Fourth International Conference on Consumer Electronics Berlin
VerifiedAdded on 2022/09/18
|19
|4504
|19
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: BLUETOOTH AND NETWORK
BLUETOOTH AND NETWORK
Name of the Student:
Name of the University:
Author’s Note:
BLUETOOTH AND NETWORK
Name of the Student:
Name of the University:
Author’s Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1BLUETOOTH AND NETWORK
Table of Contents
Introduction:-...................................................................................................................................2
Discussion:-.....................................................................................................................................2
Definition and History:-...............................................................................................................2
Mechanism:-................................................................................................................................3
Operation Mode:-.........................................................................................................................5
Protocol Architecture:-................................................................................................................7
Advantages:-................................................................................................................................8
Disadvantage:-...........................................................................................................................10
Impact:-......................................................................................................................................12
Conclusion:-...................................................................................................................................14
References:-...................................................................................................................................16
Table of Contents
Introduction:-...................................................................................................................................2
Discussion:-.....................................................................................................................................2
Definition and History:-...............................................................................................................2
Mechanism:-................................................................................................................................3
Operation Mode:-.........................................................................................................................5
Protocol Architecture:-................................................................................................................7
Advantages:-................................................................................................................................8
Disadvantage:-...........................................................................................................................10
Impact:-......................................................................................................................................12
Conclusion:-...................................................................................................................................14
References:-...................................................................................................................................16

2BLUETOOTH AND NETWORK
Introduction:-
Knowledge is measured to be the stand to uprise and reach the anticipated gradation of expansion of
civilization. Human has been exasperating to simplify his lifespan over discoveries and invention.
Telecommunication denotes, when electronic, maintained a very significant role in increasing information
which enabled experts to apply the consequence of other investigates and that prime to massive
development in several fields of knowledge and thus more mechanical device. Bluetooth is the term of a
modern knowledge that is currently becoming extensive on a moneymaking basis. Bluetooth was
launched in 1994 as a wireless supernumerary for RS-232 cables (Darroudi & Gomez, 2017). It
promises to modify the techniques meaningfully in people use machines. It functions in the unrestricted,
manufacturing, technical and medical band at 2.34 GHz to 2.495 GHz. Maximum apparatus that can be
linked at a similar time is 7. It delivers information rates up to 1.2 Mbps or 3.02 Mbps according to the
version. In this report are describing the first overview of the Bluetooth device and its network
architecture.
Discussion:-
Definition and History:-
This wireless technology is transmitting stable and mobile electronic apparatus information over short
spaces. The functioning range is based on the class of device. A diversity of digital apparatus uses
Bluetooth, counting mobile and peripheral devices, MP3 players, and individual computers. The term was
initial applied as a code language, but it fixed as time delivered. This word is originated from Herald
Bluetooth who is the 10th Danish Sovereign in Scandinavian Europe. The originators of this technology
establish the name suitable as this technology is capable of tying innumerable businesses like computing,
cellphone and motorized markets. This device connects with a diversity of electronic apparatus and makes
private networks functioning within the unrestricted 2.34 GHz band. By this technology, one is capable of
Introduction:-
Knowledge is measured to be the stand to uprise and reach the anticipated gradation of expansion of
civilization. Human has been exasperating to simplify his lifespan over discoveries and invention.
Telecommunication denotes, when electronic, maintained a very significant role in increasing information
which enabled experts to apply the consequence of other investigates and that prime to massive
development in several fields of knowledge and thus more mechanical device. Bluetooth is the term of a
modern knowledge that is currently becoming extensive on a moneymaking basis. Bluetooth was
launched in 1994 as a wireless supernumerary for RS-232 cables (Darroudi & Gomez, 2017). It
promises to modify the techniques meaningfully in people use machines. It functions in the unrestricted,
manufacturing, technical and medical band at 2.34 GHz to 2.495 GHz. Maximum apparatus that can be
linked at a similar time is 7. It delivers information rates up to 1.2 Mbps or 3.02 Mbps according to the
version. In this report are describing the first overview of the Bluetooth device and its network
architecture.
Discussion:-
Definition and History:-
This wireless technology is transmitting stable and mobile electronic apparatus information over short
spaces. The functioning range is based on the class of device. A diversity of digital apparatus uses
Bluetooth, counting mobile and peripheral devices, MP3 players, and individual computers. The term was
initial applied as a code language, but it fixed as time delivered. This word is originated from Herald
Bluetooth who is the 10th Danish Sovereign in Scandinavian Europe. The originators of this technology
establish the name suitable as this technology is capable of tying innumerable businesses like computing,
cellphone and motorized markets. This device connects with a diversity of electronic apparatus and makes
private networks functioning within the unrestricted 2.34 GHz band. By this technology, one is capable of
3BLUETOOTH AND NETWORK
combining and simplifying numerous forms of wireless network into a safe, distinct, inexpensive, ,
worldwide obtainable radiofrequency (Cho et al., 2015). Its foundation is established on a skill named
FHS spectrum, first defined in a 1942 patent by artist composer George Antheil and Hedy Lamarr who
wanted to make a method to avoid torpedoes directed by radio to be blocked.
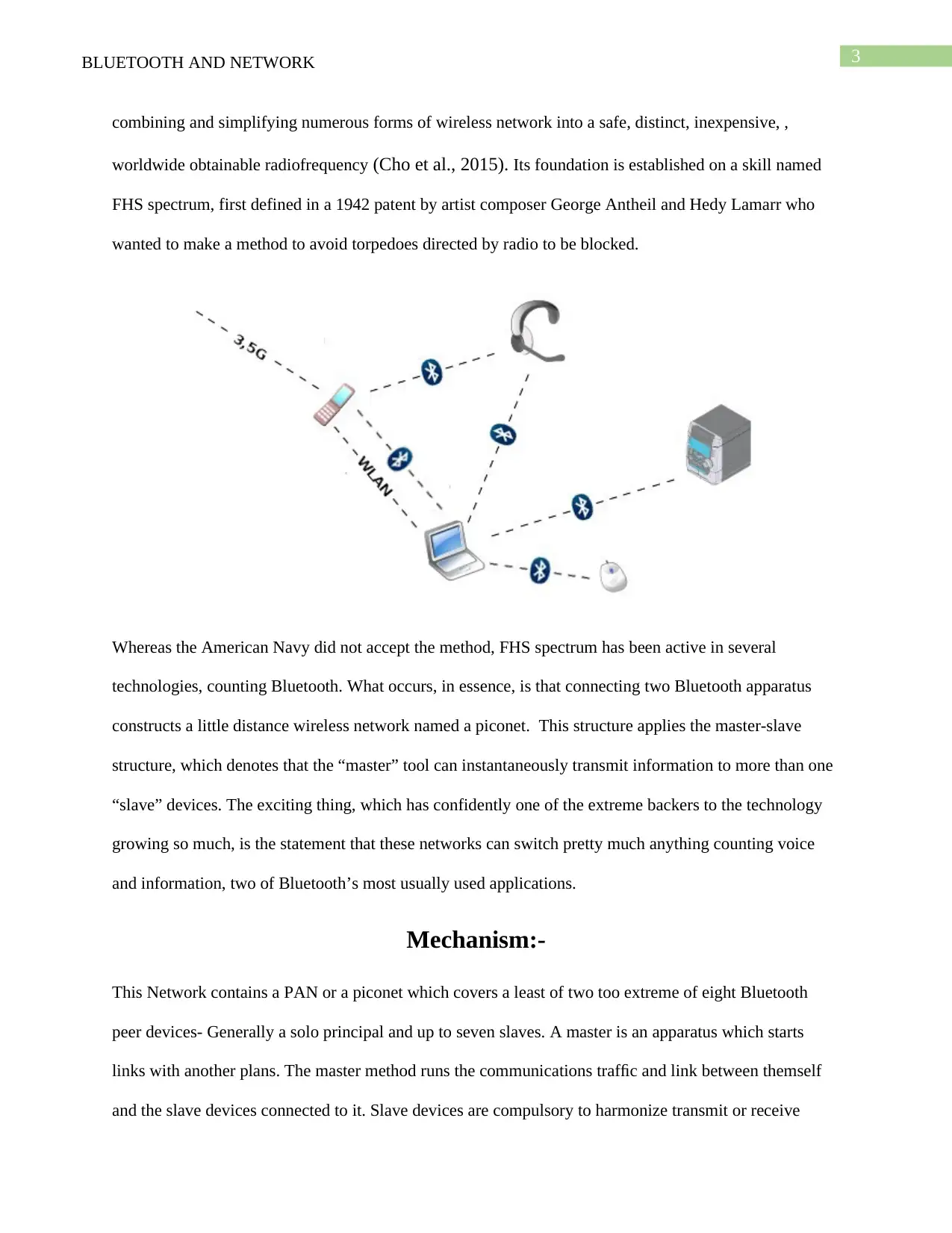
Whereas the American Navy did not accept the method, FHS spectrum has been active in several
technologies, counting Bluetooth. What occurs, in essence, is that connecting two Bluetooth apparatus
constructs a little distance wireless network named a piconet. This structure applies the master-slave
structure, which denotes that the “master” tool can instantaneously transmit information to more than one
“slave” devices. The exciting thing, which has confidently one of the extreme backers to the technology
growing so much, is the statement that these networks can switch pretty much anything counting voice
and information, two of Bluetooth’s most usually used applications.
Mechanism:-
This Network contains a PAN or a piconet which covers a least of two too extreme of eight Bluetooth
peer devices- Generally a solo principal and up to seven slaves. A master is an apparatus which starts
links with another plans. The master method runs the communications traffic and link between themself
and the slave devices connected to it. Slave devices are compulsory to harmonize transmit or receive
combining and simplifying numerous forms of wireless network into a safe, distinct, inexpensive, ,
worldwide obtainable radiofrequency (Cho et al., 2015). Its foundation is established on a skill named
FHS spectrum, first defined in a 1942 patent by artist composer George Antheil and Hedy Lamarr who
wanted to make a method to avoid torpedoes directed by radio to be blocked.
Whereas the American Navy did not accept the method, FHS spectrum has been active in several
technologies, counting Bluetooth. What occurs, in essence, is that connecting two Bluetooth apparatus
constructs a little distance wireless network named a piconet. This structure applies the master-slave
structure, which denotes that the “master” tool can instantaneously transmit information to more than one
“slave” devices. The exciting thing, which has confidently one of the extreme backers to the technology
growing so much, is the statement that these networks can switch pretty much anything counting voice
and information, two of Bluetooth’s most usually used applications.
Mechanism:-
This Network contains a PAN or a piconet which covers a least of two too extreme of eight Bluetooth
peer devices- Generally a solo principal and up to seven slaves. A master is an apparatus which starts
links with another plans. The master method runs the communications traffic and link between themself
and the slave devices connected to it. Slave devices are compulsory to harmonize transmit or receive
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4BLUETOOTH AND NETWORK
timing with their masters (Nair et al., 2015). Also, communications by slave devices are directed by the
master device. Specifically, a slave may only instigate its broadcasts in a time slot directly following the
time slot in which the master positioned it, or in a time slot openly kept for application by the slave
device. The frequency bounding arrangement is described by the device locate of the master device.
These first directs a radio signal requesting a reply from the specific slave devices within the addresses
range. The slaves reply and coordinate their step frequency as well as a clock with that of the master
tools.
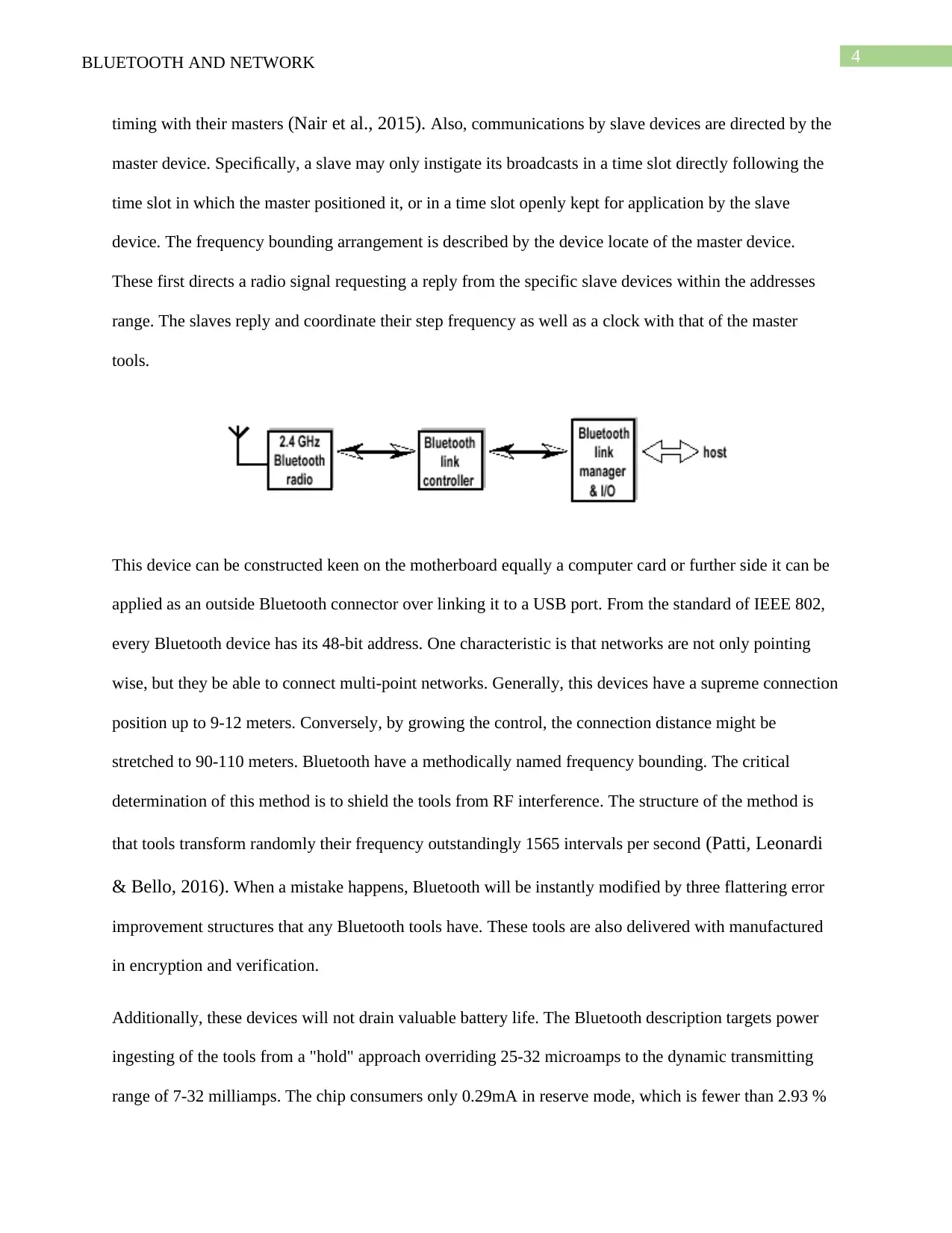
This device can be constructed keen on the motherboard equally a computer card or further side it can be
applied as an outside Bluetooth connector over linking it to a USB port. From the standard of IEEE 802,
every Bluetooth device has its 48-bit address. One characteristic is that networks are not only pointing
wise, but they be able to connect multi-point networks. Generally, this devices have a supreme connection
position up to 9-12 meters. Conversely, by growing the control, the connection distance might be
stretched to 90-110 meters. Bluetooth have a methodically named frequency bounding. The critical
determination of this method is to shield the tools from RF interference. The structure of the method is
that tools transform randomly their frequency outstandingly 1565 intervals per second (Patti, Leonardi
& Bello, 2016). When a mistake happens, Bluetooth will be instantly modified by three flattering error
improvement structures that any Bluetooth tools have. These tools are also delivered with manufactured
in encryption and verification.
Additionally, these devices will not drain valuable battery life. The Bluetooth description targets power
ingesting of the tools from a "hold" approach overriding 25-32 microamps to the dynamic transmitting
range of 7-32 milliamps. The chip consumers only 0.29mA in reserve mode, which is fewer than 2.93 %
timing with their masters (Nair et al., 2015). Also, communications by slave devices are directed by the
master device. Specifically, a slave may only instigate its broadcasts in a time slot directly following the
time slot in which the master positioned it, or in a time slot openly kept for application by the slave
device. The frequency bounding arrangement is described by the device locate of the master device.
These first directs a radio signal requesting a reply from the specific slave devices within the addresses
range. The slaves reply and coordinate their step frequency as well as a clock with that of the master
tools.
This device can be constructed keen on the motherboard equally a computer card or further side it can be
applied as an outside Bluetooth connector over linking it to a USB port. From the standard of IEEE 802,
every Bluetooth device has its 48-bit address. One characteristic is that networks are not only pointing
wise, but they be able to connect multi-point networks. Generally, this devices have a supreme connection
position up to 9-12 meters. Conversely, by growing the control, the connection distance might be
stretched to 90-110 meters. Bluetooth have a methodically named frequency bounding. The critical
determination of this method is to shield the tools from RF interference. The structure of the method is
that tools transform randomly their frequency outstandingly 1565 intervals per second (Patti, Leonardi
& Bello, 2016). When a mistake happens, Bluetooth will be instantly modified by three flattering error
improvement structures that any Bluetooth tools have. These tools are also delivered with manufactured
in encryption and verification.
Additionally, these devices will not drain valuable battery life. The Bluetooth description targets power
ingesting of the tools from a "hold" approach overriding 25-32 microamps to the dynamic transmitting
range of 7-32 milliamps. The chip consumers only 0.29mA in reserve mode, which is fewer than 2.93 %

5BLUETOOTH AND NETWORK
of the power applied by a typical mobile phone. The chips also take exceptional power-saving structures,
as they will spontaneously change to a lesser power mode as soon as traffic volume reduces or stops.
The protocol of Bluetooth baseband is a grouping of packet switching and circuit. Periods can be
earmarked for synchronous packets. Every packet is diffused in a different hop frequency. A packet
technically shields a particular slot but can be stretched to cover up to more than four slots (Jeon,
Dwijaksara & Jeong , 2016). Bluetooth can sustenance an asynchronous information channel, up to two
to four concurrent synchronous voice stations, or a channel, which instantaneously backs asynchronous
information and synchronous voice. It is therefore probable to transmission the date asynchronously
whereas talking synchronously at a similar time (Priyanka & Nagajayanthi, 2014). Every voice
channel backs 62-65 kb/s synchronous link. The asynchronous network can upkeep an irregular link of
outstandingly 715-725 kb/s in each way while authorizing 58.16 kb/s in return way, or a 430.46 kb/s
symmetric connection.
Operation Mode:-
A characteristic of this knowledge is that, once the tools come in the distance of another, they will rapidly
form systems between others. Another characteristics are that many tools can be linked together through
the ad hoc form. As the system helps different networks point as well as pointwise links, these tools can
be linked to an extreme of other seven points, a mark to multi-point construction. Each piconet has
dissimilar frequency bounding arrangement, and hereafter a quantity of piconets might be formed and
of the power applied by a typical mobile phone. The chips also take exceptional power-saving structures,
as they will spontaneously change to a lesser power mode as soon as traffic volume reduces or stops.
The protocol of Bluetooth baseband is a grouping of packet switching and circuit. Periods can be
earmarked for synchronous packets. Every packet is diffused in a different hop frequency. A packet
technically shields a particular slot but can be stretched to cover up to more than four slots (Jeon,
Dwijaksara & Jeong , 2016). Bluetooth can sustenance an asynchronous information channel, up to two
to four concurrent synchronous voice stations, or a channel, which instantaneously backs asynchronous
information and synchronous voice. It is therefore probable to transmission the date asynchronously
whereas talking synchronously at a similar time (Priyanka & Nagajayanthi, 2014). Every voice
channel backs 62-65 kb/s synchronous link. The asynchronous network can upkeep an irregular link of
outstandingly 715-725 kb/s in each way while authorizing 58.16 kb/s in return way, or a 430.46 kb/s
symmetric connection.
Operation Mode:-
A characteristic of this knowledge is that, once the tools come in the distance of another, they will rapidly
form systems between others. Another characteristics are that many tools can be linked together through
the ad hoc form. As the system helps different networks point as well as pointwise links, these tools can
be linked to an extreme of other seven points, a mark to multi-point construction. Each piconet has
dissimilar frequency bounding arrangement, and hereafter a quantity of piconets might be formed and

6BLUETOOTH AND NETWORK
connected. All operators that are distributing one piconet are corresponding piconet bounding
arrangement (Jung et al., 2017). A device applies different hopping arrangement when it is linked to
more than two piconets where it starts with two associated devices. As an example, a phone and laptop,
and might grow to seven to eight connected devices. Every Bluetooth devices have similar applications.
Though, there are two categories of ties in a piconet which are major and slave units.
A master unit is an element which coordinates other tools by its hopping sequence and clock, where the
other tools in the piconet are termed slave units. Each Bluetooth tools are peer units and have
undistinguishable implementations. Nonetheless, when creating a piconet, a single unit will perform as a
master and slave for the period of the piconet construction. In this case, there is a master entity whose
clock and bounding arrangement are applied to harmonize every piconet tools in every piconet devices
that are not the master-slave units. Apparatus coordinated to a piconet can arrive power-saving modes
named sniff and grip mode, in which device action is dropped. Another parked units take an 8-bit address.
Therefore there can be an extreme of 256 parked tools. The Bluetooth provisions have left numerous
design concerns open to execution when it originates to its application as a networking knowledge
(Varsamou & Antonakopoulos, 2014). The aim is to permit designers tractability to provide to the
separate network necessities. Nonetheless, for adjusting the technology near significant scale disposition
in ad-hoc networks, it is commanding that there be a methodical system for achieving specific of the most
common design goals.
connected. All operators that are distributing one piconet are corresponding piconet bounding
arrangement (Jung et al., 2017). A device applies different hopping arrangement when it is linked to
more than two piconets where it starts with two associated devices. As an example, a phone and laptop,
and might grow to seven to eight connected devices. Every Bluetooth devices have similar applications.
Though, there are two categories of ties in a piconet which are major and slave units.
A master unit is an element which coordinates other tools by its hopping sequence and clock, where the
other tools in the piconet are termed slave units. Each Bluetooth tools are peer units and have
undistinguishable implementations. Nonetheless, when creating a piconet, a single unit will perform as a
master and slave for the period of the piconet construction. In this case, there is a master entity whose
clock and bounding arrangement are applied to harmonize every piconet tools in every piconet devices
that are not the master-slave units. Apparatus coordinated to a piconet can arrive power-saving modes
named sniff and grip mode, in which device action is dropped. Another parked units take an 8-bit address.
Therefore there can be an extreme of 256 parked tools. The Bluetooth provisions have left numerous
design concerns open to execution when it originates to its application as a networking knowledge
(Varsamou & Antonakopoulos, 2014). The aim is to permit designers tractability to provide to the
separate network necessities. Nonetheless, for adjusting the technology near significant scale disposition
in ad-hoc networks, it is commanding that there be a methodical system for achieving specific of the most
common design goals.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BLUETOOTH AND NETWORK
Protocol Architecture:-
Radio:-
It implements modulation or demodulation of the information into radio frequency signals. It describes
the physical features of Bluetooth transceiver. This layer describes two categories of physical link such as
connection-oriented and connection-less.
Baseband Link:
It implements the connection formation within a piconet.
Link Manager Protocol:
It implements the running of the previously established links. LMP also contains verification and
encryption procedures.
HCI:
The HCI monitors the link between the module and the host. It applies more than a few HCI command
packets like as the data packets and data packets.
Protocol Architecture:-
Radio:-
It implements modulation or demodulation of the information into radio frequency signals. It describes
the physical features of Bluetooth transceiver. This layer describes two categories of physical link such as
connection-oriented and connection-less.
Baseband Link:
It implements the connection formation within a piconet.
Link Manager Protocol:
It implements the running of the previously established links. LMP also contains verification and
encryption procedures.
HCI:
The HCI monitors the link between the module and the host. It applies more than a few HCI command
packets like as the data packets and data packets.

8BLUETOOTH AND NETWORK
L2CAP:
The L2CAP layer transforms the information acquired from higher layers into packets of different
dimensions. It is also identified as the core part of the Bluetooth stack. It permits the statement between
lower and upper layers of the Bluetooth protocol stack (Yu & Yu, 2014). It correspondences the
information packets established from better layers into the method predictable by lower layers. It also
executes the subdivision and multiplexing.
SDP layer:
It permits to determine the facilities accessible on another Bluetooth assisted device.
RF communication:
It is the abbreviation for Radio Frontend Module. It delivers a serial interface with OBEX and WAP.
OBEX:
Object Exchange is a communication practice to converse objects between different devices.
WAP:
Wireless Access Protocol is applied for network and connection access.
TCS:
Telephony Control Protocol also provides telephony facility.
Application layer:
It allows the operator to interrelate with the application.
Advantages:-
It is a piece of wireless connection machinery that permits a user to link some devices in their home. Like
a wireless router, the operator can apply this device to exchange records and activate microchip
L2CAP:
The L2CAP layer transforms the information acquired from higher layers into packets of different
dimensions. It is also identified as the core part of the Bluetooth stack. It permits the statement between
lower and upper layers of the Bluetooth protocol stack (Yu & Yu, 2014). It correspondences the
information packets established from better layers into the method predictable by lower layers. It also
executes the subdivision and multiplexing.
SDP layer:
It permits to determine the facilities accessible on another Bluetooth assisted device.
RF communication:
It is the abbreviation for Radio Frontend Module. It delivers a serial interface with OBEX and WAP.
OBEX:
Object Exchange is a communication practice to converse objects between different devices.
WAP:
Wireless Access Protocol is applied for network and connection access.
TCS:
Telephony Control Protocol also provides telephony facility.
Application layer:
It allows the operator to interrelate with the application.
Advantages:-
It is a piece of wireless connection machinery that permits a user to link some devices in their home. Like
a wireless router, the operator can apply this device to exchange records and activate microchip

9BLUETOOTH AND NETWORK
technology. Wireless cellphones, even gaming supports as well as headset can all apply Bluetooth in one
track or another. Whereas Bluetooth has definite boundaries, like as a smaller distance and lesser
bandwidth than wireless internet connection, it can create the linkage between tools in user household
more dependable than another wireless replacements.
Simple Format:-
Fixing up a device link between two apparatus is easy and quick. The particular boundary for performing
so differs trusting on user devices but linking two tools that need to make one discoverable whereas the
other one images (Afonso, Maio & Simoes, 2016). When the scanning tool discoveries the
discoverable one, they start the link and put the password as fixed by their user's guide. The user should
not take to recombine the apparatus once they have been harmonizing.
Compatibility:-
The device receiver is well-matched with another tool that maintains Bluetooth, irrespective of brand,
prototype or strategy. The operator be able to apply it with their mobile phone or duos it with their
gaming console or processor for stress-free online chatting. The user keyboard can effort with their
processer PlayStation. The solitary concern they are likely to meet is if the tool in query can only pair
with an inadequate quantity of tools.
Safety:-
This device has intrinsic safety in two techniques. The principal is that it is not continuously propagating,
different a wireless link. When the user wants to join more than one devices through Bluetooth then used
to fix them. This reflectiveness is only essential until the tools have been harmonizing. Once
harmonizing, the user can turn off perceptibility and save the tools locked to different networks. The
additional level of safety is that in most circumstances, the user will want to approve the connection
applying code or PIN to link different devices. For example, if a user has their computer's Bluetooth fix to
discoverable, an outsider still cannot join to their computer till the user approve the link physically
technology. Wireless cellphones, even gaming supports as well as headset can all apply Bluetooth in one
track or another. Whereas Bluetooth has definite boundaries, like as a smaller distance and lesser
bandwidth than wireless internet connection, it can create the linkage between tools in user household
more dependable than another wireless replacements.
Simple Format:-
Fixing up a device link between two apparatus is easy and quick. The particular boundary for performing
so differs trusting on user devices but linking two tools that need to make one discoverable whereas the
other one images (Afonso, Maio & Simoes, 2016). When the scanning tool discoveries the
discoverable one, they start the link and put the password as fixed by their user's guide. The user should
not take to recombine the apparatus once they have been harmonizing.
Compatibility:-
The device receiver is well-matched with another tool that maintains Bluetooth, irrespective of brand,
prototype or strategy. The operator be able to apply it with their mobile phone or duos it with their
gaming console or processor for stress-free online chatting. The user keyboard can effort with their
processer PlayStation. The solitary concern they are likely to meet is if the tool in query can only pair
with an inadequate quantity of tools.
Safety:-
This device has intrinsic safety in two techniques. The principal is that it is not continuously propagating,
different a wireless link. When the user wants to join more than one devices through Bluetooth then used
to fix them. This reflectiveness is only essential until the tools have been harmonizing. Once
harmonizing, the user can turn off perceptibility and save the tools locked to different networks. The
additional level of safety is that in most circumstances, the user will want to approve the connection
applying code or PIN to link different devices. For example, if a user has their computer's Bluetooth fix to
discoverable, an outsider still cannot join to their computer till the user approve the link physically
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10BLUETOOTH AND NETWORK
(Leonardi, Patti & Bello, 2018). In conclusion, the lesser devices range denotes that operators outside
their home are questionable even to observe their Bluetooth device.
Less Hardware:-
Perceptibly the deficiency of connecting wires is an advantage of Bluetooth, but it is even compact than
Wireless connection. To make a wireless structure in user household applying Wi-Fi, they will want a
router to arrange the access point. All statement between two tools on a wireless structure must go over
user wireless router. With this, the tools express openly to one other. As long as their devices usually have
Bluetooth empowered, the user does not want any supplementary hardware to join them. If they do want
additional hardware, it is in the method a little USB that enhances Bluetooth link to a user device.
Disadvantage:-
The suitability of these technologies cannot be repudiated, but neither can the technique they have
harmfully obstructed everyday existing. Specific of the possessions can be distributed with if limitations
are fixed. Here this report will describe a specific harmful impression of device.
Destruction of Confidentiality:
The processors and phone generally cover secretive stuff like family photographs, bank account figures,
and PINs (Palumbo et al., 2015). The hacker directs a user a transcript when established, and it will be
released as a standard letter wherever truly it has a constructed-in network attacking software. When the
operator opens the transcript, the cyber attacker will be capable of regulating the operator’s device.
Disruption:
(Leonardi, Patti & Bello, 2018). In conclusion, the lesser devices range denotes that operators outside
their home are questionable even to observe their Bluetooth device.
Less Hardware:-
Perceptibly the deficiency of connecting wires is an advantage of Bluetooth, but it is even compact than
Wireless connection. To make a wireless structure in user household applying Wi-Fi, they will want a
router to arrange the access point. All statement between two tools on a wireless structure must go over
user wireless router. With this, the tools express openly to one other. As long as their devices usually have
Bluetooth empowered, the user does not want any supplementary hardware to join them. If they do want
additional hardware, it is in the method a little USB that enhances Bluetooth link to a user device.
Disadvantage:-
The suitability of these technologies cannot be repudiated, but neither can the technique they have
harmfully obstructed everyday existing. Specific of the possessions can be distributed with if limitations
are fixed. Here this report will describe a specific harmful impression of device.
Destruction of Confidentiality:
The processors and phone generally cover secretive stuff like family photographs, bank account figures,
and PINs (Palumbo et al., 2015). The hacker directs a user a transcript when established, and it will be
released as a standard letter wherever truly it has a constructed-in network attacking software. When the
operator opens the transcript, the cyber attacker will be capable of regulating the operator’s device.
Disruption:

11BLUETOOTH AND NETWORK
In a similar technique as taking data from the network, transporting information through Bluetooth might
damage user tools if the information cover viruses. The virus power diverges from one to other. Certain
harms are stress-free to be detached while certain viruses harm the tool when they spread the device.
Fitness Impairment:
Whereas the theme residues provocative, some persons trust the microwave radioactivity the phones emit
can create some difficulties as Alzheimer’s illness and cancer from continued use.
Apply in unsuitable places:
Applying Bluetooth to transmission information in unsuitable spaces is measured to be damaging, and
such conduct articulates an undesirable attitude (Jedda et al., 2014). For example, one student in a
schoolroom may get remindful transmitting information via Bluetooth applying their handphones while
their professor is providing a lecture.
Corrupt Contents:
A kid or a youngster may inoffensively accept a file that covers wicked contents which are not
appropriate for their stage.
Slow Data:
Every wireless technology has bounds on how rapid they can transfer information. Usually, rapid
connections mean advanced energy depletion. Because Bluetooth is envisioned to be very energy
In a similar technique as taking data from the network, transporting information through Bluetooth might
damage user tools if the information cover viruses. The virus power diverges from one to other. Certain
harms are stress-free to be detached while certain viruses harm the tool when they spread the device.
Fitness Impairment:
Whereas the theme residues provocative, some persons trust the microwave radioactivity the phones emit
can create some difficulties as Alzheimer’s illness and cancer from continued use.
Apply in unsuitable places:
Applying Bluetooth to transmission information in unsuitable spaces is measured to be damaging, and
such conduct articulates an undesirable attitude (Jedda et al., 2014). For example, one student in a
schoolroom may get remindful transmitting information via Bluetooth applying their handphones while
their professor is providing a lecture.
Corrupt Contents:
A kid or a youngster may inoffensively accept a file that covers wicked contents which are not
appropriate for their stage.
Slow Data:
Every wireless technology has bounds on how rapid they can transfer information. Usually, rapid
connections mean advanced energy depletion. Because Bluetooth is envisioned to be very energy

12BLUETOOTH AND NETWORK
effective, it directs data comparatively slowly. The Bluetooth lesser Energy average, at 20.55 megabits
per second, is much quicker than Bluetooth applied to offer and appropriate for irregular syncing and
small backup processes. Though Bluetooth is not a supernumerary for quicker technologies like USB and
Wi-Fi.
Battery Drain
While Bluetooth is an energy effective technology, it does gradually drain the battery of user cell
telephonic or processor device (El-Bendary & El-Tokhy, 2014). When allowed, Bluetooth frequently
scans for data signals, searching for innovative devices to link with, but applying energy in the procedure.
Impact:-
Thanks to these apparatus a wireless LAN can be executed without wires. These denote that every
function of a predictable fixed LAN is accessible in a WLAN counting, peripheral sharing, file
distribution, Internet access and many more.
Flexibility and low cost:
The cost-saving and flexible connection are the key benefits of wireless networks in civilization. Many
application circumstances of wireless are connected to these two structures. Flexibility supports operators
to wander on while existence linked to support systems. Many professions need wandering employees.
Portable computers are essential for persons like inventory workers, healthcare workforces, forces majors,
and emergency-care authorities. Wireless system delivers significant cost investments in the zones where
cables cannot be simply installed, like historical constructions and housing communities. In unfriendly
positions, division headquarters and other conditions where internal interacting skill might not be
accessible or reckless networking is wanted, computers prepared with wireless LANs can be prearranged
and transported completely to use.
effective, it directs data comparatively slowly. The Bluetooth lesser Energy average, at 20.55 megabits
per second, is much quicker than Bluetooth applied to offer and appropriate for irregular syncing and
small backup processes. Though Bluetooth is not a supernumerary for quicker technologies like USB and
Wi-Fi.
Battery Drain
While Bluetooth is an energy effective technology, it does gradually drain the battery of user cell
telephonic or processor device (El-Bendary & El-Tokhy, 2014). When allowed, Bluetooth frequently
scans for data signals, searching for innovative devices to link with, but applying energy in the procedure.
Impact:-
Thanks to these apparatus a wireless LAN can be executed without wires. These denote that every
function of a predictable fixed LAN is accessible in a WLAN counting, peripheral sharing, file
distribution, Internet access and many more.
Flexibility and low cost:
The cost-saving and flexible connection are the key benefits of wireless networks in civilization. Many
application circumstances of wireless are connected to these two structures. Flexibility supports operators
to wander on while existence linked to support systems. Many professions need wandering employees.
Portable computers are essential for persons like inventory workers, healthcare workforces, forces majors,
and emergency-care authorities. Wireless system delivers significant cost investments in the zones where
cables cannot be simply installed, like historical constructions and housing communities. In unfriendly
positions, division headquarters and other conditions where internal interacting skill might not be
accessible or reckless networking is wanted, computers prepared with wireless LANs can be prearranged
and transported completely to use.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13BLUETOOTH AND NETWORK
Movement of Information:
The LAN industry has been the concentrate on workplaces since the industry originated. However, just,
home networking is perceived to be a rapidly increasing market. The PC has develop a controlling stage
for entertainment, instruction, evidence access and particular investment applications (Albazrqaoe,
Huang & Xing, 2016). At household, with the extensive application of computers and the Internet
suitable the critical technique to access evidence. The role of the computer has extended and will last to
increase especially in the region of learning. On the perspective of the community side, this denotes that
wireless structures are the straightforward approach to use the internet, discover evidence, and at the
similar period the operators acquire additional information over surfing the internet.
Escaping wire mass:
This device is also one of the instances of applying wireless distance other than PDA. The purpose of
these technology is to substitute infrared, and cable links applied to attach unconnected automated tools
with a unique widespread minimum-range radio connection.
Manufacturing boom:
These applications imitate the mobile device industry setting of the discoverers of some well-known
phone like Sony Ericsson, Motorola and Nokia. There are several valuable possessions that Bluetooth had
specified to human culture.
Movement of Information:
The LAN industry has been the concentrate on workplaces since the industry originated. However, just,
home networking is perceived to be a rapidly increasing market. The PC has develop a controlling stage
for entertainment, instruction, evidence access and particular investment applications (Albazrqaoe,
Huang & Xing, 2016). At household, with the extensive application of computers and the Internet
suitable the critical technique to access evidence. The role of the computer has extended and will last to
increase especially in the region of learning. On the perspective of the community side, this denotes that
wireless structures are the straightforward approach to use the internet, discover evidence, and at the
similar period the operators acquire additional information over surfing the internet.
Escaping wire mass:
This device is also one of the instances of applying wireless distance other than PDA. The purpose of
these technology is to substitute infrared, and cable links applied to attach unconnected automated tools
with a unique widespread minimum-range radio connection.
Manufacturing boom:
These applications imitate the mobile device industry setting of the discoverers of some well-known
phone like Sony Ericsson, Motorola and Nokia. There are several valuable possessions that Bluetooth had
specified to human culture.

14BLUETOOTH AND NETWORK
Evidence Exchange:
In conferences and meetings, operators can distribute evidence rapidly with all members without any
wired networks.
Suitability:
An operator can too cordlessly control and run, for example, a projector, or can attach his receiver to his
processor or any wired linking to save hands-free for more significant tasks whereas in the workplace,
household or in the car (Chakrabarty & Engels, 2016). When laptop accepts an electronic mail, the
operator will get a warning message on the phone. Operators can also surf every received messages and
read those particular on the phone’s display.
Creative and Time saver:
In this device enabled commercial world, the phone could deliver a connection to the whole thing outside
the 10-meter range restriction (Pothuganti & Chitneni, 2014). Without even eliminating their
Bluetooth-enabled handset from their luggage or briefcase, mobile experts would be capable of checking
voice message, send a received email, fax, authenticate inventory levels, and browse the Internet over
their mainframe processors.
Conclusion:-
This report was done to measure the impression of Bluetooth technology on the social order in the
upcoming time. These paper have examined why and how Bluetooth technology has extensively
distributed and what impression that Bluetooth technology has been providing. Bluetooth apparatus in the
household are continually connecting with one other as long as they are switched on. Every device directs
out a signal, established by other devices that are transferring out their particular signals. The apparatus
scan entire signals to perceive if any are speaking it. In this method, Bluetooth makes a PAN in the
household, and the operator is not prerequisite to do anything exceptional to get the tools to express to
Evidence Exchange:
In conferences and meetings, operators can distribute evidence rapidly with all members without any
wired networks.
Suitability:
An operator can too cordlessly control and run, for example, a projector, or can attach his receiver to his
processor or any wired linking to save hands-free for more significant tasks whereas in the workplace,
household or in the car (Chakrabarty & Engels, 2016). When laptop accepts an electronic mail, the
operator will get a warning message on the phone. Operators can also surf every received messages and
read those particular on the phone’s display.
Creative and Time saver:
In this device enabled commercial world, the phone could deliver a connection to the whole thing outside
the 10-meter range restriction (Pothuganti & Chitneni, 2014). Without even eliminating their
Bluetooth-enabled handset from their luggage or briefcase, mobile experts would be capable of checking
voice message, send a received email, fax, authenticate inventory levels, and browse the Internet over
their mainframe processors.
Conclusion:-
This report was done to measure the impression of Bluetooth technology on the social order in the
upcoming time. These paper have examined why and how Bluetooth technology has extensively
distributed and what impression that Bluetooth technology has been providing. Bluetooth apparatus in the
household are continually connecting with one other as long as they are switched on. Every device directs
out a signal, established by other devices that are transferring out their particular signals. The apparatus
scan entire signals to perceive if any are speaking it. In this method, Bluetooth makes a PAN in the
household, and the operator is not prerequisite to do anything exceptional to get the tools to express to

15BLUETOOTH AND NETWORK
one other. They function in a continuous communicating mode by default. Bluetooth is a description for
Wireless Private Area. It is a technique to link and exchange evidence and information between laptops,
mobile phones, video games and digital cameras. The message is wireless and has a distance of up to 5-15
meters. In this report, the writer is describing the basic description and network architecture of the
Bluetooth network. In this report are also develops some ideas about the advantage and disadvantage of
this device which can be essential for the future work about this topic.
one other. They function in a continuous communicating mode by default. Bluetooth is a description for
Wireless Private Area. It is a technique to link and exchange evidence and information between laptops,
mobile phones, video games and digital cameras. The message is wireless and has a distance of up to 5-15
meters. In this report, the writer is describing the basic description and network architecture of the
Bluetooth network. In this report are also develops some ideas about the advantage and disadvantage of
this device which can be essential for the future work about this topic.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16BLUETOOTH AND NETWORK
References:-
Afonso, J. A., Maio, A. J. F., & Simoes, R. (2016). Performance evaluation of bluetooth low
energy for high data rate body area networks. Wireless Personal Communications, 90(1),
121-141.
Albazrqaoe, W., Huang, J., & Xing, G. (2016, June). Practical bluetooth traffic sniffing: Systems
and privacy implications. In Proceedings of the 14th Annual International Conference on
Mobile Systems, Applications, and Services (pp. 333-345).
Chakrabarty, S., & Engels, D. W. (2016, January). Black networks for bluetooth low energy. In
2016 IEEE International Conference on Consumer Electronics (ICCE) (pp. 11-14).
IEEE.
Cho, K., Park, W., Hong, M., Park, G., Cho, W., Seo, J., & Han, K. (2015). Analysis of latency
performance of Bluetooth low energy (BLE) networks. Sensors, 15(1), 59-78.
Darroudi, S. M., & Gomez, C. (2017). Bluetooth low energy mesh networks: A survey. Sensors,
17(7), 1467.
El-Bendary, M. A. M., & El-Tokhy, M. A. R. (2014). Efficient Performance and Lower
Complexity of Error Control Schemes for WPAN Bluetooth Networks. Journal of
Telecommunications and Information Technology, (4), 100-107.
Jedda, A., Casteigts, A., Jourdan, G. V., & Mouftah, H. T. (2014). Bluetooth scatternet formation
from a time-efficiency perspective. Wireless networks, 20(5), 1133-1156.
References:-
Afonso, J. A., Maio, A. J. F., & Simoes, R. (2016). Performance evaluation of bluetooth low
energy for high data rate body area networks. Wireless Personal Communications, 90(1),
121-141.
Albazrqaoe, W., Huang, J., & Xing, G. (2016, June). Practical bluetooth traffic sniffing: Systems
and privacy implications. In Proceedings of the 14th Annual International Conference on
Mobile Systems, Applications, and Services (pp. 333-345).
Chakrabarty, S., & Engels, D. W. (2016, January). Black networks for bluetooth low energy. In
2016 IEEE International Conference on Consumer Electronics (ICCE) (pp. 11-14).
IEEE.
Cho, K., Park, W., Hong, M., Park, G., Cho, W., Seo, J., & Han, K. (2015). Analysis of latency
performance of Bluetooth low energy (BLE) networks. Sensors, 15(1), 59-78.
Darroudi, S. M., & Gomez, C. (2017). Bluetooth low energy mesh networks: A survey. Sensors,
17(7), 1467.
El-Bendary, M. A. M., & El-Tokhy, M. A. R. (2014). Efficient Performance and Lower
Complexity of Error Control Schemes for WPAN Bluetooth Networks. Journal of
Telecommunications and Information Technology, (4), 100-107.
Jedda, A., Casteigts, A., Jourdan, G. V., & Mouftah, H. T. (2014). Bluetooth scatternet formation
from a time-efficiency perspective. Wireless networks, 20(5), 1133-1156.

17BLUETOOTH AND NETWORK
Jeon, W. S., Dwijaksara, M. H., & Jeong, D. G. (2016). Performance analysis of neighbor
discovery process in bluetooth low-energy networks. IEEE Transactions on Vehicular
Technology, 66(2), 1865-1871.
Jung, C., Kim, K., Seo, J., Silva, B. N., & Han, K. (2017). Topology configuration and multihop
routing protocol for bluetooth low energy networks. IEEE Access, 5, 9587-9598.
Leonardi, L., Patti, G., & Bello, L. L. (2018). Multi-hop real-time communications over
bluetooth low energy industrial wireless mesh networks. IEEE Access, 6, 26505-26519.
Nair, K., Kulkarni, J., Warde, M., Dave, Z., Rawalgaonkar, V., Gore, G., & Joshi, J. (2015,
October). Optimizing power consumption in iot based wireless sensor networks using
Bluetooth Low Energy. In 2015 International Conference on Green Computing and
Internet of Things (ICGCIoT) (pp. 589-593). IEEE.
Palumbo, F., Barsocchi, P., Chessa, S., & Augusto, J. C. (2015, August). A stigmergic approach
to indoor localization using bluetooth low energy beacons. In 2015 12th IEEE
International Conference on Advanced Video and Signal Based Surveillance (AVSS) (pp.
1-6). IEEE.
Patti, G., Leonardi, L., & Bello, L. L. (2016, October). A Bluetooth low energy real-time
protocol for industrial wireless mesh networks. In IECON 2016-42nd Annual Conference
of the IEEE Industrial Electronics Society (pp. 4627-4632). IEEE.
Pothuganti, K., & Chitneni, A. (2014). A comparative study of wireless protocols: Bluetooth,
UWB, ZigBee, and Wi-Fi. Advance in Electronic and Electric Engineering, 4(6), 655-
662.
Jeon, W. S., Dwijaksara, M. H., & Jeong, D. G. (2016). Performance analysis of neighbor
discovery process in bluetooth low-energy networks. IEEE Transactions on Vehicular
Technology, 66(2), 1865-1871.
Jung, C., Kim, K., Seo, J., Silva, B. N., & Han, K. (2017). Topology configuration and multihop
routing protocol for bluetooth low energy networks. IEEE Access, 5, 9587-9598.
Leonardi, L., Patti, G., & Bello, L. L. (2018). Multi-hop real-time communications over
bluetooth low energy industrial wireless mesh networks. IEEE Access, 6, 26505-26519.
Nair, K., Kulkarni, J., Warde, M., Dave, Z., Rawalgaonkar, V., Gore, G., & Joshi, J. (2015,
October). Optimizing power consumption in iot based wireless sensor networks using
Bluetooth Low Energy. In 2015 International Conference on Green Computing and
Internet of Things (ICGCIoT) (pp. 589-593). IEEE.
Palumbo, F., Barsocchi, P., Chessa, S., & Augusto, J. C. (2015, August). A stigmergic approach
to indoor localization using bluetooth low energy beacons. In 2015 12th IEEE
International Conference on Advanced Video and Signal Based Surveillance (AVSS) (pp.
1-6). IEEE.
Patti, G., Leonardi, L., & Bello, L. L. (2016, October). A Bluetooth low energy real-time
protocol for industrial wireless mesh networks. In IECON 2016-42nd Annual Conference
of the IEEE Industrial Electronics Society (pp. 4627-4632). IEEE.
Pothuganti, K., & Chitneni, A. (2014). A comparative study of wireless protocols: Bluetooth,
UWB, ZigBee, and Wi-Fi. Advance in Electronic and Electric Engineering, 4(6), 655-
662.

18BLUETOOTH AND NETWORK
Priyanka, S. S., & Nagajayanthi, B. (2014, November). Enhancing security in Bluetooth
networks. In 2014 International Conference on Science Engineering and Management
Research (ICSEMR) (pp. 1-3). IEEE.
Varsamou, M., & Antonakopoulos, T. (2014, September). A bluetooth smart analyzer in iBeacon
networks. In 2014 IEEE Fourth International Conference on Consumer Electronics
Berlin (ICCE-Berlin) (pp. 288-292). IEEE.
Yu, C. M., & Yu, Y. B. (2014). Reconfigurable algorithm for bluetooth sensor networks. IEEE
Sensors Journal, 14(10), 3506-3507.
Priyanka, S. S., & Nagajayanthi, B. (2014, November). Enhancing security in Bluetooth
networks. In 2014 International Conference on Science Engineering and Management
Research (ICSEMR) (pp. 1-3). IEEE.
Varsamou, M., & Antonakopoulos, T. (2014, September). A bluetooth smart analyzer in iBeacon
networks. In 2014 IEEE Fourth International Conference on Consumer Electronics
Berlin (ICCE-Berlin) (pp. 288-292). IEEE.
Yu, C. M., & Yu, Y. B. (2014). Reconfigurable algorithm for bluetooth sensor networks. IEEE
Sensors Journal, 14(10), 3506-3507.
1 out of 19
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


