Risk Management for IT Software Project
VerifiedAdded on 2020/02/24
|7
|1222
|82
AI Summary
This assignment focuses on analyzing the risks and opportunities associated with an OIT project involving a switch to new ticketing software for front-end users. The analysis utilizes a risk matrix to rank potential issues based on likelihood and impact. Proposed mitigation strategies include resource allocation, enhanced communication, and leveraging back-end user expertise. The report also emphasizes the importance of ongoing risk monitoring and control throughout the project lifecycle.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Name of University
BN205 Project Management
Risk Management Plan
Student’s Name:
8/28/2017
BN205 Project Management
Risk Management Plan
Student’s Name:
8/28/2017
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

BN205 Project Management
Executive summary
All projects have defined time period and it’s a challenge for the project manager to manage all the
issues related to the project in the defined time frame. In current report also, the issues or risks which
may arise during the project life cycle shall be identified and after analyzing its mitigation plan shall be
developed.
Page 1
Executive summary
All projects have defined time period and it’s a challenge for the project manager to manage all the
issues related to the project in the defined time frame. In current report also, the issues or risks which
may arise during the project life cycle shall be identified and after analyzing its mitigation plan shall be
developed.
Page 1

BN205 Project Management
Table of Contents
Introduction.................................................................................................................................................3
Background of the case study......................................................................................................................3
Risk Management Plan................................................................................................................................3
Risk Identification........................................................................................................................................3
Risk Analysis................................................................................................................................................4
Risk responses.............................................................................................................................................5
Risk - Monitoring and Controlling................................................................................................................5
Justification.................................................................................................................................................5
Conclusion...................................................................................................................................................5
References...................................................................................................................................................5
List of Figure
Figure1: Risk matrix.....................................................................................................................................4
Page 2
Table of Contents
Introduction.................................................................................................................................................3
Background of the case study......................................................................................................................3
Risk Management Plan................................................................................................................................3
Risk Identification........................................................................................................................................3
Risk Analysis................................................................................................................................................4
Risk responses.............................................................................................................................................5
Risk - Monitoring and Controlling................................................................................................................5
Justification.................................................................................................................................................5
Conclusion...................................................................................................................................................5
References...................................................................................................................................................5
List of Figure
Figure1: Risk matrix.....................................................................................................................................4
Page 2

BN205 Project Management
Introduction
Risk management is a tool to identify threats and opportunities, and then analyze them to provide
proper ranking, then on the basis of ranks, mitigation plans are defined1. This knowledge area of project
management deals with the threats and plan accordingly so that it doesn’t let impact any of the three
constraints of the project.
Background of the case study
All the information system related activity in the whole institute SFSU (Silicon Forest State University) is
being taken care by the department OIT (Office of Information Technology). The back end users of OIT
used ‘Request Tracker’ for communicating and tracking the ticketing system based on UNIX, whereas the
front end user were using ‘Remedy’ system for generating and tracking ticketing system. For any kind of
request to back end users, the front end users need to manually type the issue to ‘Request tracker’ and
this pain remained for three years. But now the department decided to change the front end system to
‘Request tracker’ and handed the project to Ron Bashley as project leader with the team of Harry
Bonnett. But the issue is the reporting office of Ron and Harry is different and moreover they both are at
similar organization level.
Risk Management Plan
The threats or the opportunity in any project are regulated on the preface of the techniques portrayed
in the risk management and administration plan. The exercises which incorporate into the planning of
risk administration design are identification of Risk, risk analysis, risk Mitigation and Hazard Monitoring
throughout the project life cycle2. The dangers can be of many sorts, and fit for affecting cost, plan,
quality, specialized, legally binding, acquisition, approaches and so on. A definitive point of the
arrangement is to set the relief activity get ready for all the distinguished dangers exceptionally at a
range by mentioning rank from 1 to 5, where 1 is the lowest level and 5 is the extremely high or critical.
There are different sorts of dangers alleviation procedures or steps which should be taken after ranking
all the identified risks. There can be principally four sorts of reaction after the evaluations of dangers are
accept it, avoid it, mitigate it or transfer it3.
Risk Identification
The first step of the risk management is ‘the identification of risk’. Few identified risks are:
Risk Date Raised Type Description and Cause
Page 3
Introduction
Risk management is a tool to identify threats and opportunities, and then analyze them to provide
proper ranking, then on the basis of ranks, mitigation plans are defined1. This knowledge area of project
management deals with the threats and plan accordingly so that it doesn’t let impact any of the three
constraints of the project.
Background of the case study
All the information system related activity in the whole institute SFSU (Silicon Forest State University) is
being taken care by the department OIT (Office of Information Technology). The back end users of OIT
used ‘Request Tracker’ for communicating and tracking the ticketing system based on UNIX, whereas the
front end user were using ‘Remedy’ system for generating and tracking ticketing system. For any kind of
request to back end users, the front end users need to manually type the issue to ‘Request tracker’ and
this pain remained for three years. But now the department decided to change the front end system to
‘Request tracker’ and handed the project to Ron Bashley as project leader with the team of Harry
Bonnett. But the issue is the reporting office of Ron and Harry is different and moreover they both are at
similar organization level.
Risk Management Plan
The threats or the opportunity in any project are regulated on the preface of the techniques portrayed
in the risk management and administration plan. The exercises which incorporate into the planning of
risk administration design are identification of Risk, risk analysis, risk Mitigation and Hazard Monitoring
throughout the project life cycle2. The dangers can be of many sorts, and fit for affecting cost, plan,
quality, specialized, legally binding, acquisition, approaches and so on. A definitive point of the
arrangement is to set the relief activity get ready for all the distinguished dangers exceptionally at a
range by mentioning rank from 1 to 5, where 1 is the lowest level and 5 is the extremely high or critical.
There are different sorts of dangers alleviation procedures or steps which should be taken after ranking
all the identified risks. There can be principally four sorts of reaction after the evaluations of dangers are
accept it, avoid it, mitigate it or transfer it3.
Risk Identification
The first step of the risk management is ‘the identification of risk’. Few identified risks are:
Risk Date Raised Type Description and Cause
Page 3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
BN205 Project Management
Numbe
r
Logged By
1 25/08/201
7
Pike Risk Since the activity 'collection of requirement' has already
consumed three months so there is a risk of schedule
overrun.
2 27/08/201
7
Ron Risk There is risk of having communication gap during the
project phase when none of the system shall be
available and only need to be depended on email
service
3 28/08/201
7
Baken Opportunity There is an opportunity of completing the project before
schedule due to the already availability of 'Request
Tracker' with back end users
Risk Analysis
Risk / Opportunity Analysis
Risk
Number
Description and Cause Likelihood Consequence
1 Since the activity 'collection of requirement' has already
consumed three months so there is a risk of schedule overrun. 3 4
2
There is risk of having communication gap during the project
phase when none of the system shall be available and only
need to be depended on email service 3 5
3
There is an opportunity of completing the project before
schedule due to the already availability of 'Request Tracker'
with back end users
3 4
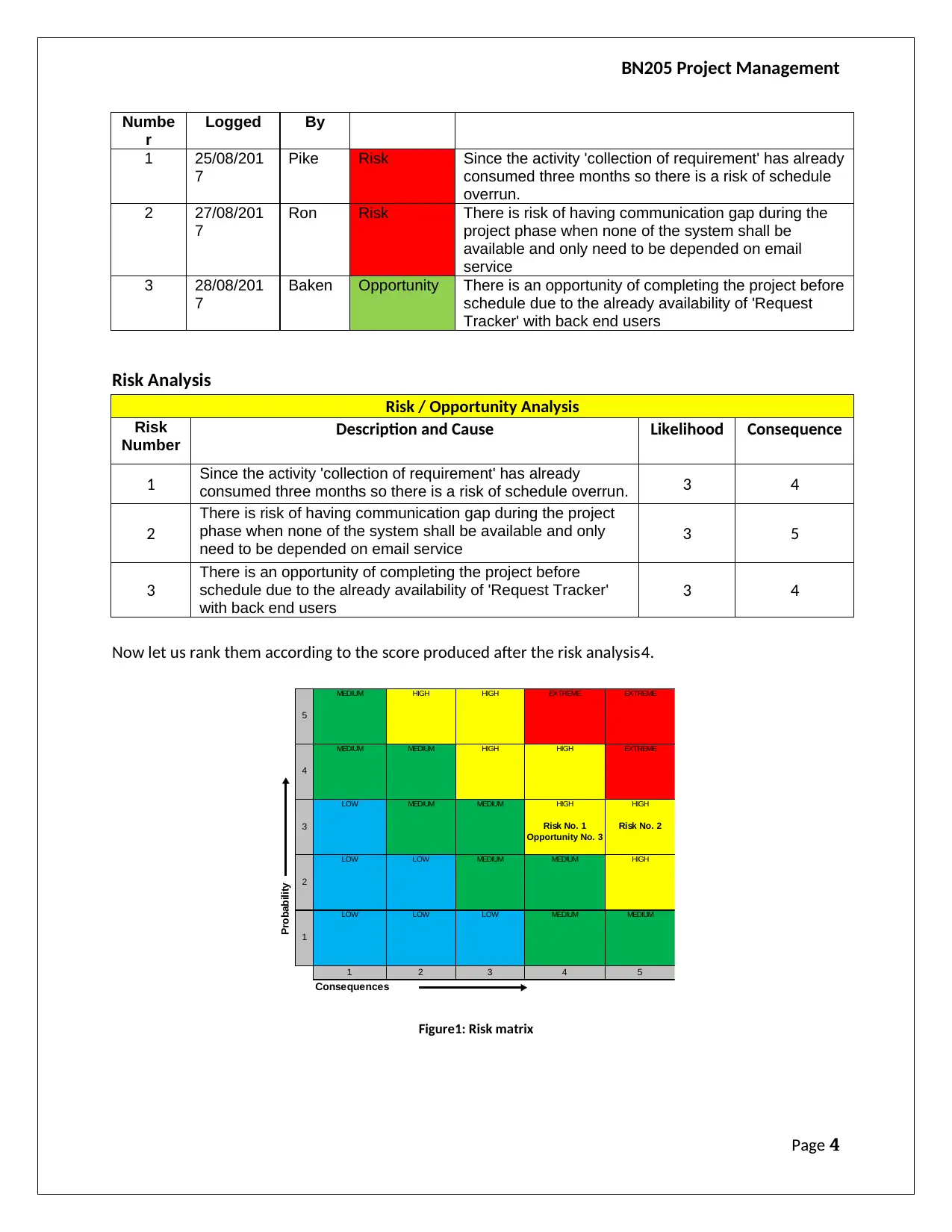
Now let us rank them according to the score produced after the risk analysis4.
1 2 3 4 5
HIGH
EXTREMEMEDIUM
HIGH
HIGH
Risk No. 1
Opportunity No. 3
MEDIUM
MEDIUM
LOW
2
5
4
3
HIGH
MEDIUM
Probability
1
LOW LOW LOW
LOW MEDIUM
Consequences
EXTREME
EXTREME
HIGH
Risk No. 2
HIGH
MEDIUM
MEDIUM
LOW
MEDIUM
MEDIUM
HIGH
Figure1: Risk matrix
Page 4
Numbe
r
Logged By
1 25/08/201
7
Pike Risk Since the activity 'collection of requirement' has already
consumed three months so there is a risk of schedule
overrun.
2 27/08/201
7
Ron Risk There is risk of having communication gap during the
project phase when none of the system shall be
available and only need to be depended on email
service
3 28/08/201
7
Baken Opportunity There is an opportunity of completing the project before
schedule due to the already availability of 'Request
Tracker' with back end users
Risk Analysis
Risk / Opportunity Analysis
Risk
Number
Description and Cause Likelihood Consequence
1 Since the activity 'collection of requirement' has already
consumed three months so there is a risk of schedule overrun. 3 4
2
There is risk of having communication gap during the project
phase when none of the system shall be available and only
need to be depended on email service 3 5
3
There is an opportunity of completing the project before
schedule due to the already availability of 'Request Tracker'
with back end users
3 4
Now let us rank them according to the score produced after the risk analysis4.
1 2 3 4 5
HIGH
EXTREMEMEDIUM
HIGH
HIGH
Risk No. 1
Opportunity No. 3
MEDIUM
MEDIUM
LOW
2
5
4
3
HIGH
MEDIUM
Probability
1
LOW LOW LOW
LOW MEDIUM
Consequences
EXTREME
EXTREME
HIGH
Risk No. 2
HIGH
MEDIUM
MEDIUM
LOW
MEDIUM
MEDIUM
HIGH
Figure1: Risk matrix
Page 4

BN205 Project Management
Risk responses
After the ranking of the risks and opportunity are done, we need to plan for the mitigation by avoiding,
accepting, reducing or sharing. Since all the risks identified are ‘HIGH’, so the responses are:
Risk 1: to control the time schedule, more resources are recommended to mobilize for the
project from other department for these three months
Risk 2: all the measures to minimize the communication gap should be adopted like ‘often and
early communicate’5 and many other.
Opportunity 3: the experience of back end users must be explored more for early completion of
the project.
Risk - Monitoring and Controlling
All the information gathered in all above steps need to be mentioned in the common risk register and
then the job of Ron should be to present and discuss the same in every review meetings. Also any more
risks which are identified by any of the stakeholders must be analyzed and provide rank to help in
mitigating. This way the risk register must be monitored throughout the project.
Justification
So after reviewing the report, it can be recommended that the risk register need to be updated
according to the step described and all the approaches need to be followed closely to avoid any risk to
impact the triple constraints of the project undertaken by OIT.
Conclusion
To conclude the whole report, first the risks involved in OIT’s project to change the ticketing software of
the front end users are identified and then by following the approaches defined in PMBoK are used. So
the risks are analyzed and the risks are given proper ranking and accordingly the mitigation planning is
done.
References
x
[1] Educba. (2016, July) 6 Basic Steps to Develop a Project Risk Management Plan. [Online].
Page 5
Risk responses
After the ranking of the risks and opportunity are done, we need to plan for the mitigation by avoiding,
accepting, reducing or sharing. Since all the risks identified are ‘HIGH’, so the responses are:
Risk 1: to control the time schedule, more resources are recommended to mobilize for the
project from other department for these three months
Risk 2: all the measures to minimize the communication gap should be adopted like ‘often and
early communicate’5 and many other.
Opportunity 3: the experience of back end users must be explored more for early completion of
the project.
Risk - Monitoring and Controlling
All the information gathered in all above steps need to be mentioned in the common risk register and
then the job of Ron should be to present and discuss the same in every review meetings. Also any more
risks which are identified by any of the stakeholders must be analyzed and provide rank to help in
mitigating. This way the risk register must be monitored throughout the project.
Justification
So after reviewing the report, it can be recommended that the risk register need to be updated
according to the step described and all the approaches need to be followed closely to avoid any risk to
impact the triple constraints of the project undertaken by OIT.
Conclusion
To conclude the whole report, first the risks involved in OIT’s project to change the ticketing software of
the front end users are identified and then by following the approaches defined in PMBoK are used. So
the risks are analyzed and the risks are given proper ranking and accordingly the mitigation planning is
done.
References
x
[1] Educba. (2016, July) 6 Basic Steps to Develop a Project Risk Management Plan. [Online].
Page 5

BN205 Project Management
https://www.educba.com/project-risk-management-plan/
[2] Vivian Kloosterman. (2014) What are the 5 Risk Management Steps in a Sound Risk Management
Process? [Online]. http://continuingprofessionaldevelopment.org/risk-management-steps-in-risk-
management-process/
[3] The MITRE Corporation. (2017) Risk Mitigation Planning, Implementation, and Progress Monitoring.
[Online]. https://www.mitre.org/publications/systems-engineering-guide/acquisition-systems-
engineering/risk-management/risk-mitigation-planning-implementation-and-progress-monitoring
[4] Nassim Nicholas. (2015, August) Making A Risk Matrix Useful. [Online].
http://causalcapital.blogspot.in/2015/08/making-risk-matrix-useful.html
[5] Naomi Karten. (2013, August) Communication Gaps and How to Close Them. [Online].
http://www.informit.com/articles/article.aspx?p=2122831&seqNum=4
x
Page 6
https://www.educba.com/project-risk-management-plan/
[2] Vivian Kloosterman. (2014) What are the 5 Risk Management Steps in a Sound Risk Management
Process? [Online]. http://continuingprofessionaldevelopment.org/risk-management-steps-in-risk-
management-process/
[3] The MITRE Corporation. (2017) Risk Mitigation Planning, Implementation, and Progress Monitoring.
[Online]. https://www.mitre.org/publications/systems-engineering-guide/acquisition-systems-
engineering/risk-management/risk-mitigation-planning-implementation-and-progress-monitoring
[4] Nassim Nicholas. (2015, August) Making A Risk Matrix Useful. [Online].
http://causalcapital.blogspot.in/2015/08/making-risk-matrix-useful.html
[5] Naomi Karten. (2013, August) Communication Gaps and How to Close Them. [Online].
http://www.informit.com/articles/article.aspx?p=2122831&seqNum=4
x
Page 6
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





