Wireshark for Network Security Analysis
VerifiedAdded on 2020/03/02
|21
|3419
|72
AI Summary
This assignment delves into the capabilities of Wireshark, a prominent network analysis tool. It discusses its ease of use, interface, and how it aids in monitoring network activity. The document emphasizes Wireshark's relevance in cybersecurity, particularly in light of increasing cyber threats like ransomware attacks. While highlighting Wireshark's user-friendliness, the assignment also acknowledges the need for continuous improvement in security algorithms to address evolving vulnerabilities.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: TCP/IP INTERNETWORKING
Assignment Number:
Assignment Title: TCP/IP Internetworking
Student Name:
Student ID:
Student Email:
Assignment Number:
Assignment Title: TCP/IP Internetworking
Student Name:
Student ID:
Student Email:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1TCP/IP INTERNETWORKING
Executive Summary
M2M Solutions, a medium estimated association, situated in Sydney, Australia is anticipating
extending its operations. What's more, the organisation has effectively gained six distinct
locales over the city to suit its six offices. Those are its Finance Office, Head Office, Information
Technology, Transport Office, Research Office and Sales Office. Prior every one of the units was
situated in a similar building, yet now after moving the divisions to new places, it will be
required to assemble a bury arrange for all its business interchanges over the offices. Starting at
now, the aggregate number of workstations being used is roughly 1200. This report tends to all
the important strides to take after to manufacture a system over those locales where each site
will have their sub connect with abandoning a few spaces for development in the number of
workstations. Likewise, it is additionally essential to use the majority of the IP locations and
squandering the base number of IPs in this procedure of design. This report reasons that static
directing is the better steering convention in this situation where divisions are restricted, and it
will assist the system overseer with making the system more secure alongside the framework
breaking down devices that were prior not permitted to use the authoritative premises. Hence,
the report discloses every one of the means to take after for usage of great system availability
in the association.
Student Name Student Number
Executive Summary
M2M Solutions, a medium estimated association, situated in Sydney, Australia is anticipating
extending its operations. What's more, the organisation has effectively gained six distinct
locales over the city to suit its six offices. Those are its Finance Office, Head Office, Information
Technology, Transport Office, Research Office and Sales Office. Prior every one of the units was
situated in a similar building, yet now after moving the divisions to new places, it will be
required to assemble a bury arrange for all its business interchanges over the offices. Starting at
now, the aggregate number of workstations being used is roughly 1200. This report tends to all
the important strides to take after to manufacture a system over those locales where each site
will have their sub connect with abandoning a few spaces for development in the number of
workstations. Likewise, it is additionally essential to use the majority of the IP locations and
squandering the base number of IPs in this procedure of design. This report reasons that static
directing is the better steering convention in this situation where divisions are restricted, and it
will assist the system overseer with making the system more secure alongside the framework
breaking down devices that were prior not permitted to use the authoritative premises. Hence,
the report discloses every one of the means to take after for usage of great system availability
in the association.
Student Name Student Number

2TCP/IP INTERNETWORKING
Table of Contents
TASK 1: Designing the Network Architecture.................................................................................3
1.1 Network Designing.......................................................................................................3
1.1.1 Network Architecture....................................................................................3
1.1.2 Devices Required...........................................................................................4
1.1.3 Subnet and Subnet Calculation.....................................................................4
1.1.4 Network Architecture..................................................................................14
1.1.5 Configuration Technique.............................................................................14
1.2 What if host number increases over 1024 per department ?....................................15
1.2.1 Difficulties....................................................................................................15
TASK 2: Network Analysis............................................................................................................ 16
2.1 Networking Protocols.................................................................................................16
2.2 Network Analysis of M2M Solution............................................................................17
2.2.1 Advantages of Network Analysis.................................................................17
Recommendation.............................................................................................................19
References................................................................................................................................... 20
Student Name Student Number
Table of Contents
TASK 1: Designing the Network Architecture.................................................................................3
1.1 Network Designing.......................................................................................................3
1.1.1 Network Architecture....................................................................................3
1.1.2 Devices Required...........................................................................................4
1.1.3 Subnet and Subnet Calculation.....................................................................4
1.1.4 Network Architecture..................................................................................14
1.1.5 Configuration Technique.............................................................................14
1.2 What if host number increases over 1024 per department ?....................................15
1.2.1 Difficulties....................................................................................................15
TASK 2: Network Analysis............................................................................................................ 16
2.1 Networking Protocols.................................................................................................16
2.2 Network Analysis of M2M Solution............................................................................17
2.2.1 Advantages of Network Analysis.................................................................17
Recommendation.............................................................................................................19
References................................................................................................................................... 20
Student Name Student Number
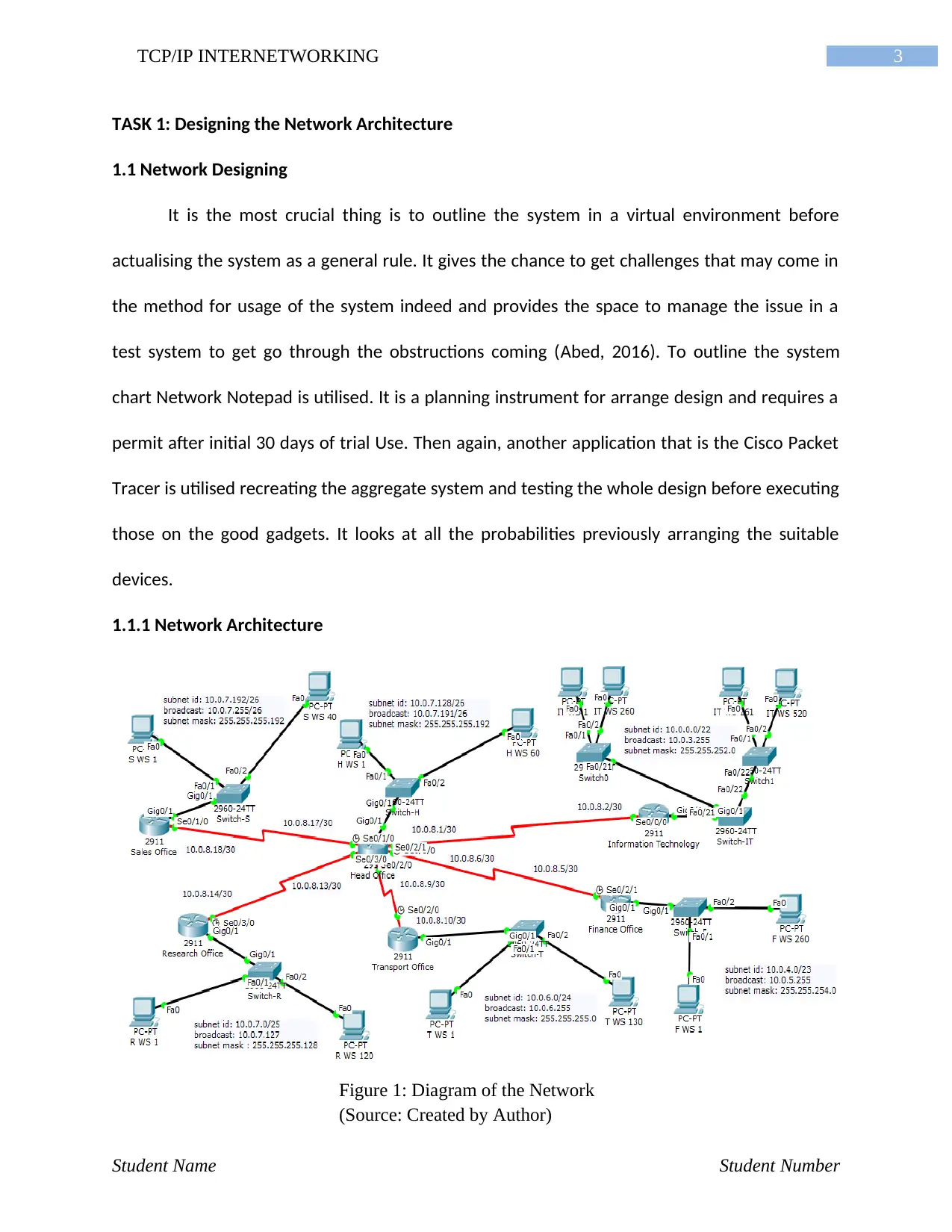
3TCP/IP INTERNETWORKING
TASK 1: Designing the Network Architecture
1.1 Network Designing
It is the most crucial thing is to outline the system in a virtual environment before
actualising the system as a general rule. It gives the chance to get challenges that may come in
the method for usage of the system indeed and provides the space to manage the issue in a
test system to get go through the obstructions coming (Abed, 2016). To outline the system
chart Network Notepad is utilised. It is a planning instrument for arrange design and requires a
permit after initial 30 days of trial Use. Then again, another application that is the Cisco Packet
Tracer is utilised recreating the aggregate system and testing the whole design before executing
those on the good gadgets. It looks at all the probabilities previously arranging the suitable
devices.
1.1.1 Network Architecture
Student Name Student Number
Figure 1: Diagram of the Network
(Source: Created by Author)
TASK 1: Designing the Network Architecture
1.1 Network Designing
It is the most crucial thing is to outline the system in a virtual environment before
actualising the system as a general rule. It gives the chance to get challenges that may come in
the method for usage of the system indeed and provides the space to manage the issue in a
test system to get go through the obstructions coming (Abed, 2016). To outline the system
chart Network Notepad is utilised. It is a planning instrument for arrange design and requires a
permit after initial 30 days of trial Use. Then again, another application that is the Cisco Packet
Tracer is utilised recreating the aggregate system and testing the whole design before executing
those on the good gadgets. It looks at all the probabilities previously arranging the suitable
devices.
1.1.1 Network Architecture
Student Name Student Number
Figure 1: Diagram of the Network
(Source: Created by Author)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4TCP/IP INTERNETWORKING
1.1.2 Devices Required
Core Networking Devices: Six switches are set in each of the constructs where the
divisions are suited (Cui et al., 2015). Switches are organising gadget that transmits
information bundles between PC systems utilising activity-coordinating capacities.
Workstations: The number of workstations used is discussed below.
520 workstations in the Information Technology department
260 workstations in the Finance Department
130 workstations in the Transport Department
120 workstations in the Research Department
60 workstations in the Head Office
40 workstations in the Sales department
1.1.3 Subnet and Subnet Calculation
The IP address is a one of a kind number doled out to every gadget on the system. Then
again, IP-tending to imply allotting IP delivers to every device on the system. Prior IP addresses
were classful. Those are the class a, b, c, d and e. This strategy winds up squandered lots of IP
addresses since IP addresses were settled in numbers for each class (Duke et al., 2015).
Accordingly, the requirement for subnetting came into the photo. Subnetting separates single
system IP into numerous diverse systems. This added to use the majority of the IP tends to that
were prior left relinquished.
The association possesses the IP Network 10.0.0.0, and it is said to utilise that system IP
to influence all to the sub network. As per the outline, the system will utilise the star topology.
In Star topology, every one of the hubs is associated with a Central centre point or focal gadget.
Student Name Student Number
1.1.2 Devices Required
Core Networking Devices: Six switches are set in each of the constructs where the
divisions are suited (Cui et al., 2015). Switches are organising gadget that transmits
information bundles between PC systems utilising activity-coordinating capacities.
Workstations: The number of workstations used is discussed below.
520 workstations in the Information Technology department
260 workstations in the Finance Department
130 workstations in the Transport Department
120 workstations in the Research Department
60 workstations in the Head Office
40 workstations in the Sales department
1.1.3 Subnet and Subnet Calculation
The IP address is a one of a kind number doled out to every gadget on the system. Then
again, IP-tending to imply allotting IP delivers to every device on the system. Prior IP addresses
were classful. Those are the class a, b, c, d and e. This strategy winds up squandered lots of IP
addresses since IP addresses were settled in numbers for each class (Duke et al., 2015).
Accordingly, the requirement for subnetting came into the photo. Subnetting separates single
system IP into numerous diverse systems. This added to use the majority of the IP tends to that
were prior left relinquished.
The association possesses the IP Network 10.0.0.0, and it is said to utilise that system IP
to influence all to the sub network. As per the outline, the system will utilise the star topology.
In Star topology, every one of the hubs is associated with a Central centre point or focal gadget.
Student Name Student Number

5TCP/IP INTERNETWORKING
For this situation, the switch situated in the head office is the essential device or switch that is
linked to five direct channels with different switches located in various offices (Keceli, Inan &
Ayanoglu, 2015). Subsequently, six rooms and five dedicated channel add up to 11 sub
networks are required. The principal technique in subnetting is to sort the system as per the
necessary IP addresses in dropping request. Along these lines in the wake of arranging IT office
with 520 workstations starts things out, then finance office with 260 workstations come next
after that Transport office with 130 workstations come third, at that point Research office with
120 workstations approach, after that the head office with 60 workstations go ahead fifth, and
the sales office comes last at 6th (Khalifa et al., 2014). From that point onward, the five different
correspondence channels are tallied. The IP address is a 32-bit address, it is separated into parts
the initial segment is the system part, and the rest is the host part.
The IP address series begins at 00000000.00000000.00000000.00000000 , That is 0.0.0.0
and Moreover, the last IP address is 11111111.11111111.11111111.11111111 That is
255.255.255.255 in Decimal individually. There is a counting strategy to decide how much bits
to be obtained from the host part. That is 2n-2. This implies on the off chance that you get 2 bits
you will get 22-2=2 IP addresses if 3 bits are acquired you will get 23-2=6 IP addresses.
Student Name Student Number
For this situation, the switch situated in the head office is the essential device or switch that is
linked to five direct channels with different switches located in various offices (Keceli, Inan &
Ayanoglu, 2015). Subsequently, six rooms and five dedicated channel add up to 11 sub
networks are required. The principal technique in subnetting is to sort the system as per the
necessary IP addresses in dropping request. Along these lines in the wake of arranging IT office
with 520 workstations starts things out, then finance office with 260 workstations come next
after that Transport office with 130 workstations come third, at that point Research office with
120 workstations approach, after that the head office with 60 workstations go ahead fifth, and
the sales office comes last at 6th (Khalifa et al., 2014). From that point onward, the five different
correspondence channels are tallied. The IP address is a 32-bit address, it is separated into parts
the initial segment is the system part, and the rest is the host part.
The IP address series begins at 00000000.00000000.00000000.00000000 , That is 0.0.0.0
and Moreover, the last IP address is 11111111.11111111.11111111.11111111 That is
255.255.255.255 in Decimal individually. There is a counting strategy to decide how much bits
to be obtained from the host part. That is 2n-2. This implies on the off chance that you get 2 bits
you will get 22-2=2 IP addresses if 3 bits are acquired you will get 23-2=6 IP addresses.
Student Name Student Number
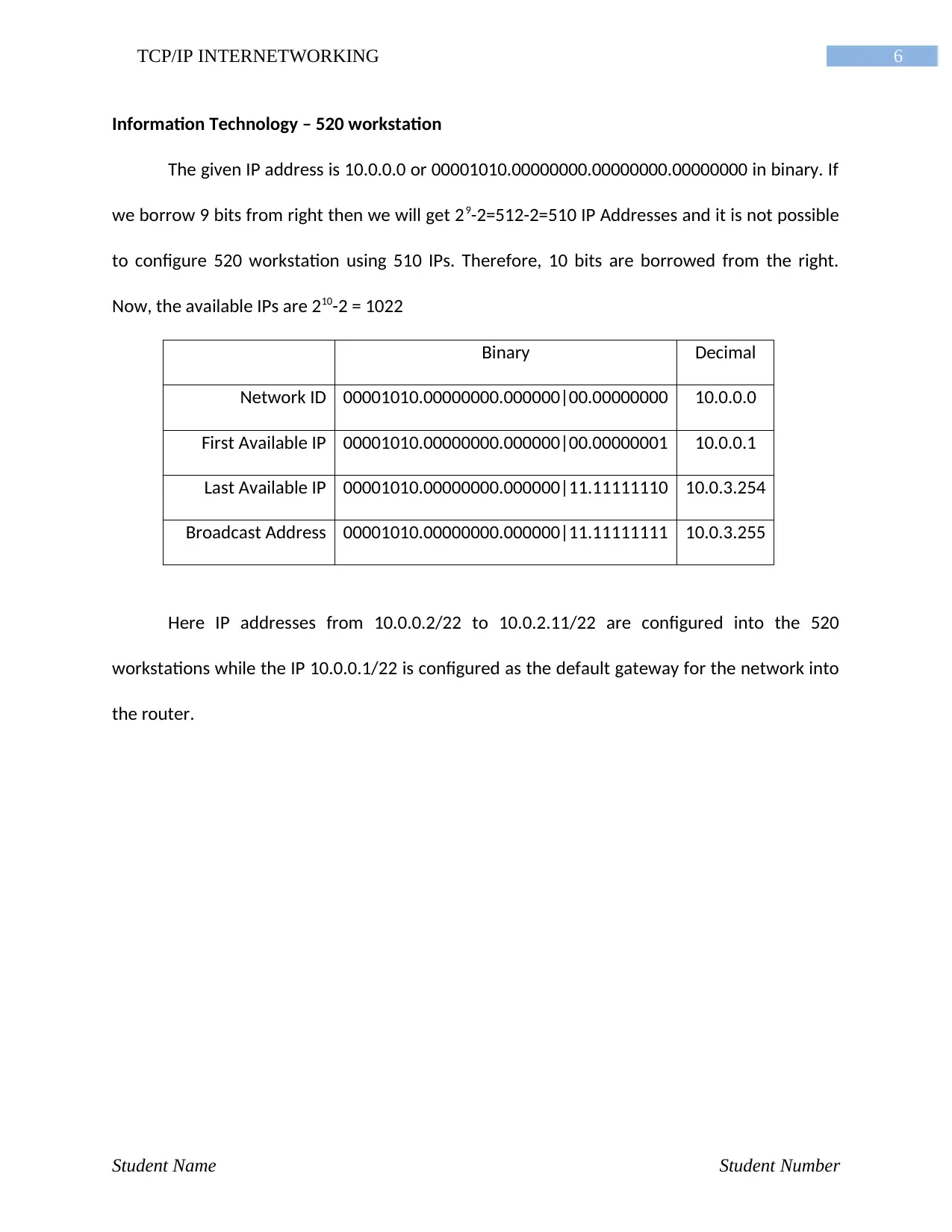
6TCP/IP INTERNETWORKING
Information Technology – 520 workstation
The given IP address is 10.0.0.0 or 00001010.00000000.00000000.00000000 in binary. If
we borrow 9 bits from right then we will get 29-2=512-2=510 IP Addresses and it is not possible
to configure 520 workstation using 510 IPs. Therefore, 10 bits are borrowed from the right.
Now, the available IPs are 210-2 = 1022
Binary Decimal
Network ID 00001010.00000000.000000|00.00000000 10.0.0.0
First Available IP 00001010.00000000.000000|00.00000001 10.0.0.1
Last Available IP 00001010.00000000.000000|11.11111110 10.0.3.254
Broadcast Address 00001010.00000000.000000|11.11111111 10.0.3.255
Here IP addresses from 10.0.0.2/22 to 10.0.2.11/22 are configured into the 520
workstations while the IP 10.0.0.1/22 is configured as the default gateway for the network into
the router.
Student Name Student Number
Information Technology – 520 workstation
The given IP address is 10.0.0.0 or 00001010.00000000.00000000.00000000 in binary. If
we borrow 9 bits from right then we will get 29-2=512-2=510 IP Addresses and it is not possible
to configure 520 workstation using 510 IPs. Therefore, 10 bits are borrowed from the right.
Now, the available IPs are 210-2 = 1022
Binary Decimal
Network ID 00001010.00000000.000000|00.00000000 10.0.0.0
First Available IP 00001010.00000000.000000|00.00000001 10.0.0.1
Last Available IP 00001010.00000000.000000|11.11111110 10.0.3.254
Broadcast Address 00001010.00000000.000000|11.11111111 10.0.3.255
Here IP addresses from 10.0.0.2/22 to 10.0.2.11/22 are configured into the 520
workstations while the IP 10.0.0.1/22 is configured as the default gateway for the network into
the router.
Student Name Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
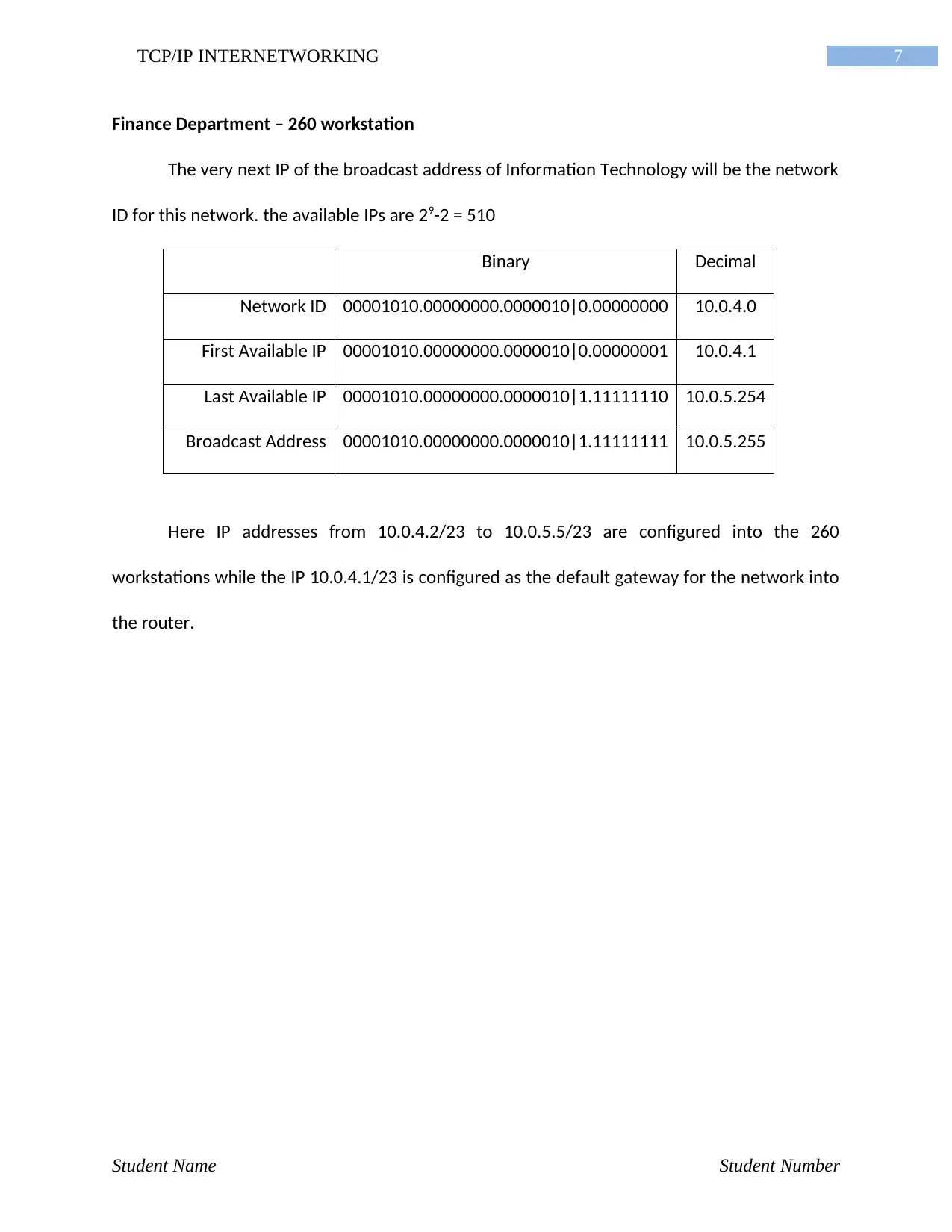
7TCP/IP INTERNETWORKING
Finance Department – 260 workstation
The very next IP of the broadcast address of Information Technology will be the network
ID for this network. the available IPs are 29-2 = 510
Binary Decimal
Network ID 00001010.00000000.0000010|0.00000000 10.0.4.0
First Available IP 00001010.00000000.0000010|0.00000001 10.0.4.1
Last Available IP 00001010.00000000.0000010|1.11111110 10.0.5.254
Broadcast Address 00001010.00000000.0000010|1.11111111 10.0.5.255
Here IP addresses from 10.0.4.2/23 to 10.0.5.5/23 are configured into the 260
workstations while the IP 10.0.4.1/23 is configured as the default gateway for the network into
the router.
Student Name Student Number
Finance Department – 260 workstation
The very next IP of the broadcast address of Information Technology will be the network
ID for this network. the available IPs are 29-2 = 510
Binary Decimal
Network ID 00001010.00000000.0000010|0.00000000 10.0.4.0
First Available IP 00001010.00000000.0000010|0.00000001 10.0.4.1
Last Available IP 00001010.00000000.0000010|1.11111110 10.0.5.254
Broadcast Address 00001010.00000000.0000010|1.11111111 10.0.5.255
Here IP addresses from 10.0.4.2/23 to 10.0.5.5/23 are configured into the 260
workstations while the IP 10.0.4.1/23 is configured as the default gateway for the network into
the router.
Student Name Student Number
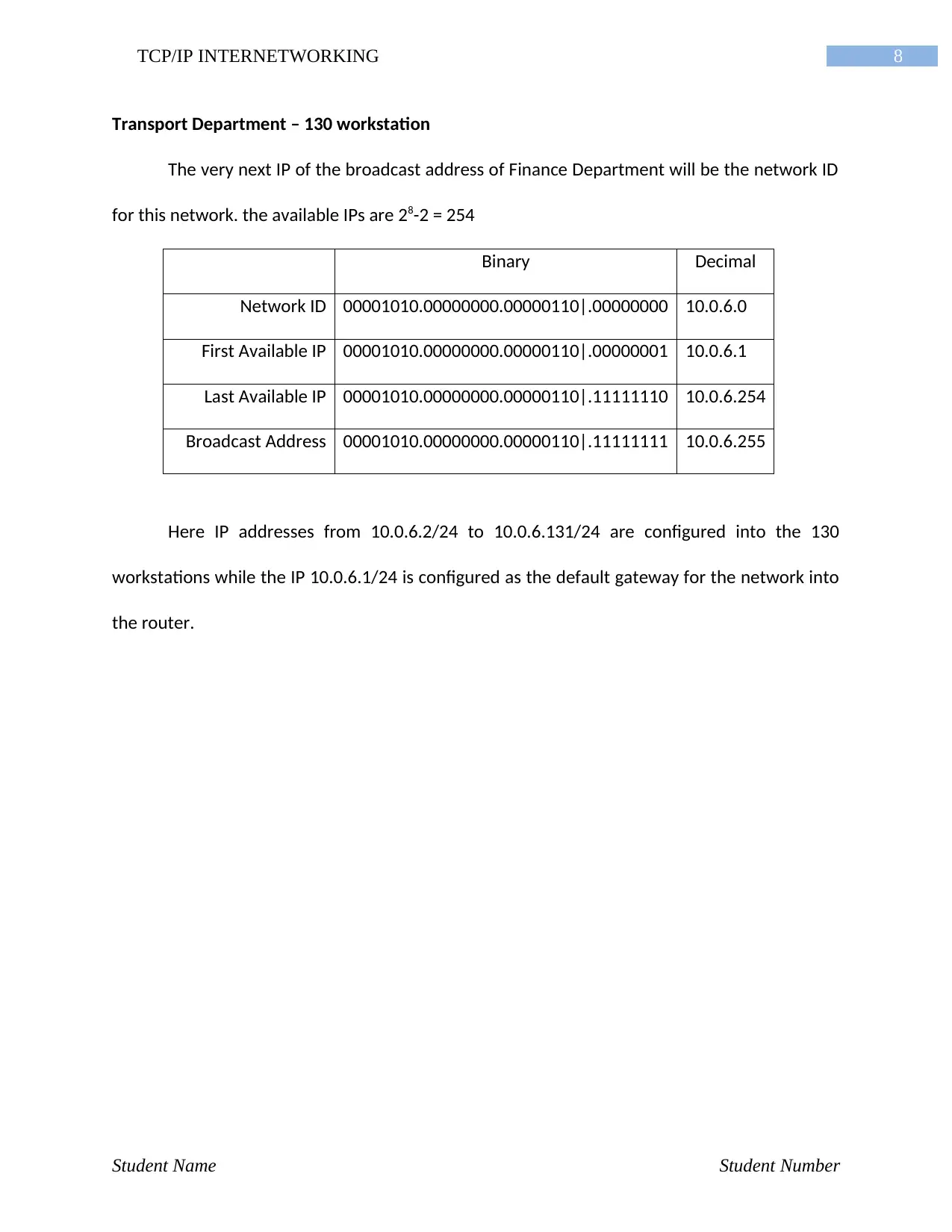
8TCP/IP INTERNETWORKING
Transport Department – 130 workstation
The very next IP of the broadcast address of Finance Department will be the network ID
for this network. the available IPs are 28-2 = 254
Binary Decimal
Network ID 00001010.00000000.00000110|.00000000 10.0.6.0
First Available IP 00001010.00000000.00000110|.00000001 10.0.6.1
Last Available IP 00001010.00000000.00000110|.11111110 10.0.6.254
Broadcast Address 00001010.00000000.00000110|.11111111 10.0.6.255
Here IP addresses from 10.0.6.2/24 to 10.0.6.131/24 are configured into the 130
workstations while the IP 10.0.6.1/24 is configured as the default gateway for the network into
the router.
Student Name Student Number
Transport Department – 130 workstation
The very next IP of the broadcast address of Finance Department will be the network ID
for this network. the available IPs are 28-2 = 254
Binary Decimal
Network ID 00001010.00000000.00000110|.00000000 10.0.6.0
First Available IP 00001010.00000000.00000110|.00000001 10.0.6.1
Last Available IP 00001010.00000000.00000110|.11111110 10.0.6.254
Broadcast Address 00001010.00000000.00000110|.11111111 10.0.6.255
Here IP addresses from 10.0.6.2/24 to 10.0.6.131/24 are configured into the 130
workstations while the IP 10.0.6.1/24 is configured as the default gateway for the network into
the router.
Student Name Student Number
9TCP/IP INTERNETWORKING
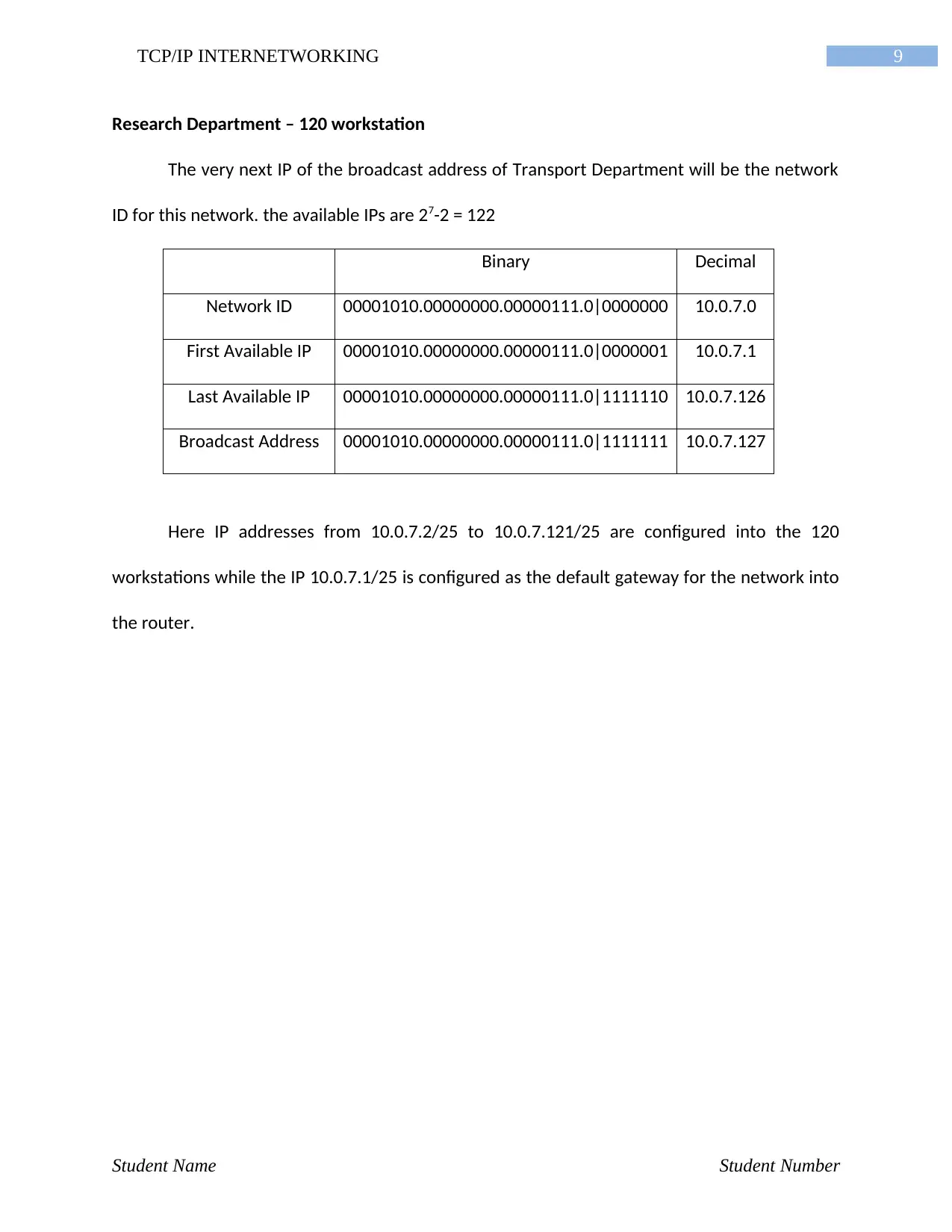
Research Department – 120 workstation
The very next IP of the broadcast address of Transport Department will be the network
ID for this network. the available IPs are 27-2 = 122
Binary Decimal
Network ID 00001010.00000000.00000111.0|0000000 10.0.7.0
First Available IP 00001010.00000000.00000111.0|0000001 10.0.7.1
Last Available IP 00001010.00000000.00000111.0|1111110 10.0.7.126
Broadcast Address 00001010.00000000.00000111.0|1111111 10.0.7.127
Here IP addresses from 10.0.7.2/25 to 10.0.7.121/25 are configured into the 120
workstations while the IP 10.0.7.1/25 is configured as the default gateway for the network into
the router.
Student Name Student Number
Research Department – 120 workstation
The very next IP of the broadcast address of Transport Department will be the network
ID for this network. the available IPs are 27-2 = 122
Binary Decimal
Network ID 00001010.00000000.00000111.0|0000000 10.0.7.0
First Available IP 00001010.00000000.00000111.0|0000001 10.0.7.1
Last Available IP 00001010.00000000.00000111.0|1111110 10.0.7.126
Broadcast Address 00001010.00000000.00000111.0|1111111 10.0.7.127
Here IP addresses from 10.0.7.2/25 to 10.0.7.121/25 are configured into the 120
workstations while the IP 10.0.7.1/25 is configured as the default gateway for the network into
the router.
Student Name Student Number
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10TCP/IP INTERNETWORKING
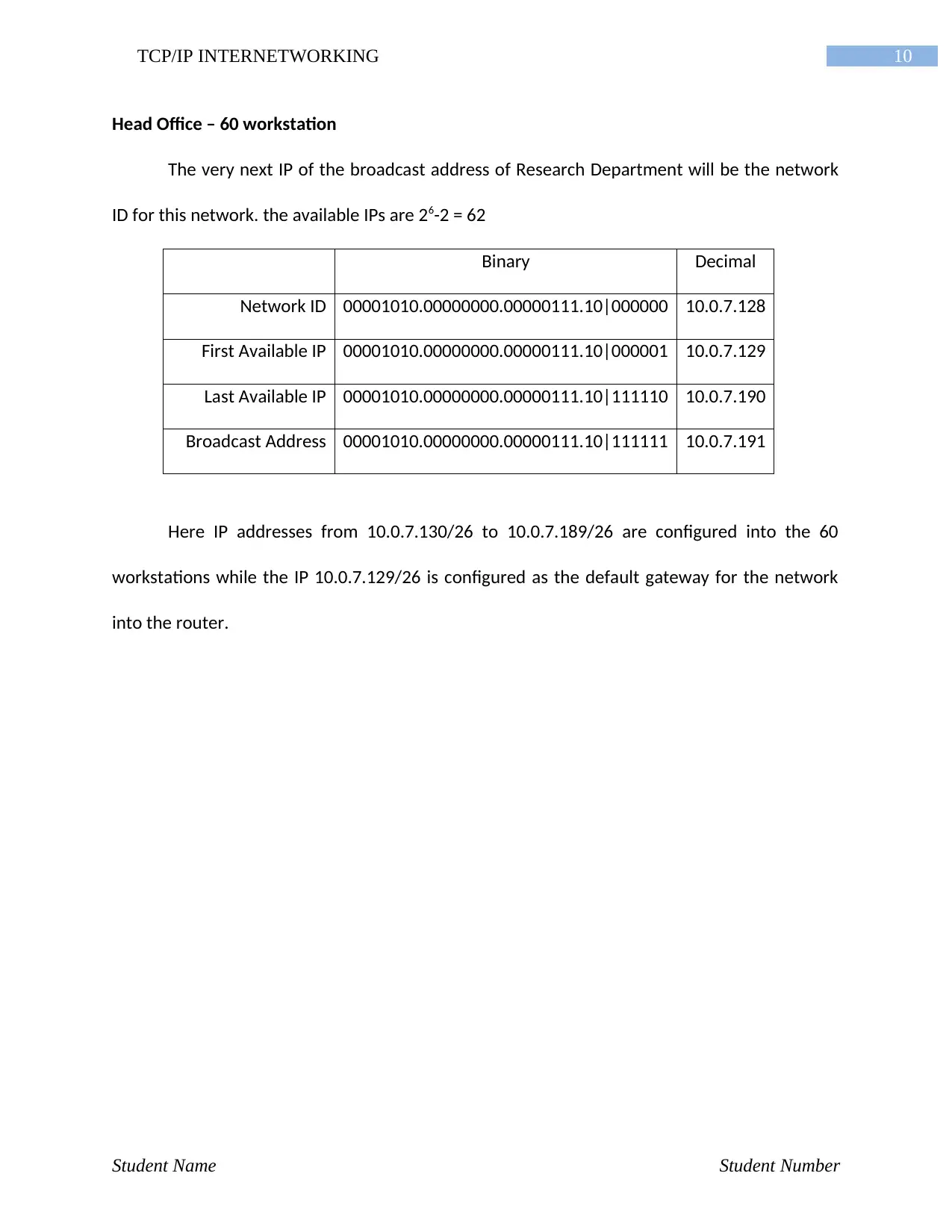
Head Office – 60 workstation
The very next IP of the broadcast address of Research Department will be the network
ID for this network. the available IPs are 26-2 = 62
Binary Decimal
Network ID 00001010.00000000.00000111.10|000000 10.0.7.128
First Available IP 00001010.00000000.00000111.10|000001 10.0.7.129
Last Available IP 00001010.00000000.00000111.10|111110 10.0.7.190
Broadcast Address 00001010.00000000.00000111.10|111111 10.0.7.191
Here IP addresses from 10.0.7.130/26 to 10.0.7.189/26 are configured into the 60
workstations while the IP 10.0.7.129/26 is configured as the default gateway for the network
into the router.
Student Name Student Number
Head Office – 60 workstation
The very next IP of the broadcast address of Research Department will be the network
ID for this network. the available IPs are 26-2 = 62
Binary Decimal
Network ID 00001010.00000000.00000111.10|000000 10.0.7.128
First Available IP 00001010.00000000.00000111.10|000001 10.0.7.129
Last Available IP 00001010.00000000.00000111.10|111110 10.0.7.190
Broadcast Address 00001010.00000000.00000111.10|111111 10.0.7.191
Here IP addresses from 10.0.7.130/26 to 10.0.7.189/26 are configured into the 60
workstations while the IP 10.0.7.129/26 is configured as the default gateway for the network
into the router.
Student Name Student Number
11TCP/IP INTERNETWORKING
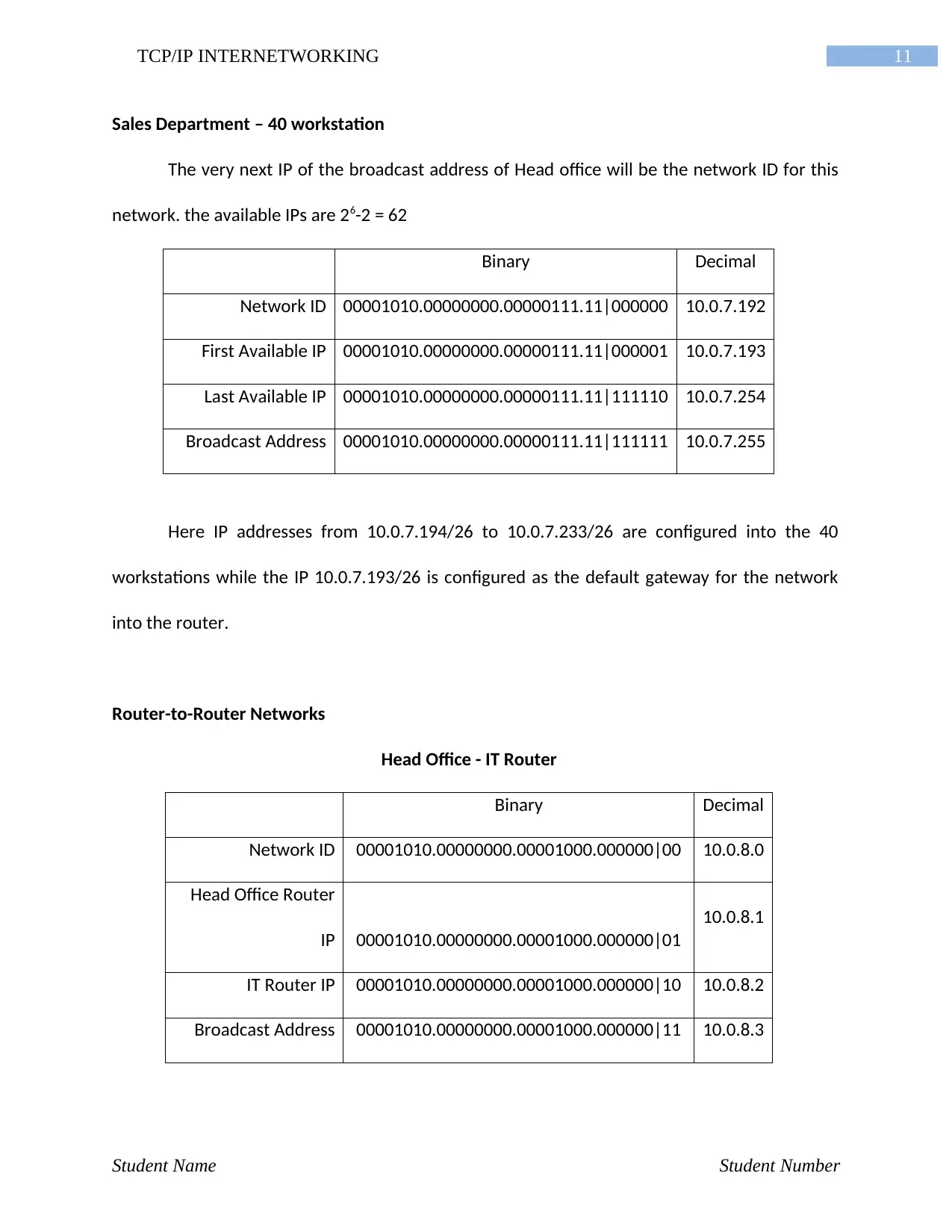
Sales Department – 40 workstation
The very next IP of the broadcast address of Head office will be the network ID for this
network. the available IPs are 26-2 = 62
Binary Decimal
Network ID 00001010.00000000.00000111.11|000000 10.0.7.192
First Available IP 00001010.00000000.00000111.11|000001 10.0.7.193
Last Available IP 00001010.00000000.00000111.11|111110 10.0.7.254
Broadcast Address 00001010.00000000.00000111.11|111111 10.0.7.255
Here IP addresses from 10.0.7.194/26 to 10.0.7.233/26 are configured into the 40
workstations while the IP 10.0.7.193/26 is configured as the default gateway for the network
into the router.
Router-to-Router Networks
Head Office - IT Router
Binary Decimal
Network ID 00001010.00000000.00001000.000000|00 10.0.8.0
Head Office Router
IP 00001010.00000000.00001000.000000|01
10.0.8.1
IT Router IP 00001010.00000000.00001000.000000|10 10.0.8.2
Broadcast Address 00001010.00000000.00001000.000000|11 10.0.8.3
Student Name Student Number
Sales Department – 40 workstation
The very next IP of the broadcast address of Head office will be the network ID for this
network. the available IPs are 26-2 = 62
Binary Decimal
Network ID 00001010.00000000.00000111.11|000000 10.0.7.192
First Available IP 00001010.00000000.00000111.11|000001 10.0.7.193
Last Available IP 00001010.00000000.00000111.11|111110 10.0.7.254
Broadcast Address 00001010.00000000.00000111.11|111111 10.0.7.255
Here IP addresses from 10.0.7.194/26 to 10.0.7.233/26 are configured into the 40
workstations while the IP 10.0.7.193/26 is configured as the default gateway for the network
into the router.
Router-to-Router Networks
Head Office - IT Router
Binary Decimal
Network ID 00001010.00000000.00001000.000000|00 10.0.8.0
Head Office Router
IP 00001010.00000000.00001000.000000|01
10.0.8.1
IT Router IP 00001010.00000000.00001000.000000|10 10.0.8.2
Broadcast Address 00001010.00000000.00001000.000000|11 10.0.8.3
Student Name Student Number
12TCP/IP INTERNETWORKING
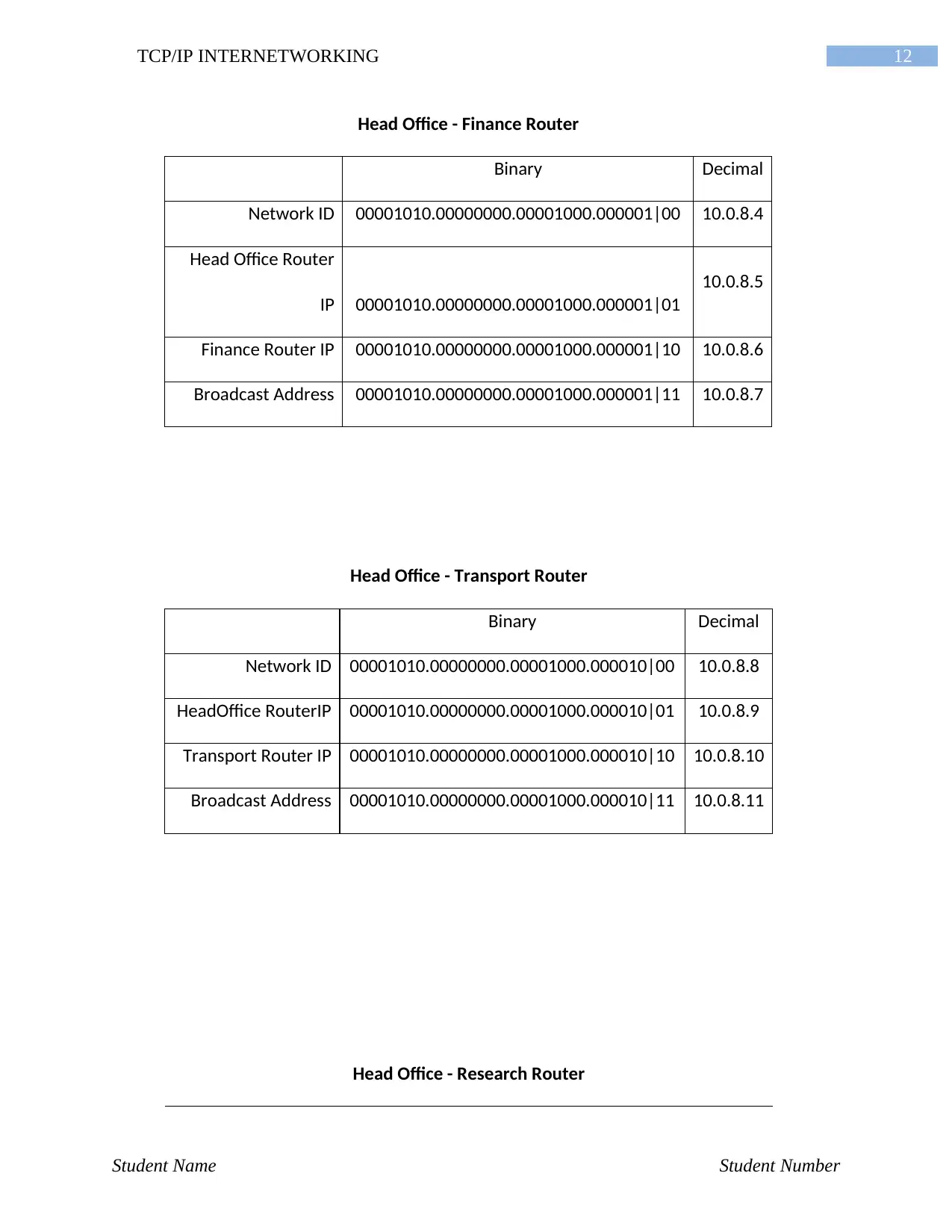
Head Office - Finance Router
Binary Decimal
Network ID 00001010.00000000.00001000.000001|00 10.0.8.4
Head Office Router
IP 00001010.00000000.00001000.000001|01
10.0.8.5
Finance Router IP 00001010.00000000.00001000.000001|10 10.0.8.6
Broadcast Address 00001010.00000000.00001000.000001|11 10.0.8.7
Head Office - Transport Router
Binary Decimal
Network ID 00001010.00000000.00001000.000010|00 10.0.8.8
HeadOffice RouterIP 00001010.00000000.00001000.000010|01 10.0.8.9
Transport Router IP 00001010.00000000.00001000.000010|10 10.0.8.10
Broadcast Address 00001010.00000000.00001000.000010|11 10.0.8.11
Head Office - Research Router
Student Name Student Number
Head Office - Finance Router
Binary Decimal
Network ID 00001010.00000000.00001000.000001|00 10.0.8.4
Head Office Router
IP 00001010.00000000.00001000.000001|01
10.0.8.5
Finance Router IP 00001010.00000000.00001000.000001|10 10.0.8.6
Broadcast Address 00001010.00000000.00001000.000001|11 10.0.8.7
Head Office - Transport Router
Binary Decimal
Network ID 00001010.00000000.00001000.000010|00 10.0.8.8
HeadOffice RouterIP 00001010.00000000.00001000.000010|01 10.0.8.9
Transport Router IP 00001010.00000000.00001000.000010|10 10.0.8.10
Broadcast Address 00001010.00000000.00001000.000010|11 10.0.8.11
Head Office - Research Router
Student Name Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13TCP/IP INTERNETWORKING
Binary Decimal
Network ID 00001010.00000000.00001000.000011|00 10.0.8.12
HeadOffice RouterIP 00001010.00000000.00001000.000011|01 10.0.8.13
Research Router IP 00001010.00000000.00001000.000011|10 10.0.8.14
Broadcast Address 00001010.00000000.00001000.000011|11 10.0.8.15
Head Office - Sales Router
Binary Decimal
Network ID 00001010.00000000.00001000.000100|00 10.0.8.16
Head Office Router
IP 00001010.00000000.00001000.000100|01
10.0.8.17
Sales Router IP 00001010.00000000.00001000.000100|10 10.0.8.18
Broadcast Address 00001010.00000000.00001000.000100|11 10.0.8.19
Student Name Student Number
Binary Decimal
Network ID 00001010.00000000.00001000.000011|00 10.0.8.12
HeadOffice RouterIP 00001010.00000000.00001000.000011|01 10.0.8.13
Research Router IP 00001010.00000000.00001000.000011|10 10.0.8.14
Broadcast Address 00001010.00000000.00001000.000011|11 10.0.8.15
Head Office - Sales Router
Binary Decimal
Network ID 00001010.00000000.00001000.000100|00 10.0.8.16
Head Office Router
IP 00001010.00000000.00001000.000100|01
10.0.8.17
Sales Router IP 00001010.00000000.00001000.000100|10 10.0.8.18
Broadcast Address 00001010.00000000.00001000.000100|11 10.0.8.19
Student Name Student Number
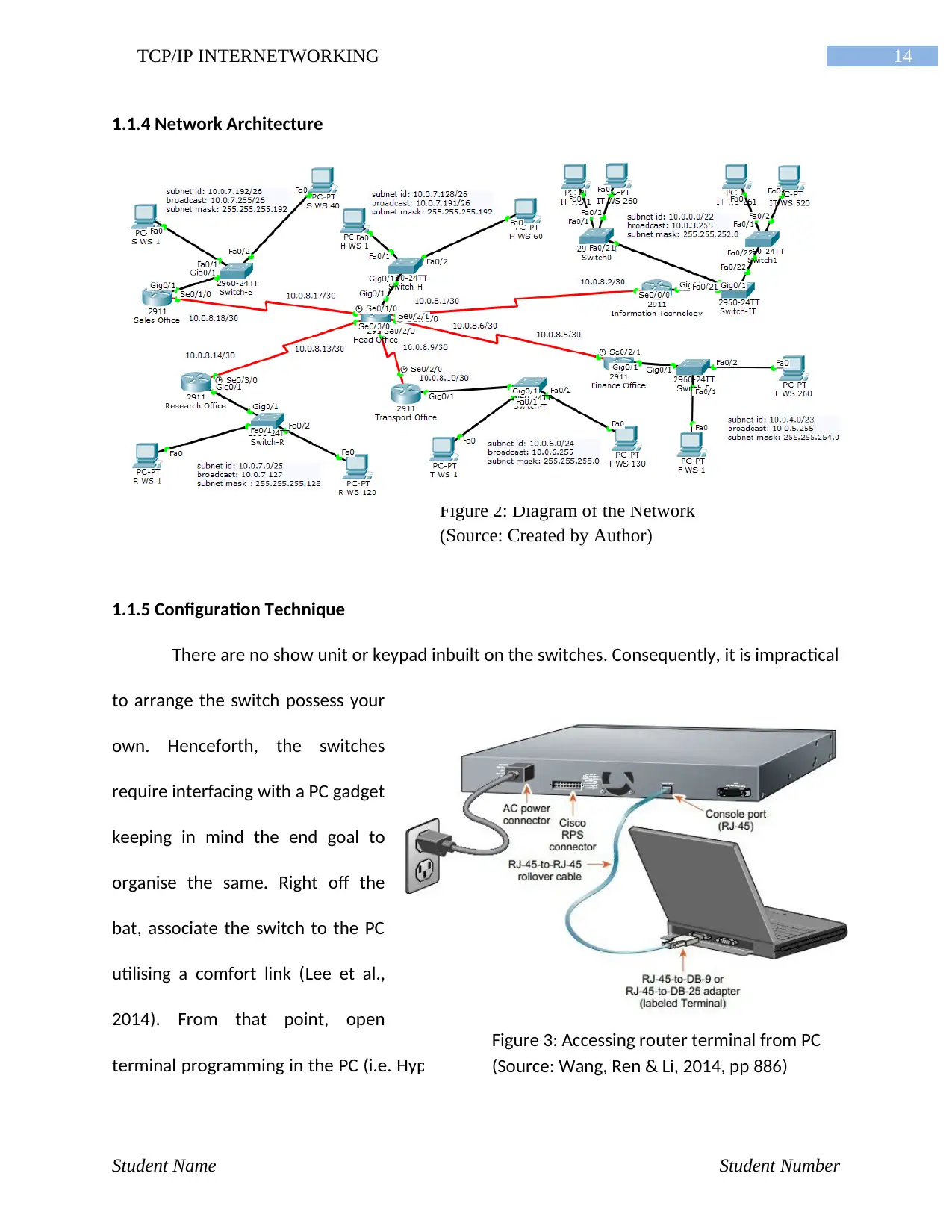
Figure 2: Diagram of the Network
(Source: Created by Author)
14TCP/IP INTERNETWORKING
1.1.4 Network Architecture
1.1.5 Configuration Technique
There are no show unit or keypad inbuilt on the switches. Consequently, it is impractical
to arrange the switch possess your
own. Henceforth, the switches
require interfacing with a PC gadget
keeping in mind the end goal to
organise the same. Right off the
bat, associate the switch to the PC
utilising a comfort link (Lee et al.,
2014). From that point, open
terminal programming in the PC (i.e. Hyper Terminal) and after that have a go at getting to the
Student Name Student Number
Figure 3: Accessing router terminal from PC
(Source: Wang, Ren & Li, 2014, pp 886)
(Source: Created by Author)
14TCP/IP INTERNETWORKING
1.1.4 Network Architecture
1.1.5 Configuration Technique
There are no show unit or keypad inbuilt on the switches. Consequently, it is impractical
to arrange the switch possess your
own. Henceforth, the switches
require interfacing with a PC gadget
keeping in mind the end goal to
organise the same. Right off the
bat, associate the switch to the PC
utilising a comfort link (Lee et al.,
2014). From that point, open
terminal programming in the PC (i.e. Hyper Terminal) and after that have a go at getting to the
Student Name Student Number
Figure 3: Accessing router terminal from PC
(Source: Wang, Ren & Li, 2014, pp 886)

15TCP/IP INTERNETWORKING
port in which the switch is associated. After fruitful endeavour, the charge terminal for the
switch will open on the PC screen. There every one of the setups should have been finished.
1.2 What if host number increases over 1024 per department ?
The hosts are being used per working starting at now is most extreme 520 on account of
Information Technology division. There are 1022 IPs assigned to IT group in which 520 IPs are
being used (Richards & Petras, 2015). Whatever is left of the offices are sub-gotten in a way that
a significant portion of the IPs is used moving insignificant IPs that are squandered. In any case,
the present outline will most likely face intense circumstances if the number of workstations
increments to more than 1024. The possible events are talked about as beneath:
1.2.1 Difficulties
The across the board system will end up plainly out of skill for the present system
director.
The system will turn out to be more muddled, and it will end up visibly intense to
investigate if any breakdown happens.
The divisions are altogether arranged to utilise static steering. The increment in have
number will influence the head gravely.
Not a solitary of the office has the accessible IPs share to allocate them to those
workstations.
If the additional hosts shape another system inside the separate room, it will turn out to
be difficult to arrange VLANs to associate those workstations.
Student Name Student Number
port in which the switch is associated. After fruitful endeavour, the charge terminal for the
switch will open on the PC screen. There every one of the setups should have been finished.
1.2 What if host number increases over 1024 per department ?
The hosts are being used per working starting at now is most extreme 520 on account of
Information Technology division. There are 1022 IPs assigned to IT group in which 520 IPs are
being used (Richards & Petras, 2015). Whatever is left of the offices are sub-gotten in a way that
a significant portion of the IPs is used moving insignificant IPs that are squandered. In any case,
the present outline will most likely face intense circumstances if the number of workstations
increments to more than 1024. The possible events are talked about as beneath:
1.2.1 Difficulties
The across the board system will end up plainly out of skill for the present system
director.
The system will turn out to be more muddled, and it will end up visibly intense to
investigate if any breakdown happens.
The divisions are altogether arranged to utilise static steering. The increment in have
number will influence the head gravely.
Not a solitary of the office has the accessible IPs share to allocate them to those
workstations.
If the additional hosts shape another system inside the separate room, it will turn out to
be difficult to arrange VLANs to associate those workstations.
Student Name Student Number
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16TCP/IP INTERNETWORKING
TASK 2: Network Analysis
2.1 Networking Protocols
A few interconnected gadgets shape a Network. The transmission of information
between the switches utilises the layer three medium where data units are parcels containing
its source and goal IP addresses. Setting up a correspondence channel requires a ton of set of
principles or guideline performed persistently on the network medium to ensure and safely set
up availability (Wang, Ren & Li, 2014). That arrangement of laws or conventions trades
information in the middle of when end clients are not transmitting any information.
Subsequently, the procedures concerning the system stay obscure to the end client. There are
constantly a few provisos remains regardless of how much the innovation propels. The
likelihood is dependably there of trading off of data by unapproved clients getting a too
particular gadget or following a system, and the system chairman stays uninformed of the
aggregate situation. From that point, the requirement for organising investigating instruments
come in advance. System Analyser or Packet Analyser, these are the projects using the parts of
PC equipment to catch the movement going through the system and records the log out of it. It
shows the information stream data flowing through the system if required it additionally
captures those packets and enables the head to audit the bundle data.
Conventions are set of tenets tends to some specific undertakings related to it. In a
correspondence organise, different protocols exist and works at various levels (Keceli, Inan &
Ayanoglu, 2015). The Transmission Control Protocol or TCP is one of those conventions that
trade messages at parcel level on the web. Moreover, Internet Protocol or IP transmits
messages at the Internet Address Level, and HTTP or Hypertext Transfer Protocol send and get
Student Name Student Number
TASK 2: Network Analysis
2.1 Networking Protocols
A few interconnected gadgets shape a Network. The transmission of information
between the switches utilises the layer three medium where data units are parcels containing
its source and goal IP addresses. Setting up a correspondence channel requires a ton of set of
principles or guideline performed persistently on the network medium to ensure and safely set
up availability (Wang, Ren & Li, 2014). That arrangement of laws or conventions trades
information in the middle of when end clients are not transmitting any information.
Subsequently, the procedures concerning the system stay obscure to the end client. There are
constantly a few provisos remains regardless of how much the innovation propels. The
likelihood is dependably there of trading off of data by unapproved clients getting a too
particular gadget or following a system, and the system chairman stays uninformed of the
aggregate situation. From that point, the requirement for organising investigating instruments
come in advance. System Analyser or Packet Analyser, these are the projects using the parts of
PC equipment to catch the movement going through the system and records the log out of it. It
shows the information stream data flowing through the system if required it additionally
captures those packets and enables the head to audit the bundle data.
Conventions are set of tenets tends to some specific undertakings related to it. In a
correspondence organise, different protocols exist and works at various levels (Keceli, Inan &
Ayanoglu, 2015). The Transmission Control Protocol or TCP is one of those conventions that
trade messages at parcel level on the web. Moreover, Internet Protocol or IP transmits
messages at the Internet Address Level, and HTTP or Hypertext Transfer Protocol send and get
Student Name Student Number

17TCP/IP INTERNETWORKING
HTML records on the web program. There are different conventions accessible playing out a
particular errand simply like this illustrations. Aggressors to hack a framework or remotely get
to or screen exercises of various clients utilise a portion of the conventions. In this manner, it is
important to think about meetings that are helpful and conventions those are defenceless
against dangers.
2.2 Network Analysis of M2M Solution
The association prior did not permit organise investigating. The reason was about its
information security and the classification of the information. In any case, when contrasted
with past situation when every one of the offices was at a similar place there was less
difference in external risk that is currently expanded tremendously in light of distinctively
situating all through the city (Richards & Petras, 2015). The more the system developed, the
more it is closer to external dangers. An unpredictable system plan that needs numerous
security levels is consistently helpless; if at any unapproved rate client accesses the system,
there is no way to recognise that risk. Presently, the association is situated in six unique ranges
that are associated with its particular system. If any one area was hacked or any programmer
blocks the signs on the halfway that may hurt the protection of a huge number of people
groups. In this manner, organise breaking down devices are desperately required for this
reason. The contextual investigation likewise recommends its significance in the association.
2.2.1 Advantages of Network Analysis
Hazard Reduction: The continuous checking of topologies, port affiliations and systems
administration conventions activity diminishes the risk.
Student Name Student Number
HTML records on the web program. There are different conventions accessible playing out a
particular errand simply like this illustrations. Aggressors to hack a framework or remotely get
to or screen exercises of various clients utilise a portion of the conventions. In this manner, it is
important to think about meetings that are helpful and conventions those are defenceless
against dangers.
2.2 Network Analysis of M2M Solution
The association prior did not permit organise investigating. The reason was about its
information security and the classification of the information. In any case, when contrasted
with past situation when every one of the offices was at a similar place there was less
difference in external risk that is currently expanded tremendously in light of distinctively
situating all through the city (Richards & Petras, 2015). The more the system developed, the
more it is closer to external dangers. An unpredictable system plan that needs numerous
security levels is consistently helpless; if at any unapproved rate client accesses the system,
there is no way to recognise that risk. Presently, the association is situated in six unique ranges
that are associated with its particular system. If any one area was hacked or any programmer
blocks the signs on the halfway that may hurt the protection of a huge number of people
groups. In this manner, organise breaking down devices are desperately required for this
reason. The contextual investigation likewise recommends its significance in the association.
2.2.1 Advantages of Network Analysis
Hazard Reduction: The continuous checking of topologies, port affiliations and systems
administration conventions activity diminishes the risk.
Student Name Student Number

18TCP/IP INTERNETWORKING
Execution Report: The ideal resource usage accomplishes benefit level understandings
that record the performance reports.
System Optimization: The accessibility of system network interfaces two closures
consistently. Advancement of the scheme will lessen insignificant system activity that
will without a doubt increment the execution of the system.
Cost Reduction: The gadgets empowering IPs is in its development. A system-checking
framework gives full system hardware to use organising resources at appropriate
planning that improves the running expense of the system.
Cost of the Tool
The system analyser instrument comes as an individual equipment that must be
introduced on the network portal. It will check all the activity and afterwards after confirmation
those will be permitted (Richards & Petras, 2015). Wireshark is an exceptionally renowned
name in the field of system examination it comes free with some restricted components. In any
case, it can be moved up to its top notch form that charges around $600 for a permit for one
year that includes some precious elements.
Ease of usability
Wireshark installer comes free, and it can be downloaded from
https://www.wireshark.org/download.html. After downloading and introducing Wireshark once
it begins running, it will demonstrate a rundown of interfaces that you need to screen. Select
your preferred interface from your run down from an extensive variety of remote to Ethernet.
Presently picking your choice, it will furnish you with the alternative to catch channel where
you will see the system activity log that can be efficiently checked. There the subtle port
Student Name Student Number
Execution Report: The ideal resource usage accomplishes benefit level understandings
that record the performance reports.
System Optimization: The accessibility of system network interfaces two closures
consistently. Advancement of the scheme will lessen insignificant system activity that
will without a doubt increment the execution of the system.
Cost Reduction: The gadgets empowering IPs is in its development. A system-checking
framework gives full system hardware to use organising resources at appropriate
planning that improves the running expense of the system.
Cost of the Tool
The system analyser instrument comes as an individual equipment that must be
introduced on the network portal. It will check all the activity and afterwards after confirmation
those will be permitted (Richards & Petras, 2015). Wireshark is an exceptionally renowned
name in the field of system examination it comes free with some restricted components. In any
case, it can be moved up to its top notch form that charges around $600 for a permit for one
year that includes some precious elements.
Ease of usability
Wireshark installer comes free, and it can be downloaded from
https://www.wireshark.org/download.html. After downloading and introducing Wireshark once
it begins running, it will demonstrate a rundown of interfaces that you need to screen. Select
your preferred interface from your run down from an extensive variety of remote to Ethernet.
Presently picking your choice, it will furnish you with the alternative to catch channel where
you will see the system activity log that can be efficiently checked. There the subtle port
Student Name Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19TCP/IP INTERNETWORKING
elements, conventions name will be composed to influence you to comprehend what those
stands for.
Recommendation
The wrongdoings on the system are expanding step by step. The current ransomware
occurrence that happens where programmers broke the firewalls of Honda's branch and
hindered their framework requesting pay-off consequently to unblock the framework. It is to be
prescribed to utilise Wireshark application on account of its fundamental approach towards its
client with a simple User Interface it moves toward becoming for easy to understand. However,
the security calculations utilised as a part of this field requires changes given the defect that
remaining parts in the framework. It is still vulnerable to dangers.
Student Name Student Number
elements, conventions name will be composed to influence you to comprehend what those
stands for.
Recommendation
The wrongdoings on the system are expanding step by step. The current ransomware
occurrence that happens where programmers broke the firewalls of Honda's branch and
hindered their framework requesting pay-off consequently to unblock the framework. It is to be
prescribed to utilise Wireshark application on account of its fundamental approach towards its
client with a simple User Interface it moves toward becoming for easy to understand. However,
the security calculations utilised as a part of this field requires changes given the defect that
remaining parts in the framework. It is still vulnerable to dangers.
Student Name Student Number

20TCP/IP INTERNETWORKING
References
Abed, G. (2016). Principles of Congestion Control for Transmission Control Protocol. Scholars
Press.
Cui, Y., Wang, L., Wang, X., Wang, H., & Wang, Y. (2015). FMTCP: A fountain code-based
multipath transmission control protocol. IEEE/ACM Transactions on Networking
(TON), 23(2), 465-478.
Duke, M., Blanton, E., Zimmermann, A., Braden, R., & Eddy, W. (2015). A roadmap for
transmission control protocol (TCP) specification documents.
Keceli, F., Inan, I., & Ayanoglu, E. (2015). Fair and efficient Transmission Control Protocol access
in the IEEE 802.11 infrastructure basic service set. Wireless Communications and Mobile
Computing, 15(9), 1376-1390.
Khalifa, T., Abdrabou, A., Naik, K., Alsabaan, M., Nayak, A., & Goel, N. (2014). Split-and
aggregated-transmission control protocol (SA-TCP) for smart power grid. IEEE
Transactions on Smart Grid, 5(1), 381-391.
Lee, K. C., Balasubramanian, S., Wang, J., & Cherian, G. (2014). U.S. Patent No. 8,780,858.
Washington, DC: U.S. Patent and Trademark Office.
Richards, C., & Petras, M. W. (2015). U.S. Patent Application No. 14/423,797.
Wang, G., Ren, Y., & Li, J. (2014). An effective approach to alleviating the challenges of
transmission control protocol. IET Communications, 8(6), 860-869.
Student Name Student Number
References
Abed, G. (2016). Principles of Congestion Control for Transmission Control Protocol. Scholars
Press.
Cui, Y., Wang, L., Wang, X., Wang, H., & Wang, Y. (2015). FMTCP: A fountain code-based
multipath transmission control protocol. IEEE/ACM Transactions on Networking
(TON), 23(2), 465-478.
Duke, M., Blanton, E., Zimmermann, A., Braden, R., & Eddy, W. (2015). A roadmap for
transmission control protocol (TCP) specification documents.
Keceli, F., Inan, I., & Ayanoglu, E. (2015). Fair and efficient Transmission Control Protocol access
in the IEEE 802.11 infrastructure basic service set. Wireless Communications and Mobile
Computing, 15(9), 1376-1390.
Khalifa, T., Abdrabou, A., Naik, K., Alsabaan, M., Nayak, A., & Goel, N. (2014). Split-and
aggregated-transmission control protocol (SA-TCP) for smart power grid. IEEE
Transactions on Smart Grid, 5(1), 381-391.
Lee, K. C., Balasubramanian, S., Wang, J., & Cherian, G. (2014). U.S. Patent No. 8,780,858.
Washington, DC: U.S. Patent and Trademark Office.
Richards, C., & Petras, M. W. (2015). U.S. Patent Application No. 14/423,797.
Wang, G., Ren, Y., & Li, J. (2014). An effective approach to alleviating the challenges of
transmission control protocol. IET Communications, 8(6), 860-869.
Student Name Student Number
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





