Information Security Fundamentals: Assessment 2
VerifiedAdded on 2024/05/21
|9
|1655
|218
AI Summary
This assessment explores fundamental security concepts, including confidentiality, integrity, and availability. It analyzes the impact of a broken ATM key on PIN combinations and examines the pros and cons of biometric authentication. The assessment also delves into the implications of false negatives in security systems and demonstrates the decryption of a ciphertext using Vigenere and Caesar cipher techniques.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

ITC595: Information security
Assessment 2
Security Fundamental
Student Name: Abdul Aqeel
Student ID: 11612827
Assessment 2
Security Fundamental
Student Name: Abdul Aqeel
Student ID: 11612827
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Abdul Aqeel 11612827
Table of Contents
Question 1..................................................................................................................................2
Importance of Confidentiality:...............................................................................................2
Integrity..................................................................................................................................2
Importance of Integrity:.........................................................................................................2
Availability:.............................................................................................................................2
Importance of Availability:.....................................................................................................2
Question 2..................................................................................................................................3
Case1 (when 0 key broken by the thief).................................................................................3
Case2 (when 0 not broken by the thief).................................................................................3
Question 3..................................................................................................................................4
1. Private Data Assault........................................................................................................4
2. Expenditure Problems.....................................................................................................4
3. Not free of Accountabilities............................................................................................4
Question 4..................................................................................................................................5
1. Private Situations:...........................................................................................................5
2. Structural Situations........................................................................................................5
Question 5..................................................................................................................................6
REFERENCES...............................................................................................................................8
1
Table of Contents
Question 1..................................................................................................................................2
Importance of Confidentiality:...............................................................................................2
Integrity..................................................................................................................................2
Importance of Integrity:.........................................................................................................2
Availability:.............................................................................................................................2
Importance of Availability:.....................................................................................................2
Question 2..................................................................................................................................3
Case1 (when 0 key broken by the thief).................................................................................3
Case2 (when 0 not broken by the thief).................................................................................3
Question 3..................................................................................................................................4
1. Private Data Assault........................................................................................................4
2. Expenditure Problems.....................................................................................................4
3. Not free of Accountabilities............................................................................................4
Question 4..................................................................................................................................5
1. Private Situations:...........................................................................................................5
2. Structural Situations........................................................................................................5
Question 5..................................................................................................................................6
REFERENCES...............................................................................................................................8
1

Abdul Aqeel 11612827
Question 1
Confidentiality:
The customer operates the ATM card and the Private Identification Number (PIN) to get to
the record the ATM. The customer specialists the stick to be private in having a framework
and amid exchange along the correspondence channel between the host outline and the
bank server.
Importance of Confidentiality:
The stick ought to be appropriately encoded. Not secured PIN through the exchange may
prompt arrangement of record. It is fundamentally concealing some vital data so that the
unauthenticated individuals would not approach the information or the data. The ATM PIN
ought to be classified by the client as it were. The strategies that could be utilized for
keeping up classification can be secret word encryption, two-stage verification, biometric
confirmation.
Integrity
The client needs that the exchange records with no noxious or the unexpected charges.
Integrity refers that the data cannot be changed without approval.
Importance of Integrity:
If a client withdrawal $1000 and adjust is $5000. Rather than refreshing $5000 in the client
account, accidentally if it as updates as $4800 then it causes startling harm of amount. As
the trades performed impact the customer account particularly, the uprightness of trades
should be secured.
Availability:
The ATM machine ought to be accessible to serve the clients dependably. In this, the
computer system is used for storing the data and procedure the information and the
security controls used to secure it.
Importance of Availability:
It expands the financial development of a bank; therefore, the ATM should be working and
functional always (Atmmarketplace, 2017).
2
Question 1
Confidentiality:
The customer operates the ATM card and the Private Identification Number (PIN) to get to
the record the ATM. The customer specialists the stick to be private in having a framework
and amid exchange along the correspondence channel between the host outline and the
bank server.
Importance of Confidentiality:
The stick ought to be appropriately encoded. Not secured PIN through the exchange may
prompt arrangement of record. It is fundamentally concealing some vital data so that the
unauthenticated individuals would not approach the information or the data. The ATM PIN
ought to be classified by the client as it were. The strategies that could be utilized for
keeping up classification can be secret word encryption, two-stage verification, biometric
confirmation.
Integrity
The client needs that the exchange records with no noxious or the unexpected charges.
Integrity refers that the data cannot be changed without approval.
Importance of Integrity:
If a client withdrawal $1000 and adjust is $5000. Rather than refreshing $5000 in the client
account, accidentally if it as updates as $4800 then it causes startling harm of amount. As
the trades performed impact the customer account particularly, the uprightness of trades
should be secured.
Availability:
The ATM machine ought to be accessible to serve the clients dependably. In this, the
computer system is used for storing the data and procedure the information and the
security controls used to secure it.
Importance of Availability:
It expands the financial development of a bank; therefore, the ATM should be working and
functional always (Atmmarketplace, 2017).
2

Abdul Aqeel 11612827
Question 2
The 10 digits 0-9 can be utilized as a part of any grouping and with reiteration in the four
digits PIN.
Case1 (when 0 key broken by the thief)
Breaking of 0 would lessen one probability of mix (0 in the thousands place) claiming
if 0 would be in the thousands place, the PIN would turn into a three-digit number.
No. of digits after the hoodlum separated a combine of sources is 5 (barring 0).
Each place can be filled in 5 courses since the redundancy is permitted.
Add up to the number of conceivable mixes before the thief can reach the right PIN
is: 54 = 625
Case2 (when 0 not broken by the thief)
There is off chance that 0 has not been ruined by the criminal, one blend will be
decreased (0 in the thousands place).
No. of digits after the cheat separated a combine of sources is 5 (counting 0).
Each place can be filled in 5 routes since the redundancy is permitted.
Add up to number of conceivable blends previously the criminal can reach to the
right PIN is: 54 - 1= 624
This is the manual game plan yet sensibly, this isn't conceivable claiming ATMs
permit just three inaccurate PINs. After that, a warning is given and card gets
incidentally secured.
3
Question 2
The 10 digits 0-9 can be utilized as a part of any grouping and with reiteration in the four
digits PIN.
Case1 (when 0 key broken by the thief)
Breaking of 0 would lessen one probability of mix (0 in the thousands place) claiming
if 0 would be in the thousands place, the PIN would turn into a three-digit number.
No. of digits after the hoodlum separated a combine of sources is 5 (barring 0).
Each place can be filled in 5 courses since the redundancy is permitted.
Add up to the number of conceivable mixes before the thief can reach the right PIN
is: 54 = 625
Case2 (when 0 not broken by the thief)
There is off chance that 0 has not been ruined by the criminal, one blend will be
decreased (0 in the thousands place).
No. of digits after the cheat separated a combine of sources is 5 (counting 0).
Each place can be filled in 5 routes since the redundancy is permitted.
Add up to number of conceivable blends previously the criminal can reach to the
right PIN is: 54 - 1= 624
This is the manual game plan yet sensibly, this isn't conceivable claiming ATMs
permit just three inaccurate PINs. After that, a warning is given and card gets
incidentally secured.
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Abdul Aqeel 11612827
Question 3
There are a few ideas in view of which the clients don't need to operate biometrics as
validation technique.
1. Private Data Assault: There is a dread among the general population to sharing their
details so much individual data on any machine. It is a mentality between persons
not to reveal in some machine with their individual information. However, the
biometrics is a vital to single noticeable evidence and is saved as a record of one's
residency in administration's record. The machines can empower two stage
confirmations to guarantee the general population.
2. Expenditure Problems: Setting up of any biometric verification or its bundles can reach
up to thousands. It is not at economically balanced. It is a one-time assumption.
Subsequently, the legislature should to give recognitions or fixed up a few plans or
associations for the formation and modernizing of the structure.
3. Not free of Accountabilities: Each framework has issues or blunders. For instance,
there is a person who has fixed up his unique finger impression as validation. If there
should be an occurrence of any cut or consume, the machine does not acknowledge
the secret word and validation falls flat. In this it is a reasons an issue.
The issue could be if there are different alternatives or openings for putting away
numerous biometrics (DASCALESCU, 2018)
4
Question 3
There are a few ideas in view of which the clients don't need to operate biometrics as
validation technique.
1. Private Data Assault: There is a dread among the general population to sharing their
details so much individual data on any machine. It is a mentality between persons
not to reveal in some machine with their individual information. However, the
biometrics is a vital to single noticeable evidence and is saved as a record of one's
residency in administration's record. The machines can empower two stage
confirmations to guarantee the general population.
2. Expenditure Problems: Setting up of any biometric verification or its bundles can reach
up to thousands. It is not at economically balanced. It is a one-time assumption.
Subsequently, the legislature should to give recognitions or fixed up a few plans or
associations for the formation and modernizing of the structure.
3. Not free of Accountabilities: Each framework has issues or blunders. For instance,
there is a person who has fixed up his unique finger impression as validation. If there
should be an occurrence of any cut or consume, the machine does not acknowledge
the secret word and validation falls flat. In this it is a reasons an issue.
The issue could be if there are different alternatives or openings for putting away
numerous biometrics (DASCALESCU, 2018)
4

Abdul Aqeel 11612827
Question 4
There are sure circumstances when the false negatives posture more genuine dangers other
than the false positives. These can be as per the following:
1. Private Situations: Occasionally, the framework neglects to perceive even the right
biometric. On the off chance that there is a framework that contains some essential
information and the framework neglects to recognize the individual's biometric, at
that point the availability would be denied, and thusly false negative would prompt
significant issues.
2. Structural Situations: There is excessively information put away physically or in
frameworks and are ensured by biometrics of some approved personals. If there is a
blunder and false negative happens, at that point the association's information would
be seized, and this would bring about genuine outcomes (365 Data Science, 2017).
5
Question 4
There are sure circumstances when the false negatives posture more genuine dangers other
than the false positives. These can be as per the following:
1. Private Situations: Occasionally, the framework neglects to perceive even the right
biometric. On the off chance that there is a framework that contains some essential
information and the framework neglects to recognize the individual's biometric, at
that point the availability would be denied, and thusly false negative would prompt
significant issues.
2. Structural Situations: There is excessively information put away physically or in
frameworks and are ensured by biometrics of some approved personals. If there is a
blunder and false negative happens, at that point the association's information would
be seized, and this would bring about genuine outcomes (365 Data Science, 2017).
5

Abdul Aqeel 11612827
Question 5
Plain Text is a data that can directly readable text human or machine. Plain text is used in
cryptography denotes message before encryption and after decryption (Crypto, 2017).
Transposition is the cyphering method which doesn’t influence the image's frequencies.
Cryptanalysis can be utilized to effectively recognize the writings doing recurrence tally of
the images. We can utilize Caesar decode strategy for the assurance of figure content.
In the above question, a ciphertext is NTJWKHXK AMK WWUJJYZTX MWKXZKUHE.
The decrypt plain text is ntjwkhxk amk wwujjyztx mwkxzkuhe.
Decrypt the Cipher Text the following step is:
Check the given text first letter is N
Where N is 13 and Key is 234
Mi = (N-2) mod 26
Mi = (13-2) mod 26
= 11 = L
T= 19 where Key is 234, Mi = (19-2) mod 26= 16 =Q
1. First, give the check the numbering to all the alphabets of given text
Key 2 3 4 2 3 4 2 3 4 2 3 4 2 3 4
Cipher
Text
N T J W K H X K A M K W W U J
Decrypted L Q F U H D V H W K H S U R F
Key 2 3 4 2 3 4 2 3 4 2 3 4 2 3
Cipher J Y Z T X M W K X Z K U H E
Decrypted H V V R U I U H T X H Q F B
To decrypt the code it is using the Vigenere cipher technique
Cipher text: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE, Key is 234
The decrypted code is LQFUHDVH WKH SURFHVVRU IUHTXHQFB
Now it required more decryption so, apply the Caesar cipher technique to decrypt the code
Where X is text that is required decryption and key is n which is equal to the 3 and the
cipher text is: LQFUHDVH WKH SURFHVVRU IUHTXHQFB
Apply the Caesar cipher technique on the L which is first letter:
6
Question 5
Plain Text is a data that can directly readable text human or machine. Plain text is used in
cryptography denotes message before encryption and after decryption (Crypto, 2017).
Transposition is the cyphering method which doesn’t influence the image's frequencies.
Cryptanalysis can be utilized to effectively recognize the writings doing recurrence tally of
the images. We can utilize Caesar decode strategy for the assurance of figure content.
In the above question, a ciphertext is NTJWKHXK AMK WWUJJYZTX MWKXZKUHE.
The decrypt plain text is ntjwkhxk amk wwujjyztx mwkxzkuhe.
Decrypt the Cipher Text the following step is:
Check the given text first letter is N
Where N is 13 and Key is 234
Mi = (N-2) mod 26
Mi = (13-2) mod 26
= 11 = L
T= 19 where Key is 234, Mi = (19-2) mod 26= 16 =Q
1. First, give the check the numbering to all the alphabets of given text
Key 2 3 4 2 3 4 2 3 4 2 3 4 2 3 4
Cipher
Text
N T J W K H X K A M K W W U J
Decrypted L Q F U H D V H W K H S U R F
Key 2 3 4 2 3 4 2 3 4 2 3 4 2 3
Cipher J Y Z T X M W K X Z K U H E
Decrypted H V V R U I U H T X H Q F B
To decrypt the code it is using the Vigenere cipher technique
Cipher text: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE, Key is 234
The decrypted code is LQFUHDVH WKH SURFHVVRU IUHTXHQFB
Now it required more decryption so, apply the Caesar cipher technique to decrypt the code
Where X is text that is required decryption and key is n which is equal to the 3 and the
cipher text is: LQFUHDVH WKH SURFHVVRU IUHTXHQFB
Apply the Caesar cipher technique on the L which is first letter:
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
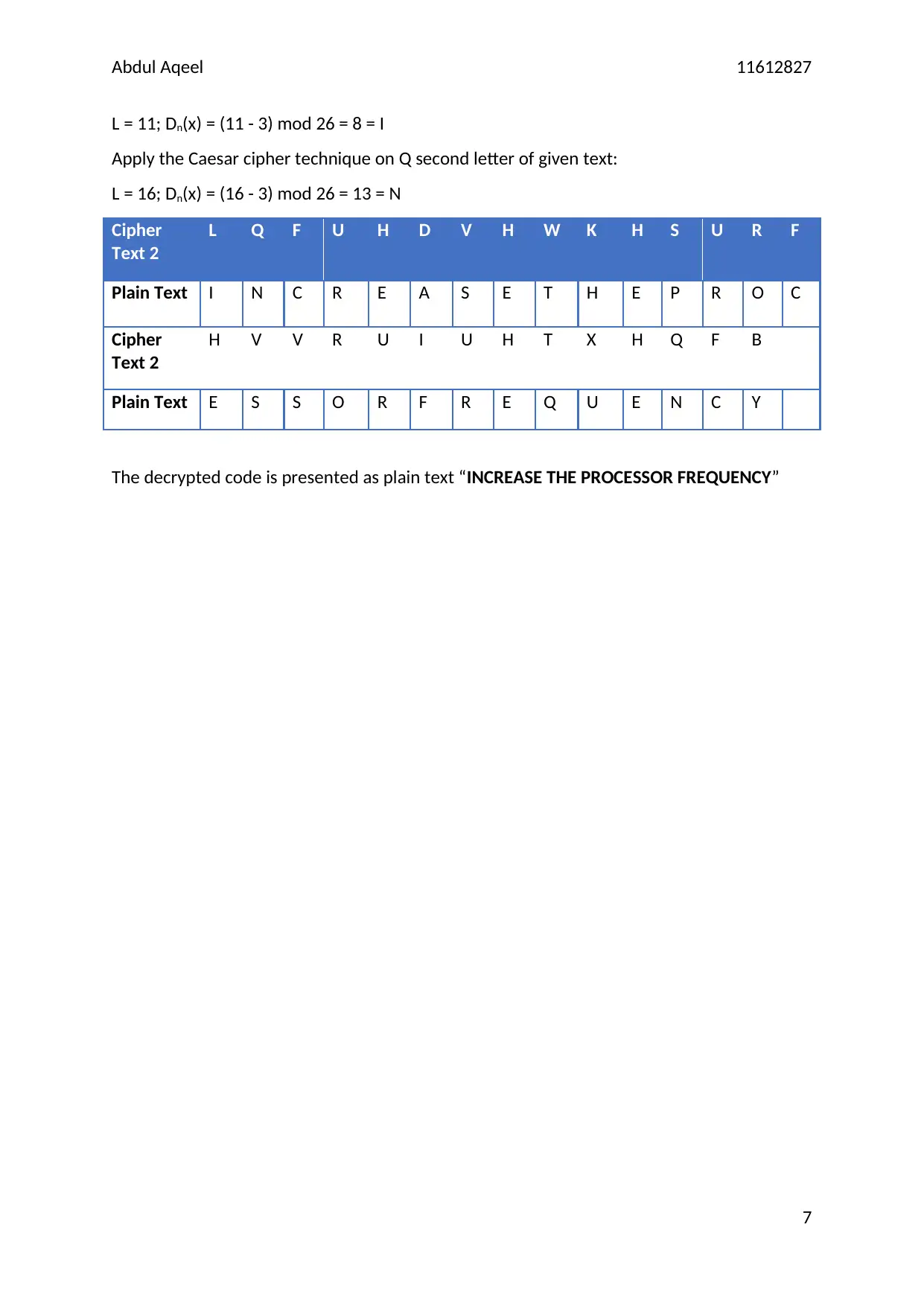
Abdul Aqeel 11612827
L = 11; Dn(x) = (11 - 3) mod 26 = 8 = I
Apply the Caesar cipher technique on Q second letter of given text:
L = 16; Dn(x) = (16 - 3) mod 26 = 13 = N
Cipher
Text 2
L Q F U H D V H W K H S U R F
Plain Text I N C R E A S E T H E P R O C
Cipher
Text 2
H V V R U I U H T X H Q F B
Plain Text E S S O R F R E Q U E N C Y
The decrypted code is presented as plain text “INCREASE THE PROCESSOR FREQUENCY”
7
L = 11; Dn(x) = (11 - 3) mod 26 = 8 = I
Apply the Caesar cipher technique on Q second letter of given text:
L = 16; Dn(x) = (16 - 3) mod 26 = 13 = N
Cipher
Text 2
L Q F U H D V H W K H S U R F
Plain Text I N C R E A S E T H E P R O C
Cipher
Text 2
H V V R U I U H T X H Q F B
Plain Text E S S O R F R E Q U E N C Y
The decrypted code is presented as plain text “INCREASE THE PROCESSOR FREQUENCY”
7

Abdul Aqeel 11612827
REFERENCES
365 Data Science. (2017). Retrieved from https://365datascience.com/false-positive-
vs-false-negative/
Atmmarketplace. (2017). Retrieved from
https://www.atmmarketplace.com/articles/atm-security-part-1-protecting-against-
brute-force-theft/
Crypto. (2017). Known-Plaintext Attack. Retrieved from
http://www.crypto-it.net/eng/attacks/known-plaintext.html
DASCALESCU, A. (2018). Retrieved from https://heimdalsecurity.com/blog/biometric-
authentication/
8
REFERENCES
365 Data Science. (2017). Retrieved from https://365datascience.com/false-positive-
vs-false-negative/
Atmmarketplace. (2017). Retrieved from
https://www.atmmarketplace.com/articles/atm-security-part-1-protecting-against-
brute-force-theft/
Crypto. (2017). Known-Plaintext Attack. Retrieved from
http://www.crypto-it.net/eng/attacks/known-plaintext.html
DASCALESCU, A. (2018). Retrieved from https://heimdalsecurity.com/blog/biometric-
authentication/
8
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




