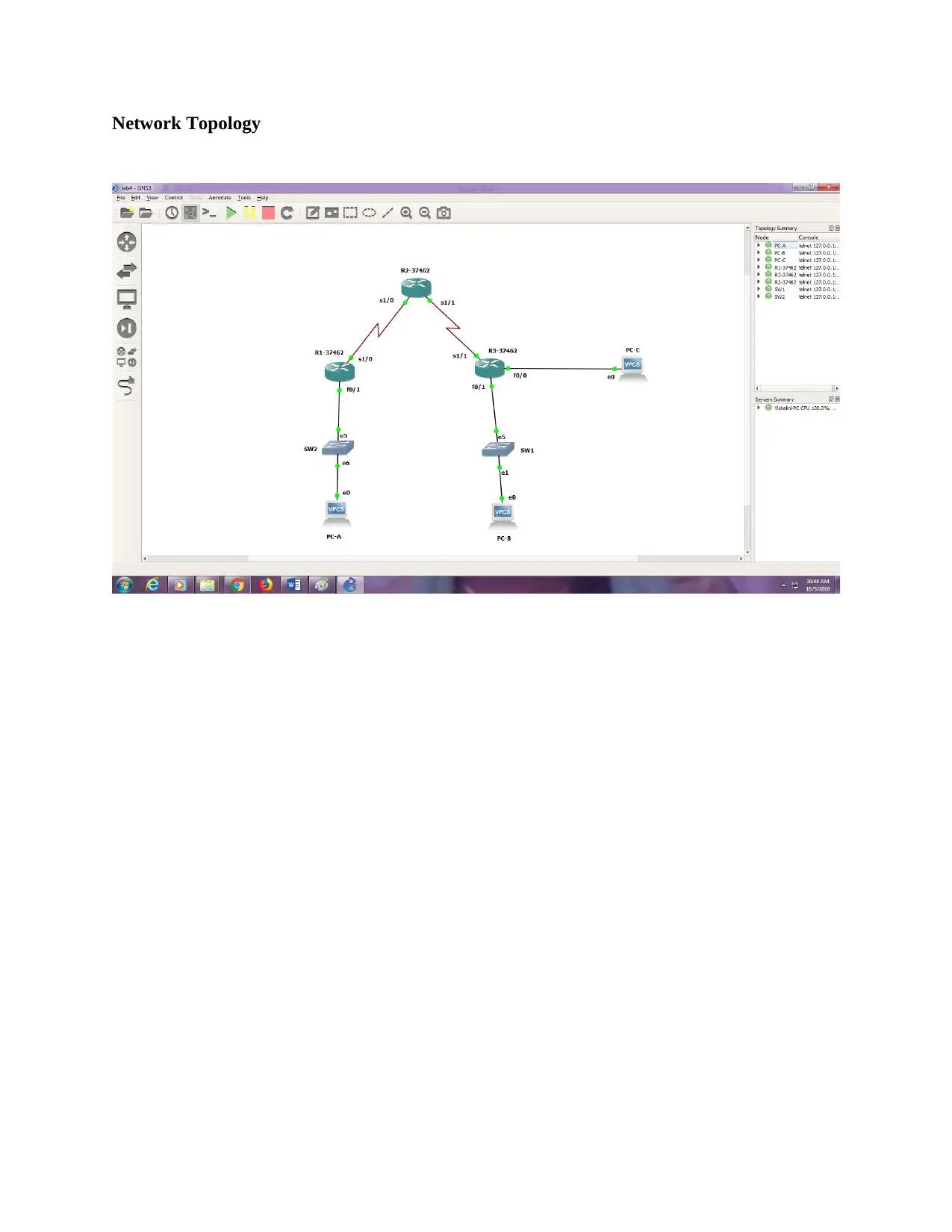
Network Topology Configuration: Firewall and Security Verification
VerifiedAdded on 2021/05/31
|21
|658
|103
Practical Assignment
AI Summary
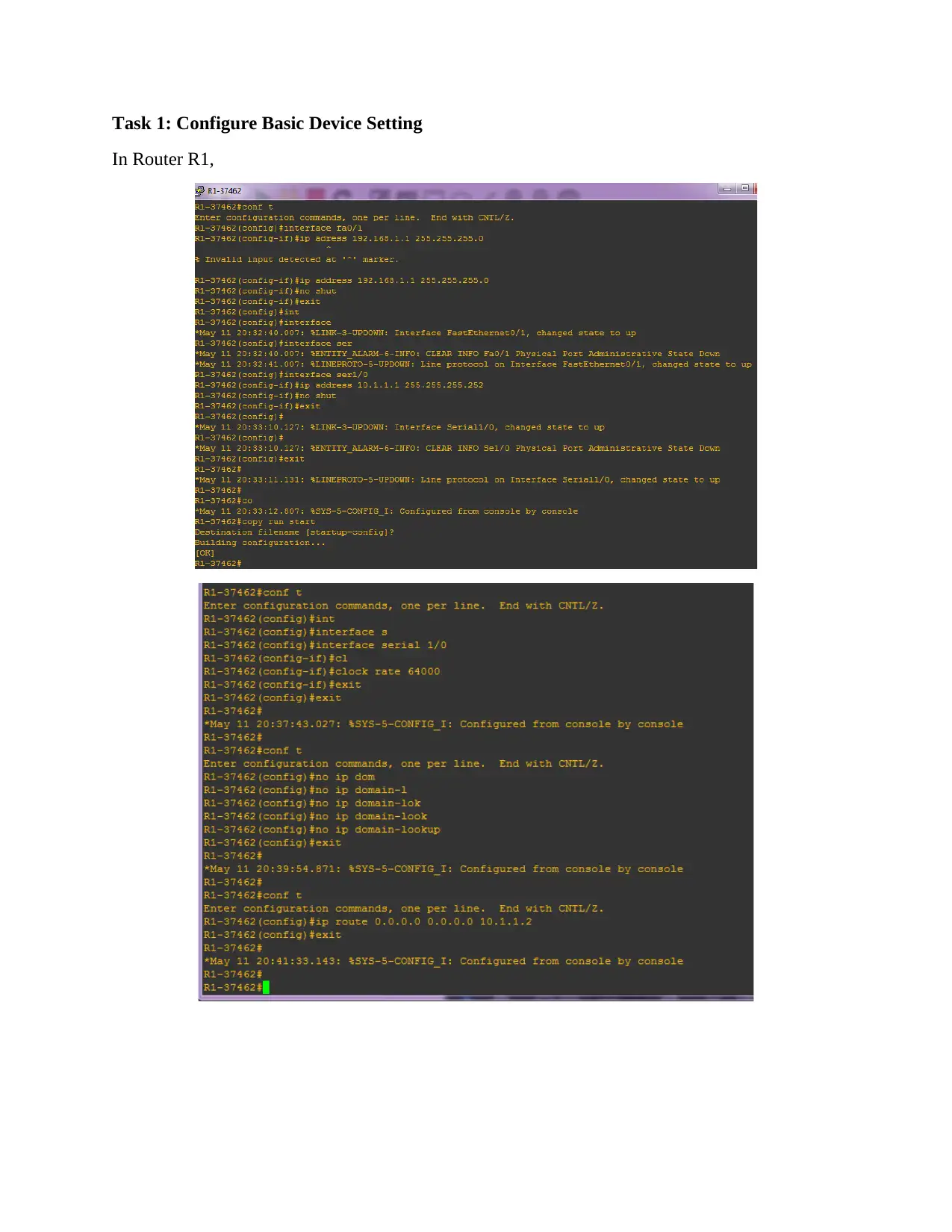
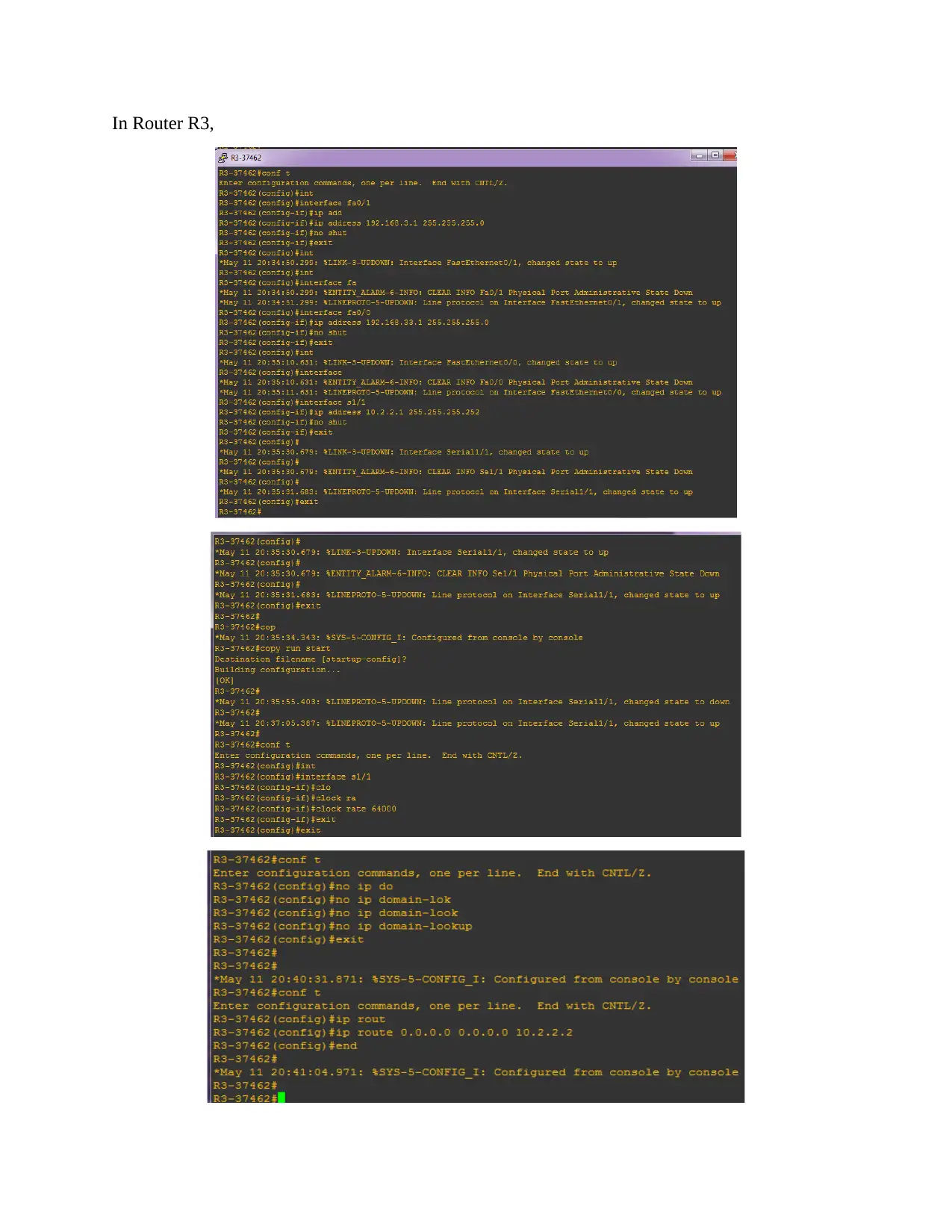
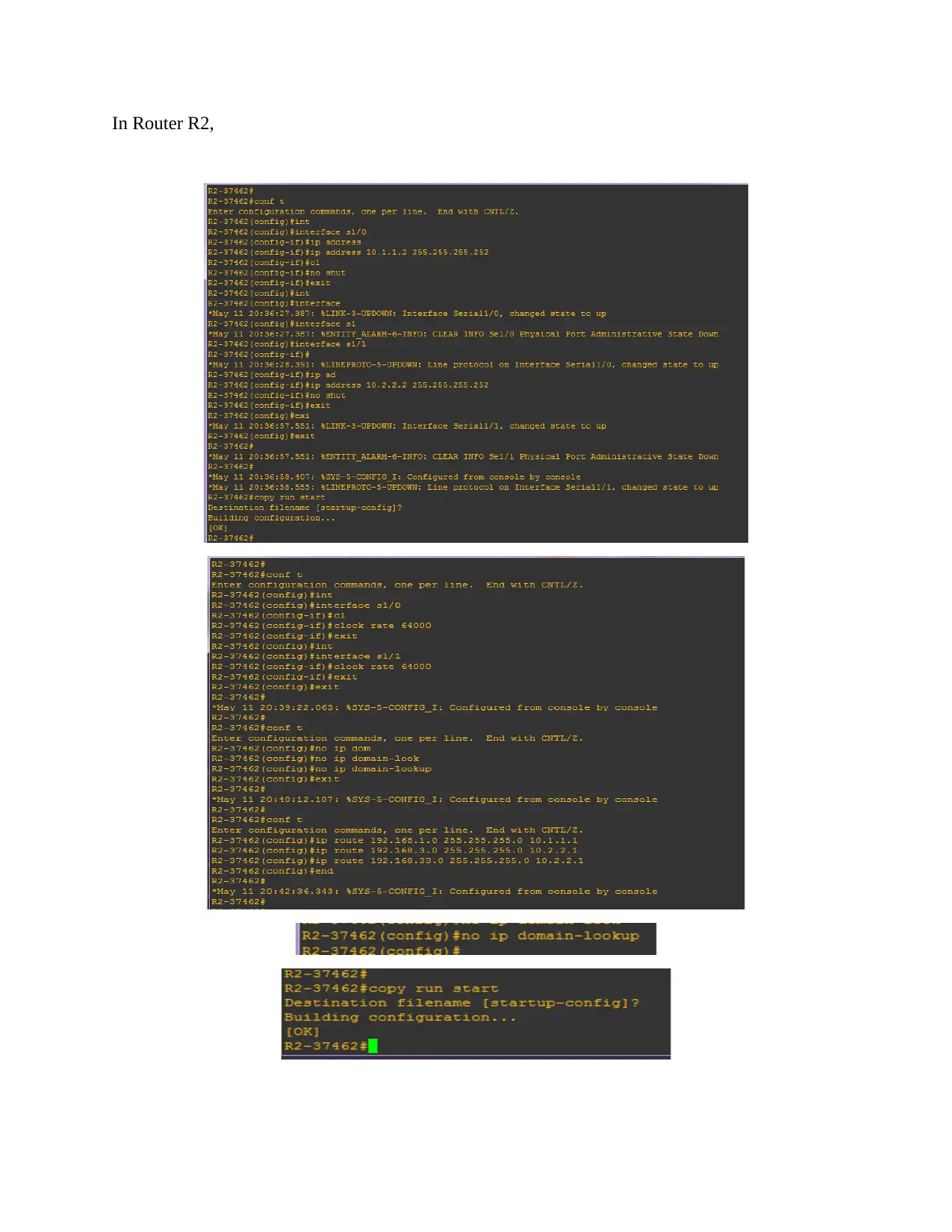
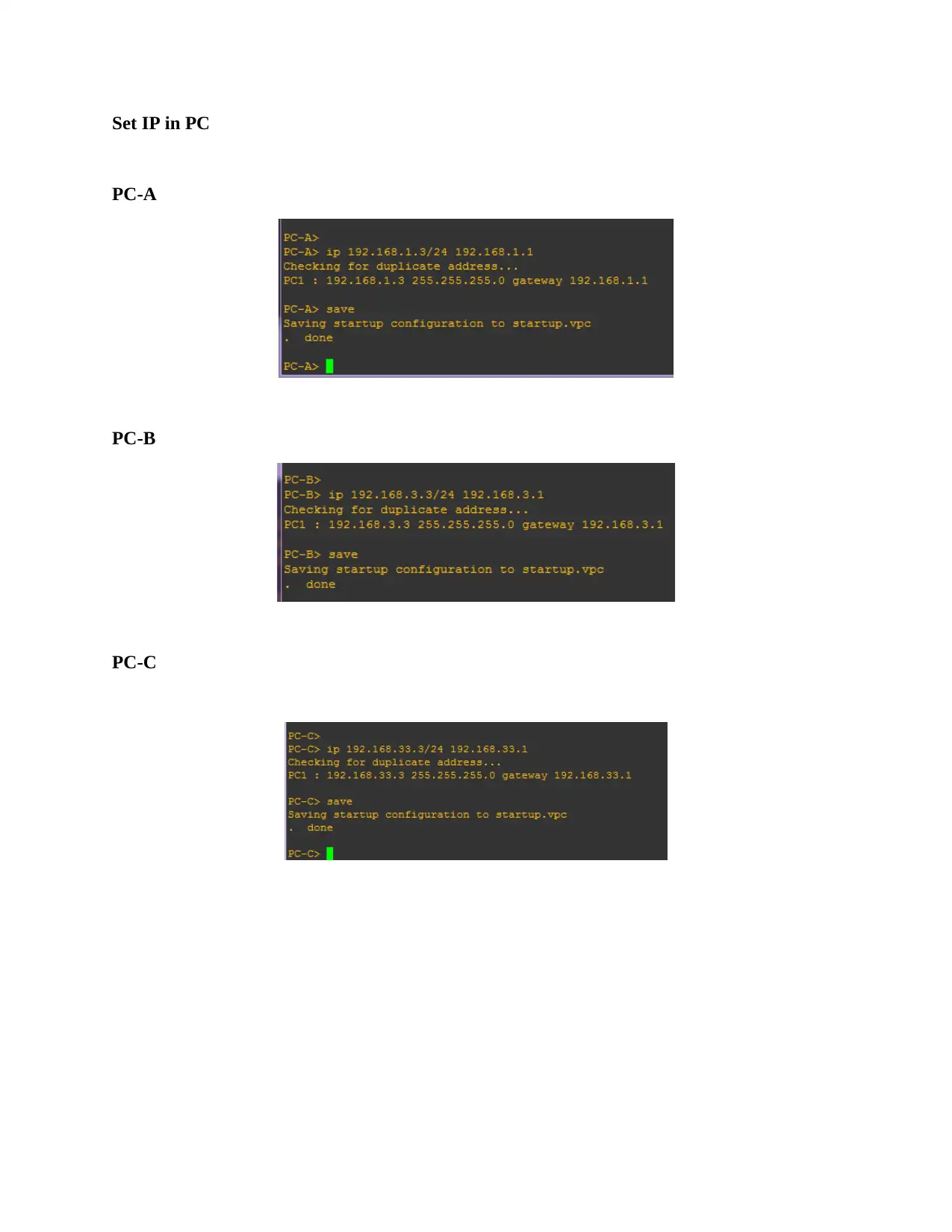
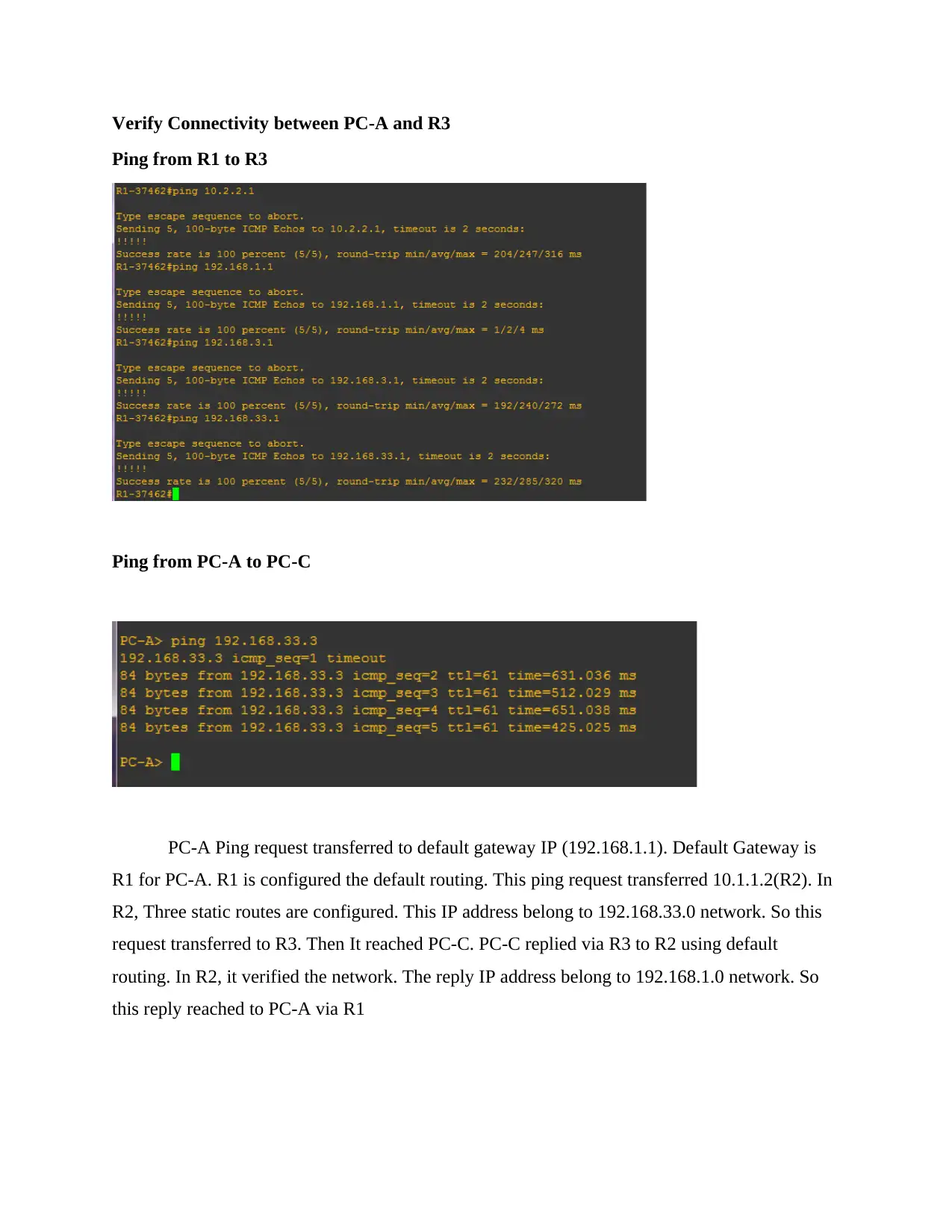
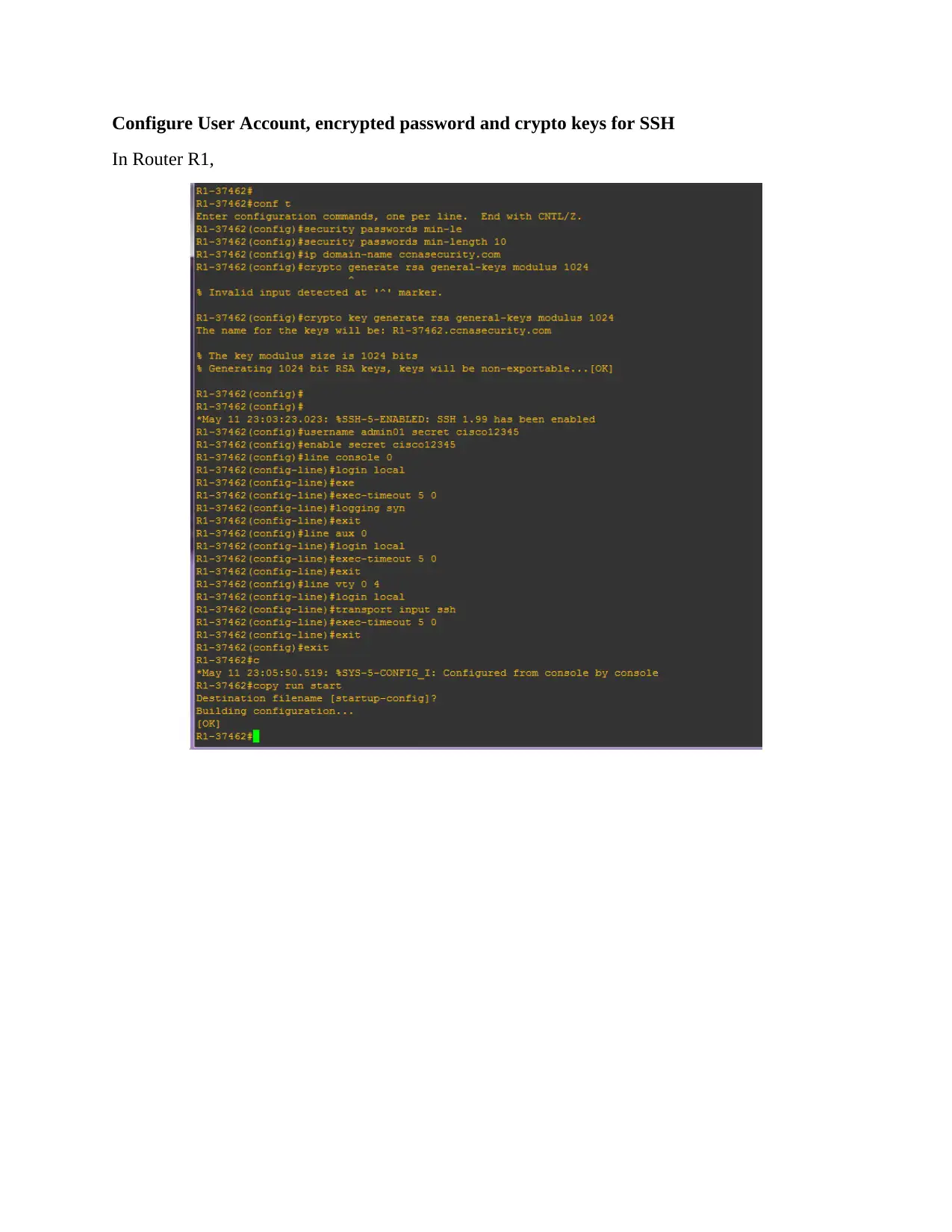
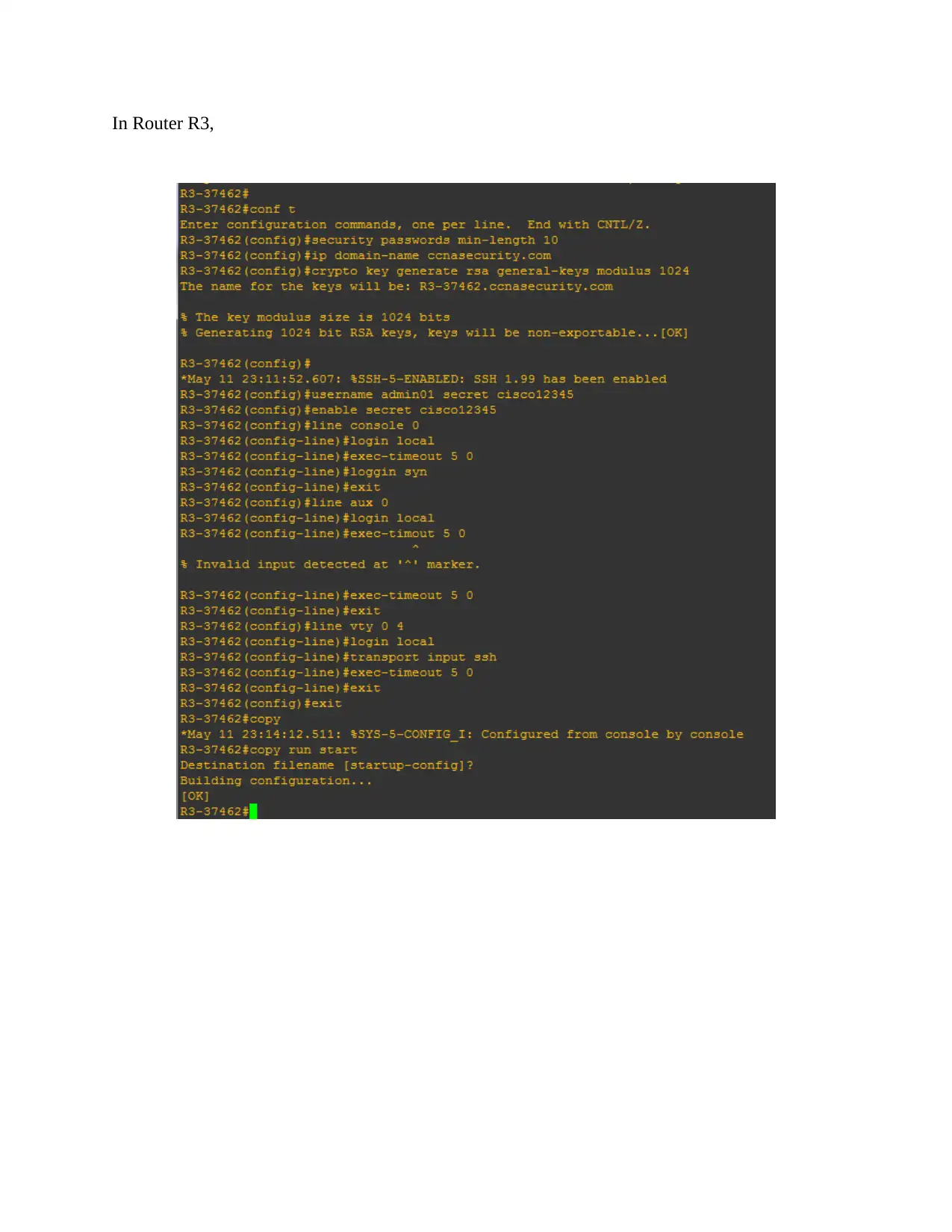
This assignment solution details the configuration of a network topology, encompassing basic device settings in routers R1, R2, and R3, along with IP address assignments for PCs PC-A, PC-B, and PC-C. It verifies network connectivity through ping tests and configures static routes. The solution further delves into setting up user accounts, encrypted passwords, and crypto keys for SSH. Part 2 focuses on configuring a zone-based policy firewall in R3, including creating security zones, policies, class maps, and zone pairs. It also covers assigning interfaces to zones and verifying the configurations. Part 3 verifies the firewall's functionality, testing traffic originating from the internet and the self-zone. The solution includes references to relevant Cisco documentation and GNS3 lab guides.
1 out of 21






![[object Object]](/_next/static/media/star-bottom.7253800d.svg)