NIDS: Exploring Multiple Gateways for Network Intrusion Detection
VerifiedAdded on 2020/04/21
|20
|3583
|59
Report
AI Summary
This report delves into the realm of Network Intrusion Detection Systems (NIDS), exploring the critical aspects of network security in the face of evolving technological landscapes. It begins by establishing the foundational background of NIDS, emphasizing the necessity of robust security measures to safeguard information from unauthorized access. The report then transitions to the project methodologies employed in NIDS, examining signature-based detection, anomaly-based detection, and stateful protocol analysis, highlighting their respective strengths and limitations. Furthermore, the report outlines a detailed project plan, including a Gantt chart that visualizes the project's schedule, work breakdown structure, and resource allocation. The project objectives are also defined, providing a clear direction for the project's goals. The report also discusses the evaluation of network security devices and the development of a project schedule, offering a comprehensive overview of the NIDS project. Finally, the report concludes with a discussion on the development of project objectives, thereby presenting a holistic perspective on the implementation of NIDS and its significance in maintaining network security. This report is available on Desklib, a platform offering AI-based study tools for students.

Running head: NETWORK INTRUSION DETECTION SYSTEMS
Exploring the Use of Multiple Gateways for Network Intrusion Detection Systems
Name of the student:
Name of the university:
Exploring the Use of Multiple Gateways for Network Intrusion Detection Systems
Name of the student:
Name of the university:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK INTRUSION DETECTION SYSTEMS
Table of Contents
1. Background of Network Intrusion detection system...................................................................2
2. Project methodologies associated to Network Intrusion detection system..................................3
3. Project plan for Network Intrusion detection system or Gantt chart...........................................5
3.1 Explanation of the problem...................................................................................................5
3.2 Evaluation..............................................................................................................................5
3.3 Development of project schedule..........................................................................................7
3.3.1 Schedule of the project...................................................................................................8
3.3.2 Work Breakdown Structure of the project....................................................................13
3.2.3 Resource list for the project..........................................................................................13
4. Development of project objectives............................................................................................16
References......................................................................................................................................18
Table of Contents
1. Background of Network Intrusion detection system...................................................................2
2. Project methodologies associated to Network Intrusion detection system..................................3
3. Project plan for Network Intrusion detection system or Gantt chart...........................................5
3.1 Explanation of the problem...................................................................................................5
3.2 Evaluation..............................................................................................................................5
3.3 Development of project schedule..........................................................................................7
3.3.1 Schedule of the project...................................................................................................8
3.3.2 Work Breakdown Structure of the project....................................................................13
3.2.3 Resource list for the project..........................................................................................13
4. Development of project objectives............................................................................................16
References......................................................................................................................................18

2NETWORK INTRUSION DETECTION SYSTEMS
1. Background of Network Intrusion detection system
After analyzing the current edge of technology and its advanced implementation in the
network systems, it has been defined that security is one of the biggest issues to be highlighted.
In order to avoid unauthenticated information access from the system the network administrators
must adopt accurate prevention measures for protecting the information from different potential
security threats (Beigi Mohammadi et al. 2014). Within the government, individual and business
requirements the computer networks those are involved needs proper security from the business
perspectives. One of the most ordinary and easy way of network protection could be done by
accessing it with proper id and its corresponding password as well.
Network intrusion detection system is also known as the Intrusion detection system or
preventative systems. Malicious activities within the network system and log data including
activities, step stopping and final report developments are monitored and controlled with the help
of intrusion detection system (Bul'ajoul, James and Pannu 2015). Within the network system if
any such malicious activities are highlighted then, intrusion detection system would be able to
send accurate alarm against the malicious activity. In order to save the IP addresses from any
kind of obstructions the network intrusion detection system is very much helpful. In addition to
this it could establish accurate connection between the datagram or information packet to the
network systems. Additionally, there are certain following actions are also associated to it that is
performed by the system are as follows:
Cyclic Redundancy checking could be done for identifying different system level
errors
The TCP level sequencing issues could also be prevented
1. Background of Network Intrusion detection system
After analyzing the current edge of technology and its advanced implementation in the
network systems, it has been defined that security is one of the biggest issues to be highlighted.
In order to avoid unauthenticated information access from the system the network administrators
must adopt accurate prevention measures for protecting the information from different potential
security threats (Beigi Mohammadi et al. 2014). Within the government, individual and business
requirements the computer networks those are involved needs proper security from the business
perspectives. One of the most ordinary and easy way of network protection could be done by
accessing it with proper id and its corresponding password as well.
Network intrusion detection system is also known as the Intrusion detection system or
preventative systems. Malicious activities within the network system and log data including
activities, step stopping and final report developments are monitored and controlled with the help
of intrusion detection system (Bul'ajoul, James and Pannu 2015). Within the network system if
any such malicious activities are highlighted then, intrusion detection system would be able to
send accurate alarm against the malicious activity. In order to save the IP addresses from any
kind of obstructions the network intrusion detection system is very much helpful. In addition to
this it could establish accurate connection between the datagram or information packet to the
network systems. Additionally, there are certain following actions are also associated to it that is
performed by the system are as follows:
Cyclic Redundancy checking could be done for identifying different system level
errors
The TCP level sequencing issues could also be prevented
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK INTRUSION DETECTION SYSTEMS
Unwanted transport and network layer options could be cleaned up
Intrusion Detection System (IDS) those are based upon network system helps to monitor
the activities of the network system. In order to share the project resources, file exchange details
and other electronic communication approaches this particular approach is very much helpful.
This is an approach of event monitoring and control. All possible incidents are the primary focus
of IDS. The information of the incidents those are relevant to the events of the observation are
stored by the IDS system for further analysis. In order to deal with the attacks and unauthorized
access the DS is found to be very much helpful. Through the collection of different information
from the possible security issues are also analyzed with the help of the IDS system. The features
of the IDS are as follows:
The activities of the users and their systems are monitored and controlled
Detail analysis of both the system and its vulnerabilities are possible
The integrity of critical systems and information files access become easier
2. Project methodologies associated to Network Intrusion detection system
Based on the details of the project topic, different project managers follows separate
project methodologies. In order to detect the incidents taking place over the network different
methodologies are applied. Most of the systems use multiple methodologies for detecting the
incidents either integrating the methodologies or by using them separately. It helps to serve
accurate detection power with a broad area. In case of Network Intrusion Detection System
(NIDS), the methodologies those have been followed by the project manager are as follows:
Detection approach, based upon signature
Unwanted transport and network layer options could be cleaned up
Intrusion Detection System (IDS) those are based upon network system helps to monitor
the activities of the network system. In order to share the project resources, file exchange details
and other electronic communication approaches this particular approach is very much helpful.
This is an approach of event monitoring and control. All possible incidents are the primary focus
of IDS. The information of the incidents those are relevant to the events of the observation are
stored by the IDS system for further analysis. In order to deal with the attacks and unauthorized
access the DS is found to be very much helpful. Through the collection of different information
from the possible security issues are also analyzed with the help of the IDS system. The features
of the IDS are as follows:
The activities of the users and their systems are monitored and controlled
Detail analysis of both the system and its vulnerabilities are possible
The integrity of critical systems and information files access become easier
2. Project methodologies associated to Network Intrusion detection system
Based on the details of the project topic, different project managers follows separate
project methodologies. In order to detect the incidents taking place over the network different
methodologies are applied. Most of the systems use multiple methodologies for detecting the
incidents either integrating the methodologies or by using them separately. It helps to serve
accurate detection power with a broad area. In case of Network Intrusion Detection System
(NIDS), the methodologies those have been followed by the project manager are as follows:
Detection approach, based upon signature
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK INTRUSION DETECTION SYSTEMS
In correspond to the mostly occurring threats, signature detection act as a pattern that is
very much helpful from the project developer perspectives. For most of the NIDS project
development this particular methodology is widely used by the project managers. In order to
identify each possible incidents signature based detection approach is very much helpful.
However, the signature detection methodology is helpful for the known threats but for the
unknown threats this particular approach is completely ineffective.
Emails contents like free pictures attached files could be affected directly by the malware
attacks (Thaseen and Kumar 2013). The extensions used for these kinds of attachments can be
changed. If the attachment extension keeps similar then, with the help of the signature based
detection methodology the attachment files could be identified but if the attackers change the
filenames then this methodology will not be able to detect the file.
The main limitation associated to this methodology is it cannot detect the unknown
threats.
Detection based upon anomaly
In order to identify the significance of the deviations, between the considered events and
the observed events, the anomalies based detect methodology is very much helpful. For
representing the normal behavior of the user’s applications and host networks bond this
methodology is very much helpful to be used (Elngar, Mohamed and Ghaleb 2013). For
monitoring the features of different network activities, number of emails, number of users,
number of login failures etc, a profile is needed to be created by using this methodology.
However, again for the known threats application of this particular methodology is very much
helpful. On the other hand for the unknown threats this application is not at all helpful.
In correspond to the mostly occurring threats, signature detection act as a pattern that is
very much helpful from the project developer perspectives. For most of the NIDS project
development this particular methodology is widely used by the project managers. In order to
identify each possible incidents signature based detection approach is very much helpful.
However, the signature detection methodology is helpful for the known threats but for the
unknown threats this particular approach is completely ineffective.
Emails contents like free pictures attached files could be affected directly by the malware
attacks (Thaseen and Kumar 2013). The extensions used for these kinds of attachments can be
changed. If the attachment extension keeps similar then, with the help of the signature based
detection methodology the attachment files could be identified but if the attackers change the
filenames then this methodology will not be able to detect the file.
The main limitation associated to this methodology is it cannot detect the unknown
threats.
Detection based upon anomaly
In order to identify the significance of the deviations, between the considered events and
the observed events, the anomalies based detect methodology is very much helpful. For
representing the normal behavior of the user’s applications and host networks bond this
methodology is very much helpful to be used (Elngar, Mohamed and Ghaleb 2013). For
monitoring the features of different network activities, number of emails, number of users,
number of login failures etc, a profile is needed to be created by using this methodology.
However, again for the known threats application of this particular methodology is very much
helpful. On the other hand for the unknown threats this application is not at all helpful.

5NETWORK INTRUSION DETECTION SYSTEMS
In order to build new profiles this particular methodology is not at all helpful.
Stateful protocol analysis
The Stateful protocol analysis approach is referred to as a process of making comparison
between the preliminarily determined profiles and the already observed events for identifying the
deviations. The way through which whether the Stateful protocols could be used or could might
not be used can be eventually determined (Wenhua and Geng 2014). The current state of the
networks can be analyzed accurately with the help of the tracking and understanding the ability
of protocol.
However, this approach is effective for single response or user request. More than one
attack cannot be detected with the help of this application by focusing on a single request. It
means that for series of requests this application is not helpful.
3. Project plan for Network Intrusion detection system or Gantt chart
3.1 Explanation of the problem
Many problems are associated to the Network Intrusion Detection System (NIDS) which
are needed to be mitigated by the project developers.
3.2 Evaluation
Different types of network security devices those are used in the intrusion detection
system. With the help of these devices the unauthenticated network attacks could be completely
minimized (Wenhua and Geng 2014). In order to increase the level of information security is
necessary for the project managers to install certain network security devices. For this particular
proposed project the devices those have been proposed to adopt are as follows:
In order to build new profiles this particular methodology is not at all helpful.
Stateful protocol analysis
The Stateful protocol analysis approach is referred to as a process of making comparison
between the preliminarily determined profiles and the already observed events for identifying the
deviations. The way through which whether the Stateful protocols could be used or could might
not be used can be eventually determined (Wenhua and Geng 2014). The current state of the
networks can be analyzed accurately with the help of the tracking and understanding the ability
of protocol.
However, this approach is effective for single response or user request. More than one
attack cannot be detected with the help of this application by focusing on a single request. It
means that for series of requests this application is not helpful.
3. Project plan for Network Intrusion detection system or Gantt chart
3.1 Explanation of the problem
Many problems are associated to the Network Intrusion Detection System (NIDS) which
are needed to be mitigated by the project developers.
3.2 Evaluation
Different types of network security devices those are used in the intrusion detection
system. With the help of these devices the unauthenticated network attacks could be completely
minimized (Wenhua and Geng 2014). In order to increase the level of information security is
necessary for the project managers to install certain network security devices. For this particular
proposed project the devices those have been proposed to adopt are as follows:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK INTRUSION DETECTION SYSTEMS
1. Script generation
2. Visual network setup
3. Current attack script setup
4. Tear down
5. Shared disk
6. IDS evaluator
7. IDS result analyzer
8. Report development
Active devices: The surplus level traffics could be completely erased with the help of
these security devices. Examples of these kinds of devices are all content filtering devices.
Preventative devices: In order to identify the potential security problems preventative
designs are very much helpful for scanning purposes (Hassan 2013). The examples of these
kinds of devices include testing devices and vulnerability assessment appliances.
Passive devices: The unwanted traffics could be identified and reported with the help of
the devices.
Unified Threat Management (UTM) system: The operations served by the UTM devices
acts as all-in-one devices and it includes firewall, content filtering and web catching as well.
Certain additional applications are also there which act as network preventatives. By
applying these systems the unwanted intrusions could be completely minimized or diminished
eventually. For regulating and managing the network system the helpful applications are as
follows:
1. Script generation
2. Visual network setup
3. Current attack script setup
4. Tear down
5. Shared disk
6. IDS evaluator
7. IDS result analyzer
8. Report development
Active devices: The surplus level traffics could be completely erased with the help of
these security devices. Examples of these kinds of devices are all content filtering devices.
Preventative devices: In order to identify the potential security problems preventative
designs are very much helpful for scanning purposes (Hassan 2013). The examples of these
kinds of devices include testing devices and vulnerability assessment appliances.
Passive devices: The unwanted traffics could be identified and reported with the help of
the devices.
Unified Threat Management (UTM) system: The operations served by the UTM devices
acts as all-in-one devices and it includes firewall, content filtering and web catching as well.
Certain additional applications are also there which act as network preventatives. By
applying these systems the unwanted intrusions could be completely minimized or diminished
eventually. For regulating and managing the network system the helpful applications are as
follows:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK INTRUSION DETECTION SYSTEMS
Firewall: Firewall is referred to as one of the most widely used prevention mechanism to
avoid unwanted information access from the data server. Firewall helps to develop network
security which manages and regulates the network system considering certain system protocols
(Faisal et al. 2015). It has the power to create a barrier between the trusted internal network and
the internet system. Firewall can be exists as a software in both hardware and other appliances to
run all the applications accurately. The systems where it acts as DHCP server, helps to operate
the network functionalities. Mostly in the private networks the firewalls are use that consists of
both hardware and software based equipments. After analyzing the detail operation of the system
it is determined that, firewall gives remote access facility to the private network by security and
authentication in logins.
Antivirus: Antivirus is referred to as a tool that helps to both detect and remove the
malicious software from the system (Thaseen and Kumar 2013). Basically, for removing the
computer virus from the system different antivirus are used by the system owners. From the
Trojan virus, spyware, keyloggers the system could even be protected eventually. Again certain
more additional products are also there that help to protect system from the URLs, phishing
attacks, DDOS, DOS etc.
3.3 Development of project schedule
In order to initiate and even complete the project successfully within the estimated time
and budget the project manager and the project analysts must develop a project schedule properly
(Al-Jarrah and Arafat 2015). It will help the project team members to define the details of the
project and also would reduce the work load from the members. However, all the scheduled
activities are required to be served by the project manager and project team members accurately
with professional responsibilities. If proper security are approached are undertaken by the project
Firewall: Firewall is referred to as one of the most widely used prevention mechanism to
avoid unwanted information access from the data server. Firewall helps to develop network
security which manages and regulates the network system considering certain system protocols
(Faisal et al. 2015). It has the power to create a barrier between the trusted internal network and
the internet system. Firewall can be exists as a software in both hardware and other appliances to
run all the applications accurately. The systems where it acts as DHCP server, helps to operate
the network functionalities. Mostly in the private networks the firewalls are use that consists of
both hardware and software based equipments. After analyzing the detail operation of the system
it is determined that, firewall gives remote access facility to the private network by security and
authentication in logins.
Antivirus: Antivirus is referred to as a tool that helps to both detect and remove the
malicious software from the system (Thaseen and Kumar 2013). Basically, for removing the
computer virus from the system different antivirus are used by the system owners. From the
Trojan virus, spyware, keyloggers the system could even be protected eventually. Again certain
more additional products are also there that help to protect system from the URLs, phishing
attacks, DDOS, DOS etc.
3.3 Development of project schedule
In order to initiate and even complete the project successfully within the estimated time
and budget the project manager and the project analysts must develop a project schedule properly
(Al-Jarrah and Arafat 2015). It will help the project team members to define the details of the
project and also would reduce the work load from the members. However, all the scheduled
activities are required to be served by the project manager and project team members accurately
with professional responsibilities. If proper security are approached are undertaken by the project
8NETWORK INTRUSION DETECTION SYSTEMS
manager then, within the estimated time limit the project would have been completed. The
schedules developed for the implementation of the intrusion detection systems in the network is
as follows:
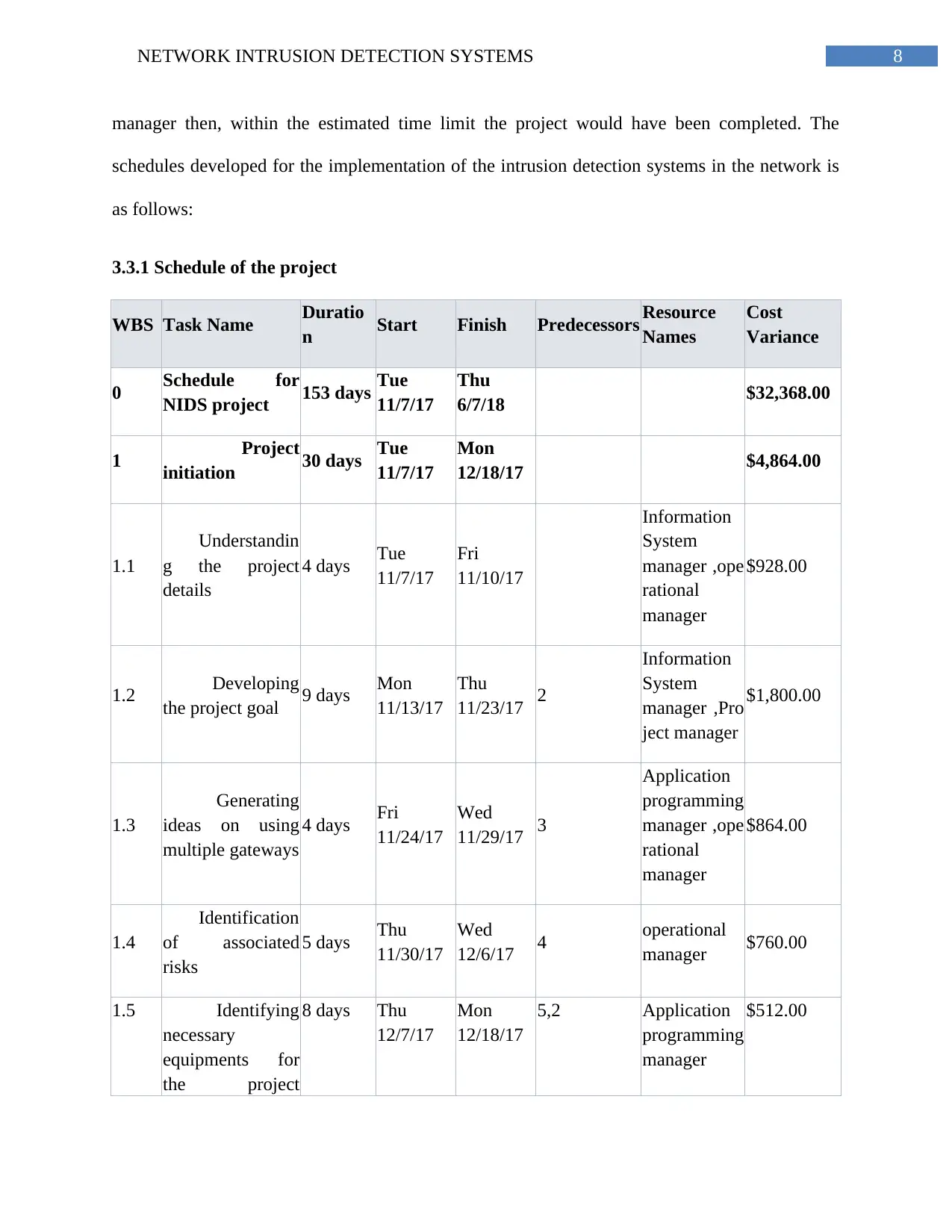
3.3.1 Schedule of the project
WBS Task Name Duratio
n Start Finish Predecessors Resource
Names
Cost
Variance
0 Schedule for
NIDS project 153 days Tue
11/7/17
Thu
6/7/18 $32,368.00
1 Project
initiation 30 days Tue
11/7/17
Mon
12/18/17 $4,864.00
1.1
Understandin
g the project
details
4 days Tue
11/7/17
Fri
11/10/17
Information
System
manager ,ope
rational
manager
$928.00
1.2 Developing
the project goal 9 days Mon
11/13/17
Thu
11/23/17 2
Information
System
manager ,Pro
ject manager
$1,800.00
1.3
Generating
ideas on using
multiple gateways
4 days Fri
11/24/17
Wed
11/29/17 3
Application
programming
manager ,ope
rational
manager
$864.00
1.4
Identification
of associated
risks
5 days Thu
11/30/17
Wed
12/6/17 4 operational
manager $760.00
1.5 Identifying
necessary
equipments for
the project
8 days Thu
12/7/17
Mon
12/18/17
5,2 Application
programming
manager
$512.00
manager then, within the estimated time limit the project would have been completed. The
schedules developed for the implementation of the intrusion detection systems in the network is
as follows:
3.3.1 Schedule of the project
WBS Task Name Duratio
n Start Finish Predecessors Resource
Names
Cost
Variance
0 Schedule for
NIDS project 153 days Tue
11/7/17
Thu
6/7/18 $32,368.00
1 Project
initiation 30 days Tue
11/7/17
Mon
12/18/17 $4,864.00
1.1
Understandin
g the project
details
4 days Tue
11/7/17
Fri
11/10/17
Information
System
manager ,ope
rational
manager
$928.00
1.2 Developing
the project goal 9 days Mon
11/13/17
Thu
11/23/17 2
Information
System
manager ,Pro
ject manager
$1,800.00
1.3
Generating
ideas on using
multiple gateways
4 days Fri
11/24/17
Wed
11/29/17 3
Application
programming
manager ,ope
rational
manager
$864.00
1.4
Identification
of associated
risks
5 days Thu
11/30/17
Wed
12/6/17 4 operational
manager $760.00
1.5 Identifying
necessary
equipments for
the project
8 days Thu
12/7/17
Mon
12/18/17
5,2 Application
programming
manager
$512.00
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
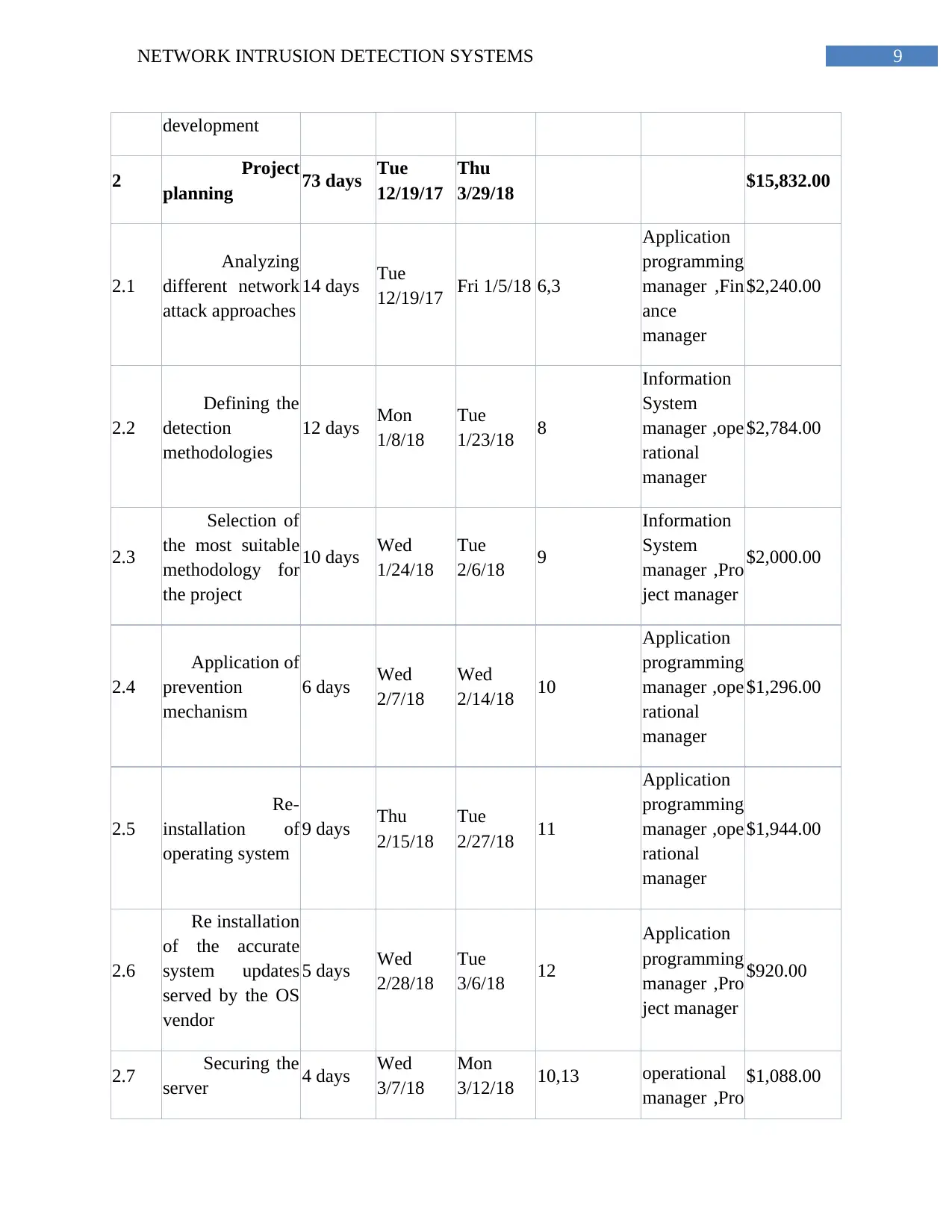
9NETWORK INTRUSION DETECTION SYSTEMS
development
2 Project
planning 73 days Tue
12/19/17
Thu
3/29/18 $15,832.00
2.1
Analyzing
different network
attack approaches
14 days Tue
12/19/17 Fri 1/5/18 6,3
Application
programming
manager ,Fin
ance
manager
$2,240.00
2.2
Defining the
detection
methodologies
12 days Mon
1/8/18
Tue
1/23/18 8
Information
System
manager ,ope
rational
manager
$2,784.00
2.3
Selection of
the most suitable
methodology for
the project
10 days Wed
1/24/18
Tue
2/6/18 9
Information
System
manager ,Pro
ject manager
$2,000.00
2.4
Application of
prevention
mechanism
6 days Wed
2/7/18
Wed
2/14/18 10
Application
programming
manager ,ope
rational
manager
$1,296.00
2.5
Re-
installation of
operating system
9 days Thu
2/15/18
Tue
2/27/18 11
Application
programming
manager ,ope
rational
manager
$1,944.00
2.6
Re installation
of the accurate
system updates
served by the OS
vendor
5 days Wed
2/28/18
Tue
3/6/18 12
Application
programming
manager ,Pro
ject manager
$920.00
2.7 Securing the
server 4 days Wed
3/7/18
Mon
3/12/18 10,13 operational
manager ,Pro
$1,088.00
development
2 Project
planning 73 days Tue
12/19/17
Thu
3/29/18 $15,832.00
2.1
Analyzing
different network
attack approaches
14 days Tue
12/19/17 Fri 1/5/18 6,3
Application
programming
manager ,Fin
ance
manager
$2,240.00
2.2
Defining the
detection
methodologies
12 days Mon
1/8/18
Tue
1/23/18 8
Information
System
manager ,ope
rational
manager
$2,784.00
2.3
Selection of
the most suitable
methodology for
the project
10 days Wed
1/24/18
Tue
2/6/18 9
Information
System
manager ,Pro
ject manager
$2,000.00
2.4
Application of
prevention
mechanism
6 days Wed
2/7/18
Wed
2/14/18 10
Application
programming
manager ,ope
rational
manager
$1,296.00
2.5
Re-
installation of
operating system
9 days Thu
2/15/18
Tue
2/27/18 11
Application
programming
manager ,ope
rational
manager
$1,944.00
2.6
Re installation
of the accurate
system updates
served by the OS
vendor
5 days Wed
2/28/18
Tue
3/6/18 12
Application
programming
manager ,Pro
ject manager
$920.00
2.7 Securing the
server 4 days Wed
3/7/18
Mon
3/12/18 10,13 operational
manager ,Pro
$1,088.00
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
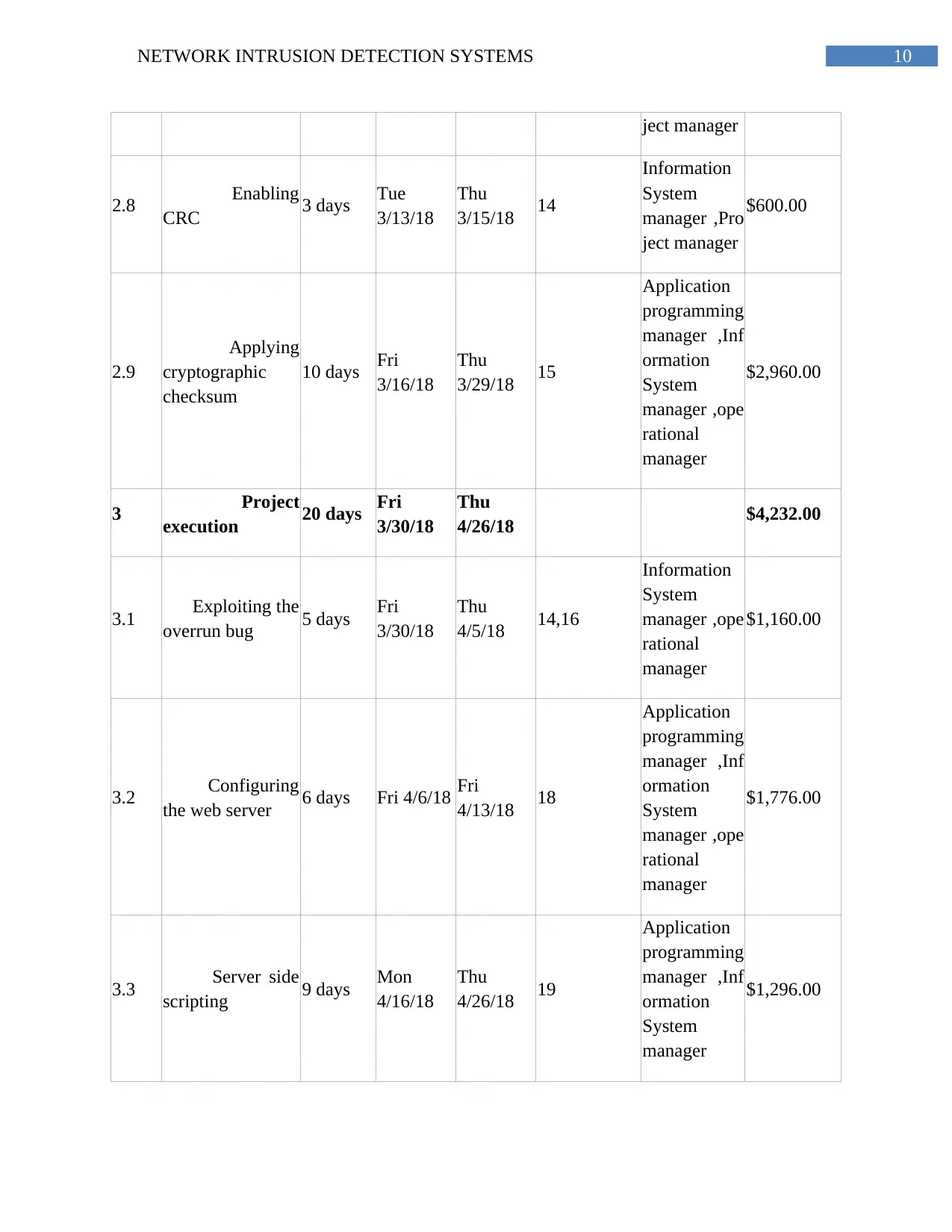
10NETWORK INTRUSION DETECTION SYSTEMS
ject manager
2.8 Enabling
CRC 3 days Tue
3/13/18
Thu
3/15/18 14
Information
System
manager ,Pro
ject manager
$600.00
2.9
Applying
cryptographic
checksum
10 days Fri
3/16/18
Thu
3/29/18 15
Application
programming
manager ,Inf
ormation
System
manager ,ope
rational
manager
$2,960.00
3 Project
execution 20 days Fri
3/30/18
Thu
4/26/18 $4,232.00
3.1 Exploiting the
overrun bug 5 days Fri
3/30/18
Thu
4/5/18 14,16
Information
System
manager ,ope
rational
manager
$1,160.00
3.2 Configuring
the web server 6 days Fri 4/6/18 Fri
4/13/18 18
Application
programming
manager ,Inf
ormation
System
manager ,ope
rational
manager
$1,776.00
3.3 Server side
scripting 9 days Mon
4/16/18
Thu
4/26/18 19
Application
programming
manager ,Inf
ormation
System
manager
$1,296.00
ject manager
2.8 Enabling
CRC 3 days Tue
3/13/18
Thu
3/15/18 14
Information
System
manager ,Pro
ject manager
$600.00
2.9
Applying
cryptographic
checksum
10 days Fri
3/16/18
Thu
3/29/18 15
Application
programming
manager ,Inf
ormation
System
manager ,ope
rational
manager
$2,960.00
3 Project
execution 20 days Fri
3/30/18
Thu
4/26/18 $4,232.00
3.1 Exploiting the
overrun bug 5 days Fri
3/30/18
Thu
4/5/18 14,16
Information
System
manager ,ope
rational
manager
$1,160.00
3.2 Configuring
the web server 6 days Fri 4/6/18 Fri
4/13/18 18
Application
programming
manager ,Inf
ormation
System
manager ,ope
rational
manager
$1,776.00
3.3 Server side
scripting 9 days Mon
4/16/18
Thu
4/26/18 19
Application
programming
manager ,Inf
ormation
System
manager
$1,296.00
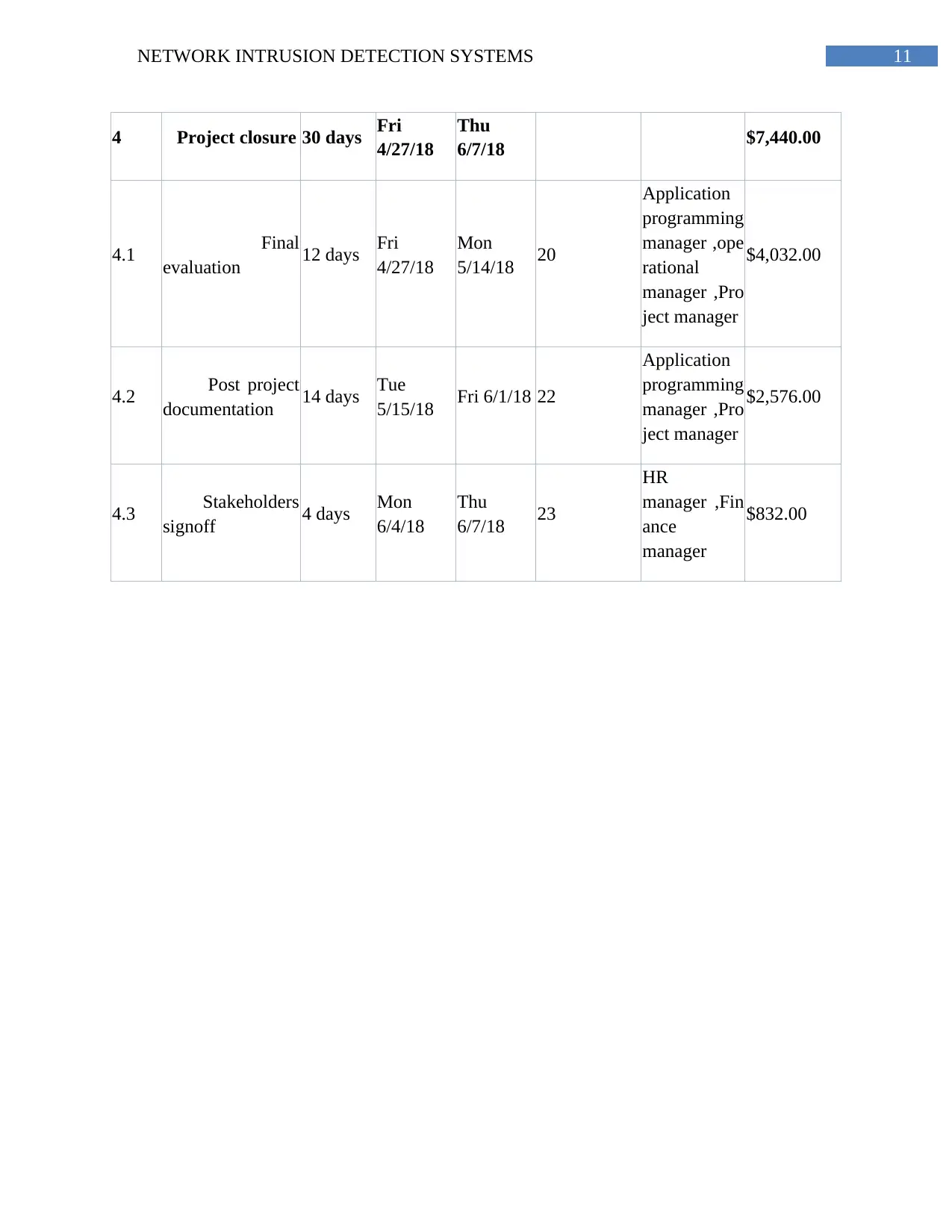
11NETWORK INTRUSION DETECTION SYSTEMS
4 Project closure 30 days Fri
4/27/18
Thu
6/7/18 $7,440.00
4.1 Final
evaluation 12 days Fri
4/27/18
Mon
5/14/18 20
Application
programming
manager ,ope
rational
manager ,Pro
ject manager
$4,032.00
4.2 Post project
documentation 14 days Tue
5/15/18 Fri 6/1/18 22
Application
programming
manager ,Pro
ject manager
$2,576.00
4.3 Stakeholders
signoff 4 days Mon
6/4/18
Thu
6/7/18 23
HR
manager ,Fin
ance
manager
$832.00
4 Project closure 30 days Fri
4/27/18
Thu
6/7/18 $7,440.00
4.1 Final
evaluation 12 days Fri
4/27/18
Mon
5/14/18 20
Application
programming
manager ,ope
rational
manager ,Pro
ject manager
$4,032.00
4.2 Post project
documentation 14 days Tue
5/15/18 Fri 6/1/18 22
Application
programming
manager ,Pro
ject manager
$2,576.00
4.3 Stakeholders
signoff 4 days Mon
6/4/18
Thu
6/7/18 23
HR
manager ,Fin
ance
manager
$832.00
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




