Information Security Assignment: Cryptography and Threats Analysis
VerifiedAdded on 2020/02/24
|4
|1500
|90
Homework Assignment
AI Summary
This assignment delves into various facets of information security, beginning with the core objectives of confidentiality, integrity, and availability, illustrated with examples from ATM systems. It then examines the Mirai malware, its operational mechanisms, potential prevention strategies, and suspected origins. The assignment further explores integrity protection, including checksum calculations and comparisons between SHA256, MD5, and SHA1. The Vigenère cipher is analyzed, including its encryption method, and the methods used to attack it. Finally, it discusses the RSA cryptographic algorithm, its public-key nature, and a weakness of digital signatures. The assignment provides a comprehensive overview of crucial information security concepts and practices.

Question 1:
(1) Three key objectives of information security.
The confidentiality is defined as the property, through which information is not made available or
either disclosed to any unauthorised personnel, entities and processes as it is defined on ISO27000.
Data integrity is concerned with the maintaining and assuring that the accuracy and completeness of
the data is maintained over the whole lifecycle of the data (Boritz, 2011). The data integrity is also
concerned with the availability of the data to unauthorised personnel. The integrity helps to assure
the data owners that there will be no interference with the information by other parties. The
availability means that when the correct parties need data, it will be availed with ease. Security
controls are the key measures which helps to make that the data is only availed to the required
personnel (Loukas and Oke, 2010). The availability offers assurance to the data owners that they will
access the data when they need it.
(2) Examples of confidentiality, integrity and availability
One example of confidentiality in ATM system is through encryption of data, which ensures that the
right personnel and owners of the cards who know the keys of the cards can access the information
stored. Hashing the data is a key example of providing the integrity of data in the ATM system. This
helps to provide the data in the original form without alteration. The backup methods of accessing
the data is a key example of data availability which is done in the ATM system. The owners can
access their account at their branches when the ATM system is not functioning.
Question 2
(1) Mirai malware
Mirai malware is able to function by changing the IP address of the internet service provider. For
the case on the attack, Mirai was able to engage on the change of Domain Name System (DNS)
servers. This makes the servers non-functional and therefore hinder access of the information. The
hackers through this malware are able to prevent the different users from accessing information on
the internet servers. This malware is able to affect the online devices alone. Devices with default
logins are the most vulnerable to the Mirai attack. One of the best strategy to prevent from Mirai
malware is through installation of well managed firewall, which h is up-to-date (Krebs, 2017).
Changing the default usernames and password will make it hard for Mirai to make changes on the
systems. Lastly, application of good network security practices will enhance the defence
mechanism.
(2) Hackers
The hackers using Mirai malware are still unclear. But through the analysis of the coding, which is
using the English language, it was found that it had strings in Russian (Krebs, 2017). This makes it
clear that Russian hackers were involved in the case. Moreover, Anna-senpai, not known whether
its real name, was able to release the malware to public. Moreover, it is believed that Paras Jha was
the main creator of Mirai.
(1) Three key objectives of information security.
The confidentiality is defined as the property, through which information is not made available or
either disclosed to any unauthorised personnel, entities and processes as it is defined on ISO27000.
Data integrity is concerned with the maintaining and assuring that the accuracy and completeness of
the data is maintained over the whole lifecycle of the data (Boritz, 2011). The data integrity is also
concerned with the availability of the data to unauthorised personnel. The integrity helps to assure
the data owners that there will be no interference with the information by other parties. The
availability means that when the correct parties need data, it will be availed with ease. Security
controls are the key measures which helps to make that the data is only availed to the required
personnel (Loukas and Oke, 2010). The availability offers assurance to the data owners that they will
access the data when they need it.
(2) Examples of confidentiality, integrity and availability
One example of confidentiality in ATM system is through encryption of data, which ensures that the
right personnel and owners of the cards who know the keys of the cards can access the information
stored. Hashing the data is a key example of providing the integrity of data in the ATM system. This
helps to provide the data in the original form without alteration. The backup methods of accessing
the data is a key example of data availability which is done in the ATM system. The owners can
access their account at their branches when the ATM system is not functioning.
Question 2
(1) Mirai malware
Mirai malware is able to function by changing the IP address of the internet service provider. For
the case on the attack, Mirai was able to engage on the change of Domain Name System (DNS)
servers. This makes the servers non-functional and therefore hinder access of the information. The
hackers through this malware are able to prevent the different users from accessing information on
the internet servers. This malware is able to affect the online devices alone. Devices with default
logins are the most vulnerable to the Mirai attack. One of the best strategy to prevent from Mirai
malware is through installation of well managed firewall, which h is up-to-date (Krebs, 2017).
Changing the default usernames and password will make it hard for Mirai to make changes on the
systems. Lastly, application of good network security practices will enhance the defence
mechanism.
(2) Hackers
The hackers using Mirai malware are still unclear. But through the analysis of the coding, which is
using the English language, it was found that it had strings in Russian (Krebs, 2017). This makes it
clear that Russian hackers were involved in the case. Moreover, Anna-senpai, not known whether
its real name, was able to release the malware to public. Moreover, it is believed that Paras Jha was
the main creator of Mirai.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

(3) DDoS attack
Distributed denial of service attacks, (DDoS), is a security threat which involved the change of
channel for the right user of some internet services to be unable to access the data through the change
of the servers and making them non-functional. The attackers using Mirai, were able to release the
malware, to all clients who were using the Dyn provider. The malware was able to offload the traffic
on the network provider and clogging the Dyn servers with other requests with different IP addresses.
This meant sure that the clients of Dyn were unable to access the internet services since the login
details were changed by the malware. The malware was able to take the advantage of the Internet of
thing devices (IoT) to execute the changes.
Question 3
Integrity protection is used to guard against improper information modification or destruction,
including ensuring information nonrepudiation and authenticity.
(1) Calculate message-digest fingerprints (checksum) for the provided files shattered-1&2.pdf:
MD5 SHA1 SHA256
shattered-1.pdf
shattered-2.pdf
(2) SHA256 vs MD5 and SHA1;
The output size, which is created by SHA256, is more than what MD5 and SHA1 are able to create,
that is the 256 bits compared to 160 bits for SHA1. Moreover, SHA1 and MD5 are more prone to
attacks unlike SHA256.
(3) Google Company announced that they achieved successful SHA-1
Based on the result, the checksum is much close and therefore able to create the collision. This
means that unintended result will be achieved and therefore lead to unsecure results due to the
collision.
Question 4
(1) Vigenère cipher
Vigenère cipher is a key method of encrypting alphabetic text through the use of interwoven Ceasar
ciphers, which is based on letters of a keyword (Bruen & Forcinito, 2011). The main difference
between Caesar and Vigenère cipher is that Caesar is a monoalphabetic while Vigenère cipher is a
polyalphabetic.
(2) By
Plaintext meet me after the toga party
Key After
ciphertext glzkx
(3) Attack Vigenère cipher
Brute Force attack Babbage attack or Kasiskis attack is a key method which can be used to attack
Vigenère cipher. Through the Brute-force attack, the key word is known and then the output for the
rest is researched (Martin, 2012). The attack is able to decrypt the Caesar Cipher through sheer
effort, which can be done through the computer. A cipher with more secure ciphers is needed to
Distributed denial of service attacks, (DDoS), is a security threat which involved the change of
channel for the right user of some internet services to be unable to access the data through the change
of the servers and making them non-functional. The attackers using Mirai, were able to release the
malware, to all clients who were using the Dyn provider. The malware was able to offload the traffic
on the network provider and clogging the Dyn servers with other requests with different IP addresses.
This meant sure that the clients of Dyn were unable to access the internet services since the login
details were changed by the malware. The malware was able to take the advantage of the Internet of
thing devices (IoT) to execute the changes.
Question 3
Integrity protection is used to guard against improper information modification or destruction,
including ensuring information nonrepudiation and authenticity.
(1) Calculate message-digest fingerprints (checksum) for the provided files shattered-1&2.pdf:
MD5 SHA1 SHA256
shattered-1.pdf
shattered-2.pdf
(2) SHA256 vs MD5 and SHA1;
The output size, which is created by SHA256, is more than what MD5 and SHA1 are able to create,
that is the 256 bits compared to 160 bits for SHA1. Moreover, SHA1 and MD5 are more prone to
attacks unlike SHA256.
(3) Google Company announced that they achieved successful SHA-1
Based on the result, the checksum is much close and therefore able to create the collision. This
means that unintended result will be achieved and therefore lead to unsecure results due to the
collision.
Question 4
(1) Vigenère cipher
Vigenère cipher is a key method of encrypting alphabetic text through the use of interwoven Ceasar
ciphers, which is based on letters of a keyword (Bruen & Forcinito, 2011). The main difference
between Caesar and Vigenère cipher is that Caesar is a monoalphabetic while Vigenère cipher is a
polyalphabetic.
(2) By
Plaintext meet me after the toga party
Key After
ciphertext glzkx
(3) Attack Vigenère cipher
Brute Force attack Babbage attack or Kasiskis attack is a key method which can be used to attack
Vigenère cipher. Through the Brute-force attack, the key word is known and then the output for the
rest is researched (Martin, 2012). The attack is able to decrypt the Caesar Cipher through sheer
effort, which can be done through the computer. A cipher with more secure ciphers is needed to

make the system more secure against attacks. This will make it hard for the attacks to identify all
the cipher words and break the Vigenère cipher.
Question 5:
(1) category of cryptographic algorithms RSA
RSA belong to the public-key cryptography algorithms, which is also known as the asymmetric
cryptography. This system uses the mathematical link keys, where one is private and the other is
public. The public key is shared to public while the private one is kept as a secret.
(2) RSA cryptography
In order to achieve the cryptography, the RSA uses the factoring of integers that are products of two
large prime numbers. The multiplication of the numbers is easy but determination of the prime
numbers is considered infeasible (Rouse, 2014). The two prime numbers p and q are generated
using Rabin-Miller primary test algorithm. Then a modulus n is calculated through the
multiplication of p and q. the public and private keys link up between themselves to form the large
prime number. This forms the public key. The private number is formed through the modulus n and
private exponential d, which is calculated through Extended Euclidean algorithm.
(3) main weakness of digital signatures
One of the key weakness of the digital signatures is the lack of secrecy, which means other methods
must be provided to cater for the secrecy of the data. This weakness of compensated through
measures such as encryption and decryption measures which are put in place.
References
KREBS, B. (January 2017). "Who is Anna-Senpai, the Mirai Worm Author?". Krebs on Security.
BORITZ, J. E. (August 2011) "IS Practitioners' Views on Core Concepts of Information Integrity".
International Journal of Accounting Information Systems. Elsevier. 6(4):260–279.
doi:10.1016/j.accinf.2005.07.001.
LOUKAS, G.; OKE, G. (September 2010). "Protection Against Denial of Service Attacks: A
Survey" (PDF). Comput. J. 53 (7): 1020–1037. doi:10.1093/comjnl/bxp078.
https://www.asisonline.org/About-ASIS/Who-We-Are/Whats-New/Pages/Mirai-Attack.aspx
BRUEN, A. A. & FORCINITO, M. A. (2011). Cryptography, Information Theory, and Error-
Correction: A Handbook for the 21st Century. John Wiley & Sons. p. 21. ISBN 978-1-118-03138-4.
MARTIN, K. M. (2012). Everyday Cryptography. Oxford University Press. p. 142. ISBN 978-0-19-
162588-6.
ROUSE, M. (2014). RSA algorithm (Rivest-Shamir-Adleman).
http://searchsecurity.techtarget.com/definition/RSA
http://www.dwheeler.com/secure-programs
Marking Criteria
the cipher words and break the Vigenère cipher.
Question 5:
(1) category of cryptographic algorithms RSA
RSA belong to the public-key cryptography algorithms, which is also known as the asymmetric
cryptography. This system uses the mathematical link keys, where one is private and the other is
public. The public key is shared to public while the private one is kept as a secret.
(2) RSA cryptography
In order to achieve the cryptography, the RSA uses the factoring of integers that are products of two
large prime numbers. The multiplication of the numbers is easy but determination of the prime
numbers is considered infeasible (Rouse, 2014). The two prime numbers p and q are generated
using Rabin-Miller primary test algorithm. Then a modulus n is calculated through the
multiplication of p and q. the public and private keys link up between themselves to form the large
prime number. This forms the public key. The private number is formed through the modulus n and
private exponential d, which is calculated through Extended Euclidean algorithm.
(3) main weakness of digital signatures
One of the key weakness of the digital signatures is the lack of secrecy, which means other methods
must be provided to cater for the secrecy of the data. This weakness of compensated through
measures such as encryption and decryption measures which are put in place.
References
KREBS, B. (January 2017). "Who is Anna-Senpai, the Mirai Worm Author?". Krebs on Security.
BORITZ, J. E. (August 2011) "IS Practitioners' Views on Core Concepts of Information Integrity".
International Journal of Accounting Information Systems. Elsevier. 6(4):260–279.
doi:10.1016/j.accinf.2005.07.001.
LOUKAS, G.; OKE, G. (September 2010). "Protection Against Denial of Service Attacks: A
Survey" (PDF). Comput. J. 53 (7): 1020–1037. doi:10.1093/comjnl/bxp078.
https://www.asisonline.org/About-ASIS/Who-We-Are/Whats-New/Pages/Mirai-Attack.aspx
BRUEN, A. A. & FORCINITO, M. A. (2011). Cryptography, Information Theory, and Error-
Correction: A Handbook for the 21st Century. John Wiley & Sons. p. 21. ISBN 978-1-118-03138-4.
MARTIN, K. M. (2012). Everyday Cryptography. Oxford University Press. p. 142. ISBN 978-0-19-
162588-6.
ROUSE, M. (2014). RSA algorithm (Rivest-Shamir-Adleman).
http://searchsecurity.techtarget.com/definition/RSA
http://www.dwheeler.com/secure-programs
Marking Criteria
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
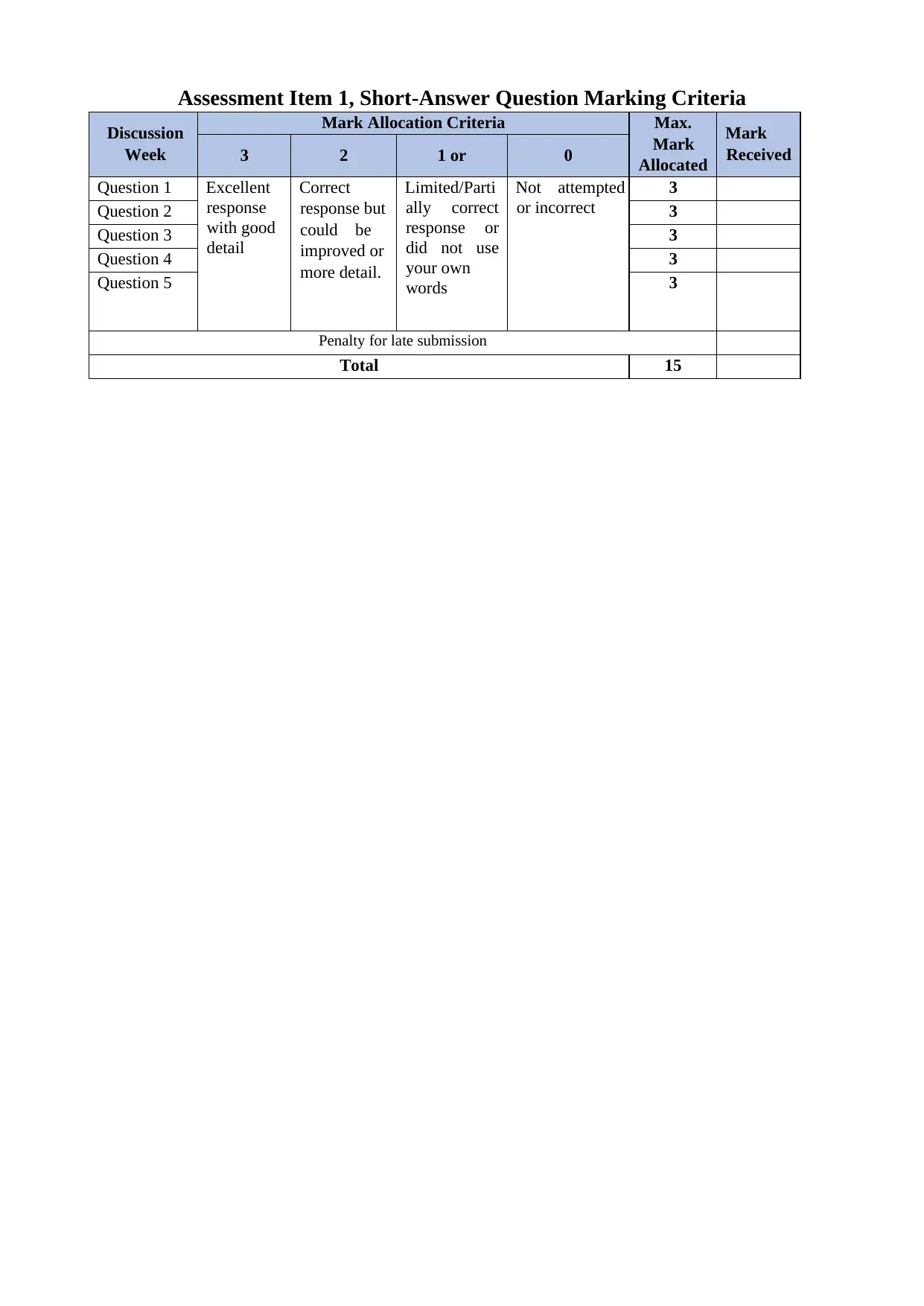
Assessment Item 1, Short-Answer Question Marking Criteria
Discussion
Week
Mark Allocation Criteria Max.
Mark
Allocated
Mark
Received3 2 1 or 0
Question 1 Excellent
response
with good
detail
Correct
response but
could be
improved or
more detail.
Limited/Parti
ally correct
response or
did not use
your own
words
Not attempted
or incorrect
3
Question 2 3
Question 3 3
Question 4 3
Question 5 3
Penalty for late submission
Total 15
Discussion
Week
Mark Allocation Criteria Max.
Mark
Allocated
Mark
Received3 2 1 or 0
Question 1 Excellent
response
with good
detail
Correct
response but
could be
improved or
more detail.
Limited/Parti
ally correct
response or
did not use
your own
words
Not attempted
or incorrect
3
Question 2 3
Question 3 3
Question 4 3
Question 5 3
Penalty for late submission
Total 15
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





