Comprehensive Network Design and Security Report for B2B Solutions
VerifiedAdded on 2020/04/07
|10
|1808
|272
Report
AI Summary
This report presents a comprehensive network design and security plan for a B2B solutions company. The project scope includes the establishment of a wide area network across six sites, focusing on network security, data confidentiality, and web-based filtering. The report details the hardware and software requirements, including routers, switches, firewalls, computers, and servers, specifying manufacturers and models. It also addresses potential security threats, such as privilege escalation, viruses, worms, Trojan horses, spyware, spamware, adwares, rootkits, and botnets, along with the assumptions made during the design process. The secure network design incorporates IP addressing schemes for each department and justifies the design based on the CIAA principles: Confidentiality, Integrity, Availability, and Authentication, emphasizing the use of cryptographic algorithms for data protection and secure communication. The conclusion highlights the benefits of the network design in terms of service delivery, resource sharing, and data security, recommending the implementation of network systems for organizations to enhance their services and enforce security.

NETWORK DESIGNING AND SECURITY.
Submitted to
[lecture name]
The B2B solution Secure Network Design
[Date]
By
[Student name]
Submitted to
[lecture name]
The B2B solution Secure Network Design
[Date]
By
[Student name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Project scope....................................................................................................................................3
Project hardware and software requirements...................................................................................3
Possible security threats to B2B network........................................................................................5
Secure Network design....................................................................................................................7
Justification of secure network design based on CIAA...................................................................8
i. Confidentiality...................................................................................................................8
ii. Integrity.............................................................................................................................8
iii. Availability....................................................................................................................8
iv. Authentications..............................................................................................................8
Conclusion.......................................................................................................................................9
References......................................................................................................................................10
Project scope....................................................................................................................................3
Project hardware and software requirements...................................................................................3
Possible security threats to B2B network........................................................................................5
Secure Network design....................................................................................................................7
Justification of secure network design based on CIAA...................................................................8
i. Confidentiality...................................................................................................................8
ii. Integrity.............................................................................................................................8
iii. Availability....................................................................................................................8
iv. Authentications..............................................................................................................8
Conclusion.......................................................................................................................................9
References......................................................................................................................................10
Project scope
This report is about a network design and security at the B2B solution company which is
a small organization which due to its growth and expansion and it has increased departments
which will be located to the six sites newly established.
Therefore to ensure the communication and sharing of the resources in those six sites a wide
area network is installed and it will ensure various aspects are achieved which includes:
i. Enforcing the network security in the proposed network.
ii. To ensure confidentiality of data across the networks and
iii. Setting up the web based filters.
iv. Setting the access-lists to the various departments
However the designed network has a total of six routers which will form subnets 1 to subnet
6 with respective departments names and the total number of computers will be 500 for all
network sites.
In order to come up with the network a well ladled B2B solutions network will be designed
below.
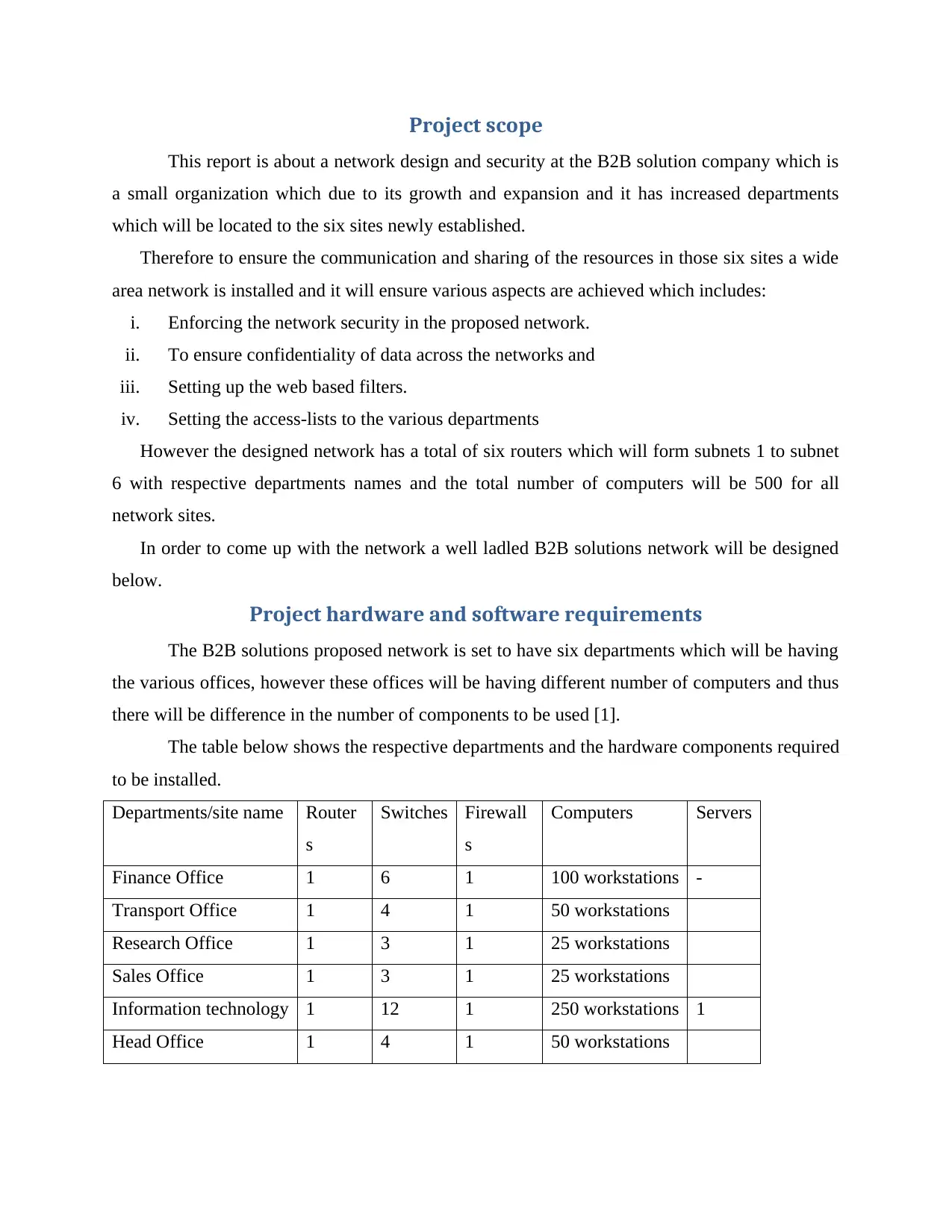
Project hardware and software requirements
The B2B solutions proposed network is set to have six departments which will be having
the various offices, however these offices will be having different number of computers and thus
there will be difference in the number of components to be used [1].
The table below shows the respective departments and the hardware components required
to be installed.
Departments/site name Router
s
Switches Firewall
s
Computers Servers
Finance Office 1 6 1 100 workstations -
Transport Office 1 4 1 50 workstations
Research Office 1 3 1 25 workstations
Sales Office 1 3 1 25 workstations
Information technology 1 12 1 250 workstations 1
Head Office 1 4 1 50 workstations
This report is about a network design and security at the B2B solution company which is
a small organization which due to its growth and expansion and it has increased departments
which will be located to the six sites newly established.
Therefore to ensure the communication and sharing of the resources in those six sites a wide
area network is installed and it will ensure various aspects are achieved which includes:
i. Enforcing the network security in the proposed network.
ii. To ensure confidentiality of data across the networks and
iii. Setting up the web based filters.
iv. Setting the access-lists to the various departments
However the designed network has a total of six routers which will form subnets 1 to subnet
6 with respective departments names and the total number of computers will be 500 for all
network sites.
In order to come up with the network a well ladled B2B solutions network will be designed
below.
Project hardware and software requirements
The B2B solutions proposed network is set to have six departments which will be having
the various offices, however these offices will be having different number of computers and thus
there will be difference in the number of components to be used [1].
The table below shows the respective departments and the hardware components required
to be installed.
Departments/site name Router
s
Switches Firewall
s
Computers Servers
Finance Office 1 6 1 100 workstations -
Transport Office 1 4 1 50 workstations
Research Office 1 3 1 25 workstations
Sales Office 1 3 1 25 workstations
Information technology 1 12 1 250 workstations 1
Head Office 1 4 1 50 workstations
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
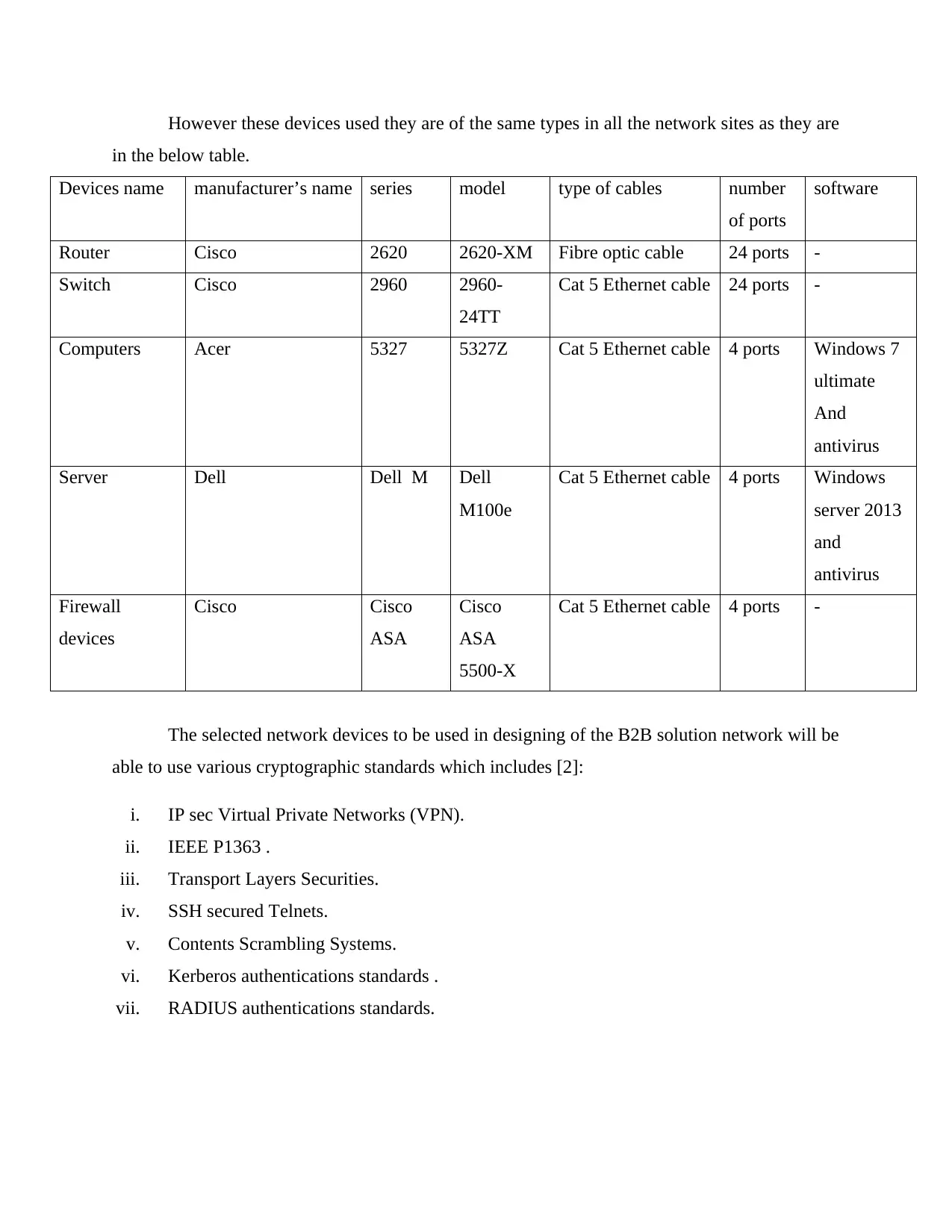
However these devices used they are of the same types in all the network sites as they are
in the below table.
Devices name manufacturer’s name series model type of cables number
of ports
software
Router Cisco 2620 2620-XM Fibre optic cable 24 ports -
Switch Cisco 2960 2960-
24TT
Cat 5 Ethernet cable 24 ports -
Computers Acer 5327 5327Z Cat 5 Ethernet cable 4 ports Windows 7
ultimate
And
antivirus
Server Dell Dell M Dell
M100e
Cat 5 Ethernet cable 4 ports Windows
server 2013
and
antivirus
Firewall
devices
Cisco Cisco
ASA
Cisco
ASA
5500-X
Cat 5 Ethernet cable 4 ports -
The selected network devices to be used in designing of the B2B solution network will be
able to use various cryptographic standards which includes [2]:
i. IP sec Virtual Private Networks (VPN).
ii. IEEE P1363 .
iii. Transport Layers Securities.
iv. SSH secured Telnets.
v. Contents Scrambling Systems.
vi. Kerberos authentications standards .
vii. RADIUS authentications standards.
in the below table.
Devices name manufacturer’s name series model type of cables number
of ports
software
Router Cisco 2620 2620-XM Fibre optic cable 24 ports -
Switch Cisco 2960 2960-
24TT
Cat 5 Ethernet cable 24 ports -
Computers Acer 5327 5327Z Cat 5 Ethernet cable 4 ports Windows 7
ultimate
And
antivirus
Server Dell Dell M Dell
M100e
Cat 5 Ethernet cable 4 ports Windows
server 2013
and
antivirus
Firewall
devices
Cisco Cisco
ASA
Cisco
ASA
5500-X
Cat 5 Ethernet cable 4 ports -
The selected network devices to be used in designing of the B2B solution network will be
able to use various cryptographic standards which includes [2]:
i. IP sec Virtual Private Networks (VPN).
ii. IEEE P1363 .
iii. Transport Layers Securities.
iv. SSH secured Telnets.
v. Contents Scrambling Systems.
vi. Kerberos authentications standards .
vii. RADIUS authentications standards.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Possible security threats to B2B network.
The B2B network is very resource full to the organization however there are various possible
threats that risks the performance of the proposed network which includes:
i. Privilege Escalation. This is a threat where the installed computer programs will be
used by the attackers and through them the attackers gain accessibility to the network
devices by passing the passwords.
ii. The viruses. This is software type of a program that when it gets to the computer
systems do multiply and eventually all other computers in the entire system get
infected through the network.
iii. The computer worms .This is almost like the viruses and it eventually make alteration
to the computer programs and by replication it fill the computer memory and
eventually end up crashing [3].
iv. Trojan horse. This is a malicious program that destroy the computer programs ,this is
with a mission to allow the hackers to access the computer system remotely and this
is termed as the denial of serve attacks and eventually the attackers still the
information.
v. Spywares software. This is a application that get into the computer through the
downloaded applications or through data sharing, this is a threat since it is able to
gather information about the connection of internet and that information is sent to the
attackers of the system.
vi. Spam ware. This is another threat that is transmitted to the devices through the email
address, upon opening it affects the network performance since it is able to use much
of network bandwidth.
vii. The adwares. This is a threat that is transmitted through the internet ,however it
appears like an advert but it slows down the networks bandwidth like the spam .
viii. The rootkit threats. This is a threat that get activation through the booting of the
system and this will eventually permit the malicious installation of the
programs ,accounts and it end up intercepting very sensitive information about the
organisation.
The B2B network is very resource full to the organization however there are various possible
threats that risks the performance of the proposed network which includes:
i. Privilege Escalation. This is a threat where the installed computer programs will be
used by the attackers and through them the attackers gain accessibility to the network
devices by passing the passwords.
ii. The viruses. This is software type of a program that when it gets to the computer
systems do multiply and eventually all other computers in the entire system get
infected through the network.
iii. The computer worms .This is almost like the viruses and it eventually make alteration
to the computer programs and by replication it fill the computer memory and
eventually end up crashing [3].
iv. Trojan horse. This is a malicious program that destroy the computer programs ,this is
with a mission to allow the hackers to access the computer system remotely and this
is termed as the denial of serve attacks and eventually the attackers still the
information.
v. Spywares software. This is a application that get into the computer through the
downloaded applications or through data sharing, this is a threat since it is able to
gather information about the connection of internet and that information is sent to the
attackers of the system.
vi. Spam ware. This is another threat that is transmitted to the devices through the email
address, upon opening it affects the network performance since it is able to use much
of network bandwidth.
vii. The adwares. This is a threat that is transmitted through the internet ,however it
appears like an advert but it slows down the networks bandwidth like the spam .
viii. The rootkit threats. This is a threat that get activation through the booting of the
system and this will eventually permit the malicious installation of the
programs ,accounts and it end up intercepting very sensitive information about the
organisation.

ix. Botnet computers. This is a computer in the network that had been interfered with and
it is infected with the Trojan horse and mainly allows the attackers to launch the
denial of services attacks.
During the designing of the B2B solutions network there were a number of assumptions that
were made regarding this network and security some of the assumptions made were:
i. There is possible attack to the network systems.
ii. Each network computer is installed with window 7 operating system.
iii. Each of the computers windows firewall is set on to prevent the unpermitted connections.
iv. Each computer in the network is installed with latest version of antivirus.
v. Each department network is connected to network firewall devices.
Therefore using the above assumptions the network design is done as in the figure below
indicating the connected devices and the network control devices.
it is infected with the Trojan horse and mainly allows the attackers to launch the
denial of services attacks.
During the designing of the B2B solutions network there were a number of assumptions that
were made regarding this network and security some of the assumptions made were:
i. There is possible attack to the network systems.
ii. Each network computer is installed with window 7 operating system.
iii. Each of the computers windows firewall is set on to prevent the unpermitted connections.
iv. Each computer in the network is installed with latest version of antivirus.
v. Each department network is connected to network firewall devices.
Therefore using the above assumptions the network design is done as in the figure below
indicating the connected devices and the network control devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
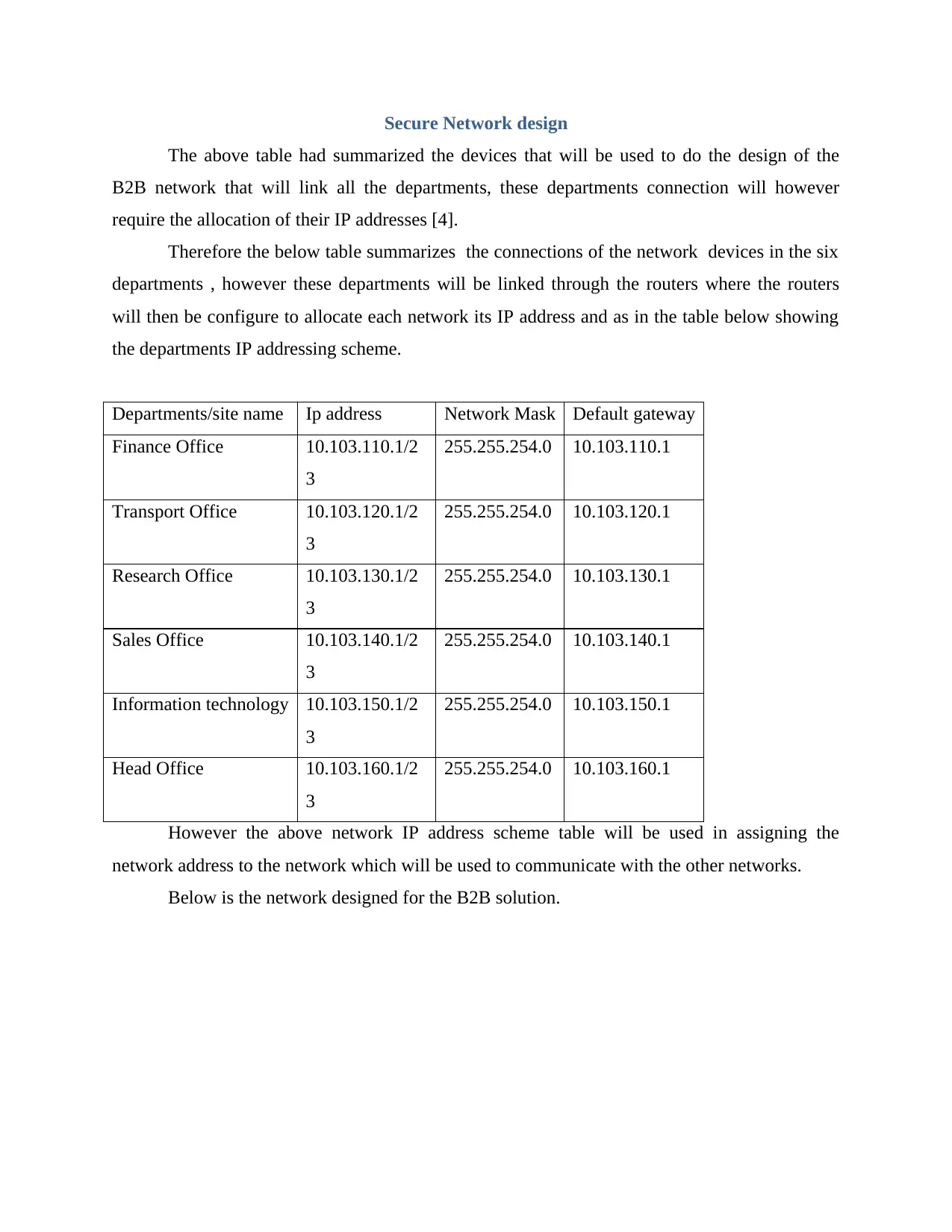
Secure Network design
The above table had summarized the devices that will be used to do the design of the
B2B network that will link all the departments, these departments connection will however
require the allocation of their IP addresses [4].
Therefore the below table summarizes the connections of the network devices in the six
departments , however these departments will be linked through the routers where the routers
will then be configure to allocate each network its IP address and as in the table below showing
the departments IP addressing scheme.
Departments/site name Ip address Network Mask Default gateway
Finance Office 10.103.110.1/2
3
255.255.254.0 10.103.110.1
Transport Office 10.103.120.1/2
3
255.255.254.0 10.103.120.1
Research Office 10.103.130.1/2
3
255.255.254.0 10.103.130.1
Sales Office 10.103.140.1/2
3
255.255.254.0 10.103.140.1
Information technology 10.103.150.1/2
3
255.255.254.0 10.103.150.1
Head Office 10.103.160.1/2
3
255.255.254.0 10.103.160.1
However the above network IP address scheme table will be used in assigning the
network address to the network which will be used to communicate with the other networks.
Below is the network designed for the B2B solution.
The above table had summarized the devices that will be used to do the design of the
B2B network that will link all the departments, these departments connection will however
require the allocation of their IP addresses [4].
Therefore the below table summarizes the connections of the network devices in the six
departments , however these departments will be linked through the routers where the routers
will then be configure to allocate each network its IP address and as in the table below showing
the departments IP addressing scheme.
Departments/site name Ip address Network Mask Default gateway
Finance Office 10.103.110.1/2
3
255.255.254.0 10.103.110.1
Transport Office 10.103.120.1/2
3
255.255.254.0 10.103.120.1
Research Office 10.103.130.1/2
3
255.255.254.0 10.103.130.1
Sales Office 10.103.140.1/2
3
255.255.254.0 10.103.140.1
Information technology 10.103.150.1/2
3
255.255.254.0 10.103.150.1
Head Office 10.103.160.1/2
3
255.255.254.0 10.103.160.1
However the above network IP address scheme table will be used in assigning the
network address to the network which will be used to communicate with the other networks.
Below is the network designed for the B2B solution.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
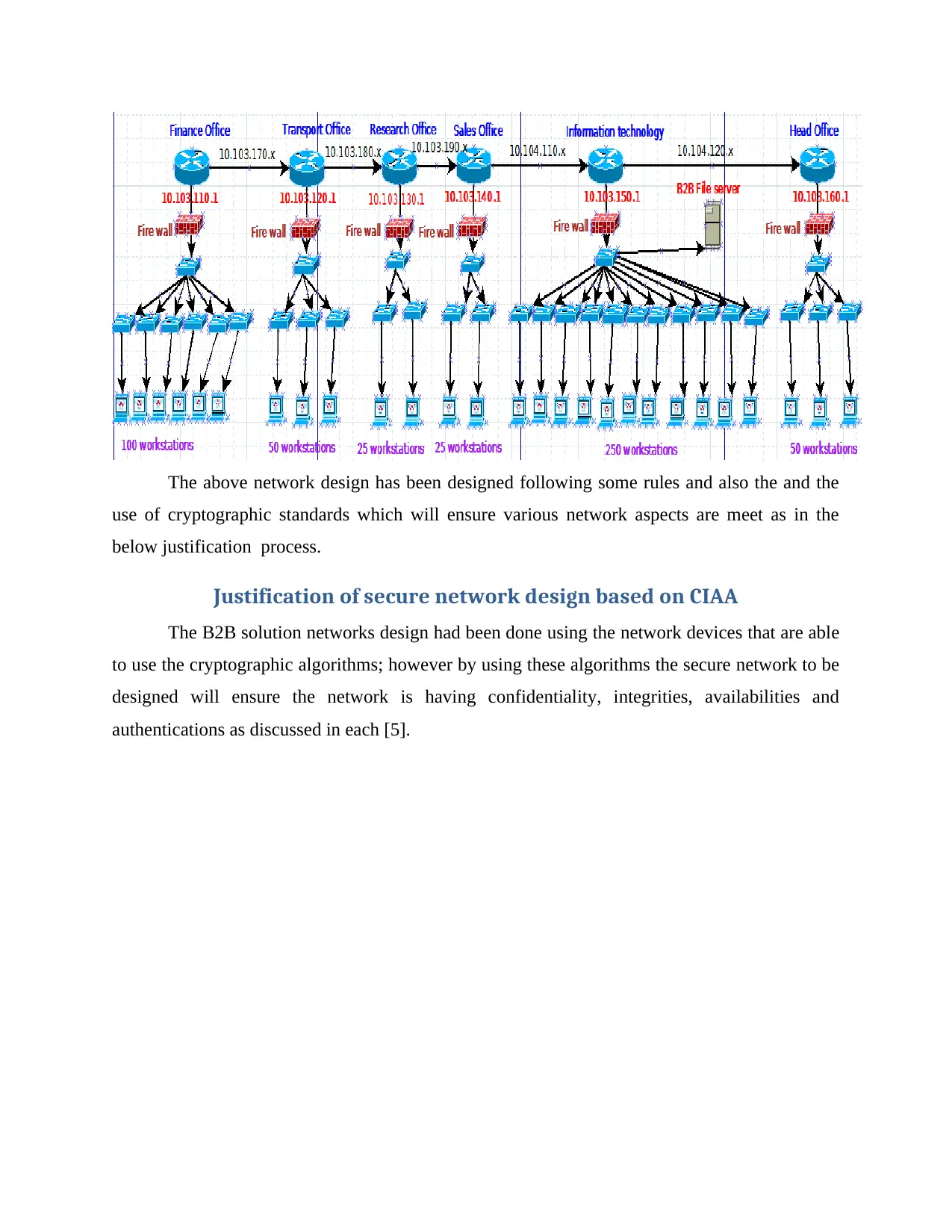
The above network design has been designed following some rules and also the and the
use of cryptographic standards which will ensure various network aspects are meet as in the
below justification process.
Justification of secure network design based on CIAA
The B2B solution networks design had been done using the network devices that are able
to use the cryptographic algorithms; however by using these algorithms the secure network to be
designed will ensure the network is having confidentiality, integrities, availabilities and
authentications as discussed in each [5].
use of cryptographic standards which will ensure various network aspects are meet as in the
below justification process.
Justification of secure network design based on CIAA
The B2B solution networks design had been done using the network devices that are able
to use the cryptographic algorithms; however by using these algorithms the secure network to be
designed will ensure the network is having confidentiality, integrities, availabilities and
authentications as discussed in each [5].

i. Confidentiality. In the B2B solution network the information is required to maintain
the privacy at all times ,however the cryptographic algorithms has been designed to
ensure that there is privacy in all network sections some of the information secured by
this algorithms includes the used password in login processes, and any other personal
information ,therefore these algorithms ensure that people with appropriate keys will
be permitted to have data access.
ii. Integrity. This is the process of securing the data changes, however the
cryptographic algorithms protect data from being viewed or change while it is being
stored or transmitted this is by provision of the checksums which are secure by the
hashes type of cryptographic algorithms [6].
iii. Availability. The network availability is essential in the B2B networks in the various
network applications ,the cryptographic algorithms ensures that the network users
cannot be able to reverse their actions in the network .This helps in identification of
the various transactions done in the network by help of the digital signatures that are
provided by the cryptographic algorithms.
iv. Authentications. The use of cryptographic algorithm the identities of the remote
server or host devices is established ,for instance using the web servers SSL
certificates one can detect whether the clients hosts are connected to the appropriate
servers in the network this is achieved by use of the cryptographic keys and this will
enable securing of the network system.
Conclusion
The B2B solution network design is a foot print for the physical network design ,this
network will be able to boost the service delivery in the company ,sharing of the
resources ,saving on time and resources in storage and access of data .
This network design will ensure that the network is secured and no intrusion in the
network ,this is by use of various measure to control the networks insecurity.
the privacy at all times ,however the cryptographic algorithms has been designed to
ensure that there is privacy in all network sections some of the information secured by
this algorithms includes the used password in login processes, and any other personal
information ,therefore these algorithms ensure that people with appropriate keys will
be permitted to have data access.
ii. Integrity. This is the process of securing the data changes, however the
cryptographic algorithms protect data from being viewed or change while it is being
stored or transmitted this is by provision of the checksums which are secure by the
hashes type of cryptographic algorithms [6].
iii. Availability. The network availability is essential in the B2B networks in the various
network applications ,the cryptographic algorithms ensures that the network users
cannot be able to reverse their actions in the network .This helps in identification of
the various transactions done in the network by help of the digital signatures that are
provided by the cryptographic algorithms.
iv. Authentications. The use of cryptographic algorithm the identities of the remote
server or host devices is established ,for instance using the web servers SSL
certificates one can detect whether the clients hosts are connected to the appropriate
servers in the network this is achieved by use of the cryptographic keys and this will
enable securing of the network system.
Conclusion
The B2B solution network design is a foot print for the physical network design ,this
network will be able to boost the service delivery in the company ,sharing of the
resources ,saving on time and resources in storage and access of data .
This network design will ensure that the network is secured and no intrusion in the
network ,this is by use of various measure to control the networks insecurity.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

However this security measure is achieved by ensuring those network devices has ability
to use the crypto graphical standards that will ensure that the network is confidential, integral,
accessible and also is authenticated [7].
Therefore for all organization it is recommended to do installation of the network system
in order to integrate all the organization services and enforce the security.
References.
[1] A.Thomas,The Practice of System and Network Administration, New York:Addison-Wesley
Professional.
[2] D.Jeff,Routing TCP/IP, London: Cisco Press.,2016.
[3].D.Kevin, Cisco IOS Cookbook, New York: O'Reilly Media,2015.
[4] E.Douglas, Internetworking with TCP/IP Principles, Protocols, and Architecture, New York:
Prentice Hall,2015.
to use the crypto graphical standards that will ensure that the network is confidential, integral,
accessible and also is authenticated [7].
Therefore for all organization it is recommended to do installation of the network system
in order to integrate all the organization services and enforce the security.
References.
[1] A.Thomas,The Practice of System and Network Administration, New York:Addison-Wesley
Professional.
[2] D.Jeff,Routing TCP/IP, London: Cisco Press.,2016.
[3].D.Kevin, Cisco IOS Cookbook, New York: O'Reilly Media,2015.
[4] E.Douglas, Internetworking with TCP/IP Principles, Protocols, and Architecture, New York:
Prentice Hall,2015.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




