Electrical Networking: Metcalfe’s Law, Cache Memory and IoT Report
VerifiedAdded on 2023/06/05
|13
|1999
|183
Report
AI Summary
This report delves into fundamental networking concepts, starting with Metcalfe's Law and its implications for network value. It explores cache memory, its function in speeding up CPU operations, and different mapping methods. The report includes a truth table analysis and a detailed explanation of the IEEE 754 standard for floating-point numbers, including its components and special values. Furthermore, it discusses the Internet of Things (IoT), its applications in various sectors like smart homes, smart cities, and connected health, and the challenges associated with its implementation, such as meeting client expectations and overcoming connectivity issues. The report concludes by highlighting the outcomes of using IoT, including machine learning and the shift from product-centric to platform-based business models. This document is available on Desklib, a platform offering a wide range of study resources for students.

BACHELOR OF NETWORKING 1
BACHELOR OF NETWORKING
Authors Name/s per 1st Affiliation (Author)
Dept. name of the organization
Name of organization, acronyms acceptable
City, Country
e-mail address
Authors Name/s per 2nd Affiliation (Author)
Dept. name of the organization
Name of organization, acronyms acceptable
City, Country
e-mail address
BACHELOR OF NETWORKING
Authors Name/s per 1st Affiliation (Author)
Dept. name of the organization
Name of organization, acronyms acceptable
City, Country
e-mail address
Authors Name/s per 2nd Affiliation (Author)
Dept. name of the organization
Name of organization, acronyms acceptable
City, Country
e-mail address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Electrical power 2
Part A
Question 1
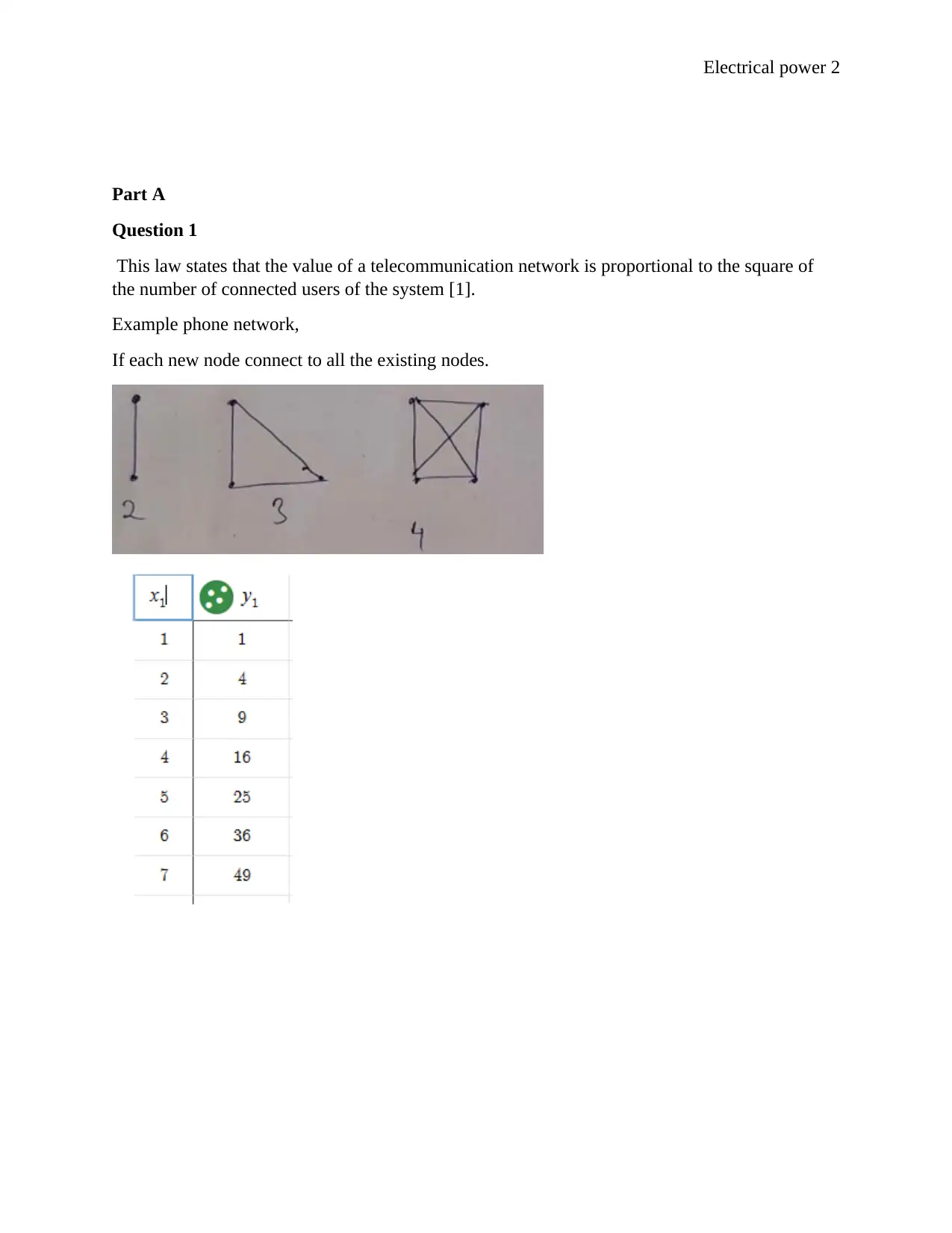
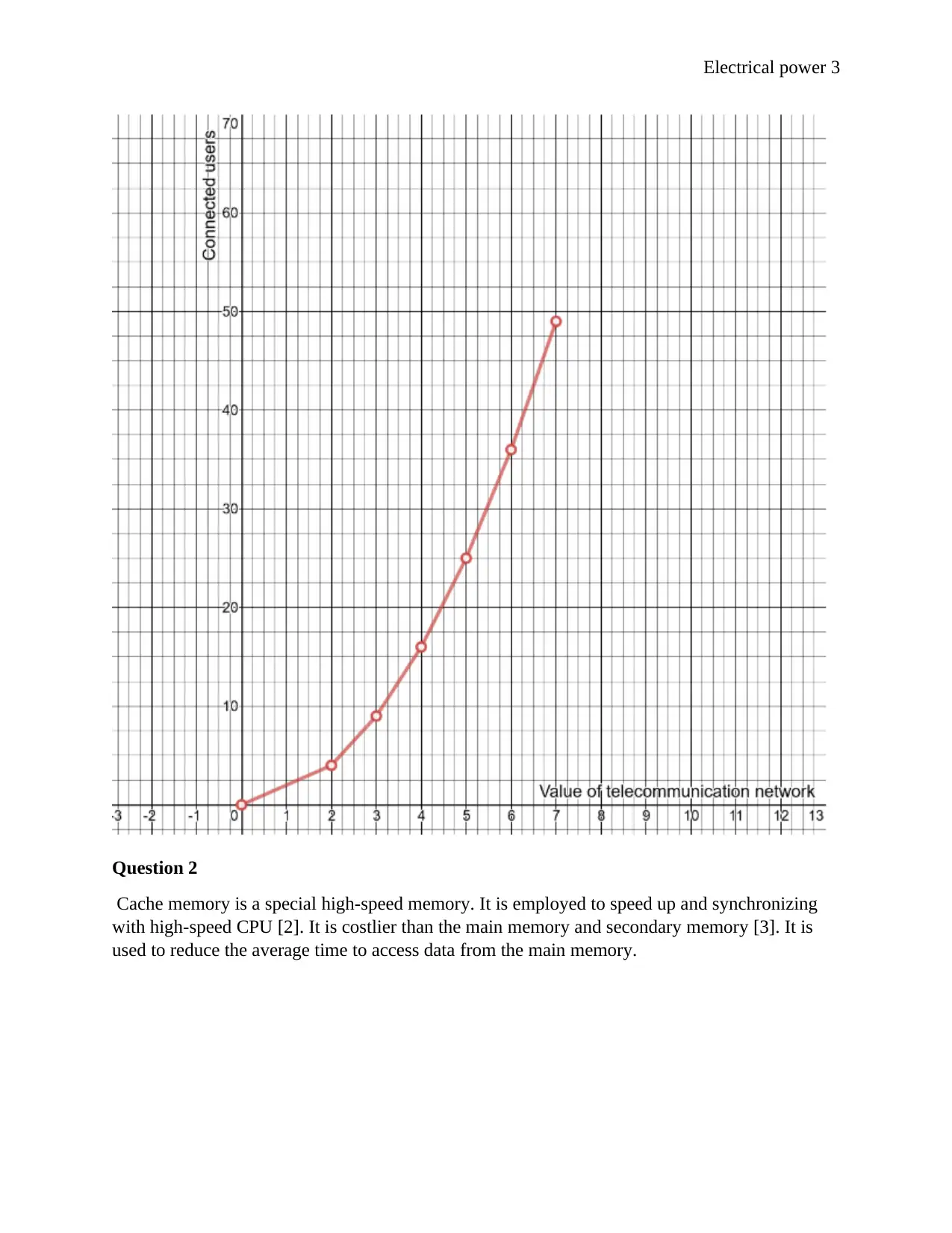
This law states that the value of a telecommunication network is proportional to the square of
the number of connected users of the system [1].
Example phone network,
If each new node connect to all the existing nodes.
Part A
Question 1
This law states that the value of a telecommunication network is proportional to the square of
the number of connected users of the system [1].
Example phone network,
If each new node connect to all the existing nodes.
Electrical power 3
Question 2
Cache memory is a special high-speed memory. It is employed to speed up and synchronizing
with high-speed CPU [2]. It is costlier than the main memory and secondary memory [3]. It is
used to reduce the average time to access data from the main memory.
Question 2
Cache memory is a special high-speed memory. It is employed to speed up and synchronizing
with high-speed CPU [2]. It is costlier than the main memory and secondary memory [3]. It is
used to reduce the average time to access data from the main memory.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Electrical power 4
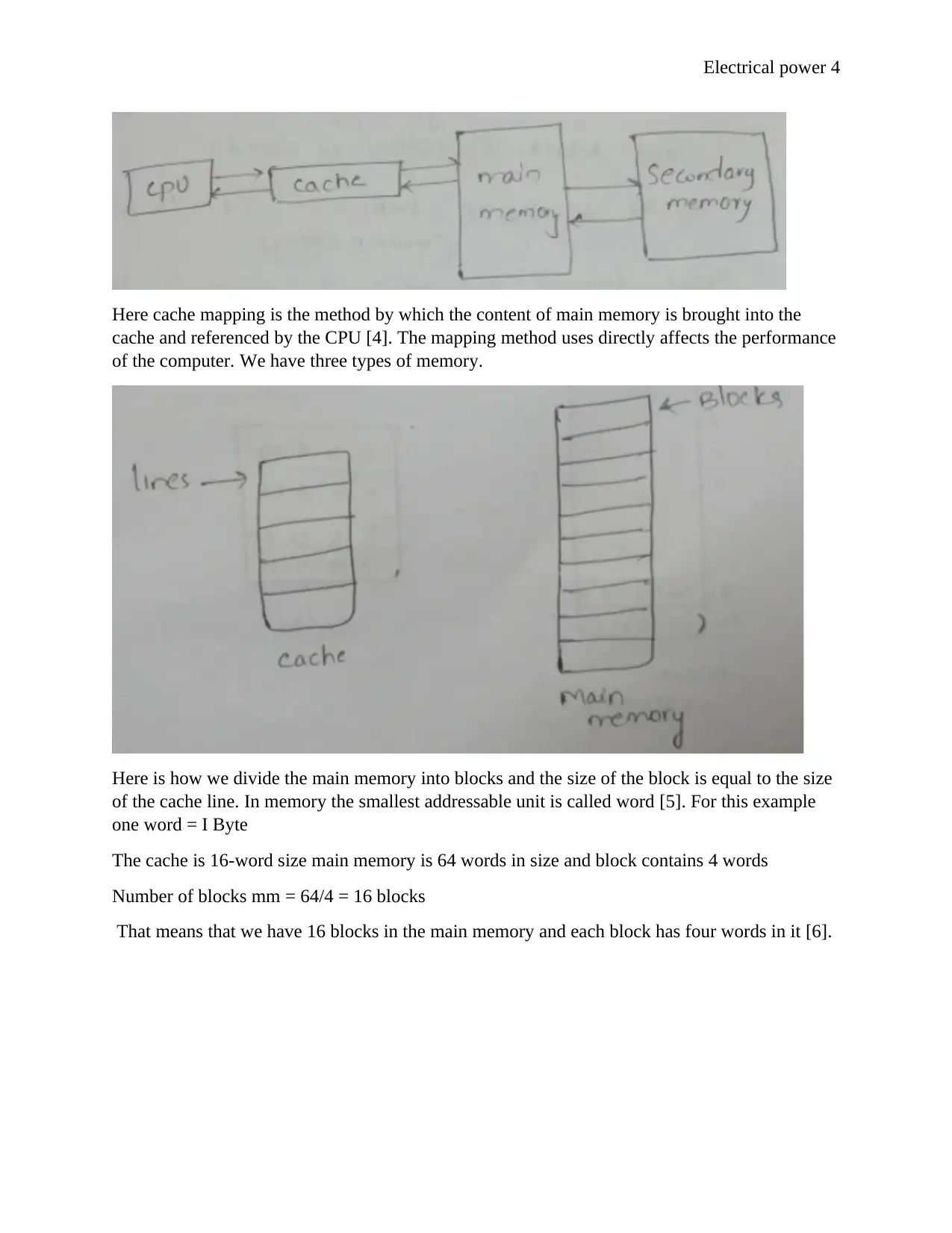
Here cache mapping is the method by which the content of main memory is brought into the
cache and referenced by the CPU [4]. The mapping method uses directly affects the performance
of the computer. We have three types of memory.
Here is how we divide the main memory into blocks and the size of the block is equal to the size
of the cache line. In memory the smallest addressable unit is called word [5]. For this example
one word = I Byte
The cache is 16-word size main memory is 64 words in size and block contains 4 words
Number of blocks mm = 64/4 = 16 blocks
That means that we have 16 blocks in the main memory and each block has four words in it [6].
Here cache mapping is the method by which the content of main memory is brought into the
cache and referenced by the CPU [4]. The mapping method uses directly affects the performance
of the computer. We have three types of memory.
Here is how we divide the main memory into blocks and the size of the block is equal to the size
of the cache line. In memory the smallest addressable unit is called word [5]. For this example
one word = I Byte
The cache is 16-word size main memory is 64 words in size and block contains 4 words
Number of blocks mm = 64/4 = 16 blocks
That means that we have 16 blocks in the main memory and each block has four words in it [6].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Electrical power 5
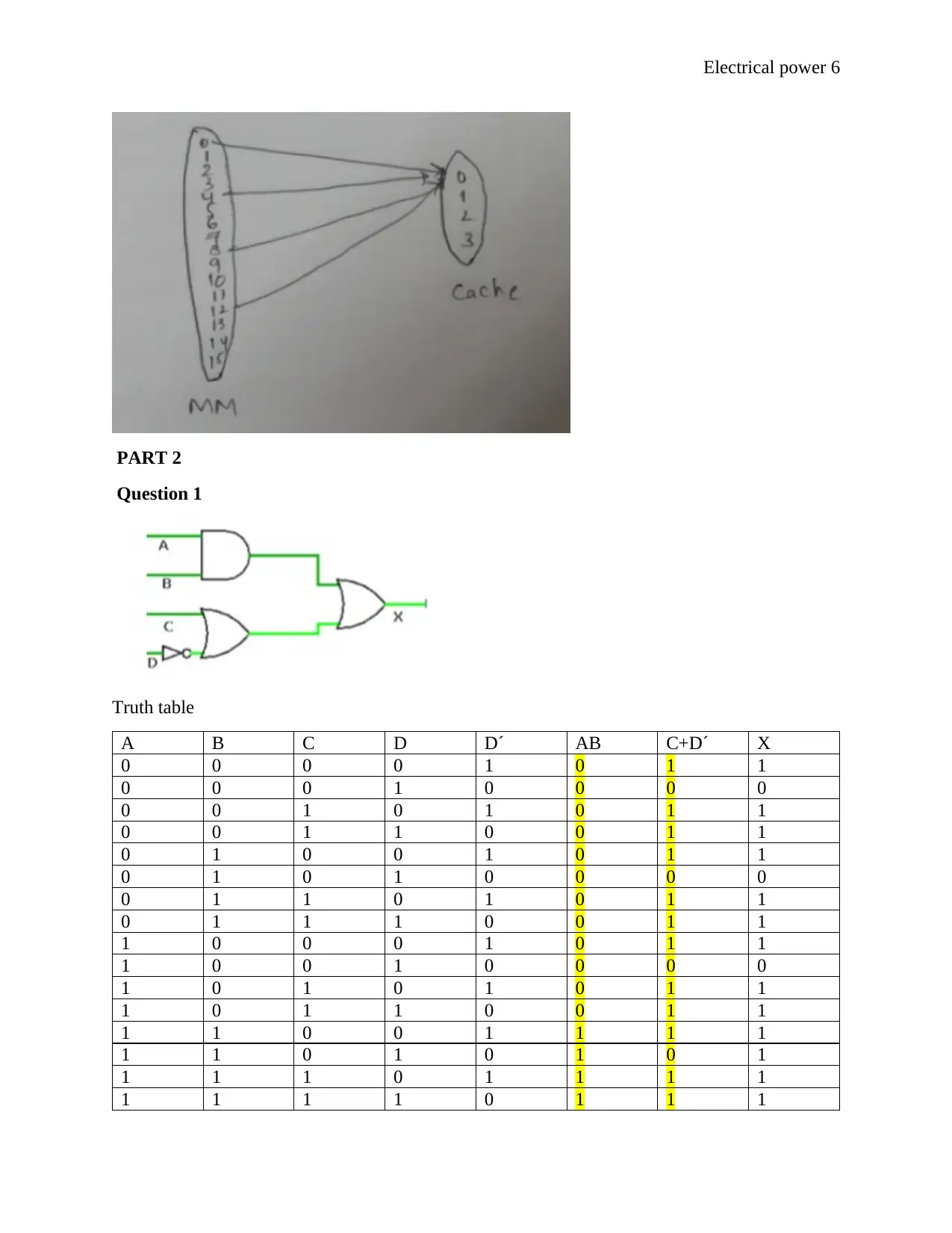
CPU generates an address, The address should represent 64 words. So 6 bits, the six bits can be
divided into two parts as below
Example 010110
This number in decimal is 22 it hence means that 22nd word is represented in this address
The block number represented by 4 bit because of 16 blocks in main memory ( 24 = 16)
0101 = block 5 means 5th line last two bits = 10 2
So in block 5, 2nd-word direct mapping will follow 1 to many mapping as given by the following
diagram
CPU generates an address, The address should represent 64 words. So 6 bits, the six bits can be
divided into two parts as below
Example 010110
This number in decimal is 22 it hence means that 22nd word is represented in this address
The block number represented by 4 bit because of 16 blocks in main memory ( 24 = 16)
0101 = block 5 means 5th line last two bits = 10 2
So in block 5, 2nd-word direct mapping will follow 1 to many mapping as given by the following
diagram
Electrical power 6
PART 2
Question 1
Truth table
A B C D D´ AB C+D´ X
0 0 0 0 1 0 1 1
0 0 0 1 0 0 0 0
0 0 1 0 1 0 1 1
0 0 1 1 0 0 1 1
0 1 0 0 1 0 1 1
0 1 0 1 0 0 0 0
0 1 1 0 1 0 1 1
0 1 1 1 0 0 1 1
1 0 0 0 1 0 1 1
1 0 0 1 0 0 0 0
1 0 1 0 1 0 1 1
1 0 1 1 0 0 1 1
1 1 0 0 1 1 1 1
1 1 0 1 0 1 0 1
1 1 1 0 1 1 1 1
1 1 1 1 0 1 1 1
PART 2
Question 1
Truth table
A B C D D´ AB C+D´ X
0 0 0 0 1 0 1 1
0 0 0 1 0 0 0 0
0 0 1 0 1 0 1 1
0 0 1 1 0 0 1 1
0 1 0 0 1 0 1 1
0 1 0 1 0 0 0 0
0 1 1 0 1 0 1 1
0 1 1 1 0 0 1 1
1 0 0 0 1 0 1 1
1 0 0 1 0 0 0 0
1 0 1 0 1 0 1 1
1 0 1 1 0 0 1 1
1 1 0 0 1 1 1 1
1 1 0 1 0 1 0 1
1 1 1 0 1 1 1 1
1 1 1 1 0 1 1 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Electrical power 7
Question 2
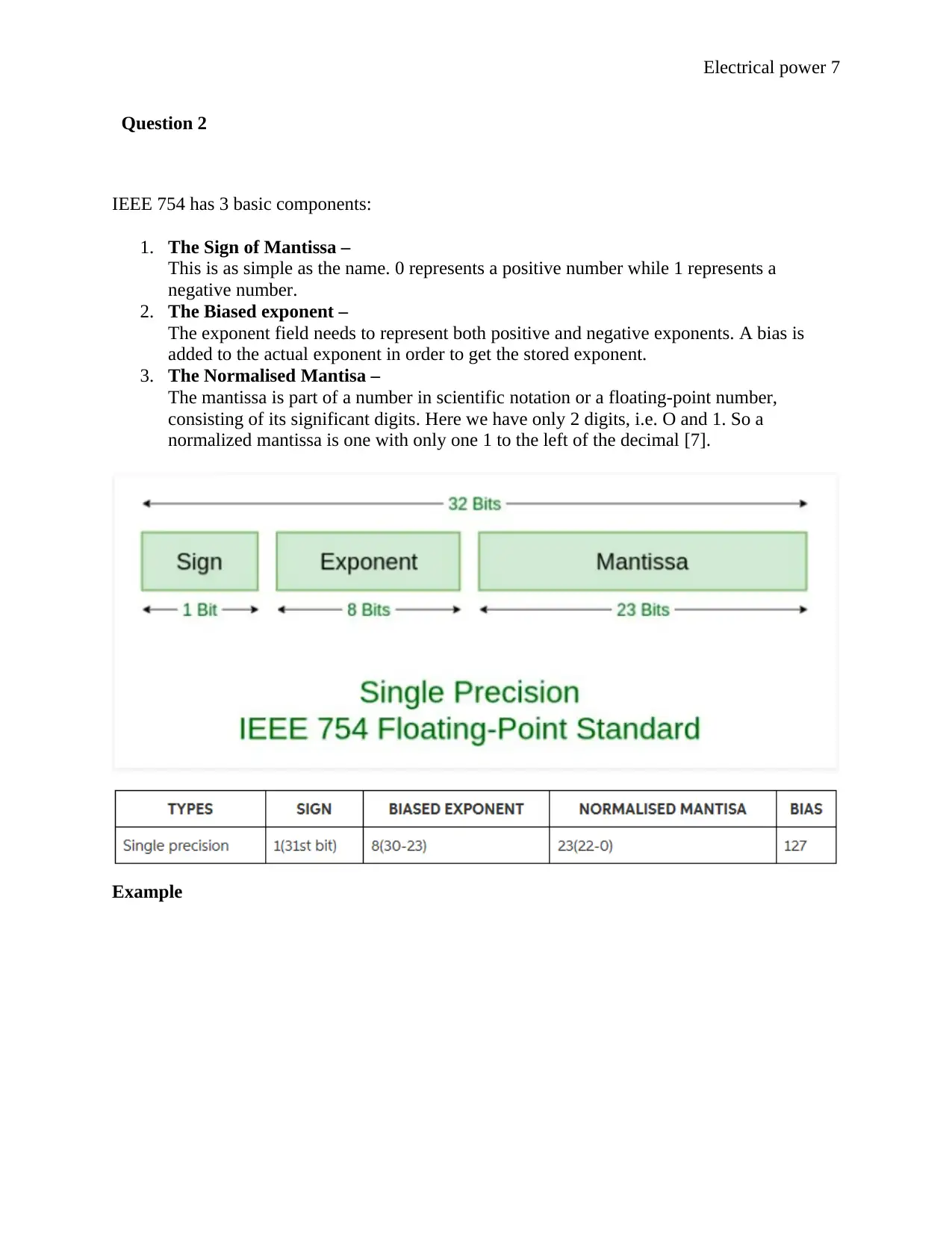
IEEE 754 has 3 basic components:
1. The Sign of Mantissa –
This is as simple as the name. 0 represents a positive number while 1 represents a
negative number.
2. The Biased exponent –
The exponent field needs to represent both positive and negative exponents. A bias is
added to the actual exponent in order to get the stored exponent.
3. The Normalised Mantisa –
The mantissa is part of a number in scientific notation or a floating-point number,
consisting of its significant digits. Here we have only 2 digits, i.e. O and 1. So a
normalized mantissa is one with only one 1 to the left of the decimal [7].
Example
Question 2
IEEE 754 has 3 basic components:
1. The Sign of Mantissa –
This is as simple as the name. 0 represents a positive number while 1 represents a
negative number.
2. The Biased exponent –
The exponent field needs to represent both positive and negative exponents. A bias is
added to the actual exponent in order to get the stored exponent.
3. The Normalised Mantisa –
The mantissa is part of a number in scientific notation or a floating-point number,
consisting of its significant digits. Here we have only 2 digits, i.e. O and 1. So a
normalized mantissa is one with only one 1 to the left of the decimal [7].
Example
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Electrical power 8
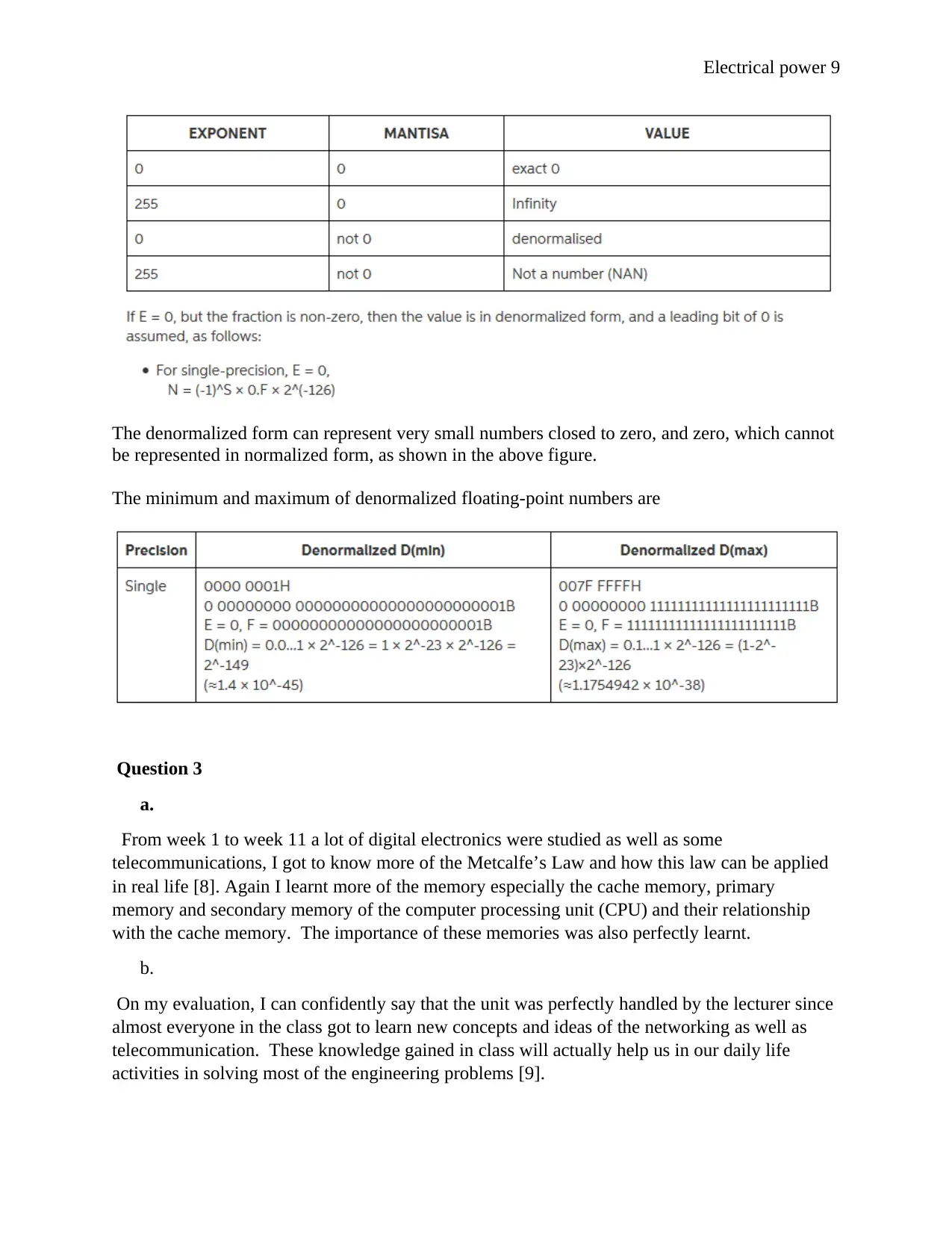
IEEE has reserved some values that can ambiguity.
Zero –
Zero is a special value denoted with an exponent and mantissa of 0. -0 and +0 are distinct
values, though they both are equal.
Denormalised –
If the exponent is all zeros, but the mantissa is not then the value is a denormalized
number. This means this number does not have an assumed leading one before the binary
point.
Infinity –
The values +infinity and -infinity are denoted with an exponent of all ones and a mantissa
of all zeros. The sign bit distinguishes between negative infinity and positive infinity.
Operations with infinite values are well defined in IEEE.
Not A Number (NAN) –The value NAN is used to represent a value that is an error. This
is represented when exponent field is all ones with a zero sign bit or a mantissa that it, not
1 followed by zeros. This is a special value that might be used to denote a variable that
doesn't yet hold value.
IEEE has reserved some values that can ambiguity.
Zero –
Zero is a special value denoted with an exponent and mantissa of 0. -0 and +0 are distinct
values, though they both are equal.
Denormalised –
If the exponent is all zeros, but the mantissa is not then the value is a denormalized
number. This means this number does not have an assumed leading one before the binary
point.
Infinity –
The values +infinity and -infinity are denoted with an exponent of all ones and a mantissa
of all zeros. The sign bit distinguishes between negative infinity and positive infinity.
Operations with infinite values are well defined in IEEE.
Not A Number (NAN) –The value NAN is used to represent a value that is an error. This
is represented when exponent field is all ones with a zero sign bit or a mantissa that it, not
1 followed by zeros. This is a special value that might be used to denote a variable that
doesn't yet hold value.
Electrical power 9
The denormalized form can represent very small numbers closed to zero, and zero, which cannot
be represented in normalized form, as shown in the above figure.
The minimum and maximum of denormalized floating-point numbers are
Question 3
a.
From week 1 to week 11 a lot of digital electronics were studied as well as some
telecommunications, I got to know more of the Metcalfe’s Law and how this law can be applied
in real life [8]. Again I learnt more of the memory especially the cache memory, primary
memory and secondary memory of the computer processing unit (CPU) and their relationship
with the cache memory. The importance of these memories was also perfectly learnt.
b.
On my evaluation, I can confidently say that the unit was perfectly handled by the lecturer since
almost everyone in the class got to learn new concepts and ideas of the networking as well as
telecommunication. These knowledge gained in class will actually help us in our daily life
activities in solving most of the engineering problems [9].
The denormalized form can represent very small numbers closed to zero, and zero, which cannot
be represented in normalized form, as shown in the above figure.
The minimum and maximum of denormalized floating-point numbers are
Question 3
a.
From week 1 to week 11 a lot of digital electronics were studied as well as some
telecommunications, I got to know more of the Metcalfe’s Law and how this law can be applied
in real life [8]. Again I learnt more of the memory especially the cache memory, primary
memory and secondary memory of the computer processing unit (CPU) and their relationship
with the cache memory. The importance of these memories was also perfectly learnt.
b.
On my evaluation, I can confidently say that the unit was perfectly handled by the lecturer since
almost everyone in the class got to learn new concepts and ideas of the networking as well as
telecommunication. These knowledge gained in class will actually help us in our daily life
activities in solving most of the engineering problems [9].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Electrical power 10
c.
On the unit feedback, I can just say that the unit was perfectly handled and the lecturer was fully
committed to the course. The students also did their best to help them understand the unit
perfectly as it was taught by the lecturer.
PART C
Question 1
Background and challenges
Internet of things is a technology which has the intersection of design, business models,
sensors and networks. Basically, this is an idea of the wireless communication as well as the
digital intelligence which is in most cases embedded into almost everything we use for example
building, clothing, flowerbeds, vehicles and even the ground beneath our feet. Internet of things
has been made possible due to the fact that there is actually advances in technology as well as
manufacturing. And in computing, the components like batteries, chips, sensors, transistors etc
have been made so smaller, higher efficiency and less power consumption [10]. Therefore these
advances in technology make it highly possible and easier to incorporate computing technology
in almost everything like environment, devices and objects. The internet of things faces some of
the challenges which are listed below;
Meeting the client expectation. It is somehow challenging to meet the client´s expectation
with the use of the internet of things. This is because human minds are very dynamic and
adverse. You can meet the expectation of few but not all.
Keeping the internet of things hardware updated. It is not always easy to update the
hardware of the IoT.
Overcoming connectivity issues. In most cases, there can be some issues with the connectivity
which actually is not easy to overcome. Therefore the IoT system still faces such issues.
Governmental regulation. For every business person who intends to the internet of thing
device will have to wait for the government regulation which will govern the applications of
these devices. Therefore no one will start using such devices before the government gives the
regulations which govern their applications.
IoT application in block diagram
The internet of things can be applied in most scenarios. This will help in automation and
coordination of most things, below are fields where the internet of Things can be applied;
c.
On the unit feedback, I can just say that the unit was perfectly handled and the lecturer was fully
committed to the course. The students also did their best to help them understand the unit
perfectly as it was taught by the lecturer.
PART C
Question 1
Background and challenges
Internet of things is a technology which has the intersection of design, business models,
sensors and networks. Basically, this is an idea of the wireless communication as well as the
digital intelligence which is in most cases embedded into almost everything we use for example
building, clothing, flowerbeds, vehicles and even the ground beneath our feet. Internet of things
has been made possible due to the fact that there is actually advances in technology as well as
manufacturing. And in computing, the components like batteries, chips, sensors, transistors etc
have been made so smaller, higher efficiency and less power consumption [10]. Therefore these
advances in technology make it highly possible and easier to incorporate computing technology
in almost everything like environment, devices and objects. The internet of things faces some of
the challenges which are listed below;
Meeting the client expectation. It is somehow challenging to meet the client´s expectation
with the use of the internet of things. This is because human minds are very dynamic and
adverse. You can meet the expectation of few but not all.
Keeping the internet of things hardware updated. It is not always easy to update the
hardware of the IoT.
Overcoming connectivity issues. In most cases, there can be some issues with the connectivity
which actually is not easy to overcome. Therefore the IoT system still faces such issues.
Governmental regulation. For every business person who intends to the internet of thing
device will have to wait for the government regulation which will govern the applications of
these devices. Therefore no one will start using such devices before the government gives the
regulations which govern their applications.
IoT application in block diagram
The internet of things can be applied in most scenarios. This will help in automation and
coordination of most things, below are fields where the internet of Things can be applied;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Electrical power 11
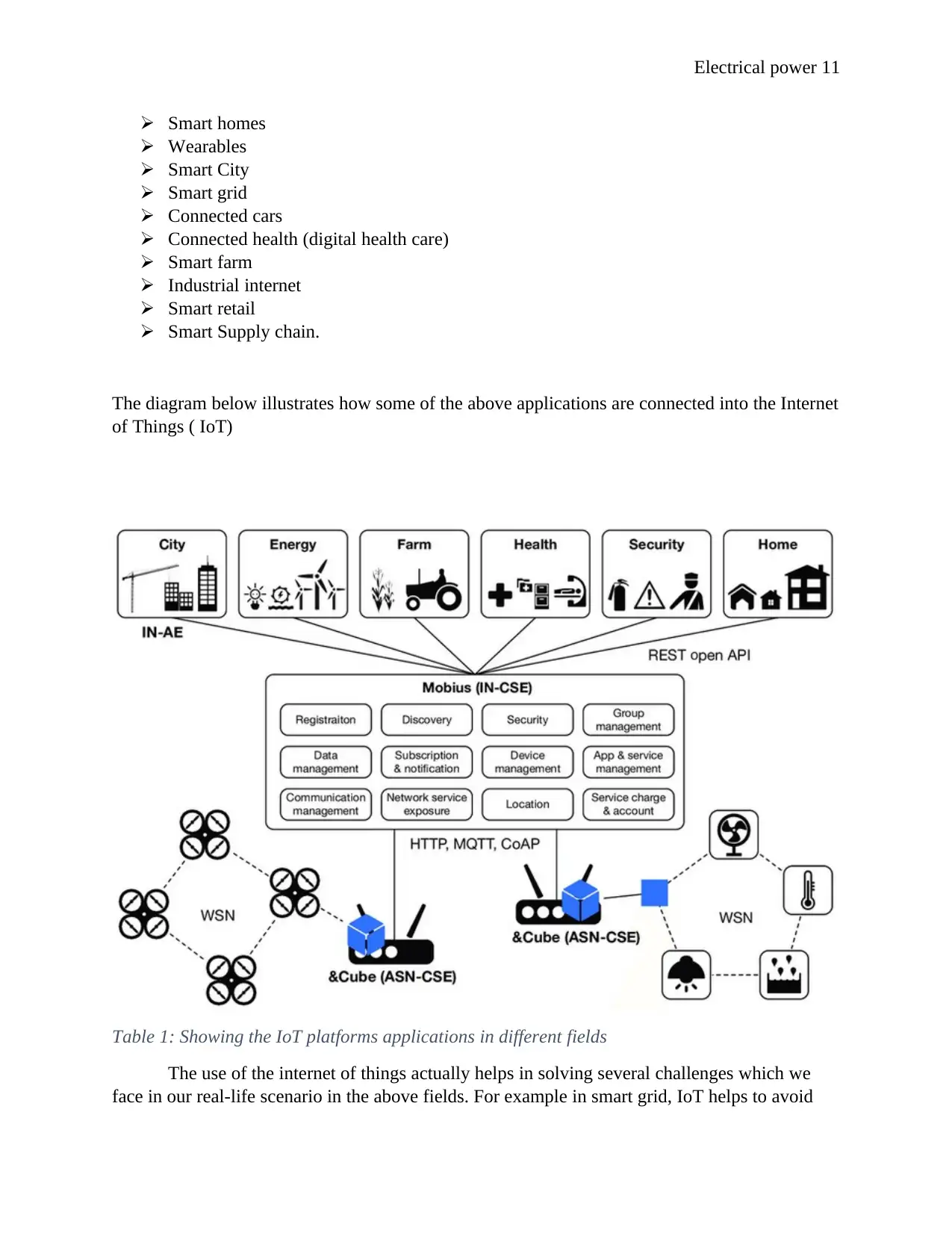
Smart homes
Wearables
Smart City
Smart grid
Connected cars
Connected health (digital health care)
Smart farm
Industrial internet
Smart retail
Smart Supply chain.
The diagram below illustrates how some of the above applications are connected into the Internet
of Things ( IoT)
Table 1: Showing the IoT platforms applications in different fields
The use of the internet of things actually helps in solving several challenges which we
face in our real-life scenario in the above fields. For example in smart grid, IoT helps to avoid
Smart homes
Wearables
Smart City
Smart grid
Connected cars
Connected health (digital health care)
Smart farm
Industrial internet
Smart retail
Smart Supply chain.
The diagram below illustrates how some of the above applications are connected into the Internet
of Things ( IoT)
Table 1: Showing the IoT platforms applications in different fields
The use of the internet of things actually helps in solving several challenges which we
face in our real-life scenario in the above fields. For example in smart grid, IoT helps to avoid

Electrical power 12
the frauds who may interfere with the normal connection of electricity and transmission. In the
farm, IoT helps to avoid the challenges which may be faced by farmers during their crop
cultivations. The use of IoT helps them to get the solutions for these challenges.
Outcome
Below are some of the two main outcomes of using the IoT,
1. Machine learn
Traditionally business had limited insight into what occurs in the business field. For the client´s
office/ home, in the distributors in the transits, on the shop floor. Through capturing continuous
data from a sensor in the business field. Machine learning has both artificial intelligence and data
science discipline, assists isolate the signal from noise in such data streams.
2. From product to platform
A platform for a digital space to equalize demand and supply hence transact business for
example Uber. Platforms contain big benefits over traditional products offerings constituting the
capability to harness network effects. IoT generates new platform opportunities for the
visionaries ready to develop them.
the frauds who may interfere with the normal connection of electricity and transmission. In the
farm, IoT helps to avoid the challenges which may be faced by farmers during their crop
cultivations. The use of IoT helps them to get the solutions for these challenges.
Outcome
Below are some of the two main outcomes of using the IoT,
1. Machine learn
Traditionally business had limited insight into what occurs in the business field. For the client´s
office/ home, in the distributors in the transits, on the shop floor. Through capturing continuous
data from a sensor in the business field. Machine learning has both artificial intelligence and data
science discipline, assists isolate the signal from noise in such data streams.
2. From product to platform
A platform for a digital space to equalize demand and supply hence transact business for
example Uber. Platforms contain big benefits over traditional products offerings constituting the
capability to harness network effects. IoT generates new platform opportunities for the
visionaries ready to develop them.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





