Mitigating DOS Attacks on Web Servers: Analysis & Snort IDS Setup
VerifiedAdded on 2023/03/23
|15
|2149
|61
Report
AI Summary
This report provides a detailed analysis of Denial of Service (DOS) attacks on web servers and offers solutions for mitigation, focusing on the configuration and implementation of Snort Intrusion Detection System (IDS). It begins by outlining a DOS attack scenario, assumptions, and solutions to address cyber security attacks, emphasizing the importance of real-time intelligence in preventing and containing such attacks. The report then delves into the specifics of Snort IDS, including its components, configuration steps, and implementation, demonstrating how it works to detect and prevent malicious activities. It also covers the types of IDS (NIDS and HIDS) and their roles in network security. The conclusion highlights the necessity for organizations to proactively protect themselves against cyber threats to avoid reputational damage and financial losses, referencing multiple research papers and articles.

Assignment
DOS Attack on web server
DOS Attack on web server
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of contents
1. Introduction ……………………………………………………………………………………. 2
2. DOS attack scenario ……………………………………………………………………………. 2
3. Assumptions ……………………………………………………………………………………. 3
4. Solutions to address cyber security attack ……………………………………………………… 4
5. Information gathered from snort IDS ………………………………………………………….. 5
6. Configuring snort IDS …………………………………………………………………………. 6
7. Implementation of configuration on snort IDS ……………………………………………….. 7
8. Demonstration of how snort IDS works ………………………………………………………. 9
9. Conclusion ……………………………………………………………………………………. 11
10. Reference ……………………………………………………………………………………. 12
Page 1
1. Introduction ……………………………………………………………………………………. 2
2. DOS attack scenario ……………………………………………………………………………. 2
3. Assumptions ……………………………………………………………………………………. 3
4. Solutions to address cyber security attack ……………………………………………………… 4
5. Information gathered from snort IDS ………………………………………………………….. 5
6. Configuring snort IDS …………………………………………………………………………. 6
7. Implementation of configuration on snort IDS ……………………………………………….. 7
8. Demonstration of how snort IDS works ………………………………………………………. 9
9. Conclusion ……………………………………………………………………………………. 11
10. Reference ……………………………………………………………………………………. 12
Page 1

Introduction
Nowadays, individuals spend much time on the Internet. This virtual world to a great extent mirrors
the genuine one: there is wrongdoing, which tragically is a necessary piece of society. The
developing trade of data and electronic installments - this is actually the goody that draws in
lawbreakers. The purpose of the current day cybercrime is to extort money from organizations.
They are well structured and planned by the hackers. Productivity, chance administration,
improvement of new markets are likewise its significant parts. Casualties of cybercriminals, are
private clients, undertakings and associations everything being equal. Monetary harm from such
vindictive acts could reach $9 trillion by 2021. Among different dangers, late attacks have prompted
the conclusion of independent ventures, delays in performing indispensable careful tasks and
disturbances in the arrangement of open administrations.
DOS Attack scenario.
The Armada Collective group was first observed in 2015. They attacked different money related
administrations and web facilitating destinations in Russia, Switzerland, Greece, and Thailand.
They again re-developed in Central Europe in October 2017. They used to do a demo-DDoS assault
to compromise the person in question.
Here is a coercion letter from Armada Collective:
Page 2
Nowadays, individuals spend much time on the Internet. This virtual world to a great extent mirrors
the genuine one: there is wrongdoing, which tragically is a necessary piece of society. The
developing trade of data and electronic installments - this is actually the goody that draws in
lawbreakers. The purpose of the current day cybercrime is to extort money from organizations.
They are well structured and planned by the hackers. Productivity, chance administration,
improvement of new markets are likewise its significant parts. Casualties of cybercriminals, are
private clients, undertakings and associations everything being equal. Monetary harm from such
vindictive acts could reach $9 trillion by 2021. Among different dangers, late attacks have prompted
the conclusion of independent ventures, delays in performing indispensable careful tasks and
disturbances in the arrangement of open administrations.
DOS Attack scenario.
The Armada Collective group was first observed in 2015. They attacked different money related
administrations and web facilitating destinations in Russia, Switzerland, Greece, and Thailand.
They again re-developed in Central Europe in October 2017. They used to do a demo-DDoS assault
to compromise the person in question.
Here is a coercion letter from Armada Collective:
Page 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This group is known to bring out intelligent DoS attacks through NTP. The NTP convention is a
convention that is utilized to synchronize PC check times in a convention. The NTP convention
gives help in decision making in the network. At the point when an overseer sends the monlist order
to a NTP server, the server reacts with a rundown of 600 hosts that are associated with that NTP
server.
The attacker can misuse this by making a fashioned NTP parcel which has a monlist order
containing the IP address of the person in question and after that sending various duplicates to the
NTP server. The NTP server send reaction to more that 600 PCs connected to the server upon
receiving instruction from the unkown address. Accordingly the injured individual gets an excessive
amount of information from the NTP reaction and it can crash:
Assumptions.
• Ttunneling engineering: the association straightforwardly develops an entry over the interPLMN
spine direct towards a Packet Data Gateway in the HPLMN
• Tunnel establishment is free of the basic WLAN Access Authentication and Authorisation.
Page 3
convention that is utilized to synchronize PC check times in a convention. The NTP convention
gives help in decision making in the network. At the point when an overseer sends the monlist order
to a NTP server, the server reacts with a rundown of 600 hosts that are associated with that NTP
server.
The attacker can misuse this by making a fashioned NTP parcel which has a monlist order
containing the IP address of the person in question and after that sending various duplicates to the
NTP server. The NTP server send reaction to more that 600 PCs connected to the server upon
receiving instruction from the unkown address. Accordingly the injured individual gets an excessive
amount of information from the NTP reaction and it can crash:
Assumptions.
• Ttunneling engineering: the association straightforwardly develops an entry over the interPLMN
spine direct towards a Packet Data Gateway in the HPLMN
• Tunnel establishment is free of the basic WLAN Access Authentication and Authorisation.
Page 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

• After entry establishment, channels can be given to the VPLMN which grant portrayal of traffic-
related with a lone section in the VPLMN
Solution to address cyber security attack.
Real time intelligence is an amazing asset for avoiding and containing cyber attacks. The more it
takes to recognize a hack, the more exorbitant it results. A research carried out by Ponemon
Institute stated that the IT team should notice cyber attack in there systems within the first 15
minutes. With only 120 seconds' notice of a trade off, coming about expenses could be decreased
by 30%.
As indicated by James Hatch, chief of digital administrations at BAE Systems, "Recognizing [a
cyber attack] early is critical. It could be the contrast between losing 10% of your [computers] and
half." Unfortunately, as a general rule, overall it takes organizations over seven months to find a
pernicious attack.
With laws expecting organizations to uncover cyber attacks and the dimension at which these
attacks happen, it is never again less expensive to fix the attack than it is to proactively stop them.
Organizations need to alleviate these dangers or risk harming their notorieties to the point that
clients never again trust them with their business. Many organizations do not know were to start
protecting their systems against cyber attack. Some of the steps that an organisation should take
include;
Keeping systems upto date by applying the most recent patches to PCs, servers, and
equipment. These patches frequently contain basic security refreshes that plug known
vulnerabilities.
related with a lone section in the VPLMN
Solution to address cyber security attack.
Real time intelligence is an amazing asset for avoiding and containing cyber attacks. The more it
takes to recognize a hack, the more exorbitant it results. A research carried out by Ponemon
Institute stated that the IT team should notice cyber attack in there systems within the first 15
minutes. With only 120 seconds' notice of a trade off, coming about expenses could be decreased
by 30%.
As indicated by James Hatch, chief of digital administrations at BAE Systems, "Recognizing [a
cyber attack] early is critical. It could be the contrast between losing 10% of your [computers] and
half." Unfortunately, as a general rule, overall it takes organizations over seven months to find a
pernicious attack.
With laws expecting organizations to uncover cyber attacks and the dimension at which these
attacks happen, it is never again less expensive to fix the attack than it is to proactively stop them.
Organizations need to alleviate these dangers or risk harming their notorieties to the point that
clients never again trust them with their business. Many organizations do not know were to start
protecting their systems against cyber attack. Some of the steps that an organisation should take
include;
Keeping systems upto date by applying the most recent patches to PCs, servers, and
equipment. These patches frequently contain basic security refreshes that plug known
vulnerabilities.

Page 4
Setting up a procedure for the reinforcement and recuperation of fundamental information.
With this set up, a business can recoup from ransomware dangers and obliteration brought
about by insider dangers without costly cleanup costs.
Character and access the executives arrangements that limit clients from getting to
information that they don't have to see. IAM study prefers that most of the clients should be
working on offline mode so that in case of cyber attack, it can’t affect the whole system.
Appropriately arranged security controls that alert you to potential assaults and help frustrate
them. These incorporate firewalls, hostile to malware applications, interruption discovery
and anticipation arrangements, and email security arrangements.
Having multiple cyber security team in an organization. By not depending on a solitary
seller, you can work with items and arrangements that attention on explicit requirements
from specialists instead of a merchant that is a handyman yet ace of none.
Information gathered from snort IDS.
Host impedance region structures keep running on all PCs or contraptions in the system with
direct access to both the web and the endeavor internal system. HIDS have extraordinary
position over NIDS in that they may more then likely recognize odd structure bundles that
begin from inside the alliance or poisonous traffic that a NIDS has neglect to see. HIDS may
additionally have the choice to see destructive traffic that begins from the host itself, as
when the host has been sullied with malware and is endeavoring to spread to different
frameworks.
SIDS gathers information packet on the network and compares it with the database data.
Setting up a procedure for the reinforcement and recuperation of fundamental information.
With this set up, a business can recoup from ransomware dangers and obliteration brought
about by insider dangers without costly cleanup costs.
Character and access the executives arrangements that limit clients from getting to
information that they don't have to see. IAM study prefers that most of the clients should be
working on offline mode so that in case of cyber attack, it can’t affect the whole system.
Appropriately arranged security controls that alert you to potential assaults and help frustrate
them. These incorporate firewalls, hostile to malware applications, interruption discovery
and anticipation arrangements, and email security arrangements.
Having multiple cyber security team in an organization. By not depending on a solitary
seller, you can work with items and arrangements that attention on explicit requirements
from specialists instead of a merchant that is a handyman yet ace of none.
Information gathered from snort IDS.
Host impedance region structures keep running on all PCs or contraptions in the system with
direct access to both the web and the endeavor internal system. HIDS have extraordinary
position over NIDS in that they may more then likely recognize odd structure bundles that
begin from inside the alliance or poisonous traffic that a NIDS has neglect to see. HIDS may
additionally have the choice to see destructive traffic that begins from the host itself, as
when the host has been sullied with malware and is endeavoring to spread to different
frameworks.
SIDS gathers information packet on the network and compares it with the database data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Page 5
Host-based Intrusion Detection System that are introduced as operators on a host. This
framework can investigate framework and application log documents to recognize any
interloper action
Configuring snort IDS
Types of IDS
NIDS
NIDS represent Network Intrusion Detection System. The snort IDS gathers all the packets passing
through the network and compares with the ones stored in the database. In case a packet coming
from outside matches the one in the database then alarm will be raised on the system.Grunt is an
astounding case of a NIDS.
HIDS
HIDS represents Host Intrusion Detection System which, clearly, goes about as a host. Such sorts of
IDS screen framework and application logs to identify interloper movement. A few IDS responds
when some vindictive movement happens, others screen every one of the deals going to the host
where IDS is introduced and give cautions continuously.
Introduction to snort
Snort is a Network Intrusion Detection System (NIDS). It's very prevalent and is open source which
which helps in screen organize traffic progressively, thus it can likewise be considered as a parcel
sniffer. Basically snort IDS analyses all the data packets passing through the network to ensure that
there is no malware or payload. It can also be used for investigating and and searching if there are
any malware in the system . It is fit for distinguishing different assaults like port sweeps, cradle
flood, and so forth. It's accessible for all stages for example Windows, Linux, and so forth. It
doesn't require any recompilation with the framework or equipment to added to your conveyance;
Host-based Intrusion Detection System that are introduced as operators on a host. This
framework can investigate framework and application log documents to recognize any
interloper action
Configuring snort IDS
Types of IDS
NIDS
NIDS represent Network Intrusion Detection System. The snort IDS gathers all the packets passing
through the network and compares with the ones stored in the database. In case a packet coming
from outside matches the one in the database then alarm will be raised on the system.Grunt is an
astounding case of a NIDS.
HIDS
HIDS represents Host Intrusion Detection System which, clearly, goes about as a host. Such sorts of
IDS screen framework and application logs to identify interloper movement. A few IDS responds
when some vindictive movement happens, others screen every one of the deals going to the host
where IDS is introduced and give cautions continuously.
Introduction to snort
Snort is a Network Intrusion Detection System (NIDS). It's very prevalent and is open source which
which helps in screen organize traffic progressively, thus it can likewise be considered as a parcel
sniffer. Basically snort IDS analyses all the data packets passing through the network to ensure that
there is no malware or payload. It can also be used for investigating and and searching if there are
any malware in the system . It is fit for distinguishing different assaults like port sweeps, cradle
flood, and so forth. It's accessible for all stages for example Windows, Linux, and so forth. It
doesn't require any recompilation with the framework or equipment to added to your conveyance;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Page 6
root benefits are required however. It reviews all the system traffic against the gave set of
guidelines and
after that alarms the organization about any suspicious action. it's isolated into numerous parts and
every one of the segments cooperate to identify an interruption. Following are the significant parts
of snort :
Parcel Decoder
Pre-processors
Location Engine
Logging and Alerting System
Yield Modules
Configuring snort IDS
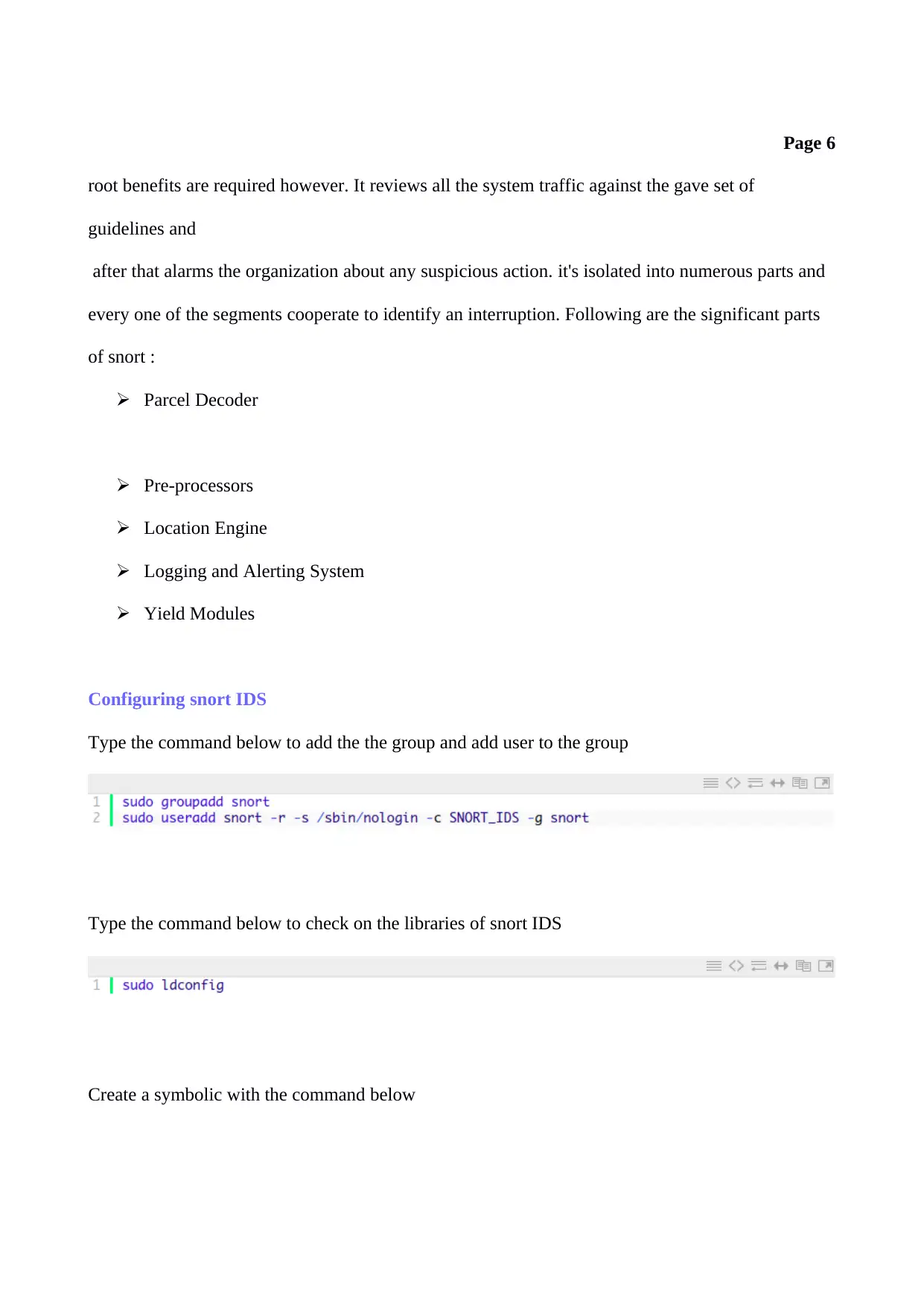
Type the command below to add the the group and add user to the group
Type the command below to check on the libraries of snort IDS
Create a symbolic with the command below
root benefits are required however. It reviews all the system traffic against the gave set of
guidelines and
after that alarms the organization about any suspicious action. it's isolated into numerous parts and
every one of the segments cooperate to identify an interruption. Following are the significant parts
of snort :
Parcel Decoder
Pre-processors
Location Engine
Logging and Alerting System
Yield Modules
Configuring snort IDS
Type the command below to add the the group and add user to the group
Type the command below to check on the libraries of snort IDS
Create a symbolic with the command below
Page7
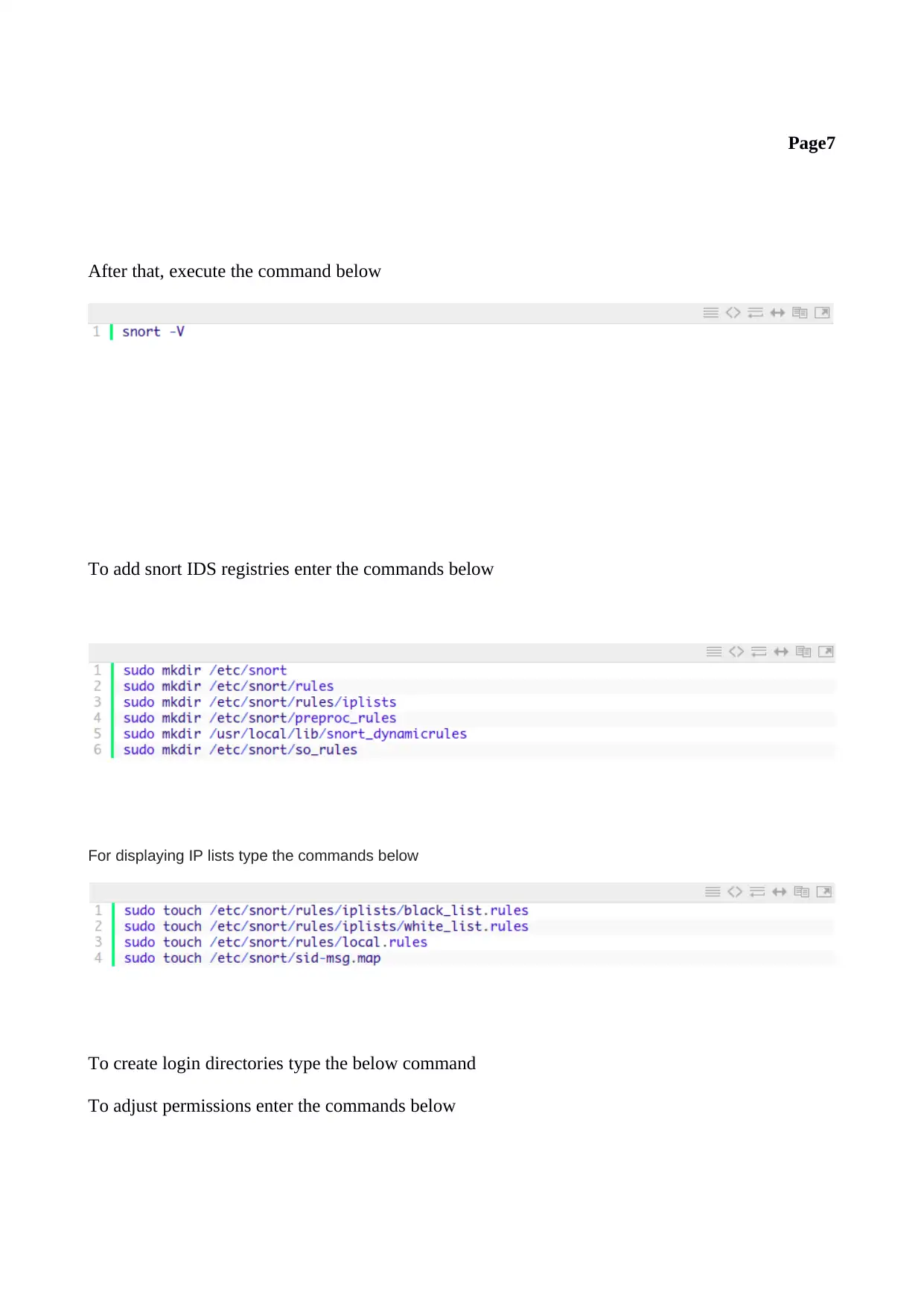
After that, execute the command below
To add snort IDS registries enter the commands below
For displaying IP lists type the commands below
To create login directories type the below command
To adjust permissions enter the commands below
After that, execute the command below
To add snort IDS registries enter the commands below
For displaying IP lists type the commands below
To create login directories type the below command
To adjust permissions enter the commands below
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Page 8
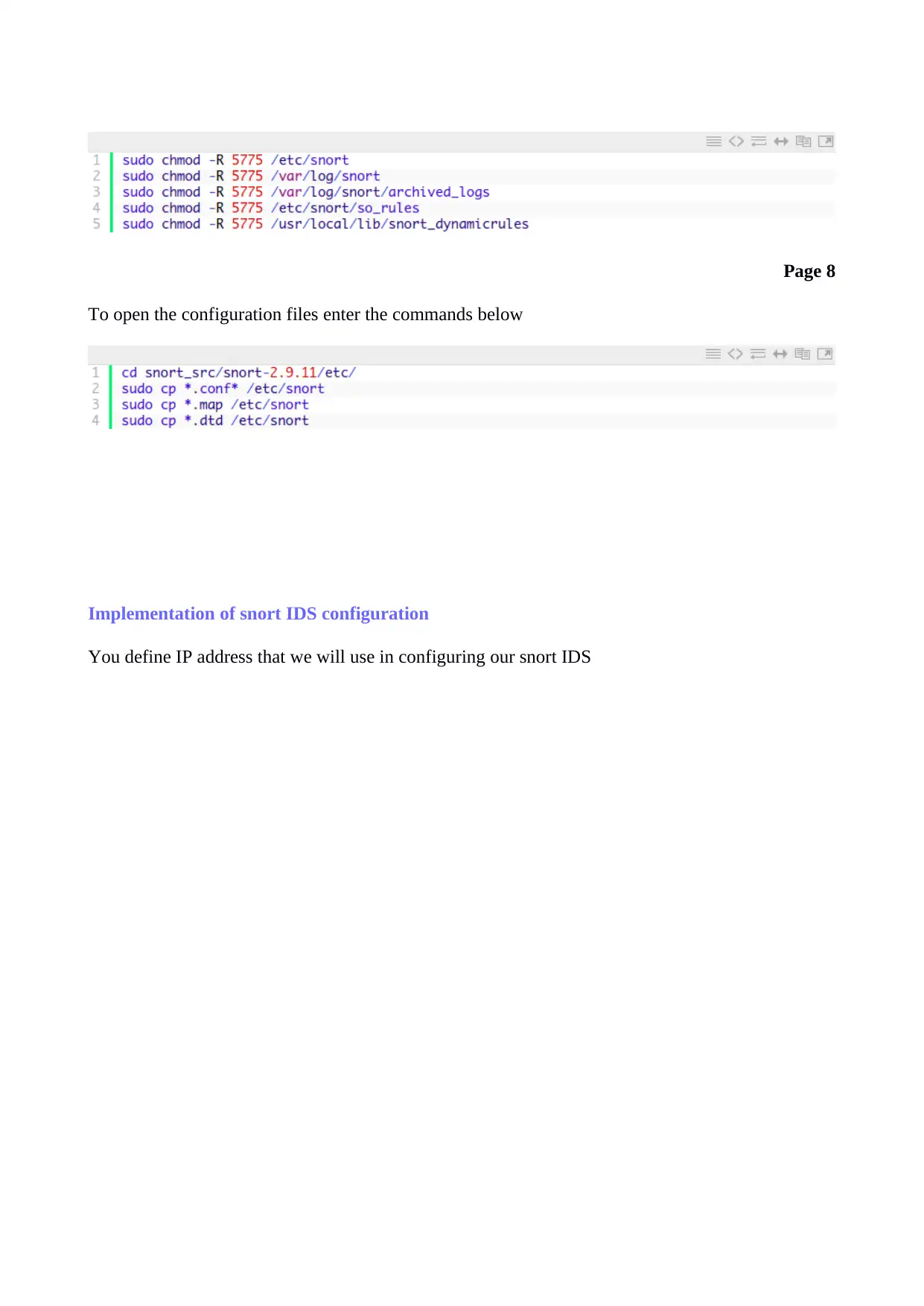
To open the configuration files enter the commands below
Implementation of snort IDS configuration
You define IP address that we will use in configuring our snort IDS
To open the configuration files enter the commands below
Implementation of snort IDS configuration
You define IP address that we will use in configuring our snort IDS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Page 9
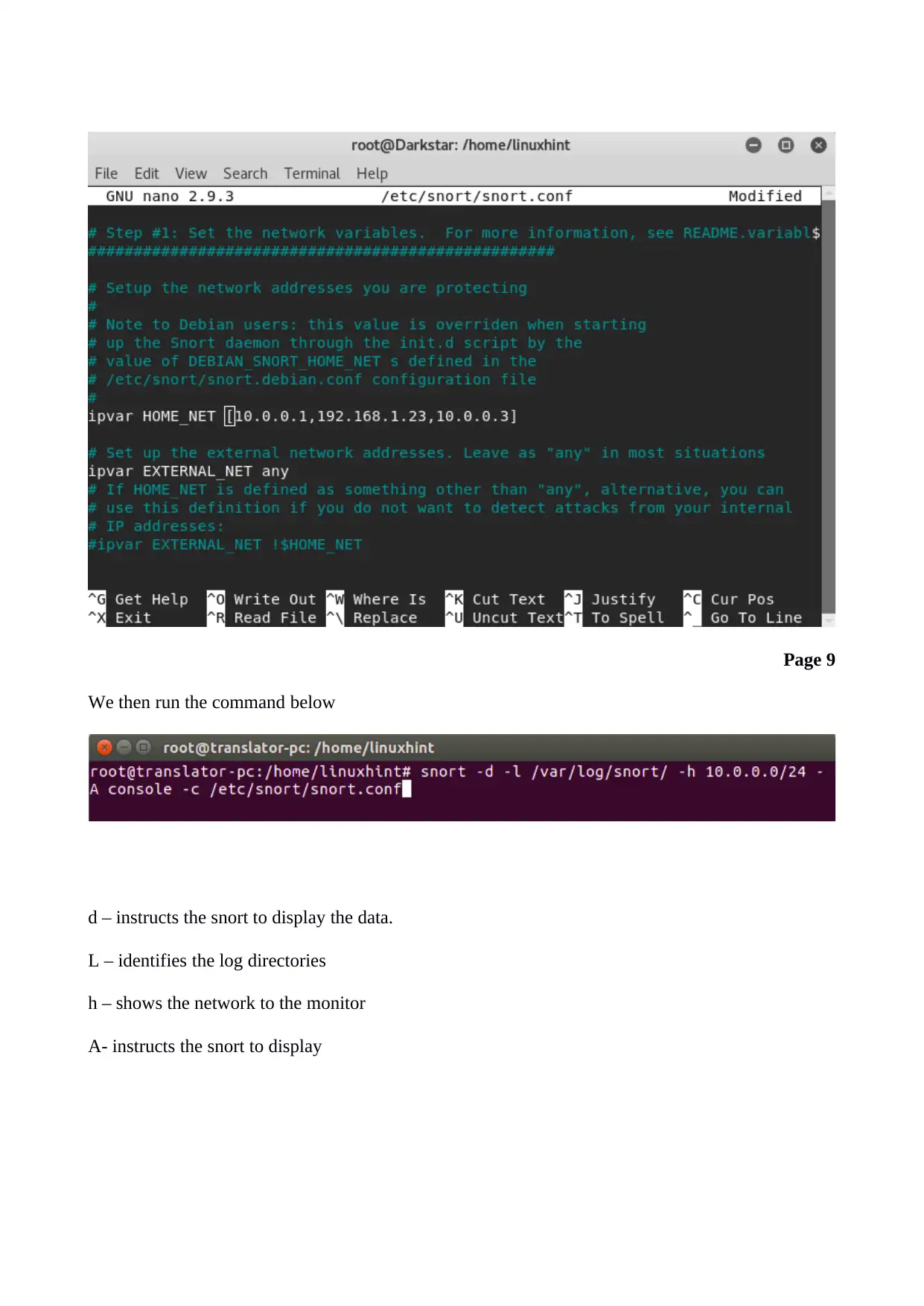
We then run the command below
d – instructs the snort to display the data.
L – identifies the log directories
h – shows the network to the monitor
A- instructs the snort to display
We then run the command below
d – instructs the snort to display the data.
L – identifies the log directories
h – shows the network to the monitor
A- instructs the snort to display
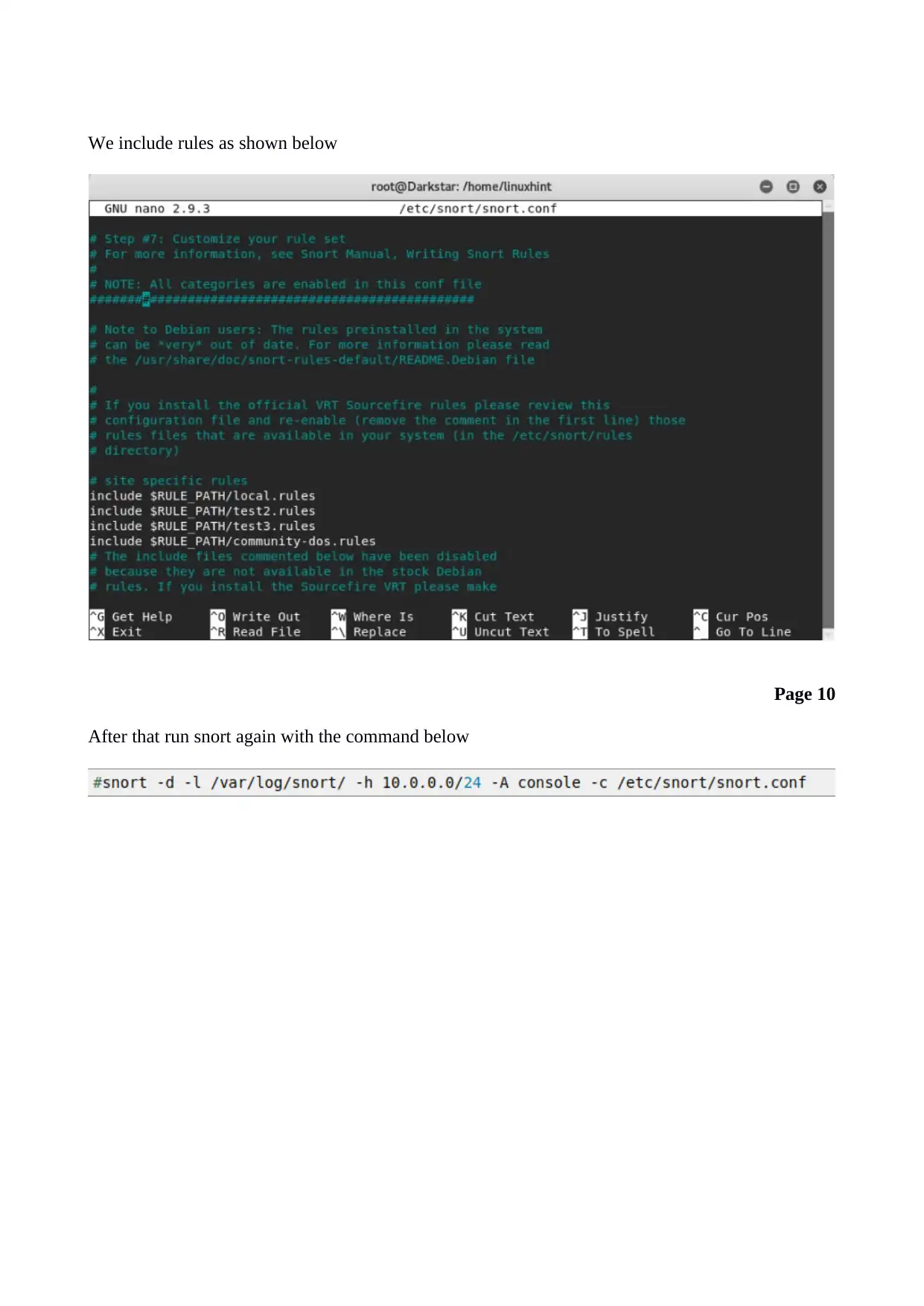
We include rules as shown below
Page 10
After that run snort again with the command below
Page 10
After that run snort again with the command below
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


