DOS Attack from the vendor's network
Added on 2023-03-20
17 Pages2675 Words76 Views
Assignment
DOS Attack from the vendor's network
DOS Attack from the vendor's network

Table of contents
1. Introduction ............................................................................................ 2
2. Scenario where DOS attack occur from vendor’s network ...................................... 2
3. Assumptions ............................................................................................ 4
4. Integral actions ........................................................................................ 4
5. Information captured from snort IDS ............................................................... 5
6. Configuration of snort IDS ........................................................................... 5
7. Implementation of snort IDS in virtual machine .................................................. 8
8. Performing DOS attack on kali linux, IDS and web server ..................................... 10
9. Conclusion .............................................................................................. 13
10. Reference .............................................................................................. 14
Page 1
1. Introduction ............................................................................................ 2
2. Scenario where DOS attack occur from vendor’s network ...................................... 2
3. Assumptions ............................................................................................ 4
4. Integral actions ........................................................................................ 4
5. Information captured from snort IDS ............................................................... 5
6. Configuration of snort IDS ........................................................................... 5
7. Implementation of snort IDS in virtual machine .................................................. 8
8. Performing DOS attack on kali linux, IDS and web server ..................................... 10
9. Conclusion .............................................................................................. 13
10. Reference .............................................................................................. 14
Page 1

Introduction
As innovation advancement and capacities of data warfare have grown fundamentally as of late, the
likelihood of digital attacks have expanded too. PC organize attacks principally known as digital
attacks can crush enemy information, PC frameworks, and arranges, and can majorly affect a foe's
capacity to take up arms. In the digital field, the circumstance is, somehow or another, more awful
than essentially paying too little notice to a potential new risk until it shows itself. Dangers in the
digital field have showed themselves. We are helped continually to remember our vulnerabilities to
the risk, yet regardless we are not doing what's needed(Chen, Ho, Zhang, & Yu, 2017). Each hour of
consistently, some individual or gathering is composing or spreading another troublesome infection
or worm or is breaking into a PC arrange or to hurt a system by some different methods. It is
typically said that it is exceptionally profitable and easy to acquire PC our system and to expand its
use and yet it is altogether troublesome and undeniably progressively costly to create innovations to
make it secure essentially in light of the web, a system which is utilized to share data as opposed to
concealing it. Most digital aggressors are pulled in to high esteem targets, for example, systems,
servers, or switches, whose disturbance could yield money related.
Scenario where DOS attack occur from vendor's network.
As innovation advancement and capacities of data warfare have grown fundamentally as of late, the
likelihood of digital attacks have expanded too. PC organize attacks principally known as digital
attacks can crush enemy information, PC frameworks, and arranges, and can majorly affect a foe's
capacity to take up arms. In the digital field, the circumstance is, somehow or another, more awful
than essentially paying too little notice to a potential new risk until it shows itself. Dangers in the
digital field have showed themselves. We are helped continually to remember our vulnerabilities to
the risk, yet regardless we are not doing what's needed(Chen, Ho, Zhang, & Yu, 2017). Each hour of
consistently, some individual or gathering is composing or spreading another troublesome infection
or worm or is breaking into a PC arrange or to hurt a system by some different methods. It is
typically said that it is exceptionally profitable and easy to acquire PC our system and to expand its
use and yet it is altogether troublesome and undeniably progressively costly to create innovations to
make it secure essentially in light of the web, a system which is utilized to share data as opposed to
concealing it. Most digital aggressors are pulled in to high esteem targets, for example, systems,
servers, or switches, whose disturbance could yield money related.
Scenario where DOS attack occur from vendor's network.

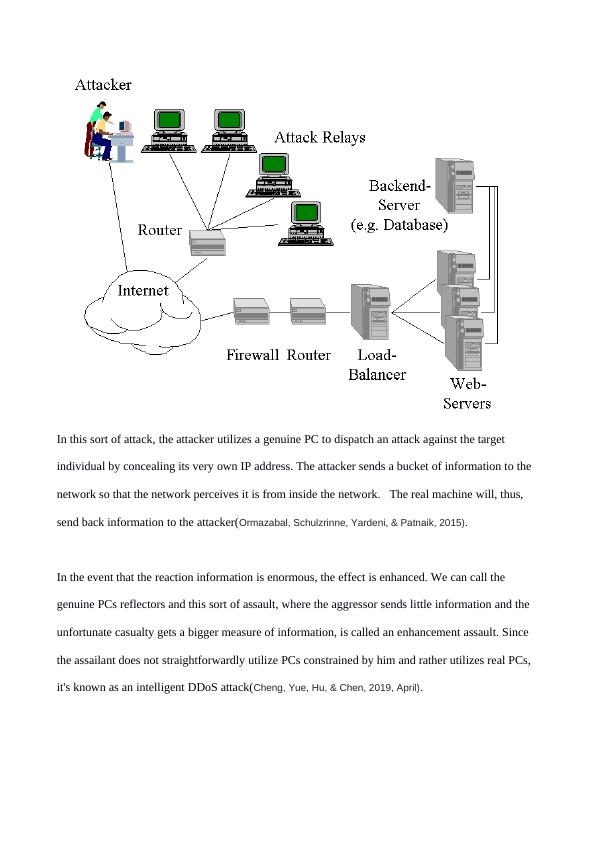
In this sort of attack, the attacker utilizes a genuine PC to dispatch an attack against the target
individual by concealing its very own IP address. The attacker sends a bucket of information to the
network so that the network perceives it is from inside the network. The real machine will, thus,
send back information to the attacker(Ormazabal, Schulzrinne, Yardeni, & Patnaik, 2015).
In the event that the reaction information is enormous, the effect is enhanced. We can call the
genuine PCs reflectors and this sort of assault, where the aggressor sends little information and the
unfortunate casualty gets a bigger measure of information, is called an enhancement assault. Since
the assailant does not straightforwardly utilize PCs constrained by him and rather utilizes real PCs,
it's known as an intelligent DDoS attack(Cheng, Yue, Hu, & Chen, 2019, April).
individual by concealing its very own IP address. The attacker sends a bucket of information to the
network so that the network perceives it is from inside the network. The real machine will, thus,
send back information to the attacker(Ormazabal, Schulzrinne, Yardeni, & Patnaik, 2015).
In the event that the reaction information is enormous, the effect is enhanced. We can call the
genuine PCs reflectors and this sort of assault, where the aggressor sends little information and the
unfortunate casualty gets a bigger measure of information, is called an enhancement assault. Since
the assailant does not straightforwardly utilize PCs constrained by him and rather utilizes real PCs,
it's known as an intelligent DDoS attack(Cheng, Yue, Hu, & Chen, 2019, April).
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
DOS Attack from the vendor's networklg...
|16
|2585
|39
DOS attack from the vendor’s networklg...
|21
|2684
|488
DOS Attack on Web Serverlg...
|15
|2149
|61
Secure Network Assignment 2022lg...
|29
|5551
|13