cipher is “NTJWKHXK AMK WWUJJYZTX MWKXZKUHE”.
The decrypted plaintext will be “INCREASE THE PROCESS OR FREQUENCY”.
Steps for decrypting the transposition cipher using substitution technique
The alphabets A-Z are firstly numbered starting from 0, 1, 2, 3 and so on.
A B C D E F G H I J K L M N O P Q R S
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
T U V W X Y Z
19 20 21 22 23 24 25
The key for decrypting the cipher text is 2 3 4. Now the mathematical formula that is (a-
k) mod 26 is applied. "a" here is the character and "k" here is the key to decrypt the
cipher text.
N T J W K H X K A M K W W U J J Y
13 19 9 22 10 7 23 10 0 12 10 22 22 20 9 9 24
-2 -3 -4 -2 -3 -4 -2 -3 -4 -2 -3 -4 -2 -3 -4 -2 -3
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
Z T X M W K X Z K U H E
25 19 23 12 22 10 23 25 10 20 7 4
-4 -2 -3 -4 -2 -3 -4 -2 -3 -4 -2 -3
21 17 20 8 20 7 19 23 7 16 5 1
Now apply the Mod 26 to each character in the cipher text.
N T J W K H X K A M K W W U J J
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Shaik Yousuf naseer 11585839
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
m
od
26
mo
d
26
mo
d
26
mod
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mod
26
mo
d
26
mo
d
26
mo
d
26
mod
26
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
Z T X M W K X Z K U H E
21 17 20 8 20 7 19 23 7 16 5 1
mod
26
mod
26
mod
26
mod 26 mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
21 17 20 8 20 7 19 23 7 16 5 1
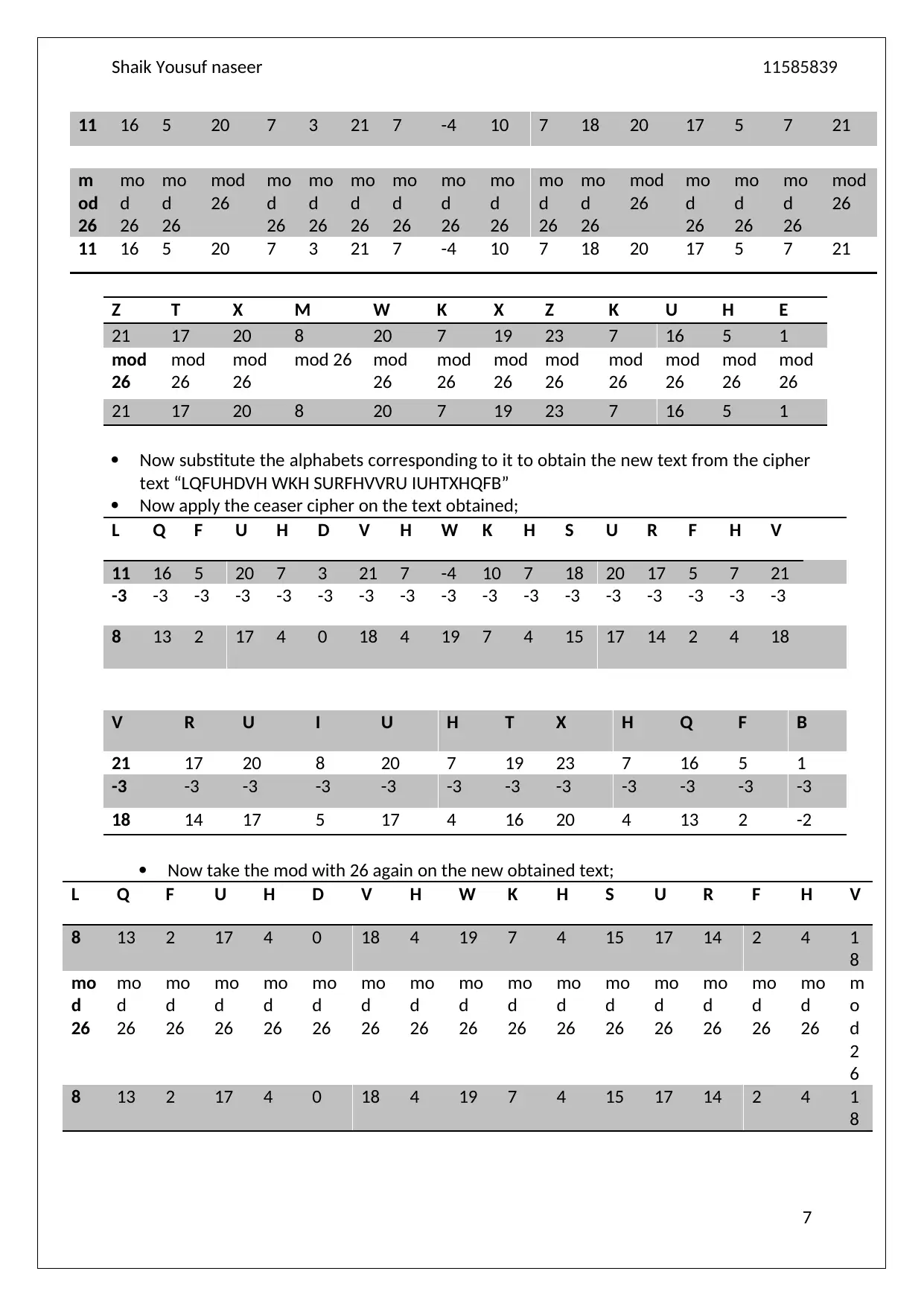
Now substitute the alphabets corresponding to it to obtain the new text from the cipher
text “LQFUHDVH WKH SURFHVVRU IUHTXHQFB”
Now apply the ceaser cipher on the text obtained;
L Q F U H D V H W K H S U R F H V
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
-3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3
8 13 2 17 4 0 18 4 19 7 4 15 17 14 2 4 18
V R U I U H T X H Q F B
21 17 20 8 20 7 19 23 7 16 5 1
-3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3
18 14 17 5 17 4 16 20 4 13 2 -2
Now take the mod with 26 again on the new obtained text;
L Q F U H D V H W K H S U R F H V
8 13 2 17 4 0 18 4 19 7 4 15 17 14 2 4 1
8
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
m
o
d
2
6
8 13 2 17 4 0 18 4 19 7 4 15 17 14 2 4 1
8
7
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
m
od
26
mo
d
26
mo
d
26
mod
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mod
26
mo
d
26
mo
d
26
mo
d
26
mod
26
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
Z T X M W K X Z K U H E
21 17 20 8 20 7 19 23 7 16 5 1
mod
26
mod
26
mod
26
mod 26 mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
21 17 20 8 20 7 19 23 7 16 5 1
Now substitute the alphabets corresponding to it to obtain the new text from the cipher
text “LQFUHDVH WKH SURFHVVRU IUHTXHQFB”
Now apply the ceaser cipher on the text obtained;
L Q F U H D V H W K H S U R F H V
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
-3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3
8 13 2 17 4 0 18 4 19 7 4 15 17 14 2 4 18
V R U I U H T X H Q F B
21 17 20 8 20 7 19 23 7 16 5 1
-3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3 -3
18 14 17 5 17 4 16 20 4 13 2 -2
Now take the mod with 26 again on the new obtained text;
L Q F U H D V H W K H S U R F H V
8 13 2 17 4 0 18 4 19 7 4 15 17 14 2 4 1
8
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
mo
d
26
m
o
d
2
6
8 13 2 17 4 0 18 4 19 7 4 15 17 14 2 4 1
8
7
Shaik Yousuf naseer 11585839
V R U I U H T X H Q F B
18 14 17 5 17 4 16 20 4 13 2 24
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
18 14 17 5 17 4 16 20 4 13 2 24
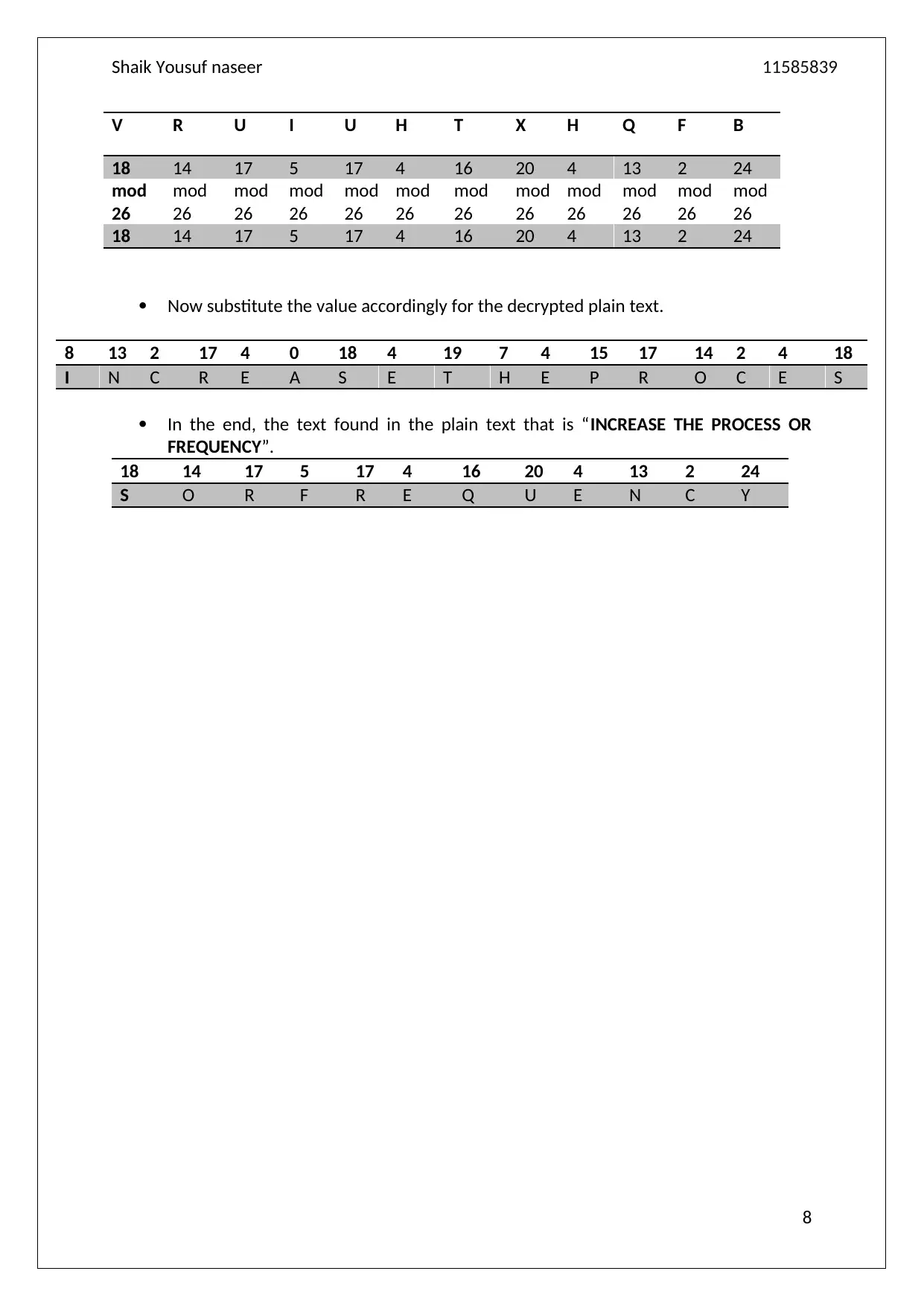
Now substitute the value accordingly for the decrypted plain text.
8 13 2 17 4 0 18 4 19 7 4 15 17 14 2 4 18
I N C R E A S E T H E P R O C E S
In the end, the text found in the plain text that is “INCREASE THE PROCESS OR
FREQUENCY”.
18 14 17 5 17 4 16 20 4 13 2 24
S O R F R E Q U E N C Y
8
V R U I U H T X H Q F B
18 14 17 5 17 4 16 20 4 13 2 24
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
mod
26
18 14 17 5 17 4 16 20 4 13 2 24
Now substitute the value accordingly for the decrypted plain text.
8 13 2 17 4 0 18 4 19 7 4 15 17 14 2 4 18
I N C R E A S E T H E P R O C E S
In the end, the text found in the plain text that is “INCREASE THE PROCESS OR
FREQUENCY”.
18 14 17 5 17 4 16 20 4 13 2 24
S O R F R E Q U E N C Y
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Shaik Yousuf naseer 11585839
References
Bhargava, U., Sharma, A., Chawla, R., & Thakral, P. (2017). A new algorithm
combining substitution & transposition cipher techniques for secure communication.
In Trends in Electronics and Informatics (ICEI), 2017 International Conference on (pp.
619-624). IEEE.
Jain, A. K., Nandakumar, K., & Ross, A. (2016). 50 years of biometric research:
Accomplishments, challenges, and opportunities. Pattern Recognition Letters, 79, 80-
105.
Peltier, T. R. (2010). Information security risk analysis. Auerbach publications.
Pereira, S., Kennedy, M., & Viljoen, P. (2015). U.S. Patent No. 8,931,086. Washington,
DC: U.S. Patent and Trademark Office.
Stallings, W., Brown, L., Bauer, M. D., & Bhattacharjee, A. K. (2012). Computer
security: principles and practice (pp. 978-0). Pearson Education.
Whitman, M. E., & Mattord, H. J. (2011). Principles of information security. Cengage
Learning.
9
References
Bhargava, U., Sharma, A., Chawla, R., & Thakral, P. (2017). A new algorithm
combining substitution & transposition cipher techniques for secure communication.
In Trends in Electronics and Informatics (ICEI), 2017 International Conference on (pp.
619-624). IEEE.
Jain, A. K., Nandakumar, K., & Ross, A. (2016). 50 years of biometric research:
Accomplishments, challenges, and opportunities. Pattern Recognition Letters, 79, 80-
105.
Peltier, T. R. (2010). Information security risk analysis. Auerbach publications.
Pereira, S., Kennedy, M., & Viljoen, P. (2015). U.S. Patent No. 8,931,086. Washington,
DC: U.S. Patent and Trademark Office.
Stallings, W., Brown, L., Bauer, M. D., & Bhattacharjee, A. K. (2012). Computer
security: principles and practice (pp. 978-0). Pearson Education.
Whitman, M. E., & Mattord, H. J. (2011). Principles of information security. Cengage
Learning.
9
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





