Electronics 1: Wireless Communication Networks Assignment 1 Solution
VerifiedAdded on 2023/02/01
|11
|1881
|62
Homework Assignment
AI Summary
This assignment solution for an Electronics course (likely Electronics 1) covers a range of topics in wireless communication networks. It begins with an analysis of a pizza ordering and delivery system using a layered model, followed by a diagram depicting information transfer between French and Chinese Prime Ministers using translators and telephones. The solution then delves into waveform analysis, calculating frequency, time period, amplitude, and phase shift for various waveforms, including sinusoidal signals. It also addresses the calculation of source rate and channel capacity, applying the Shannon theorem. Furthermore, the assignment includes calculations for isotropic free space loss and frequency spectrum analysis. It explores channel capacity based on Nyquist criteria and differentiates between packet and circuit switching, highlighting their advantages and disadvantages. Finally, the solution provides calculations for determining antenna heights based on distance and height ratios.

ELECTORNICS 0
Wireless networks and
communication
Wireless networks and
communication
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ELECTRONIC
1
Assignment no. 1
Question 1: Describe the ordering and delivery of pizza
Above figure indicates a layer model for ordering and delivery of a pizza which includes
guests, host, telephone, and pizza cock and order clerk. From the figure it is analysed
that the guest adequately submits the request with the cook. The host imparts this
request to the clerk, who puts in the request with the cook. The telephone framework
gives the physical links for the request to be transported from host to clerk. The cook
provides the pizza to the assistant with the request structure. The assistant boxes the
pizza with the conveyance address, and the conveyance car encases all of the requests
to be delivered. The street gives the bodily way to the conveyance.
Question 2: Draw a diagram to depict the condition
From the above figure it is analysed that both French PM and Chinese PM use
translators that convert information into the English language in an effective manner.
The telephone is one of the best platforms for sending information from one place to
another and both PMs Use this process. When the French Prime minister speaks
something then he addresses his remarks to the Chinese Prime Minister. For which a
telephone system is used for transferring messages from two translators and the Prime
Minister of French use translator system for translating his remarks into the English
1
Assignment no. 1
Question 1: Describe the ordering and delivery of pizza
Above figure indicates a layer model for ordering and delivery of a pizza which includes
guests, host, telephone, and pizza cock and order clerk. From the figure it is analysed
that the guest adequately submits the request with the cook. The host imparts this
request to the clerk, who puts in the request with the cook. The telephone framework
gives the physical links for the request to be transported from host to clerk. The cook
provides the pizza to the assistant with the request structure. The assistant boxes the
pizza with the conveyance address, and the conveyance car encases all of the requests
to be delivered. The street gives the bodily way to the conveyance.
Question 2: Draw a diagram to depict the condition
From the above figure it is analysed that both French PM and Chinese PM use
translators that convert information into the English language in an effective manner.
The telephone is one of the best platforms for sending information from one place to
another and both PMs Use this process. When the French Prime minister speaks
something then he addresses his remarks to the Chinese Prime Minister. For which a
telephone system is used for transferring messages from two translators and the Prime
Minister of French use translator system for translating his remarks into the English
ELECTRONIC
2
language. After that, he transfers these signals to the Chinese Prime Minister who also
uses translators and translates these signals into the Chinese language.
Question 3
For the first Waveform:
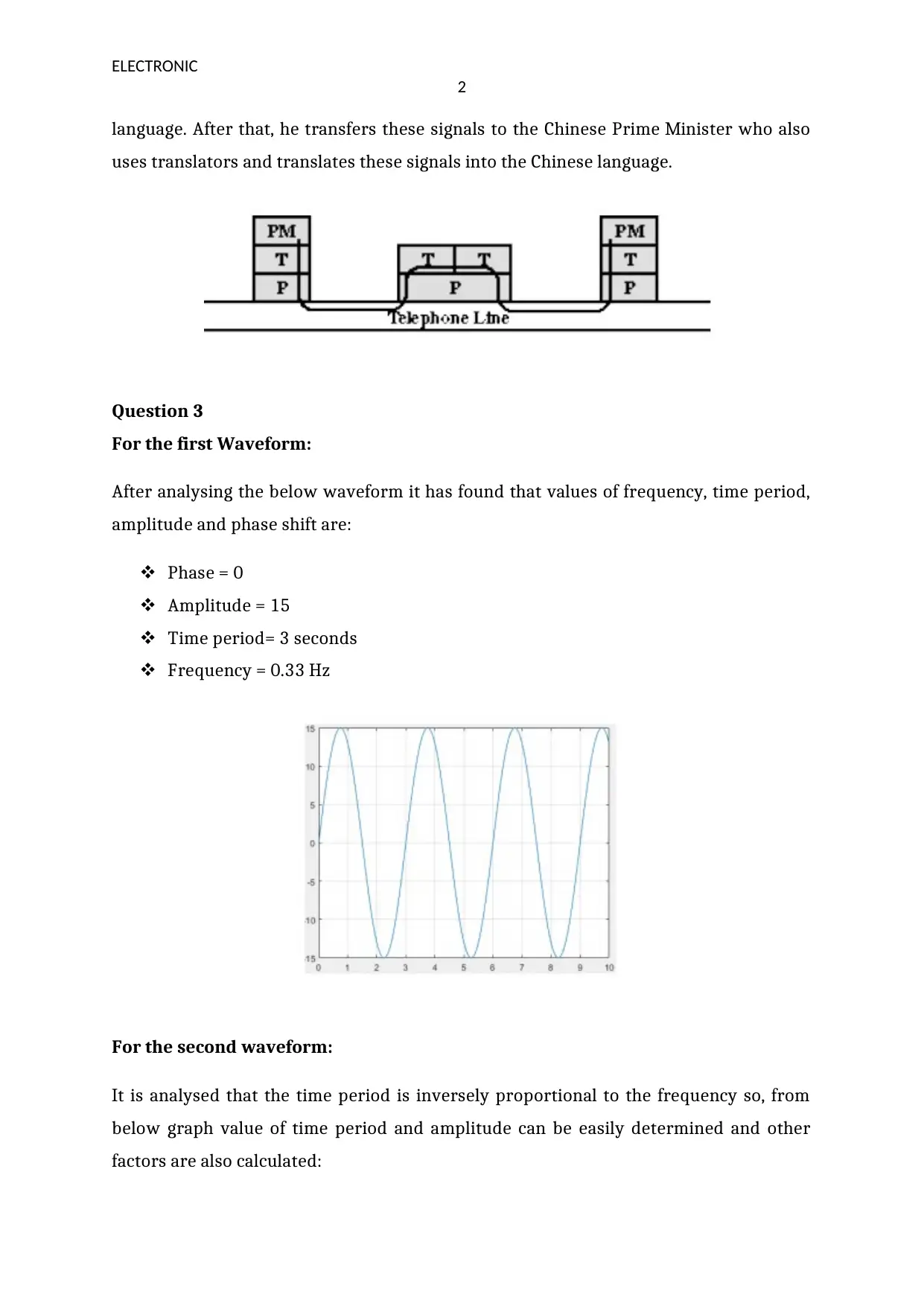
After analysing the below waveform it has found that values of frequency, time period,
amplitude and phase shift are:
Phase = 0
Amplitude = 15
Time period= 3 seconds
Frequency = 0.33 Hz
For the second waveform:
It is analysed that the time period is inversely proportional to the frequency so, from
below graph value of time period and amplitude can be easily determined and other
factors are also calculated:
2
language. After that, he transfers these signals to the Chinese Prime Minister who also
uses translators and translates these signals into the Chinese language.
Question 3
For the first Waveform:
After analysing the below waveform it has found that values of frequency, time period,
amplitude and phase shift are:
Phase = 0
Amplitude = 15
Time period= 3 seconds
Frequency = 0.33 Hz
For the second waveform:
It is analysed that the time period is inversely proportional to the frequency so, from
below graph value of time period and amplitude can be easily determined and other
factors are also calculated:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ELECTRONIC
3
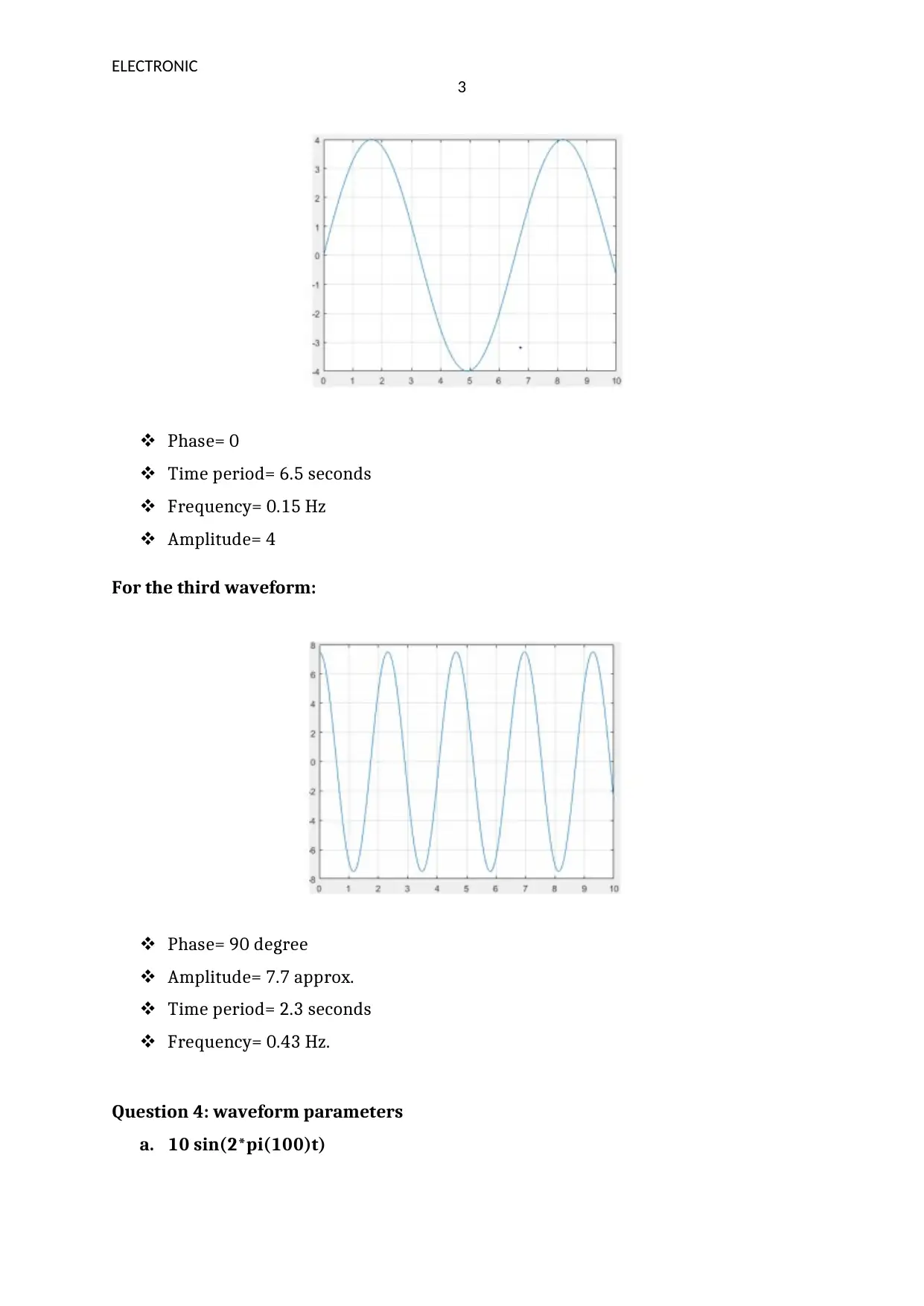
Phase= 0
Time period= 6.5 seconds
Frequency= 0.15 Hz
Amplitude= 4
For the third waveform:
Phase= 90 degree
Amplitude= 7.7 approx.
Time period= 2.3 seconds
Frequency= 0.43 Hz.
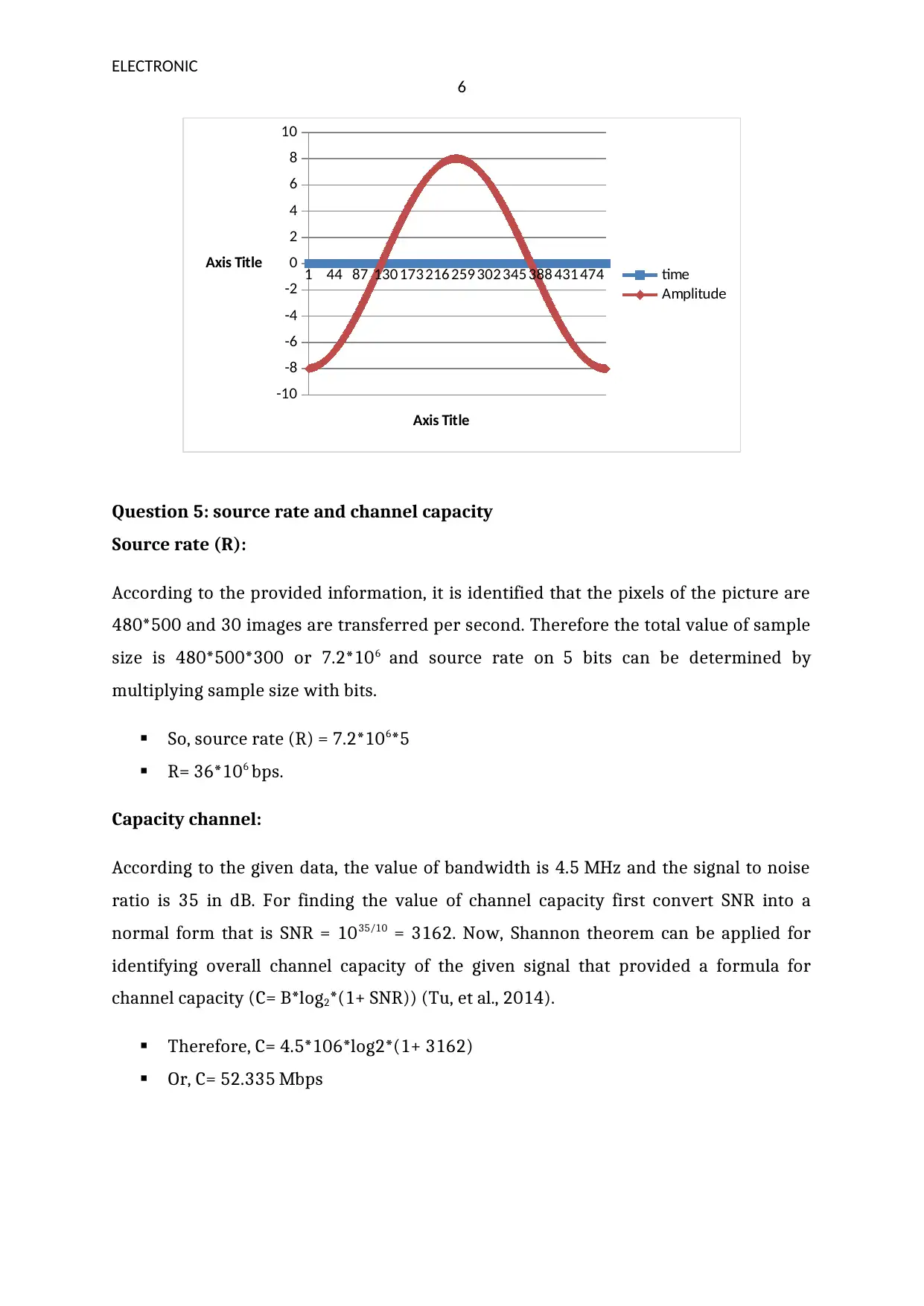
Question 4: waveform parameters
a. 10 sin(2*pi(100)t)
3
Phase= 0
Time period= 6.5 seconds
Frequency= 0.15 Hz
Amplitude= 4
For the third waveform:
Phase= 90 degree
Amplitude= 7.7 approx.
Time period= 2.3 seconds
Frequency= 0.43 Hz.
Question 4: waveform parameters
a. 10 sin(2*pi(100)t)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
ELECTRONIC
4
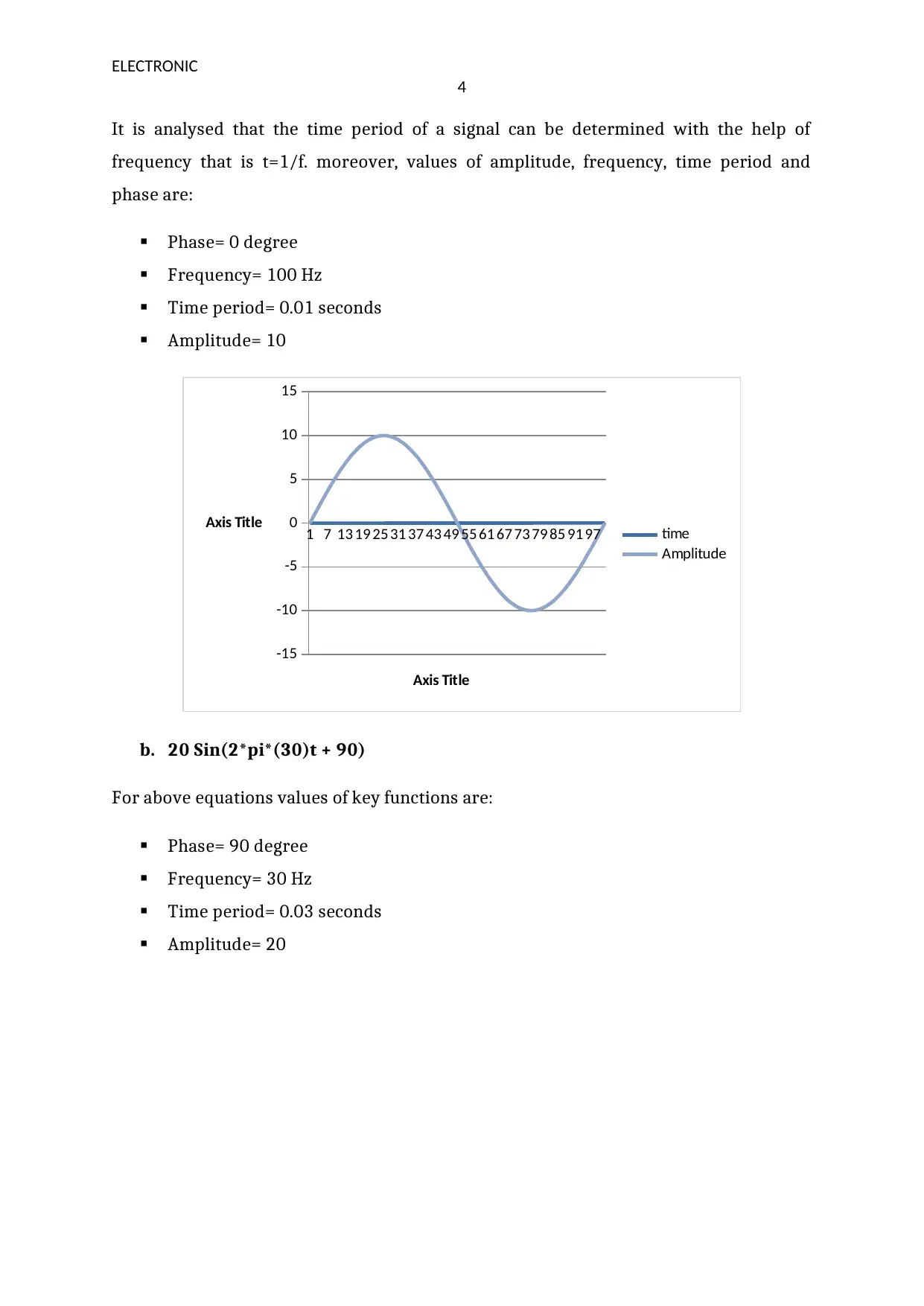
It is analysed that the time period of a signal can be determined with the help of
frequency that is t=1/f. moreover, values of amplitude, frequency, time period and
phase are:
Phase= 0 degree
Frequency= 100 Hz
Time period= 0.01 seconds
Amplitude= 10
1 7 13 19 25 31 37 43 49 55 61 67 73 79 85 91 97
-15
-10
-5
0
5
10
15
time
Amplitude
Axis Title
Axis Title
b. 20 Sin(2*pi*(30)t + 90)
For above equations values of key functions are:
Phase= 90 degree
Frequency= 30 Hz
Time period= 0.03 seconds
Amplitude= 20
4
It is analysed that the time period of a signal can be determined with the help of
frequency that is t=1/f. moreover, values of amplitude, frequency, time period and
phase are:
Phase= 0 degree
Frequency= 100 Hz
Time period= 0.01 seconds
Amplitude= 10
1 7 13 19 25 31 37 43 49 55 61 67 73 79 85 91 97
-15
-10
-5
0
5
10
15
time
Amplitude
Axis Title
Axis Title
b. 20 Sin(2*pi*(30)t + 90)
For above equations values of key functions are:
Phase= 90 degree
Frequency= 30 Hz
Time period= 0.03 seconds
Amplitude= 20
ELECTRONIC
5
1 29 57 85 113141169197225253281309
-25
-20
-15
-10
-5
0
5
10
15
20
25
time
Amplitude
Axis Title
Axis Title
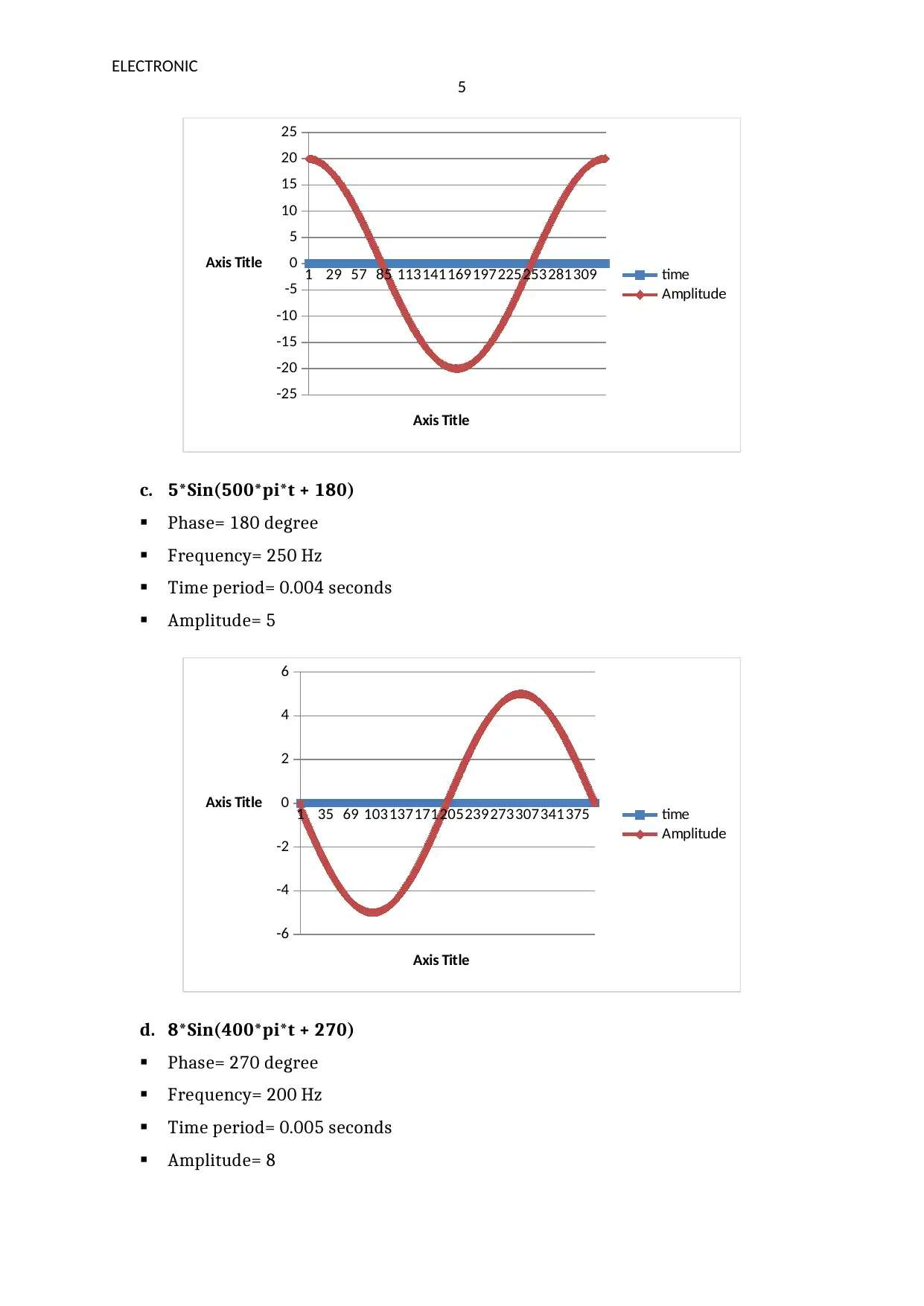
c. 5*Sin(500*pi*t + 180)
Phase= 180 degree
Frequency= 250 Hz
Time period= 0.004 seconds
Amplitude= 5
1 35 69 103137171205239273307341375
-6
-4
-2
0
2
4
6
time
Amplitude
Axis Title
Axis Title
d. 8*Sin(400*pi*t + 270)
Phase= 270 degree
Frequency= 200 Hz
Time period= 0.005 seconds
Amplitude= 8
5
1 29 57 85 113141169197225253281309
-25
-20
-15
-10
-5
0
5
10
15
20
25
time
Amplitude
Axis Title
Axis Title
c. 5*Sin(500*pi*t + 180)
Phase= 180 degree
Frequency= 250 Hz
Time period= 0.004 seconds
Amplitude= 5
1 35 69 103137171205239273307341375
-6
-4
-2
0
2
4
6
time
Amplitude
Axis Title
Axis Title
d. 8*Sin(400*pi*t + 270)
Phase= 270 degree
Frequency= 200 Hz
Time period= 0.005 seconds
Amplitude= 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ELECTRONIC
6
1 44 87 130 173 216 259 302 345 388 431 474
-10
-8
-6
-4
-2
0
2
4
6
8
10
time
Amplitude
Axis Title
Axis Title
Question 5: source rate and channel capacity
Source rate (R):
According to the provided information, it is identified that the pixels of the picture are
480*500 and 30 images are transferred per second. Therefore the total value of sample
size is 480*500*300 or 7.2*106 and source rate on 5 bits can be determined by
multiplying sample size with bits.
So, source rate (R) = 7.2*106*5
R= 36*106 bps.
Capacity channel:
According to the given data, the value of bandwidth is 4.5 MHz and the signal to noise
ratio is 35 in dB. For finding the value of channel capacity first convert SNR into a
normal form that is SNR = 1035/10 = 3162. Now, Shannon theorem can be applied for
identifying overall channel capacity of the given signal that provided a formula for
channel capacity (C= B*log2*(1+ SNR)) (Tu, et al., 2014).
Therefore, C= 4.5*106*log2*(1+ 3162)
Or, C= 52.335 Mbps
6
1 44 87 130 173 216 259 302 345 388 431 474
-10
-8
-6
-4
-2
0
2
4
6
8
10
time
Amplitude
Axis Title
Axis Title
Question 5: source rate and channel capacity
Source rate (R):
According to the provided information, it is identified that the pixels of the picture are
480*500 and 30 images are transferred per second. Therefore the total value of sample
size is 480*500*300 or 7.2*106 and source rate on 5 bits can be determined by
multiplying sample size with bits.
So, source rate (R) = 7.2*106*5
R= 36*106 bps.
Capacity channel:
According to the given data, the value of bandwidth is 4.5 MHz and the signal to noise
ratio is 35 in dB. For finding the value of channel capacity first convert SNR into a
normal form that is SNR = 1035/10 = 3162. Now, Shannon theorem can be applied for
identifying overall channel capacity of the given signal that provided a formula for
channel capacity (C= B*log2*(1+ SNR)) (Tu, et al., 2014).
Therefore, C= 4.5*106*log2*(1+ 3162)
Or, C= 52.335 Mbps
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ELECTRONIC
7
Question 6: isotropic free space loss
From given scenario it is identified that f= 4 GHz, distance= 35863 kilometres and value
of isotropic free space loss can be calculated from following formula:
PL= 20log10 (f) +20log10 (d) - 147.56 dB
So, PL= 20log10 (4*109) +20log10 (35.863*106) - 147.56 dB
Or, PL= 195.66 dB
Question 7: frequency, bandwidth, and spectrum and channel capacity of the
given signal:
As per the given question the value of signal s(t) is 5*sin(200𝜋 𝑡 ) + sin(600𝜋𝑡) and it
contains two frequency signals such as 100 Hz and 300 Hz. So, the final value of
frequency is GCD of both these factors or GCD (100, 300)= 100 Hz.
Therefore, frequency= 100 Hz.
And bandwidth is 300-100= 200 Hz.
For finding the spectrum of the given signal it is very important to determine frequency
factors from the input signal. After converting signal into the complex form frequency
pairs can be determined and these are {(100, 2.5), (-100, 2.5), (300, 0.5), (-300, 0.5)}.
Below chart indicates the frequency spectrum of the given signal:
-300 -200 -100 0 100 200
0
0.5
1
1.5
2
2.5
3
Series1
7
Question 6: isotropic free space loss
From given scenario it is identified that f= 4 GHz, distance= 35863 kilometres and value
of isotropic free space loss can be calculated from following formula:
PL= 20log10 (f) +20log10 (d) - 147.56 dB
So, PL= 20log10 (4*109) +20log10 (35.863*106) - 147.56 dB
Or, PL= 195.66 dB
Question 7: frequency, bandwidth, and spectrum and channel capacity of the
given signal:
As per the given question the value of signal s(t) is 5*sin(200𝜋 𝑡 ) + sin(600𝜋𝑡) and it
contains two frequency signals such as 100 Hz and 300 Hz. So, the final value of
frequency is GCD of both these factors or GCD (100, 300)= 100 Hz.
Therefore, frequency= 100 Hz.
And bandwidth is 300-100= 200 Hz.
For finding the spectrum of the given signal it is very important to determine frequency
factors from the input signal. After converting signal into the complex form frequency
pairs can be determined and these are {(100, 2.5), (-100, 2.5), (300, 0.5), (-300, 0.5)}.
Below chart indicates the frequency spectrum of the given signal:
-300 -200 -100 0 100 200
0
0.5
1
1.5
2
2.5
3
Series1

ELECTRONIC
8
Channel capacity can be determined with the help of Nyquist criteria that use
bandwidth and numbers of levels for finding the capacity of the channel (Mo, and Heath,
2015).
C= 2*B*log2(M) (Akdeniz, et al., 2014).
According to the given question numbers of levels are 2, 4 and 8 and the channel
capacity of each level is given below:
At M=2
C= 2*200log2 (2)
C= 400 bits/s/Hz
At M= 4:
C= 2*200log2 (4)
C= 800 bits/s/Hz
At M= 8:
C= 2*200log2 (8)
C= 1200 bits/s/Hz
Question 8: nyquist formula
After analysing the fundamental concept of Nyquist theorem the data rate of a signal
over a channel can be calculated with the help of bandwidth and numbers of levels ( Le,
eta l., 2014). Therefore, the formula for calculating the data rate is described below:
Data rate= bandwidth* log2(L)
So, data rate over a channel can be enhanced by increasing numbers of levels in the
signal which is another approach for increasing the bit rate. Nyquist criteria also
identified that increasing numbers of levels in the signal may decrease the reliability of
the system which is one of the biggest disadvantages of this process.
Question 9: packet switching vs. circuit switching
Difference between packet switching and circuit switching
Circuit switching Packet Switching
Less efficient More efficient
Take more time for sending information Transfer data or information immediately
All data signals follow a single path Each data use different data packet along
with a different path (Farrington, et al.,
2011).
Waste a huge amount of bandwidth (Das, No bandwidth wastage
8
Channel capacity can be determined with the help of Nyquist criteria that use
bandwidth and numbers of levels for finding the capacity of the channel (Mo, and Heath,
2015).
C= 2*B*log2(M) (Akdeniz, et al., 2014).
According to the given question numbers of levels are 2, 4 and 8 and the channel
capacity of each level is given below:
At M=2
C= 2*200log2 (2)
C= 400 bits/s/Hz
At M= 4:
C= 2*200log2 (4)
C= 800 bits/s/Hz
At M= 8:
C= 2*200log2 (8)
C= 1200 bits/s/Hz
Question 8: nyquist formula
After analysing the fundamental concept of Nyquist theorem the data rate of a signal
over a channel can be calculated with the help of bandwidth and numbers of levels ( Le,
eta l., 2014). Therefore, the formula for calculating the data rate is described below:
Data rate= bandwidth* log2(L)
So, data rate over a channel can be enhanced by increasing numbers of levels in the
signal which is another approach for increasing the bit rate. Nyquist criteria also
identified that increasing numbers of levels in the signal may decrease the reliability of
the system which is one of the biggest disadvantages of this process.
Question 9: packet switching vs. circuit switching
Difference between packet switching and circuit switching
Circuit switching Packet Switching
Less efficient More efficient
Take more time for sending information Transfer data or information immediately
All data signals follow a single path Each data use different data packet along
with a different path (Farrington, et al.,
2011).
Waste a huge amount of bandwidth (Das, No bandwidth wastage
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ELECTRONIC
9
Parulkar, and McKeown, 2009).
Advantages of packet switching over circuit switching
More efficient and effective
Does not require any external pathway
Reduce errors and distortion in communication systems
Question 10: Height of antennas
As per the given case, D= 40 KM and h1= 2h2
So, for finding the value of height distance formula can be used that is D=
3.57*sqrt (kH1+kH2)
Here, K= 4/3 and d=40 KM, and h1=2h2
So, 40= 3.57*1.1547(sqrt(3H2))
After solving the above equation it is observed that the height of one antenna is
31.6 meters and another antenna is 63.3 meters.
9
Parulkar, and McKeown, 2009).
Advantages of packet switching over circuit switching
More efficient and effective
Does not require any external pathway
Reduce errors and distortion in communication systems
Question 10: Height of antennas
As per the given case, D= 40 KM and h1= 2h2
So, for finding the value of height distance formula can be used that is D=
3.57*sqrt (kH1+kH2)
Here, K= 4/3 and d=40 KM, and h1=2h2
So, 40= 3.57*1.1547(sqrt(3H2))
After solving the above equation it is observed that the height of one antenna is
31.6 meters and another antenna is 63.3 meters.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ELECTRONIC
10
References
Akdeniz, M.R., Liu, Y., Samimi, M.K., Sun, S., Rangan, S., Rappaport, T.S. and Erkip, E.,
(2014) Millimeter wave channel modeling and cellular capacity evaluation. IEEE journal
on selected areas in communications, 32(6), pp.1164-1179.
Das, S., Parulkar, G. and McKeown, N., (2009) Simple unified control for packet and
circuit networks. In 2009 IEEE/LEOS Summer Topical Meeting, 10(8), pp. 147-148.
Farrington, N., Porter, G., Radhakrishnan, S., Bazzaz, H.H., Subramanya, V., Fainman, Y.,
Papen, G. and Vahdat, A., (2011) Helios: a hybrid electrical/optical switch architecture
for modular data centers. ACM SIGCOMM Computer Communication Review, 41(4),
pp.339-350.
Le, C., Schellmann, M., Fuhrwerk, M. and Peissig, J., (2014) On the practical benefits of
faster-than-Nyquist signaling. In 2014 International Conference on Advanced
Technologies for Communications (ATC 2014), 12(2), pp. 208-213.
Mo, J. and Heath, R.W., (2015) Capacity analysis of one-bit quantized MIMO systems
with transmitter channel state information. IEEE transactions on signal
processing, 63(20), pp.5498-5512.
Tu, J.H., Rowley, C.W., Kutz, J.N. and Shang, J.K., (2014) Spectral analysis of fluid flows
using sub-Nyquist-rate PIV data. Experiments in Fluids, 55(9), p.1805.
10
References
Akdeniz, M.R., Liu, Y., Samimi, M.K., Sun, S., Rangan, S., Rappaport, T.S. and Erkip, E.,
(2014) Millimeter wave channel modeling and cellular capacity evaluation. IEEE journal
on selected areas in communications, 32(6), pp.1164-1179.
Das, S., Parulkar, G. and McKeown, N., (2009) Simple unified control for packet and
circuit networks. In 2009 IEEE/LEOS Summer Topical Meeting, 10(8), pp. 147-148.
Farrington, N., Porter, G., Radhakrishnan, S., Bazzaz, H.H., Subramanya, V., Fainman, Y.,
Papen, G. and Vahdat, A., (2011) Helios: a hybrid electrical/optical switch architecture
for modular data centers. ACM SIGCOMM Computer Communication Review, 41(4),
pp.339-350.
Le, C., Schellmann, M., Fuhrwerk, M. and Peissig, J., (2014) On the practical benefits of
faster-than-Nyquist signaling. In 2014 International Conference on Advanced
Technologies for Communications (ATC 2014), 12(2), pp. 208-213.
Mo, J. and Heath, R.W., (2015) Capacity analysis of one-bit quantized MIMO systems
with transmitter channel state information. IEEE transactions on signal
processing, 63(20), pp.5498-5512.
Tu, J.H., Rowley, C.W., Kutz, J.N. and Shang, J.K., (2014) Spectral analysis of fluid flows
using sub-Nyquist-rate PIV data. Experiments in Fluids, 55(9), p.1805.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




