Wireless Communications - Electrical Engineering Assignment
VerifiedAdded on 2020/02/24
|14
|1453
|183
Homework Assignment
AI Summary
This assignment solution delves into the intricacies of wireless communications, addressing key concepts such as WiMAX, Bluetooth, and ZigBee technologies. It explores the standards and encryption techniques, including TripleDES, DES, and RC2, used in WiMAX. The solution analyzes the functionality and security risks associated with Personal Area Networks (PANs) like Bluetooth and ZigBee, including device configuration issues, potential attacks like person-in-the-middle, and denial-of-service threats. Furthermore, the assignment examines energy harvesting in wireless sensor networks and its applications, summarizing relevant research papers and highlighting the advantages and challenges of energy harvesting technologies. The solution also includes a comprehensive list of references used in the assignment.

Running head: WIRELESS COMMUNICATIONS
Wireless communications
Name of the student
Name of the University
Author Note
Wireless communications
Name of the student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WIRELESS COMMUNICATIONS
Answer to question 1:
The Worldwide Interoperability for Microwave Access (WiMAX) is widely used for the
connectivity among various devices using the standards of IEEE 802.16. The common
techniques used in this method is the multiple input multiple outputs (MIMO) and orthogonal
frequency division multiplexing (OFDM) techniques (Rengaraju, Lung and Srinivasan 2012).
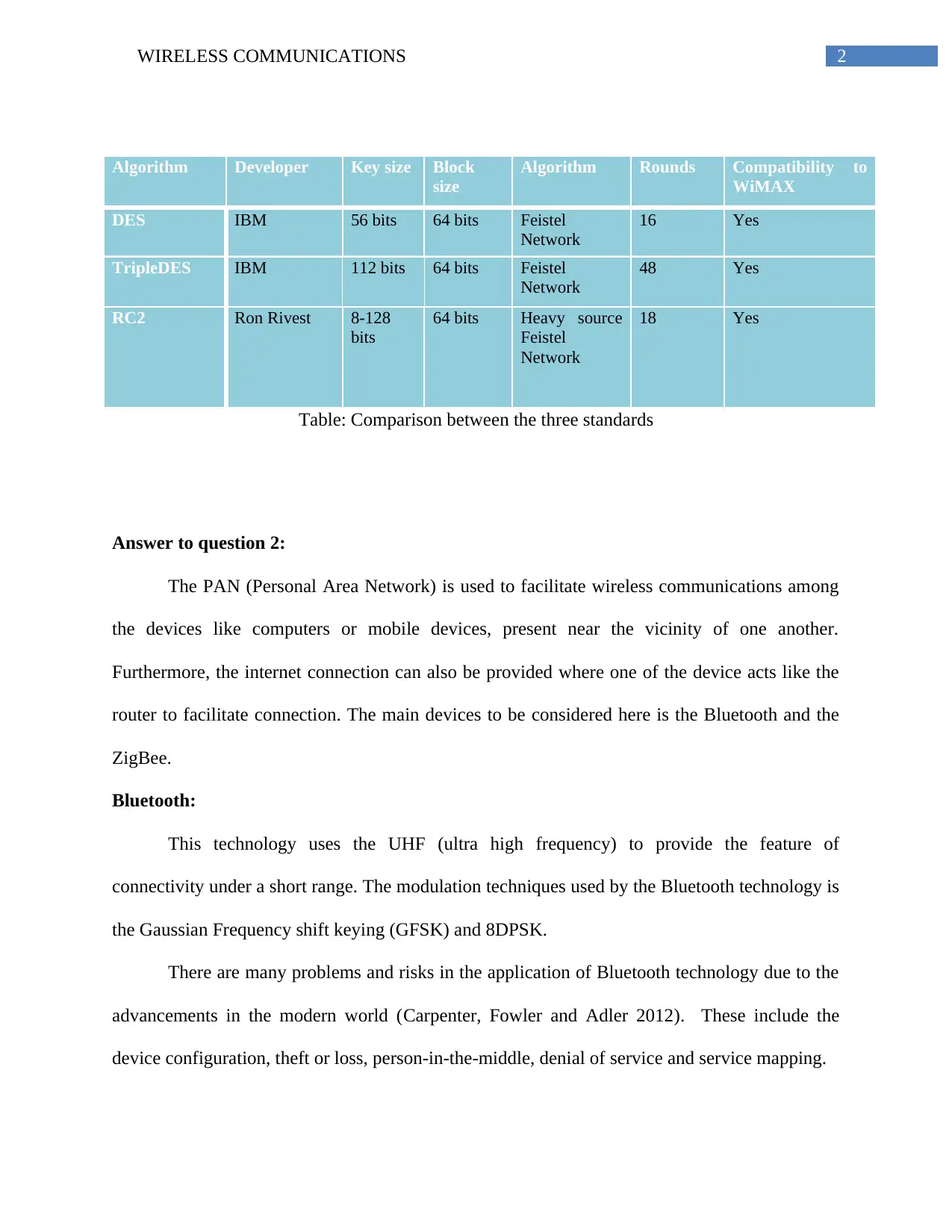
The main standards of the application of encryption purposes are the TripleDES, DES and RC2.
TripleDES:
This is another symmetric key algorithm process whose operation is the same as that of
the DES. However, the application is the main difference in these techniques. It applies the
encryption techniques for three time using three keys (i, j, k) (Kamali, Bennett and Cox 2012).
As the two key methods are vulnerable to the middle key attacks, the presence of three keys are
justified.
DES:
The Data Encryption Standard (DES) is an encryption standard following a symmetric
key algorithm. Cryptography offers the most widespread use of this algorithm. The
transformation of a text bit of a specified length to a cipher bit of similar length is the main
functions of DES (Rengaraju, Lung and Srinivasan 2012). The method also includes the
presence of a decryption key to be applied.
RC2:
The symmetric key algorithm made by Ron Rivest is named the RC2. However, the main
difference with the other two is their variable size key bits. It consists of 18 rounds for
encryption where 16 of them are of one type and the other two are of another (Kamali, Bennett
and Cox 2012). The main two types are either the MIXING or the MASHING.
Answer to question 1:
The Worldwide Interoperability for Microwave Access (WiMAX) is widely used for the
connectivity among various devices using the standards of IEEE 802.16. The common
techniques used in this method is the multiple input multiple outputs (MIMO) and orthogonal
frequency division multiplexing (OFDM) techniques (Rengaraju, Lung and Srinivasan 2012).
The main standards of the application of encryption purposes are the TripleDES, DES and RC2.
TripleDES:
This is another symmetric key algorithm process whose operation is the same as that of
the DES. However, the application is the main difference in these techniques. It applies the
encryption techniques for three time using three keys (i, j, k) (Kamali, Bennett and Cox 2012).
As the two key methods are vulnerable to the middle key attacks, the presence of three keys are
justified.
DES:
The Data Encryption Standard (DES) is an encryption standard following a symmetric
key algorithm. Cryptography offers the most widespread use of this algorithm. The
transformation of a text bit of a specified length to a cipher bit of similar length is the main
functions of DES (Rengaraju, Lung and Srinivasan 2012). The method also includes the
presence of a decryption key to be applied.
RC2:
The symmetric key algorithm made by Ron Rivest is named the RC2. However, the main
difference with the other two is their variable size key bits. It consists of 18 rounds for
encryption where 16 of them are of one type and the other two are of another (Kamali, Bennett
and Cox 2012). The main two types are either the MIXING or the MASHING.
2WIRELESS COMMUNICATIONS
Algorithm Developer Key size Block
size
Algorithm Rounds Compatibility to
WiMAX
DES IBM 56 bits 64 bits Feistel
Network
16 Yes
TripleDES IBM 112 bits 64 bits Feistel
Network
48 Yes
RC2 Ron Rivest 8-128
bits
64 bits Heavy source
Feistel
Network
18 Yes
Table: Comparison between the three standards
Answer to question 2:
The PAN (Personal Area Network) is used to facilitate wireless communications among
the devices like computers or mobile devices, present near the vicinity of one another.
Furthermore, the internet connection can also be provided where one of the device acts like the
router to facilitate connection. The main devices to be considered here is the Bluetooth and the
ZigBee.
Bluetooth:
This technology uses the UHF (ultra high frequency) to provide the feature of
connectivity under a short range. The modulation techniques used by the Bluetooth technology is
the Gaussian Frequency shift keying (GFSK) and 8DPSK.
There are many problems and risks in the application of Bluetooth technology due to the
advancements in the modern world (Carpenter, Fowler and Adler 2012). These include the
device configuration, theft or loss, person-in-the-middle, denial of service and service mapping.
Algorithm Developer Key size Block
size
Algorithm Rounds Compatibility to
WiMAX
DES IBM 56 bits 64 bits Feistel
Network
16 Yes
TripleDES IBM 112 bits 64 bits Feistel
Network
48 Yes
RC2 Ron Rivest 8-128
bits
64 bits Heavy source
Feistel
Network
18 Yes
Table: Comparison between the three standards
Answer to question 2:
The PAN (Personal Area Network) is used to facilitate wireless communications among
the devices like computers or mobile devices, present near the vicinity of one another.
Furthermore, the internet connection can also be provided where one of the device acts like the
router to facilitate connection. The main devices to be considered here is the Bluetooth and the
ZigBee.
Bluetooth:
This technology uses the UHF (ultra high frequency) to provide the feature of
connectivity under a short range. The modulation techniques used by the Bluetooth technology is
the Gaussian Frequency shift keying (GFSK) and 8DPSK.
There are many problems and risks in the application of Bluetooth technology due to the
advancements in the modern world (Carpenter, Fowler and Adler 2012). These include the
device configuration, theft or loss, person-in-the-middle, denial of service and service mapping.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3WIRELESS COMMUNICATIONS
The default configuration of the device is applied by the manufacturer. Due to its
complex working nature, people often neglect the need for customizing it. This leads to open
access to the ON mode, the BD_ADDR and clock (Versichele et al. 2012). Unethical attackers in
the vicinity can access the device using these to steal information.
Loss of devices is another concern were the presence of paired keys in the device can
lead to the attacker getting access to the paired device list to get access and steal information.
Person-in-the-middle is another process used by the unethical attackers to get access to
devices. Using this technology, an attacker can mimic another device to get access to the list of
devices it is being connected to. This process is also another known method for information
stealing and eavesdropping.
Denial of service is another attack that can be used to negate access to a system.
Although, cases for a denial of service attack has not been reported, it can be used to provide
signal jamming features and drain out the battery of the device by constantly sending
connectivity requests.
The service mapping is another method where security implications are possible. As a
device searches for another device for connection establishment, the service discovery protocol
(SDP) is mainly used to reference such requirements (Versichele et al. 2012). The attackers can
get the lists of various devices in the vicinity and get access to them.
ZigBee:
The main applications of this technique are automation in houses. The main features of
this technology are the small range connectivity and IEEE 802.15.4 compliance.
The default configuration of the device is applied by the manufacturer. Due to its
complex working nature, people often neglect the need for customizing it. This leads to open
access to the ON mode, the BD_ADDR and clock (Versichele et al. 2012). Unethical attackers in
the vicinity can access the device using these to steal information.
Loss of devices is another concern were the presence of paired keys in the device can
lead to the attacker getting access to the paired device list to get access and steal information.
Person-in-the-middle is another process used by the unethical attackers to get access to
devices. Using this technology, an attacker can mimic another device to get access to the list of
devices it is being connected to. This process is also another known method for information
stealing and eavesdropping.
Denial of service is another attack that can be used to negate access to a system.
Although, cases for a denial of service attack has not been reported, it can be used to provide
signal jamming features and drain out the battery of the device by constantly sending
connectivity requests.
The service mapping is another method where security implications are possible. As a
device searches for another device for connection establishment, the service discovery protocol
(SDP) is mainly used to reference such requirements (Versichele et al. 2012). The attackers can
get the lists of various devices in the vicinity and get access to them.
ZigBee:
The main applications of this technique are automation in houses. The main features of
this technology are the small range connectivity and IEEE 802.15.4 compliance.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4WIRELESS COMMUNICATIONS
The absence of physical security is the main problems of this technology (Rohitha et al.
2012). As the access keys for a particular device is integrated in the hardware, loss or stealing of
that device can be used to get access to the home network.
The next security challenge is the absence of security measures in the key detection and
the lack of detection of intruders.
Answer to question 3:
1. Energy harvesting in wireless sensor networks:
The modern devices need to utilize the coefficients of energy to utilize the internet of
things concept. Due to the increase of threats and risks in the modern world, the main
requirements of a device are to stay under working period for a long time (Energy harvesting in
wireless sensor networks: A comprehensive review 2017). The provided journal reports about
the presence of various sources for energy harnessing. These sources are either man-made or
natural. Furthermore, the disadvantages of such applications are also included in the provide
journal. These include the installation problems in existing devices, compliance to modern
standards and the prototype implementations (Energy harvesting in wireless sensor networks: A
comprehensive review 2017). The journal concludes by pointing out the various advantages to
such innovative applications.
2. Energy Harvesting Wireless Communications: A Review of Recent Advances
The provide journal discusses the various contributions of wireless applications. In
addition the framework for the connection along with their needed resources for implementation
is also discussed in the journal. It also discusses the various theoretical calculations for applying
the innovations (Energy Harvesting Wireless Communications: A Review of Recent Advances
The absence of physical security is the main problems of this technology (Rohitha et al.
2012). As the access keys for a particular device is integrated in the hardware, loss or stealing of
that device can be used to get access to the home network.
The next security challenge is the absence of security measures in the key detection and
the lack of detection of intruders.
Answer to question 3:
1. Energy harvesting in wireless sensor networks:
The modern devices need to utilize the coefficients of energy to utilize the internet of
things concept. Due to the increase of threats and risks in the modern world, the main
requirements of a device are to stay under working period for a long time (Energy harvesting in
wireless sensor networks: A comprehensive review 2017). The provided journal reports about
the presence of various sources for energy harnessing. These sources are either man-made or
natural. Furthermore, the disadvantages of such applications are also included in the provide
journal. These include the installation problems in existing devices, compliance to modern
standards and the prototype implementations (Energy harvesting in wireless sensor networks: A
comprehensive review 2017). The journal concludes by pointing out the various advantages to
such innovative applications.
2. Energy Harvesting Wireless Communications: A Review of Recent Advances
The provide journal discusses the various contributions of wireless applications. In
addition the framework for the connection along with their needed resources for implementation
is also discussed in the journal. It also discusses the various theoretical calculations for applying
the innovations (Energy Harvesting Wireless Communications: A Review of Recent Advances

5WIRELESS COMMUNICATIONS
2017). The main aim for the journal is to make room for the application of these innovations in
medical science, safety and environment.
Answer to question 4:
2017). The main aim for the journal is to make room for the application of these innovations in
medical science, safety and environment.
Answer to question 4:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6WIRELESS COMMUNICATIONS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7WIRELESS COMMUNICATIONS
8WIRELESS COMMUNICATIONS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9WIRELESS COMMUNICATIONS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10WIRELESS COMMUNICATIONS

11WIRELESS COMMUNICATIONS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





