Data Mining Assignment: Weka, Social Media, and Privacy Concerns
VerifiedAdded on 2023/01/16
|8
|1268
|35
Homework Assignment
AI Summary
This assignment comprises two tasks. Task 1 involves using Weka software to analyze the 'cpu.with.vendor.arff' dataset. The student is required to determine the number of instances and attributes, list the attributes and vendor values, and identify the class value of a specific instance. Task 2 focuses on a written exercise exploring how data mining techniques are used in social media platforms like Facebook and YouTube. The student discusses how these techniques compromise privacy, encourage addictive and manipulative behavior, and evaluates the significance of these effects for individuals and society. Additionally, the assignment includes a discussion of the ethical implications of these data mining practices, referencing articles on the subject and the Cambridge Analytica scandal. The student also provides a detailed explanation of how informed consent is a prerequisite for any research that involves human subjects.

Assessment Item 2: Weka and Written Exercise
Statistics
Student Name:
Instructor Name:
Course Number:
4 April 2019
Statistics
Student Name:
Instructor Name:
Course Number:
4 April 2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 1: Weka Visualization and Analysis
For this task, you are required to install the Weka software, that you will then use throughout
the duration of this subject. You will also do some tasks with the Weka software for data
visualization and analysis. The first task will build the practical and technical skills that will
enable you to compare and evaluate output patterns for visualization.
Load the cpu.with.vendor.arff dataset as follows: Click on the ‘Open file’ button on the top
left corner of the Weka panel, select the data folder and then the file
named cpu.with.vendor.arff. Use this data set to answer the following questions:
1. How many instances and attributes does the dataset have? [1 mark]
Answer
There are 8 attributes and 209 instances
2. List the attributes of the dataset [1 mark]
Answer
The attributes of the dataset are;
Vendor
MYCT
MMIN
MMAX
CACH
CHMIN
CHMAX
Class
3. List the values of the vendor attribute. How are they different from values of the
MYCT attribute? [2 marks]
Answer
The values of the vendor attribute are nominal (string). The values are as follows;
No. Label Count No. Label Count No. Label Count
1 adviser 1 11 dg 7 21 microdata 1
2 amdahl 9 12 formation 5 22 nas 19
3 apollo 2 13 four-phase 1 23 ncr 13
4 basf 2 14 gould 3 24 nixdorf 3
5 bti 2 15 hp 7 25 perkin-elmer 3
6 burroughs 8 16 harris 7 26 prime 5
7 c.r.d 6 17 honeywell 13 27 siemens 12
8 Cdc 9 18 ibm 32 28 sperry 13
For this task, you are required to install the Weka software, that you will then use throughout
the duration of this subject. You will also do some tasks with the Weka software for data
visualization and analysis. The first task will build the practical and technical skills that will
enable you to compare and evaluate output patterns for visualization.
Load the cpu.with.vendor.arff dataset as follows: Click on the ‘Open file’ button on the top
left corner of the Weka panel, select the data folder and then the file
named cpu.with.vendor.arff. Use this data set to answer the following questions:
1. How many instances and attributes does the dataset have? [1 mark]
Answer
There are 8 attributes and 209 instances
2. List the attributes of the dataset [1 mark]
Answer
The attributes of the dataset are;
Vendor
MYCT
MMIN
MMAX
CACH
CHMIN
CHMAX
Class
3. List the values of the vendor attribute. How are they different from values of the
MYCT attribute? [2 marks]
Answer
The values of the vendor attribute are nominal (string). The values are as follows;
No. Label Count No. Label Count No. Label Count
1 adviser 1 11 dg 7 21 microdata 1
2 amdahl 9 12 formation 5 22 nas 19
3 apollo 2 13 four-phase 1 23 ncr 13
4 basf 2 14 gould 3 24 nixdorf 3
5 bti 2 15 hp 7 25 perkin-elmer 3
6 burroughs 8 16 harris 7 26 prime 5
7 c.r.d 6 17 honeywell 13 27 siemens 12
8 Cdc 9 18 ibm 32 28 sperry 13
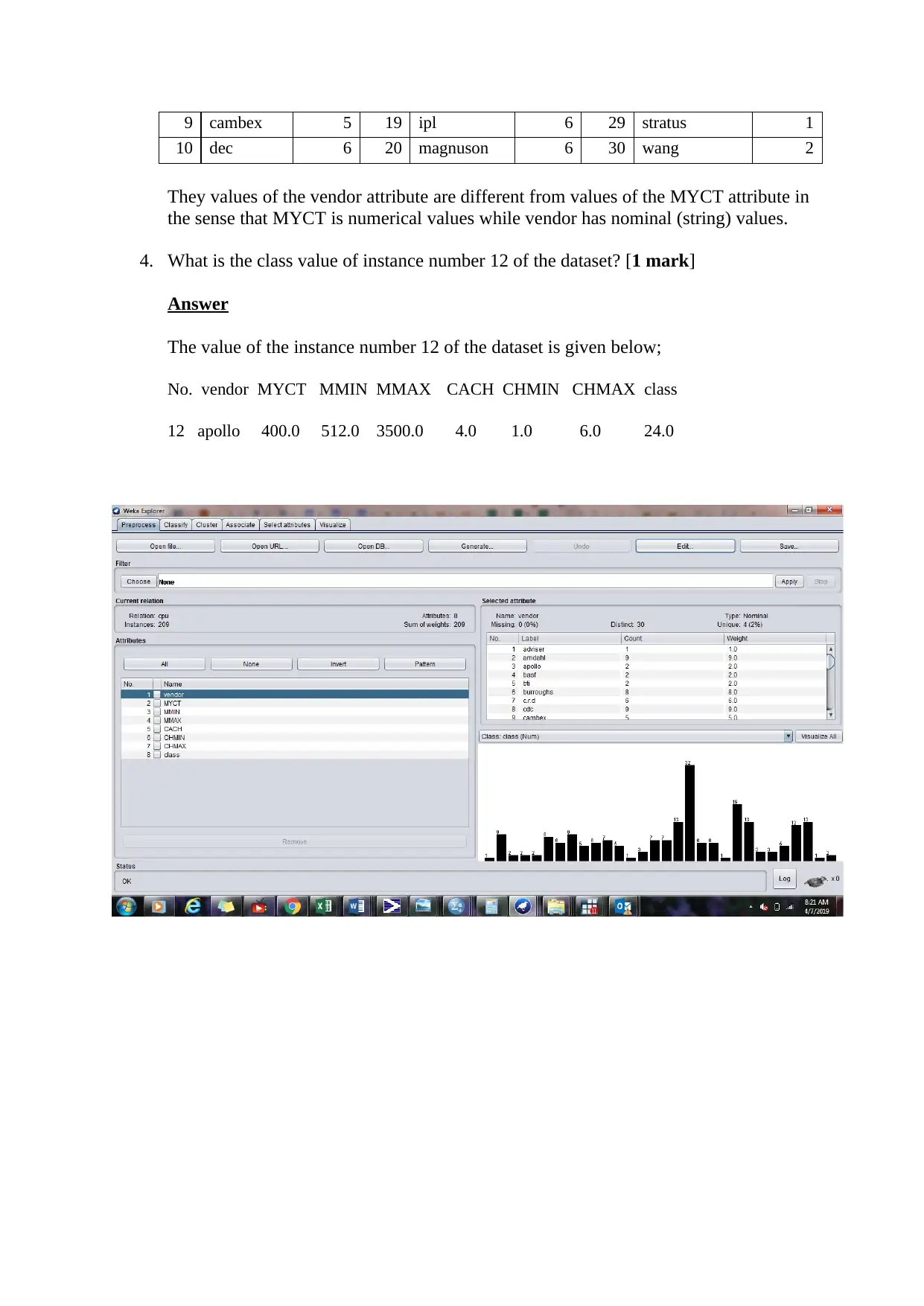
9 cambex 5 19 ipl 6 29 stratus 1
10 dec 6 20 magnuson 6 30 wang 2
They values of the vendor attribute are different from values of the MYCT attribute in
the sense that MYCT is numerical values while vendor has nominal (string) values.
4. What is the class value of instance number 12 of the dataset? [1 mark]
Answer
The value of the instance number 12 of the dataset is given below;
No. vendor MYCT MMIN MMAX CACH CHMIN CHMAX class
12 apollo 400.0 512.0 3500.0 4.0 1.0 6.0 24.0
10 dec 6 20 magnuson 6 30 wang 2
They values of the vendor attribute are different from values of the MYCT attribute in
the sense that MYCT is numerical values while vendor has nominal (string) values.
4. What is the class value of instance number 12 of the dataset? [1 mark]
Answer
The value of the instance number 12 of the dataset is given below;
No. vendor MYCT MMIN MMAX CACH CHMIN CHMAX class
12 apollo 400.0 512.0 3500.0 4.0 1.0 6.0 24.0
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 2: Written Exercise
Topic: Privacy, Addictive and Manipulative behavior in Social Media
In this task, you are required to read the journal articles provided below and write a short
discussion paper based on the topic of how data mining techniques are used in social media
applications such as Facebook and Youtube to compromise privacy and encourage addictive
and manipulative behavior.
Explanation of how data mining is used to compromise privacy and encourage
addictive and manipulative behavior
Most of the social media platforms such as Facebook use manipulative algorithms to
compromise privacy and encourage addictive behaviour (Krishnan , 2018). The control of
the opinion of the public over the social media platforms has risen as a great risk to the
general public life. Around the globe, various government bodies and ideological groups
are abusing the internet based platforms to spread garbage news and misinforming the
public, practice restriction and control, and undermine trust in media, open establishments
and science.
Data mining is also used to compromise privacy through obtaining private information
from the using by the use of application quizzes. Unsuspecting users are duped to answer
quizzes not knowing that their private information is being collected. Cambridge
Analytica-political research firm gained access to Facebook data for over 50 million users
by using a 3rd party that issued users with some kind of application on personality quiz a
— it is reported that the users (Facebook users) had totally no learning of this and had not
expressly given any form of consent for this to occur (What You Don’t Know About How
Facebook Uses Your Data, 2018).
Topic: Privacy, Addictive and Manipulative behavior in Social Media
In this task, you are required to read the journal articles provided below and write a short
discussion paper based on the topic of how data mining techniques are used in social media
applications such as Facebook and Youtube to compromise privacy and encourage addictive
and manipulative behavior.
Explanation of how data mining is used to compromise privacy and encourage
addictive and manipulative behavior
Most of the social media platforms such as Facebook use manipulative algorithms to
compromise privacy and encourage addictive behaviour (Krishnan , 2018). The control of
the opinion of the public over the social media platforms has risen as a great risk to the
general public life. Around the globe, various government bodies and ideological groups
are abusing the internet based platforms to spread garbage news and misinforming the
public, practice restriction and control, and undermine trust in media, open establishments
and science.
Data mining is also used to compromise privacy through obtaining private information
from the using by the use of application quizzes. Unsuspecting users are duped to answer
quizzes not knowing that their private information is being collected. Cambridge
Analytica-political research firm gained access to Facebook data for over 50 million users
by using a 3rd party that issued users with some kind of application on personality quiz a
— it is reported that the users (Facebook users) had totally no learning of this and had not
expressly given any form of consent for this to occur (What You Don’t Know About How
Facebook Uses Your Data, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

According to ethics and data privacy, a person whose data is being collected should be
informed and he/she should sign a consent authorizing the collection and use of such data
(Kshetri, 2014). The firm (Cambridge Analytica) not at any time acquired the clients'
consent to utilize their information, nor did Facebook inform their clients when it
discovered Cambridge had their data. This clearly shows how data mining is used to
compromise privacy and encourage addictive and manipulative behaviour.
Evaluation of the significance of these effects for individuals and society as a whole
The effects of data mining compromises the privacy of an individual. The manipulative
algorithms are geared towards influencing individuals to think in a certain way. The
algorithms are essentially positioned to influence how the social media users think so the
individual user can be influenced to act in a certain manner that the algorithm wants. The
effects can also spill over to the society in general where the society might get swayed
through the use of such data mining and manipulative algorithms to vote in a certain way.
Cambridge Analytica’s end goal was to use manipulative algorithms that would persuade
users to vote in favour of their client (The Facebook Data Mining Scandal — What
happened, 2018). This involved displaying messages that were intended to bring a
behaviour change among the users.
Discussion on the ethical implications of these data mining practices
Assenting to informed consent is both a legitimate and a moral prerequisite for any
examination or research that relates to human subjects (DeCosta, et al., 2014). It is where
a subject (human subject) is educated pretty much all parts of data mining, which are
critical for the subject to settle on a choice and in the wake of examining all parts of the
preliminary the participant voluntarily affirms his or her ability to take part in a specific
informed and he/she should sign a consent authorizing the collection and use of such data
(Kshetri, 2014). The firm (Cambridge Analytica) not at any time acquired the clients'
consent to utilize their information, nor did Facebook inform their clients when it
discovered Cambridge had their data. This clearly shows how data mining is used to
compromise privacy and encourage addictive and manipulative behaviour.
Evaluation of the significance of these effects for individuals and society as a whole
The effects of data mining compromises the privacy of an individual. The manipulative
algorithms are geared towards influencing individuals to think in a certain way. The
algorithms are essentially positioned to influence how the social media users think so the
individual user can be influenced to act in a certain manner that the algorithm wants. The
effects can also spill over to the society in general where the society might get swayed
through the use of such data mining and manipulative algorithms to vote in a certain way.
Cambridge Analytica’s end goal was to use manipulative algorithms that would persuade
users to vote in favour of their client (The Facebook Data Mining Scandal — What
happened, 2018). This involved displaying messages that were intended to bring a
behaviour change among the users.
Discussion on the ethical implications of these data mining practices
Assenting to informed consent is both a legitimate and a moral prerequisite for any
examination or research that relates to human subjects (DeCosta, et al., 2014). It is where
a subject (human subject) is educated pretty much all parts of data mining, which are
critical for the subject to settle on a choice and in the wake of examining all parts of the
preliminary the participant voluntarily affirms his or her ability to take part in a specific

study and noteworthiness of the exploration for headway of medicinal learning and social
welfare..
References
DeCosta, A., D’souza , N., Krishnan, S., Chhabra , M. S., Shihaam , I., & Goswami, K.
(2014). Community based trials and informed consent in rural north India. Journal of
Medical Ethics, 30(5), 318–23.
Krishnan , G.-M. (2018, June 15). Jaron Lanier interview on how social media ruins your
life. (G.-M. Krishnan , Producer) Retrieved April 9, 2019, from Channel4:
https://www.channel4.com/news/jaron-lanier-interview-on-how-social-media-ruins-
your-life
Kshetri, N. (2014). Big data׳s impact on privacy, security and consumer welfare.
Telecommunications Policy, 38(11), 1134–1145. doi:10.1016/j.telpol.2014.10.002
The Facebook Data Mining Scandal — What happened. (2018, March 29). Retrieved from A
Medium Corporation: https://medium.com/@IAMEIdentity/the-facebook-data-
mining-scandal-what-happened-82154855aeca
What You Don’t Know About How Facebook Uses Your Data. (2018, April 11). (N. Singer,
Producer) Retrieved April 9, 2019, from The New York Times:
https://www.nytimes.com/2018/04/11/technology/facebook-privacy-hearings.html
welfare..
References
DeCosta, A., D’souza , N., Krishnan, S., Chhabra , M. S., Shihaam , I., & Goswami, K.
(2014). Community based trials and informed consent in rural north India. Journal of
Medical Ethics, 30(5), 318–23.
Krishnan , G.-M. (2018, June 15). Jaron Lanier interview on how social media ruins your
life. (G.-M. Krishnan , Producer) Retrieved April 9, 2019, from Channel4:
https://www.channel4.com/news/jaron-lanier-interview-on-how-social-media-ruins-
your-life
Kshetri, N. (2014). Big data׳s impact on privacy, security and consumer welfare.
Telecommunications Policy, 38(11), 1134–1145. doi:10.1016/j.telpol.2014.10.002
The Facebook Data Mining Scandal — What happened. (2018, March 29). Retrieved from A
Medium Corporation: https://medium.com/@IAMEIdentity/the-facebook-data-
mining-scandal-what-happened-82154855aeca
What You Don’t Know About How Facebook Uses Your Data. (2018, April 11). (N. Singer,
Producer) Retrieved April 9, 2019, from The New York Times:
https://www.nytimes.com/2018/04/11/technology/facebook-privacy-hearings.html
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Screen shots
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1 out of 8
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
