Cybersecurity Analysis: Detecting DoS Attacks from Vendor's Network
VerifiedAdded on 2023/03/20
|17
|2675
|76
Report
AI Summary
This report presents an analysis of a Denial-of-Service (DoS) attack originating from a vendor's network, focusing on the use of a Snort Intrusion Detection System (IDS) within a Demilitarized Zone (DMZ). The report details the scenario, assumptions, and integral actions taken to secure the network. It outlines the information captured by Snort IDS, including its configuration and implementation within a virtual machine environment. The report covers the performance of a DoS attack using Kali Linux and Metasploit, demonstrating how Snort IDS detects and prevents such attacks. The report also explores the concept of SYN flood attacks and the use of Metasploit to launch them against a web server. The report concludes by emphasizing the role of IDS in monitoring and uncovering malicious activities, and provides references to relevant research papers.

Assignment
DOS Attack from the vendor's network
DOS Attack from the vendor's network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of contents
1. Introduction ……………………………………………………………………………….. 2
2. Scenario where DOS attack occur from vendor’s network ……………………………….. 2
3. Assumptions ……………………………………………………………………………….. 4
4. Integral actions ……………………………………………………………………………. 4
5. Information captured from snort IDS ……………………………………………………… 5
6. Configuration of snort IDS ………………………………………………………………… 5
7. Implementation of snort IDS in virtual machine ………………………………………….. 8
8. Performing DOS attack on kali linux, IDS and web server ………………………………. 10
9. Conclusion …………………………………………………………………………………. 13
10. Reference …………………………………………………………………………………. 14
Page 1
1. Introduction ……………………………………………………………………………….. 2
2. Scenario where DOS attack occur from vendor’s network ……………………………….. 2
3. Assumptions ……………………………………………………………………………….. 4
4. Integral actions ……………………………………………………………………………. 4
5. Information captured from snort IDS ……………………………………………………… 5
6. Configuration of snort IDS ………………………………………………………………… 5
7. Implementation of snort IDS in virtual machine ………………………………………….. 8
8. Performing DOS attack on kali linux, IDS and web server ………………………………. 10
9. Conclusion …………………………………………………………………………………. 13
10. Reference …………………………………………………………………………………. 14
Page 1

Introduction
As innovation advancement and capacities of data warfare have grown fundamentally as of late, the
likelihood of digital attacks have expanded too. PC organize attacks principally known as digital
attacks can crush enemy information, PC frameworks, and arranges, and can majorly affect a foe's
capacity to take up arms. In the digital field, the circumstance is, somehow or another, more awful
than essentially paying too little notice to a potential new risk until it shows itself. Dangers in the
digital field have showed themselves. We are helped continually to remember our vulnerabilities to
the risk, yet regardless we are not doing what's needed(Chen, Ho, Zhang, & Yu, 2017). Each hour of
consistently, some individual or gathering is composing or spreading another troublesome infection
or worm or is breaking into a PC arrange or to hurt a system by some different methods. It is
typically said that it is exceptionally profitable and easy to acquire PC our system and to expand its
use and yet it is altogether troublesome and undeniably progressively costly to create innovations to
make it secure essentially in light of the web, a system which is utilized to share data as opposed to
concealing it. Most digital aggressors are pulled in to high esteem targets, for example, systems,
servers, or switches, whose disturbance could yield money related.
Scenario where DOS attack occur from vendor's network.
As innovation advancement and capacities of data warfare have grown fundamentally as of late, the
likelihood of digital attacks have expanded too. PC organize attacks principally known as digital
attacks can crush enemy information, PC frameworks, and arranges, and can majorly affect a foe's
capacity to take up arms. In the digital field, the circumstance is, somehow or another, more awful
than essentially paying too little notice to a potential new risk until it shows itself. Dangers in the
digital field have showed themselves. We are helped continually to remember our vulnerabilities to
the risk, yet regardless we are not doing what's needed(Chen, Ho, Zhang, & Yu, 2017). Each hour of
consistently, some individual or gathering is composing or spreading another troublesome infection
or worm or is breaking into a PC arrange or to hurt a system by some different methods. It is
typically said that it is exceptionally profitable and easy to acquire PC our system and to expand its
use and yet it is altogether troublesome and undeniably progressively costly to create innovations to
make it secure essentially in light of the web, a system which is utilized to share data as opposed to
concealing it. Most digital aggressors are pulled in to high esteem targets, for example, systems,
servers, or switches, whose disturbance could yield money related.
Scenario where DOS attack occur from vendor's network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
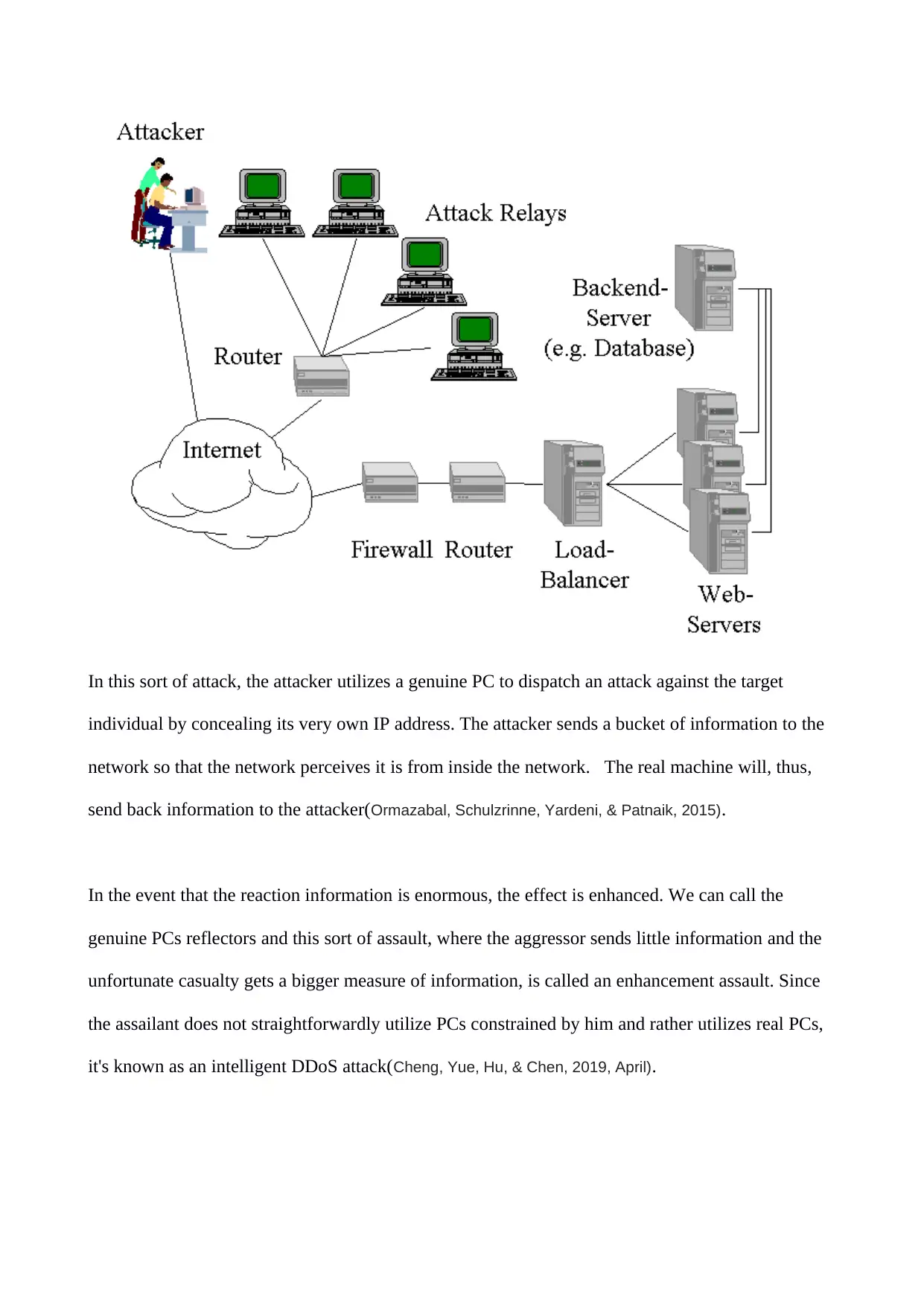
In this sort of attack, the attacker utilizes a genuine PC to dispatch an attack against the target
individual by concealing its very own IP address. The attacker sends a bucket of information to the
network so that the network perceives it is from inside the network. The real machine will, thus,
send back information to the attacker(Ormazabal, Schulzrinne, Yardeni, & Patnaik, 2015).
In the event that the reaction information is enormous, the effect is enhanced. We can call the
genuine PCs reflectors and this sort of assault, where the aggressor sends little information and the
unfortunate casualty gets a bigger measure of information, is called an enhancement assault. Since
the assailant does not straightforwardly utilize PCs constrained by him and rather utilizes real PCs,
it's known as an intelligent DDoS attack(Cheng, Yue, Hu, & Chen, 2019, April).
individual by concealing its very own IP address. The attacker sends a bucket of information to the
network so that the network perceives it is from inside the network. The real machine will, thus,
send back information to the attacker(Ormazabal, Schulzrinne, Yardeni, & Patnaik, 2015).
In the event that the reaction information is enormous, the effect is enhanced. We can call the
genuine PCs reflectors and this sort of assault, where the aggressor sends little information and the
unfortunate casualty gets a bigger measure of information, is called an enhancement assault. Since
the assailant does not straightforwardly utilize PCs constrained by him and rather utilizes real PCs,
it's known as an intelligent DDoS attack(Cheng, Yue, Hu, & Chen, 2019, April).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The reflectors are not traded off machines, not at all like botnets. Reflectors are machines that react
to a specific solicitation. It very well may be a DNS demand or a Networking Time Protocol (NTP)
demand, etc.
DNS intensification assaults, WordPress pingback assaults, and NTP assaults are enhancement
assaults. In a DNS intensification assault, the assailant sends a produced bundle to the DNS server
containing the IP address of the person in question. The DNS server answers back to the
unfortunate casualty rather with bigger information. Different sorts of enhancement assault
incorporate SMTP, SSDP, etc.
We will take a gander at a case of such an assault in the following segment. The PCs that are
utilized to send traffic to the injured individual are not the traded off ones and are called reflectors.
There are a few gatherings of digital crooks in charge of doing pay-off DDoS assaults, for example,
DD4BC, Armada Collective, Fancy Bear, XMR-Squad, and Lizard Squad.
These gatherings target undertakings. They will initially convey a coercion email, trailed by an
assault if the unfortunate casualty does not pay the payment.
(Chelladhurai, Chelliah, & Kumar, 2016, June).
Assumptions.
• A start to finish burrowing architecture: the organization transparently builds up a passage over
the interPLMN spine straightforwardly towards a Packet Data Gateway in the HPLMN
• Tunnel foundation is free of the underlying WLAN Access Authentication and Authorisation
(specifically, it is autonomously verified and approved)
to a specific solicitation. It very well may be a DNS demand or a Networking Time Protocol (NTP)
demand, etc.
DNS intensification assaults, WordPress pingback assaults, and NTP assaults are enhancement
assaults. In a DNS intensification assault, the assailant sends a produced bundle to the DNS server
containing the IP address of the person in question. The DNS server answers back to the
unfortunate casualty rather with bigger information. Different sorts of enhancement assault
incorporate SMTP, SSDP, etc.
We will take a gander at a case of such an assault in the following segment. The PCs that are
utilized to send traffic to the injured individual are not the traded off ones and are called reflectors.
There are a few gatherings of digital crooks in charge of doing pay-off DDoS assaults, for example,
DD4BC, Armada Collective, Fancy Bear, XMR-Squad, and Lizard Squad.
These gatherings target undertakings. They will initially convey a coercion email, trailed by an
assault if the unfortunate casualty does not pay the payment.
(Chelladhurai, Chelliah, & Kumar, 2016, June).
Assumptions.
• A start to finish burrowing architecture: the organization transparently builds up a passage over
the interPLMN spine straightforwardly towards a Packet Data Gateway in the HPLMN
• Tunnel foundation is free of the underlying WLAN Access Authentication and Authorisation
(specifically, it is autonomously verified and approved)

• After passage foundation, channels can be given to the VPLMN which permit characterization of
traffic-related with a solitary passage in the VPLMN
Integral Actions:
Organizations can take a few strategic strides to secure themselves. These include:
Authorizing a multi-layered safeguard methodology. Guarantee that it covers your whole
endeavor, all endpoints, cell phones, applications, and information. Where conceivable, use
encryption and a few factor validation for system and information get to.
Playing out an vendor evaluation or making administration level concurrences with vendors:
Implement a "least benefit" approach in regards to who and what others can get to. Make it a
propensity to survey the utilization of accreditations with vendors. You could even make it a stride
further with an administration level understanding, which authoritatively commits that vendors
follow your organization's security approaches. Your SLA should give your organization the
privilege to review the vendor's consistence.
Ceaselessly backing-up information. This can defend against ransomware, which freezes PC
documents until the victims fulfills the money related needs. Sponsorship up information can
demonstrate basic if your PCs or servers get bolted in light of the fact that you wouldn't have to pay
for access to your information.
Patching frequently. A product fix is a code update in existing programming. They are regularly
impermanent fixes between full arrivals of programming. A fix may fix a product bug, address new
security powerlessness, address programming dependability issues, or put in new drivers.
Whitelisting software applications. Application whitelisting would keep PCs from introducing
non-endorsed software. This enables overseers to have substantially more control.
Information captured in snort IDS.
traffic-related with a solitary passage in the VPLMN
Integral Actions:
Organizations can take a few strategic strides to secure themselves. These include:
Authorizing a multi-layered safeguard methodology. Guarantee that it covers your whole
endeavor, all endpoints, cell phones, applications, and information. Where conceivable, use
encryption and a few factor validation for system and information get to.
Playing out an vendor evaluation or making administration level concurrences with vendors:
Implement a "least benefit" approach in regards to who and what others can get to. Make it a
propensity to survey the utilization of accreditations with vendors. You could even make it a stride
further with an administration level understanding, which authoritatively commits that vendors
follow your organization's security approaches. Your SLA should give your organization the
privilege to review the vendor's consistence.
Ceaselessly backing-up information. This can defend against ransomware, which freezes PC
documents until the victims fulfills the money related needs. Sponsorship up information can
demonstrate basic if your PCs or servers get bolted in light of the fact that you wouldn't have to pay
for access to your information.
Patching frequently. A product fix is a code update in existing programming. They are regularly
impermanent fixes between full arrivals of programming. A fix may fix a product bug, address new
security powerlessness, address programming dependability issues, or put in new drivers.
Whitelisting software applications. Application whitelisting would keep PCs from introducing
non-endorsed software. This enables overseers to have substantially more control.
Information captured in snort IDS.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

System Intrusion Detection System (NIDS) that catch information bundles going on the
system media and match them to a database of marks
Host-based Intrusion Detection System (HIDS) that are introduced as operators on a host.
This framework can investigate framework and application log records to recognize any
gatecrasher action
Engraving based interruption affirmation structures screen the majority of the packs crossing
the system and look at them against a database of imprint of known malicious dangers,
much like antivirus programming(Gope, Lee, & Quek, 2016).
Configuring snort IDS
Introduction to IDS
IDS Stands for Intrusion Detection System. The procedures and techniques on which an IDS is
established on are utilized to screen and uncover malignant exercises both on the host and system
level. When the said exercises happen then an alarm is issued to mindful all of the assault. It tends
to be equipment or programming or a blend of both; relies upon the prerequisite. An IDS utilize
both mark or peculiarity based procedure together or independently; again relying upon necessity.
Your system topology figures out where to include interruption discovery frameworks. Regardless
of whether it ought to be situated at least one spots relies upon in the event that you need to follow
inner danger or outer risk. For example, on the off chance that you need to shield yourself from
outside traffic, at that point you should put an IDS at the switch and in the event that you need to
ensure the internal system, at that point place the IDS on each system section(Wei, Fung, 2015, June).
Classifications of IDS
Signature-Based IDS
system media and match them to a database of marks
Host-based Intrusion Detection System (HIDS) that are introduced as operators on a host.
This framework can investigate framework and application log records to recognize any
gatecrasher action
Engraving based interruption affirmation structures screen the majority of the packs crossing
the system and look at them against a database of imprint of known malicious dangers,
much like antivirus programming(Gope, Lee, & Quek, 2016).
Configuring snort IDS
Introduction to IDS
IDS Stands for Intrusion Detection System. The procedures and techniques on which an IDS is
established on are utilized to screen and uncover malignant exercises both on the host and system
level. When the said exercises happen then an alarm is issued to mindful all of the assault. It tends
to be equipment or programming or a blend of both; relies upon the prerequisite. An IDS utilize
both mark or peculiarity based procedure together or independently; again relying upon necessity.
Your system topology figures out where to include interruption discovery frameworks. Regardless
of whether it ought to be situated at least one spots relies upon in the event that you need to follow
inner danger or outer risk. For example, on the off chance that you need to shield yourself from
outside traffic, at that point you should put an IDS at the switch and in the event that you need to
ensure the internal system, at that point place the IDS on each system section(Wei, Fung, 2015, June).
Classifications of IDS
Signature-Based IDS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
This IDS checks marks of information parcels in the system traffic. Fundamentally, it finds the
information bundles and uses their marks to affirm whether they are a danger or not. Such marks are
generally known for interruption related marks or peculiarities identified with web convention.
Gatecrashers, for example, PC infections, and so forth, dependably have a mark, subsequently, it
tends to be effectively recognized by programming IDS. As it utilizes marks to recognize the
dangers(Wu, Zhang, Yue, 2016).
Anomaly IDS
This IDS generally distinguishes if an information parcel carries on irregularity. It issues an alarm if
parcel inconsistencies are available in convention header parts. This framework creates preferred
outcomes at times over mark based IDS. Ordinarily such IDS catches information from the system
and on these bundles, it at that point applies the standards to it so as to identify irregularities(Dridi,
Zhani, 2016, October).
Snort is installed with the command below;
After installation is complete, open configuration file via nano or any other text editor with the
command below;
After opening, set up the network addresses that you would like to protect. For example, in our case
it is;
information bundles and uses their marks to affirm whether they are a danger or not. Such marks are
generally known for interruption related marks or peculiarities identified with web convention.
Gatecrashers, for example, PC infections, and so forth, dependably have a mark, subsequently, it
tends to be effectively recognized by programming IDS. As it utilizes marks to recognize the
dangers(Wu, Zhang, Yue, 2016).
Anomaly IDS
This IDS generally distinguishes if an information parcel carries on irregularity. It issues an alarm if
parcel inconsistencies are available in convention header parts. This framework creates preferred
outcomes at times over mark based IDS. Ordinarily such IDS catches information from the system
and on these bundles, it at that point applies the standards to it so as to identify irregularities(Dridi,
Zhani, 2016, October).
Snort is installed with the command below;
After installation is complete, open configuration file via nano or any other text editor with the
command below;
After opening, set up the network addresses that you would like to protect. For example, in our case
it is;
We now run the below command to enable IDS mode of the snort;
We can start making changes to the rules in snort through the commands given below;
Implementation of the configuration in (4) above
Installation of snort IDS
Type the command below
We can start making changes to the rules in snort through the commands given below;
Implementation of the configuration in (4) above
Installation of snort IDS
Type the command below
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Set up addresses to protect in the network
Enable IDS by running the command below;
Enable IDS by running the command below;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
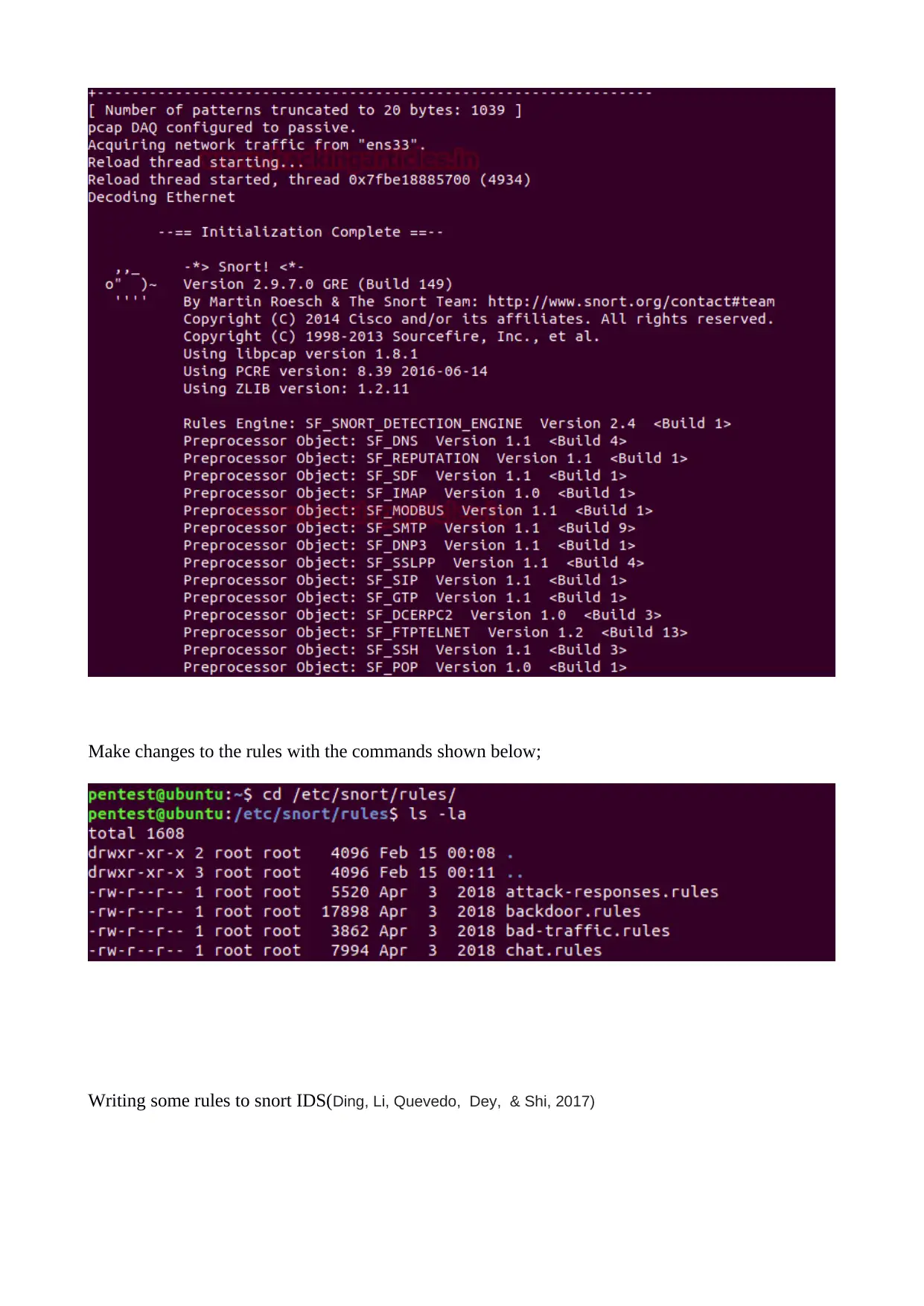
Make changes to the rules with the commands shown below;
Writing some rules to snort IDS(Ding, Li, Quevedo, Dey, & Shi, 2017)
Writing some rules to snort IDS(Ding, Li, Quevedo, Dey, & Shi, 2017)
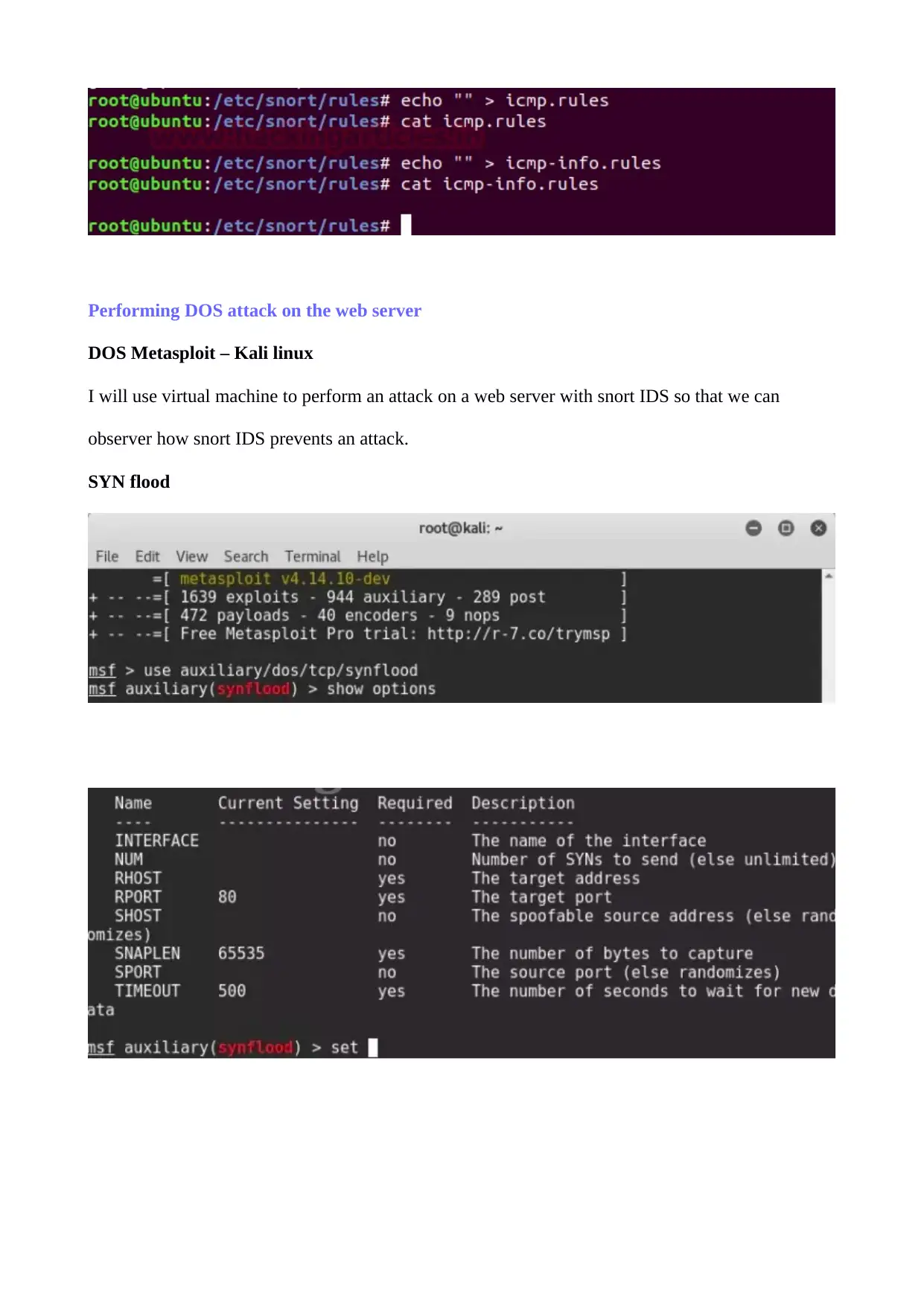
Performing DOS attack on the web server
DOS Metasploit – Kali linux
I will use virtual machine to perform an attack on a web server with snort IDS so that we can
observer how snort IDS prevents an attack.
SYN flood
DOS Metasploit – Kali linux
I will use virtual machine to perform an attack on a web server with snort IDS so that we can
observer how snort IDS prevents an attack.
SYN flood
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



