RFID Technology Implementation Survey
VerifiedAdded on 2020/05/11
|111
|27574
|62
AI Summary
This assignment presents a survey questionnaire focused on understanding the implementation and perception of RFID (Radio-Frequency Identification) technology within organizations. It covers various aspects like implementation timelines, drivers for adoption (asset tracking, WIP), advantages over barcode scanners, specific use cases, objectives, perceived benefits, technical specifications, privacy and security concerns, cost considerations, government support needs, and future outlook. The survey aims to gather insights into the current state and future potential of RFID technology.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
RFID and mobile fusion for authenticated ATM transaction
Name of the Student:
Name of the University:
Author note:
RFID and mobile fusion for authenticated ATM transaction
Name of the Student:
Name of the University:
Author note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Abstract
This paper gives a research on radio frequency identification (RFID) innovation. At first RFID
tags were created to in the long run supplant scanner tags in supply chains. Their favorable
circumstances are that they can be perused remotely and without observable pathway; contain
more data than scanner tags. The RFID innovation did not stop at thing level labeling. Since the
utilizations for RFID tags are so across the board, there is an extensive enthusiasm for bringing
down the expenses for creating them. For reasons unknown printing labels may turn into a
feasible other option to customary creation. The study deals with reviewing literature from
different sources. In addition, research methodology, finding and analysis as well as conclusion
and recommendations are discussed in the study.
Abstract
This paper gives a research on radio frequency identification (RFID) innovation. At first RFID
tags were created to in the long run supplant scanner tags in supply chains. Their favorable
circumstances are that they can be perused remotely and without observable pathway; contain
more data than scanner tags. The RFID innovation did not stop at thing level labeling. Since the
utilizations for RFID tags are so across the board, there is an extensive enthusiasm for bringing
down the expenses for creating them. For reasons unknown printing labels may turn into a
feasible other option to customary creation. The study deals with reviewing literature from
different sources. In addition, research methodology, finding and analysis as well as conclusion
and recommendations are discussed in the study.

2RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Acknowledgement
Conducting the research study enhances me to improve my knowledge as well as analytical
ability in RFID technology. It gave me the chance to face challenges all the while and conquer
them. It will not be possible to conduct the research without the significant direction of my
professors, companions and every one of who have added to this advancing knowledge. I also
want to thank my supervisor __________ for helping me in my research work as well as give
their full support during the research process. I would also thank all the participants within this
study for giving their time and helping me out. From the support of people, I am inspired to work
on the research in this subject area. Finally, thank you to my family members those help me and
encourage me.
Thank You.
Acknowledgement
Conducting the research study enhances me to improve my knowledge as well as analytical
ability in RFID technology. It gave me the chance to face challenges all the while and conquer
them. It will not be possible to conduct the research without the significant direction of my
professors, companions and every one of who have added to this advancing knowledge. I also
want to thank my supervisor __________ for helping me in my research work as well as give
their full support during the research process. I would also thank all the participants within this
study for giving their time and helping me out. From the support of people, I am inspired to work
on the research in this subject area. Finally, thank you to my family members those help me and
encourage me.
Thank You.

3RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Table of Contents
Chapter 1: Introduction....................................................................................................................8
1.1 Background of the study............................................................................................................8
1.2 Research Aims and Objectives..................................................................................................9
1.2.1 Aims of the study....................................................................................................................9
1.2.2 Objectives of the study...........................................................................................................9
1.3 Research Questions..................................................................................................................10
1.4 Problem Statement...................................................................................................................10
1.5 Rationale of the study..............................................................................................................12
1.6 Structure of the study...............................................................................................................13
Capter 2: Literature Review...........................................................................................................15
2.1 Preface.....................................................................................................................................15
2.2 Overview of Radio Frequency Identification (RFID) technology...........................................15
2.3 Development history of RFID.................................................................................................19
2.4 Components in RFID used at present days..............................................................................20
2.4.1 Frequency bands...................................................................................................................22
2.4.2 Sources of energy.................................................................................................................23
2.4.3 Standards...............................................................................................................................24
2.5 Principles of RFID...................................................................................................................24
2.6 Applications of RFID..............................................................................................................29
Table of Contents
Chapter 1: Introduction....................................................................................................................8
1.1 Background of the study............................................................................................................8
1.2 Research Aims and Objectives..................................................................................................9
1.2.1 Aims of the study....................................................................................................................9
1.2.2 Objectives of the study...........................................................................................................9
1.3 Research Questions..................................................................................................................10
1.4 Problem Statement...................................................................................................................10
1.5 Rationale of the study..............................................................................................................12
1.6 Structure of the study...............................................................................................................13
Capter 2: Literature Review...........................................................................................................15
2.1 Preface.....................................................................................................................................15
2.2 Overview of Radio Frequency Identification (RFID) technology...........................................15
2.3 Development history of RFID.................................................................................................19
2.4 Components in RFID used at present days..............................................................................20
2.4.1 Frequency bands...................................................................................................................22
2.4.2 Sources of energy.................................................................................................................23
2.4.3 Standards...............................................................................................................................24
2.5 Principles of RFID...................................................................................................................24
2.6 Applications of RFID..............................................................................................................29
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
2.6.1 Supply chain management system........................................................................................29
2.6.2 Application in fashion industry............................................................................................32
2.6.3 Inventory management.........................................................................................................33
2.6.4 Production control................................................................................................................34
2.6.5 Retail management...............................................................................................................34
2.6.6 RFID for brand segregation..................................................................................................36
2.6.7 RFID tags for care labeling...................................................................................................37
2.7 Advantages of RFID technology.............................................................................................39
2.8 Privacy and security issues in RFID........................................................................................40
2.9 Summary..................................................................................................................................43
Chapter 3: Research Methodology................................................................................................43
3.1 Preface.....................................................................................................................................43
3.2 Method Outline........................................................................................................................43
3.3 Research Onion........................................................................................................................44
3.4 Research Philosophy................................................................................................................45
3.5 Research Approach..................................................................................................................46
3.6 Research Design......................................................................................................................46
3.7 Research strategy.....................................................................................................................48
3.8 Data Collection........................................................................................................................48
3.9 Sample Size.............................................................................................................................49
2.6.1 Supply chain management system........................................................................................29
2.6.2 Application in fashion industry............................................................................................32
2.6.3 Inventory management.........................................................................................................33
2.6.4 Production control................................................................................................................34
2.6.5 Retail management...............................................................................................................34
2.6.6 RFID for brand segregation..................................................................................................36
2.6.7 RFID tags for care labeling...................................................................................................37
2.7 Advantages of RFID technology.............................................................................................39
2.8 Privacy and security issues in RFID........................................................................................40
2.9 Summary..................................................................................................................................43
Chapter 3: Research Methodology................................................................................................43
3.1 Preface.....................................................................................................................................43
3.2 Method Outline........................................................................................................................43
3.3 Research Onion........................................................................................................................44
3.4 Research Philosophy................................................................................................................45
3.5 Research Approach..................................................................................................................46
3.6 Research Design......................................................................................................................46
3.7 Research strategy.....................................................................................................................48
3.8 Data Collection........................................................................................................................48
3.9 Sample Size.............................................................................................................................49

5RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
3.10 Data Analysis.........................................................................................................................49
3.11 Accessibility issues................................................................................................................50
3.12 Ethical Consideration.............................................................................................................50
3.13 Gantt chart.............................................................................................................................51
3.14 Summary................................................................................................................................51
Chapter 4: Results and findings.....................................................................................................53
4.1 Preface.....................................................................................................................................53
4.2 Quantitative analysis................................................................................................................53
4.3 Summary..................................................................................................................................76
Chapter 5: Conclusion and Recommendations..............................................................................77
5.1 Conclusion...............................................................................................................................77
5.2 Linking with objectives...........................................................................................................77
5.3 Recommendations....................................................................................................................78
5.4 Limitation and Future scopes...................................................................................................79
References......................................................................................................................................81
Bibliography..................................................................................................................................91
Appendices..................................................................................................................................108
Appendix 1...................................................................................................................................108
Appendix 2...................................................................................................................................109
3.10 Data Analysis.........................................................................................................................49
3.11 Accessibility issues................................................................................................................50
3.12 Ethical Consideration.............................................................................................................50
3.13 Gantt chart.............................................................................................................................51
3.14 Summary................................................................................................................................51
Chapter 4: Results and findings.....................................................................................................53
4.1 Preface.....................................................................................................................................53
4.2 Quantitative analysis................................................................................................................53
4.3 Summary..................................................................................................................................76
Chapter 5: Conclusion and Recommendations..............................................................................77
5.1 Conclusion...............................................................................................................................77
5.2 Linking with objectives...........................................................................................................77
5.3 Recommendations....................................................................................................................78
5.4 Limitation and Future scopes...................................................................................................79
References......................................................................................................................................81
Bibliography..................................................................................................................................91
Appendices..................................................................................................................................108
Appendix 1...................................................................................................................................108
Appendix 2...................................................................................................................................109

6RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
List of tables
Table 1: Differences between active tags and passive tags...............................................15
Table 2: Use of RFID technology......................................................................................51
Table 3: Time-period of using RFID technology..............................................................53
Table 4: Major drivers for implementing RFID................................................................54
Table 5: Advantages of using RFID technology...............................................................56
Table 6: Purposes of implementing RFID.........................................................................57
Table 7: the objectives for using RFID..............................................................................59
Table 8: Tracking products accurately as advantage for RFID.........................................60
Table 9: Reader specifications of RFID............................................................................62
Table 10: Antenna specifications of RFID........................................................................63
Table 11: Product specifications of RFID.........................................................................65
Table 12: Privacy and security in RFID............................................................................66
Table 13: Cost of implementing RFID..............................................................................68
Table 14: Governments’ support for RFID.......................................................................69
Table 15: Major concerns for implementing RFID technology........................................71
Table 16: Future of RFID technology...............................................................................72
Table 17: Gantt chart.......................................................................................................106
List of tables
Table 1: Differences between active tags and passive tags...............................................15
Table 2: Use of RFID technology......................................................................................51
Table 3: Time-period of using RFID technology..............................................................53
Table 4: Major drivers for implementing RFID................................................................54
Table 5: Advantages of using RFID technology...............................................................56
Table 6: Purposes of implementing RFID.........................................................................57
Table 7: the objectives for using RFID..............................................................................59
Table 8: Tracking products accurately as advantage for RFID.........................................60
Table 9: Reader specifications of RFID............................................................................62
Table 10: Antenna specifications of RFID........................................................................63
Table 11: Product specifications of RFID.........................................................................65
Table 12: Privacy and security in RFID............................................................................66
Table 13: Cost of implementing RFID..............................................................................68
Table 14: Governments’ support for RFID.......................................................................69
Table 15: Major concerns for implementing RFID technology........................................71
Table 16: Future of RFID technology...............................................................................72
Table 17: Gantt chart.......................................................................................................106
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
List of figures
Figure 1: A passive RFID tag............................................................................................22
Figure 2: Near filed mechanism of RFID tags..................................................................27
Figure 3: Far field mechanism of RFID tags.....................................................................29
Figure 4: Benefits in supply chain.....................................................................................31
Figure 5: Research onion...................................................................................................45
Figure 6: Use of RFID technology....................................................................................54
Figure 7: Time-period of using RFID technology.............................................................55
Figure 8: Major drivers for implementing RFID...............................................................56
Figure 9: Advantages of using RFID technology..............................................................58
Figure 10: Purposes of implementing RFID......................................................................59
Figure 11: the objectives for using RFID..........................................................................61
Figure 12: Tracking products accurately as advantage for RFID......................................62
Figure 13: Reader specifications of RFID.........................................................................64
Figure 14: Antenna specifications of RFID.......................................................................65
Figure 15: Product specifications of RFID........................................................................67
Figure 16: Privacy and security in RFID...........................................................................68
Figure 17: Cost of implementing RFID.............................................................................70
Figure 18: Governments’ support for RFID......................................................................71
Figure 19: Major concerns for implementing RFID technology.......................................73
Figure 20: Future of RFID technology..............................................................................74
List of figures
Figure 1: A passive RFID tag............................................................................................22
Figure 2: Near filed mechanism of RFID tags..................................................................27
Figure 3: Far field mechanism of RFID tags.....................................................................29
Figure 4: Benefits in supply chain.....................................................................................31
Figure 5: Research onion...................................................................................................45
Figure 6: Use of RFID technology....................................................................................54
Figure 7: Time-period of using RFID technology.............................................................55
Figure 8: Major drivers for implementing RFID...............................................................56
Figure 9: Advantages of using RFID technology..............................................................58
Figure 10: Purposes of implementing RFID......................................................................59
Figure 11: the objectives for using RFID..........................................................................61
Figure 12: Tracking products accurately as advantage for RFID......................................62
Figure 13: Reader specifications of RFID.........................................................................64
Figure 14: Antenna specifications of RFID.......................................................................65
Figure 15: Product specifications of RFID........................................................................67
Figure 16: Privacy and security in RFID...........................................................................68
Figure 17: Cost of implementing RFID.............................................................................70
Figure 18: Governments’ support for RFID......................................................................71
Figure 19: Major concerns for implementing RFID technology.......................................73
Figure 20: Future of RFID technology..............................................................................74

8RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Chapter 1: Introduction
1.1 Background of the study
At present years, radio frequency identification technology (RFID) has moved from
obscurity into mainstream applications. It helps to handle manufacturing products and materials
in faster way (Dobkin 2012). In addition, RFID enables detection from a distance along with the
earlier bar code technology. RFID technology has been around 60 years in market and was
developed in order to enhance warfare technologies. The cards enabled RFID have brought
revolution in large sectors handling a large number of products. RFID tags can support a larger
set of unique IDs compared to bar codes. Moreover, it can incorporate additional data like
manufacturer, type of product as well as measurement of environmental factors like temperature.
Along with these, RFID systems can discern several distinctive tags, which are located in the
general area without taking any human assistance.
On contrary, consider a super market checkout where it is required to orient each bar-
coded item toward reader before scanning. However, it has not been in mainstream over 50
years. The primary reason is cost. In terms of electronic identification technologies, it is
important to compete with the rock-bottom pricing of printed signs. Thus, it is required to be low
cost and provide added value for the organization in order to recover the cost. However, RFID is
not so affordable compared traditional tagging technologies (Zhu et al. 2012). On contrary, RFID
can offer added value for enabling it in large scale adoption in order to manage customer retail
products. The benefits with RFID tags is that these are not based on the line of sight concept as
well as used in times of adverse weather conditions consisting of snow, fog as well as ice.
Chapter 1: Introduction
1.1 Background of the study
At present years, radio frequency identification technology (RFID) has moved from
obscurity into mainstream applications. It helps to handle manufacturing products and materials
in faster way (Dobkin 2012). In addition, RFID enables detection from a distance along with the
earlier bar code technology. RFID technology has been around 60 years in market and was
developed in order to enhance warfare technologies. The cards enabled RFID have brought
revolution in large sectors handling a large number of products. RFID tags can support a larger
set of unique IDs compared to bar codes. Moreover, it can incorporate additional data like
manufacturer, type of product as well as measurement of environmental factors like temperature.
Along with these, RFID systems can discern several distinctive tags, which are located in the
general area without taking any human assistance.
On contrary, consider a super market checkout where it is required to orient each bar-
coded item toward reader before scanning. However, it has not been in mainstream over 50
years. The primary reason is cost. In terms of electronic identification technologies, it is
important to compete with the rock-bottom pricing of printed signs. Thus, it is required to be low
cost and provide added value for the organization in order to recover the cost. However, RFID is
not so affordable compared traditional tagging technologies (Zhu et al. 2012). On contrary, RFID
can offer added value for enabling it in large scale adoption in order to manage customer retail
products. The benefits with RFID tags is that these are not based on the line of sight concept as
well as used in times of adverse weather conditions consisting of snow, fog as well as ice.

9RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
At initial times, RFID tags were mainly used in military for tracking of missiles as well
as occasionally in telemetry. After that, for low cost of operation as well as in-expensive devices
availability, these are utilized in daily activities. On the other hand, International Standards
Organization 18000 as well as its sub parametric rules can specify the needs as well as protocols
to be followed in terms of standards (Ruiz et al. 2012). These have sub clauses, which mention
regarding their air interface as well as its usage. In recent days, RFID devices are utilized for
several purposes such as passports, tracking of products, automotive parts detection as well as in
transport systems such as highway toll tags. However, security and privacy issues, commercial
developments along with implementation of RFID are major issues in using the technology.
1.2 Research Aims and Objectives
1.2.1 Aims of the study
The research aims to find new approaches in terms of security as well as sustainability of
RFID technology. At present days, it has been seen that several issues are involved with security
and privacy of mobile devices. As the current industries are facing rapid technological changes,
it becomes necessary to identify the issues and develop a sustainable system that can provide
competitive advantages. Moreover, the aim of the present study is to identify the RFID and
mobile fusion for enabling authenticated transaction in ATMs.
1.2.2 Objectives of the study
The major objective of the present study is to provide an idea regarding security system,
which can be developed through mobile devices for authorized users as well as proposed
methods that can assist to implement RFID technology easily. In, the objectives of the study can
be stated as followed.
At initial times, RFID tags were mainly used in military for tracking of missiles as well
as occasionally in telemetry. After that, for low cost of operation as well as in-expensive devices
availability, these are utilized in daily activities. On the other hand, International Standards
Organization 18000 as well as its sub parametric rules can specify the needs as well as protocols
to be followed in terms of standards (Ruiz et al. 2012). These have sub clauses, which mention
regarding their air interface as well as its usage. In recent days, RFID devices are utilized for
several purposes such as passports, tracking of products, automotive parts detection as well as in
transport systems such as highway toll tags. However, security and privacy issues, commercial
developments along with implementation of RFID are major issues in using the technology.
1.2 Research Aims and Objectives
1.2.1 Aims of the study
The research aims to find new approaches in terms of security as well as sustainability of
RFID technology. At present days, it has been seen that several issues are involved with security
and privacy of mobile devices. As the current industries are facing rapid technological changes,
it becomes necessary to identify the issues and develop a sustainable system that can provide
competitive advantages. Moreover, the aim of the present study is to identify the RFID and
mobile fusion for enabling authenticated transaction in ATMs.
1.2.2 Objectives of the study
The major objective of the present study is to provide an idea regarding security system,
which can be developed through mobile devices for authorized users as well as proposed
methods that can assist to implement RFID technology easily. In, the objectives of the study can
be stated as followed.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
To understand how RFID technology can be used in the online industry
To identify both positive and negative impact of such technology on people
To critically analyze the challenges faced while implementing and using RFID
technology
To recommend solutions in order to overcome the challenges
1.3 Research Questions
The research questions are important to be discussed as it would be helpful through
getting answers of the questions in the particular research. In the present study, the research
questions can be explained as followed.
How RFID technology is used in the online industry?
What are the positive and negative impacts of using RFID technology on people?
What are the challenges faced while deploying and using RFID technology?
How the challenges can be mitigated?
1.4 Problem Statement
The utilization of RFID technology has endangered considerable controversy as well as
product boycotts by consumer privacy advocates. There are two major concerns of using RFID
can be stated as followed.
If a tagged product is paid for by credit card or in conjunction with utilization of
loyalty card, it would be possible to indirectly minimize the identity of the buyer
through reading the unique ID of the item.
On the other hand, there are chances of indirect monitoring by third parties.
To understand how RFID technology can be used in the online industry
To identify both positive and negative impact of such technology on people
To critically analyze the challenges faced while implementing and using RFID
technology
To recommend solutions in order to overcome the challenges
1.3 Research Questions
The research questions are important to be discussed as it would be helpful through
getting answers of the questions in the particular research. In the present study, the research
questions can be explained as followed.
How RFID technology is used in the online industry?
What are the positive and negative impacts of using RFID technology on people?
What are the challenges faced while deploying and using RFID technology?
How the challenges can be mitigated?
1.4 Problem Statement
The utilization of RFID technology has endangered considerable controversy as well as
product boycotts by consumer privacy advocates. There are two major concerns of using RFID
can be stated as followed.
If a tagged product is paid for by credit card or in conjunction with utilization of
loyalty card, it would be possible to indirectly minimize the identity of the buyer
through reading the unique ID of the item.
On the other hand, there are chances of indirect monitoring by third parties.

11RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
The anti-RFID advocacy as well as inquiry and regulations of RFID without any
type of particular regulation law.
Moreover, the basic success of the technology lies in proper comprehension of the
technology as well as other features that can be helpful to mitigate potential issues. Even though,
the technology is existed for several years, the challenges are major concerns for widespread of
RFID technology (Schneider et al. 2012). The security and privacy of RFID against the
unauthorized readers is considered as a great challenge to the privacy of consumers. The
customers utilizing the product with RFID tags can be easily traced. It results high chances in
violating privacy. The consumers utilizing the product with RFID tags can be easily traced. The
RFID tag broadcasts the ID serial number of the EPC to nearby reader. As a result, there is a
high chance of violating privacy. In addition, the size of the dress bought for a woman can be
publicly readable by nearby scanner. In this perspective, Benetton, a cloth retailer has planned to
withdraw the utilization of RFID tags in apparel products. Consumer against Supermarket Policy
Invasion and Numbering group has claimed that RFID tags embedded in the products can track
creating unwanted surveillance of customers and invasion of privacy.
On the other side, in the field clothing and radio frequency identification becomes one of
the most promising technological technologies. It is utilized in manufacturing, warehousing,
logistics, inventory, distribution and automatic object tracking as well as supply chain
management system (Jia et al. 2012). There are several retailers as well as manufacturers like
Tesco, Prada, CVS, Wal-mart and Procter & Gamble are deploying the particular technology as
well as exploring the impact of RFID technology on business. Adoption of the technology may
enhance the potential advantages of supply chain management through minimization of inventor
losses. In addition, it increases efficiency as well as speed of processes and enhancement in
The anti-RFID advocacy as well as inquiry and regulations of RFID without any
type of particular regulation law.
Moreover, the basic success of the technology lies in proper comprehension of the
technology as well as other features that can be helpful to mitigate potential issues. Even though,
the technology is existed for several years, the challenges are major concerns for widespread of
RFID technology (Schneider et al. 2012). The security and privacy of RFID against the
unauthorized readers is considered as a great challenge to the privacy of consumers. The
customers utilizing the product with RFID tags can be easily traced. It results high chances in
violating privacy. The consumers utilizing the product with RFID tags can be easily traced. The
RFID tag broadcasts the ID serial number of the EPC to nearby reader. As a result, there is a
high chance of violating privacy. In addition, the size of the dress bought for a woman can be
publicly readable by nearby scanner. In this perspective, Benetton, a cloth retailer has planned to
withdraw the utilization of RFID tags in apparel products. Consumer against Supermarket Policy
Invasion and Numbering group has claimed that RFID tags embedded in the products can track
creating unwanted surveillance of customers and invasion of privacy.
On the other side, in the field clothing and radio frequency identification becomes one of
the most promising technological technologies. It is utilized in manufacturing, warehousing,
logistics, inventory, distribution and automatic object tracking as well as supply chain
management system (Jia et al. 2012). There are several retailers as well as manufacturers like
Tesco, Prada, CVS, Wal-mart and Procter & Gamble are deploying the particular technology as
well as exploring the impact of RFID technology on business. Adoption of the technology may
enhance the potential advantages of supply chain management through minimization of inventor
losses. In addition, it increases efficiency as well as speed of processes and enhancement in

12RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
information accuracy. Thus, it becomes important to identify the potential challenges and issues
faced while deploying and using RFID technology and properly understand the efficient
procedure of using the technology.
1.5 Rationale of the study
With rapid development of science and technology, radio frequency identification has
been utilized in a number of practical applications like as enhancing supply chain management
system, tracking pets and products, accessing office buildings as well as speeding up the process
of toll collection on roadways (Zhong et al. 2013). Additionally, RFID is generally utilized to
identify people automatically, objects and animals utilizing short range radio frequency for
communicating digital information between a stationary locations (reader) as well as movable
object (tag). RFID technology can also be tracked products in a manner that is similar to the use
of bar codes for identification of products. However, RFID technology carries additional
advantages as it does not need line of sight in order to read the tag. Additionally, it has a longer
read range bar code reader as well as tags that have ability to store more data tan bar codes. The
readers can simultaneously communicate with several tags. The feature could allow the
customers in order to breeze grocery store checkout counters while a reader can identify all items
present in the shopping cart at the same time, whereas bar code do scanning individually. Even
through the use of RFID technology has several advantages, privacy and security issues along
with deployment issues are major challenges for organizations’ owners (Yao et al. 2012). Hence,
it is an issue to identify the issues and challenges lied in the use of RFID technology.
Even though the applications of RFID technology has become more widespread in
current years, there are several issues and challenges are the part of it. The rapid development of
technology has brought a drastic change in online industry. It enables to adopt RFID technology
information accuracy. Thus, it becomes important to identify the potential challenges and issues
faced while deploying and using RFID technology and properly understand the efficient
procedure of using the technology.
1.5 Rationale of the study
With rapid development of science and technology, radio frequency identification has
been utilized in a number of practical applications like as enhancing supply chain management
system, tracking pets and products, accessing office buildings as well as speeding up the process
of toll collection on roadways (Zhong et al. 2013). Additionally, RFID is generally utilized to
identify people automatically, objects and animals utilizing short range radio frequency for
communicating digital information between a stationary locations (reader) as well as movable
object (tag). RFID technology can also be tracked products in a manner that is similar to the use
of bar codes for identification of products. However, RFID technology carries additional
advantages as it does not need line of sight in order to read the tag. Additionally, it has a longer
read range bar code reader as well as tags that have ability to store more data tan bar codes. The
readers can simultaneously communicate with several tags. The feature could allow the
customers in order to breeze grocery store checkout counters while a reader can identify all items
present in the shopping cart at the same time, whereas bar code do scanning individually. Even
through the use of RFID technology has several advantages, privacy and security issues along
with deployment issues are major challenges for organizations’ owners (Yao et al. 2012). Hence,
it is an issue to identify the issues and challenges lied in the use of RFID technology.
Even though the applications of RFID technology has become more widespread in
current years, there are several issues and challenges are the part of it. The rapid development of
technology has brought a drastic change in online industry. It enables to adopt RFID technology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
to make the process faster. However, privacy concerns represent as one of the largest barriers in
order to widespread the process of adoption. Wang and Katabi (2013) stated that implementation
of radio frequency identification technology has various benefits and importance. The main
importance of implementation of RFID technology through which organizations can gain
competitive advantages: Easy Tracking is one of the advantages. RFID technology helps in easy
tracking of the object and unique identification of the objects. The movement and the location of
the object can be easily tracked with the help of RFID technology and thus it reduces the
complexities of the unique identification of any object. In addition, it helps in improvement of
efficiency.
The efficiency of the management and tracking of any object are highly improved with
the help of RFID technology. Increment in Accuracy can be obtained for using RFID in
organizations. The accuracy of the information and the data of RFID tags are highly incremented
or increased (Lehpamer 2012). The accuracy of information is extremely important and this can
be done by RFID technology. Reduction of Costs is one of the benefits for using RFID
technology in the organizations. RFID technology reduces the overall cost by reducing the
complexities of distribution. It also helps to increase in Speed. The speed of any system is
incremented if it has Radio frequency identification technology within it. Thus from the above
mentioned importance, it can be concluded that implementation of RFID technology is extremely
important for any organization. However, security issues and privacy concerns are related to it.
1.6 Structure of the study
The study includes five chapters such as introduction, literature review, research
methodology, findings and analysis along with conclusion and recommendations. Introduction
chapter deals with research aims, objective, problem statement and research rationale through
to make the process faster. However, privacy concerns represent as one of the largest barriers in
order to widespread the process of adoption. Wang and Katabi (2013) stated that implementation
of radio frequency identification technology has various benefits and importance. The main
importance of implementation of RFID technology through which organizations can gain
competitive advantages: Easy Tracking is one of the advantages. RFID technology helps in easy
tracking of the object and unique identification of the objects. The movement and the location of
the object can be easily tracked with the help of RFID technology and thus it reduces the
complexities of the unique identification of any object. In addition, it helps in improvement of
efficiency.
The efficiency of the management and tracking of any object are highly improved with
the help of RFID technology. Increment in Accuracy can be obtained for using RFID in
organizations. The accuracy of the information and the data of RFID tags are highly incremented
or increased (Lehpamer 2012). The accuracy of information is extremely important and this can
be done by RFID technology. Reduction of Costs is one of the benefits for using RFID
technology in the organizations. RFID technology reduces the overall cost by reducing the
complexities of distribution. It also helps to increase in Speed. The speed of any system is
incremented if it has Radio frequency identification technology within it. Thus from the above
mentioned importance, it can be concluded that implementation of RFID technology is extremely
important for any organization. However, security issues and privacy concerns are related to it.
1.6 Structure of the study
The study includes five chapters such as introduction, literature review, research
methodology, findings and analysis along with conclusion and recommendations. Introduction
chapter deals with research aims, objective, problem statement and research rationale through

14RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
which research can be successful. On the other hand, literature review chapter discusses about
the topic from different literatures like books and journals. Research methodology chapter
explains selection of different types of methodological tools in the research. Finding and analysis
chapter discusses data gathered from primary sources. Conclusion and recommendation chapter
ends up with finding and recommendations for overcoming the issues.
which research can be successful. On the other hand, literature review chapter discusses about
the topic from different literatures like books and journals. Research methodology chapter
explains selection of different types of methodological tools in the research. Finding and analysis
chapter discusses data gathered from primary sources. Conclusion and recommendation chapter
ends up with finding and recommendations for overcoming the issues.

15RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Chapter 2: Literature Review
2.1 Preface
In this chapter of research, reviewing literature from different sources such as books,
journals and websites is achieved regarding RFID. Overview of radio frequency identification,
its principle, present applications and benefits are discussed in this chapter of research. In
addition, limitations faced while adopting RFID are also discussed in this chapter of the research.
Data from secondary sources are reviewed and discussed in this chapter of research.
2.2 Overview of Radio Frequency Identification (RFID) technology
Radio frequency identification (RFID) has been utilized as a part of various viable
applications, for example, enhancing supply chain management system, accessing office
buildings and accelerating the process of toll collection on roadways. RFID is utilized to
consequently distinguish individuals, items, and creatures utilizing short range radio technology
to impart advanced data between a stationary area and a movable object (Yang et al. 2014).
RFID technology can be utilized to track items in a way like utilizing bar code for identifying
products. However, RFID likewise conveys extra advantages. RFID does not require line of sight
to read the tag. It has a longer read range compared to bar code reader.
The tags can store more data compared to bar codes. In addition, readers can at the same
time speak with different tags. This functionality could enable clients to easily get through
supermarket checkout counters while a reader distinguishes all things in a shopping basket in the
meantime, rather than scanning bar code individually. RFID tags fall into two classes, active
tags, which contain an interior power source, and passive tags, which get control from the flag of
Chapter 2: Literature Review
2.1 Preface
In this chapter of research, reviewing literature from different sources such as books,
journals and websites is achieved regarding RFID. Overview of radio frequency identification,
its principle, present applications and benefits are discussed in this chapter of research. In
addition, limitations faced while adopting RFID are also discussed in this chapter of the research.
Data from secondary sources are reviewed and discussed in this chapter of research.
2.2 Overview of Radio Frequency Identification (RFID) technology
Radio frequency identification (RFID) has been utilized as a part of various viable
applications, for example, enhancing supply chain management system, accessing office
buildings and accelerating the process of toll collection on roadways. RFID is utilized to
consequently distinguish individuals, items, and creatures utilizing short range radio technology
to impart advanced data between a stationary area and a movable object (Yang et al. 2014).
RFID technology can be utilized to track items in a way like utilizing bar code for identifying
products. However, RFID likewise conveys extra advantages. RFID does not require line of sight
to read the tag. It has a longer read range compared to bar code reader.
The tags can store more data compared to bar codes. In addition, readers can at the same
time speak with different tags. This functionality could enable clients to easily get through
supermarket checkout counters while a reader distinguishes all things in a shopping basket in the
meantime, rather than scanning bar code individually. RFID tags fall into two classes, active
tags, which contain an interior power source, and passive tags, which get control from the flag of
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
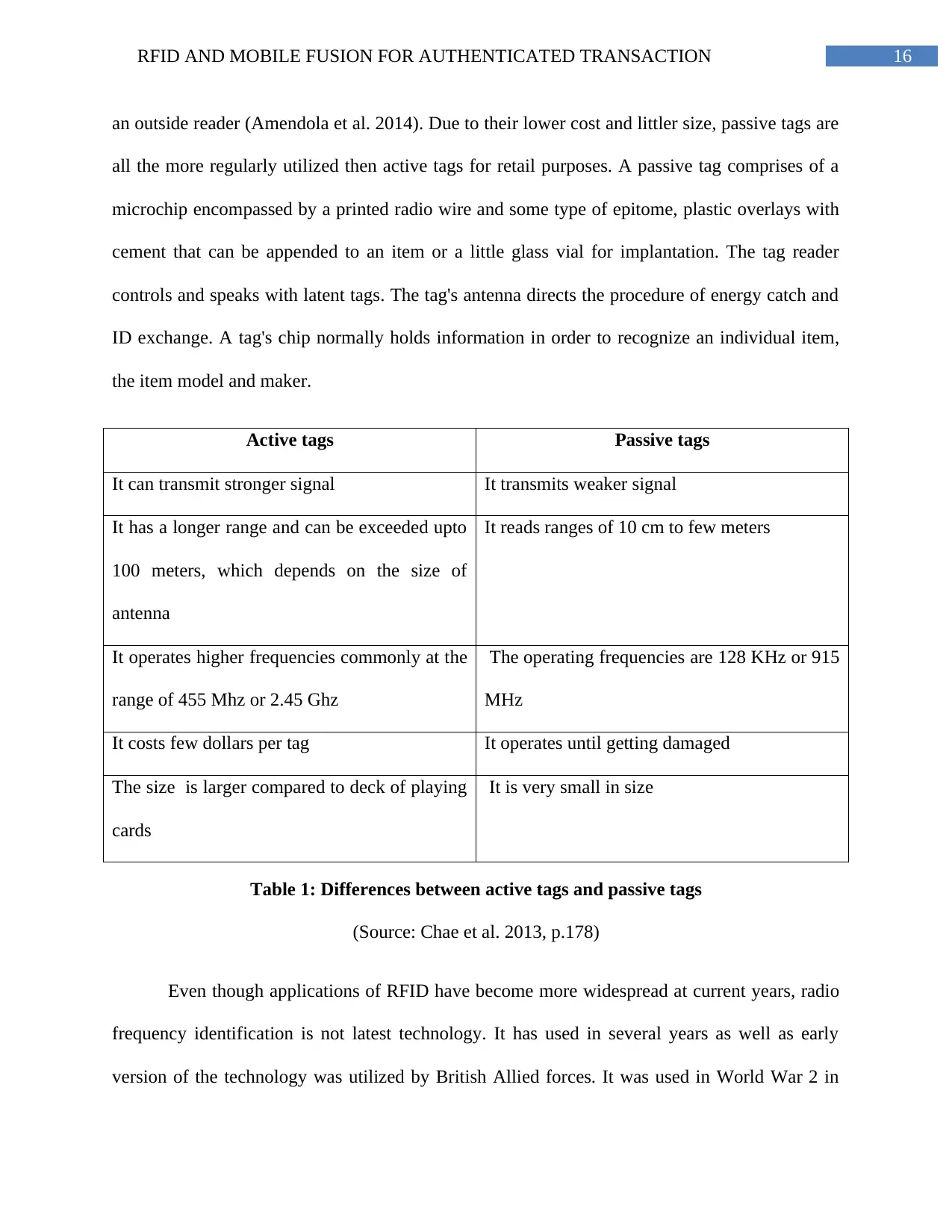
16RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
an outside reader (Amendola et al. 2014). Due to their lower cost and littler size, passive tags are
all the more regularly utilized then active tags for retail purposes. A passive tag comprises of a
microchip encompassed by a printed radio wire and some type of epitome, plastic overlays with
cement that can be appended to an item or a little glass vial for implantation. The tag reader
controls and speaks with latent tags. The tag's antenna directs the procedure of energy catch and
ID exchange. A tag's chip normally holds information in order to recognize an individual item,
the item model and maker.
Active tags Passive tags
It can transmit stronger signal It transmits weaker signal
It has a longer range and can be exceeded upto
100 meters, which depends on the size of
antenna
It reads ranges of 10 cm to few meters
It operates higher frequencies commonly at the
range of 455 Mhz or 2.45 Ghz
The operating frequencies are 128 KHz or 915
MHz
It costs few dollars per tag It operates until getting damaged
The size is larger compared to deck of playing
cards
It is very small in size
Table 1: Differences between active tags and passive tags
(Source: Chae et al. 2013, p.178)
Even though applications of RFID have become more widespread at current years, radio
frequency identification is not latest technology. It has used in several years as well as early
version of the technology was utilized by British Allied forces. It was used in World War 2 in
an outside reader (Amendola et al. 2014). Due to their lower cost and littler size, passive tags are
all the more regularly utilized then active tags for retail purposes. A passive tag comprises of a
microchip encompassed by a printed radio wire and some type of epitome, plastic overlays with
cement that can be appended to an item or a little glass vial for implantation. The tag reader
controls and speaks with latent tags. The tag's antenna directs the procedure of energy catch and
ID exchange. A tag's chip normally holds information in order to recognize an individual item,
the item model and maker.
Active tags Passive tags
It can transmit stronger signal It transmits weaker signal
It has a longer range and can be exceeded upto
100 meters, which depends on the size of
antenna
It reads ranges of 10 cm to few meters
It operates higher frequencies commonly at the
range of 455 Mhz or 2.45 Ghz
The operating frequencies are 128 KHz or 915
MHz
It costs few dollars per tag It operates until getting damaged
The size is larger compared to deck of playing
cards
It is very small in size
Table 1: Differences between active tags and passive tags
(Source: Chae et al. 2013, p.178)
Even though applications of RFID have become more widespread at current years, radio
frequency identification is not latest technology. It has used in several years as well as early
version of the technology was utilized by British Allied forces. It was used in World War 2 in

17RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
order to identify the aircrafts. In addition, it was used for automatic identification for limit access
in order to access in serving purpose of securing areas and make the badges tough to forge.
There are different ranges in which RFID technology has been executed, including the
accompanying critical applications.
• RFID electronic toll collection distinguishes can identify mounted with RFID
transponders and consequently deduct toll charges electronically without hindering movement
stream.
• Animal RFID embed tags have been utilized to distinguish and track creatures and
acquire data about their proprietors (Tian et al. 2012). Joined with GPS, it is conceivable to
perform day and night observation of individual creatures and fish in nature.
• RFID book tracking is considered as an important issue in the library group for use in
overseeing broad accumulations of books, original copies, and uncommon things, and in addition
offering self checkout and assurance against burglary.
• Healthcare providers are thinking about the utilization of RFID technology to enhance
the capacity to precisely distinguish and track patients, doctor's facility staff, restorative
hardware, and blood items (Yang et al. 2013). Various contextual analyses have exhibited that
not exclusively does RFID technology make treatment more secure and more effective, however
it likewise has the side advantages of forestalling data fraud and lessening paper work, both of
which cut expenses. In any case, a recently distributed research examine uncovered that RFID
systems in doctor's facilities may make basic care therapeutic hardware breakdown.
order to identify the aircrafts. In addition, it was used for automatic identification for limit access
in order to access in serving purpose of securing areas and make the badges tough to forge.
There are different ranges in which RFID technology has been executed, including the
accompanying critical applications.
• RFID electronic toll collection distinguishes can identify mounted with RFID
transponders and consequently deduct toll charges electronically without hindering movement
stream.
• Animal RFID embed tags have been utilized to distinguish and track creatures and
acquire data about their proprietors (Tian et al. 2012). Joined with GPS, it is conceivable to
perform day and night observation of individual creatures and fish in nature.
• RFID book tracking is considered as an important issue in the library group for use in
overseeing broad accumulations of books, original copies, and uncommon things, and in addition
offering self checkout and assurance against burglary.
• Healthcare providers are thinking about the utilization of RFID technology to enhance
the capacity to precisely distinguish and track patients, doctor's facility staff, restorative
hardware, and blood items (Yang et al. 2013). Various contextual analyses have exhibited that
not exclusively does RFID technology make treatment more secure and more effective, however
it likewise has the side advantages of forestalling data fraud and lessening paper work, both of
which cut expenses. In any case, a recently distributed research examine uncovered that RFID
systems in doctor's facilities may make basic care therapeutic hardware breakdown.

18RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
• The pharmaceutical business conveys RFID technology to track drugs, lessen stock
cost, and avert duplicating and burglary. The manager for the U.S. Habitats for Medicare and
Medicaid Services, Mark McClellan, called RFID "the most encouraging technology" for
managing drug-falsifying issues.
• Access control has been among the most well-known uses of RFID technology in light
of the fact that RFID identifications give many preferences over conventional access control
identifications, including quick access, toughness without mechanical wear, and a better capacity
than ensure information on the card (Wang et al. 2014). Notwithstanding customary applications,
for example, building access, RFID get to cards have been utilized as a part of less conventional
applications, for example, ski passes, metro passes, and toll entryways.
• The e-travel permit is the up and coming age of international ID, which is outfitted with
an inserted RFID chip to store computerized data and biometric information of the visa holder.
The goal is to give a confided in record to decrease extortion, influence movement to control
quicker, and upgrade the level of security. www.intechopen.com RFID Technology, Security
Vulnerabilities, and Countermeasures
• Supply chains are the greatest recipient of the RFID technology. The utilization of
RFID in supply ties makes it conceivable to give moment stock management, increase visibility
of asset, track shipments, follow reviewed items, and prevent theft (Li et al. 2012). Despite the
fact that RFID technology has been around for the greater part a century, just as of late have
RFID security and protection issues started to pull in consideration from both scholastic and
corporate research groups. Specifically, when managing passive RFID tags, it can be
• The pharmaceutical business conveys RFID technology to track drugs, lessen stock
cost, and avert duplicating and burglary. The manager for the U.S. Habitats for Medicare and
Medicaid Services, Mark McClellan, called RFID "the most encouraging technology" for
managing drug-falsifying issues.
• Access control has been among the most well-known uses of RFID technology in light
of the fact that RFID identifications give many preferences over conventional access control
identifications, including quick access, toughness without mechanical wear, and a better capacity
than ensure information on the card (Wang et al. 2014). Notwithstanding customary applications,
for example, building access, RFID get to cards have been utilized as a part of less conventional
applications, for example, ski passes, metro passes, and toll entryways.
• The e-travel permit is the up and coming age of international ID, which is outfitted with
an inserted RFID chip to store computerized data and biometric information of the visa holder.
The goal is to give a confided in record to decrease extortion, influence movement to control
quicker, and upgrade the level of security. www.intechopen.com RFID Technology, Security
Vulnerabilities, and Countermeasures
• Supply chains are the greatest recipient of the RFID technology. The utilization of
RFID in supply ties makes it conceivable to give moment stock management, increase visibility
of asset, track shipments, follow reviewed items, and prevent theft (Li et al. 2012). Despite the
fact that RFID technology has been around for the greater part a century, just as of late have
RFID security and protection issues started to pull in consideration from both scholastic and
corporate research groups. Specifically, when managing passive RFID tags, it can be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
recommended that there is a need to partition the read scope of a tag into four distinct ranges as
takes after:
• Nominal read range − the standard operating scope of a tag under typical planned utilize
• Rogue scanning range − the read scope of a tag when utilizing a delicate reader outfitted
with a capable reception apparatus or a receiving wire cluster or potentially a higher flag
transmission control
• Tag-to-reader eavesdropping range − the range that another reader can spy tag
emanations without controlling the tag itself, which can even be bigger than the rebel checking
range
• Reader-to-tag listening in run − the range that another reader can catch the flag sent by
the reader to the tag, which is bigger than any of the above ranges.
2.3 Development history of RFID
The first RFID application was developed for "Identification Friend or Foe" system
(IFF). It was used by the British in the Second World War. Transponders were placed into the
fighter planes as well as tanks along with reading units that could query them to decide whether
to attack (Viani et al. 2012). Successors of this technology are still used in armies around the
world. The first commercial RFID application was the "Electronic Article Surveillance" (EAS).
It was developed in the seventies as a theft prevention system. It was based on tags that can store
a single bit. That bit was read when the customer left the store and the system would sound alarm
when the bit was not unset.
recommended that there is a need to partition the read scope of a tag into four distinct ranges as
takes after:
• Nominal read range − the standard operating scope of a tag under typical planned utilize
• Rogue scanning range − the read scope of a tag when utilizing a delicate reader outfitted
with a capable reception apparatus or a receiving wire cluster or potentially a higher flag
transmission control
• Tag-to-reader eavesdropping range − the range that another reader can spy tag
emanations without controlling the tag itself, which can even be bigger than the rebel checking
range
• Reader-to-tag listening in run − the range that another reader can catch the flag sent by
the reader to the tag, which is bigger than any of the above ranges.
2.3 Development history of RFID
The first RFID application was developed for "Identification Friend or Foe" system
(IFF). It was used by the British in the Second World War. Transponders were placed into the
fighter planes as well as tanks along with reading units that could query them to decide whether
to attack (Viani et al. 2012). Successors of this technology are still used in armies around the
world. The first commercial RFID application was the "Electronic Article Surveillance" (EAS).
It was developed in the seventies as a theft prevention system. It was based on tags that can store
a single bit. That bit was read when the customer left the store and the system would sound alarm
when the bit was not unset.

20RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
In the end-seventies RFID tags made its way into the agriculture for example for animal
tagging. In the eighties RFID technology got a boost when Norway and several US states
decided to uses RFID for toll collection on roads. In addition to toll collection the following
decade brought a vast number of new applications, such as ski pass, gasoline cards, money cards,
etc. In 1999 the Auto-ID Center at MIT was founded. Its task was to develop a global standard
for item-level tagging (Sun 2012). The Auto-ID was near in 2003 after completing the work on
the Electronic Product Code (EPC). At the same time the newly founded EPCglobal Inc.
continues the work. The probably first paper related to RFID technology was the landmark paper
by Harry Stockman, "Communication by Means of Reflected Power" in October 1948. On the
other hand, the first patent on RFID was issued in 1973 for a passive radio transponder with
memory.
2.4 Components in RFID used at present days
At present days, the parts RFID tags comprise of, how they work on a principal, and what
sorts of tags do exist. It concentrates on how tags are controlled and what frequency ranges is
utilized (DiGiampaol and Martinelli 2012). The area finishes up by covering a couple of
imperative benchmarks. RFID transponders comprise as a rule of: Micro chip, Antenna, Case
and Battery.
The size of the chip is depended on the Antenna. Its size and frame is reliant on the
frequency the tag is utilizing. The span of a tag likewise relies upon its region of utilization. It
can extend from not as much as a millimeter for inserts to the measure of a book in holder
calculated. Notwithstanding the miniaturized scale chip, a few tags additionally have rewritable
memory appended where the tag can store refreshes between reading cycles or new information
like serial numbers (Zheng and Li 2013). The antenna is plainly unmistakable. As said before the
In the end-seventies RFID tags made its way into the agriculture for example for animal
tagging. In the eighties RFID technology got a boost when Norway and several US states
decided to uses RFID for toll collection on roads. In addition to toll collection the following
decade brought a vast number of new applications, such as ski pass, gasoline cards, money cards,
etc. In 1999 the Auto-ID Center at MIT was founded. Its task was to develop a global standard
for item-level tagging (Sun 2012). The Auto-ID was near in 2003 after completing the work on
the Electronic Product Code (EPC). At the same time the newly founded EPCglobal Inc.
continues the work. The probably first paper related to RFID technology was the landmark paper
by Harry Stockman, "Communication by Means of Reflected Power" in October 1948. On the
other hand, the first patent on RFID was issued in 1973 for a passive radio transponder with
memory.
2.4 Components in RFID used at present days
At present days, the parts RFID tags comprise of, how they work on a principal, and what
sorts of tags do exist. It concentrates on how tags are controlled and what frequency ranges is
utilized (DiGiampaol and Martinelli 2012). The area finishes up by covering a couple of
imperative benchmarks. RFID transponders comprise as a rule of: Micro chip, Antenna, Case
and Battery.
The size of the chip is depended on the Antenna. Its size and frame is reliant on the
frequency the tag is utilizing. The span of a tag likewise relies upon its region of utilization. It
can extend from not as much as a millimeter for inserts to the measure of a book in holder
calculated. Notwithstanding the miniaturized scale chip, a few tags additionally have rewritable
memory appended where the tag can store refreshes between reading cycles or new information
like serial numbers (Zheng and Li 2013). The antenna is plainly unmistakable. As said before the

21RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
radio wire has the biggest effect of the extent of the tag. The microchip is noticeable in the focal
point of the tag, and since this is a detached tag it doesn't have an internal power source.
Figure 1: A passive RFID tag
(Source: Ransford et al. 2012)
On a basic level a RFID tag functions as takes after: the reading unit creates an electro-
magnetic field which prompts a current into the tag's radio wire. The current is utilized to control
the chip. In passive tags the current additionally charges a condenser which ensures continuous
power for the chip. In active tags a battery replaces the condenser. Once activated tags get
general, the reading unit and answers by sending its serial number or the asked for data (Thomas
et al. 2012). All in all the tag does not have enough energy to make its own electro-magnetic
field; rather it utilizes back scrambling to regulate the field sent by the reading unit. Since most
liquids retain electromagnetic fields and most metal mirror those fields the reading of tags in
nearness of those materials is confounded. Amid a reading cycle, the reader needs to ceaselessly
control the tag. The made field is called consistent wave, and in light of the fact that the quality
of the field diminishes with the square of the separation the readers need to utilize a somewhat
vast power (Gong et al. 2012). That field overwhelms any reaction a tag could give, so
consequently tags answer on side-channels which are found straightforwardly underneath or
more the frequency of the persistent wave.
radio wire has the biggest effect of the extent of the tag. The microchip is noticeable in the focal
point of the tag, and since this is a detached tag it doesn't have an internal power source.
Figure 1: A passive RFID tag
(Source: Ransford et al. 2012)
On a basic level a RFID tag functions as takes after: the reading unit creates an electro-
magnetic field which prompts a current into the tag's radio wire. The current is utilized to control
the chip. In passive tags the current additionally charges a condenser which ensures continuous
power for the chip. In active tags a battery replaces the condenser. Once activated tags get
general, the reading unit and answers by sending its serial number or the asked for data (Thomas
et al. 2012). All in all the tag does not have enough energy to make its own electro-magnetic
field; rather it utilizes back scrambling to regulate the field sent by the reading unit. Since most
liquids retain electromagnetic fields and most metal mirror those fields the reading of tags in
nearness of those materials is confounded. Amid a reading cycle, the reader needs to ceaselessly
control the tag. The made field is called consistent wave, and in light of the fact that the quality
of the field diminishes with the square of the separation the readers need to utilize a somewhat
vast power (Gong et al. 2012). That field overwhelms any reaction a tag could give, so
consequently tags answer on side-channels which are found straightforwardly underneath or
more the frequency of the persistent wave.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
2.4.1 Frequency bands
RFID tags can be categorized into three types of frequency range.
Low frequency: It has range from 30KHz to 500kHz
High frequency: It has range from 10KHz to 15MHz
Ultra high frequency: It has range from 850KHz to 950MHz and 2.4HHz -
2.5GHHz as well as 5.8GHz
Low frequency tags are less expensive than any of the higher frequency tags. They are
sufficiently quick for most applications, however for bigger measures of information the time a
tag needs to remain in a readers range will increment. Another preferred standpoint is that low
frequency tags are slightest influenced by the nearness of liquids or metal. The drawback of such
tags is their short perusing range (Shahzad and Liu 2012). The most well-known frequencies
utilized for low frequency tags are 125 KHz to 134.2 kHz as well as 140 KHz to 148.5 kHz.
High frequency tags have higher transmission rates and ranges yet in addition cost more than LF
tags. Savvy tags are the most widely recognized individual from this gathering and they work at
13.56MHz.
Zheng and Li (2012) mentioned that UHF tags have the most noteworthy scope of all
tags. It ranges from 3-6 meters for passive tags and 30+ meters for active tags. Furthermore the
transmission rate is additionally high, which permits to peruse a solitary tag in a brief timeframe.
This element is critical where taged substances are moving with a rapid and stay just for a brief
span in a reader extend. UHF tags are additionally more costly than some other tag and are
seriously influenced by liquids and metal. Those properties make UHF generally valuable in
mechanized toll accumulation systems (Varadhan et al. 2013). Frequencies for LF and HF tags
2.4.1 Frequency bands
RFID tags can be categorized into three types of frequency range.
Low frequency: It has range from 30KHz to 500kHz
High frequency: It has range from 10KHz to 15MHz
Ultra high frequency: It has range from 850KHz to 950MHz and 2.4HHz -
2.5GHHz as well as 5.8GHz
Low frequency tags are less expensive than any of the higher frequency tags. They are
sufficiently quick for most applications, however for bigger measures of information the time a
tag needs to remain in a readers range will increment. Another preferred standpoint is that low
frequency tags are slightest influenced by the nearness of liquids or metal. The drawback of such
tags is their short perusing range (Shahzad and Liu 2012). The most well-known frequencies
utilized for low frequency tags are 125 KHz to 134.2 kHz as well as 140 KHz to 148.5 kHz.
High frequency tags have higher transmission rates and ranges yet in addition cost more than LF
tags. Savvy tags are the most widely recognized individual from this gathering and they work at
13.56MHz.
Zheng and Li (2012) mentioned that UHF tags have the most noteworthy scope of all
tags. It ranges from 3-6 meters for passive tags and 30+ meters for active tags. Furthermore the
transmission rate is additionally high, which permits to peruse a solitary tag in a brief timeframe.
This element is critical where taged substances are moving with a rapid and stay just for a brief
span in a reader extend. UHF tags are additionally more costly than some other tag and are
seriously influenced by liquids and metal. Those properties make UHF generally valuable in
mechanized toll accumulation systems (Varadhan et al. 2013). Frequencies for LF and HF tags

23RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
are permit excluded and can be utilized around the world; however frequencies for UHF tags
vary from nation to nation and require an allow.
2.4.2 Sources of energy
There are 3 types of RFID tags in connection to power sources such as passive, semi-
passive and active. The Passive tags don't have an inward power source, and they thusly depend
on the power actuated by the reader. This implies the reader needs to keep up its field until the
point that the exchange is finished. On account of the absence of a battery, these tags are the
littlest and least expensive tags accessible; be that as it may it additionally confines its perusing
extent to a range in the vicinity of 2 mm and a couple of meters. As an additional advantage
those tags are likewise appropriate to be delivered by printing. Besides their life expectancy is
boundless since they don't rely upon an interior power source.
The second type of tags is semi-passive tags. Those tags have an internal power source
that keeps the small scale chip fueled consistently. There are many preferences: Because the chip
is constantly fueled it can react speedier to demands, accordingly expanding the quantity of tags
that can be questioned every second which is critical to a few applications. Besides, since the
receiving wire isn't required for gathering power it can be advanced for back disseminating and
in this way expanding the perusing range (Potyrailo et al. 2012). The tags of RFID operate at
several frequencies that have ranges from a few kilo hertz to mega hertz as well as in giga hertz.
In addition, secure access application as well as product tracking industry utilizes low
frequencies at the time of tracking vehicle, smart card applications utilize higher frequency
ranges.
are permit excluded and can be utilized around the world; however frequencies for UHF tags
vary from nation to nation and require an allow.
2.4.2 Sources of energy
There are 3 types of RFID tags in connection to power sources such as passive, semi-
passive and active. The Passive tags don't have an inward power source, and they thusly depend
on the power actuated by the reader. This implies the reader needs to keep up its field until the
point that the exchange is finished. On account of the absence of a battery, these tags are the
littlest and least expensive tags accessible; be that as it may it additionally confines its perusing
extent to a range in the vicinity of 2 mm and a couple of meters. As an additional advantage
those tags are likewise appropriate to be delivered by printing. Besides their life expectancy is
boundless since they don't rely upon an interior power source.
The second type of tags is semi-passive tags. Those tags have an internal power source
that keeps the small scale chip fueled consistently. There are many preferences: Because the chip
is constantly fueled it can react speedier to demands, accordingly expanding the quantity of tags
that can be questioned every second which is critical to a few applications. Besides, since the
receiving wire isn't required for gathering power it can be advanced for back disseminating and
in this way expanding the perusing range (Potyrailo et al. 2012). The tags of RFID operate at
several frequencies that have ranges from a few kilo hertz to mega hertz as well as in giga hertz.
In addition, secure access application as well as product tracking industry utilizes low
frequencies at the time of tracking vehicle, smart card applications utilize higher frequency
ranges.

24RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
In addition, in order to wrap things up, since the tag does not utilize any energy from the
field the back scattered flag is more grounded, expanding the range significantly further. Due to
the last two reasons, a semi-active tag has as a rule a range bigger than an passive tag. The third
kind of tags is active tags. Like semi-active tags they contain an inner power source however
they utilize the energy provided for both, to control the small scale chip and to produce a flag on
the reception apparatus (Alomair et al. 2012). Active tags that send signals without being
questioned are called guides. A active tag's range can be several meters, making it perfect for
finding items or filling in as milestone focuses.
2.4.3 Standards
The wide range of possible applications needs several types of tags, conflicting goals. It
is reflected in the standard number. In addition, a short list of RFID standards that follows ISO
11784, ISO 14223, and ISO 18000. In addition, the lists are not exhaustive. RFID technology is
internet associated surprises that there are RFCs are available (Costa et al. 2013). Current hype
around RFID technology results explosion in the patents. There are more than 1800 related
patents as well as over 5700 patents explaining the RFID systems that are backlogged.
2.5 Principles of RFID
There are several types of RFID exist; however at the most top level, RFID devices can
be divided into two classes: active and passive. Active tags require a power source that they are
either associated with a controlled system or utilize energy put away in a coordinated battery. In
the last case, a tag’s lifetime is constrained by the put away energy, adjusted against the quantity
of read operations the gadget must experience (Yoon 2012). One case of an active tag is the
transponder connected to an air ship that distinguishes its national starting point. Detached RFID
is of intrigue in light of the fact that the tags don't require batteries or support. The tags likewise
In addition, in order to wrap things up, since the tag does not utilize any energy from the
field the back scattered flag is more grounded, expanding the range significantly further. Due to
the last two reasons, a semi-active tag has as a rule a range bigger than an passive tag. The third
kind of tags is active tags. Like semi-active tags they contain an inner power source however
they utilize the energy provided for both, to control the small scale chip and to produce a flag on
the reception apparatus (Alomair et al. 2012). Active tags that send signals without being
questioned are called guides. A active tag's range can be several meters, making it perfect for
finding items or filling in as milestone focuses.
2.4.3 Standards
The wide range of possible applications needs several types of tags, conflicting goals. It
is reflected in the standard number. In addition, a short list of RFID standards that follows ISO
11784, ISO 14223, and ISO 18000. In addition, the lists are not exhaustive. RFID technology is
internet associated surprises that there are RFCs are available (Costa et al. 2013). Current hype
around RFID technology results explosion in the patents. There are more than 1800 related
patents as well as over 5700 patents explaining the RFID systems that are backlogged.
2.5 Principles of RFID
There are several types of RFID exist; however at the most top level, RFID devices can
be divided into two classes: active and passive. Active tags require a power source that they are
either associated with a controlled system or utilize energy put away in a coordinated battery. In
the last case, a tag’s lifetime is constrained by the put away energy, adjusted against the quantity
of read operations the gadget must experience (Yoon 2012). One case of an active tag is the
transponder connected to an air ship that distinguishes its national starting point. Detached RFID
is of intrigue in light of the fact that the tags don't require batteries or support. The tags likewise
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
have an uncertain operational life and are sufficiently little to fit into a pragmatic glue mark. An
inactive tag comprises of three sections: a receiving wire, a semi-conductor chip connected to the
radio wire, and some type of epitome. The tag reader is in charge of driving and speaking with a
tag. The tag receiving wire catches energy and exchanges the tag’s ID. The exemplification
keeps up the tag’s respectability and shields the receiving wire and chip from ecological
conditions or reagents. Kitsos (2016) asserted that two in a general sense distinctive RFID
configuration approaches exist for exchanging power from the reader to the tag: attractive
enlistment and electromagnetic (EM) wave catch. These two outlines exploit the EM properties
related with a RF radio wire the near field and the far field. Through different tweak systems,
near and far-field-based signs can likewise transmit and get information.
Near field RFID
Faraday's rule of magnetic induction is the premise of near field coupling between a
reader and tag. A reader passes a vast rotating current through a perusing loop, bringing about an
exchanging attractive field in its area. In the event that you put a tag that joins a littler loop in
this field, a substituting voltage will show up crosswise over it. In the event that this voltage is
corrected and coupled to a capacitor, a repository of charge gathers, which you would then be
able to use to control the tag chip (Wu et al. 2013). Tags are used near field coupling send
information back to the reader utilizing load balance. Since any current drawn from the tag coil
will offer ascent to its own little attractive field, which will restrict the reader's field the reader
loop can identify this as a little increment in current moving through it.
have an uncertain operational life and are sufficiently little to fit into a pragmatic glue mark. An
inactive tag comprises of three sections: a receiving wire, a semi-conductor chip connected to the
radio wire, and some type of epitome. The tag reader is in charge of driving and speaking with a
tag. The tag receiving wire catches energy and exchanges the tag’s ID. The exemplification
keeps up the tag’s respectability and shields the receiving wire and chip from ecological
conditions or reagents. Kitsos (2016) asserted that two in a general sense distinctive RFID
configuration approaches exist for exchanging power from the reader to the tag: attractive
enlistment and electromagnetic (EM) wave catch. These two outlines exploit the EM properties
related with a RF radio wire the near field and the far field. Through different tweak systems,
near and far-field-based signs can likewise transmit and get information.
Near field RFID
Faraday's rule of magnetic induction is the premise of near field coupling between a
reader and tag. A reader passes a vast rotating current through a perusing loop, bringing about an
exchanging attractive field in its area. In the event that you put a tag that joins a littler loop in
this field, a substituting voltage will show up crosswise over it. In the event that this voltage is
corrected and coupled to a capacitor, a repository of charge gathers, which you would then be
able to use to control the tag chip (Wu et al. 2013). Tags are used near field coupling send
information back to the reader utilizing load balance. Since any current drawn from the tag coil
will offer ascent to its own little attractive field, which will restrict the reader's field the reader
loop can identify this as a little increment in current moving through it.

26RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Figure 2: Near filed mechanism of RFID tags
(Source: Wamba 2012, p.644)
This current is relative to the heap connected to the tag’s coil. This is a similar standard
utilized as a part of energy transformers found in many homes today albeit generally a
transformer's essential and optional loop are twisted firmly together to guarantee productive
power exchange. Nonetheless, as the attractive field reaches out past the essential coil, an
auxiliary loop can even now obtain a portion of the energy at a separation, like a reader and a tag
(Rose et al. 2015). The reader would then be able to recuperate this flag by checking the
adjustment in current through the reader coil. An assortment of adjustment encodings are
conceivable relying upon the quantity of ID bits required, the information exchange rate, and
extra excess bits put in the code to expel mistakes coming about because of commotion in the
correspondence channel.
Near field coupling is the clearest approach for actualizing an aloof RFID system. Hence,
as the frequency of operation builds, the separation over which near field coupling can work
diminishes. A further constraint is the energy accessible for acceptance as a component of
Figure 2: Near filed mechanism of RFID tags
(Source: Wamba 2012, p.644)
This current is relative to the heap connected to the tag’s coil. This is a similar standard
utilized as a part of energy transformers found in many homes today albeit generally a
transformer's essential and optional loop are twisted firmly together to guarantee productive
power exchange. Nonetheless, as the attractive field reaches out past the essential coil, an
auxiliary loop can even now obtain a portion of the energy at a separation, like a reader and a tag
(Rose et al. 2015). The reader would then be able to recuperate this flag by checking the
adjustment in current through the reader coil. An assortment of adjustment encodings are
conceivable relying upon the quantity of ID bits required, the information exchange rate, and
extra excess bits put in the code to expel mistakes coming about because of commotion in the
correspondence channel.
Near field coupling is the clearest approach for actualizing an aloof RFID system. Hence,
as the frequency of operation builds, the separation over which near field coupling can work
diminishes. A further constraint is the energy accessible for acceptance as a component of

27RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
separation from the reader coil. In this way, as applications require more ID bits and also
segregation between various tags in a similar region for a settled read time, each tag requires a
higher information rate and in this manner a higher working frequency (Costa et al. 2013). These
outline weights have prompted new aloof RFID plans in light of far-field correspondence.
Far-field RFID
RFID tags in view of far-field emanations catch EM waves proliferating from a dipole
receiving wire joined to the reader. A littler dipole reception apparatus in the tag gets this energy
as an exchanging potential contrast that shows up over the arms of the dipole. A diode can
redress this potential and connection it to a capacitor, which will bring about a gathering of
energy keeping in mind the end goal to control its gadgets (Shirehjini et al. 2012). The strategy
utilized by originators for business far-field RFID tags is back disseminating. However, they
outline a radio wire with exact measurements, it can be tuned to a specific frequency and retain
the vast majority of the energy that achieves it at that frequency.
separation from the reader coil. In this way, as applications require more ID bits and also
segregation between various tags in a similar region for a settled read time, each tag requires a
higher information rate and in this manner a higher working frequency (Costa et al. 2013). These
outline weights have prompted new aloof RFID plans in light of far-field correspondence.
Far-field RFID
RFID tags in view of far-field emanations catch EM waves proliferating from a dipole
receiving wire joined to the reader. A littler dipole reception apparatus in the tag gets this energy
as an exchanging potential contrast that shows up over the arms of the dipole. A diode can
redress this potential and connection it to a capacitor, which will bring about a gathering of
energy keeping in mind the end goal to control its gadgets (Shirehjini et al. 2012). The strategy
utilized by originators for business far-field RFID tags is back disseminating. However, they
outline a radio wire with exact measurements, it can be tuned to a specific frequency and retain
the vast majority of the energy that achieves it at that frequency.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

28RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Figure 3: Far field mechanism of RFID tags
(Source: Shirehjini et al. 2012 p.2142)
On the other hand, if an impedance mismatch happens at this frequency, the receiving
wire will reflect back a portion of the energy toward the reader, which would then be able to
recognize the energy utilizing a delicate radio beneficiary. By changing the receiving wire's
impedance after some time, the tag can reflect back pretty much of the approaching sign in an
example that encodes the ID of tags. DiGiampaolo and Martinelli (2014) commented that
practically speaking, you can detune radio wire of tags for this reason by putting a transistor over
its dipole and after that turning it in part on and off. As a harsh plan direct, tags that utilization
far field standards work at more noteworthy than 100 MHz regularly in the ultra high-frequency
(UHF) band, (for example, 2.45 GHz); underneath this frequency is the space of RFID in view of
near field coupling.
A far-field system's range is restricted by the measure of energy that achieves the tag
from the reader and by how delicate the reader's radio recipient is to the reflected flag. The
genuine return flag is little, since it's the aftereffect of two weakening, each in view of a reverse
square law the principal constriction happens as EM waves transmit from the reader to the tag,
and the second when reflected waves go once more from the tag to the reader. Because of
Moore's law and the contracting highlight size of semiconductor producing, the energy required
to control a tag at a given frequency keeps on diminishing as of now as low as a couple of
microwatts (Chen et al. 2013). In this way, with present day semiconductors, configuration tags
can be read at progressively more prominent separations than were conceivable a couple of years
Figure 3: Far field mechanism of RFID tags
(Source: Shirehjini et al. 2012 p.2142)
On the other hand, if an impedance mismatch happens at this frequency, the receiving
wire will reflect back a portion of the energy toward the reader, which would then be able to
recognize the energy utilizing a delicate radio beneficiary. By changing the receiving wire's
impedance after some time, the tag can reflect back pretty much of the approaching sign in an
example that encodes the ID of tags. DiGiampaolo and Martinelli (2014) commented that
practically speaking, you can detune radio wire of tags for this reason by putting a transistor over
its dipole and after that turning it in part on and off. As a harsh plan direct, tags that utilization
far field standards work at more noteworthy than 100 MHz regularly in the ultra high-frequency
(UHF) band, (for example, 2.45 GHz); underneath this frequency is the space of RFID in view of
near field coupling.
A far-field system's range is restricted by the measure of energy that achieves the tag
from the reader and by how delicate the reader's radio recipient is to the reflected flag. The
genuine return flag is little, since it's the aftereffect of two weakening, each in view of a reverse
square law the principal constriction happens as EM waves transmit from the reader to the tag,
and the second when reflected waves go once more from the tag to the reader. Because of
Moore's law and the contracting highlight size of semiconductor producing, the energy required
to control a tag at a given frequency keeps on diminishing as of now as low as a couple of
microwatts (Chen et al. 2013). In this way, with present day semiconductors, configuration tags
can be read at progressively more prominent separations than were conceivable a couple of years

29RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
back. Moreover, cheap radio beneficiaries have been created with enhanced affectability so they
would now be able to distinguish signals, for a sensible cost.
2.6 Applications of RFID
2.6.1 Supply chain management system
Supply chain management aims to build adequacy and proficiency of whole esteem
included chains. This implies the concentration from dealing with a solitary organization shifts
towards dealing with a heap of various organizations. The test lies in the structure of these chains
framed by the organizations (Wamba et al. 2013). Rather than having single lines with no
communication, each organization has normally a few unique providers and a few distinct
clients, which thusly makes it difficult to recognize the chains and in addition to know who is an
individual from the possess production network.
In light of this essential another technology comes into put which can facilitate the
information trade and give another amount and nature of information with respect to the diverse
levels of the store network. The RFID technology has as its protest decrease or to take out the
arrangement intermittence between genuine things like items from one perspective and
information in IT systems then again. The RFID technology can be viewed as a go between this
present reality and the virtual world. RFID coordinates the "universe of things" in the system
world. Once the foundation is set up, RFID technology accomplishes this combination with
insignificant human mediation. Kapoor and Piramuthu (2012) stated that it is equipped for
altering the system information to fit in with this present reality information at a diminished cost.
Moreover RFID can expand the nature of the information it gathers from this present reality.
back. Moreover, cheap radio beneficiaries have been created with enhanced affectability so they
would now be able to distinguish signals, for a sensible cost.
2.6 Applications of RFID
2.6.1 Supply chain management system
Supply chain management aims to build adequacy and proficiency of whole esteem
included chains. This implies the concentration from dealing with a solitary organization shifts
towards dealing with a heap of various organizations. The test lies in the structure of these chains
framed by the organizations (Wamba et al. 2013). Rather than having single lines with no
communication, each organization has normally a few unique providers and a few distinct
clients, which thusly makes it difficult to recognize the chains and in addition to know who is an
individual from the possess production network.
In light of this essential another technology comes into put which can facilitate the
information trade and give another amount and nature of information with respect to the diverse
levels of the store network. The RFID technology has as its protest decrease or to take out the
arrangement intermittence between genuine things like items from one perspective and
information in IT systems then again. The RFID technology can be viewed as a go between this
present reality and the virtual world. RFID coordinates the "universe of things" in the system
world. Once the foundation is set up, RFID technology accomplishes this combination with
insignificant human mediation. Kapoor and Piramuthu (2012) stated that it is equipped for
altering the system information to fit in with this present reality information at a diminished cost.
Moreover RFID can expand the nature of the information it gathers from this present reality.

30RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Subsequently RFID expands the joining profundity by moving the concentration from e.g. an
item class to the single item or from a period traverse to a specific point in time.
Figure 4: Benefits in supply chain
(Source: Zhong et al. 2015 p.261)
The accessibility of exact continuous information in data systems, which thus permits
ongoing management of procedures, is one further trademark favorable position of RFID
engineering. The two issues, the RFID technology and the production network management, are
about joining despite the fact that they concentrate on various parts of incorporation. The
developing RFID technology can be connected in the additionally very youthful condition of
Subsequently RFID expands the joining profundity by moving the concentration from e.g. an
item class to the single item or from a period traverse to a specific point in time.
Figure 4: Benefits in supply chain
(Source: Zhong et al. 2015 p.261)
The accessibility of exact continuous information in data systems, which thus permits
ongoing management of procedures, is one further trademark favorable position of RFID
engineering. The two issues, the RFID technology and the production network management, are
about joining despite the fact that they concentrate on various parts of incorporation. The
developing RFID technology can be connected in the additionally very youthful condition of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

31RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
store network management. The accompanying passages attempt to analyze the suggestions
between the technology and the management idea (Vena et al. 2012). The utilization of RFID
technology is productive in mechanical divisions. This division needs high process security
because of strict directions in regards to giving proof for data concerning the item. The cost of
the RFID tag keeps its utilization on thing level. Rather it began toward the finish of the 1990s
with the sending of RFID tags in shut strategic cycles on reusable boxes and compartments.
At present days, RFID tags are additionally utilized as a part of open cycles as on
cardboard boxes or beds. RFID names are still excessively costly, making it impossible to apply
them, for example on each and every yogurt in the general store. This will turn out to be most
likely conceivable when RFID chips can be imprinted in large scale manufacturing on polymer-
premise. As of now in 2003 for instance it was first conceivable to print a transistor in large scale
manufacturing (Kim et al. 2012). Regardless of the possibility that it doesn't appear to be
productive yet to send RFID in the retail exchange, retail organizations utilize them on the
foundation of extreme rivalry and with the consciousness of conceivable cost cuttings in
coordination and on representatives in stores and stockrooms. With the mix of the RFID
technology and the inventory network management, new applications advanced.
They can be separated them into issue arranged advancements and technology driven
developments, additionally rang base advancements. Issue situated developments prompt process
changes did in little advances (Liao and Hsiao 2014). A current issue is attempted to be
diminished or fathomed utilizing a higher quality standard while coordinating true information
with system information. These applications are utilized where current applications need to
satisfy the prerequisites .In the territory of store network management these applications are
control errands for instance with respect to logging the receipts of merchandise, keeping an eye
store network management. The accompanying passages attempt to analyze the suggestions
between the technology and the management idea (Vena et al. 2012). The utilization of RFID
technology is productive in mechanical divisions. This division needs high process security
because of strict directions in regards to giving proof for data concerning the item. The cost of
the RFID tag keeps its utilization on thing level. Rather it began toward the finish of the 1990s
with the sending of RFID tags in shut strategic cycles on reusable boxes and compartments.
At present days, RFID tags are additionally utilized as a part of open cycles as on
cardboard boxes or beds. RFID names are still excessively costly, making it impossible to apply
them, for example on each and every yogurt in the general store. This will turn out to be most
likely conceivable when RFID chips can be imprinted in large scale manufacturing on polymer-
premise. As of now in 2003 for instance it was first conceivable to print a transistor in large scale
manufacturing (Kim et al. 2012). Regardless of the possibility that it doesn't appear to be
productive yet to send RFID in the retail exchange, retail organizations utilize them on the
foundation of extreme rivalry and with the consciousness of conceivable cost cuttings in
coordination and on representatives in stores and stockrooms. With the mix of the RFID
technology and the inventory network management, new applications advanced.
They can be separated them into issue arranged advancements and technology driven
developments, additionally rang base advancements. Issue situated developments prompt process
changes did in little advances (Liao and Hsiao 2014). A current issue is attempted to be
diminished or fathomed utilizing a higher quality standard while coordinating true information
with system information. These applications are utilized where current applications need to
satisfy the prerequisites .In the territory of store network management these applications are
control errands for instance with respect to logging the receipts of merchandise, keeping an eye

32RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
on merchandise, item streams, creation control, robbery evasion, harm shirking and falsification
evasion .
2.6.2 Application in fashion industry
In the field of textile and apparel the RFID is utilized as a part of assembling, stock
control, warehousing, logistics, automatic object tracking and supply chain management system.
For instance, the completed articles of clothing, diverse example pieces and embellishments can
be followed and the advance of the creation procedure can be checked. In handling and weaving,
the texture parts can be followed effortlessly. In spinning mills, the bales of cotton and the yarns
can be followed effortlessly (Vena et al. 2013). The blending of various yarn parcels which is a
noteworthy issue in turning plants can be kept away from. A scope of issues exceptional to mold
industry can be comprehended by introducing the RFID system in different procedures engaged
with form store network.
Design industry can be isolated into four segments, for example, fabricating, abroad
transportation, dissemination and retailing. In assembling RFID can be utilized to keep away
from item and part blending, and blending of various accessories. In abroad transportation RFID
can be utilized to track and follow the transfer prior and then afterward Free on Board, if item is
outsourced (Girbau et al. 2012). RFID fundamentally can fathom the issue of arranging and
following the item rapidly, consequently lessening the lead time amid conveyance. In dominant
part of the retail shops, the space is an imperative, which should be utilized effectively. RFID is
utilized to deal with the stock to distinguish the thing rapidly and accurately in order to keep
away from "seek lament", and accordingly help to tackle the issue.
on merchandise, item streams, creation control, robbery evasion, harm shirking and falsification
evasion .
2.6.2 Application in fashion industry
In the field of textile and apparel the RFID is utilized as a part of assembling, stock
control, warehousing, logistics, automatic object tracking and supply chain management system.
For instance, the completed articles of clothing, diverse example pieces and embellishments can
be followed and the advance of the creation procedure can be checked. In handling and weaving,
the texture parts can be followed effortlessly. In spinning mills, the bales of cotton and the yarns
can be followed effortlessly (Vena et al. 2013). The blending of various yarn parcels which is a
noteworthy issue in turning plants can be kept away from. A scope of issues exceptional to mold
industry can be comprehended by introducing the RFID system in different procedures engaged
with form store network.
Design industry can be isolated into four segments, for example, fabricating, abroad
transportation, dissemination and retailing. In assembling RFID can be utilized to keep away
from item and part blending, and blending of various accessories. In abroad transportation RFID
can be utilized to track and follow the transfer prior and then afterward Free on Board, if item is
outsourced (Girbau et al. 2012). RFID fundamentally can fathom the issue of arranging and
following the item rapidly, consequently lessening the lead time amid conveyance. In dominant
part of the retail shops, the space is an imperative, which should be utilized effectively. RFID is
utilized to deal with the stock to distinguish the thing rapidly and accurately in order to keep
away from "seek lament", and accordingly help to tackle the issue.

33RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
2.6.3 Inventory management
The utilization of RFID system aids better stock management and improves client
shopping background. The RFID system can demonstrate the kind of attire offering quicker or
slower, which give altered notice on picked garments as per the RFID tags. The RFID utilize
likewise helps in diminishing work (Nativi and Lee 2012). For instance, American Apparel
connected RFID system in eight of their stores, which spared around 60 to 80 hour for every
week in labor and diminished out-of-stock items attributable to ignorance.
Thus, the Japanese attire maker 'Sankei' is utilizing a RFID system in assembling to track
garments amid the assembling procedure notwithstanding the online deals. An effective
contextual investigation has been led by Kaufhaulf departmental store in Europe on the effect of
RFID on their procedures and production network. They have reasoned that RFID can be utilized
as a part of warehousing to track the merchandise and aid cross docking operation as the
products got are not isolated in the distribution center but rather put away as they are gotten from
the producer (Lim et al. 2013). In the dispersion focus' receivable zone RFID readers can be
executed to track the out of this world in. They got products are enrolled and the information put
away on RFID transponders can be perused for every great however got in beds or individual
mold thing on holder. In this the errand of tallying holders, things and beds can be wiped out and
amount can be controlled up to 100% fulfillment level.
2.6.4 Production control
Inside the stores of the creation office the stock level can be immediately checked which
helps in an ongoing and productive stock management. The area and development of the
segments, semi-completed and the completed items can be recognized by the RFID system,
which helps underway observing and control. The execution of divisions and the people can be
2.6.3 Inventory management
The utilization of RFID system aids better stock management and improves client
shopping background. The RFID system can demonstrate the kind of attire offering quicker or
slower, which give altered notice on picked garments as per the RFID tags. The RFID utilize
likewise helps in diminishing work (Nativi and Lee 2012). For instance, American Apparel
connected RFID system in eight of their stores, which spared around 60 to 80 hour for every
week in labor and diminished out-of-stock items attributable to ignorance.
Thus, the Japanese attire maker 'Sankei' is utilizing a RFID system in assembling to track
garments amid the assembling procedure notwithstanding the online deals. An effective
contextual investigation has been led by Kaufhaulf departmental store in Europe on the effect of
RFID on their procedures and production network. They have reasoned that RFID can be utilized
as a part of warehousing to track the merchandise and aid cross docking operation as the
products got are not isolated in the distribution center but rather put away as they are gotten from
the producer (Lim et al. 2013). In the dispersion focus' receivable zone RFID readers can be
executed to track the out of this world in. They got products are enrolled and the information put
away on RFID transponders can be perused for every great however got in beds or individual
mold thing on holder. In this the errand of tallying holders, things and beds can be wiped out and
amount can be controlled up to 100% fulfillment level.
2.6.4 Production control
Inside the stores of the creation office the stock level can be immediately checked which
helps in an ongoing and productive stock management. The area and development of the
segments, semi-completed and the completed items can be recognized by the RFID system,
which helps underway observing and control. The execution of divisions and the people can be
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

34RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
assessed by the rate of development of the article of clothing segments from the offices or people
(Vena et al. 2012). It helps in enhancing the efficiency and the quality. In the pressing floor the
blending of various styles and sizes can be evaded by RFID tags. Likewise the quantity of pieces
in pressed containers can be checked without opening, which spares the time and work.
2.6.5 Retail management
Park and Lee (2013) stated that it can be utilized as a part of retail to screen and control
the floor level out-of-stocks (OOS). It is for the most part required where there is high item show
thickness, low staffing level and odds of misusing is high. The stock level of the things is
appropriately kept up and the things can be gathered by their request. So, while getting the
merchandise at the store the precision of the conveyances can be guaranteed rapidly with less
work. This can enhance the stock exactness and programmed renewal of stock. Generally the
retailers confirm the exactness and trustworthiness of the shipment by open-box review before
stocking or putting away of products (De Donno 2013). However, now it is conceivable to
peruse every one of the things pressed inside the container without opening, which spares time
and work cost. So the RFID gives another skyline to the retailers in accepting of materials, which
wipes out the receipt debate, blending of various quality items and so forth.
The RFID has been utilized by number of significant retailers in Europe and USA.
Walmart is among the early adopters of RFID all through their store network and the providers
working with Walmart had been under strain to execute RFID in their inventory network
segment too. The reason of actualizing RFID is line with Walmart's corporate system of being
taken a toll intensity and quicker reaction. After effectively usage and utilization of RFID by
Walmart, other enormous retailers like Marks and Spencer and Tesco in UK are receiving it,
Coles amass in Australia have given an idea of grasping this innovation (Ngai et al. 2012). Form
assessed by the rate of development of the article of clothing segments from the offices or people
(Vena et al. 2012). It helps in enhancing the efficiency and the quality. In the pressing floor the
blending of various styles and sizes can be evaded by RFID tags. Likewise the quantity of pieces
in pressed containers can be checked without opening, which spares the time and work.
2.6.5 Retail management
Park and Lee (2013) stated that it can be utilized as a part of retail to screen and control
the floor level out-of-stocks (OOS). It is for the most part required where there is high item show
thickness, low staffing level and odds of misusing is high. The stock level of the things is
appropriately kept up and the things can be gathered by their request. So, while getting the
merchandise at the store the precision of the conveyances can be guaranteed rapidly with less
work. This can enhance the stock exactness and programmed renewal of stock. Generally the
retailers confirm the exactness and trustworthiness of the shipment by open-box review before
stocking or putting away of products (De Donno 2013). However, now it is conceivable to
peruse every one of the things pressed inside the container without opening, which spares time
and work cost. So the RFID gives another skyline to the retailers in accepting of materials, which
wipes out the receipt debate, blending of various quality items and so forth.
The RFID has been utilized by number of significant retailers in Europe and USA.
Walmart is among the early adopters of RFID all through their store network and the providers
working with Walmart had been under strain to execute RFID in their inventory network
segment too. The reason of actualizing RFID is line with Walmart's corporate system of being
taken a toll intensity and quicker reaction. After effectively usage and utilization of RFID by
Walmart, other enormous retailers like Marks and Spencer and Tesco in UK are receiving it,
Coles amass in Australia have given an idea of grasping this innovation (Ngai et al. 2012). Form

35RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
industry is constantly viewed as the late adopter of new innovation than others, however in
embracing RFID it isn't lingering behind. The burglary of articles of clothing from the fitting
room can be anticipated by mounting a little reader at the section purpose of the room. The tag
data of the piece of clothing is caught when the client takes the article of clothing to the fitting
room.
The things that are taken to the fitting room however not turn out are accounted for as
potential misfortune things. Therefore, the RFID can be utilized to recognize the missing stock
and indictment of the shoplifters. Moreover, the disengagement of the garments is consequently
recognized and clients can be given exhortation on the fitting of the garments they are attempting
on (Yu et al. 2012). The later errand can be accomplished by the utilization of smart experiment
with lodges and shrewd mirrors. The savvy mirror can prompt on extra apparel and mold extras.
Organizations, for example, Marks and Spencer, Levi Strauss and Co. are introducing
RFID to secure information on the measure of stocks each day with the goal that the stock can be
recharged. On the other hand, noteworthy distinction was seen between the information got from
the RFID systems and the genuine stock levels. The store stock recuperation and recharging
process by and by utilized is totally manual, unsystematic and incapable. Likewise it requires
quite a while and high work power and some prevalent things are not renewed for a considerable
length of time (Jung and Lee 2012). This can be overwhelmed by RFID innovation. The tags
help to evaluate the stock level every now and again and there is an in-stock position change up
to 30%. This positively affects deals and consumer loyalty. It keeps the design or the regular
stock to lie undetected in the back room and to be sold at critical markdowns consequently
enhancing the overall revenue. Likewise at the purpose of offers the RFID tag can be perused
rapidly and it dodges the physical treatment of the item as in standardized tag system.
industry is constantly viewed as the late adopter of new innovation than others, however in
embracing RFID it isn't lingering behind. The burglary of articles of clothing from the fitting
room can be anticipated by mounting a little reader at the section purpose of the room. The tag
data of the piece of clothing is caught when the client takes the article of clothing to the fitting
room.
The things that are taken to the fitting room however not turn out are accounted for as
potential misfortune things. Therefore, the RFID can be utilized to recognize the missing stock
and indictment of the shoplifters. Moreover, the disengagement of the garments is consequently
recognized and clients can be given exhortation on the fitting of the garments they are attempting
on (Yu et al. 2012). The later errand can be accomplished by the utilization of smart experiment
with lodges and shrewd mirrors. The savvy mirror can prompt on extra apparel and mold extras.
Organizations, for example, Marks and Spencer, Levi Strauss and Co. are introducing
RFID to secure information on the measure of stocks each day with the goal that the stock can be
recharged. On the other hand, noteworthy distinction was seen between the information got from
the RFID systems and the genuine stock levels. The store stock recuperation and recharging
process by and by utilized is totally manual, unsystematic and incapable. Likewise it requires
quite a while and high work power and some prevalent things are not renewed for a considerable
length of time (Jung and Lee 2012). This can be overwhelmed by RFID innovation. The tags
help to evaluate the stock level every now and again and there is an in-stock position change up
to 30%. This positively affects deals and consumer loyalty. It keeps the design or the regular
stock to lie undetected in the back room and to be sold at critical markdowns consequently
enhancing the overall revenue. Likewise at the purpose of offers the RFID tag can be perused
rapidly and it dodges the physical treatment of the item as in standardized tag system.

36RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
The RFID tags can be put along the edge creases or fix or in a paper cartoon mark
without influencing the stylish interest of the article of clothing. The quantity of things sold is
naturally balanced from the measure of stock. Consequently, the clients can be educated about
the status or supply of stock by intuitive show screens (Costin et al. 2012). The utilization of
RFID tags has decreased the out of stock rate of Walmart by 16% and RFID empowered stores
were 63% more successful in renewing out of stocks than control stores.
2.6.6 RFID for brand segregation
It will be very helpful to embrace RFID system for departmental stores, which stocks a
scope of items and brands under one rooftop. The diverse brands can be controlled as far as their
stock and area effectively utilizing RFID though it would be very testing undertaking to isolate
the brands on the off chance that they are blended. RFID likewise lessens the human dependent
as this innovation is slightest human ward when observing the stock level, mark recognizable
proof and item credibility (De Marco et al. 2012). Radio frequency identification can likewise be
utilized to maintain a strategic distance from unlawful item modification to dim market and
expanding item security and to give data about shopping conduct of client at retail. Having every
one of these issues fathomed, material and mold production network can be made more
streamlined and effective regarding expense and execution. RFID utilized as a part of fitting
room Radio frequency recognizable proof innovation is utilized as a part of the fitting room in
another approach by a German departmental store "Galeria Kaufhof in Essen". Programmed
recommendations are given to men purchasing garments in the store when they go to a changing
area to attempt a suit (Tan et al. 2013). A smart mirror advises them what sort of suit or
embellishments will be fitting. A RFID reader on the savvy reflect in the fitting room figures out
which attire has been brought into the room from the RFID tag connected to the clothing. The
The RFID tags can be put along the edge creases or fix or in a paper cartoon mark
without influencing the stylish interest of the article of clothing. The quantity of things sold is
naturally balanced from the measure of stock. Consequently, the clients can be educated about
the status or supply of stock by intuitive show screens (Costin et al. 2012). The utilization of
RFID tags has decreased the out of stock rate of Walmart by 16% and RFID empowered stores
were 63% more successful in renewing out of stocks than control stores.
2.6.6 RFID for brand segregation
It will be very helpful to embrace RFID system for departmental stores, which stocks a
scope of items and brands under one rooftop. The diverse brands can be controlled as far as their
stock and area effectively utilizing RFID though it would be very testing undertaking to isolate
the brands on the off chance that they are blended. RFID likewise lessens the human dependent
as this innovation is slightest human ward when observing the stock level, mark recognizable
proof and item credibility (De Marco et al. 2012). Radio frequency identification can likewise be
utilized to maintain a strategic distance from unlawful item modification to dim market and
expanding item security and to give data about shopping conduct of client at retail. Having every
one of these issues fathomed, material and mold production network can be made more
streamlined and effective regarding expense and execution. RFID utilized as a part of fitting
room Radio frequency recognizable proof innovation is utilized as a part of the fitting room in
another approach by a German departmental store "Galeria Kaufhof in Essen". Programmed
recommendations are given to men purchasing garments in the store when they go to a changing
area to attempt a suit (Tan et al. 2013). A smart mirror advises them what sort of suit or
embellishments will be fitting. A RFID reader on the savvy reflect in the fitting room figures out
which attire has been brought into the room from the RFID tag connected to the clothing. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

37RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
fitting embellishments are then shown on a reasonable interface. This system is utilized as a part
of blend with smart racks, which can read what stock is right now in stock, so clients can be,
indicated different styles and sizes that are accessible.
2.6.7 RFID tags for care labeling
The current care names are printed or woven names putting away constrained. The
electronic marks utilize RFID tags for putting away data electronically on a piece of clothing.
The same RFID tag utilized for containing the item subtle elements at the purpose of offer can't
be utilized for putting away the wash mind directions, because of the protection concerns.
Henceforth, extra tags are required for the wash mind guidelines, which will expand the cost of
the article of clothing (Fabian et al. 2012). Moreover, the buyers require exceptional readers to
extricate the data put away in the RFID tag. Thus, they will incline toward the physical mark
rather than an electronic name.
Besides, the utilization of RFID tags in the piece of clothing, may posture wellbeing
dangers to the customers because of the presentation to radiation. The other concern identified
with the utilization of RFID tag is the electronic waste. A fitting strategy ought to be concocted
to reuse or reuse the RFID tags, on the off chance that they are expelled at the purpose of offer.
Likewise, if clients expel the chip sooner or later, appropriate transfer of the tags is fundamental,
which makes extra stresses the organizations. Additionally, alternate issues identified with RFID
are the absence of institutionalization and high cost.
Institutionalizing the innovation, outline and utilization of the tags can comprehend the
issues identified with absence of institutionalization, though the mechanical improvements can
defeat the cost related issues. Radio frequency recognizable proof tags can be utilized as a part of
fitting embellishments are then shown on a reasonable interface. This system is utilized as a part
of blend with smart racks, which can read what stock is right now in stock, so clients can be,
indicated different styles and sizes that are accessible.
2.6.7 RFID tags for care labeling
The current care names are printed or woven names putting away constrained. The
electronic marks utilize RFID tags for putting away data electronically on a piece of clothing.
The same RFID tag utilized for containing the item subtle elements at the purpose of offer can't
be utilized for putting away the wash mind directions, because of the protection concerns.
Henceforth, extra tags are required for the wash mind guidelines, which will expand the cost of
the article of clothing (Fabian et al. 2012). Moreover, the buyers require exceptional readers to
extricate the data put away in the RFID tag. Thus, they will incline toward the physical mark
rather than an electronic name.
Besides, the utilization of RFID tags in the piece of clothing, may posture wellbeing
dangers to the customers because of the presentation to radiation. The other concern identified
with the utilization of RFID tag is the electronic waste. A fitting strategy ought to be concocted
to reuse or reuse the RFID tags, on the off chance that they are expelled at the purpose of offer.
Likewise, if clients expel the chip sooner or later, appropriate transfer of the tags is fundamental,
which makes extra stresses the organizations. Additionally, alternate issues identified with RFID
are the absence of institutionalization and high cost.
Institutionalizing the innovation, outline and utilization of the tags can comprehend the
issues identified with absence of institutionalization, though the mechanical improvements can
defeat the cost related issues. Radio frequency recognizable proof tags can be utilized as a part of

38RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
mix with the enlisted ID number (RN) system, which is as of now being used in a few spots
including the USA (Zheng and Li 2013). The Federal Trade Commission (FTC) issues the RN,
which can be utilized on the material name rather than the organization name. The utilization of
RN system helps the purchasers to effectively distinguish an organization from the RN utilizing
web. The RN system utilizes less space on the mark and more space is accessible for other care
guidelines. Along these lines, the consolidated utilization of RFID and RN number systems
could additionally profit industry and customers.
On the other hand, the utilization of RFID tags is still in its infancy stage. Thus, it is too
soon to finish up the last state of RFID tag and its effect on purchasers. One of the enterprises
watched advantages to the purchasers by incorporating washing directions in the tag. In
Germany, RFID chips are being utilized as a part of nursing homes to help the medical
attendants in effectively arranging the piece of clothing as indicated by mind guidelines (Kassim
et al. 2012). Thus, there is a potential advantage of RFID tags to the shoppers. In any case, all the
real downsides ought to be overcome to make RFID tags a success.
2.7 Advantages of RFID technology
In spite of the fact that RFID isn't probably going to altogether supplant usually utilized
scanner tags soon, the accompanying preferences propose to moreover applying RFID for
included estimation of identification:
• Tag detection not requiring human intervention lessens business costs and disposes of
human blunders from information accumulation,
• As there are no viewable pathway is required, tag arrangement is less compelled,
• RFID tags have a more drawn out read go than, such as barcodes
mix with the enlisted ID number (RN) system, which is as of now being used in a few spots
including the USA (Zheng and Li 2013). The Federal Trade Commission (FTC) issues the RN,
which can be utilized on the material name rather than the organization name. The utilization of
RN system helps the purchasers to effectively distinguish an organization from the RN utilizing
web. The RN system utilizes less space on the mark and more space is accessible for other care
guidelines. Along these lines, the consolidated utilization of RFID and RN number systems
could additionally profit industry and customers.
On the other hand, the utilization of RFID tags is still in its infancy stage. Thus, it is too
soon to finish up the last state of RFID tag and its effect on purchasers. One of the enterprises
watched advantages to the purchasers by incorporating washing directions in the tag. In
Germany, RFID chips are being utilized as a part of nursing homes to help the medical
attendants in effectively arranging the piece of clothing as indicated by mind guidelines (Kassim
et al. 2012). Thus, there is a potential advantage of RFID tags to the shoppers. In any case, all the
real downsides ought to be overcome to make RFID tags a success.
2.7 Advantages of RFID technology
In spite of the fact that RFID isn't probably going to altogether supplant usually utilized
scanner tags soon, the accompanying preferences propose to moreover applying RFID for
included estimation of identification:
• Tag detection not requiring human intervention lessens business costs and disposes of
human blunders from information accumulation,
• As there are no viewable pathway is required, tag arrangement is less compelled,
• RFID tags have a more drawn out read go than, such as barcodes

39RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
• Tags can have read or write memory ability, while such barcode tags do not
• A RFID tag can store a lot of information also to a unique identifier (Feng et al. 2013),
• Unique identification becomes simpler to actualize with RFID than with standardized
identifications,
• Its capacity to recognize products exclusively instead of blandly.
• Tags are less touchy to antagonistic conditions,
• Many tags can be read properly at the same time,
• RFID labels can be joined with sensors,
• Automatic reading at a few spots decreases time slacks and mistakes in a stock,
• Tags can locally store extra data; such circulated information stockpiling may build
adaptation to internal failure of the whole framework,
• It reduces stock control and provisioning costs,
• It reduces warranty claim costs of processing.
2.8 Privacy and security issues in RFID
Radio frequency identification technology or RFID technology are utilized for tracking
tags in several objects. It reduces the complexities of unique identification and recognition these
objects. These tags consist of the information that is stored and recorded electronically.
However, in spite of having such widespread utilization and application, RFID technology does
have some of the most vulnerable security and privacy threats (Sarkka et al. 2012). These risks
• Tags can have read or write memory ability, while such barcode tags do not
• A RFID tag can store a lot of information also to a unique identifier (Feng et al. 2013),
• Unique identification becomes simpler to actualize with RFID than with standardized
identifications,
• Its capacity to recognize products exclusively instead of blandly.
• Tags are less touchy to antagonistic conditions,
• Many tags can be read properly at the same time,
• RFID labels can be joined with sensors,
• Automatic reading at a few spots decreases time slacks and mistakes in a stock,
• Tags can locally store extra data; such circulated information stockpiling may build
adaptation to internal failure of the whole framework,
• It reduces stock control and provisioning costs,
• It reduces warranty claim costs of processing.
2.8 Privacy and security issues in RFID
Radio frequency identification technology or RFID technology are utilized for tracking
tags in several objects. It reduces the complexities of unique identification and recognition these
objects. These tags consist of the information that is stored and recorded electronically.
However, in spite of having such widespread utilization and application, RFID technology does
have some of the most vulnerable security and privacy threats (Sarkka et al. 2012). These risks
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

40RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
and challenges often turn out to be extremely dangerous for any system. The most vulnerable
privacy and security issues and challenges in RFID technology are as follows:
i) RFID Counterfeiting: RFID Counterfeiting is one of the most significant privacy
issues. The word counterfeit refers to fake or forge. Most of the tags in RFID do not utilize any
encryption algorithm and thus there is a high chance that the data in the tags can be easily
intercepted (Chen et al. 2012). Moreover, the data can even be modified or altered and the tags
can be changed into certain invalid tags. The user will not have any idea about this
counterfeiting. The price of the products can be reduced to lower price. The tag can also be
changed into the tag of another item.
ii) RFID Sniffing: Sniffing is another major privacy issue in the deployment of RFID
technology. The readers of RFID technology sends request to the tags for the identity of an
object. When the reader reads the data of the tag, it is automatically verified with the previously
stored data. However, most of the tags of RFID do not have the approach of making the
difference between a fake and a real user. The intruder utilizes this opportunity and he reads the
tags for his dangerous purposes.
iii) Tracking: The data and the information present in the tags of RFID, helps to track
and locate a particular object easily. The moment a tag is attached with an object, it
automatically enters into the field of the RFID reader (Athalye et al. 2013). The intruder or the
attacker can easily track the location and the movement of the object, even if certain encryption
algorithms are utilized for communication between the readers of RFID and tags of RFID. An
intruder normally utilizes mobile robots for tracking the movement and location of any object.
and challenges often turn out to be extremely dangerous for any system. The most vulnerable
privacy and security issues and challenges in RFID technology are as follows:
i) RFID Counterfeiting: RFID Counterfeiting is one of the most significant privacy
issues. The word counterfeit refers to fake or forge. Most of the tags in RFID do not utilize any
encryption algorithm and thus there is a high chance that the data in the tags can be easily
intercepted (Chen et al. 2012). Moreover, the data can even be modified or altered and the tags
can be changed into certain invalid tags. The user will not have any idea about this
counterfeiting. The price of the products can be reduced to lower price. The tag can also be
changed into the tag of another item.
ii) RFID Sniffing: Sniffing is another major privacy issue in the deployment of RFID
technology. The readers of RFID technology sends request to the tags for the identity of an
object. When the reader reads the data of the tag, it is automatically verified with the previously
stored data. However, most of the tags of RFID do not have the approach of making the
difference between a fake and a real user. The intruder utilizes this opportunity and he reads the
tags for his dangerous purposes.
iii) Tracking: The data and the information present in the tags of RFID, helps to track
and locate a particular object easily. The moment a tag is attached with an object, it
automatically enters into the field of the RFID reader (Athalye et al. 2013). The intruder or the
attacker can easily track the location and the movement of the object, even if certain encryption
algorithms are utilized for communication between the readers of RFID and tags of RFID. An
intruder normally utilizes mobile robots for tracking the movement and location of any object.

41RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
iv) Denial of Service Attacks: Denial of Service attack is again one of the most
significant privacy issues in Radio frequency identification technology. When a particular reader
of RFID requests for the information of a RFID tag, it receives the identification id and compares
between the several and different id that are stored within the server of the database. In this
particular case, the reader of RFID and the backend server are exposed to the denial of service
attacks (He and Zeadally 2015). When these types of attacks occur, the tags of RFID fail in the
verification of the identity of the reader and thus as a result, the entire service of RFID is
interrupted.
v) Spoofing: The spoofing attack is the situation, where the intruder masquerades the tags
of RFID, by simply falsifying the information present in it. The attacker claims himself as the
authorized user and the victim does not have any idea about it. When the attacker gets the
complete access of the system with the credentials that are spoofed, he gets the opportunity to do
all invalid and illegal activities (Lu et al. 2013). These activities include the modification of
RFID id, denying the services and spreading erroneous and malicious code.
vi) Virus: Montaser and Moselhi (2014) commented that virus attacks are another most
important and significant attack in RFID. Virus disrupts or even blocks the communication
between the RFID reader and the database. Moreover, the tags can be easily destroyed and
disclosed in front of the RFID readers.
vii) Physical Attacks: This type of attack occurs when the intruder physically gets all the
tags of RFID and modifies and changes the information of those tags. This particular type of
attack occurs in various and several ways like the intruder, utilizing the probe to read and to
change the data and the information present on the RFID tags (Wu et al. 2013). The radial bands
iv) Denial of Service Attacks: Denial of Service attack is again one of the most
significant privacy issues in Radio frequency identification technology. When a particular reader
of RFID requests for the information of a RFID tag, it receives the identification id and compares
between the several and different id that are stored within the server of the database. In this
particular case, the reader of RFID and the backend server are exposed to the denial of service
attacks (He and Zeadally 2015). When these types of attacks occur, the tags of RFID fail in the
verification of the identity of the reader and thus as a result, the entire service of RFID is
interrupted.
v) Spoofing: The spoofing attack is the situation, where the intruder masquerades the tags
of RFID, by simply falsifying the information present in it. The attacker claims himself as the
authorized user and the victim does not have any idea about it. When the attacker gets the
complete access of the system with the credentials that are spoofed, he gets the opportunity to do
all invalid and illegal activities (Lu et al. 2013). These activities include the modification of
RFID id, denying the services and spreading erroneous and malicious code.
vi) Virus: Montaser and Moselhi (2014) commented that virus attacks are another most
important and significant attack in RFID. Virus disrupts or even blocks the communication
between the RFID reader and the database. Moreover, the tags can be easily destroyed and
disclosed in front of the RFID readers.
vii) Physical Attacks: This type of attack occurs when the intruder physically gets all the
tags of RFID and modifies and changes the information of those tags. This particular type of
attack occurs in various and several ways like the intruder, utilizing the probe to read and to
change the data and the information present on the RFID tags (Wu et al. 2013). The radial bands

42RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
or the X-Ray band destroy the information or the data present in the tags that an intruder utilizes
in the attacks of the RFID system. This particular type of attack in RFID technology is known as
the radiation imprinting. The interference of electromagnet mainly disrupts and intercepts the
communication between the RFID reader and the tags.
viii) Replay Attacks: This type of attacks or privacy issue occurs when the intruder
intercepts the communicating message between the RFID reader and the RFID tags. He usually
records the response of the tag, which is utilized as the response of the request done by the reader
(Catarinucci et al. 2012). The most common example of replay attacks is an intruder, keeping
records of the communication between the proximity card and the access of the card reader. This
is utilized for the accessing the secured facility of any system.
2.9 Summary
From above chapter, it can be summarized that at present days, RFID is rapidly used in
supply chain management system for tracking pallet of items. However, additionally it makes
concerns, most basic protection concern, yet in addition other security related issues. The paper
displayed conceivable situations how security can be traded off by RFID labels yet additionally a
few answers for ensure against it. Since RFID innovation turns out to be increasingly normal,
assaults against the framework itself begin to show up. This chapter recorded the most widely
recognized, beginning from normal sniffing and listening stealthily finished foreswearing of
administration to new RFID infections. The paper additionally demonstrated that there is
something else entirely to RFID than simply supply chain management.
or the X-Ray band destroy the information or the data present in the tags that an intruder utilizes
in the attacks of the RFID system. This particular type of attack in RFID technology is known as
the radiation imprinting. The interference of electromagnet mainly disrupts and intercepts the
communication between the RFID reader and the tags.
viii) Replay Attacks: This type of attacks or privacy issue occurs when the intruder
intercepts the communicating message between the RFID reader and the RFID tags. He usually
records the response of the tag, which is utilized as the response of the request done by the reader
(Catarinucci et al. 2012). The most common example of replay attacks is an intruder, keeping
records of the communication between the proximity card and the access of the card reader. This
is utilized for the accessing the secured facility of any system.
2.9 Summary
From above chapter, it can be summarized that at present days, RFID is rapidly used in
supply chain management system for tracking pallet of items. However, additionally it makes
concerns, most basic protection concern, yet in addition other security related issues. The paper
displayed conceivable situations how security can be traded off by RFID labels yet additionally a
few answers for ensure against it. Since RFID innovation turns out to be increasingly normal,
assaults against the framework itself begin to show up. This chapter recorded the most widely
recognized, beginning from normal sniffing and listening stealthily finished foreswearing of
administration to new RFID infections. The paper additionally demonstrated that there is
something else entirely to RFID than simply supply chain management.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

43RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Chapter 3: Research Methodology
3.1 Preface
The methodology if the research has been discussed in this chapter. The Research
methodology helps in maintaining the study in a proper manner for ensuring success in the
research. The research has followed positivism philosophy with deductive approach. It helps in
describing different types of theories and models related to the research topic in the literature
review. This chapter focuses on the data collection technique and design of the research. The
limitation of the research has been depicted in the chapter that helps in understanding the
challenges faced during the conduction of the study.
3.2 Method Outline
As commented by Flick (2015), research outline is the method that helps in maintaining
the range of the study. It contains purpose of the research, positivism philosophy and deductive
approach. On the other hand, data has been collected for primary sources. The collected data has
been analyzed by using quantitative data analysis. A survey has been done on the 55 system
engineers of different companies. Research methods are the procedures that are used in the
research. They represent to the instruments of the exchange, provide approaches to gather, sort
and dissect data with the goal that you can arrive at a few conclusions. In the event that utilize
the correct kind of techniques for your specific sort of look into, at that point ought to have the
capacity to persuade other individual’s that conclusions have some legitimacy.
3.3 Research Onion
The research Onion is a framework that helps in defining a positive research
methodology in the study. Each layer of the research onion depicts various methods of the
Chapter 3: Research Methodology
3.1 Preface
The methodology if the research has been discussed in this chapter. The Research
methodology helps in maintaining the study in a proper manner for ensuring success in the
research. The research has followed positivism philosophy with deductive approach. It helps in
describing different types of theories and models related to the research topic in the literature
review. This chapter focuses on the data collection technique and design of the research. The
limitation of the research has been depicted in the chapter that helps in understanding the
challenges faced during the conduction of the study.
3.2 Method Outline
As commented by Flick (2015), research outline is the method that helps in maintaining
the range of the study. It contains purpose of the research, positivism philosophy and deductive
approach. On the other hand, data has been collected for primary sources. The collected data has
been analyzed by using quantitative data analysis. A survey has been done on the 55 system
engineers of different companies. Research methods are the procedures that are used in the
research. They represent to the instruments of the exchange, provide approaches to gather, sort
and dissect data with the goal that you can arrive at a few conclusions. In the event that utilize
the correct kind of techniques for your specific sort of look into, at that point ought to have the
capacity to persuade other individual’s that conclusions have some legitimacy.
3.3 Research Onion
The research Onion is a framework that helps in defining a positive research
methodology in the study. Each layer of the research onion depicts various methods of the
44RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
resa4rch methodology. The first layer provides an idea of research philosophies. The second
layer provides approach of the research.
Figure 5: Research onion
(Source: Saunders et al. 2009, pp. 52)
3.4 Research Philosophy
As per Flick (2015), the research philosophy helps in giving the measurements and data
in regards to a specific investigation of research. Research philosophy gives the major
information of the ideas of the research topic. The significant research philosophy is of two sorts
including Ontology and Epistemology. There are philosophical parts of theory including
axiology and phenomenology.
Silverman (2016) argued that the specific theory for research confers from the
epistemology worldview. The exploration reasoning incorporates the positivism, authenticity and
posts positivism. The positivism rationality manages the philosophical parts of the exploration by
resa4rch methodology. The first layer provides an idea of research philosophies. The second
layer provides approach of the research.
Figure 5: Research onion
(Source: Saunders et al. 2009, pp. 52)
3.4 Research Philosophy
As per Flick (2015), the research philosophy helps in giving the measurements and data
in regards to a specific investigation of research. Research philosophy gives the major
information of the ideas of the research topic. The significant research philosophy is of two sorts
including Ontology and Epistemology. There are philosophical parts of theory including
axiology and phenomenology.
Silverman (2016) argued that the specific theory for research confers from the
epistemology worldview. The exploration reasoning incorporates the positivism, authenticity and
posts positivism. The positivism rationality manages the philosophical parts of the exploration by

45RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
using the truth and related theory. Such individuals accept there are general facts that are holding
up to be found. While the individuals who accept there is no reality other than what people make
in their heads are known as 'constructivists' or 'interpretivists'. The term constructivist has risen
as the individuals who utilize this approach what's more, who accept, in connection to inquire
about, that there is no goal reality, however, that the truth is developed by every person. Along
these lines the truth is subjective. Phenomenology is the term given to the exploration approach
of such specialists. Post positivism theory crosschecks any information of research. Post
positivism gives clearness to the exploration think about. As remarked by (Taylor, Bogdan and
DeVault (2015), authenticity manages objectives and destinations of the research consider.
This research has picked the positivism theory. The major challenges in the use of the
RFID have been discussed with the help of the positivism philosophy. Different theories related
to this topic have been discussed in the research.
3.5 Research Approach
The two main types of the research approaches are Deductive and inductive approach.
The deductive approach deals with the analysis of the previous theories on the same topic in the
market. On the other hand, the inductive approach focuses on the new theories and models
regarding the RFID technology. Quantitative research regularly converts into the utilization of
factual examination to make the association between what is known and what can be realized
through research. Gathering and breaking down information utilizing quantitative methodologies
requires a comprehension of the connections among factors utilizing either illustrative or
inferential insights. Engaging insights are utilized to draw derivations about populaces and to
assess the parameters of those populaces. Subjective research is a thorough way to deal with
finding the responses to questions. It includes investing a broad measure of energy in the field,
using the truth and related theory. Such individuals accept there are general facts that are holding
up to be found. While the individuals who accept there is no reality other than what people make
in their heads are known as 'constructivists' or 'interpretivists'. The term constructivist has risen
as the individuals who utilize this approach what's more, who accept, in connection to inquire
about, that there is no goal reality, however, that the truth is developed by every person. Along
these lines the truth is subjective. Phenomenology is the term given to the exploration approach
of such specialists. Post positivism theory crosschecks any information of research. Post
positivism gives clearness to the exploration think about. As remarked by (Taylor, Bogdan and
DeVault (2015), authenticity manages objectives and destinations of the research consider.
This research has picked the positivism theory. The major challenges in the use of the
RFID have been discussed with the help of the positivism philosophy. Different theories related
to this topic have been discussed in the research.
3.5 Research Approach
The two main types of the research approaches are Deductive and inductive approach.
The deductive approach deals with the analysis of the previous theories on the same topic in the
market. On the other hand, the inductive approach focuses on the new theories and models
regarding the RFID technology. Quantitative research regularly converts into the utilization of
factual examination to make the association between what is known and what can be realized
through research. Gathering and breaking down information utilizing quantitative methodologies
requires a comprehension of the connections among factors utilizing either illustrative or
inferential insights. Engaging insights are utilized to draw derivations about populaces and to
assess the parameters of those populaces. Subjective research is a thorough way to deal with
finding the responses to questions. It includes investing a broad measure of energy in the field,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

46RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
working in the regularly mind boggling, time expending procedure of information investigation,
composing long entries, and taking an interest in a type of social also, human science inquire
about that does not have firm rules or particular methodology.
This research has selected the deductive approach. The previous theories and model are
discussed in the literature review that helps in gaining major knowledge aboutissues in the RFID
technology in the business organization in market. In this way, deductive approach have helped
in maintaining proper analysis of the literature review of the research topic in the market.
3.6 Research Design
Various sorts of research design are fitting for the diverse sorts of research ventures. The
decision of which configuration to apply relies upon the idea of the issues postured by the
examination points. Each kind of research design has a scope of research strategies that are
generally used to gather and break down the kind of information that is produced by the research.
There are three sorts of the research design including exploratory, explanatory and descriptive
design. Research configuration gives a precise basic reason that gives an appropriate and the
unmistakable reason for the research (Flick 2015). Different sorts of designs of a research help to
control a researcher by keeping in mind the end goal to bargain the organization with the
destinations of a research. This plan depends on perception as methods for gathering
information. It endeavors to analyze circumstances keeping in mind the end goal to build up
what is the standard, i.e. what can be anticipated to happen again under similar conditions.
'Perception' can take many structures. Contingent upon the sort of data looked for, individuals
can be talked with, surveys dispersed, visual records made, even sounds and smells recorded.
Critical is that the perceptions are composed down or recorded in some route, all together that
working in the regularly mind boggling, time expending procedure of information investigation,
composing long entries, and taking an interest in a type of social also, human science inquire
about that does not have firm rules or particular methodology.
This research has selected the deductive approach. The previous theories and model are
discussed in the literature review that helps in gaining major knowledge aboutissues in the RFID
technology in the business organization in market. In this way, deductive approach have helped
in maintaining proper analysis of the literature review of the research topic in the market.
3.6 Research Design
Various sorts of research design are fitting for the diverse sorts of research ventures. The
decision of which configuration to apply relies upon the idea of the issues postured by the
examination points. Each kind of research design has a scope of research strategies that are
generally used to gather and break down the kind of information that is produced by the research.
There are three sorts of the research design including exploratory, explanatory and descriptive
design. Research configuration gives a precise basic reason that gives an appropriate and the
unmistakable reason for the research (Flick 2015). Different sorts of designs of a research help to
control a researcher by keeping in mind the end goal to bargain the organization with the
destinations of a research. This plan depends on perception as methods for gathering
information. It endeavors to analyze circumstances keeping in mind the end goal to build up
what is the standard, i.e. what can be anticipated to happen again under similar conditions.
'Perception' can take many structures. Contingent upon the sort of data looked for, individuals
can be talked with, surveys dispersed, visual records made, even sounds and smells recorded.
Critical is that the perceptions are composed down or recorded in some route, all together that

47RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
they can be therefore broke down. The scale of the examination is impacted by two central point:
the level of intricacy of the study and the extension or degree of the study.
As remarked by Mackey and Gass (2015), exploratory research configuration is a long
haul procedure of research outline. This outline furnishes a connection with the inductive plan of
the research. Illustrative research helps in interfacing distinctive plans to comprehend the
circumstances and results of specific research. Illustrative research configuration leads entire
research with more investigation and the clarification by putting more detail data of the related
research point. The engaging research design has been taken in this exploration. These help in
investigating the point of the exploration with additional data (Taylor, Bogdan and DeVault
2015). Engaging research reason has given the full and in addition, the correct photo of the
researcher by consolidating included data.
3.7 Research strategy
The research strategy helps in investigating the research issue. As commented by
Saunders (2009), research strategy is a general arrangement that helps scientist in noting the
exploration inquiries efficiently. A viable research strategy contains the clear goals, research
questions, information accumulation assets and different imperatives that influence the
exploration in various routes, for example, get to confinements, time impediments, area and cash
restrictions, moral issue requirements and so forth. A powerful research methodology encourages
the analyst to characterize that why researcher utilizing a specific research technique in order to
direct the researcher think about in a compelling way. Research system is likewise useful for the
analyst to utilize particular information gathering strategies to help the contentions (Saunders
2009). The researcher used to collect data from various sources that help in analyzing the study
of the research. In this case, the researcher has opted for the online survey to collect data and
they can be therefore broke down. The scale of the examination is impacted by two central point:
the level of intricacy of the study and the extension or degree of the study.
As remarked by Mackey and Gass (2015), exploratory research configuration is a long
haul procedure of research outline. This outline furnishes a connection with the inductive plan of
the research. Illustrative research helps in interfacing distinctive plans to comprehend the
circumstances and results of specific research. Illustrative research configuration leads entire
research with more investigation and the clarification by putting more detail data of the related
research point. The engaging research design has been taken in this exploration. These help in
investigating the point of the exploration with additional data (Taylor, Bogdan and DeVault
2015). Engaging research reason has given the full and in addition, the correct photo of the
researcher by consolidating included data.
3.7 Research strategy
The research strategy helps in investigating the research issue. As commented by
Saunders (2009), research strategy is a general arrangement that helps scientist in noting the
exploration inquiries efficiently. A viable research strategy contains the clear goals, research
questions, information accumulation assets and different imperatives that influence the
exploration in various routes, for example, get to confinements, time impediments, area and cash
restrictions, moral issue requirements and so forth. A powerful research methodology encourages
the analyst to characterize that why researcher utilizing a specific research technique in order to
direct the researcher think about in a compelling way. Research system is likewise useful for the
analyst to utilize particular information gathering strategies to help the contentions (Saunders
2009). The researcher used to collect data from various sources that help in analyzing the study
of the research. In this case, the researcher has opted for the online survey to collect data and

48RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
information related to the research topic. There are 15 questionnaires in the online survey and 55
system engineers of different companies have participated in the survey. The answers of the
participants were taken as the data and information for the research.
3.8 Data Collection
The data collection and gathering has been an important element in the context of the
research. Data and information are collected from various sources for the conduction of the study
in an ethical manner. Data information are properly analyzed for obtaining the result and
outcome from the study of the research. There are mainly two sources of data collection
including secondary method and primary method (Frankland et al. 2013). The secondary method
of data collection gathers data from online journals, articles, books, databases and government
reports related to the research topic. On the other hand, primary data collection gathers data from
conducting online surveys, interviews and experiments. Both the primary and secondary data
collection methods are used for gathering data in some researches. In this case, the researcher has
used primary data collection method for data collection (Silverman 2016). Critical is that the
perceptions are composed down or recorded in some route, all together that they can be therefore
broke down. The scale of the examination is impacted by two central points: the level of
intricacy of the study and the extension or degree of the study. Online survey has been conducted
among the system engineers of different companies. The primary data collection method has
helped in collecting data and information for the study of the research.
3.9 Sample Size
The sample size refers to the number of participants participated in the research. In this
case, there are total 65 system engineers taken. However, only 55 employees were selected for
information related to the research topic. There are 15 questionnaires in the online survey and 55
system engineers of different companies have participated in the survey. The answers of the
participants were taken as the data and information for the research.
3.8 Data Collection
The data collection and gathering has been an important element in the context of the
research. Data and information are collected from various sources for the conduction of the study
in an ethical manner. Data information are properly analyzed for obtaining the result and
outcome from the study of the research. There are mainly two sources of data collection
including secondary method and primary method (Frankland et al. 2013). The secondary method
of data collection gathers data from online journals, articles, books, databases and government
reports related to the research topic. On the other hand, primary data collection gathers data from
conducting online surveys, interviews and experiments. Both the primary and secondary data
collection methods are used for gathering data in some researches. In this case, the researcher has
used primary data collection method for data collection (Silverman 2016). Critical is that the
perceptions are composed down or recorded in some route, all together that they can be therefore
broke down. The scale of the examination is impacted by two central points: the level of
intricacy of the study and the extension or degree of the study. Online survey has been conducted
among the system engineers of different companies. The primary data collection method has
helped in collecting data and information for the study of the research.
3.9 Sample Size
The sample size refers to the number of participants participated in the research. In this
case, there are total 65 system engineers taken. However, only 55 employees were selected for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

49RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
participating in the survey. The rest ten employees’ company does not uses RFID technology.
The feedbacks of the participants have taken for gathering data for the study of the research.
3.10 Data Analysis
Data Analysis is the process of analyzing the data information collected from various
sources during the conduction of research. Data Analysis helps in obtaining prior understanding
of the objectives of the research. The data analysis helps in maintaining the success criteria of the
research. The results and outcomes of the research depend upon the analysis of the data and
information. The two types of data analysis are qualitative and quantitative method. The
qualitative data analysis deals with the analysis of the data collected from the secondary sources.
The qualitative data analysis helps in summarizing the data and information gathered from the
secondary sources (Gast and Ledford 2014). The data collected from the online journals, articles
and books are analyzed using this method. On the other hand, quantitative data analysis refers to
the data collected from the primary sources. The data collected from organizing online survey is
analyzed by using the quantitative data analysis. In this case, the quantitative data analysis has
been used for the analysis of the data and information. The data has been properly analyzed by
the quantitative data analysis.
3.11 Accessibility issues
The accessibility issues refer to the challenges faced during the conduction of the
research. The issues can occur during the data collection method. In this case, the researcher has
used primary data collection method. Therefore, there was problem in managing the system
engineers of different companies using RFID. Many companies were nit using the RFID
technology. Therefore, there was a reduction in the number of participation in online survey
(Taylor, S.J., Bogdan, R. and DeVault 2015).The feedbacks of the participants were not properly
participating in the survey. The rest ten employees’ company does not uses RFID technology.
The feedbacks of the participants have taken for gathering data for the study of the research.
3.10 Data Analysis
Data Analysis is the process of analyzing the data information collected from various
sources during the conduction of research. Data Analysis helps in obtaining prior understanding
of the objectives of the research. The data analysis helps in maintaining the success criteria of the
research. The results and outcomes of the research depend upon the analysis of the data and
information. The two types of data analysis are qualitative and quantitative method. The
qualitative data analysis deals with the analysis of the data collected from the secondary sources.
The qualitative data analysis helps in summarizing the data and information gathered from the
secondary sources (Gast and Ledford 2014). The data collected from the online journals, articles
and books are analyzed using this method. On the other hand, quantitative data analysis refers to
the data collected from the primary sources. The data collected from organizing online survey is
analyzed by using the quantitative data analysis. In this case, the quantitative data analysis has
been used for the analysis of the data and information. The data has been properly analyzed by
the quantitative data analysis.
3.11 Accessibility issues
The accessibility issues refer to the challenges faced during the conduction of the
research. The issues can occur during the data collection method. In this case, the researcher has
used primary data collection method. Therefore, there was problem in managing the system
engineers of different companies using RFID. Many companies were nit using the RFID
technology. Therefore, there was a reduction in the number of participation in online survey
(Taylor, S.J., Bogdan, R. and DeVault 2015).The feedbacks of the participants were not properly

50RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
provided that cause loss in the data. The access to the participants was not good. There was
communication and language problem with the participants of the survey. The time provided for
the conduction of the research was short that causes problem in completing the research. There
was a rush in completing research that causes degradation in the quality of outcomes. There was
financial problem in the research. Advanced tools and techniques have not been used in the
research that would cause a difference in results. The researcher has less money to conduct the
survey that causes problems in purchasing different items required in the study of research.
3.12 Ethical Consideration
Ethical consideration is an important element of the research. The conduction of the
research has to be ethical. In this research, all the ethical consideration has been maintained in a
proper way. The participants of the survey are not forced and they can leave the survey at any
time according to their wish. The research has followed various rules under the Data Protection
Act 1998. According to this act, the personal info ration of the participants of the survey has been
kept secret and not disclosed in front of anyone without their permission (Slater, Evans and
Turner 2016).
Therefore, the security of the personal data has been kept in mind that helps in preventing
data loss. RFID innovation has additionally guaranteed to increment the measure of total
information that is gathered. When managing information, particularly the huge sum that RFID
will create, ethical issues about how the information is to be utilized are pervasive. The results of
the research have been kept secret within the participants of the research. The data and
information has not been coursed at any case. The result of the research has been published for
any kind of personal use (Smith 2015). The huge amount of information that will be made using
RFID unquestionably provides reason to feel ambiguous about the capacity of a buyer to
provided that cause loss in the data. The access to the participants was not good. There was
communication and language problem with the participants of the survey. The time provided for
the conduction of the research was short that causes problem in completing the research. There
was a rush in completing research that causes degradation in the quality of outcomes. There was
financial problem in the research. Advanced tools and techniques have not been used in the
research that would cause a difference in results. The researcher has less money to conduct the
survey that causes problems in purchasing different items required in the study of research.
3.12 Ethical Consideration
Ethical consideration is an important element of the research. The conduction of the
research has to be ethical. In this research, all the ethical consideration has been maintained in a
proper way. The participants of the survey are not forced and they can leave the survey at any
time according to their wish. The research has followed various rules under the Data Protection
Act 1998. According to this act, the personal info ration of the participants of the survey has been
kept secret and not disclosed in front of anyone without their permission (Slater, Evans and
Turner 2016).
Therefore, the security of the personal data has been kept in mind that helps in preventing
data loss. RFID innovation has additionally guaranteed to increment the measure of total
information that is gathered. When managing information, particularly the huge sum that RFID
will create, ethical issues about how the information is to be utilized are pervasive. The results of
the research have been kept secret within the participants of the research. The data and
information has not been coursed at any case. The result of the research has been published for
any kind of personal use (Smith 2015). The huge amount of information that will be made using
RFID unquestionably provides reason to feel ambiguous about the capacity of a buyer to

51RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
command how individual information is being utilized. In the business world, direction as to
what should be possible with individual buyer data has dependably involved concern. With the
guarantee of RFID information being an exponential increment in the measure of information
being gathered, new information accumulation necessities and requirements are being explored.
3.13 Gantt chart
(Refer to Appendix)
3.14 Summary
It can be summarized that the use for the proper methodology has helped in maintaining
the success of the research. The research has successfully implemented the data analysis
methods. The research has used positivism philosophy for gaining knowledge from the theories
in the literature review. The research has used quantitative method of data collection. The data
has been collected from organizing survey. The participants of the survey are system engineers
of the different companies. The limitations of the research have been depicted properly. The lack
in time and money has been prevailing in the research that has created issues in the research.
command how individual information is being utilized. In the business world, direction as to
what should be possible with individual buyer data has dependably involved concern. With the
guarantee of RFID information being an exponential increment in the measure of information
being gathered, new information accumulation necessities and requirements are being explored.
3.13 Gantt chart
(Refer to Appendix)
3.14 Summary
It can be summarized that the use for the proper methodology has helped in maintaining
the success of the research. The research has successfully implemented the data analysis
methods. The research has used positivism philosophy for gaining knowledge from the theories
in the literature review. The research has used quantitative method of data collection. The data
has been collected from organizing survey. The participants of the survey are system engineers
of the different companies. The limitations of the research have been depicted properly. The lack
in time and money has been prevailing in the research that has created issues in the research.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
52RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Chapter 4: Results and findings
4.1 Preface
The chapter analysis and findings regarding present innovation of RFID. With the
expanding omnipresence of RFID tags, notwithstanding, security turned into a worry. The paper
plots conceivable threats that can damage one's security and it likewise portrays counter
measures. Survey questionnaire has been formed and quantitative analysis is achieved in this
chapter of research.
4.2 Quantitative analysis
Q1. Does your organization use RFID technology?
Options Responses (%) Respondents Total Number of
respondents
Yes 84.61% 55 65
No 15.39% 10 65
Chapter 4: Results and findings
4.1 Preface
The chapter analysis and findings regarding present innovation of RFID. With the
expanding omnipresence of RFID tags, notwithstanding, security turned into a worry. The paper
plots conceivable threats that can damage one's security and it likewise portrays counter
measures. Survey questionnaire has been formed and quantitative analysis is achieved in this
chapter of research.
4.2 Quantitative analysis
Q1. Does your organization use RFID technology?
Options Responses (%) Respondents Total Number of
respondents
Yes 84.61% 55 65
No 15.39% 10 65

53RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Table 2: Use of RFID technology
Strongly agree Agree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
36.36% 36.36%
Use of RFID technology
Figure 6: Use of RFID technology
Findings and analysis
According to the data obtained in survey, there are 84.61% respondents out of total
number of number respondents’ organization use RFID technology in their organization. On the
other hand, there are 15.39% respondents in the survey have said that their organization does not
use RFID.
There are several advantages of using RFID that are already discussed in literature review
chapter of the research. RFID technology assists in easy tracking of the object as well as unique
detection of the objects. Moreover, it helps to improve efficiency in the operation procedure. On
the other hand, several issues like privacy and security concerns are involved with the use of
RFID technology. Hence, it is important to analyze the role of RFID technology and get its
potential benefits.
Q2. How long your organization has implemented RFID technology?
Table 2: Use of RFID technology
Strongly agree Agree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
36.36% 36.36%
Use of RFID technology
Figure 6: Use of RFID technology
Findings and analysis
According to the data obtained in survey, there are 84.61% respondents out of total
number of number respondents’ organization use RFID technology in their organization. On the
other hand, there are 15.39% respondents in the survey have said that their organization does not
use RFID.
There are several advantages of using RFID that are already discussed in literature review
chapter of the research. RFID technology assists in easy tracking of the object as well as unique
detection of the objects. Moreover, it helps to improve efficiency in the operation procedure. On
the other hand, several issues like privacy and security concerns are involved with the use of
RFID technology. Hence, it is important to analyze the role of RFID technology and get its
potential benefits.
Q2. How long your organization has implemented RFID technology?
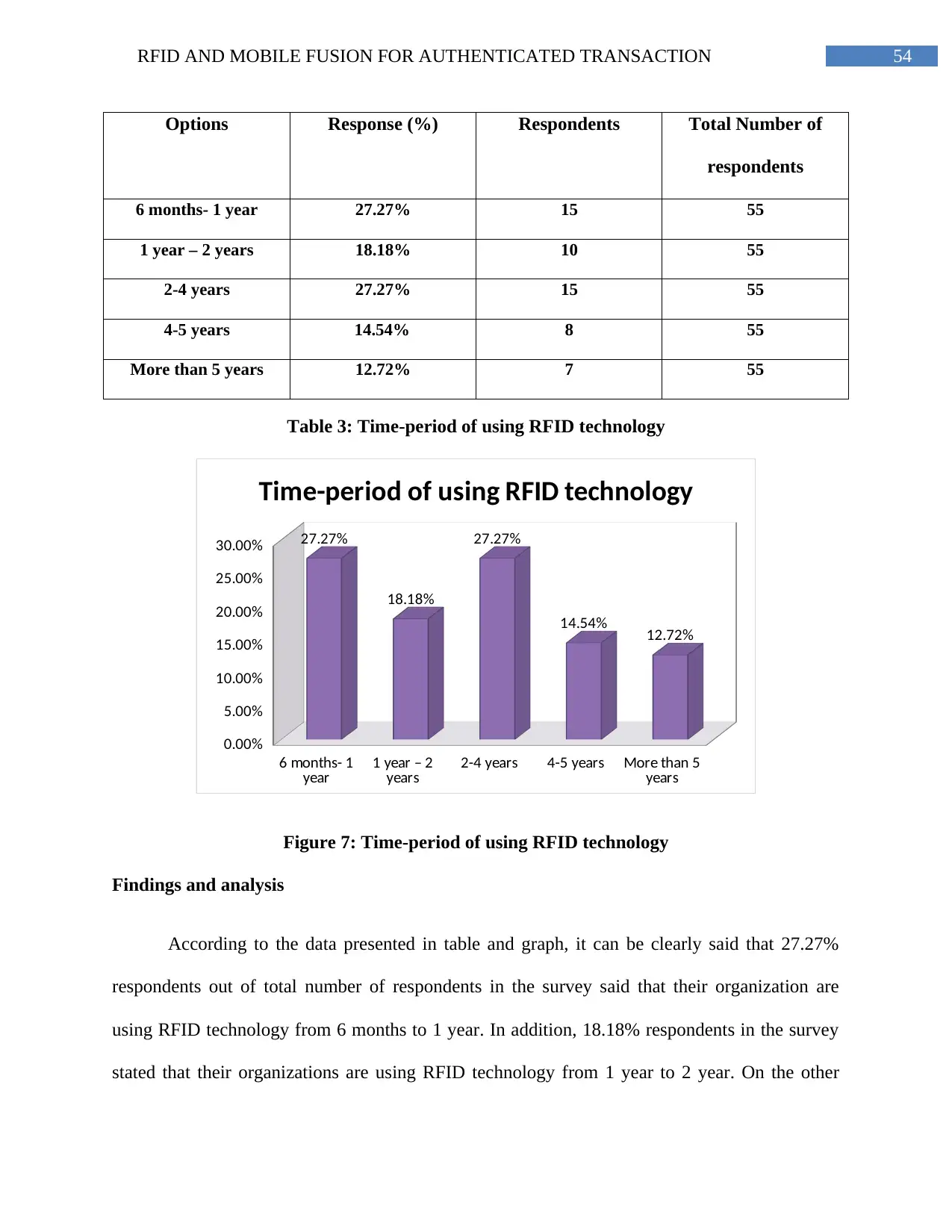
54RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Options Response (%) Respondents Total Number of
respondents
6 months- 1 year 27.27% 15 55
1 year – 2 years 18.18% 10 55
2-4 years 27.27% 15 55
4-5 years 14.54% 8 55
More than 5 years 12.72% 7 55
Table 3: Time-period of using RFID technology
6 months- 1
year 1 year – 2
years 2-4 years 4-5 years More than 5
years
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00% 27.27%
18.18%
27.27%
14.54% 12.72%
Time-period of using RFID technology
Figure 7: Time-period of using RFID technology
Findings and analysis
According to the data presented in table and graph, it can be clearly said that 27.27%
respondents out of total number of respondents in the survey said that their organization are
using RFID technology from 6 months to 1 year. In addition, 18.18% respondents in the survey
stated that their organizations are using RFID technology from 1 year to 2 year. On the other
Options Response (%) Respondents Total Number of
respondents
6 months- 1 year 27.27% 15 55
1 year – 2 years 18.18% 10 55
2-4 years 27.27% 15 55
4-5 years 14.54% 8 55
More than 5 years 12.72% 7 55
Table 3: Time-period of using RFID technology
6 months- 1
year 1 year – 2
years 2-4 years 4-5 years More than 5
years
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00% 27.27%
18.18%
27.27%
14.54% 12.72%
Time-period of using RFID technology
Figure 7: Time-period of using RFID technology
Findings and analysis
According to the data presented in table and graph, it can be clearly said that 27.27%
respondents out of total number of respondents in the survey said that their organization are
using RFID technology from 6 months to 1 year. In addition, 18.18% respondents in the survey
stated that their organizations are using RFID technology from 1 year to 2 year. On the other
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
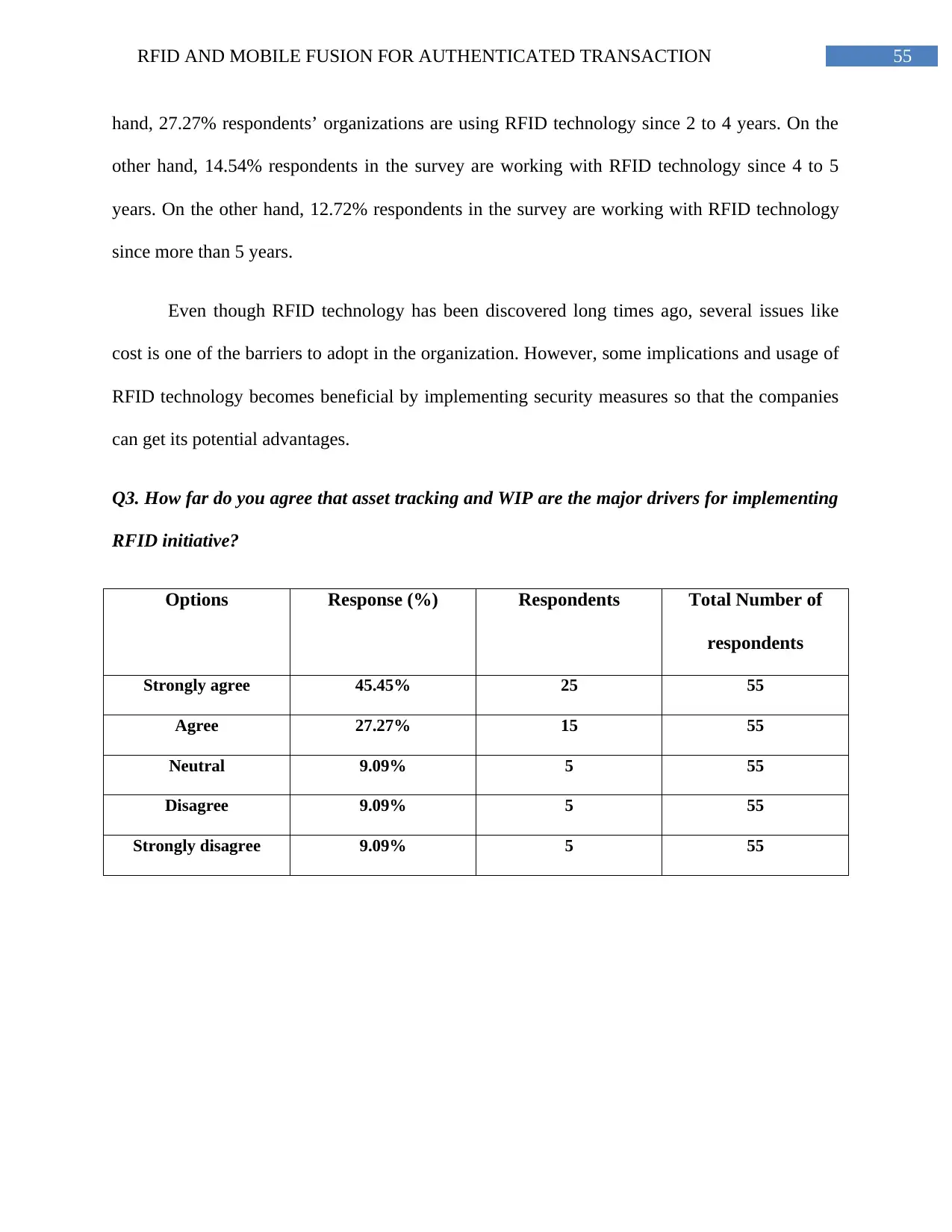
55RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
hand, 27.27% respondents’ organizations are using RFID technology since 2 to 4 years. On the
other hand, 14.54% respondents in the survey are working with RFID technology since 4 to 5
years. On the other hand, 12.72% respondents in the survey are working with RFID technology
since more than 5 years.
Even though RFID technology has been discovered long times ago, several issues like
cost is one of the barriers to adopt in the organization. However, some implications and usage of
RFID technology becomes beneficial by implementing security measures so that the companies
can get its potential advantages.
Q3. How far do you agree that asset tracking and WIP are the major drivers for implementing
RFID initiative?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 45.45% 25 55
Agree 27.27% 15 55
Neutral 9.09% 5 55
Disagree 9.09% 5 55
Strongly disagree 9.09% 5 55
hand, 27.27% respondents’ organizations are using RFID technology since 2 to 4 years. On the
other hand, 14.54% respondents in the survey are working with RFID technology since 4 to 5
years. On the other hand, 12.72% respondents in the survey are working with RFID technology
since more than 5 years.
Even though RFID technology has been discovered long times ago, several issues like
cost is one of the barriers to adopt in the organization. However, some implications and usage of
RFID technology becomes beneficial by implementing security measures so that the companies
can get its potential advantages.
Q3. How far do you agree that asset tracking and WIP are the major drivers for implementing
RFID initiative?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 45.45% 25 55
Agree 27.27% 15 55
Neutral 9.09% 5 55
Disagree 9.09% 5 55
Strongly disagree 9.09% 5 55
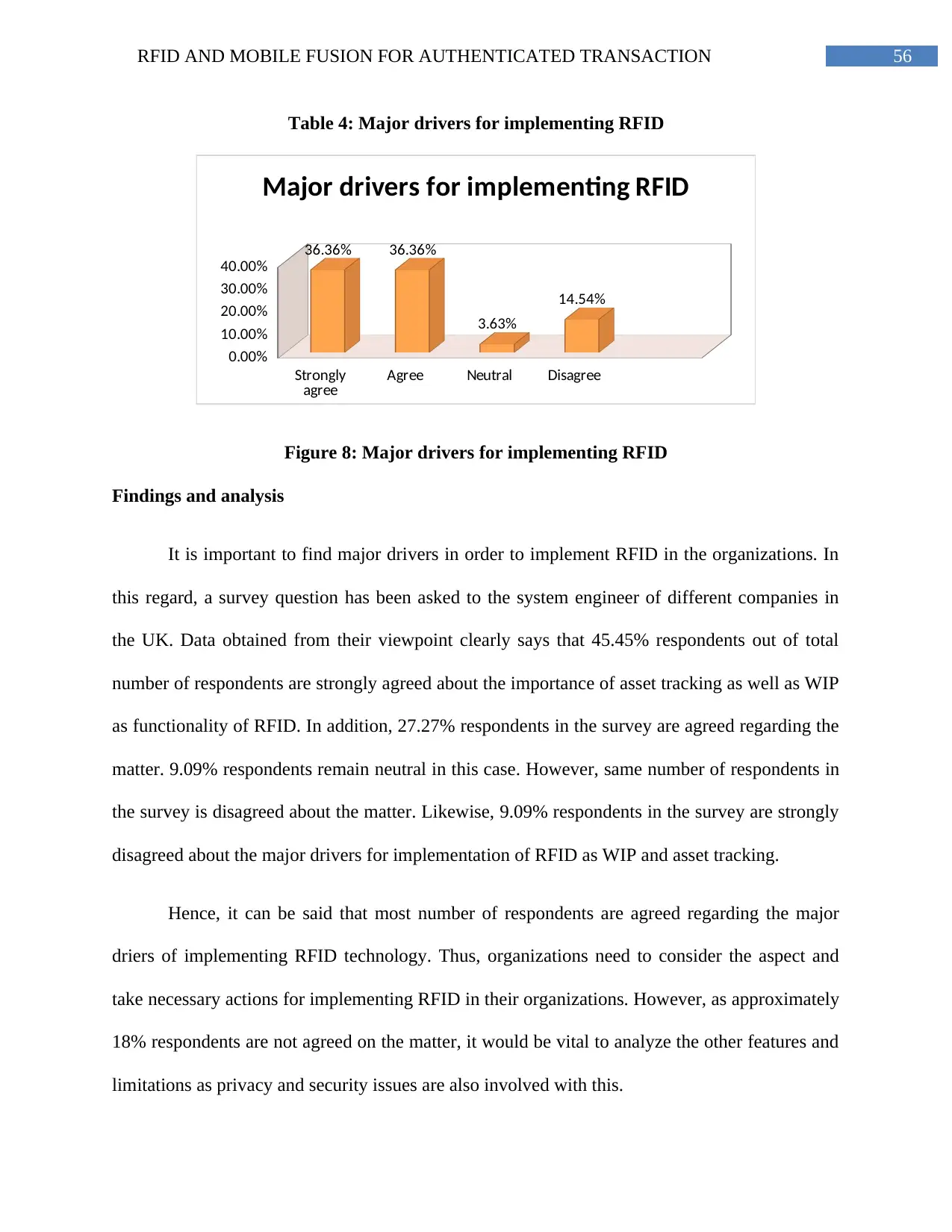
56RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Table 4: Major drivers for implementing RFID
Strongly
agree Agree Neutral Disagree
0.00%
10.00%
20.00%
30.00%
40.00%
36.36% 36.36%
3.63%
14.54%
Major drivers for implementing RFID
Figure 8: Major drivers for implementing RFID
Findings and analysis
It is important to find major drivers in order to implement RFID in the organizations. In
this regard, a survey question has been asked to the system engineer of different companies in
the UK. Data obtained from their viewpoint clearly says that 45.45% respondents out of total
number of respondents are strongly agreed about the importance of asset tracking as well as WIP
as functionality of RFID. In addition, 27.27% respondents in the survey are agreed regarding the
matter. 9.09% respondents remain neutral in this case. However, same number of respondents in
the survey is disagreed about the matter. Likewise, 9.09% respondents in the survey are strongly
disagreed about the major drivers for implementation of RFID as WIP and asset tracking.
Hence, it can be said that most number of respondents are agreed regarding the major
driers of implementing RFID technology. Thus, organizations need to consider the aspect and
take necessary actions for implementing RFID in their organizations. However, as approximately
18% respondents are not agreed on the matter, it would be vital to analyze the other features and
limitations as privacy and security issues are also involved with this.
Table 4: Major drivers for implementing RFID
Strongly
agree Agree Neutral Disagree
0.00%
10.00%
20.00%
30.00%
40.00%
36.36% 36.36%
3.63%
14.54%
Major drivers for implementing RFID
Figure 8: Major drivers for implementing RFID
Findings and analysis
It is important to find major drivers in order to implement RFID in the organizations. In
this regard, a survey question has been asked to the system engineer of different companies in
the UK. Data obtained from their viewpoint clearly says that 45.45% respondents out of total
number of respondents are strongly agreed about the importance of asset tracking as well as WIP
as functionality of RFID. In addition, 27.27% respondents in the survey are agreed regarding the
matter. 9.09% respondents remain neutral in this case. However, same number of respondents in
the survey is disagreed about the matter. Likewise, 9.09% respondents in the survey are strongly
disagreed about the major drivers for implementation of RFID as WIP and asset tracking.
Hence, it can be said that most number of respondents are agreed regarding the major
driers of implementing RFID technology. Thus, organizations need to consider the aspect and
take necessary actions for implementing RFID in their organizations. However, as approximately
18% respondents are not agreed on the matter, it would be vital to analyze the other features and
limitations as privacy and security issues are also involved with this.
57RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Q4. How far you agree that implementation of RFID technology has potential advantages over
bar code scanner?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 36.36% 20 55
Agree 36.36% 20 55
Neutral 3.63% 2 55
Disagree 14.54% 8 55
Strongly disagree 9.09% 5 55
Table 5: Advantages of using RFID technology
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00% 36.36% 36.36%
3.63%
14.54%
9.09%
Advantages of using RFID technology
Figure 9: Advantages of using RFID technology
Findings and analysis
Q4. How far you agree that implementation of RFID technology has potential advantages over
bar code scanner?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 36.36% 20 55
Agree 36.36% 20 55
Neutral 3.63% 2 55
Disagree 14.54% 8 55
Strongly disagree 9.09% 5 55
Table 5: Advantages of using RFID technology
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00% 36.36% 36.36%
3.63%
14.54%
9.09%
Advantages of using RFID technology
Figure 9: Advantages of using RFID technology
Findings and analysis
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
58RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
According to the data obtained from the table and graph, it can be stated that 36.36%
respondents out of total number of respondents are strongly agreed that RFID technology has
potential benefits compared to barcode scanner used in industry, whereas same number of
respondents participated in the survey are agreed about the matter that RFID technology is better
for usage compared to bar code scanner. However, 3.63% respondents are neutral about the
matter.
On the other hand, 14.54% respondents and 9.09% respondents are disagreed and
strongly disagreed about the matter respectively. As discussed in literature review, barcode
scanner can scan items one by one, whereas RFID can do its operations entirely at a time in a
line of sight. Thus, organizations need to consider this advantage for RFID. However, cost issue
is one of the major concerns for adopting RFID technology.
Q5. Which of the following purposes of your organization for implementing RFID system?
Options Response (%) Respondents Total Number of
respondents
Lockable section for
detection
27.27% 15 55
Rewritable section for
specific use
36.36% 20 55
Security functions for
anti-theft
36.36% 20 55
According to the data obtained from the table and graph, it can be stated that 36.36%
respondents out of total number of respondents are strongly agreed that RFID technology has
potential benefits compared to barcode scanner used in industry, whereas same number of
respondents participated in the survey are agreed about the matter that RFID technology is better
for usage compared to bar code scanner. However, 3.63% respondents are neutral about the
matter.
On the other hand, 14.54% respondents and 9.09% respondents are disagreed and
strongly disagreed about the matter respectively. As discussed in literature review, barcode
scanner can scan items one by one, whereas RFID can do its operations entirely at a time in a
line of sight. Thus, organizations need to consider this advantage for RFID. However, cost issue
is one of the major concerns for adopting RFID technology.
Q5. Which of the following purposes of your organization for implementing RFID system?
Options Response (%) Respondents Total Number of
respondents
Lockable section for
detection
27.27% 15 55
Rewritable section for
specific use
36.36% 20 55
Security functions for
anti-theft
36.36% 20 55
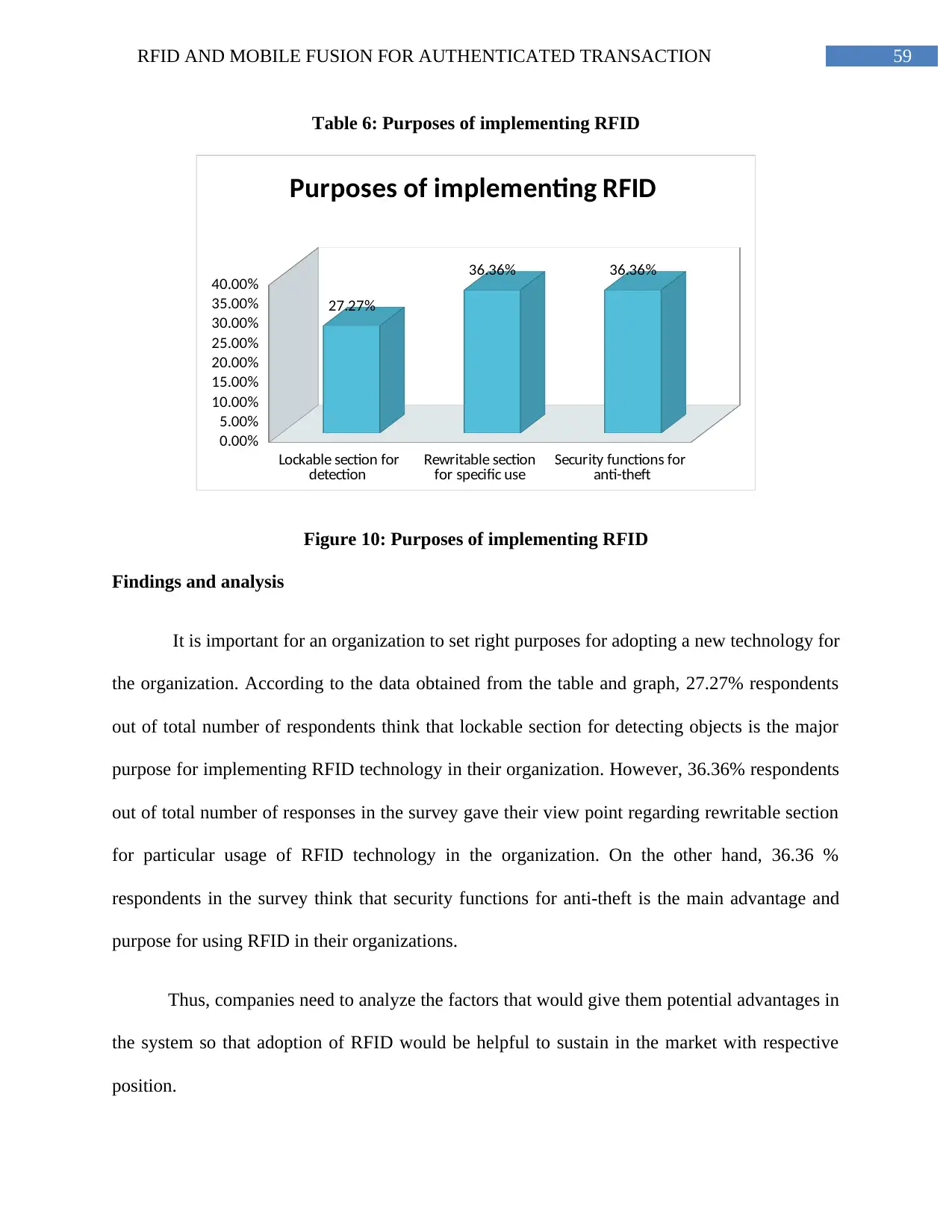
59RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Table 6: Purposes of implementing RFID
Lockable section for
detection Rewritable section
for specific use Security functions for
anti-theft
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
27.27%
36.36% 36.36%
Purposes of implementing RFID
Figure 10: Purposes of implementing RFID
Findings and analysis
It is important for an organization to set right purposes for adopting a new technology for
the organization. According to the data obtained from the table and graph, 27.27% respondents
out of total number of respondents think that lockable section for detecting objects is the major
purpose for implementing RFID technology in their organization. However, 36.36% respondents
out of total number of responses in the survey gave their view point regarding rewritable section
for particular usage of RFID technology in the organization. On the other hand, 36.36 %
respondents in the survey think that security functions for anti-theft is the main advantage and
purpose for using RFID in their organizations.
Thus, companies need to analyze the factors that would give them potential advantages in
the system so that adoption of RFID would be helpful to sustain in the market with respective
position.
Table 6: Purposes of implementing RFID
Lockable section for
detection Rewritable section
for specific use Security functions for
anti-theft
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
27.27%
36.36% 36.36%
Purposes of implementing RFID
Figure 10: Purposes of implementing RFID
Findings and analysis
It is important for an organization to set right purposes for adopting a new technology for
the organization. According to the data obtained from the table and graph, 27.27% respondents
out of total number of respondents think that lockable section for detecting objects is the major
purpose for implementing RFID technology in their organization. However, 36.36% respondents
out of total number of responses in the survey gave their view point regarding rewritable section
for particular usage of RFID technology in the organization. On the other hand, 36.36 %
respondents in the survey think that security functions for anti-theft is the main advantage and
purpose for using RFID in their organizations.
Thus, companies need to analyze the factors that would give them potential advantages in
the system so that adoption of RFID would be helpful to sustain in the market with respective
position.
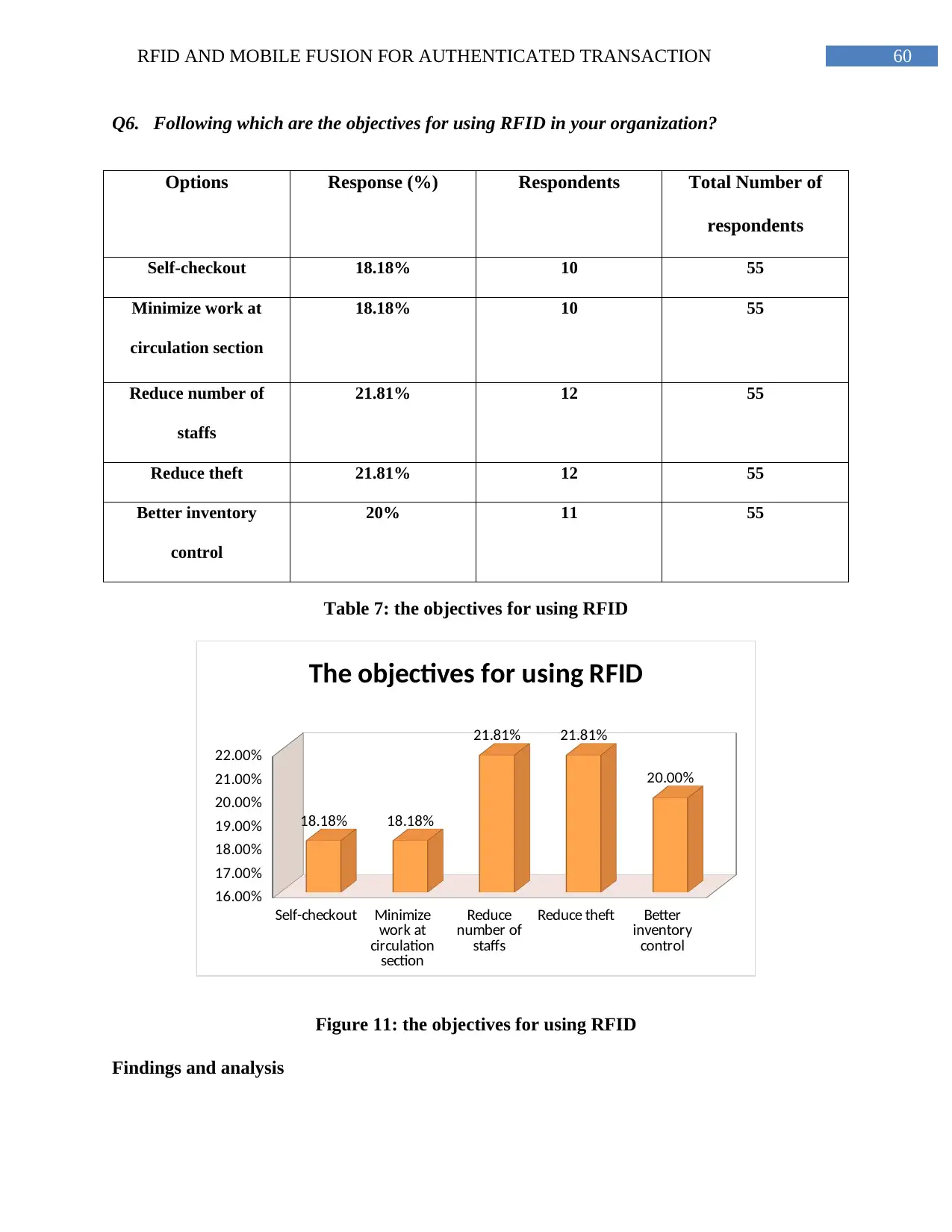
60RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Q6. Following which are the objectives for using RFID in your organization?
Options Response (%) Respondents Total Number of
respondents
Self-checkout 18.18% 10 55
Minimize work at
circulation section
18.18% 10 55
Reduce number of
staffs
21.81% 12 55
Reduce theft 21.81% 12 55
Better inventory
control
20% 11 55
Table 7: the objectives for using RFID
Self-checkout Minimize
work at
circulation
section
Reduce
number of
staffs
Reduce theft Better
inventory
control
16.00%
17.00%
18.00%
19.00%
20.00%
21.00%
22.00%
18.18% 18.18%
21.81% 21.81%
20.00%
The objectives for using RFID
Figure 11: the objectives for using RFID
Findings and analysis
Q6. Following which are the objectives for using RFID in your organization?
Options Response (%) Respondents Total Number of
respondents
Self-checkout 18.18% 10 55
Minimize work at
circulation section
18.18% 10 55
Reduce number of
staffs
21.81% 12 55
Reduce theft 21.81% 12 55
Better inventory
control
20% 11 55
Table 7: the objectives for using RFID
Self-checkout Minimize
work at
circulation
section
Reduce
number of
staffs
Reduce theft Better
inventory
control
16.00%
17.00%
18.00%
19.00%
20.00%
21.00%
22.00%
18.18% 18.18%
21.81% 21.81%
20.00%
The objectives for using RFID
Figure 11: the objectives for using RFID
Findings and analysis
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
61RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
According to the data presented in table, it states that 18.18% respondents out of total
number of respondents in the survey said that self-checkout is the functionality for which
companies have adopted RFID in the organization. However, 18.18% respondents in the survey
think that adoption of RFID technology would assist to minimize work at circulation section.
Moreover, 21.81% respondents in the survey think that it would be helpful to reduce number of
staffs in the organization. Approximately 21.81% respondents in the survey think that use of
RFID is helpful to reduce theft in the organization. There are 20% respondents in the survey
think that RFID is helpful to do better inventory control.
As organizations need to focus on minimizing staffs in order to lessen additional profit,
RFID usage can be helpful to achieve the goal. On the other hand, reducing theft is one of the
major advantages for implementing RFID in the organization; they would get this potential
benefit.
Q7. How far you agree that tracking products accurately is the main advantage for using
RFID technology?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 45.45% 25 55
Agree 36.36% 20 55
Neutral 3.63% 2 55
Disagree 5.45% 3 55
Strongly disagree 9.09% 5 55
According to the data presented in table, it states that 18.18% respondents out of total
number of respondents in the survey said that self-checkout is the functionality for which
companies have adopted RFID in the organization. However, 18.18% respondents in the survey
think that adoption of RFID technology would assist to minimize work at circulation section.
Moreover, 21.81% respondents in the survey think that it would be helpful to reduce number of
staffs in the organization. Approximately 21.81% respondents in the survey think that use of
RFID is helpful to reduce theft in the organization. There are 20% respondents in the survey
think that RFID is helpful to do better inventory control.
As organizations need to focus on minimizing staffs in order to lessen additional profit,
RFID usage can be helpful to achieve the goal. On the other hand, reducing theft is one of the
major advantages for implementing RFID in the organization; they would get this potential
benefit.
Q7. How far you agree that tracking products accurately is the main advantage for using
RFID technology?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 45.45% 25 55
Agree 36.36% 20 55
Neutral 3.63% 2 55
Disagree 5.45% 3 55
Strongly disagree 9.09% 5 55
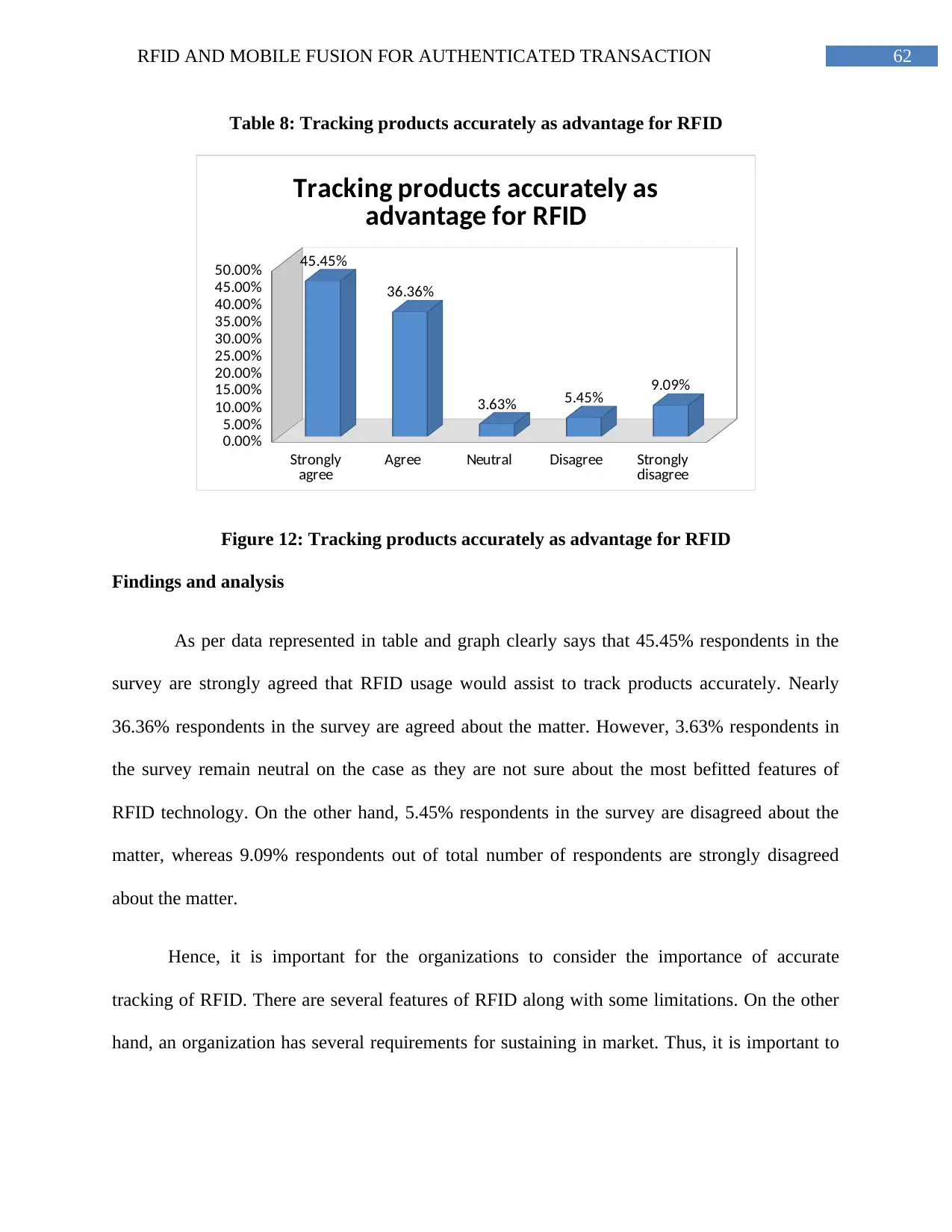
62RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Table 8: Tracking products accurately as advantage for RFID
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
45.00%
50.00% 45.45%
36.36%
3.63% 5.45% 9.09%
Tracking products accurately as
advantage for RFID
Figure 12: Tracking products accurately as advantage for RFID
Findings and analysis
As per data represented in table and graph clearly says that 45.45% respondents in the
survey are strongly agreed that RFID usage would assist to track products accurately. Nearly
36.36% respondents in the survey are agreed about the matter. However, 3.63% respondents in
the survey remain neutral on the case as they are not sure about the most befitted features of
RFID technology. On the other hand, 5.45% respondents in the survey are disagreed about the
matter, whereas 9.09% respondents out of total number of respondents are strongly disagreed
about the matter.
Hence, it is important for the organizations to consider the importance of accurate
tracking of RFID. There are several features of RFID along with some limitations. On the other
hand, an organization has several requirements for sustaining in market. Thus, it is important to
Table 8: Tracking products accurately as advantage for RFID
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
45.00%
50.00% 45.45%
36.36%
3.63% 5.45% 9.09%
Tracking products accurately as
advantage for RFID
Figure 12: Tracking products accurately as advantage for RFID
Findings and analysis
As per data represented in table and graph clearly says that 45.45% respondents in the
survey are strongly agreed that RFID usage would assist to track products accurately. Nearly
36.36% respondents in the survey are agreed about the matter. However, 3.63% respondents in
the survey remain neutral on the case as they are not sure about the most befitted features of
RFID technology. On the other hand, 5.45% respondents in the survey are disagreed about the
matter, whereas 9.09% respondents out of total number of respondents are strongly disagreed
about the matter.
Hence, it is important for the organizations to consider the importance of accurate
tracking of RFID. There are several features of RFID along with some limitations. On the other
hand, an organization has several requirements for sustaining in market. Thus, it is important to
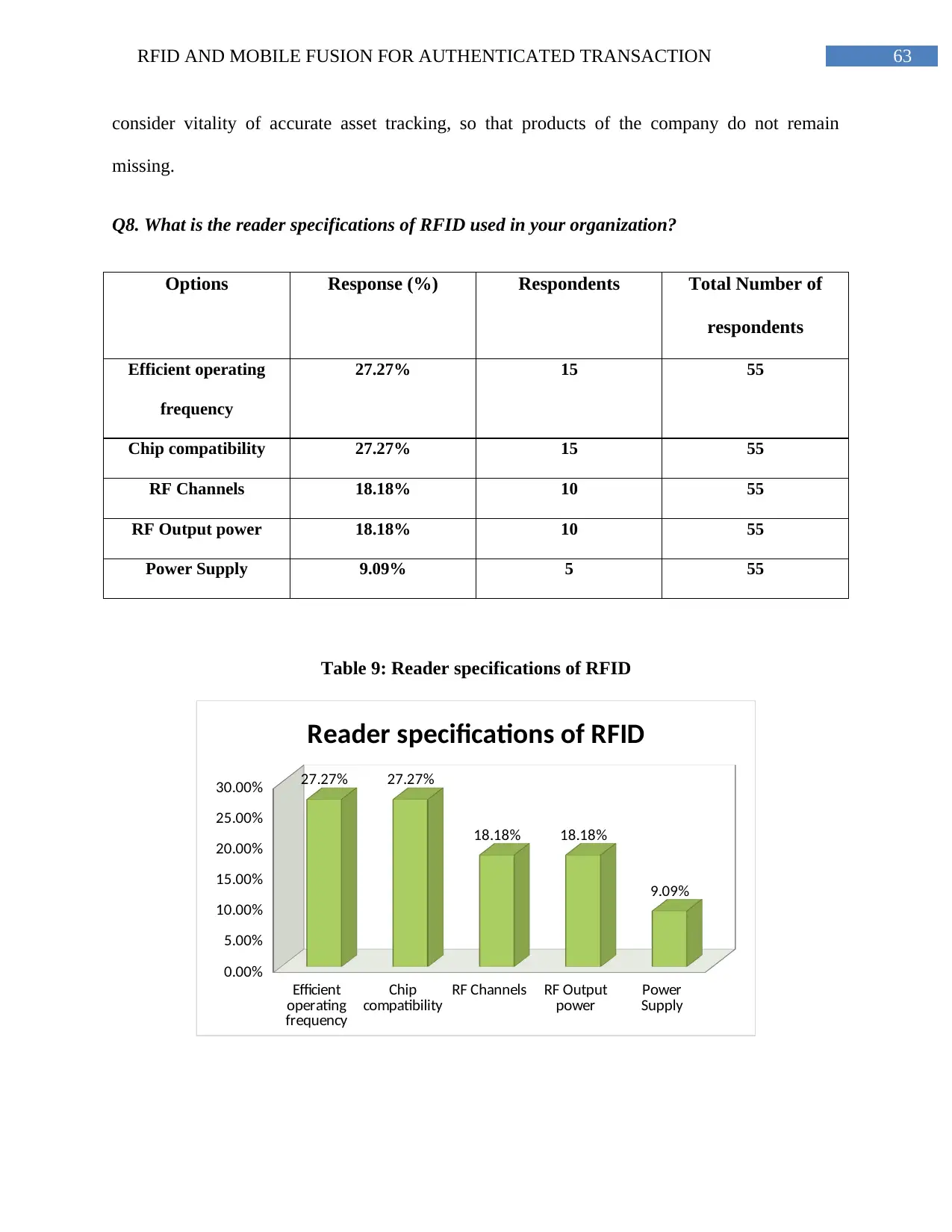
63RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
consider vitality of accurate asset tracking, so that products of the company do not remain
missing.
Q8. What is the reader specifications of RFID used in your organization?
Options Response (%) Respondents Total Number of
respondents
Efficient operating
frequency
27.27% 15 55
Chip compatibility 27.27% 15 55
RF Channels 18.18% 10 55
RF Output power 18.18% 10 55
Power Supply 9.09% 5 55
Table 9: Reader specifications of RFID
Efficient
operating
frequency
Chip
compatibility RF Channels RF Output
power Power
Supply
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00% 27.27% 27.27%
18.18% 18.18%
9.09%
Reader specifications of RFID
consider vitality of accurate asset tracking, so that products of the company do not remain
missing.
Q8. What is the reader specifications of RFID used in your organization?
Options Response (%) Respondents Total Number of
respondents
Efficient operating
frequency
27.27% 15 55
Chip compatibility 27.27% 15 55
RF Channels 18.18% 10 55
RF Output power 18.18% 10 55
Power Supply 9.09% 5 55
Table 9: Reader specifications of RFID
Efficient
operating
frequency
Chip
compatibility RF Channels RF Output
power Power
Supply
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00% 27.27% 27.27%
18.18% 18.18%
9.09%
Reader specifications of RFID
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
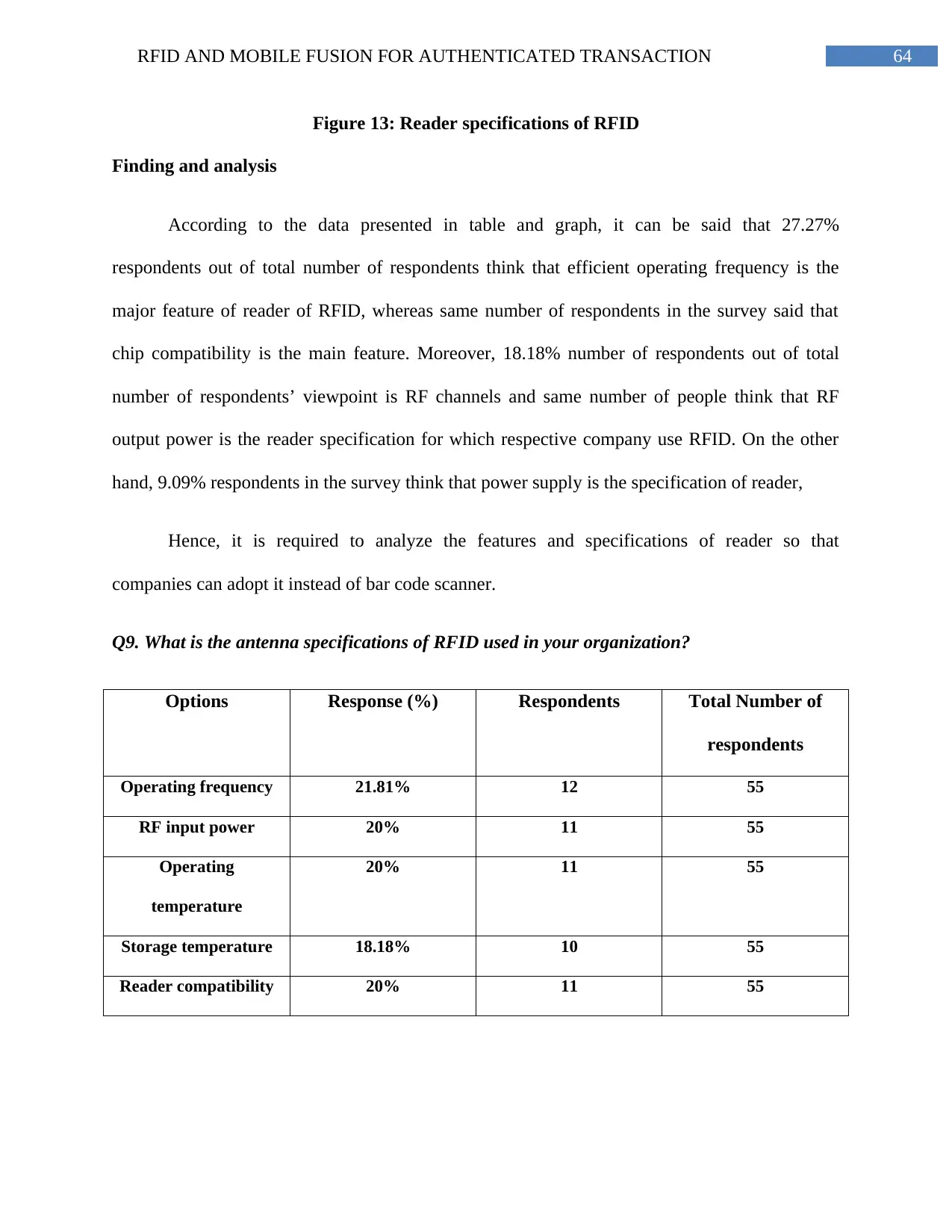
64RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Figure 13: Reader specifications of RFID
Finding and analysis
According to the data presented in table and graph, it can be said that 27.27%
respondents out of total number of respondents think that efficient operating frequency is the
major feature of reader of RFID, whereas same number of respondents in the survey said that
chip compatibility is the main feature. Moreover, 18.18% number of respondents out of total
number of respondents’ viewpoint is RF channels and same number of people think that RF
output power is the reader specification for which respective company use RFID. On the other
hand, 9.09% respondents in the survey think that power supply is the specification of reader,
Hence, it is required to analyze the features and specifications of reader so that
companies can adopt it instead of bar code scanner.
Q9. What is the antenna specifications of RFID used in your organization?
Options Response (%) Respondents Total Number of
respondents
Operating frequency 21.81% 12 55
RF input power 20% 11 55
Operating
temperature
20% 11 55
Storage temperature 18.18% 10 55
Reader compatibility 20% 11 55
Figure 13: Reader specifications of RFID
Finding and analysis
According to the data presented in table and graph, it can be said that 27.27%
respondents out of total number of respondents think that efficient operating frequency is the
major feature of reader of RFID, whereas same number of respondents in the survey said that
chip compatibility is the main feature. Moreover, 18.18% number of respondents out of total
number of respondents’ viewpoint is RF channels and same number of people think that RF
output power is the reader specification for which respective company use RFID. On the other
hand, 9.09% respondents in the survey think that power supply is the specification of reader,
Hence, it is required to analyze the features and specifications of reader so that
companies can adopt it instead of bar code scanner.
Q9. What is the antenna specifications of RFID used in your organization?
Options Response (%) Respondents Total Number of
respondents
Operating frequency 21.81% 12 55
RF input power 20% 11 55
Operating
temperature
20% 11 55
Storage temperature 18.18% 10 55
Reader compatibility 20% 11 55
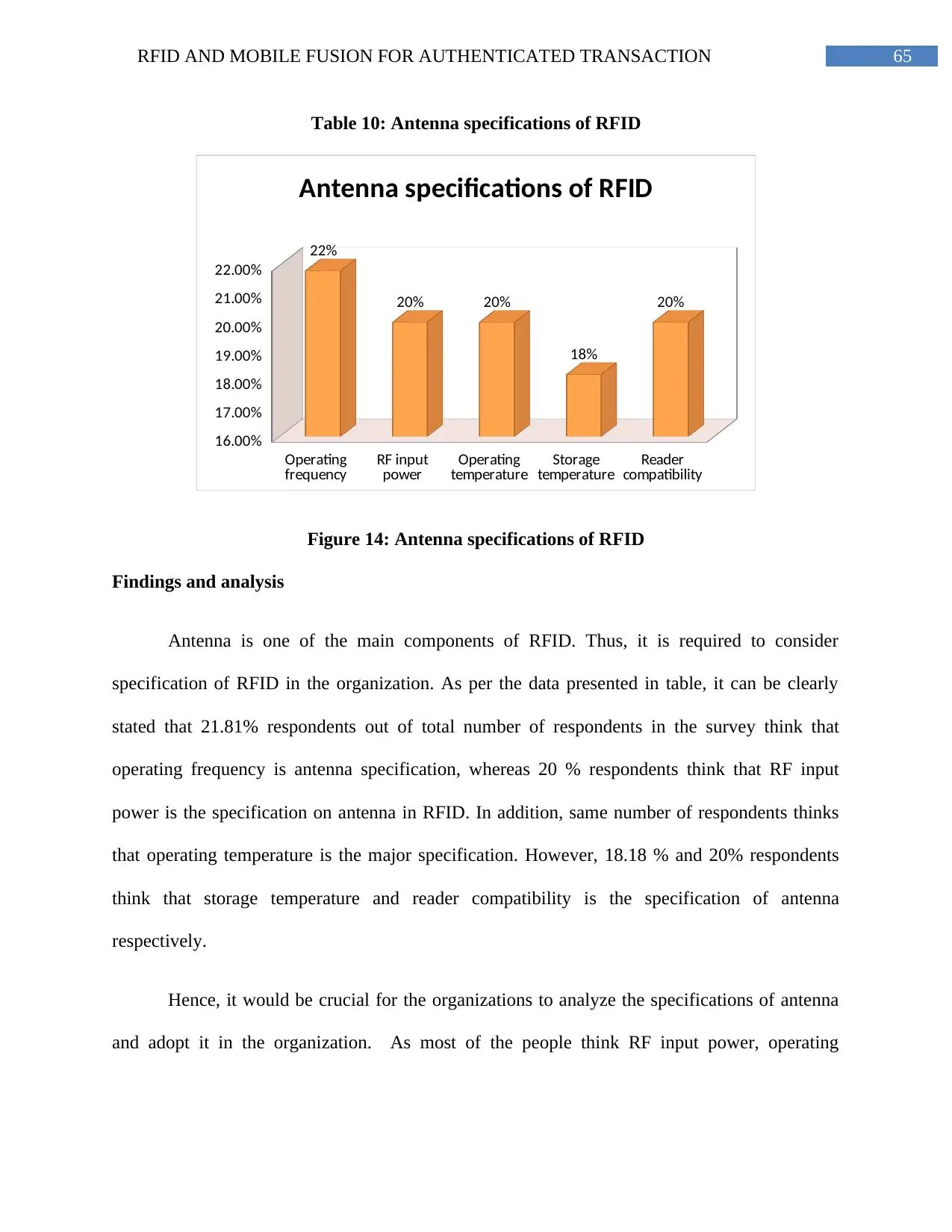
65RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Table 10: Antenna specifications of RFID
Operating
frequency RF input
power Operating
temperature Storage
temperature Reader
compatibility
16.00%
17.00%
18.00%
19.00%
20.00%
21.00%
22.00%
22%
20% 20%
18%
20%
Antenna specifications of RFID
Figure 14: Antenna specifications of RFID
Findings and analysis
Antenna is one of the main components of RFID. Thus, it is required to consider
specification of RFID in the organization. As per the data presented in table, it can be clearly
stated that 21.81% respondents out of total number of respondents in the survey think that
operating frequency is antenna specification, whereas 20 % respondents think that RF input
power is the specification on antenna in RFID. In addition, same number of respondents thinks
that operating temperature is the major specification. However, 18.18 % and 20% respondents
think that storage temperature and reader compatibility is the specification of antenna
respectively.
Hence, it would be crucial for the organizations to analyze the specifications of antenna
and adopt it in the organization. As most of the people think RF input power, operating
Table 10: Antenna specifications of RFID
Operating
frequency RF input
power Operating
temperature Storage
temperature Reader
compatibility
16.00%
17.00%
18.00%
19.00%
20.00%
21.00%
22.00%
22%
20% 20%
18%
20%
Antenna specifications of RFID
Figure 14: Antenna specifications of RFID
Findings and analysis
Antenna is one of the main components of RFID. Thus, it is required to consider
specification of RFID in the organization. As per the data presented in table, it can be clearly
stated that 21.81% respondents out of total number of respondents in the survey think that
operating frequency is antenna specification, whereas 20 % respondents think that RF input
power is the specification on antenna in RFID. In addition, same number of respondents thinks
that operating temperature is the major specification. However, 18.18 % and 20% respondents
think that storage temperature and reader compatibility is the specification of antenna
respectively.
Hence, it would be crucial for the organizations to analyze the specifications of antenna
and adopt it in the organization. As most of the people think RF input power, operating
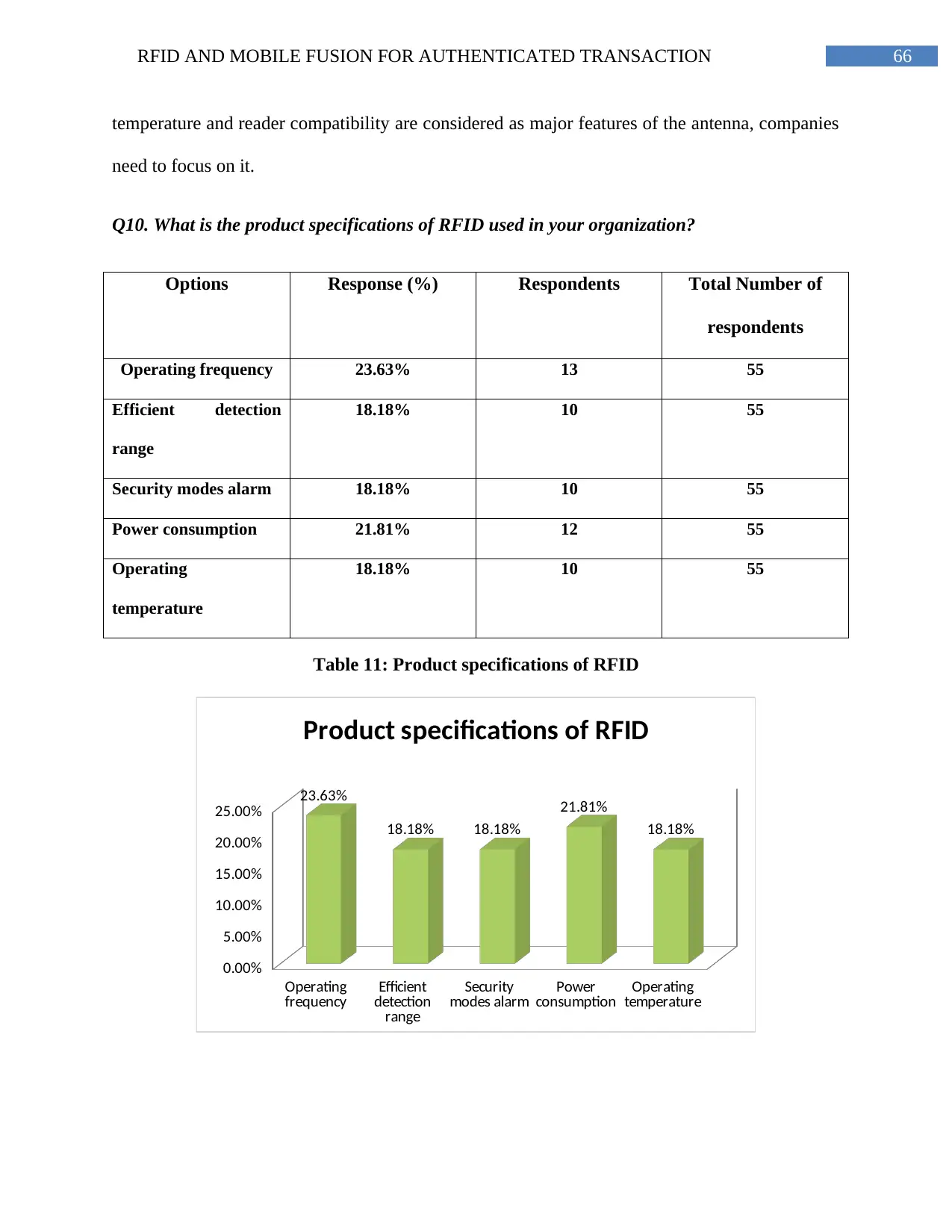
66RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
temperature and reader compatibility are considered as major features of the antenna, companies
need to focus on it.
Q10. What is the product specifications of RFID used in your organization?
Options Response (%) Respondents Total Number of
respondents
Operating frequency 23.63% 13 55
Efficient detection
range
18.18% 10 55
Security modes alarm 18.18% 10 55
Power consumption 21.81% 12 55
Operating
temperature
18.18% 10 55
Table 11: Product specifications of RFID
Operating
frequency Efficient
detection
range
Security
modes alarm Power
consumption Operating
temperature
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
23.63%
18.18% 18.18%
21.81%
18.18%
Product specifications of RFID
temperature and reader compatibility are considered as major features of the antenna, companies
need to focus on it.
Q10. What is the product specifications of RFID used in your organization?
Options Response (%) Respondents Total Number of
respondents
Operating frequency 23.63% 13 55
Efficient detection
range
18.18% 10 55
Security modes alarm 18.18% 10 55
Power consumption 21.81% 12 55
Operating
temperature
18.18% 10 55
Table 11: Product specifications of RFID
Operating
frequency Efficient
detection
range
Security
modes alarm Power
consumption Operating
temperature
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
23.63%
18.18% 18.18%
21.81%
18.18%
Product specifications of RFID
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
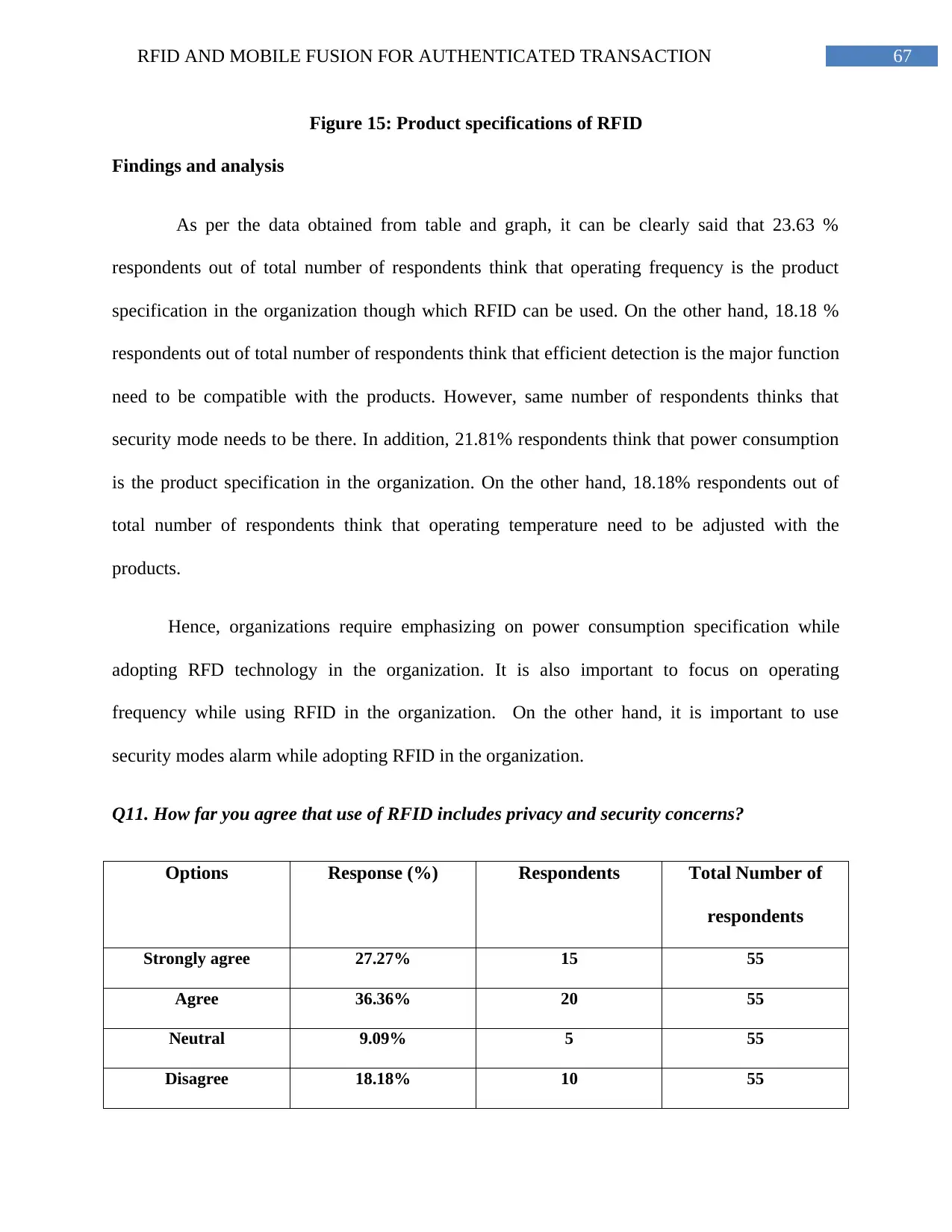
67RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Figure 15: Product specifications of RFID
Findings and analysis
As per the data obtained from table and graph, it can be clearly said that 23.63 %
respondents out of total number of respondents think that operating frequency is the product
specification in the organization though which RFID can be used. On the other hand, 18.18 %
respondents out of total number of respondents think that efficient detection is the major function
need to be compatible with the products. However, same number of respondents thinks that
security mode needs to be there. In addition, 21.81% respondents think that power consumption
is the product specification in the organization. On the other hand, 18.18% respondents out of
total number of respondents think that operating temperature need to be adjusted with the
products.
Hence, organizations require emphasizing on power consumption specification while
adopting RFD technology in the organization. It is also important to focus on operating
frequency while using RFID in the organization. On the other hand, it is important to use
security modes alarm while adopting RFID in the organization.
Q11. How far you agree that use of RFID includes privacy and security concerns?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 27.27% 15 55
Agree 36.36% 20 55
Neutral 9.09% 5 55
Disagree 18.18% 10 55
Figure 15: Product specifications of RFID
Findings and analysis
As per the data obtained from table and graph, it can be clearly said that 23.63 %
respondents out of total number of respondents think that operating frequency is the product
specification in the organization though which RFID can be used. On the other hand, 18.18 %
respondents out of total number of respondents think that efficient detection is the major function
need to be compatible with the products. However, same number of respondents thinks that
security mode needs to be there. In addition, 21.81% respondents think that power consumption
is the product specification in the organization. On the other hand, 18.18% respondents out of
total number of respondents think that operating temperature need to be adjusted with the
products.
Hence, organizations require emphasizing on power consumption specification while
adopting RFD technology in the organization. It is also important to focus on operating
frequency while using RFID in the organization. On the other hand, it is important to use
security modes alarm while adopting RFID in the organization.
Q11. How far you agree that use of RFID includes privacy and security concerns?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 27.27% 15 55
Agree 36.36% 20 55
Neutral 9.09% 5 55
Disagree 18.18% 10 55
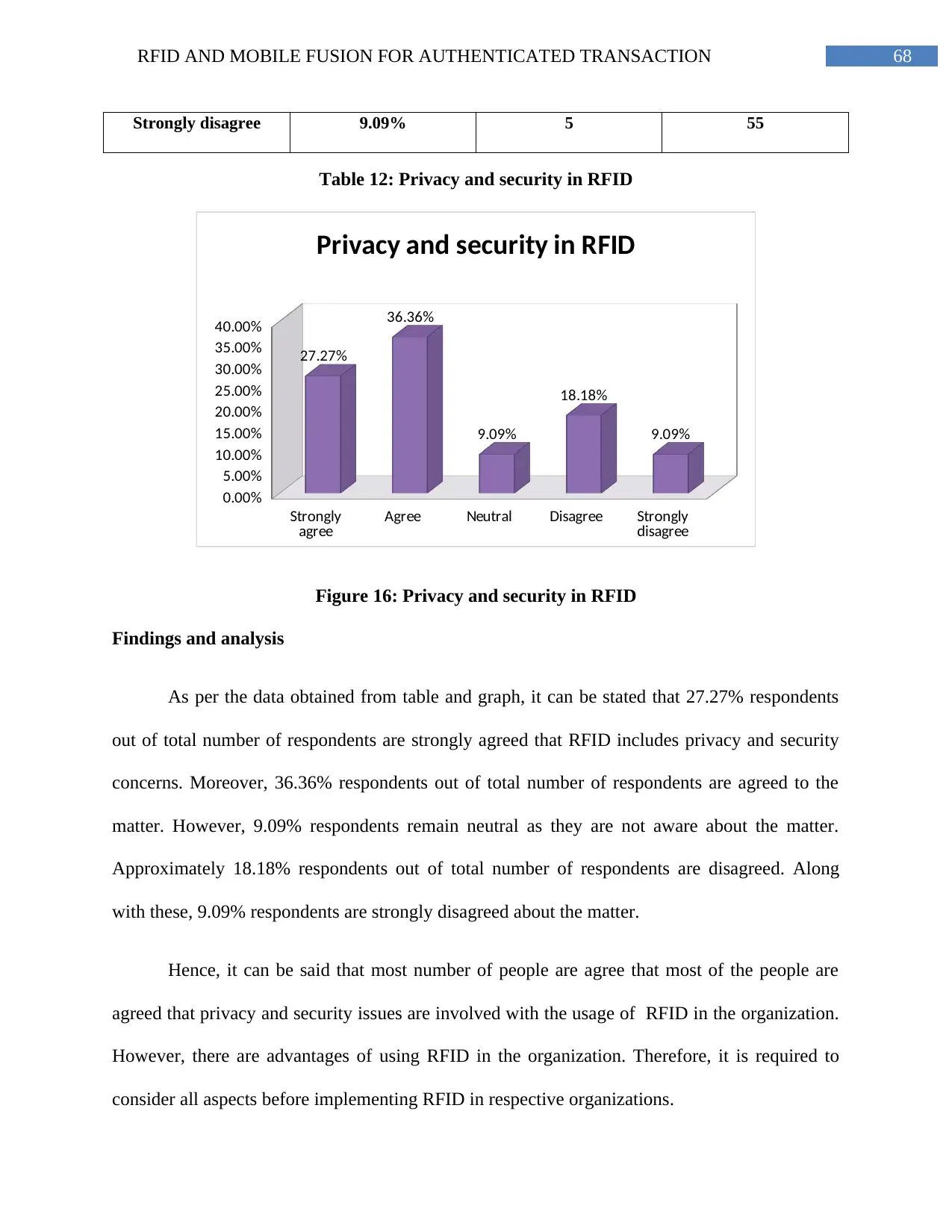
68RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Strongly disagree 9.09% 5 55
Table 12: Privacy and security in RFID
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
27.27%
36.36%
9.09%
18.18%
9.09%
Privacy and security in RFID
Figure 16: Privacy and security in RFID
Findings and analysis
As per the data obtained from table and graph, it can be stated that 27.27% respondents
out of total number of respondents are strongly agreed that RFID includes privacy and security
concerns. Moreover, 36.36% respondents out of total number of respondents are agreed to the
matter. However, 9.09% respondents remain neutral as they are not aware about the matter.
Approximately 18.18% respondents out of total number of respondents are disagreed. Along
with these, 9.09% respondents are strongly disagreed about the matter.
Hence, it can be said that most number of people are agree that most of the people are
agreed that privacy and security issues are involved with the usage of RFID in the organization.
However, there are advantages of using RFID in the organization. Therefore, it is required to
consider all aspects before implementing RFID in respective organizations.
Strongly disagree 9.09% 5 55
Table 12: Privacy and security in RFID
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
27.27%
36.36%
9.09%
18.18%
9.09%
Privacy and security in RFID
Figure 16: Privacy and security in RFID
Findings and analysis
As per the data obtained from table and graph, it can be stated that 27.27% respondents
out of total number of respondents are strongly agreed that RFID includes privacy and security
concerns. Moreover, 36.36% respondents out of total number of respondents are agreed to the
matter. However, 9.09% respondents remain neutral as they are not aware about the matter.
Approximately 18.18% respondents out of total number of respondents are disagreed. Along
with these, 9.09% respondents are strongly disagreed about the matter.
Hence, it can be said that most number of people are agree that most of the people are
agreed that privacy and security issues are involved with the usage of RFID in the organization.
However, there are advantages of using RFID in the organization. Therefore, it is required to
consider all aspects before implementing RFID in respective organizations.
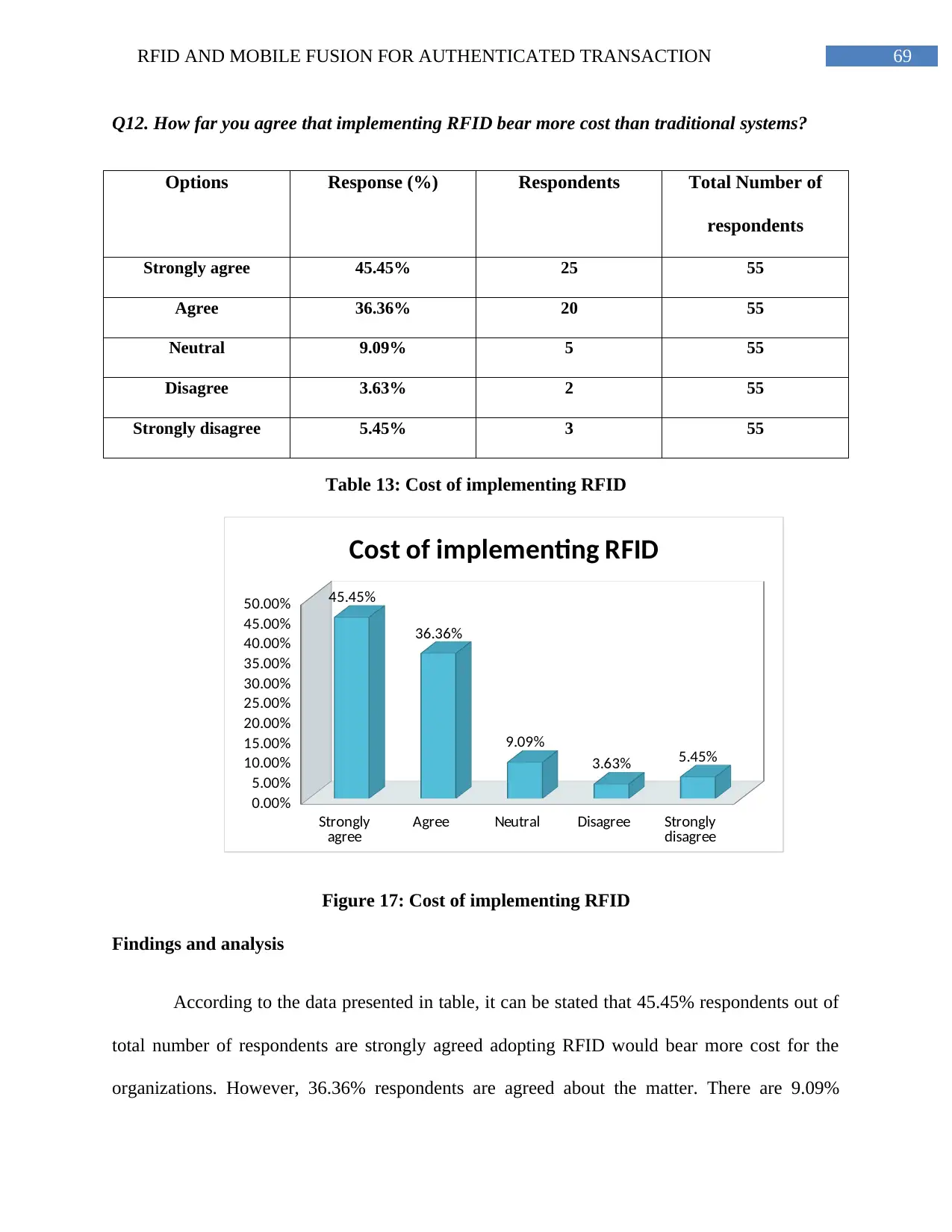
69RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Q12. How far you agree that implementing RFID bear more cost than traditional systems?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 45.45% 25 55
Agree 36.36% 20 55
Neutral 9.09% 5 55
Disagree 3.63% 2 55
Strongly disagree 5.45% 3 55
Table 13: Cost of implementing RFID
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
45.00%
50.00% 45.45%
36.36%
9.09%
3.63% 5.45%
Cost of implementing RFID
Figure 17: Cost of implementing RFID
Findings and analysis
According to the data presented in table, it can be stated that 45.45% respondents out of
total number of respondents are strongly agreed adopting RFID would bear more cost for the
organizations. However, 36.36% respondents are agreed about the matter. There are 9.09%
Q12. How far you agree that implementing RFID bear more cost than traditional systems?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 45.45% 25 55
Agree 36.36% 20 55
Neutral 9.09% 5 55
Disagree 3.63% 2 55
Strongly disagree 5.45% 3 55
Table 13: Cost of implementing RFID
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
45.00%
50.00% 45.45%
36.36%
9.09%
3.63% 5.45%
Cost of implementing RFID
Figure 17: Cost of implementing RFID
Findings and analysis
According to the data presented in table, it can be stated that 45.45% respondents out of
total number of respondents are strongly agreed adopting RFID would bear more cost for the
organizations. However, 36.36% respondents are agreed about the matter. There are 9.09%
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
70RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
respondents out of total number of respondents are neutral. On the other hand, 3.63%
respondents are disagreed about the matter. There are 5.45 % respondents strongly disagreed
about the matter.
As a business organization needs to consider cost before implementing a technology in
the organization, it is required considering the more bearing cost of RFID compared to
conventional system in the organization.
Q13. How far you agree that governments’ support need to be there for adopting RFID
technology?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 36.36% 20 55
Agree 32.72% 18 55
Neutral 3.63% 2 55
Disagree 18.18% 10 55
Strongly disagree 27.27% 15 55
respondents out of total number of respondents are neutral. On the other hand, 3.63%
respondents are disagreed about the matter. There are 5.45 % respondents strongly disagreed
about the matter.
As a business organization needs to consider cost before implementing a technology in
the organization, it is required considering the more bearing cost of RFID compared to
conventional system in the organization.
Q13. How far you agree that governments’ support need to be there for adopting RFID
technology?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 36.36% 20 55
Agree 32.72% 18 55
Neutral 3.63% 2 55
Disagree 18.18% 10 55
Strongly disagree 27.27% 15 55
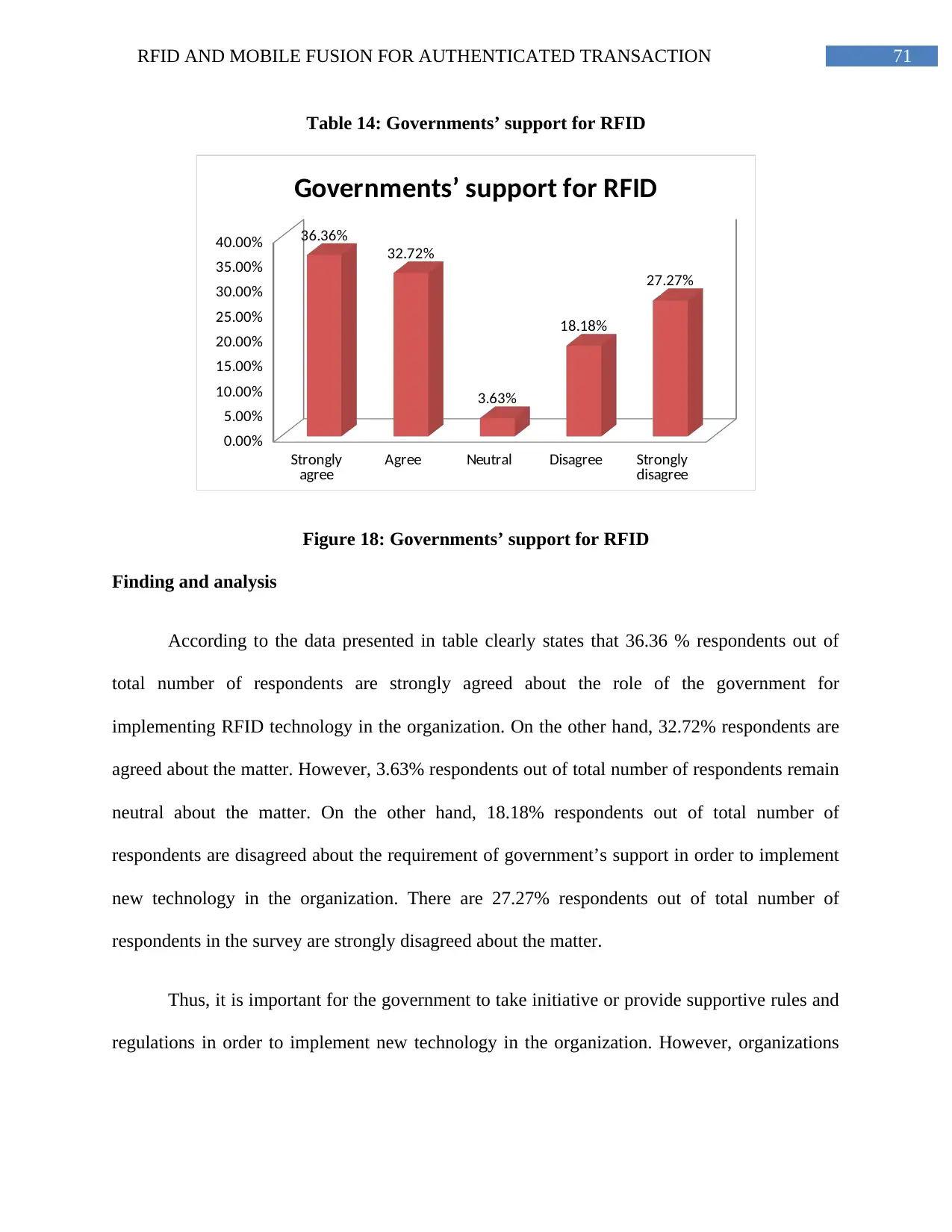
71RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Table 14: Governments’ support for RFID
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00% 36.36%
32.72%
3.63%
18.18%
27.27%
Governments’ support for RFID
Figure 18: Governments’ support for RFID
Finding and analysis
According to the data presented in table clearly states that 36.36 % respondents out of
total number of respondents are strongly agreed about the role of the government for
implementing RFID technology in the organization. On the other hand, 32.72% respondents are
agreed about the matter. However, 3.63% respondents out of total number of respondents remain
neutral about the matter. On the other hand, 18.18% respondents out of total number of
respondents are disagreed about the requirement of government’s support in order to implement
new technology in the organization. There are 27.27% respondents out of total number of
respondents in the survey are strongly disagreed about the matter.
Thus, it is important for the government to take initiative or provide supportive rules and
regulations in order to implement new technology in the organization. However, organizations
Table 14: Governments’ support for RFID
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00% 36.36%
32.72%
3.63%
18.18%
27.27%
Governments’ support for RFID
Figure 18: Governments’ support for RFID
Finding and analysis
According to the data presented in table clearly states that 36.36 % respondents out of
total number of respondents are strongly agreed about the role of the government for
implementing RFID technology in the organization. On the other hand, 32.72% respondents are
agreed about the matter. However, 3.63% respondents out of total number of respondents remain
neutral about the matter. On the other hand, 18.18% respondents out of total number of
respondents are disagreed about the requirement of government’s support in order to implement
new technology in the organization. There are 27.27% respondents out of total number of
respondents in the survey are strongly disagreed about the matter.
Thus, it is important for the government to take initiative or provide supportive rules and
regulations in order to implement new technology in the organization. However, organizations
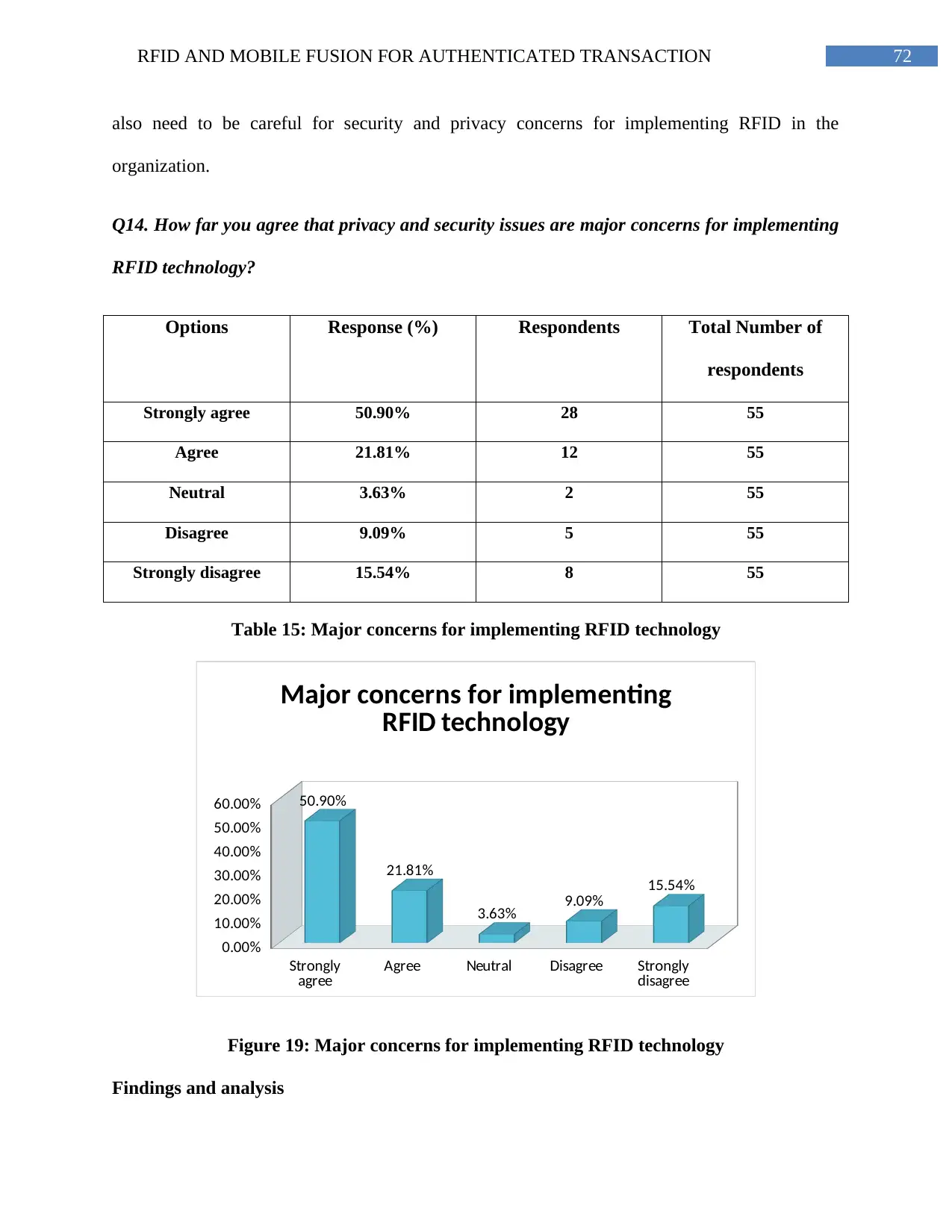
72RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
also need to be careful for security and privacy concerns for implementing RFID in the
organization.
Q14. How far you agree that privacy and security issues are major concerns for implementing
RFID technology?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 50.90% 28 55
Agree 21.81% 12 55
Neutral 3.63% 2 55
Disagree 9.09% 5 55
Strongly disagree 15.54% 8 55
Table 15: Major concerns for implementing RFID technology
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
10.00%
20.00%
30.00%
40.00%
50.00%
60.00% 50.90%
21.81%
3.63% 9.09% 15.54%
Major concerns for implementing
RFID technology
Figure 19: Major concerns for implementing RFID technology
Findings and analysis
also need to be careful for security and privacy concerns for implementing RFID in the
organization.
Q14. How far you agree that privacy and security issues are major concerns for implementing
RFID technology?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 50.90% 28 55
Agree 21.81% 12 55
Neutral 3.63% 2 55
Disagree 9.09% 5 55
Strongly disagree 15.54% 8 55
Table 15: Major concerns for implementing RFID technology
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
10.00%
20.00%
30.00%
40.00%
50.00%
60.00% 50.90%
21.81%
3.63% 9.09% 15.54%
Major concerns for implementing
RFID technology
Figure 19: Major concerns for implementing RFID technology
Findings and analysis
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
73RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
According to the presented in table and graph, it can be clearly stated that 50.09%
respondents out of total number of respondents are strongly agreed about privacy and security
issues as major concerns for implementing RFID technology. In addition, 21.81% respondents
out of total number of respondents are agreed about the matter. On the other hand, 3.63%
respondents out of total number of respondents are neutral. There are 9.09% respondents out of
total number of respondents are disagreed about the matter. In addition, 15.54% respondents out
of total number of respondents are strongly disagreed about the matter
Hence, it is important to consider privacy and security issues as major concerns in the
organization. However, potential advantages need to be analyzed as well so that benefits of RFID
can be obtained in the organization.
Q15. How far you agree that RFID technology will be the cutting edge technology that
provides potential benefits in future?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 45.45% 25 55
Agree 36.36% 20 55
Neutral 9.09% 5 55
Disagree 18.18% 10 55
Strongly disagree 9.09% 5 55
According to the presented in table and graph, it can be clearly stated that 50.09%
respondents out of total number of respondents are strongly agreed about privacy and security
issues as major concerns for implementing RFID technology. In addition, 21.81% respondents
out of total number of respondents are agreed about the matter. On the other hand, 3.63%
respondents out of total number of respondents are neutral. There are 9.09% respondents out of
total number of respondents are disagreed about the matter. In addition, 15.54% respondents out
of total number of respondents are strongly disagreed about the matter
Hence, it is important to consider privacy and security issues as major concerns in the
organization. However, potential advantages need to be analyzed as well so that benefits of RFID
can be obtained in the organization.
Q15. How far you agree that RFID technology will be the cutting edge technology that
provides potential benefits in future?
Options Response (%) Respondents Total Number of
respondents
Strongly agree 45.45% 25 55
Agree 36.36% 20 55
Neutral 9.09% 5 55
Disagree 18.18% 10 55
Strongly disagree 9.09% 5 55
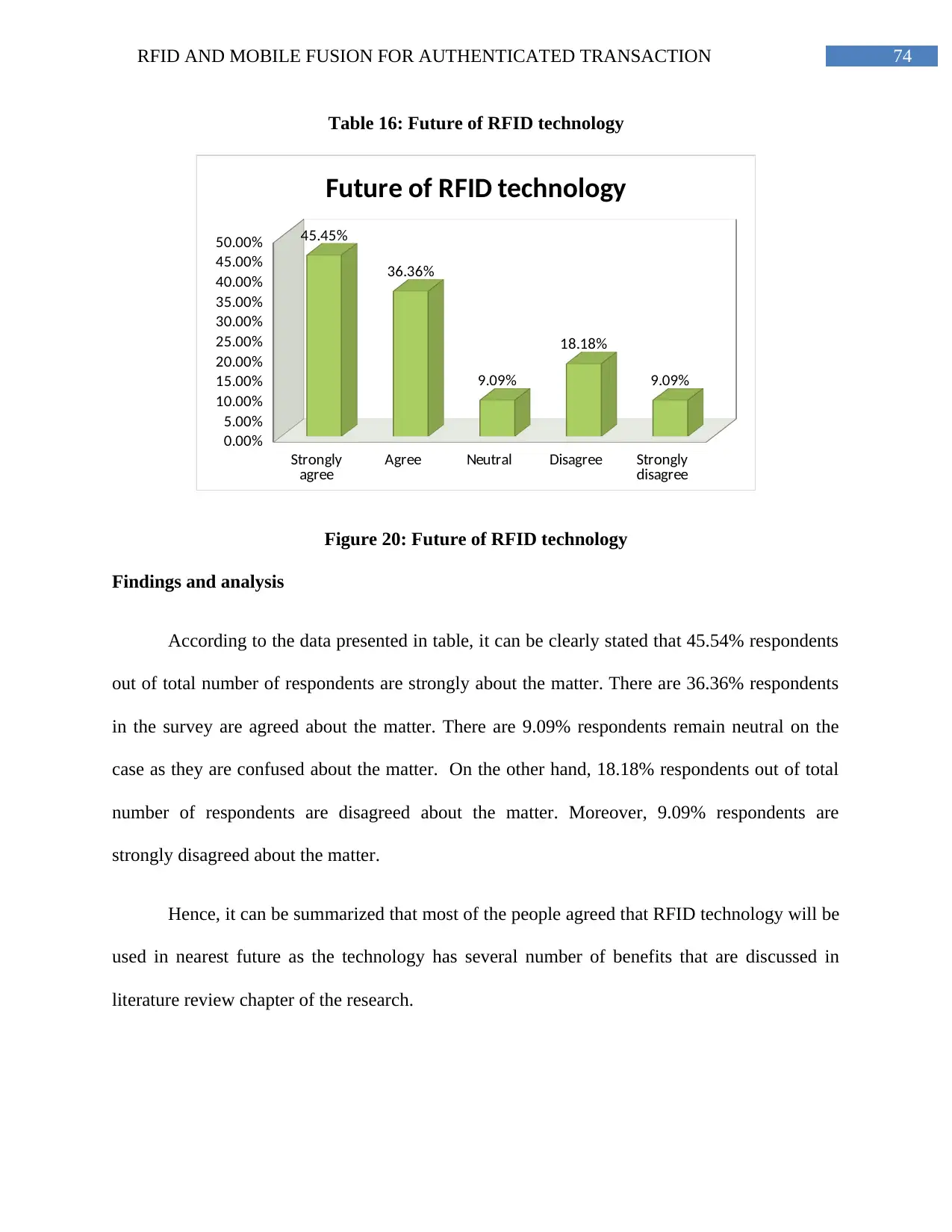
74RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Table 16: Future of RFID technology
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
45.00%
50.00% 45.45%
36.36%
9.09%
18.18%
9.09%
Future of RFID technology
Figure 20: Future of RFID technology
Findings and analysis
According to the data presented in table, it can be clearly stated that 45.54% respondents
out of total number of respondents are strongly about the matter. There are 36.36% respondents
in the survey are agreed about the matter. There are 9.09% respondents remain neutral on the
case as they are confused about the matter. On the other hand, 18.18% respondents out of total
number of respondents are disagreed about the matter. Moreover, 9.09% respondents are
strongly disagreed about the matter.
Hence, it can be summarized that most of the people agreed that RFID technology will be
used in nearest future as the technology has several number of benefits that are discussed in
literature review chapter of the research.
Table 16: Future of RFID technology
Strongly
agree Agree Neutral Disagree Strongly
disagree
0.00%
5.00%
10.00%
15.00%
20.00%
25.00%
30.00%
35.00%
40.00%
45.00%
50.00% 45.45%
36.36%
9.09%
18.18%
9.09%
Future of RFID technology
Figure 20: Future of RFID technology
Findings and analysis
According to the data presented in table, it can be clearly stated that 45.54% respondents
out of total number of respondents are strongly about the matter. There are 36.36% respondents
in the survey are agreed about the matter. There are 9.09% respondents remain neutral on the
case as they are confused about the matter. On the other hand, 18.18% respondents out of total
number of respondents are disagreed about the matter. Moreover, 9.09% respondents are
strongly disagreed about the matter.
Hence, it can be summarized that most of the people agreed that RFID technology will be
used in nearest future as the technology has several number of benefits that are discussed in
literature review chapter of the research.

75RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
4.3 Summary
From above discussion, it can be summarized that security and privacy issues are integral
part of adopting RFID technology in the organization. Vulnerability, risk and challenges also
often turn out as dangerous for the organization. However, for having several advantages such as
easy tracking, improvement in efficiency, organizations need to adopt RFID in the organization.
In addition, increment in accuracy would be additional advantage for which organizations would
gain competitive benefits for deploying RFID in their operations.
4.3 Summary
From above discussion, it can be summarized that security and privacy issues are integral
part of adopting RFID technology in the organization. Vulnerability, risk and challenges also
often turn out as dangerous for the organization. However, for having several advantages such as
easy tracking, improvement in efficiency, organizations need to adopt RFID in the organization.
In addition, increment in accuracy would be additional advantage for which organizations would
gain competitive benefits for deploying RFID in their operations.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

76RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Chapter 5: Conclusion and Recommendations
5.1 Conclusion
The paper has given a review of the present state and patterns of RFID innovation.
Despite the fact that various impediments and uncertain issues still ruin the across the board use
of RFID, it becomes very popular among industry owners. Notwithstanding these difficulties,
RFID keeps on making advances into stock control frameworks, and it won't be long until the
segment costs fall sufficiently low to make RFID an alluring financial recommendation. Besides,
broad designing endeavors are under approach to beat current specialized confinements and to
assemble exact and solid label perusing frameworks. It may likewise begin to see financial gain
from the bigger merchants to change item bundling and its related materials to all the more
successfully incorporate RFID. At long last, at this sensitive stage, while significant partnerships
are trialing the innovation, media response and candid protection gatherings can impact the
tenets by which we utilize the innovation. RFID's potential advantages are vast, and we're certain
to see numerous novel applications n the future some of which cannot be started to envision. The
parts that go into RFID readers and tags are basic radio communications, yet their littler size and
expansive arrangement upgrade the energy of the innovation and raise worries about the security
impacts of RFID sending. These worries are frequently commenced on improbable presumptions
about where the innovation will go and how it will be utilized.
5.2 Linking with objectives
Objective 1: To understand how RFID technology can be used in the online industry
Chapter 5: Conclusion and Recommendations
5.1 Conclusion
The paper has given a review of the present state and patterns of RFID innovation.
Despite the fact that various impediments and uncertain issues still ruin the across the board use
of RFID, it becomes very popular among industry owners. Notwithstanding these difficulties,
RFID keeps on making advances into stock control frameworks, and it won't be long until the
segment costs fall sufficiently low to make RFID an alluring financial recommendation. Besides,
broad designing endeavors are under approach to beat current specialized confinements and to
assemble exact and solid label perusing frameworks. It may likewise begin to see financial gain
from the bigger merchants to change item bundling and its related materials to all the more
successfully incorporate RFID. At long last, at this sensitive stage, while significant partnerships
are trialing the innovation, media response and candid protection gatherings can impact the
tenets by which we utilize the innovation. RFID's potential advantages are vast, and we're certain
to see numerous novel applications n the future some of which cannot be started to envision. The
parts that go into RFID readers and tags are basic radio communications, yet their littler size and
expansive arrangement upgrade the energy of the innovation and raise worries about the security
impacts of RFID sending. These worries are frequently commenced on improbable presumptions
about where the innovation will go and how it will be utilized.
5.2 Linking with objectives
Objective 1: To understand how RFID technology can be used in the online industry

77RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
It is important to understand the role and process of using RFID in online industry for
researching on the particular topic. In the literature review section, overview of RFID and its
components used at present days are discussed. On the other hand, in the survey section, question
no 7, 8 and 9 fulfill the purpose of this objective. Hence, the objective is successfully taken in the
research.
Objective 2: To identify both positive and negative impact of such technology on people
In the literature review section, advantages and disadvantages are critically reviewed. On
the other hand, survey questionnaire number 5, 9 and 10 are fulfilled with the objective. Hence,
the objective is justified in the research.
Objective 3: To critically analyze the challenges faced while implementing and using RFID
technology
The challenges for adopting RFID technology is discussed in the literature review chapter
like privacy and security issues are associated with it. On the other hand, in survey questionnaire
section, security and privacy issues related questions are asked. Thus, the objective is properly
justified in the research.
Objective 4: To recommend solutions in order to overcome the challenges
It is important for an organization to overcome the challenges faced while using RFID in
their organization. In order to solve the issues, recommendations are provided so that the
objective is justified in the research.
It is important to understand the role and process of using RFID in online industry for
researching on the particular topic. In the literature review section, overview of RFID and its
components used at present days are discussed. On the other hand, in the survey section, question
no 7, 8 and 9 fulfill the purpose of this objective. Hence, the objective is successfully taken in the
research.
Objective 2: To identify both positive and negative impact of such technology on people
In the literature review section, advantages and disadvantages are critically reviewed. On
the other hand, survey questionnaire number 5, 9 and 10 are fulfilled with the objective. Hence,
the objective is justified in the research.
Objective 3: To critically analyze the challenges faced while implementing and using RFID
technology
The challenges for adopting RFID technology is discussed in the literature review chapter
like privacy and security issues are associated with it. On the other hand, in survey questionnaire
section, security and privacy issues related questions are asked. Thus, the objective is properly
justified in the research.
Objective 4: To recommend solutions in order to overcome the challenges
It is important for an organization to overcome the challenges faced while using RFID in
their organization. In order to solve the issues, recommendations are provided so that the
objective is justified in the research.

78RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
5.3 Recommendations
Concerns over attack of protection have provoked a few states to draft enactment
concerning the utilization of RFID. Pending enactment in California, Senate Bill 1834, limits the
measure of data on the tag. Pending Massachusetts enactment, House Bill 1447 and Senate Bill
181, requires marks and logos to advise buyers about he utilize and reason for RFID on items
and readers. The enactment likewise requires the capacity to evacuate labels that are not
fundamental to the item and limits the data put away on labels to stock and comparative
purposes.
There are a few models identified with RFID innovation. The models cover the
accompanying themes:
•identification, the coding of special thing identifiers, or other information on the RF tag;
•data and framework conventions, successfully the middleware of a RFID framework;
•the air interface is wireless communication between the reader and the tag;
•application support, which gives counsel about how to actualize the innovation;
•testing, compliance as well as wellbeing and security, that is, the principles that oversee
RFID operations and terminology
5.4 Limitation and Future scopes
Even though the research has given potential outcomes, there are some limitations as well
involved with this. Due to limited time and money, researcher faced issues in gathering data.
Few of the participants were not agreed about to answer the questions, whereas somebody has
given haphazard answers due to close ended questionnaire. On the other hand, adequate money
5.3 Recommendations
Concerns over attack of protection have provoked a few states to draft enactment
concerning the utilization of RFID. Pending enactment in California, Senate Bill 1834, limits the
measure of data on the tag. Pending Massachusetts enactment, House Bill 1447 and Senate Bill
181, requires marks and logos to advise buyers about he utilize and reason for RFID on items
and readers. The enactment likewise requires the capacity to evacuate labels that are not
fundamental to the item and limits the data put away on labels to stock and comparative
purposes.
There are a few models identified with RFID innovation. The models cover the
accompanying themes:
•identification, the coding of special thing identifiers, or other information on the RF tag;
•data and framework conventions, successfully the middleware of a RFID framework;
•the air interface is wireless communication between the reader and the tag;
•application support, which gives counsel about how to actualize the innovation;
•testing, compliance as well as wellbeing and security, that is, the principles that oversee
RFID operations and terminology
5.4 Limitation and Future scopes
Even though the research has given potential outcomes, there are some limitations as well
involved with this. Due to limited time and money, researcher faced issues in gathering data.
Few of the participants were not agreed about to answer the questions, whereas somebody has
given haphazard answers due to close ended questionnaire. On the other hand, adequate money
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

79RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
would be helpful to use better software like SPSS in order to get better and accurate outcome for
the research.
In the future research, the particular study will be important in order to make further
improvement regarding the matter. In addition, future researcher can use it as secondary sources
for doing research similar to the topic. Recommendations would be helpful for the industry
owners to take proper steps in order to use RFID effectively and efficiently.
would be helpful to use better software like SPSS in order to get better and accurate outcome for
the research.
In the future research, the particular study will be important in order to make further
improvement regarding the matter. In addition, future researcher can use it as secondary sources
for doing research similar to the topic. Recommendations would be helpful for the industry
owners to take proper steps in order to use RFID effectively and efficiently.

80RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
References
Alomair, B., Clark, A., Cuellar, J. and Poovendran, R., 2012. Scalable RFID systems: a privacy-
preserving protocol with constant-time identification. IEEE Transactions on Parallel and
Distributed Systems, 23(8), pp.1536-1550.
Amendola, S., Lodato, R., Manzari, S., Occhiuzzi, C. and Marrocco, G., 2014. RFID technology
for IoT-based personal healthcare in smart spaces. IEEE Internet of Things Journal, 1(2),
pp.144-152.
Athalye, A., Savic, V., Bolic, M. and Djuric, P.M., 2013. Novel semi-passive RFID system for
indoor localization. IEEE Sensors Journal, 13(2), pp.528-537.
Catarinucci, L., De Donno, D., Colella, R., Ricciato, F. and Tarricone, L., 2012. A cost-
effective SDR platform for performance characterization of RFID tags. IEEE Transactions on
Instrumentation and Measurement, 61(4), pp.903-911.
Chae, H.J., Salajegheh, M., Yeager, D.J., Smith, J.R. and Fu, K., 2013. Maximalist
cryptography and computation on the WISP UHF RFID tag. In Wirelessly Powered Sensor
Networks and Computational RFID (pp. 175-187). Springer New York.
Chen, J.C., Cheng, C.H. and Huang, P.B., 2013. Supply chain management with lean
production and RFID application: A case study. Expert Systems with Applications, 40(9),
pp.3389-3397.
Chen, H.D., Kuo, S.H. and Tsai, C.H., 2012. Coupling-feed circularly polarized RFID tag
antenna mountable on metallic surface. IEEE Transactions on Antennas and
Propagation, 60(5), pp.2166-2174.
References
Alomair, B., Clark, A., Cuellar, J. and Poovendran, R., 2012. Scalable RFID systems: a privacy-
preserving protocol with constant-time identification. IEEE Transactions on Parallel and
Distributed Systems, 23(8), pp.1536-1550.
Amendola, S., Lodato, R., Manzari, S., Occhiuzzi, C. and Marrocco, G., 2014. RFID technology
for IoT-based personal healthcare in smart spaces. IEEE Internet of Things Journal, 1(2),
pp.144-152.
Athalye, A., Savic, V., Bolic, M. and Djuric, P.M., 2013. Novel semi-passive RFID system for
indoor localization. IEEE Sensors Journal, 13(2), pp.528-537.
Catarinucci, L., De Donno, D., Colella, R., Ricciato, F. and Tarricone, L., 2012. A cost-
effective SDR platform for performance characterization of RFID tags. IEEE Transactions on
Instrumentation and Measurement, 61(4), pp.903-911.
Chae, H.J., Salajegheh, M., Yeager, D.J., Smith, J.R. and Fu, K., 2013. Maximalist
cryptography and computation on the WISP UHF RFID tag. In Wirelessly Powered Sensor
Networks and Computational RFID (pp. 175-187). Springer New York.
Chen, J.C., Cheng, C.H. and Huang, P.B., 2013. Supply chain management with lean
production and RFID application: A case study. Expert Systems with Applications, 40(9),
pp.3389-3397.
Chen, H.D., Kuo, S.H. and Tsai, C.H., 2012. Coupling-feed circularly polarized RFID tag
antenna mountable on metallic surface. IEEE Transactions on Antennas and
Propagation, 60(5), pp.2166-2174.

81RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Costa, C., Antonucci, F., Pallottino, F., Aguzzi, J., Sarriá, D. and Menesatti, P., 2013. A review
on agri-food supply chain traceability by means of RFID technology. Food and Bioprocess
Technology, 6(2), pp.353-366.
Costa, F., Genovesi, S. and Monorchio, A., 2013. A chipless RFID based on multiresonant
high-impedance surfaces. IEEE transactions on microwave theory and techniques, 61(1),
pp.146-153.
Costin, A., Pradhananga, N. and Teizer, J., 2012. Leveraging passive RFID technology for
construction resource field mobility and status monitoring in a high-rise renovation
project. Automation in Construction, 24, pp.1-15.
De Donno, D., Catarinucci, L. and Tarricone, L., 2013. An UHF RFID energy-harvesting
system enhanced by a DC-DC charge pump in silicon-on-insulator technology. IEEE
Microwave and Wireless Components Letters, 23(6), pp.315-317.
De Marco, A., Cagliano, A.C., Nervo, M.L. and Rafele, C., 2012. Using System Dynamics to
assess the impact of RFID technology on retail operations. International journal of production
economics, 135(1), pp.333-344.
DiGiampaolo, E. and Martinelli, F., 2012. A passive UHF-RFID system for the localization of
an indoor autonomous vehicle. IEEE Transactions on Industrial Electronics, 59(10), pp.3961-
3970.
DiGiampaolo, E. and Martinelli, F., 2014. Mobile robot localization using the phase of passive
UHF RFID signals. IEEE Transactions on Industrial Electronics, 61(1), pp.365-376.
Dobkin, D.M., 2012. The rf in RFID: uhf RFID in practice. Newnes.
Costa, C., Antonucci, F., Pallottino, F., Aguzzi, J., Sarriá, D. and Menesatti, P., 2013. A review
on agri-food supply chain traceability by means of RFID technology. Food and Bioprocess
Technology, 6(2), pp.353-366.
Costa, F., Genovesi, S. and Monorchio, A., 2013. A chipless RFID based on multiresonant
high-impedance surfaces. IEEE transactions on microwave theory and techniques, 61(1),
pp.146-153.
Costin, A., Pradhananga, N. and Teizer, J., 2012. Leveraging passive RFID technology for
construction resource field mobility and status monitoring in a high-rise renovation
project. Automation in Construction, 24, pp.1-15.
De Donno, D., Catarinucci, L. and Tarricone, L., 2013. An UHF RFID energy-harvesting
system enhanced by a DC-DC charge pump in silicon-on-insulator technology. IEEE
Microwave and Wireless Components Letters, 23(6), pp.315-317.
De Marco, A., Cagliano, A.C., Nervo, M.L. and Rafele, C., 2012. Using System Dynamics to
assess the impact of RFID technology on retail operations. International journal of production
economics, 135(1), pp.333-344.
DiGiampaolo, E. and Martinelli, F., 2012. A passive UHF-RFID system for the localization of
an indoor autonomous vehicle. IEEE Transactions on Industrial Electronics, 59(10), pp.3961-
3970.
DiGiampaolo, E. and Martinelli, F., 2014. Mobile robot localization using the phase of passive
UHF RFID signals. IEEE Transactions on Industrial Electronics, 61(1), pp.365-376.
Dobkin, D.M., 2012. The rf in RFID: uhf RFID in practice. Newnes.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

82RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Fabian, B., Ermakova, T. and Muller, C., 2012. SHARDIS: A privacy-enhanced discovery
service for RFID-based product information. IEEE Transactions on Industrial Informatics, 8(3),
pp.707-718.
Feng, J., Fu, Z., Wang, Z., Xu, M. and Zhang, X., 2013. Development and evaluation on a
RFID-based traceability system for cattle/beef quality safety in China. Food control, 31(2),
pp.314-325.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage, pp.7-19.
Frankland, R., Mitchell, C.M., Ferguson, J.D., Sziklai, A.T., Verma, A.K., Popowski, J.E. and
Sturgeon, D.H., Applications In Internet Time, Llc, 2013. Integrated change management unit.
U.S. Patent 8,484,111.
Gast, D.L. and Ledford, J.R., 2014. Single case research methodology: Applications in special
education and behavioral sciences. Routledge.
Girbau, D., Ramos, Á., Lazaro, A., Rima, S. and Villarino, R., 2012. Passive wireless
temperature sensor based on time-coded UWB chipless RFID tags. IEEE Transactions on
Microwave Theory and Techniques, 60(11), pp.3623-3632.
Gong, Y.J., Shen, M., Zhang, J., Kaynak, O., Chen, W.N. and Zhan, Z.H., 2012. Optimizing
RFID network planning by using a particle swarm optimization algorithm with redundant reader
elimination. IEEE Transactions on Industrial Informatics, 8(4), pp.900-912.
Fabian, B., Ermakova, T. and Muller, C., 2012. SHARDIS: A privacy-enhanced discovery
service for RFID-based product information. IEEE Transactions on Industrial Informatics, 8(3),
pp.707-718.
Feng, J., Fu, Z., Wang, Z., Xu, M. and Zhang, X., 2013. Development and evaluation on a
RFID-based traceability system for cattle/beef quality safety in China. Food control, 31(2),
pp.314-325.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage, pp.7-19.
Frankland, R., Mitchell, C.M., Ferguson, J.D., Sziklai, A.T., Verma, A.K., Popowski, J.E. and
Sturgeon, D.H., Applications In Internet Time, Llc, 2013. Integrated change management unit.
U.S. Patent 8,484,111.
Gast, D.L. and Ledford, J.R., 2014. Single case research methodology: Applications in special
education and behavioral sciences. Routledge.
Girbau, D., Ramos, Á., Lazaro, A., Rima, S. and Villarino, R., 2012. Passive wireless
temperature sensor based on time-coded UWB chipless RFID tags. IEEE Transactions on
Microwave Theory and Techniques, 60(11), pp.3623-3632.
Gong, Y.J., Shen, M., Zhang, J., Kaynak, O., Chen, W.N. and Zhan, Z.H., 2012. Optimizing
RFID network planning by using a particle swarm optimization algorithm with redundant reader
elimination. IEEE Transactions on Industrial Informatics, 8(4), pp.900-912.

83RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
He, D. and Zeadally, S., 2015. An analysis of rfid authentication schemes for internet of things
in healthcare environment using elliptic curve cryptography. IEEE internet of things
journal, 2(1), pp.72-83.
Islam, M.A. and Karmakar, N.C., 2012. A novel compact printable dual-polarized chipless
RFID system. IEEE Transactions on Microwave Theory and Techniques, 60(7), pp.2142-2151.
Jia, X., Feng, Q., Fan, T. and Lei, Q., 2012, April. RFID technology and its applications in
Internet of Things (IoT). In Consumer Electronics, Communications and Networks (CECNet),
2012 2nd International Conference on (pp. 1282-1285). IEEE.
Jung, Y.K. and Lee, B., 2012. Dual-band circularly polarized microstrip RFID reader antenna
using metamaterial branch-line coupler. IEEE Transactions on Antennas and
Propagation, 60(2), pp.786-791.
Kapoor, G. and Piramuthu, S., 2012. Single RFID tag ownership transfer protocols. IEEE
Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 42(2),
pp.164-173.
Kassim, M., Mazlan, H., Zaini, N. and Salleh, M.K., 2012, July. Web-based student attendance
system using RFID technology. In Control and System Graduate Research Colloquium
(ICSGRC), 2012 IEEE (pp. 213-218). IEEE.
Kim, Y., Lee, B., Yang, S., Byun, I., Jeong, I. and Cho, S.M., 2012. Use of copper ink for
fabricating conductive electrodes and RFID antenna tags by screen printing. Current Applied
Physics, 12(2), pp.473-478.
Kitsos, P. ed., 2016. Security in RFID and sensor networks. CRC Press.
He, D. and Zeadally, S., 2015. An analysis of rfid authentication schemes for internet of things
in healthcare environment using elliptic curve cryptography. IEEE internet of things
journal, 2(1), pp.72-83.
Islam, M.A. and Karmakar, N.C., 2012. A novel compact printable dual-polarized chipless
RFID system. IEEE Transactions on Microwave Theory and Techniques, 60(7), pp.2142-2151.
Jia, X., Feng, Q., Fan, T. and Lei, Q., 2012, April. RFID technology and its applications in
Internet of Things (IoT). In Consumer Electronics, Communications and Networks (CECNet),
2012 2nd International Conference on (pp. 1282-1285). IEEE.
Jung, Y.K. and Lee, B., 2012. Dual-band circularly polarized microstrip RFID reader antenna
using metamaterial branch-line coupler. IEEE Transactions on Antennas and
Propagation, 60(2), pp.786-791.
Kapoor, G. and Piramuthu, S., 2012. Single RFID tag ownership transfer protocols. IEEE
Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 42(2),
pp.164-173.
Kassim, M., Mazlan, H., Zaini, N. and Salleh, M.K., 2012, July. Web-based student attendance
system using RFID technology. In Control and System Graduate Research Colloquium
(ICSGRC), 2012 IEEE (pp. 213-218). IEEE.
Kim, Y., Lee, B., Yang, S., Byun, I., Jeong, I. and Cho, S.M., 2012. Use of copper ink for
fabricating conductive electrodes and RFID antenna tags by screen printing. Current Applied
Physics, 12(2), pp.473-478.
Kitsos, P. ed., 2016. Security in RFID and sensor networks. CRC Press.

84RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Lehpamer, H., 2012. RFID design principles. Artech House.
Li, N., Calis, G. and Becerik-Gerber, B., 2012. Measuring and monitoring occupancy with an
RFID based system for demand-driven HVAC operations. Automation in construction, 24,
pp.89-99.
Liao, Y.P. and Hsiao, C.M., 2014. A secure ECC-based RFID authentication scheme integrated
with ID-verifier transfer protocol. Ad Hoc Networks, 18, pp.133-146.
Lim, M.K., Bahr, W. and Leung, S.C., 2013. RFID in the warehouse: A literature analysis
(1995–2010) of its applications, benefits, challenges and future trends. International Journal of
Production Economics, 145(1), pp.409-430.
Lu, M.T., Lin, S.W. and Tzeng, G.H., 2013. Improving RFID adoption in Taiwan's healthcare
industry based on a DEMATEL technique with a hybrid MCDM model. Decision Support
Systems, 56, pp.259-269.
Montaser, A. and Moselhi, O., 2014. RFID indoor location identification for construction
projects. Automation in Construction, 39, pp.167-179.
Nativi, J.J. and Lee, S., 2012. Impact of RFID information-sharing strategies on a decentralized
supply chain with reverse logistics operations. International Journal of Production
Economics, 136(2), pp.366-377.
Ngai, E.W.T., Chau, D.C.K., Poon, J.K.L., Chan, A.Y.M., Chan, B.C.M. and Wu, W.W.S.,
2012. Implementing an RFID-based manufacturing process management system: Lessons
learned and success factors. Journal of Engineering and Technology Management, 29(1),
pp.112-130.
Lehpamer, H., 2012. RFID design principles. Artech House.
Li, N., Calis, G. and Becerik-Gerber, B., 2012. Measuring and monitoring occupancy with an
RFID based system for demand-driven HVAC operations. Automation in construction, 24,
pp.89-99.
Liao, Y.P. and Hsiao, C.M., 2014. A secure ECC-based RFID authentication scheme integrated
with ID-verifier transfer protocol. Ad Hoc Networks, 18, pp.133-146.
Lim, M.K., Bahr, W. and Leung, S.C., 2013. RFID in the warehouse: A literature analysis
(1995–2010) of its applications, benefits, challenges and future trends. International Journal of
Production Economics, 145(1), pp.409-430.
Lu, M.T., Lin, S.W. and Tzeng, G.H., 2013. Improving RFID adoption in Taiwan's healthcare
industry based on a DEMATEL technique with a hybrid MCDM model. Decision Support
Systems, 56, pp.259-269.
Montaser, A. and Moselhi, O., 2014. RFID indoor location identification for construction
projects. Automation in Construction, 39, pp.167-179.
Nativi, J.J. and Lee, S., 2012. Impact of RFID information-sharing strategies on a decentralized
supply chain with reverse logistics operations. International Journal of Production
Economics, 136(2), pp.366-377.
Ngai, E.W.T., Chau, D.C.K., Poon, J.K.L., Chan, A.Y.M., Chan, B.C.M. and Wu, W.W.S.,
2012. Implementing an RFID-based manufacturing process management system: Lessons
learned and success factors. Journal of Engineering and Technology Management, 29(1),
pp.112-130.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

85RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Park, S. and Lee, H., 2013. Self-recognition of vehicle position using UHF passive RFID
tags. IEEE Transactions on Industrial Electronics, 60(1), pp.226-234.
Potyrailo, R.A., Nagraj, N., Tang, Z., Mondello, F.J., Surman, C. and Morris, W., 2012.
Battery-free radio frequency identification (RFID) sensors for food quality and safety. Journal
of agricultural and food chemistry, 60(35), p.8535.
Ransford, B., Sorber, J. and Fu, K., 2012. Mementos: System support for long-running
computation on RFID-scale devices. Acm Sigplan Notices, 47(4), pp.159-170.
Rose, D.P., Ratterman, M.E., Griffin, D.K., Hou, L., Kelley-Loughnane, N., Naik, R.R., Hagen,
J.A., Papautsky, I. and Heikenfeld, J.C., 2015. Adhesive RFID sensor patch for monitoring of
sweat electrolytes. IEEE Transactions on Biomedical Engineering, 62(6), pp.1457-1465.
Ruiz, A.R.J., Granja, F.S., Honorato, J.C.P. and Rosas, J.I.G., 2012. Accurate pedestrian indoor
navigation by tightly coupling foot-mounted IMU and RFID measurements. IEEE Transactions
on Instrumentation and Measurement, 61(1), pp.178-189.
Sarkka, S., Viikari, V.V., Huusko, M. and Jaakkola, K., 2012. Phase-based UHF RFID tracking
with nonlinear Kalman filtering and smoothing. IEEE Sensors Journal, 12(5), pp.904-910.
Saunders, M., Lewis, P. and Thornhill, A., 2009. Research Onion. Research methods for
business students, pp.39-64.
Schneider, C.W., Tautz, J., Grünewald, B. and Fuchs, S., 2012. RFID tracking of sublethal
effects of two neonicotinoid insecticides on the foraging behavior of Apis mellifera. PloS
one, 7(1), p.e30023.
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Park, S. and Lee, H., 2013. Self-recognition of vehicle position using UHF passive RFID
tags. IEEE Transactions on Industrial Electronics, 60(1), pp.226-234.
Potyrailo, R.A., Nagraj, N., Tang, Z., Mondello, F.J., Surman, C. and Morris, W., 2012.
Battery-free radio frequency identification (RFID) sensors for food quality and safety. Journal
of agricultural and food chemistry, 60(35), p.8535.
Ransford, B., Sorber, J. and Fu, K., 2012. Mementos: System support for long-running
computation on RFID-scale devices. Acm Sigplan Notices, 47(4), pp.159-170.
Rose, D.P., Ratterman, M.E., Griffin, D.K., Hou, L., Kelley-Loughnane, N., Naik, R.R., Hagen,
J.A., Papautsky, I. and Heikenfeld, J.C., 2015. Adhesive RFID sensor patch for monitoring of
sweat electrolytes. IEEE Transactions on Biomedical Engineering, 62(6), pp.1457-1465.
Ruiz, A.R.J., Granja, F.S., Honorato, J.C.P. and Rosas, J.I.G., 2012. Accurate pedestrian indoor
navigation by tightly coupling foot-mounted IMU and RFID measurements. IEEE Transactions
on Instrumentation and Measurement, 61(1), pp.178-189.
Sarkka, S., Viikari, V.V., Huusko, M. and Jaakkola, K., 2012. Phase-based UHF RFID tracking
with nonlinear Kalman filtering and smoothing. IEEE Sensors Journal, 12(5), pp.904-910.
Saunders, M., Lewis, P. and Thornhill, A., 2009. Research Onion. Research methods for
business students, pp.39-64.
Schneider, C.W., Tautz, J., Grünewald, B. and Fuchs, S., 2012. RFID tracking of sublethal
effects of two neonicotinoid insecticides on the foraging behavior of Apis mellifera. PloS
one, 7(1), p.e30023.

86RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Shahzad, M. and Liu, A.X., 2012, August. Every bit counts: Fast and scalable RFID estimation.
In Proceedings of the 18th annual international conference on Mobile computing and
networking (pp. 365-376). ACM.
Shirehjini, A.A.N., Yassine, A. and Shirmohammadi, S., 2012. An RFID-based position and
orientation measurement system for mobile objects in intelligent environments. IEEE
Transactions on Instrumentation and Measurement, 61(6), pp.1664-1675.
Silverman, D. ed., 2016. Qualitative research. Sage, pp. 2-43.
Slater, M.J., Evans, A.L. and Turner, M.J., 2016. Implementing a social identity approach for
effective change management. Journal of Change Management, 16(1), pp.18-37.
Smith, J.A. ed., 2015. Qualitative psychology: A practical guide to research methods. Sage.
Sun, C., 2012. Application of RFID technology for logistics on internet of things. AASRI
Procedia, 1, pp.106-111.
Tan, Z., Daamen, R., Humbert, A., Ponomarev, Y.V., Chae, Y. and Pertijs, M.A., 2013. A 1.2-V
8.3-nJ CMOS humidity sensor for RFID applications. IEEE Journal of Solid-State
Circuits, 48(10), pp.2469-2477.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons.
Thomas, S.J., Wheeler, E., Teizer, J. and Reynolds, M.S., 2012. Quadrature amplitude
modulated backscatter in passive and semipassive UHF RFID systems. IEEE Transactions on
Microwave Theory and Techniques, 60(4), pp.1175-1182.
Shahzad, M. and Liu, A.X., 2012, August. Every bit counts: Fast and scalable RFID estimation.
In Proceedings of the 18th annual international conference on Mobile computing and
networking (pp. 365-376). ACM.
Shirehjini, A.A.N., Yassine, A. and Shirmohammadi, S., 2012. An RFID-based position and
orientation measurement system for mobile objects in intelligent environments. IEEE
Transactions on Instrumentation and Measurement, 61(6), pp.1664-1675.
Silverman, D. ed., 2016. Qualitative research. Sage, pp. 2-43.
Slater, M.J., Evans, A.L. and Turner, M.J., 2016. Implementing a social identity approach for
effective change management. Journal of Change Management, 16(1), pp.18-37.
Smith, J.A. ed., 2015. Qualitative psychology: A practical guide to research methods. Sage.
Sun, C., 2012. Application of RFID technology for logistics on internet of things. AASRI
Procedia, 1, pp.106-111.
Tan, Z., Daamen, R., Humbert, A., Ponomarev, Y.V., Chae, Y. and Pertijs, M.A., 2013. A 1.2-V
8.3-nJ CMOS humidity sensor for RFID applications. IEEE Journal of Solid-State
Circuits, 48(10), pp.2469-2477.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons.
Thomas, S.J., Wheeler, E., Teizer, J. and Reynolds, M.S., 2012. Quadrature amplitude
modulated backscatter in passive and semipassive UHF RFID systems. IEEE Transactions on
Microwave Theory and Techniques, 60(4), pp.1175-1182.

87RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Tian, Y., Chen, G. and Li, J., 2012. A new ultralightweight RFID authentication protocol with
permutation. IEEE Communications Letters, 16(5), pp.702-705.
Varadhan, C., Pakkathillam, J.K., Kanagasabai, M., Sivasamy, R., Natarajan, R. and
Palaniswamy, S.K., 2013. Triband antenna structures for RFID systems deploying fractal
geometry. IEEE antennas and wireless propagation letters, 12, pp.437-440.
Vena, A., Perret, E. and Tedjini, S., 2012. High-capacity chipless RFID tag insensitive to the
polarization. IEEE Transactions on Antennas and Propagation, 60(10), pp.4509-4515.
Vena, A., Perret, E. and Tedjni, S., 2013. A depolarizing chipless RFID tag for robust detection
and its FCC compliant UWB reading system. IEEE transactions on microwave theory and
techniques, 61(8), pp.2982-2994.
Vena, A., Perret, E. and Tedjini, S., 2012. A fully printable chipless RFID tag with detuning
correction technique. IEEE Microwave and Wireless Components Letters, 22(4), pp.209-211.
Viani, F., Salucci, M., Robol, F., Oliveri, G. and Massa, A., 2012. Design of a UHF RFID/GPS
fractal antenna for logistics management. Journal of Electromagnetic Waves and
Applications, 26(4), pp.480-492.
Wamba, S.F., 2012. RFID-enabled healthcare applications, issues and benefits: An archival
analysis (1997–2011). Journal of medical systems, 36(6), pp.3393-3398.
Wamba, S.F., Anand, A. and Carter, L., 2013. A literature review of RFID-enabled healthcare
applications and issues. International Journal of Information Management, 33(5), pp.875-891.
Tian, Y., Chen, G. and Li, J., 2012. A new ultralightweight RFID authentication protocol with
permutation. IEEE Communications Letters, 16(5), pp.702-705.
Varadhan, C., Pakkathillam, J.K., Kanagasabai, M., Sivasamy, R., Natarajan, R. and
Palaniswamy, S.K., 2013. Triband antenna structures for RFID systems deploying fractal
geometry. IEEE antennas and wireless propagation letters, 12, pp.437-440.
Vena, A., Perret, E. and Tedjini, S., 2012. High-capacity chipless RFID tag insensitive to the
polarization. IEEE Transactions on Antennas and Propagation, 60(10), pp.4509-4515.
Vena, A., Perret, E. and Tedjni, S., 2013. A depolarizing chipless RFID tag for robust detection
and its FCC compliant UWB reading system. IEEE transactions on microwave theory and
techniques, 61(8), pp.2982-2994.
Vena, A., Perret, E. and Tedjini, S., 2012. A fully printable chipless RFID tag with detuning
correction technique. IEEE Microwave and Wireless Components Letters, 22(4), pp.209-211.
Viani, F., Salucci, M., Robol, F., Oliveri, G. and Massa, A., 2012. Design of a UHF RFID/GPS
fractal antenna for logistics management. Journal of Electromagnetic Waves and
Applications, 26(4), pp.480-492.
Wamba, S.F., 2012. RFID-enabled healthcare applications, issues and benefits: An archival
analysis (1997–2011). Journal of medical systems, 36(6), pp.3393-3398.
Wamba, S.F., Anand, A. and Carter, L., 2013. A literature review of RFID-enabled healthcare
applications and issues. International Journal of Information Management, 33(5), pp.875-891.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

88RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Wang, J. and Katabi, D., 2013. Dude, where's my card?: RFID positioning that works with
multipath and non-line of sight. ACM SIGCOMM Computer Communication Review, 43(4),
pp.51-62.
Wang, L., Da Xu, L., Bi, Z. and Xu, Y., 2014. Data cleaning for RFID and WSN
integration. IEEE transactions on industrial informatics, 10(1), pp.408-418.
Wu, H., Zeng, Y., Feng, J. and Gu, Y., 2013. Binary tree slotted ALOHA for passive RFID tag
anticollision. IEEE Transactions on Parallel and Distributed Systems, 24(1), pp.19-31.
Wu, T., Su, H., Gan, L., Chen, H., Huang, J. and Zhang, H., 2013. A compact and broadband
microstrip stacked patch antenna with circular polarization for 2.45-GHz mobile RFID
reader. IEEE Antennas and Wireless Propagation Letters, 12, pp.623-626.
Yang, L., Chen, Y., Li, X.Y., Xiao, C., Li, M. and Liu, Y., 2014, September. Tagoram: Real-
time tracking of mobile RFID tags to high precision using COTS devices. In Proceedings of the
20th annual international conference on Mobile computing and networking (pp. 237-248).
ACM.
Yang, P., Wu, W., Moniri, M. and Chibelushi, C.C., 2013. Efficient object localization using
sparsely distributed passive RFID tags. IEEE transactions on industrial electronics, 60(12),
pp.5914-5924.
Yao, W., Chu, C.H. and Li, Z., 2012. The adoption and implementation of RFID technologies in
healthcare: a literature review. Journal of medical systems, 36(6), pp.3507-3525.
Yoon, E.J., 2012. Improvement of the securing RFID systems conforming to EPC class 1
generation 2 standard. Expert Systems with Applications, 39(1), pp.1589-1594.
Wang, J. and Katabi, D., 2013. Dude, where's my card?: RFID positioning that works with
multipath and non-line of sight. ACM SIGCOMM Computer Communication Review, 43(4),
pp.51-62.
Wang, L., Da Xu, L., Bi, Z. and Xu, Y., 2014. Data cleaning for RFID and WSN
integration. IEEE transactions on industrial informatics, 10(1), pp.408-418.
Wu, H., Zeng, Y., Feng, J. and Gu, Y., 2013. Binary tree slotted ALOHA for passive RFID tag
anticollision. IEEE Transactions on Parallel and Distributed Systems, 24(1), pp.19-31.
Wu, T., Su, H., Gan, L., Chen, H., Huang, J. and Zhang, H., 2013. A compact and broadband
microstrip stacked patch antenna with circular polarization for 2.45-GHz mobile RFID
reader. IEEE Antennas and Wireless Propagation Letters, 12, pp.623-626.
Yang, L., Chen, Y., Li, X.Y., Xiao, C., Li, M. and Liu, Y., 2014, September. Tagoram: Real-
time tracking of mobile RFID tags to high precision using COTS devices. In Proceedings of the
20th annual international conference on Mobile computing and networking (pp. 237-248).
ACM.
Yang, P., Wu, W., Moniri, M. and Chibelushi, C.C., 2013. Efficient object localization using
sparsely distributed passive RFID tags. IEEE transactions on industrial electronics, 60(12),
pp.5914-5924.
Yao, W., Chu, C.H. and Li, Z., 2012. The adoption and implementation of RFID technologies in
healthcare: a literature review. Journal of medical systems, 36(6), pp.3507-3525.
Yoon, E.J., 2012. Improvement of the securing RFID systems conforming to EPC class 1
generation 2 standard. Expert Systems with Applications, 39(1), pp.1589-1594.

89RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Yu, Y.C., Hou, T.W. and Chiang, T.C., 2012. Low cost RFID real lightweight binding proof
protocol for medication errors and patient safety. Journal of medical systems, 36(2), pp.823-
828.
Zheng, Y. and Li, M., 2013. Fast tag searching protocol for large-scale RFID
systems. IEEE/ACM Transactions on Networking (TON), 21(3), pp.924-934.
Zheng, Y. and Li, M., 2012. PET: Probabilistic estimating tree for large-scale RFID
estimation. IEEE Transactions on Mobile Computing, 11(11), pp.1763-1774.
Zheng, Y. and Li, M., 2013, April. ZOE: Fast cardinality estimation for large-scale RFID
systems. In INFOCOM, 2013 Proceedings IEEE (pp. 908-916). IEEE.
Zhong, R.Y., Dai, Q.Y., Qu, T., Hu, G.J. and Huang, G.Q., 2013. RFID-enabled real-time
manufacturing execution system for mass-customization production. Robotics and Computer-
Integrated Manufacturing, 29(2), pp.283-292.
Zhong, R.Y., Huang, G.Q., Lan, S., Dai, Q.Y., Chen, X. and Zhang, T., 2015. A big data
approach for logistics trajectory discovery from RFID-enabled production data. International
Journal of Production Economics, 165, pp.260-272.
Zhu, X., Mukhopadhyay, S.K. and Kurata, H., 2012. A review of RFID technology and its
managerial applications in different industries. Journal of Engineering and Technology
Management, 29(1), pp.152-167.
Yu, Y.C., Hou, T.W. and Chiang, T.C., 2012. Low cost RFID real lightweight binding proof
protocol for medication errors and patient safety. Journal of medical systems, 36(2), pp.823-
828.
Zheng, Y. and Li, M., 2013. Fast tag searching protocol for large-scale RFID
systems. IEEE/ACM Transactions on Networking (TON), 21(3), pp.924-934.
Zheng, Y. and Li, M., 2012. PET: Probabilistic estimating tree for large-scale RFID
estimation. IEEE Transactions on Mobile Computing, 11(11), pp.1763-1774.
Zheng, Y. and Li, M., 2013, April. ZOE: Fast cardinality estimation for large-scale RFID
systems. In INFOCOM, 2013 Proceedings IEEE (pp. 908-916). IEEE.
Zhong, R.Y., Dai, Q.Y., Qu, T., Hu, G.J. and Huang, G.Q., 2013. RFID-enabled real-time
manufacturing execution system for mass-customization production. Robotics and Computer-
Integrated Manufacturing, 29(2), pp.283-292.
Zhong, R.Y., Huang, G.Q., Lan, S., Dai, Q.Y., Chen, X. and Zhang, T., 2015. A big data
approach for logistics trajectory discovery from RFID-enabled production data. International
Journal of Production Economics, 165, pp.260-272.
Zhu, X., Mukhopadhyay, S.K. and Kurata, H., 2012. A review of RFID technology and its
managerial applications in different industries. Journal of Engineering and Technology
Management, 29(1), pp.152-167.

90RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Bibliography
Alomair, B., Clark, A., Cuellar, J. and Poovendran, R., 2012. Scalable RFID systems: a privacy-
preserving protocol with constant-time identification. IEEE Transactions on Parallel and
Distributed Systems, 23(8), pp.1536-1550.
Amendola, S., Lodato, R., Manzari, S., Occhiuzzi, C. and Marrocco, G., 2014. RFID technology
for IoT-based personal healthcare in smart spaces. IEEE Internet of Things Journal, 1(2),
pp.144-152.
Arulogun, O.T., Olatunbosun, A., Fakolujo, O.A. and Olaniyi, O.M., 2013. RFID-based students
attendance management system. International Journal of Scientific & Engineering
Research, 4(2), pp.1-9.
Asadzadeh, P., Kulik, L. and Tanin, E., 2012. Gesture recognition using RFID
technology. Personal and Ubiquitous Computing, 16(3), pp.225-234.
Athalye, A., Savic, V., Bolic, M. and Djuric, P.M., 2013. Novel semi-passive RFID system for
indoor localization. IEEE Sensors Journal, 13(2), pp.528-537.
Attaran, M., 2012. Critical success factors and challenges of implementing RFID in supply chain
management. Journal of supply chain and operations management, 10(1), pp.144-167.
Babar, A.A., Bjorninen, T., Bhagavati, V.A., Sydanheimo, L., Kallio, P. and Ukkonen, L., 2012.
Small and flexible metal mountable passive UHF RFID tag on high-dielectric polymer-ceramic
composite substrate. IEEE Antennas and Wireless Propagation Letters, 11, pp.1319-1322.
Bibliography
Alomair, B., Clark, A., Cuellar, J. and Poovendran, R., 2012. Scalable RFID systems: a privacy-
preserving protocol with constant-time identification. IEEE Transactions on Parallel and
Distributed Systems, 23(8), pp.1536-1550.
Amendola, S., Lodato, R., Manzari, S., Occhiuzzi, C. and Marrocco, G., 2014. RFID technology
for IoT-based personal healthcare in smart spaces. IEEE Internet of Things Journal, 1(2),
pp.144-152.
Arulogun, O.T., Olatunbosun, A., Fakolujo, O.A. and Olaniyi, O.M., 2013. RFID-based students
attendance management system. International Journal of Scientific & Engineering
Research, 4(2), pp.1-9.
Asadzadeh, P., Kulik, L. and Tanin, E., 2012. Gesture recognition using RFID
technology. Personal and Ubiquitous Computing, 16(3), pp.225-234.
Athalye, A., Savic, V., Bolic, M. and Djuric, P.M., 2013. Novel semi-passive RFID system for
indoor localization. IEEE Sensors Journal, 13(2), pp.528-537.
Attaran, M., 2012. Critical success factors and challenges of implementing RFID in supply chain
management. Journal of supply chain and operations management, 10(1), pp.144-167.
Babar, A.A., Bjorninen, T., Bhagavati, V.A., Sydanheimo, L., Kallio, P. and Ukkonen, L., 2012.
Small and flexible metal mountable passive UHF RFID tag on high-dielectric polymer-ceramic
composite substrate. IEEE Antennas and Wireless Propagation Letters, 11, pp.1319-1322.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

91RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Bertoncini, C., Rudd, K., Nousain, B. and Hinders, M., 2012. Wavelet fingerprinting of radio-
frequency identification (RFID) tags. IEEE Transactions on Industrial Electronics, 59(12),
pp.4843-4850.
Boyer, C. and Roy, S., 2014. —Invited Paper—Backscatter Communication and RFID: Coding,
Energy, and MIMO Analysis. IEEE Transactions on Communications, 62(3), pp.770-785.
Bueno-Delgado, M.V., Ferrero, R., Gandino, F., Pavon-Marino, P. and Rebaudengo, M., 2013. A
geometric distribution reader anti-collision protocol for RFID dense reader environments. IEEE
Transactions on Automation Science and Engineering, 10(2), pp.296-306.
Casula, G.A., Montisci, G. and Mazzarella, G., 2013. A wideband PET inkjet-printed antenna for
UHF RFID. IEEE Antennas and Wireless Propagation Letters, 12, pp.1400-1403.
Catarinucci, L., De Donno, D., Colella, R., Ricciato, F. and Tarricone, L., 2012. A cost-effective
SDR platform for performance characterization of RFID tags. IEEE Transactions on
Instrumentation and Measurement, 61(4), pp.903-911.
Catarinucci, L., Colella, R. and Tarricone, L., 2013. Enhanced UHF RFID sensor-tag. IEEE
Microwave and Wireless Components Letters, 23(1), pp.49-51.
Chae, H.J., Salajegheh, M., Yeager, D.J., Smith, J.R. and Fu, K., 2013. Maximalist cryptography
and computation on the WISP UHF RFID tag. In Wirelessly Powered Sensor Networks and
Computational RFID (pp. 175-187). Springer New York.
Chen, J.C., Cheng, C.H. and Huang, P.B., 2013. Supply chain management with lean production
and RFID application: A case study. Expert Systems with Applications, 40(9), pp.3389-3397.
Bertoncini, C., Rudd, K., Nousain, B. and Hinders, M., 2012. Wavelet fingerprinting of radio-
frequency identification (RFID) tags. IEEE Transactions on Industrial Electronics, 59(12),
pp.4843-4850.
Boyer, C. and Roy, S., 2014. —Invited Paper—Backscatter Communication and RFID: Coding,
Energy, and MIMO Analysis. IEEE Transactions on Communications, 62(3), pp.770-785.
Bueno-Delgado, M.V., Ferrero, R., Gandino, F., Pavon-Marino, P. and Rebaudengo, M., 2013. A
geometric distribution reader anti-collision protocol for RFID dense reader environments. IEEE
Transactions on Automation Science and Engineering, 10(2), pp.296-306.
Casula, G.A., Montisci, G. and Mazzarella, G., 2013. A wideband PET inkjet-printed antenna for
UHF RFID. IEEE Antennas and Wireless Propagation Letters, 12, pp.1400-1403.
Catarinucci, L., De Donno, D., Colella, R., Ricciato, F. and Tarricone, L., 2012. A cost-effective
SDR platform for performance characterization of RFID tags. IEEE Transactions on
Instrumentation and Measurement, 61(4), pp.903-911.
Catarinucci, L., Colella, R. and Tarricone, L., 2013. Enhanced UHF RFID sensor-tag. IEEE
Microwave and Wireless Components Letters, 23(1), pp.49-51.
Chae, H.J., Salajegheh, M., Yeager, D.J., Smith, J.R. and Fu, K., 2013. Maximalist cryptography
and computation on the WISP UHF RFID tag. In Wirelessly Powered Sensor Networks and
Computational RFID (pp. 175-187). Springer New York.
Chen, J.C., Cheng, C.H. and Huang, P.B., 2013. Supply chain management with lean production
and RFID application: A case study. Expert Systems with Applications, 40(9), pp.3389-3397.

92RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Chen, H.D., Kuo, S.H. and Tsai, C.H., 2012. Coupling-feed circularly polarized RFID tag
antenna mountable on metallic surface. IEEE Transactions on Antennas and Propagation, 60(5),
pp.2166-2174.
Chong, A.Y.L. and Chan, F.T., 2012. Structural equation modeling for multi-stage analysis on
Radio Frequency Identification (RFID) diffusion in the health care industry. Expert Systems with
Applications, 39(10), pp.8645-8654.
Condea, C., Thiesse, F. and Fleisch, E., 2012. RFID-enabled shelf replenishment with backroom
monitoring in retail stores. Decision Support Systems, 52(4), pp.839-849.
Costa, C., Antonucci, F., Pallottino, F., Aguzzi, J., Sarriá, D. and Menesatti, P., 2013. A review
on agri-food supply chain traceability by means of RFID technology. Food and Bioprocess
Technology, 6(2), pp.353-366.
Costa, F., Genovesi, S. and Monorchio, A., 2013. A chipless RFID based on multiresonant high-
impedance surfaces. IEEE transactions on microwave theory and techniques, 61(1), pp.146-153.
Costin, A., Pradhananga, N. and Teizer, J., 2012. Leveraging passive RFID technology for
construction resource field mobility and status monitoring in a high-rise renovation
project. Automation in Construction, 24, pp.1-15.
Coustasse, A., Tomblin, S. and Slack, C., 2013. Impact of radio-frequency identification (RFID)
technologies on the hospital supply chain: a literature review. Perspectives in Health Information
Management, 10(Fall).
Chen, H.D., Kuo, S.H. and Tsai, C.H., 2012. Coupling-feed circularly polarized RFID tag
antenna mountable on metallic surface. IEEE Transactions on Antennas and Propagation, 60(5),
pp.2166-2174.
Chong, A.Y.L. and Chan, F.T., 2012. Structural equation modeling for multi-stage analysis on
Radio Frequency Identification (RFID) diffusion in the health care industry. Expert Systems with
Applications, 39(10), pp.8645-8654.
Condea, C., Thiesse, F. and Fleisch, E., 2012. RFID-enabled shelf replenishment with backroom
monitoring in retail stores. Decision Support Systems, 52(4), pp.839-849.
Costa, C., Antonucci, F., Pallottino, F., Aguzzi, J., Sarriá, D. and Menesatti, P., 2013. A review
on agri-food supply chain traceability by means of RFID technology. Food and Bioprocess
Technology, 6(2), pp.353-366.
Costa, F., Genovesi, S. and Monorchio, A., 2013. A chipless RFID based on multiresonant high-
impedance surfaces. IEEE transactions on microwave theory and techniques, 61(1), pp.146-153.
Costin, A., Pradhananga, N. and Teizer, J., 2012. Leveraging passive RFID technology for
construction resource field mobility and status monitoring in a high-rise renovation
project. Automation in Construction, 24, pp.1-15.
Coustasse, A., Tomblin, S. and Slack, C., 2013. Impact of radio-frequency identification (RFID)
technologies on the hospital supply chain: a literature review. Perspectives in Health Information
Management, 10(Fall).

93RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Dai, H. and Tseng, M.M., 2012. The impacts of RFID implementation on reducing inventory
inaccuracy in a multi-stage supply chain. International Journal of Production
Economics, 139(2), pp.634-641.
De Donno, D., Catarinucci, L. and Tarricone, L., 2013. An UHF RFID energy-harvesting system
enhanced by a DC-DC charge pump in silicon-on-insulator technology. IEEE Microwave and
Wireless Components Letters, 23(6), pp.315-317.
De Donno, D., Catarinucci, L. and Tarricone, L., 2014. RAMSES: RFID augmented module for
smart environmental sensing. IEEE Transactions on Instrumentation and Measurement, 63(7),
pp.1701-1708.
De Donno, D., Catarinucci, L. and Tarricone, L., 2014. A battery-assisted sensor-enhanced RFID
tag enabling heterogeneous wireless sensor networks. IEEE Sensors Journal, 14(4), pp.1048-
1055.
De Marco, A., Cagliano, A.C., Nervo, M.L. and Rafele, C., 2012. Using System Dynamics to
assess the impact of RFID technology on retail operations. International journal of production
economics, 135(1), pp.333-344.
DiGiampaolo, E. and Martinelli, F., 2012. A passive UHF-RFID system for the localization of an
indoor autonomous vehicle. IEEE Transactions on Industrial Electronics, 59(10), pp.3961-3970.
DiGiampaolo, E. and Martinelli, F., 2014. Mobile robot localization using the phase of passive
UHF RFID signals. IEEE Transactions on Industrial Electronics, 61(1), pp.365-376.
Dobkin, D.M., 2012. The rf in RFID: uhf RFID in practice. Newnes.
Dai, H. and Tseng, M.M., 2012. The impacts of RFID implementation on reducing inventory
inaccuracy in a multi-stage supply chain. International Journal of Production
Economics, 139(2), pp.634-641.
De Donno, D., Catarinucci, L. and Tarricone, L., 2013. An UHF RFID energy-harvesting system
enhanced by a DC-DC charge pump in silicon-on-insulator technology. IEEE Microwave and
Wireless Components Letters, 23(6), pp.315-317.
De Donno, D., Catarinucci, L. and Tarricone, L., 2014. RAMSES: RFID augmented module for
smart environmental sensing. IEEE Transactions on Instrumentation and Measurement, 63(7),
pp.1701-1708.
De Donno, D., Catarinucci, L. and Tarricone, L., 2014. A battery-assisted sensor-enhanced RFID
tag enabling heterogeneous wireless sensor networks. IEEE Sensors Journal, 14(4), pp.1048-
1055.
De Marco, A., Cagliano, A.C., Nervo, M.L. and Rafele, C., 2012. Using System Dynamics to
assess the impact of RFID technology on retail operations. International journal of production
economics, 135(1), pp.333-344.
DiGiampaolo, E. and Martinelli, F., 2012. A passive UHF-RFID system for the localization of an
indoor autonomous vehicle. IEEE Transactions on Industrial Electronics, 59(10), pp.3961-3970.
DiGiampaolo, E. and Martinelli, F., 2014. Mobile robot localization using the phase of passive
UHF RFID signals. IEEE Transactions on Industrial Electronics, 61(1), pp.365-376.
Dobkin, D.M., 2012. The rf in RFID: uhf RFID in practice. Newnes.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

94RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Dominguez-Péry, C., Ageron, B. and Neubert, G., 2013. A service science framework to enhance
value creation in service innovation projects. An RFID case study. International Journal of
Production Economics, 141(2), pp.440-451.
Doss, R., Sundaresan, S. and Zhou, W., 2013. A practical quadratic residues based scheme for
authentication and privacy in mobile RFID systems. Ad Hoc Networks, 11(1), pp.383-396.
Dwivedi, Y.K., Kapoor, K.K., Williams, M.D. and Williams, J., 2013. RFID systems in libraries:
An empirical examination of factors affecting system use and user satisfaction. International
Journal of Information Management, 33(2), pp.367-377.
Fabian, B., Ermakova, T. and Muller, C., 2012. SHARDIS: A privacy-enhanced discovery
service for RFID-based product information. IEEE Transactions on Industrial Informatics, 8(3),
pp.707-718.
Fan, T.J., Chang, X.Y., Gu, C.H., Yi, J.J. and Deng, S., 2014. Benefits of RFID technology for
reducing inventory shrinkage. International Journal of Production Economics, 147, pp.659-665.
Feng, J., Fu, Z., Wang, Z., Xu, M. and Zhang, X., 2013. Development and evaluation on a RFID-
based traceability system for cattle/beef quality safety in China. Food control, 31(2), pp.314-325.
Finkenzeller, K., 2015. RFID-Handbuch: Grundlagen und praktische Anwendungen von
Transpondern, kontaktlosen Chipkarten und NFC. Carl Hanser Verlag GmbH Co KG.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage, pp.7-19.
Dominguez-Péry, C., Ageron, B. and Neubert, G., 2013. A service science framework to enhance
value creation in service innovation projects. An RFID case study. International Journal of
Production Economics, 141(2), pp.440-451.
Doss, R., Sundaresan, S. and Zhou, W., 2013. A practical quadratic residues based scheme for
authentication and privacy in mobile RFID systems. Ad Hoc Networks, 11(1), pp.383-396.
Dwivedi, Y.K., Kapoor, K.K., Williams, M.D. and Williams, J., 2013. RFID systems in libraries:
An empirical examination of factors affecting system use and user satisfaction. International
Journal of Information Management, 33(2), pp.367-377.
Fabian, B., Ermakova, T. and Muller, C., 2012. SHARDIS: A privacy-enhanced discovery
service for RFID-based product information. IEEE Transactions on Industrial Informatics, 8(3),
pp.707-718.
Fan, T.J., Chang, X.Y., Gu, C.H., Yi, J.J. and Deng, S., 2014. Benefits of RFID technology for
reducing inventory shrinkage. International Journal of Production Economics, 147, pp.659-665.
Feng, J., Fu, Z., Wang, Z., Xu, M. and Zhang, X., 2013. Development and evaluation on a RFID-
based traceability system for cattle/beef quality safety in China. Food control, 31(2), pp.314-325.
Finkenzeller, K., 2015. RFID-Handbuch: Grundlagen und praktische Anwendungen von
Transpondern, kontaktlosen Chipkarten und NFC. Carl Hanser Verlag GmbH Co KG.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage, pp.7-19.

95RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Fosso Wamba, S., 2012. Achieving supply chain integration using RFID technology: the case of
emerging intelligent B-to-B e-commerce processes in a living laboratory. Business Process
Management Journal, 18(1), pp.58-81.
Frankland, R., Mitchell, C.M., Ferguson, J.D., Sziklai, A.T., Verma, A.K., Popowski, J.E. and
Sturgeon, D.H., Applications In Internet Time, Llc, 2013. Integrated change management unit.
U.S. Patent 8,484,111.
Gast, D.L. and Ledford, J.R., 2014. Single case research methodology: Applications in special
education and behavioral sciences. Routledge.
Girbau, D., Ramos, Á., Lazaro, A., Rima, S. and Villarino, R., 2012. Passive wireless
temperature sensor based on time-coded UWB chipless RFID tags. IEEE Transactions on
Microwave Theory and Techniques, 60(11), pp.3623-3632.
Girbau, D., Lorenzo, J., Lazaro, A., Ferrater, C. and Villarino, R., 2012. Frequency-coded
chipless RFID tag based on dual-band resonators. IEEE Antennas and Wireless Propagation
Letters, 11, pp.126-128.
Gong, Y.J., Shen, M., Zhang, J., Kaynak, O., Chen, W.N. and Zhan, Z.H., 2012. Optimizing
RFID network planning by using a particle swarm optimization algorithm with redundant reader
elimination. IEEE Transactions on Industrial Informatics, 8(4), pp.900-912.
He, D. and Zeadally, S., 2015. An analysis of rfid authentication schemes for internet of things in
healthcare environment using elliptic curve cryptography. IEEE internet of things journal, 2(1),
pp.72-83.
Fosso Wamba, S., 2012. Achieving supply chain integration using RFID technology: the case of
emerging intelligent B-to-B e-commerce processes in a living laboratory. Business Process
Management Journal, 18(1), pp.58-81.
Frankland, R., Mitchell, C.M., Ferguson, J.D., Sziklai, A.T., Verma, A.K., Popowski, J.E. and
Sturgeon, D.H., Applications In Internet Time, Llc, 2013. Integrated change management unit.
U.S. Patent 8,484,111.
Gast, D.L. and Ledford, J.R., 2014. Single case research methodology: Applications in special
education and behavioral sciences. Routledge.
Girbau, D., Ramos, Á., Lazaro, A., Rima, S. and Villarino, R., 2012. Passive wireless
temperature sensor based on time-coded UWB chipless RFID tags. IEEE Transactions on
Microwave Theory and Techniques, 60(11), pp.3623-3632.
Girbau, D., Lorenzo, J., Lazaro, A., Ferrater, C. and Villarino, R., 2012. Frequency-coded
chipless RFID tag based on dual-band resonators. IEEE Antennas and Wireless Propagation
Letters, 11, pp.126-128.
Gong, Y.J., Shen, M., Zhang, J., Kaynak, O., Chen, W.N. and Zhan, Z.H., 2012. Optimizing
RFID network planning by using a particle swarm optimization algorithm with redundant reader
elimination. IEEE Transactions on Industrial Informatics, 8(4), pp.900-912.
He, D. and Zeadally, S., 2015. An analysis of rfid authentication schemes for internet of things in
healthcare environment using elliptic curve cryptography. IEEE internet of things journal, 2(1),
pp.72-83.

96RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Hohberger, C., Davis, R., Briggs, L., Gutierrez, A. and Veeramani, D., 2012. Applying radio-
frequency identification (RFID) technology in transfusion medicine. Biologicals, 40(3), pp.209-
213.
Islam, M.A. and Karmakar, N.C., 2012. A novel compact printable dual-polarized chipless RFID
system. IEEE Transactions on Microwave Theory and Techniques, 60(7), pp.2142-2151.
Jia, X., Feng, Q., Fan, T. and Lei, Q., 2012, April. RFID technology and its applications in
Internet of Things (IoT). In Consumer Electronics, Communications and Networks (CECNet),
2012 2nd International Conference on (pp. 1282-1285). IEEE.
Jia, X., Feng, Q. and Yu, L., 2012. Stability analysis of an efficient anti-collision protocol for
RFID tag identification. IEEE Transactions on Communications, 60(8), pp.2285-2294.
Jung, Y.K. and Lee, B., 2012. Dual-band circularly polarized microstrip RFID reader antenna
using metamaterial branch-line coupler. IEEE Transactions on Antennas and
Propagation, 60(2), pp.786-791.
Kapoor, G. and Piramuthu, S., 2012. Single RFID tag ownership transfer protocols. IEEE
Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 42(2),
pp.164-173.
Kassim, M., Mazlan, H., Zaini, N. and Salleh, M.K., 2012, July. Web-based student attendance
system using RFID technology. In Control and System Graduate Research Colloquium
(ICSGRC), 2012 IEEE (pp. 213-218). IEEE.
Hohberger, C., Davis, R., Briggs, L., Gutierrez, A. and Veeramani, D., 2012. Applying radio-
frequency identification (RFID) technology in transfusion medicine. Biologicals, 40(3), pp.209-
213.
Islam, M.A. and Karmakar, N.C., 2012. A novel compact printable dual-polarized chipless RFID
system. IEEE Transactions on Microwave Theory and Techniques, 60(7), pp.2142-2151.
Jia, X., Feng, Q., Fan, T. and Lei, Q., 2012, April. RFID technology and its applications in
Internet of Things (IoT). In Consumer Electronics, Communications and Networks (CECNet),
2012 2nd International Conference on (pp. 1282-1285). IEEE.
Jia, X., Feng, Q. and Yu, L., 2012. Stability analysis of an efficient anti-collision protocol for
RFID tag identification. IEEE Transactions on Communications, 60(8), pp.2285-2294.
Jung, Y.K. and Lee, B., 2012. Dual-band circularly polarized microstrip RFID reader antenna
using metamaterial branch-line coupler. IEEE Transactions on Antennas and
Propagation, 60(2), pp.786-791.
Kapoor, G. and Piramuthu, S., 2012. Single RFID tag ownership transfer protocols. IEEE
Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 42(2),
pp.164-173.
Kassim, M., Mazlan, H., Zaini, N. and Salleh, M.K., 2012, July. Web-based student attendance
system using RFID technology. In Control and System Graduate Research Colloquium
(ICSGRC), 2012 IEEE (pp. 213-218). IEEE.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

97RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Kim, Y., Lee, B., Yang, S., Byun, I., Jeong, I. and Cho, S.M., 2012. Use of copper ink for
fabricating conductive electrodes and RFID antenna tags by screen printing. Current Applied
Physics, 12(2), pp.473-478.
Kim, S.C., Jeong, Y.S. and Park, S.O., 2013. RFID-based indoor location tracking to ensure the
safety of the elderly in smart home environments. Personal and ubiquitous computing, 17(8),
pp.1699-1707.
Kim, S., Mariotti, C., Alimenti, F., Mezzanotte, P., Georgiadis, A., Collado, A., Roselli, L. and
Tentzeris, M.M., 2013. No battery required: Perpetual RFID-enabled wireless sensors for
cognitive intelligence applications. IEEE Microwave Magazine, 14(5), pp.66-77.
Kitsos, P. ed., 2016. Security in RFID and sensor networks. CRC Press.
Kubicki, S., Lepreux, S. and Kolski, C., 2012. RFID-driven situation awareness on TangiSense,
a table interacting with tangible objects. Personal and Ubiquitous Computing, 16(8), pp.1079-
1094.
Lee, C.F., Chien, H.Y. and Laih, C.S., 2012. Server‐less RFID authentication and searching
protocol with enhanced security. International Journal of Communication Systems, 25(3),
pp.376-385.
Lehpamer, H., 2012. RFID design principles. Artech House.
Li, N., Calis, G. and Becerik-Gerber, B., 2012. Measuring and monitoring occupancy with an
RFID based system for demand-driven HVAC operations. Automation in construction, 24,
pp.89-99.
Kim, Y., Lee, B., Yang, S., Byun, I., Jeong, I. and Cho, S.M., 2012. Use of copper ink for
fabricating conductive electrodes and RFID antenna tags by screen printing. Current Applied
Physics, 12(2), pp.473-478.
Kim, S.C., Jeong, Y.S. and Park, S.O., 2013. RFID-based indoor location tracking to ensure the
safety of the elderly in smart home environments. Personal and ubiquitous computing, 17(8),
pp.1699-1707.
Kim, S., Mariotti, C., Alimenti, F., Mezzanotte, P., Georgiadis, A., Collado, A., Roselli, L. and
Tentzeris, M.M., 2013. No battery required: Perpetual RFID-enabled wireless sensors for
cognitive intelligence applications. IEEE Microwave Magazine, 14(5), pp.66-77.
Kitsos, P. ed., 2016. Security in RFID and sensor networks. CRC Press.
Kubicki, S., Lepreux, S. and Kolski, C., 2012. RFID-driven situation awareness on TangiSense,
a table interacting with tangible objects. Personal and Ubiquitous Computing, 16(8), pp.1079-
1094.
Lee, C.F., Chien, H.Y. and Laih, C.S., 2012. Server‐less RFID authentication and searching
protocol with enhanced security. International Journal of Communication Systems, 25(3),
pp.376-385.
Lehpamer, H., 2012. RFID design principles. Artech House.
Li, N., Calis, G. and Becerik-Gerber, B., 2012. Measuring and monitoring occupancy with an
RFID based system for demand-driven HVAC operations. Automation in construction, 24,
pp.89-99.

98RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Liao, Y.P. and Hsiao, C.M., 2014. A secure ECC-based RFID authentication scheme integrated
with ID-verifier transfer protocol. Ad Hoc Networks, 18, pp.133-146.
Lim, M.K., Bahr, W. and Leung, S.C., 2013. RFID in the warehouse: A literature analysis
(1995–2010) of its applications, benefits, challenges and future trends. International Journal of
Production Economics, 145(1), pp.409-430.
Liu, T., Yang, L., Lin, Q., Guo, Y. and Liu, Y., 2014, April. Anchor-free backscatter positioning
for RFID tags with high accuracy. In INFOCOM, 2014 Proceedings IEEE (pp. 379-387). IEEE.
Lu, M.T., Lin, S.W. and Tzeng, G.H., 2013. Improving RFID adoption in Taiwan's healthcare
industry based on a DEMATEL technique with a hybrid MCDM model. Decision Support
Systems, 56, pp.259-269.
Luo, W., Chen, S., Li, T. and Qiao, Y., 2012, June. Probabilistic missing-tag detection and
energy-time tradeoff in large-scale RFID systems. In Proceedings of the thirteenth ACM
international symposium on Mobile Ad Hoc Networking and Computing (pp. 95-104). ACM.
Montaser, A. and Moselhi, O., 2014. RFID indoor location identification for construction
projects. Automation in Construction, 39, pp.167-179.
Nainan, S., Parekh, R. and Shah, T., 2013. RFID technology based attendance management
system. arXiv preprint arXiv:1306.5381.
Nair, R., Perret, E. and Tedjini, S., 2012, June. Temporal multi-frequency encoding technique for
chipless RFID applications. In Microwave Symposium Digest (MTT), 2012 IEEE MTT-S
International (pp. 1-3). IEEE.
Liao, Y.P. and Hsiao, C.M., 2014. A secure ECC-based RFID authentication scheme integrated
with ID-verifier transfer protocol. Ad Hoc Networks, 18, pp.133-146.
Lim, M.K., Bahr, W. and Leung, S.C., 2013. RFID in the warehouse: A literature analysis
(1995–2010) of its applications, benefits, challenges and future trends. International Journal of
Production Economics, 145(1), pp.409-430.
Liu, T., Yang, L., Lin, Q., Guo, Y. and Liu, Y., 2014, April. Anchor-free backscatter positioning
for RFID tags with high accuracy. In INFOCOM, 2014 Proceedings IEEE (pp. 379-387). IEEE.
Lu, M.T., Lin, S.W. and Tzeng, G.H., 2013. Improving RFID adoption in Taiwan's healthcare
industry based on a DEMATEL technique with a hybrid MCDM model. Decision Support
Systems, 56, pp.259-269.
Luo, W., Chen, S., Li, T. and Qiao, Y., 2012, June. Probabilistic missing-tag detection and
energy-time tradeoff in large-scale RFID systems. In Proceedings of the thirteenth ACM
international symposium on Mobile Ad Hoc Networking and Computing (pp. 95-104). ACM.
Montaser, A. and Moselhi, O., 2014. RFID indoor location identification for construction
projects. Automation in Construction, 39, pp.167-179.
Nainan, S., Parekh, R. and Shah, T., 2013. RFID technology based attendance management
system. arXiv preprint arXiv:1306.5381.
Nair, R., Perret, E. and Tedjini, S., 2012, June. Temporal multi-frequency encoding technique for
chipless RFID applications. In Microwave Symposium Digest (MTT), 2012 IEEE MTT-S
International (pp. 1-3). IEEE.

99RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Nativi, J.J. and Lee, S., 2012. Impact of RFID information-sharing strategies on a decentralized
supply chain with reverse logistics operations. International Journal of Production
Economics, 136(2), pp.366-377.
Ngai, E.W.T., Chau, D.C.K., Poon, J.K.L., Chan, A.Y.M., Chan, B.C.M. and Wu, W.W.S., 2012.
Implementing an RFID-based manufacturing process management system: Lessons learned and
success factors. Journal of Engineering and Technology Management, 29(1), pp.112-130.
Occhiuzzi, C., Caizzone, S. and Marrocco, G., 2013. Passive UHF RFID antennas for sensing
applications: Principles, methods, and classifcations. IEEE Antennas and Propagation
Magazine, 55(6), pp.14-34.
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Papetti, P., Costa, C., Antonucci, F., Figorilli, S., Solaini, S. and Menesatti, P., 2012. A RFID
web-based infotracing system for the artisanal Italian cheese quality traceability. Food
Control, 27(1), pp.234-241.
Park, S. and Lee, H., 2013. Self-recognition of vehicle position using UHF passive RFID
tags. IEEE Transactions on Industrial Electronics, 60(1), pp.226-234.
Piramuthu, S., Farahani, P. and Grunow, M., 2013. RFID-generated traceability for contaminated
product recall in perishable food supply networks. European Journal of Operational
Research, 225(2), pp.253-262.
Potyrailo, R.A., Nagraj, N., Tang, Z., Mondello, F.J., Surman, C. and Morris, W., 2012. Battery-
free radio frequency identification (RFID) sensors for food quality and safety. Journal of
agricultural and food chemistry, 60(35), p.8535.
Nativi, J.J. and Lee, S., 2012. Impact of RFID information-sharing strategies on a decentralized
supply chain with reverse logistics operations. International Journal of Production
Economics, 136(2), pp.366-377.
Ngai, E.W.T., Chau, D.C.K., Poon, J.K.L., Chan, A.Y.M., Chan, B.C.M. and Wu, W.W.S., 2012.
Implementing an RFID-based manufacturing process management system: Lessons learned and
success factors. Journal of Engineering and Technology Management, 29(1), pp.112-130.
Occhiuzzi, C., Caizzone, S. and Marrocco, G., 2013. Passive UHF RFID antennas for sensing
applications: Principles, methods, and classifcations. IEEE Antennas and Propagation
Magazine, 55(6), pp.14-34.
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Papetti, P., Costa, C., Antonucci, F., Figorilli, S., Solaini, S. and Menesatti, P., 2012. A RFID
web-based infotracing system for the artisanal Italian cheese quality traceability. Food
Control, 27(1), pp.234-241.
Park, S. and Lee, H., 2013. Self-recognition of vehicle position using UHF passive RFID
tags. IEEE Transactions on Industrial Electronics, 60(1), pp.226-234.
Piramuthu, S., Farahani, P. and Grunow, M., 2013. RFID-generated traceability for contaminated
product recall in perishable food supply networks. European Journal of Operational
Research, 225(2), pp.253-262.
Potyrailo, R.A., Nagraj, N., Tang, Z., Mondello, F.J., Surman, C. and Morris, W., 2012. Battery-
free radio frequency identification (RFID) sensors for food quality and safety. Journal of
agricultural and food chemistry, 60(35), p.8535.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

100RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Qian, J.P., Yang, X.T., Wu, X.M., Zhao, L., Fan, B.L. and Xing, B., 2012. A traceability system
incorporating 2D barcode and RFID technology for wheat flour mills. Computers and electronics
in agriculture, 89, pp.76-85.
Qu, T., Yang, H.D., Huang, G.Q., Zhang, Y.F., Luo, H. and Qin, W., 2012. A case of
implementing RFID-based real-time shop-floor material management for household electrical
appliance manufacturers. Journal of Intelligent Manufacturing, pp.1-14.
Ransford, B., Sorber, J. and Fu, K., 2012. Mementos: System support for long-running
computation on RFID-scale devices. Acm Sigplan Notices, 47(4), pp.159-170.
Rose, D.P., Ratterman, M.E., Griffin, D.K., Hou, L., Kelley-Loughnane, N., Naik, R.R., Hagen,
J.A., Papautsky, I. and Heikenfeld, J.C., 2015. Adhesive RFID sensor patch for monitoring of
sweat electrolytes. IEEE Transactions on Biomedical Engineering, 62(6), pp.1457-1465.
Ruiz, A.R.J., Granja, F.S., Honorato, J.C.P. and Rosas, J.I.G., 2012. Accurate pedestrian indoor
navigation by tightly coupling foot-mounted IMU and RFID measurements. IEEE Transactions
on Instrumentation and Measurement, 61(1), pp.178-189.
Sarkka, S., Viikari, V.V., Huusko, M. and Jaakkola, K., 2012. Phase-based UHF RFID tracking
with nonlinear Kalman filtering and smoothing. IEEE Sensors Journal, 12(5), pp.904-910.
Saunders, M., Lewis, P. and Thornhill, A., 2009. Research Onion. Research methods for
business students, pp.39-64.
Schneider, C.W., Tautz, J., Grünewald, B. and Fuchs, S., 2012. RFID tracking of sublethal
effects of two neonicotinoid insecticides on the foraging behavior of Apis mellifera. PloS
one, 7(1), p.e30023.
Qian, J.P., Yang, X.T., Wu, X.M., Zhao, L., Fan, B.L. and Xing, B., 2012. A traceability system
incorporating 2D barcode and RFID technology for wheat flour mills. Computers and electronics
in agriculture, 89, pp.76-85.
Qu, T., Yang, H.D., Huang, G.Q., Zhang, Y.F., Luo, H. and Qin, W., 2012. A case of
implementing RFID-based real-time shop-floor material management for household electrical
appliance manufacturers. Journal of Intelligent Manufacturing, pp.1-14.
Ransford, B., Sorber, J. and Fu, K., 2012. Mementos: System support for long-running
computation on RFID-scale devices. Acm Sigplan Notices, 47(4), pp.159-170.
Rose, D.P., Ratterman, M.E., Griffin, D.K., Hou, L., Kelley-Loughnane, N., Naik, R.R., Hagen,
J.A., Papautsky, I. and Heikenfeld, J.C., 2015. Adhesive RFID sensor patch for monitoring of
sweat electrolytes. IEEE Transactions on Biomedical Engineering, 62(6), pp.1457-1465.
Ruiz, A.R.J., Granja, F.S., Honorato, J.C.P. and Rosas, J.I.G., 2012. Accurate pedestrian indoor
navigation by tightly coupling foot-mounted IMU and RFID measurements. IEEE Transactions
on Instrumentation and Measurement, 61(1), pp.178-189.
Sarkka, S., Viikari, V.V., Huusko, M. and Jaakkola, K., 2012. Phase-based UHF RFID tracking
with nonlinear Kalman filtering and smoothing. IEEE Sensors Journal, 12(5), pp.904-910.
Saunders, M., Lewis, P. and Thornhill, A., 2009. Research Onion. Research methods for
business students, pp.39-64.
Schneider, C.W., Tautz, J., Grünewald, B. and Fuchs, S., 2012. RFID tracking of sublethal
effects of two neonicotinoid insecticides on the foraging behavior of Apis mellifera. PloS
one, 7(1), p.e30023.

101RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Shahzad, M. and Liu, A.X., 2012, August. Every bit counts: Fast and scalable RFID estimation.
In Proceedings of the 18th annual international conference on Mobile computing and
networking (pp. 365-376). ACM.
Shi, J., Qing, X., Chen, Z.N. and Goh, C.K., 2013. Electrically large dual-loop antenna for UHF
near-field RFID reader. IEEE Transactions on Antennas and Propagation, 61(3), pp.1019-1025.
Shirehjini, A.A.N., Yassine, A. and Shirmohammadi, S., 2012. An RFID-based position and
orientation measurement system for mobile objects in intelligent environments. IEEE
Transactions on Instrumentation and Measurement, 61(6), pp.1664-1675.
Shirehjini, A.A.N., Yassine, A. and Shirmohammadi, S., 2012. Equipment location in hospitals
using RFID-based positioning system. IEEE Transactions on information technology in
biomedicine, 16(6), pp.1058-1069.
Silverman, D. ed., 2016. Qualitative research. Sage, pp. 2-43.
Slater, M.J., Evans, A.L. and Turner, M.J., 2016. Implementing a social identity approach for
effective change management. Journal of Change Management, 16(1), pp.18-37.
Smith, J.R. ed., 2013. Wirelessly Powered Sensor Networks and Computational RFID. Springer
Science & Business Media.
Smith, J.A. ed., 2015. Qualitative psychology: A practical guide to research methods. Sage.
Sun, C., 2012. Application of RFID technology for logistics on internet of things. AASRI
Procedia, 1, pp.106-111.
Shahzad, M. and Liu, A.X., 2012, August. Every bit counts: Fast and scalable RFID estimation.
In Proceedings of the 18th annual international conference on Mobile computing and
networking (pp. 365-376). ACM.
Shi, J., Qing, X., Chen, Z.N. and Goh, C.K., 2013. Electrically large dual-loop antenna for UHF
near-field RFID reader. IEEE Transactions on Antennas and Propagation, 61(3), pp.1019-1025.
Shirehjini, A.A.N., Yassine, A. and Shirmohammadi, S., 2012. An RFID-based position and
orientation measurement system for mobile objects in intelligent environments. IEEE
Transactions on Instrumentation and Measurement, 61(6), pp.1664-1675.
Shirehjini, A.A.N., Yassine, A. and Shirmohammadi, S., 2012. Equipment location in hospitals
using RFID-based positioning system. IEEE Transactions on information technology in
biomedicine, 16(6), pp.1058-1069.
Silverman, D. ed., 2016. Qualitative research. Sage, pp. 2-43.
Slater, M.J., Evans, A.L. and Turner, M.J., 2016. Implementing a social identity approach for
effective change management. Journal of Change Management, 16(1), pp.18-37.
Smith, J.R. ed., 2013. Wirelessly Powered Sensor Networks and Computational RFID. Springer
Science & Business Media.
Smith, J.A. ed., 2015. Qualitative psychology: A practical guide to research methods. Sage.
Sun, C., 2012. Application of RFID technology for logistics on internet of things. AASRI
Procedia, 1, pp.106-111.

102RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Tan, Z., Daamen, R., Humbert, A., Ponomarev, Y.V., Chae, Y. and Pertijs, M.A., 2013. A 1.2-V
8.3-nJ CMOS humidity sensor for RFID applications. IEEE Journal of Solid-State
Circuits, 48(10), pp.2469-2477.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons
Thomas, S.J., Wheeler, E., Teizer, J. and Reynolds, M.S., 2012. Quadrature amplitude modulated
backscatter in passive and semipassive UHF RFID systems. IEEE Transactions on Microwave
Theory and Techniques, 60(4), pp.1175-1182.
Tian, Y., Chen, G. and Li, J., 2012. A new ultralightweight RFID authentication protocol with
permutation. IEEE Communications Letters, 16(5), pp.702-705.
Tsai, C.Y. and Chung, S.H., 2012. A personalized route recommendation service for theme parks
using RFID information and tourist behavior. Decision Support Systems, 52(2), pp.514-527.
Ustundag, A., 2014. The value of RFID. Springer.
Varadhan, C., Pakkathillam, J.K., Kanagasabai, M., Sivasamy, R., Natarajan, R. and
Palaniswamy, S.K., 2013. Triband antenna structures for RFID systems deploying fractal
geometry. IEEE antennas and wireless propagation letters, 12, pp.437-440.
Vargo, R., Zoschg, R., Borgoyn, E.C. and Naughton, M., Vocollect, Inc., 2014. Method and
system for correctly identifying specific RFID tags. U.S. Patent 8,659,397.
Vena, A., Perret, E. and Tedjini, S., 2012. High-capacity chipless RFID tag insensitive to the
polarization. IEEE Transactions on Antennas and Propagation, 60(10), pp.4509-4515.
Tan, Z., Daamen, R., Humbert, A., Ponomarev, Y.V., Chae, Y. and Pertijs, M.A., 2013. A 1.2-V
8.3-nJ CMOS humidity sensor for RFID applications. IEEE Journal of Solid-State
Circuits, 48(10), pp.2469-2477.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons
Thomas, S.J., Wheeler, E., Teizer, J. and Reynolds, M.S., 2012. Quadrature amplitude modulated
backscatter in passive and semipassive UHF RFID systems. IEEE Transactions on Microwave
Theory and Techniques, 60(4), pp.1175-1182.
Tian, Y., Chen, G. and Li, J., 2012. A new ultralightweight RFID authentication protocol with
permutation. IEEE Communications Letters, 16(5), pp.702-705.
Tsai, C.Y. and Chung, S.H., 2012. A personalized route recommendation service for theme parks
using RFID information and tourist behavior. Decision Support Systems, 52(2), pp.514-527.
Ustundag, A., 2014. The value of RFID. Springer.
Varadhan, C., Pakkathillam, J.K., Kanagasabai, M., Sivasamy, R., Natarajan, R. and
Palaniswamy, S.K., 2013. Triband antenna structures for RFID systems deploying fractal
geometry. IEEE antennas and wireless propagation letters, 12, pp.437-440.
Vargo, R., Zoschg, R., Borgoyn, E.C. and Naughton, M., Vocollect, Inc., 2014. Method and
system for correctly identifying specific RFID tags. U.S. Patent 8,659,397.
Vena, A., Perret, E. and Tedjini, S., 2012. High-capacity chipless RFID tag insensitive to the
polarization. IEEE Transactions on Antennas and Propagation, 60(10), pp.4509-4515.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

103RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Vena, A., Perret, E. and Tedjni, S., 2013. A depolarizing chipless RFID tag for robust detection
and its FCC compliant UWB reading system. IEEE transactions on microwave theory and
techniques, 61(8), pp.2982-2994.
Vena, A., Perret, E. and Tedjini, S., 2012. A fully printable chipless RFID tag with detuning
correction technique. IEEE Microwave and Wireless Components Letters, 22(4), pp.209-211.
Vena, A., Perret, E. and Tedjini, S., 2012. Design of compact and auto-compensated single-layer
chipless RFID tag. IEEE Transactions on Microwave Theory and Techniques, 60(9), pp.2913-
2924.
Viani, F., Salucci, M., Robol, F., Oliveri, G. and Massa, A., 2012. Design of a UHF RFID/GPS
fractal antenna for logistics management. Journal of Electromagnetic Waves and
Applications, 26(4), pp.480-492.
Wamba, S.F., 2012. RFID-enabled healthcare applications, issues and benefits: An archival
analysis (1997–2011). Journal of medical systems, 36(6), pp.3393-3398.
Wamba, S.F., Anand, A. and Carter, L., 2013. A literature review of RFID-enabled healthcare
applications and issues. International Journal of Information Management, 33(5), pp.875-891.
Wang, J. and Katabi, D., 2013. Dude, where's my card?: RFID positioning that works with
multipath and non-line of sight. ACM SIGCOMM Computer Communication Review, 43(4),
pp.51-62.
Wang, L., Da Xu, L., Bi, Z. and Xu, Y., 2014. Data cleaning for RFID and WSN
integration. IEEE transactions on industrial informatics, 10(1), pp.408-418.
Vena, A., Perret, E. and Tedjni, S., 2013. A depolarizing chipless RFID tag for robust detection
and its FCC compliant UWB reading system. IEEE transactions on microwave theory and
techniques, 61(8), pp.2982-2994.
Vena, A., Perret, E. and Tedjini, S., 2012. A fully printable chipless RFID tag with detuning
correction technique. IEEE Microwave and Wireless Components Letters, 22(4), pp.209-211.
Vena, A., Perret, E. and Tedjini, S., 2012. Design of compact and auto-compensated single-layer
chipless RFID tag. IEEE Transactions on Microwave Theory and Techniques, 60(9), pp.2913-
2924.
Viani, F., Salucci, M., Robol, F., Oliveri, G. and Massa, A., 2012. Design of a UHF RFID/GPS
fractal antenna for logistics management. Journal of Electromagnetic Waves and
Applications, 26(4), pp.480-492.
Wamba, S.F., 2012. RFID-enabled healthcare applications, issues and benefits: An archival
analysis (1997–2011). Journal of medical systems, 36(6), pp.3393-3398.
Wamba, S.F., Anand, A. and Carter, L., 2013. A literature review of RFID-enabled healthcare
applications and issues. International Journal of Information Management, 33(5), pp.875-891.
Wang, J. and Katabi, D., 2013. Dude, where's my card?: RFID positioning that works with
multipath and non-line of sight. ACM SIGCOMM Computer Communication Review, 43(4),
pp.51-62.
Wang, L., Da Xu, L., Bi, Z. and Xu, Y., 2014. Data cleaning for RFID and WSN
integration. IEEE transactions on industrial informatics, 10(1), pp.408-418.

104RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Wickboldt, A.K. and Piramuthu, S., 2012. Patient safety through RFID: Vulnerabilities in
recently proposed grouping protocols. Journal of Medical Systems, 36(2), pp.431-435.
Wu, H., Zeng, Y., Feng, J. and Gu, Y., 2013. Binary tree slotted ALOHA for passive RFID tag
anticollision. IEEE Transactions on Parallel and Distributed Systems, 24(1), pp.19-31.
Wu, T., Su, H., Gan, L., Chen, H., Huang, J. and Zhang, H., 2013. A compact and broadband
microstrip stacked patch antenna with circular polarization for 2.45-GHz mobile RFID
reader. IEEE Antennas and Wireless Propagation Letters, 12, pp.623-626.
Yang, L., Chen, Y., Li, X.Y., Xiao, C., Li, M. and Liu, Y., 2014, September. Tagoram: Real-time
tracking of mobile RFID tags to high precision using COTS devices. In Proceedings of the 20th
annual international conference on Mobile computing and networking (pp. 237-248). ACM.
Yang, P., Wu, W., Moniri, M. and Chibelushi, C.C., 2013. Efficient object localization using
sparsely distributed passive RFID tags. IEEE transactions on industrial electronics, 60(12),
pp.5914-5924.
Yao, W., Chu, C.H. and Li, Z., 2012. The adoption and implementation of RFID technologies in
healthcare: a literature review. Journal of medical systems, 36(6), pp.3507-3525.
Yen, Y.C., Lo, N.W. and Wu, T.C., 2012. Two RFID-based solutions for secure inpatient
medication administration. Journal of medical systems, 36(5), pp.2769-2778.
Yoon, E.J., 2012. Improvement of the securing RFID systems conforming to EPC class 1
generation 2 standard. Expert Systems with Applications, 39(1), pp.1589-1594.
Yu, Y.C., Hou, T.W. and Chiang, T.C., 2012. Low cost RFID real lightweight binding proof
protocol for medication errors and patient safety. Journal of medical systems, 36(2), pp.823-828.
Wickboldt, A.K. and Piramuthu, S., 2012. Patient safety through RFID: Vulnerabilities in
recently proposed grouping protocols. Journal of Medical Systems, 36(2), pp.431-435.
Wu, H., Zeng, Y., Feng, J. and Gu, Y., 2013. Binary tree slotted ALOHA for passive RFID tag
anticollision. IEEE Transactions on Parallel and Distributed Systems, 24(1), pp.19-31.
Wu, T., Su, H., Gan, L., Chen, H., Huang, J. and Zhang, H., 2013. A compact and broadband
microstrip stacked patch antenna with circular polarization for 2.45-GHz mobile RFID
reader. IEEE Antennas and Wireless Propagation Letters, 12, pp.623-626.
Yang, L., Chen, Y., Li, X.Y., Xiao, C., Li, M. and Liu, Y., 2014, September. Tagoram: Real-time
tracking of mobile RFID tags to high precision using COTS devices. In Proceedings of the 20th
annual international conference on Mobile computing and networking (pp. 237-248). ACM.
Yang, P., Wu, W., Moniri, M. and Chibelushi, C.C., 2013. Efficient object localization using
sparsely distributed passive RFID tags. IEEE transactions on industrial electronics, 60(12),
pp.5914-5924.
Yao, W., Chu, C.H. and Li, Z., 2012. The adoption and implementation of RFID technologies in
healthcare: a literature review. Journal of medical systems, 36(6), pp.3507-3525.
Yen, Y.C., Lo, N.W. and Wu, T.C., 2012. Two RFID-based solutions for secure inpatient
medication administration. Journal of medical systems, 36(5), pp.2769-2778.
Yoon, E.J., 2012. Improvement of the securing RFID systems conforming to EPC class 1
generation 2 standard. Expert Systems with Applications, 39(1), pp.1589-1594.
Yu, Y.C., Hou, T.W. and Chiang, T.C., 2012. Low cost RFID real lightweight binding proof
protocol for medication errors and patient safety. Journal of medical systems, 36(2), pp.823-828.

105RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Zelbst, P.J., Green, K.W., Sower, V.E. and Reyes, P.M., 2012. Impact of RFID on manufacturing
effectiveness and efficiency. International Journal of Operations & Production
Management, 32(3), pp.329-350.
Zhang, Y., Jiang, P., Huang, G., Qu, T., Zhou, G. and Hong, J., 2012. RFID-enabled real-time
manufacturing information tracking infrastructure for extended enterprises. Journal of Intelligent
Manufacturing, 23(6), pp.2357-2366.
Zheng, Y. and Li, M., 2013. Fast tag searching protocol for large-scale RFID
systems. IEEE/ACM Transactions on Networking (TON), 21(3), pp.924-934.
Zheng, Y. and Li, M., 2012. PET: Probabilistic estimating tree for large-scale RFID
estimation. IEEE Transactions on Mobile Computing, 11(11), pp.1763-1774.
Zheng, Y. and Li, M., 2013, April. ZOE: Fast cardinality estimation for large-scale RFID
systems. In INFOCOM, 2013 Proceedings IEEE (pp. 908-916). IEEE.
Zhong, R.Y., Dai, Q.Y., Qu, T., Hu, G.J. and Huang, G.Q., 2013. RFID-enabled real-time
manufacturing execution system for mass-customization production. Robotics and Computer-
Integrated Manufacturing, 29(2), pp.283-292.
Zhong, R.Y., Huang, G.Q., Lan, S., Dai, Q.Y., Chen, X. and Zhang, T., 2015. A big data
approach for logistics trajectory discovery from RFID-enabled production data. International
Journal of Production Economics, 165, pp.260-272.
Zhou, Z., Chen, B. and Yu, H., 2016. Understanding RFID counting protocols. IEEE/ACM
Transactions on Networking (TON), 24(1), pp.312-327.
Zelbst, P.J., Green, K.W., Sower, V.E. and Reyes, P.M., 2012. Impact of RFID on manufacturing
effectiveness and efficiency. International Journal of Operations & Production
Management, 32(3), pp.329-350.
Zhang, Y., Jiang, P., Huang, G., Qu, T., Zhou, G. and Hong, J., 2012. RFID-enabled real-time
manufacturing information tracking infrastructure for extended enterprises. Journal of Intelligent
Manufacturing, 23(6), pp.2357-2366.
Zheng, Y. and Li, M., 2013. Fast tag searching protocol for large-scale RFID
systems. IEEE/ACM Transactions on Networking (TON), 21(3), pp.924-934.
Zheng, Y. and Li, M., 2012. PET: Probabilistic estimating tree for large-scale RFID
estimation. IEEE Transactions on Mobile Computing, 11(11), pp.1763-1774.
Zheng, Y. and Li, M., 2013, April. ZOE: Fast cardinality estimation for large-scale RFID
systems. In INFOCOM, 2013 Proceedings IEEE (pp. 908-916). IEEE.
Zhong, R.Y., Dai, Q.Y., Qu, T., Hu, G.J. and Huang, G.Q., 2013. RFID-enabled real-time
manufacturing execution system for mass-customization production. Robotics and Computer-
Integrated Manufacturing, 29(2), pp.283-292.
Zhong, R.Y., Huang, G.Q., Lan, S., Dai, Q.Y., Chen, X. and Zhang, T., 2015. A big data
approach for logistics trajectory discovery from RFID-enabled production data. International
Journal of Production Economics, 165, pp.260-272.
Zhou, Z., Chen, B. and Yu, H., 2016. Understanding RFID counting protocols. IEEE/ACM
Transactions on Networking (TON), 24(1), pp.312-327.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

106RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Zhu, X., Mukhopadhyay, S.K. and Kurata, H., 2012. A review of RFID technology and its
managerial applications in different industries. Journal of Engineering and Technology
Management, 29(1), pp.152-167.
Zhu, W., Cao, J., Xu, Y., Yang, L. and Kong, J., 2014. Fault-tolerant RFID reader localization
based on passive RFID tags. IEEE Transactions on Parallel and Distributed Systems, 25(8),
pp.2065-2076.
Zhu, X., Mukhopadhyay, S.K. and Kurata, H., 2012. A review of RFID technology and its
managerial applications in different industries. Journal of Engineering and Technology
Management, 29(1), pp.152-167.
Zhu, W., Cao, J., Xu, Y., Yang, L. and Kong, J., 2014. Fault-tolerant RFID reader localization
based on passive RFID tags. IEEE Transactions on Parallel and Distributed Systems, 25(8),
pp.2065-2076.
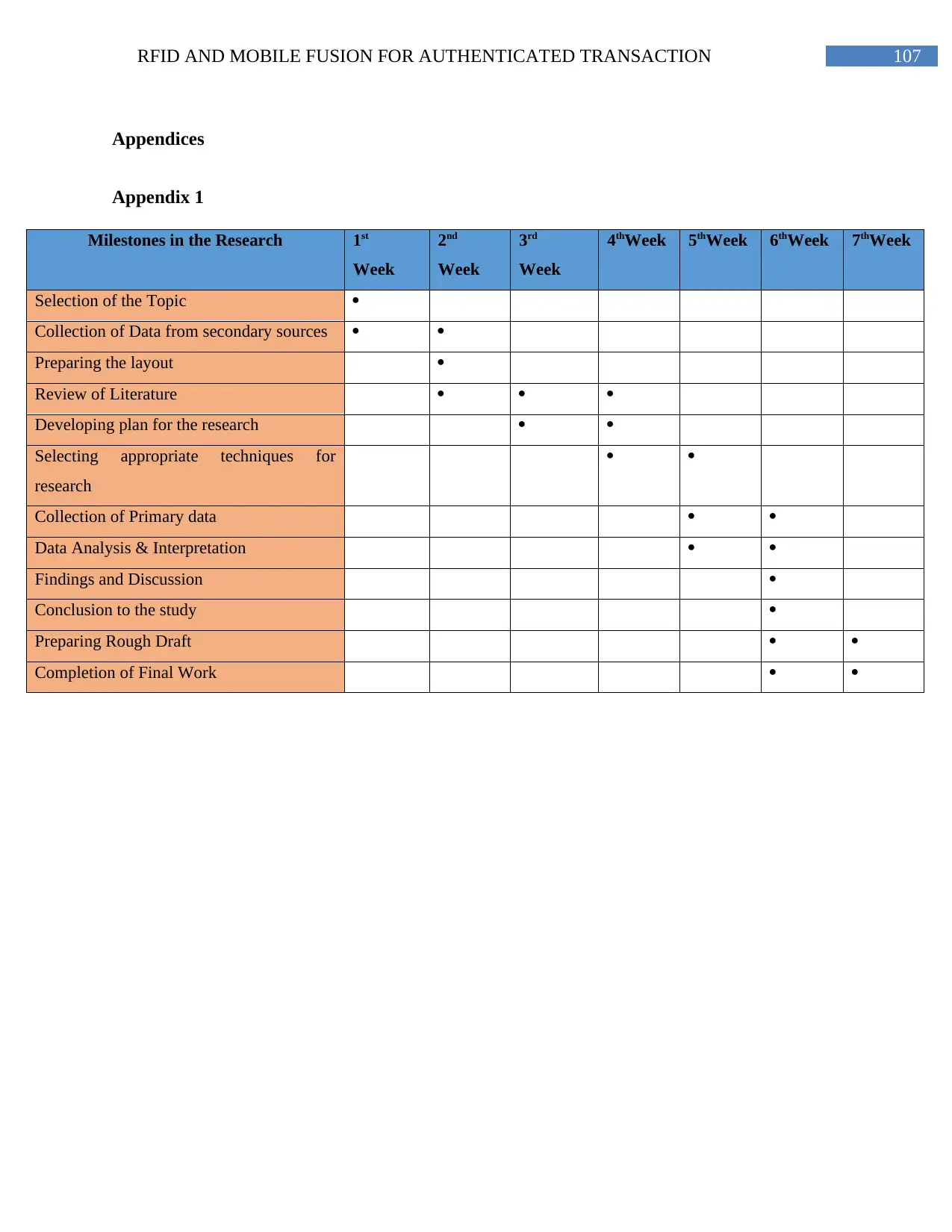
107RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Appendices
Appendix 1
Milestones in the Research 1st
Week
2nd
Week
3rd
Week
4thWeek 5thWeek 6thWeek 7thWeek
Selection of the Topic
Collection of Data from secondary sources
Preparing the layout
Review of Literature
Developing plan for the research
Selecting appropriate techniques for
research
Collection of Primary data
Data Analysis & Interpretation
Findings and Discussion
Conclusion to the study
Preparing Rough Draft
Completion of Final Work
Appendices
Appendix 1
Milestones in the Research 1st
Week
2nd
Week
3rd
Week
4thWeek 5thWeek 6thWeek 7thWeek
Selection of the Topic
Collection of Data from secondary sources
Preparing the layout
Review of Literature
Developing plan for the research
Selecting appropriate techniques for
research
Collection of Primary data
Data Analysis & Interpretation
Findings and Discussion
Conclusion to the study
Preparing Rough Draft
Completion of Final Work

108RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Table 17: Gantt chart
Appendix 2
Survey questionnaire
Q1. Does your organization use RFID technology?
Options
Yes
No
Q2. How long your organization has implemented RFID technology?
Options
6 months- 1 year
1 year – 2 years
2-4 years
4-5 years
More than 5 years
Q3. How far do you agree that asset tracking and WIP are the major drivers for implementing
RFID initiative?
Options
Strongly agree
Agree
Table 17: Gantt chart
Appendix 2
Survey questionnaire
Q1. Does your organization use RFID technology?
Options
Yes
No
Q2. How long your organization has implemented RFID technology?
Options
6 months- 1 year
1 year – 2 years
2-4 years
4-5 years
More than 5 years
Q3. How far do you agree that asset tracking and WIP are the major drivers for implementing
RFID initiative?
Options
Strongly agree
Agree
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

109RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Neutral
Disagree
Strongly disagree
Q4. How far you agree that implementation of RFID technology has potential advantages over
bar code scanner?
Options
Strongly agree
Agree
Neutral
Disagree
Strongly disagree
Q5. Which of the following purposes of your organization for implementing RFID system?
Options
Lockable section for
detection
Rewritable section for
specific use
Security functions for
anti-theft
Neutral
Disagree
Strongly disagree
Q4. How far you agree that implementation of RFID technology has potential advantages over
bar code scanner?
Options
Strongly agree
Agree
Neutral
Disagree
Strongly disagree
Q5. Which of the following purposes of your organization for implementing RFID system?
Options
Lockable section for
detection
Rewritable section for
specific use
Security functions for
anti-theft
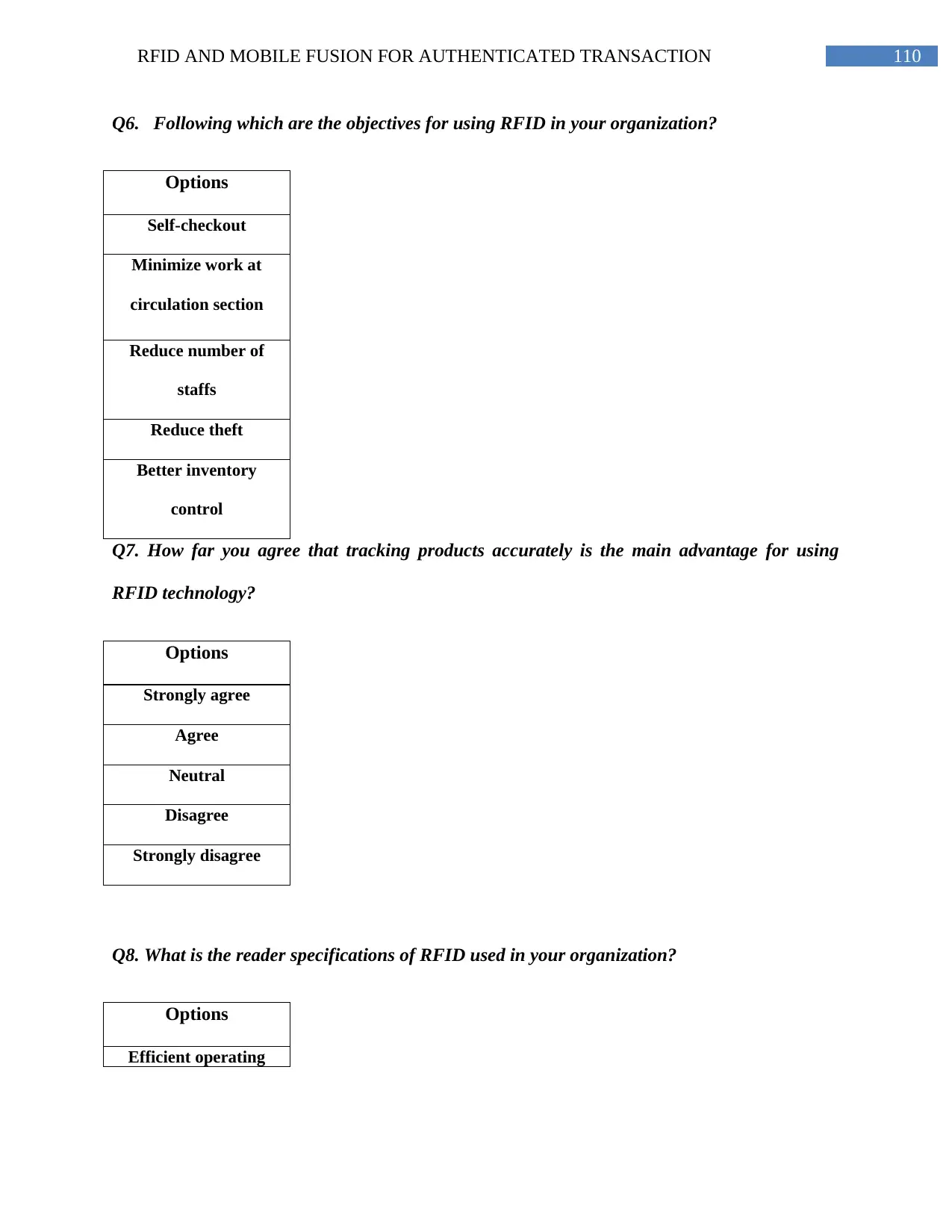
110RFID AND MOBILE FUSION FOR AUTHENTICATED TRANSACTION
Q6. Following which are the objectives for using RFID in your organization?
Options
Self-checkout
Minimize work at
circulation section
Reduce number of
staffs
Reduce theft
Better inventory
control
Q7. How far you agree that tracking products accurately is the main advantage for using
RFID technology?
Options
Strongly agree
Agree
Neutral
Disagree
Strongly disagree
Q8. What is the reader specifications of RFID used in your organization?
Options
Efficient operating
Q6. Following which are the objectives for using RFID in your organization?
Options
Self-checkout
Minimize work at
circulation section
Reduce number of
staffs
Reduce theft
Better inventory
control
Q7. How far you agree that tracking products accurately is the main advantage for using
RFID technology?
Options
Strongly agree
Agree
Neutral
Disagree
Strongly disagree
Q8. What is the reader specifications of RFID used in your organization?
Options
Efficient operating
1 out of 111
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





