Security and Privacy Challenges for IoT
VerifiedAdded on 2023/01/12
|8
|2522
|92
AI Summary
This assignment discusses the security and privacy challenges faced by IoT devices. It covers the types of IoT devices and their applications, compares different variants of attacks against IoT, explores measures and security protection techniques against IoT attacks, and discusses two specified protocols for IoT devices. The assignment provides a comprehensive overview of the topic and highlights the importance of security in the IoT ecosystem.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CASE STUDY
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of content
INTRODUCTION...........................................................................................................................1
MAIN BODY..................................................................................................................................1
IOT devices, types and their application.....................................................................................1
Compare three variants of attacks against IoT............................................................................2
Three measure and security protection technique against IOT attack.........................................3
Discuss two protocol specified to IOT device.............................................................................5
SUMMARY.....................................................................................................................................5
REREFENCES................................................................................................................................6
INTRODUCTION...........................................................................................................................1
MAIN BODY..................................................................................................................................1
IOT devices, types and their application.....................................................................................1
Compare three variants of attacks against IoT............................................................................2
Three measure and security protection technique against IOT attack.........................................3
Discuss two protocol specified to IOT device.............................................................................5
SUMMARY.....................................................................................................................................5
REREFENCES................................................................................................................................6

INTRODUCTION
IoT is also known as Internet of things which is a kind of system of interrelated
computing devices, digital and mechanical machines that helps in providing unique identifiers
and ability of transferring data over internet that do not requires human to computer or human to
human interaction (Huh, Cho and Kim, 2017). IoT has become one of the most important part of
today’s life for communication, data transfer or automating any kind task in order to ease human
work. But as advancement in technology is increasing attack against IoT devices is also
increasing. Attackers are becoming more and more aware and are using various kinds of
malware for data theft or for many other such purposes. It has also become important to focus on
security protection of such IoT devices in order to reduce risk of data theft etc. for the users. This
assignment will lay emphasis on Security and privacy challenges for IoT’s.
MAIN BODY
IOT devices, types and their application
IoT devices or things in internet of things are a kind of non- Standard computing devices
that helps in connecting to a network as well as also helps in transmitting data in an easy manner.
IoT basically involves extension of internet connectivity beyond standard devices like desktops,
smart phones and many more. With the help of technology these devices can communicate,
interact and share data with each other over internet. These devices can also be monitored and
controlled remotely. Some of the most commonly known IoT devices and their application are as
follows:
There are various kinds of devices that can talk to each other within an environment in
order to automate all the task within an environment and can also communicate with each other
using Sensor data. These devices can be used to automate all the home task, industry task and
all the other kinds of business- related task. These smart sensor data devices can be categorized
into three main categories: industrial, consumer and enterprise.
Consumer connected devices are smart TV, toys, smart speakers, smart appliances and
many more. One of the most commonly used IoT technology is Smart meters which is used by
consumers for security reasons (Kolias and et al., 2017). There are many other Smart
applications that can be used by consumers are smart lightening, smart security systems, smart
air conditioners and many more.
Devices of IOT
1
IoT is also known as Internet of things which is a kind of system of interrelated
computing devices, digital and mechanical machines that helps in providing unique identifiers
and ability of transferring data over internet that do not requires human to computer or human to
human interaction (Huh, Cho and Kim, 2017). IoT has become one of the most important part of
today’s life for communication, data transfer or automating any kind task in order to ease human
work. But as advancement in technology is increasing attack against IoT devices is also
increasing. Attackers are becoming more and more aware and are using various kinds of
malware for data theft or for many other such purposes. It has also become important to focus on
security protection of such IoT devices in order to reduce risk of data theft etc. for the users. This
assignment will lay emphasis on Security and privacy challenges for IoT’s.
MAIN BODY
IOT devices, types and their application
IoT devices or things in internet of things are a kind of non- Standard computing devices
that helps in connecting to a network as well as also helps in transmitting data in an easy manner.
IoT basically involves extension of internet connectivity beyond standard devices like desktops,
smart phones and many more. With the help of technology these devices can communicate,
interact and share data with each other over internet. These devices can also be monitored and
controlled remotely. Some of the most commonly known IoT devices and their application are as
follows:
There are various kinds of devices that can talk to each other within an environment in
order to automate all the task within an environment and can also communicate with each other
using Sensor data. These devices can be used to automate all the home task, industry task and
all the other kinds of business- related task. These smart sensor data devices can be categorized
into three main categories: industrial, consumer and enterprise.
Consumer connected devices are smart TV, toys, smart speakers, smart appliances and
many more. One of the most commonly used IoT technology is Smart meters which is used by
consumers for security reasons (Kolias and et al., 2017). There are many other Smart
applications that can be used by consumers are smart lightening, smart security systems, smart
air conditioners and many more.
Devices of IOT
1

Smart home is one of the most common examples of IoT device, if this device is installed within
home of consumer then he can directly communicate with from his car with the garage to open
the gate, installed thermostats can automatically adjust room temperature as preferred. These
smart homes help in performing all the daily routine tasks automatically (Christidis and
Devetsikiotis, 2016).
Applications of IOT
Home automation – in recent times smart homes are highly been developed. It includes sensor
technology and wireless sensors. This has enhanced the life of people. Use of sensors is done for
automatic light off, on, window and door open and close, etc. with this energy is saved and
conserved.
Smart cities - it is also an application of IOT in which smart transport is developed. RFID, GPD
sensor, etc. are used as IOT devices. This has enabled in managing traffic system and recording
movement of vehicles. Alongside, intelligence parking, automated traffic lights, GPS, and other
applications are used in it.
Smart water systems – This is also an application of IOT in which smart water systems are
used. It enables in maintaining the inflow and outflow of water. There are smart water meters as
well. Usually, these water systems are used for predicting floods (Ray, 2018).
Within enterprises as well there are smart sensors that are mostly located within
conference rooms that mostly help employees to assist them schedule of the meeting room,
ensure room size, features that are available. If there is requirement of conducting a power point
presentation them light of the room are automatically dim which is appropriate for the speaker
for the presentation.
Compare three variants of attacks against IoT
It is identified that with increase in use of technology the number of attacks has also
increased. This has resulted in stealing of confidential data and info. There are many types of
attacks which can occur. It can be in different forms such as virus, trojan, malware, etc. and
causes high damage of entire system. Likewise, in IOT as well there are several variants of
attacks. They are defined as :
Man in the middle attack – it is a common attack in IOT where an adversary connected within
network control communication between two nodes. Through this, data can be interrupted,
changed, etc. in communication. This attack is classified into 3 category that is impersonation
2
home of consumer then he can directly communicate with from his car with the garage to open
the gate, installed thermostats can automatically adjust room temperature as preferred. These
smart homes help in performing all the daily routine tasks automatically (Christidis and
Devetsikiotis, 2016).
Applications of IOT
Home automation – in recent times smart homes are highly been developed. It includes sensor
technology and wireless sensors. This has enhanced the life of people. Use of sensors is done for
automatic light off, on, window and door open and close, etc. with this energy is saved and
conserved.
Smart cities - it is also an application of IOT in which smart transport is developed. RFID, GPD
sensor, etc. are used as IOT devices. This has enabled in managing traffic system and recording
movement of vehicles. Alongside, intelligence parking, automated traffic lights, GPS, and other
applications are used in it.
Smart water systems – This is also an application of IOT in which smart water systems are
used. It enables in maintaining the inflow and outflow of water. There are smart water meters as
well. Usually, these water systems are used for predicting floods (Ray, 2018).
Within enterprises as well there are smart sensors that are mostly located within
conference rooms that mostly help employees to assist them schedule of the meeting room,
ensure room size, features that are available. If there is requirement of conducting a power point
presentation them light of the room are automatically dim which is appropriate for the speaker
for the presentation.
Compare three variants of attacks against IoT
It is identified that with increase in use of technology the number of attacks has also
increased. This has resulted in stealing of confidential data and info. There are many types of
attacks which can occur. It can be in different forms such as virus, trojan, malware, etc. and
causes high damage of entire system. Likewise, in IOT as well there are several variants of
attacks. They are defined as :
Man in the middle attack – it is a common attack in IOT where an adversary connected within
network control communication between two nodes. Through this, data can be interrupted,
changed, etc. in communication. This attack is classified into 3 category that is impersonation
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
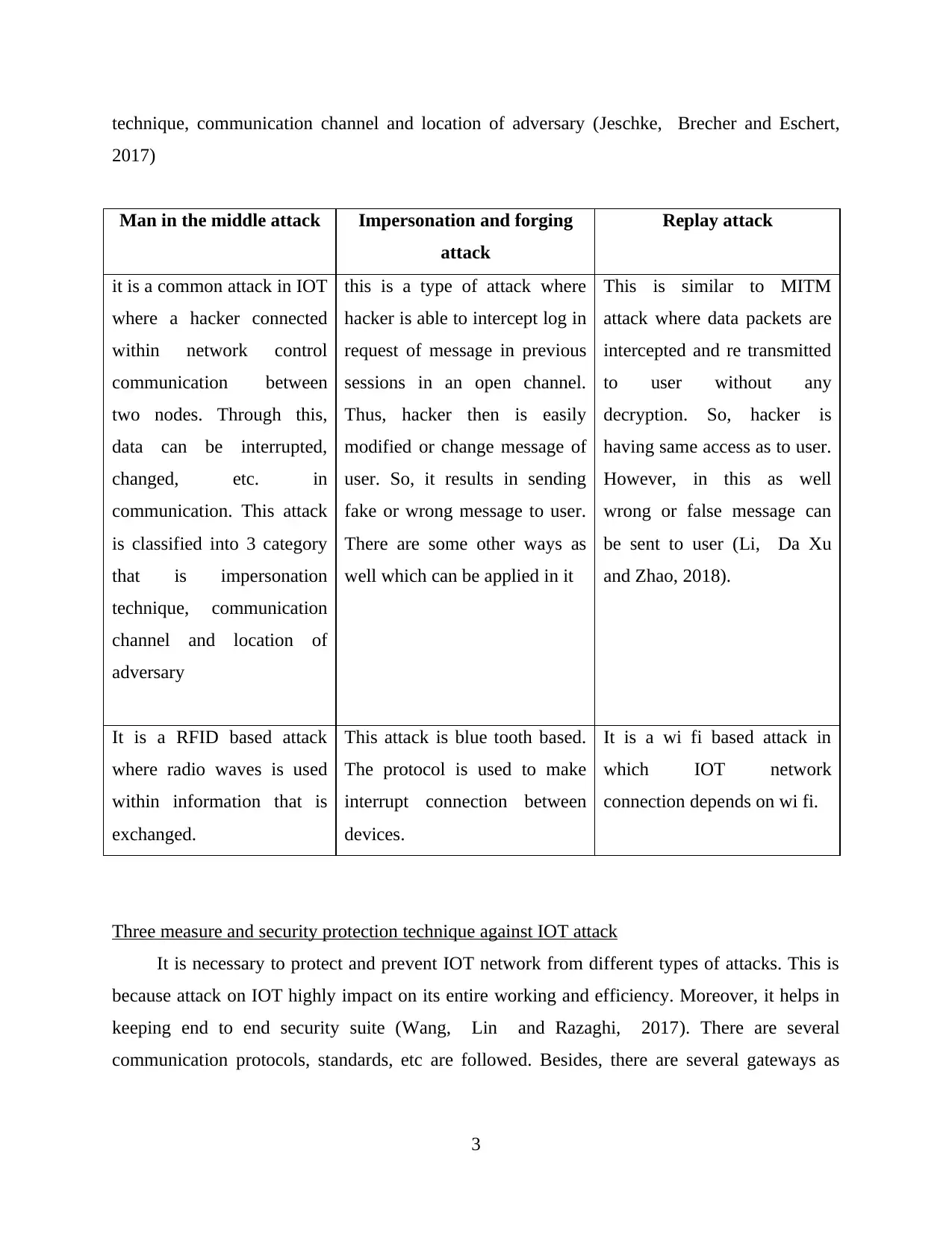
technique, communication channel and location of adversary (Jeschke, Brecher and Eschert,
2017)
Man in the middle attack Impersonation and forging
attack
Replay attack
it is a common attack in IOT
where a hacker connected
within network control
communication between
two nodes. Through this,
data can be interrupted,
changed, etc. in
communication. This attack
is classified into 3 category
that is impersonation
technique, communication
channel and location of
adversary
this is a type of attack where
hacker is able to intercept log in
request of message in previous
sessions in an open channel.
Thus, hacker then is easily
modified or change message of
user. So, it results in sending
fake or wrong message to user.
There are some other ways as
well which can be applied in it
This is similar to MITM
attack where data packets are
intercepted and re transmitted
to user without any
decryption. So, hacker is
having same access as to user.
However, in this as well
wrong or false message can
be sent to user (Li, Da Xu
and Zhao, 2018).
It is a RFID based attack
where radio waves is used
within information that is
exchanged.
This attack is blue tooth based.
The protocol is used to make
interrupt connection between
devices.
It is a wi fi based attack in
which IOT network
connection depends on wi fi.
Three measure and security protection technique against IOT attack
It is necessary to protect and prevent IOT network from different types of attacks. This is
because attack on IOT highly impact on its entire working and efficiency. Moreover, it helps in
keeping end to end security suite (Wang, Lin and Razaghi, 2017). There are several
communication protocols, standards, etc are followed. Besides, there are several gateways as
3
2017)
Man in the middle attack Impersonation and forging
attack
Replay attack
it is a common attack in IOT
where a hacker connected
within network control
communication between
two nodes. Through this,
data can be interrupted,
changed, etc. in
communication. This attack
is classified into 3 category
that is impersonation
technique, communication
channel and location of
adversary
this is a type of attack where
hacker is able to intercept log in
request of message in previous
sessions in an open channel.
Thus, hacker then is easily
modified or change message of
user. So, it results in sending
fake or wrong message to user.
There are some other ways as
well which can be applied in it
This is similar to MITM
attack where data packets are
intercepted and re transmitted
to user without any
decryption. So, hacker is
having same access as to user.
However, in this as well
wrong or false message can
be sent to user (Li, Da Xu
and Zhao, 2018).
It is a RFID based attack
where radio waves is used
within information that is
exchanged.
This attack is blue tooth based.
The protocol is used to make
interrupt connection between
devices.
It is a wi fi based attack in
which IOT network
connection depends on wi fi.
Three measure and security protection technique against IOT attack
It is necessary to protect and prevent IOT network from different types of attacks. This is
because attack on IOT highly impact on its entire working and efficiency. Moreover, it helps in
keeping end to end security suite (Wang, Lin and Razaghi, 2017). There are several
communication protocols, standards, etc are followed. Besides, there are several gateways as
3

well which is included in IOT. Thus, the measure and security protection technique are as
follows : (Security measures to protect IOT, 2018)
Network security – In this IOT can be protected with help of certain measures. They are
End point security- It is a security measure the protect enterprise IOT network which is accessed
via computer, laptop, etc. here, a potential entry point is created which prevent security threats. -
The end point security suite filters out all threats.
Network firewall – basically firewall is used to filter traffic. Likewise, in IOT as well firewall
can be used to create a barrier which prevent unnecessary traffic from another network. The
firewall can be installed in devices, laptops, etc. also, it can be either hardware or software based.
Device security the security techniques are related to protecting devices connected to IOT
network. They are described as
Hard ware security modules- HSM are commonly used in protecting the IOT network through
keys. Here, the keys are made up of cryptography combination which is centrally installed. They
can only be accessed centrally (Botta,De Donato and Pescapé, 2016)
Key manager- here, a manager authenticates IoT devices and monitors data that is been shared
on cellular and non-cellular networks, such as LoRa, avoiding unsanctioned devices from
connecting to the computer network. It makes way for a robust digital security over a trusted
instrument of remote credential initiation, secure key provisioning, and application lifecycle
management.
Communication security- Here, security measures are installed within communication.
End to end encryption- the data that is transferred in IOT network is stored in backend with
cryptographic algorithms. This help in upholding data by intruder. Also, it limits the capability of
encryption process.
Machine to machine – in many IOT network rather than having the involvement of humans at
both ends the machines can be installed for authentication purpose. It will be highly useful in
protecting from threats (Sethi and Sarangi, 2017).
API security- it can be used to validate and maintain integrity of data between IOT devices and
backend software. With this only authenticated, certified apps as well as developers will be
allowed to integrate with IOT network and use it.
Cloud security – It offers a portfolio of app and systems which can be used to protect IOT. Here,
cloud asset and licensing network technology is used to protect threats and attacks.
4
follows : (Security measures to protect IOT, 2018)
Network security – In this IOT can be protected with help of certain measures. They are
End point security- It is a security measure the protect enterprise IOT network which is accessed
via computer, laptop, etc. here, a potential entry point is created which prevent security threats. -
The end point security suite filters out all threats.
Network firewall – basically firewall is used to filter traffic. Likewise, in IOT as well firewall
can be used to create a barrier which prevent unnecessary traffic from another network. The
firewall can be installed in devices, laptops, etc. also, it can be either hardware or software based.
Device security the security techniques are related to protecting devices connected to IOT
network. They are described as
Hard ware security modules- HSM are commonly used in protecting the IOT network through
keys. Here, the keys are made up of cryptography combination which is centrally installed. They
can only be accessed centrally (Botta,De Donato and Pescapé, 2016)
Key manager- here, a manager authenticates IoT devices and monitors data that is been shared
on cellular and non-cellular networks, such as LoRa, avoiding unsanctioned devices from
connecting to the computer network. It makes way for a robust digital security over a trusted
instrument of remote credential initiation, secure key provisioning, and application lifecycle
management.
Communication security- Here, security measures are installed within communication.
End to end encryption- the data that is transferred in IOT network is stored in backend with
cryptographic algorithms. This help in upholding data by intruder. Also, it limits the capability of
encryption process.
Machine to machine – in many IOT network rather than having the involvement of humans at
both ends the machines can be installed for authentication purpose. It will be highly useful in
protecting from threats (Sethi and Sarangi, 2017).
API security- it can be used to validate and maintain integrity of data between IOT devices and
backend software. With this only authenticated, certified apps as well as developers will be
allowed to integrate with IOT network and use it.
Cloud security – It offers a portfolio of app and systems which can be used to protect IOT. Here,
cloud asset and licensing network technology is used to protect threats and attacks.
4

Discuss two protocol specified to IOT device
IOT is used for various tasks and activities. Also, there are many specified protocols that
defines how IOT must be used. The protocol are guidelines which has to be followed in setting
of network. It consists of rules followed in communication and sharing of data and info. They
vary on basis of network (Alaba, Othman and Alotaibi, 2017). In similar way, in IOT there are
certain protocols specified which has to be used. They are described as below :
IEEE 802.15.4 – this is a protocol developed for communication between high and low
frequency devices connected in IOT. it consists of standards for physical layer of IP stack. In
IEEE coding done is redundant which enable in smooth communication. Along with it, IPV6
protocols is also used in adaption layer. Through it, devices can directly communicate with help
of IP address. The CoAP protocol is used in most IOT application. It uses EXI data format. It
helps in reliable communication between network.
Light weight application layer protocol – It is a new developed protocol used in IOT network.
The protocol carry message in IOT. in this standards are defined regarding communication
between server and device. Besides that, main purpose of this protocol is to remote device
management and transfer of info between different nodes in LWM2M network. It provides a
proper interface to send message in IOT network and within server and devices. Usually it is
used with constrained application protocol (Christidis and Devetsikiotis, 2016). The protocol
allows nodes like sensor or devices to communicate within network. But its integration with
HTTP allows in providing extra support like multi cast operations. However, as name depicts the
protocol is basically used in small devices due to its low parsing complexity.
SUMMARY
It can be summarised that IoT is a system of interrelated computing devices, digital and
mechanical machines. Its devices are smart locks, sensors, smart homes, etc. in IOT as well there
are several variants of attacks. They are man in the middle, impersonation and forging and replay
attacks. Alongside, there are some security protection techniques which is followed such as
network, device and communication. In that there are several types as well firewall, end to end
encryption, and others. IOT uses certain authentication protocols as well that are IEEE 802.15.4
and Light weight application layer protocol
5
IOT is used for various tasks and activities. Also, there are many specified protocols that
defines how IOT must be used. The protocol are guidelines which has to be followed in setting
of network. It consists of rules followed in communication and sharing of data and info. They
vary on basis of network (Alaba, Othman and Alotaibi, 2017). In similar way, in IOT there are
certain protocols specified which has to be used. They are described as below :
IEEE 802.15.4 – this is a protocol developed for communication between high and low
frequency devices connected in IOT. it consists of standards for physical layer of IP stack. In
IEEE coding done is redundant which enable in smooth communication. Along with it, IPV6
protocols is also used in adaption layer. Through it, devices can directly communicate with help
of IP address. The CoAP protocol is used in most IOT application. It uses EXI data format. It
helps in reliable communication between network.
Light weight application layer protocol – It is a new developed protocol used in IOT network.
The protocol carry message in IOT. in this standards are defined regarding communication
between server and device. Besides that, main purpose of this protocol is to remote device
management and transfer of info between different nodes in LWM2M network. It provides a
proper interface to send message in IOT network and within server and devices. Usually it is
used with constrained application protocol (Christidis and Devetsikiotis, 2016). The protocol
allows nodes like sensor or devices to communicate within network. But its integration with
HTTP allows in providing extra support like multi cast operations. However, as name depicts the
protocol is basically used in small devices due to its low parsing complexity.
SUMMARY
It can be summarised that IoT is a system of interrelated computing devices, digital and
mechanical machines. Its devices are smart locks, sensors, smart homes, etc. in IOT as well there
are several variants of attacks. They are man in the middle, impersonation and forging and replay
attacks. Alongside, there are some security protection techniques which is followed such as
network, device and communication. In that there are several types as well firewall, end to end
encryption, and others. IOT uses certain authentication protocols as well that are IEEE 802.15.4
and Light weight application layer protocol
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REREFENCES
Books and Journals
Alaba, F.A., Othman, M. and Alotaibi, F., 2017. Internet of Things security: A survey. Journal of
Network and Computer Applications, 88, pp.10-28.
Botta, A., De Donato, W. and Pescapé, A., 2016. Integration of cloud computing and internet of
things: a survey. Future generation computer systems, 56, pp.684-700.
Christidis, K. and Devetsikiotis, M., 2016. Blockchains and smart contracts for the internet of
things. Ieee Access, 4, pp.2292-2303.
Huh, S., Cho, S. and Kim, S., 2017, February. Managing IoT devices using blockchain platform.
In 2017 19th international conference on advanced communication technology
(ICACT) (pp. 464-467). IEEE.
Jeschke, S., Brecher, C. and Eschert, T., 2017. Industrial internet of things and cyber
manufacturing systems. In Industrial internet of things (pp. 3-19). Springer, Cham.
Kolias, C., and et al., 2017. DDoS in the IoT: Mirai and other botnets. Computer. 50(7). pp.80-
84.
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Ray, P.P., 2018. A survey on Internet of Things architectures. Journal of King Saud University-
Computer and Information Sciences, 30(3), pp.291-319.
Sethi, P. and Sarangi, S.R., 2017. Internet of things: architectures, protocols, and
applications. Journal of Electrical and C
Wang, Y.P.E., Lin, X. and Razaghi, H.S., 2017. A primer on 3GPP narrowband Internet of
Things. IEEE Communications Magazine, 55(3), pp.117-123.
Online
Security measures to protect IOT, 2018. [online] Available through : <
https://jaxenter.com/security-measures-protect-iot-devices-150550.html>
6
Books and Journals
Alaba, F.A., Othman, M. and Alotaibi, F., 2017. Internet of Things security: A survey. Journal of
Network and Computer Applications, 88, pp.10-28.
Botta, A., De Donato, W. and Pescapé, A., 2016. Integration of cloud computing and internet of
things: a survey. Future generation computer systems, 56, pp.684-700.
Christidis, K. and Devetsikiotis, M., 2016. Blockchains and smart contracts for the internet of
things. Ieee Access, 4, pp.2292-2303.
Huh, S., Cho, S. and Kim, S., 2017, February. Managing IoT devices using blockchain platform.
In 2017 19th international conference on advanced communication technology
(ICACT) (pp. 464-467). IEEE.
Jeschke, S., Brecher, C. and Eschert, T., 2017. Industrial internet of things and cyber
manufacturing systems. In Industrial internet of things (pp. 3-19). Springer, Cham.
Kolias, C., and et al., 2017. DDoS in the IoT: Mirai and other botnets. Computer. 50(7). pp.80-
84.
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Ray, P.P., 2018. A survey on Internet of Things architectures. Journal of King Saud University-
Computer and Information Sciences, 30(3), pp.291-319.
Sethi, P. and Sarangi, S.R., 2017. Internet of things: architectures, protocols, and
applications. Journal of Electrical and C
Wang, Y.P.E., Lin, X. and Razaghi, H.S., 2017. A primer on 3GPP narrowband Internet of
Things. IEEE Communications Magazine, 55(3), pp.117-123.
Online
Security measures to protect IOT, 2018. [online] Available through : <
https://jaxenter.com/security-measures-protect-iot-devices-150550.html>
6
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




