IT Solutions for Health Care Organizations
VerifiedAdded on 2023/03/29
|16
|4637
|96
AI Summary
This research report discusses the use of IT solutions in health care organizations, focusing on data storage infrastructure, network infrastructure, privacy and security protection mechanisms, policies for operations security, potential risks, and disaster recovery strategies. It highlights the importance of centralized storage management and the need for secure data handling in the healthcare domain.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Group Research Report Template
IT solutions for health care organizations
IT solutions for health care organizations
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

ABSTRACT
Most Grid technology up to now has been designed for high-performance plus high-
throughput data and processing store Health Care. Grid applications targeted mainly at the
Physics neighbourhood initially, but recently many other domains, such as (computational)
Biology, Pharmaceutics, and Healthcare research, have proven improving interest in Main
grid infrastructure. Present Grid middleware, including glide or maybe the Globes Toolkit;
hide many aspects like data distribution and duplication from users of the functional system.
As the complete result, jobs and information are often relocated through several Grid
elements in different management domains in implicit methods without the awareness of the
end-user. Medical applications, nevertheless, have got strict requirements on safe data
handling and store Health Care due to data personal privacy concerns. Therefore, middleware
meant for use Health Care in the healthcare domain should be extended to back up
(application-defined) treatments that define exactly where particular data may be saved, in
what form, and which usually jobs from which users may access this data through what hosts
or management domains.
Keywords:
Healthcare innovation, innovation process
.
2 | P a g e
Most Grid technology up to now has been designed for high-performance plus high-
throughput data and processing store Health Care. Grid applications targeted mainly at the
Physics neighbourhood initially, but recently many other domains, such as (computational)
Biology, Pharmaceutics, and Healthcare research, have proven improving interest in Main
grid infrastructure. Present Grid middleware, including glide or maybe the Globes Toolkit;
hide many aspects like data distribution and duplication from users of the functional system.
As the complete result, jobs and information are often relocated through several Grid
elements in different management domains in implicit methods without the awareness of the
end-user. Medical applications, nevertheless, have got strict requirements on safe data
handling and store Health Care due to data personal privacy concerns. Therefore, middleware
meant for use Health Care in the healthcare domain should be extended to back up
(application-defined) treatments that define exactly where particular data may be saved, in
what form, and which usually jobs from which users may access this data through what hosts
or management domains.
Keywords:
Healthcare innovation, innovation process
.
2 | P a g e

TABLE OF CONTENTS
1. Data Storage Infrastructure .....................................................Page 5
2. Network Infrastructure .............................................................Page 6
3. Privacy and Security Protection Mechanisms ........................Page 7
4. Policies that Ensure Operations Security ................................Page 9
5. Potential Risks ...........................................................................Page 10
6. Disaster Recovery .....................................................................Page 11
3 | P a g e
1. Data Storage Infrastructure .....................................................Page 5
2. Network Infrastructure .............................................................Page 6
3. Privacy and Security Protection Mechanisms ........................Page 7
4. Policies that Ensure Operations Security ................................Page 9
5. Potential Risks ...........................................................................Page 10
6. Disaster Recovery .....................................................................Page 11
3 | P a g e
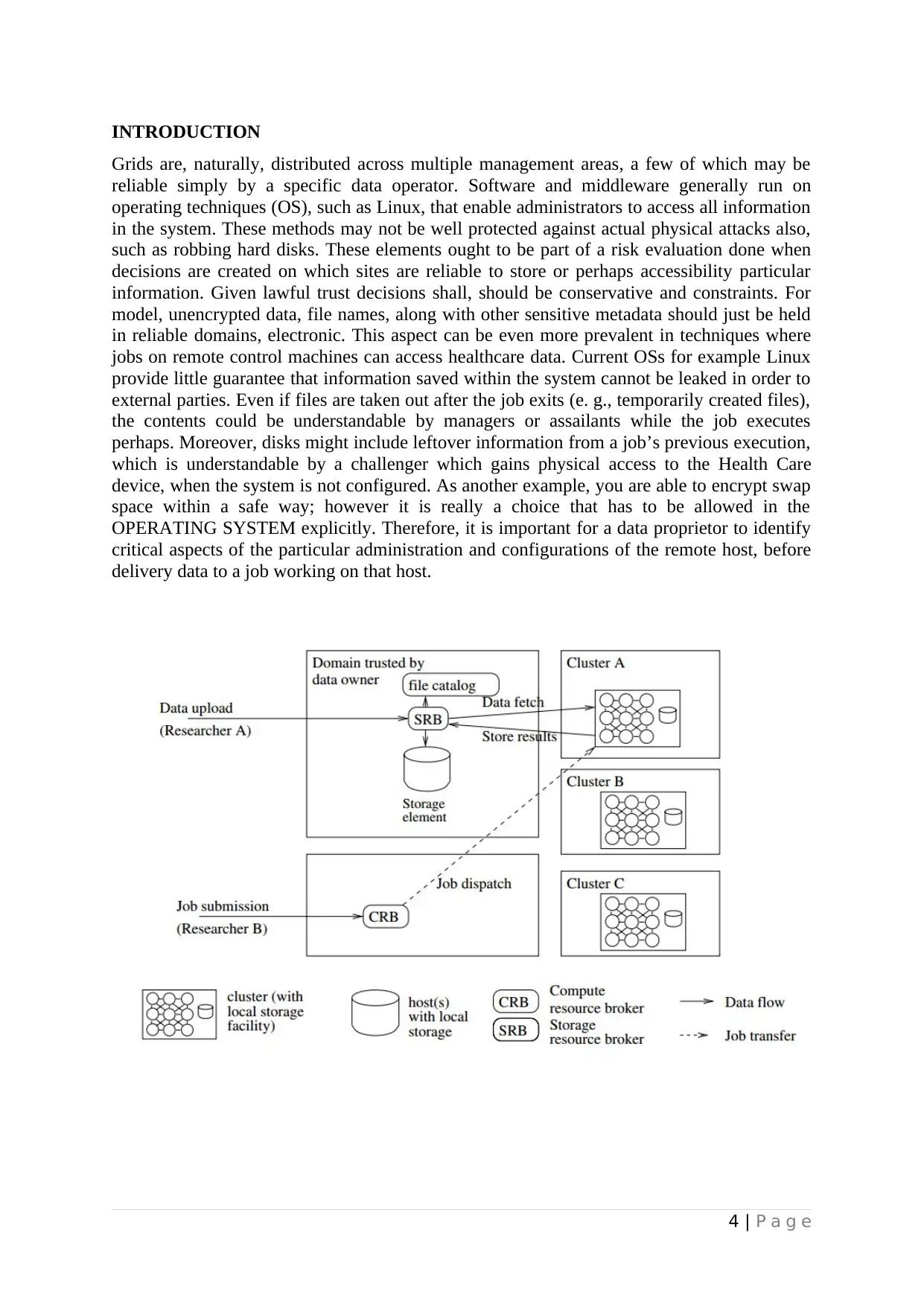
INTRODUCTION
Grids are, naturally, distributed across multiple management areas, a few of which may be
reliable simply by a specific data operator. Software and middleware generally run on
operating techniques (OS), such as Linux, that enable administrators to access all information
in the system. These methods may not be well protected against actual physical attacks also,
such as robbing hard disks. These elements ought to be part of a risk evaluation done when
decisions are created on which sites are reliable to store or perhaps accessibility particular
information. Given lawful trust decisions shall, should be conservative and constraints. For
model, unencrypted data, file names, along with other sensitive metadata should just be held
in reliable domains, electronic. This aspect can be even more prevalent in techniques where
jobs on remote control machines can access healthcare data. Current OSs for example Linux
provide little guarantee that information saved within the system cannot be leaked in order to
external parties. Even if files are taken out after the job exits (e. g., temporarily created files),
the contents could be understandable by managers or assailants while the job executes
perhaps. Moreover, disks might include leftover information from a job’s previous execution,
which is understandable by a challenger which gains physical access to the Health Care
device, when the system is not configured. As another example, you are able to encrypt swap
space within a safe way; however it is really a choice that has to be allowed in the
OPERATING SYSTEM explicitly. Therefore, it is important for a data proprietor to identify
critical aspects of the particular administration and configurations of the remote host, before
delivery data to a job working on that host.
4 | P a g e
Grids are, naturally, distributed across multiple management areas, a few of which may be
reliable simply by a specific data operator. Software and middleware generally run on
operating techniques (OS), such as Linux, that enable administrators to access all information
in the system. These methods may not be well protected against actual physical attacks also,
such as robbing hard disks. These elements ought to be part of a risk evaluation done when
decisions are created on which sites are reliable to store or perhaps accessibility particular
information. Given lawful trust decisions shall, should be conservative and constraints. For
model, unencrypted data, file names, along with other sensitive metadata should just be held
in reliable domains, electronic. This aspect can be even more prevalent in techniques where
jobs on remote control machines can access healthcare data. Current OSs for example Linux
provide little guarantee that information saved within the system cannot be leaked in order to
external parties. Even if files are taken out after the job exits (e. g., temporarily created files),
the contents could be understandable by managers or assailants while the job executes
perhaps. Moreover, disks might include leftover information from a job’s previous execution,
which is understandable by a challenger which gains physical access to the Health Care
device, when the system is not configured. As another example, you are able to encrypt swap
space within a safe way; however it is really a choice that has to be allowed in the
OPERATING SYSTEM explicitly. Therefore, it is important for a data proprietor to identify
critical aspects of the particular administration and configurations of the remote host, before
delivery data to a job working on that host.
4 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Documentation of a data access needs that the connecting job’s proprietor is on the User
ACL, that the host on which the particular connecting job runs is definitely on the Host ACL,
which the attributes in the RHPL match the properties within the connecting host’s HPL.
Paperwork of a data request includes the following steps, assuming GSI host/Proxy certificate
based authentication.
o At connection period, the connecting process (either the particular working job or
even middleware, in case of information pre-fetching) authenticates with the TSRB
utilizing the job’s Proxy resulting in an authenticated, certificate and encrypted
SSL/TLS station.
o The information from the Web proxy certificate is matched against the consumer
ACL to see if accessibility is allowed. If not necessarily, an error is came back that
will not recommend whether the data is available.
MAIN BODY
Data Storage Infrastructure
Space for storage software is often packaged with all the various methods that health care
organizations purchase from different application suppliers, every operational system requires
self-employed maintenance and administration. Most of the time, separate storage systems
are usually controlled by different working systems-Windows®, UNIX, Linux®, AIX®,
Sun™ Solaris™, HP-UX, plus others-and the management features of each storage island
perform only within that island’s particular operating system.
The end result is that a hospital may manage storage in a variety of ways in the server level
using various storage hardware vendors and various backup solutions, which can be
expensive and inefficient. For many hospital wards, storage space demands are growing from
to 70 percent every year up and present data storage systems are certainly not scalable to
meet the needs of exponentially increasing levels of retained data.
With the distribute of advanced medical image resolution technologies to other departments
as well as the growing demand for top quality storage requirements have placed heavy deem,
s on and healthcare IT and system resources. A single x-ray may take up to 12 megabytes
associated with storage, and a 500-bed medical center can easily generate 1 to 2 terabytes of
storage per year within x-rays alone, with backed-up data doubling that necessity.
The particular rapidly growing storage in hospital wards translates to more IT staff sources
needed to manage it, as well as the demand is burdensome because of different especially
storage space systems that individually need to be managed. Without an enterprise-wide
storage space solution, providers are ongoing to purchase and deploy extra storage islands-
each of which usually requires more individual administration even. Implementation of a
solution that will centralizes the management associated with stored data using a solitary
interface would maximize the use of these various storage techniques to accommodate
growing amounts of information, therefore reducing costs for purchasing additional storage
space hardware and relieving needs on IT. Since stored data must be saved regularly, the
dramatically growth in storage specifications translates to challenging demands upon
traditional backup methods. Based on industry estimates, storage space capacity
requirements for healthcare imaging data every 1 . 5 years double, since PACS is used
outside of the radiology department and the technologies becomes more sophisticated.
5 | P a g e
ACL, that the host on which the particular connecting job runs is definitely on the Host ACL,
which the attributes in the RHPL match the properties within the connecting host’s HPL.
Paperwork of a data request includes the following steps, assuming GSI host/Proxy certificate
based authentication.
o At connection period, the connecting process (either the particular working job or
even middleware, in case of information pre-fetching) authenticates with the TSRB
utilizing the job’s Proxy resulting in an authenticated, certificate and encrypted
SSL/TLS station.
o The information from the Web proxy certificate is matched against the consumer
ACL to see if accessibility is allowed. If not necessarily, an error is came back that
will not recommend whether the data is available.
MAIN BODY
Data Storage Infrastructure
Space for storage software is often packaged with all the various methods that health care
organizations purchase from different application suppliers, every operational system requires
self-employed maintenance and administration. Most of the time, separate storage systems
are usually controlled by different working systems-Windows®, UNIX, Linux®, AIX®,
Sun™ Solaris™, HP-UX, plus others-and the management features of each storage island
perform only within that island’s particular operating system.
The end result is that a hospital may manage storage in a variety of ways in the server level
using various storage hardware vendors and various backup solutions, which can be
expensive and inefficient. For many hospital wards, storage space demands are growing from
to 70 percent every year up and present data storage systems are certainly not scalable to
meet the needs of exponentially increasing levels of retained data.
With the distribute of advanced medical image resolution technologies to other departments
as well as the growing demand for top quality storage requirements have placed heavy deem,
s on and healthcare IT and system resources. A single x-ray may take up to 12 megabytes
associated with storage, and a 500-bed medical center can easily generate 1 to 2 terabytes of
storage per year within x-rays alone, with backed-up data doubling that necessity.
The particular rapidly growing storage in hospital wards translates to more IT staff sources
needed to manage it, as well as the demand is burdensome because of different especially
storage space systems that individually need to be managed. Without an enterprise-wide
storage space solution, providers are ongoing to purchase and deploy extra storage islands-
each of which usually requires more individual administration even. Implementation of a
solution that will centralizes the management associated with stored data using a solitary
interface would maximize the use of these various storage techniques to accommodate
growing amounts of information, therefore reducing costs for purchasing additional storage
space hardware and relieving needs on IT. Since stored data must be saved regularly, the
dramatically growth in storage specifications translates to challenging demands upon
traditional backup methods. Based on industry estimates, storage space capacity
requirements for healthcare imaging data every 1 . 5 years double, since PACS is used
outside of the radiology department and the technologies becomes more sophisticated.
5 | P a g e
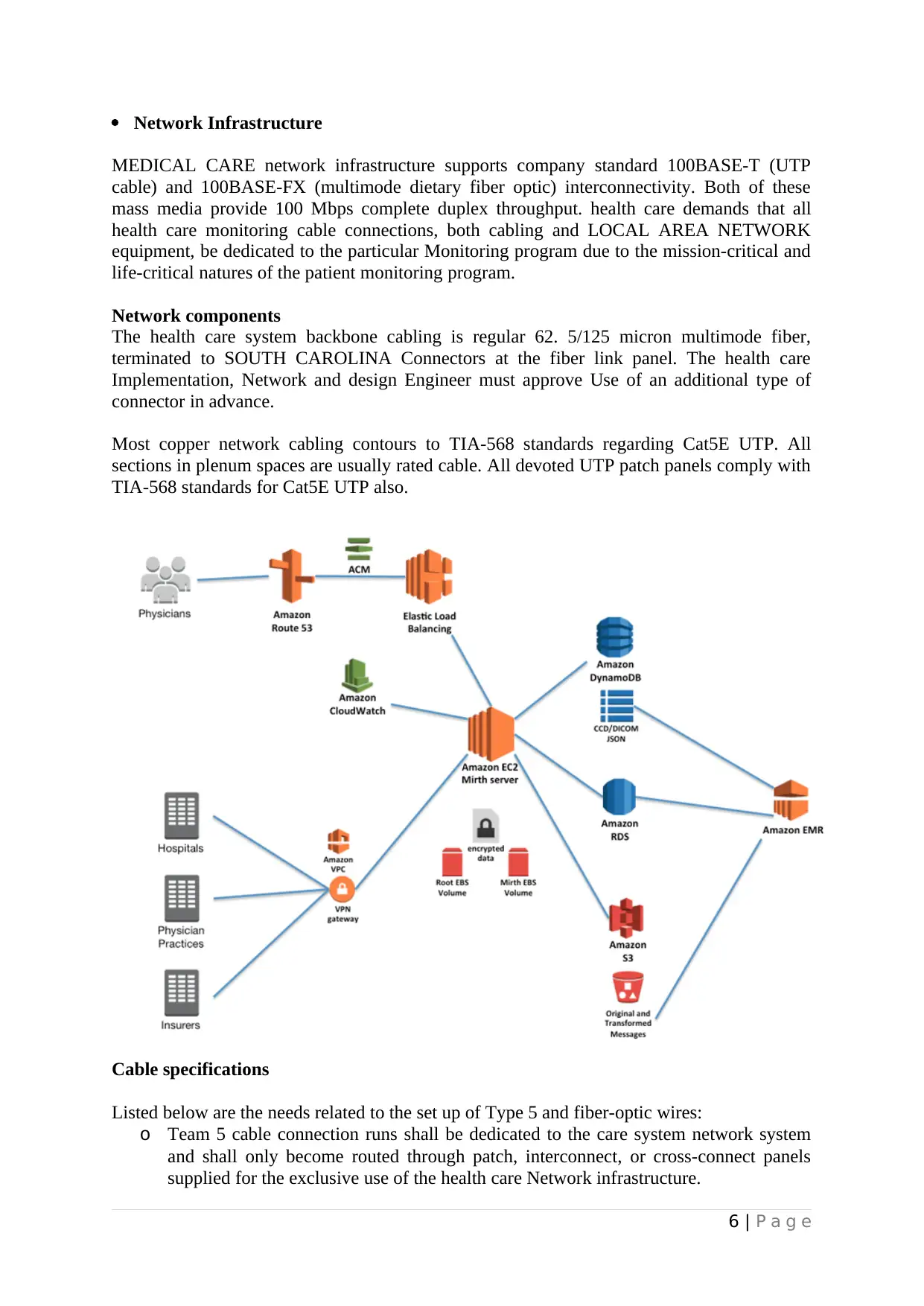
Network Infrastructure
MEDICAL CARE network infrastructure supports company standard 100BASE-T (UTP
cable) and 100BASE-FX (multimode dietary fiber optic) interconnectivity. Both of these
mass media provide 100 Mbps complete duplex throughput. health care demands that all
health care monitoring cable connections, both cabling and LOCAL AREA NETWORK
equipment, be dedicated to the particular Monitoring program due to the mission-critical and
life-critical natures of the patient monitoring program.
Network components
The health care system backbone cabling is regular 62. 5/125 micron multimode fiber,
terminated to SOUTH CAROLINA Connectors at the fiber link panel. The health care
Implementation, Network and design Engineer must approve Use of an additional type of
connector in advance.
Most copper network cabling contours to TIA-568 standards regarding Cat5E UTP. All
sections in plenum spaces are usually rated cable. All devoted UTP patch panels comply with
TIA-568 standards for Cat5E UTP also.
Cable specifications
Listed below are the needs related to the set up of Type 5 and fiber-optic wires:
o Team 5 cable connection runs shall be dedicated to the care system network system
and shall only become routed through patch, interconnect, or cross-connect panels
supplied for the exclusive use of the health care Network infrastructure.
6 | P a g e
MEDICAL CARE network infrastructure supports company standard 100BASE-T (UTP
cable) and 100BASE-FX (multimode dietary fiber optic) interconnectivity. Both of these
mass media provide 100 Mbps complete duplex throughput. health care demands that all
health care monitoring cable connections, both cabling and LOCAL AREA NETWORK
equipment, be dedicated to the particular Monitoring program due to the mission-critical and
life-critical natures of the patient monitoring program.
Network components
The health care system backbone cabling is regular 62. 5/125 micron multimode fiber,
terminated to SOUTH CAROLINA Connectors at the fiber link panel. The health care
Implementation, Network and design Engineer must approve Use of an additional type of
connector in advance.
Most copper network cabling contours to TIA-568 standards regarding Cat5E UTP. All
sections in plenum spaces are usually rated cable. All devoted UTP patch panels comply with
TIA-568 standards for Cat5E UTP also.
Cable specifications
Listed below are the needs related to the set up of Type 5 and fiber-optic wires:
o Team 5 cable connection runs shall be dedicated to the care system network system
and shall only become routed through patch, interconnect, or cross-connect panels
supplied for the exclusive use of the health care Network infrastructure.
6 | P a g e

o For social networking designed by wellbeing care, punch-down panels shall be
labeled for each the summary sheet from the Interconnect matrix in the medical care
design pack health Care.
o Category 5 cable operates to workstation locations will be terminated with industry-
standard RJ-45 wall Jacks supplied by the particular cable contractor.
o
Remote control link (VPN)
Certain health care products are equipped with incite exec, an electronic digital services
interface that allows remote control access to The well being treatment Healthcare Support
Center with a secure Internet connection to allow On-Demand or Proactive Electronic
Services.
o Sufficient space shall be provided within designated equipment closets to
accommodate HEALTH CARE infrastructure elements.
o Closets shall be made obtainable for the HEALTH CARE installation group during all
phases associated with implementation for the Purposes of setting up, integrating,
testing, and fine-tuning the CARESCAPE system.
Laser light printers
Centered on the kind of equipment purchased, network laser printers may be set up included
in the Monitoring system. Please send to product documentation to get specific setup
procedures plus supported printer Models.
Privacy and Security Protection Mechanisms
Privacy is important for the firm and your customers. Carried on trust in your business
methods, products and secure handling of the clients’ unique information affects your
profitability. Your personal privacy plan is a pledge for your customers that you will use plus
protect their information within methods that they expect which adhere to your legal
commitments.
Maybe your personal privacy policy ought to address the following sorts of data:
o Personally Recognizable Information: Often referred to as PII, this particular given
information includes this kind of aspects as first plus last names, business or even
home addresses, email addresses, credit score bank and card accounts taxpayer
identification numbers, Social Security numbers, numbers and patient numbers.
o Personal Wellness Details: Whether you’re a health care provider with lots of delicate
patient information or even you just manage wellbeing or healthcare information for a
small number of workers, it’s vital that you protect that will details.
o Customer information: This particular contains payment information like credit or
debit card numbers and confirmation codes, shipping and payment addresses, email
addresses, buying preferences, phone numbers, purchasing history and shopping
behavior.
Create layers associated with defense
7 | P a g e
labeled for each the summary sheet from the Interconnect matrix in the medical care
design pack health Care.
o Category 5 cable operates to workstation locations will be terminated with industry-
standard RJ-45 wall Jacks supplied by the particular cable contractor.
o
Remote control link (VPN)
Certain health care products are equipped with incite exec, an electronic digital services
interface that allows remote control access to The well being treatment Healthcare Support
Center with a secure Internet connection to allow On-Demand or Proactive Electronic
Services.
o Sufficient space shall be provided within designated equipment closets to
accommodate HEALTH CARE infrastructure elements.
o Closets shall be made obtainable for the HEALTH CARE installation group during all
phases associated with implementation for the Purposes of setting up, integrating,
testing, and fine-tuning the CARESCAPE system.
Laser light printers
Centered on the kind of equipment purchased, network laser printers may be set up included
in the Monitoring system. Please send to product documentation to get specific setup
procedures plus supported printer Models.
Privacy and Security Protection Mechanisms
Privacy is important for the firm and your customers. Carried on trust in your business
methods, products and secure handling of the clients’ unique information affects your
profitability. Your personal privacy plan is a pledge for your customers that you will use plus
protect their information within methods that they expect which adhere to your legal
commitments.
Maybe your personal privacy policy ought to address the following sorts of data:
o Personally Recognizable Information: Often referred to as PII, this particular given
information includes this kind of aspects as first plus last names, business or even
home addresses, email addresses, credit score bank and card accounts taxpayer
identification numbers, Social Security numbers, numbers and patient numbers.
o Personal Wellness Details: Whether you’re a health care provider with lots of delicate
patient information or even you just manage wellbeing or healthcare information for a
small number of workers, it’s vital that you protect that will details.
o Customer information: This particular contains payment information like credit or
debit card numbers and confirmation codes, shipping and payment addresses, email
addresses, buying preferences, phone numbers, purchasing history and shopping
behavior.
Create layers associated with defense
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Protecting data, similar to other security challenge, is all about creating layers of safety. The
idea of layering security is easy: You cannot and should not depend on just one security
mechanism -- such as a security password - to guard something sensitive.
Inventory data
We all mentioned before the need to conduct the details inventory so you possess a complete
picture of all the information your business possesses or regulates. It’s essential to get a full
inventory, so you don’t neglect some sensitive data that may be exposed.
Identify and shield sensitive and precious data
Data category is probably the most important steps in data safety. Not all data is created
identical, and few businesses possess the time or resources to give maximum security to all
their particular information.
Control access to data
Regardless of what kind of data you have, you should control access to it. The greater
sensitive the data, the more restricted the access. As a general rule, entry to data should be on
a need-to-know time period. Only individuals who possess a specific need to access particular
data should be allowed to do this.
Secure data
Along with administrative safeguards that figure out that has access to what details, technical
safeguards are essential. Both primary safeguards for information are security passwords and
encryption. Passwords implemented to protect your own most sensitive data ought to be the
strongest they can reasonably become.
Some recognized ways of two-factor acknowledgement include:
o Something the requestor independently knows as a secret, like a password or the
FLAG.
o Something the requestor uniquely possesses, such as a passport, physical token or
IDENTIFICATION card.
o Something the particular requestor can uniquely supply as biometric data, like a
fingerprint or face angles.
Back data up
Just like critical as protecting your computer data is backing it up. If you think your data is
stolen simply by thieves or hackers, or even erased accidentally simply by an employee, you
shall a minimum of have the particular copy in order to fall back on. Place a plan in place that
will recognizes what data is usually backed up and how; how usually it’s backed up; who is
accountable for creating backups; where and exactly how the backups are saved; and who has
access to these backup copies.
Plan for information loss or maybe theft
Each continuing firm has to policy for the unexpected, and that includes losing or maybe theft
of information from your business. Not only may theft and even lack of data hurt your
business, client and brand confidence, additionally, it may expose you to the often-costly
8 | P a g e
idea of layering security is easy: You cannot and should not depend on just one security
mechanism -- such as a security password - to guard something sensitive.
Inventory data
We all mentioned before the need to conduct the details inventory so you possess a complete
picture of all the information your business possesses or regulates. It’s essential to get a full
inventory, so you don’t neglect some sensitive data that may be exposed.
Identify and shield sensitive and precious data
Data category is probably the most important steps in data safety. Not all data is created
identical, and few businesses possess the time or resources to give maximum security to all
their particular information.
Control access to data
Regardless of what kind of data you have, you should control access to it. The greater
sensitive the data, the more restricted the access. As a general rule, entry to data should be on
a need-to-know time period. Only individuals who possess a specific need to access particular
data should be allowed to do this.
Secure data
Along with administrative safeguards that figure out that has access to what details, technical
safeguards are essential. Both primary safeguards for information are security passwords and
encryption. Passwords implemented to protect your own most sensitive data ought to be the
strongest they can reasonably become.
Some recognized ways of two-factor acknowledgement include:
o Something the requestor independently knows as a secret, like a password or the
FLAG.
o Something the requestor uniquely possesses, such as a passport, physical token or
IDENTIFICATION card.
o Something the particular requestor can uniquely supply as biometric data, like a
fingerprint or face angles.
Back data up
Just like critical as protecting your computer data is backing it up. If you think your data is
stolen simply by thieves or hackers, or even erased accidentally simply by an employee, you
shall a minimum of have the particular copy in order to fall back on. Place a plan in place that
will recognizes what data is usually backed up and how; how usually it’s backed up; who is
accountable for creating backups; where and exactly how the backups are saved; and who has
access to these backup copies.
Plan for information loss or maybe theft
Each continuing firm has to policy for the unexpected, and that includes losing or maybe theft
of information from your business. Not only may theft and even lack of data hurt your
business, client and brand confidence, additionally, it may expose you to the often-costly
8 | P a g e

state and federal regulations that protect data protection and personal privacy. Data loss can
in addition expose businesses to substantial litigation risk.
Appropriate Entry and Audit Trail Overseeing
All organizations have an responsibility to keep information ‘safe plus secure’ and have
appropriate procedures in place to prevent unauthorized access to, or even alteration, damage
or disclosure of, the information and against their unintended reduction or destruction” within
conformity with sections 2(1)(d) and 2C of the Information Protection Acts 1988 and 2003.
Policies that Ensure Operations Security
PLAN, PROCEDURES, SUGGESTIONS
o OMES IS provides, among many other responsibilities, the particular mandate to
establish minimum necessary standards for information protection and internal
controls along with contingency planning and problem recovery.
o In reference to the particular obligations above stated the particular Statute reads as
follows: "Such standards shall, upon possession, be the minimum needs appropriate to
all companies. These requirements will be compatible with the criteria established for
the Oklahoma Got Telecommunications Network.
AUDIENCE
The Policy, techniques, guidelines and best practices are usually for distribution to all
Condition agencies through their particular Security Representative who will after that be
responsible for communicating the details to mention employees as well as contractors or
even extra entities whose placement obligations include the creation, maintenance, or access
of Condition information residing on any computer program or program.
DETAILS CONFIDENTIALITY
The overriding premise is that all provided info hosted or produced by simply a State Agency
is usually property of the State. As a result, this information will be utilized for performance
of position associated duties solely. All of agency staff must be recommended to:
(A) Keep security passwords personal,
(B) Avoid maintaining the particular paper record associated with account details, unless this
can be saved securely,
(C) Change security passwords whenever there is any sign of possible system or even
password compromise,
(D) Choose quality security passwords with a minimal size of eight heroes which are:
(I) easy to keep in mind,
(ii) not based on anything at all somebody else could easily imagine and even obtain
using individual related information, e. h. names, telephone numbers plus dates of
birth and so forth,
(Iii) Free of consecutive similar characters or all-numeric or even all alphabetical
groups,
(E) Modify passwords at regular periods (passwords for privileged balances should be
changed more frequently compared to normal passwords),
(F) Prevent reusing as well as cycling previous passwords
9 | P a g e
in addition expose businesses to substantial litigation risk.
Appropriate Entry and Audit Trail Overseeing
All organizations have an responsibility to keep information ‘safe plus secure’ and have
appropriate procedures in place to prevent unauthorized access to, or even alteration, damage
or disclosure of, the information and against their unintended reduction or destruction” within
conformity with sections 2(1)(d) and 2C of the Information Protection Acts 1988 and 2003.
Policies that Ensure Operations Security
PLAN, PROCEDURES, SUGGESTIONS
o OMES IS provides, among many other responsibilities, the particular mandate to
establish minimum necessary standards for information protection and internal
controls along with contingency planning and problem recovery.
o In reference to the particular obligations above stated the particular Statute reads as
follows: "Such standards shall, upon possession, be the minimum needs appropriate to
all companies. These requirements will be compatible with the criteria established for
the Oklahoma Got Telecommunications Network.
AUDIENCE
The Policy, techniques, guidelines and best practices are usually for distribution to all
Condition agencies through their particular Security Representative who will after that be
responsible for communicating the details to mention employees as well as contractors or
even extra entities whose placement obligations include the creation, maintenance, or access
of Condition information residing on any computer program or program.
DETAILS CONFIDENTIALITY
The overriding premise is that all provided info hosted or produced by simply a State Agency
is usually property of the State. As a result, this information will be utilized for performance
of position associated duties solely. All of agency staff must be recommended to:
(A) Keep security passwords personal,
(B) Avoid maintaining the particular paper record associated with account details, unless this
can be saved securely,
(C) Change security passwords whenever there is any sign of possible system or even
password compromise,
(D) Choose quality security passwords with a minimal size of eight heroes which are:
(I) easy to keep in mind,
(ii) not based on anything at all somebody else could easily imagine and even obtain
using individual related information, e. h. names, telephone numbers plus dates of
birth and so forth,
(Iii) Free of consecutive similar characters or all-numeric or even all alphabetical
groups,
(E) Modify passwords at regular periods (passwords for privileged balances should be
changed more frequently compared to normal passwords),
(F) Prevent reusing as well as cycling previous passwords
9 | P a g e

INFO SECURITY
The State Company Director whose Agency gathers and keeps (owns) the data is responsible
for interpreting all privacy restrictions imposed by simply laws and regulations and statutes
as well as creating info classification and granting details access. System limitations may
prevent all of the following procedures to become implemented, however, when feasible,
these rules apply:
o Security passwords will be required to be considered a minimum of 8 characters
lengthy, which has at least one (1) numeric character.
o Security passwords will certainly expire in the more 90 instances.
o Security passwords will be deactivated if not employed for a period of 60 days.
o Account details for a given consumer should not be used again in a twelve thirty day’s
period.
INFORMATION ACCESSIBILITY
o Information availability will be the responsibility of the website hosting Condition
Agency. Access to information is going to be granted as needed to all of State
Agencies to support their own required functions, timelines and processes.
o Required accessibility will vary with normal series of use (I. e. info is used throughout
the period continuously, but is only accessed throughout the evening by a backup
procedure periodically, becomes archival following the backup is complete).
SECURITY PROGRAM ADMINISTRATION
o Managing information safety within the State can be split into three components:
o Central organization (OMES IS) is responsible for direction and command in all
factors of information safety.
o Agencies that sponsor info services are responsible for producing system specific
suggestions plus policies to complement, but not confront those issued by the main
organization.
o All institutions are required to develop procedures particular to their information and
procedure flows to protect the sincerity of information and guard towards misuse or
decrease. This is simply not limited to, but includes personal computer based
information systems.
AWARENESS/TRAINING
o Awareness is not really training. The purpose of awareness delivering presentations
are basically to focus interest on security and are meant to allow individuals to
recognize THIS security concerns and react accordingly. Attention relies on achieving
broad audiences, whereas education is more formal, having the particular goal of
building info plus skills to help work performance.
o Effective THIS security awareness delivering presentations should be designed.
Interest presentations should be on-going, creative and motivational, with the
objective of focusing interest so that the learning will be included into conscious
decision-making.
10 | P a g e
The State Company Director whose Agency gathers and keeps (owns) the data is responsible
for interpreting all privacy restrictions imposed by simply laws and regulations and statutes
as well as creating info classification and granting details access. System limitations may
prevent all of the following procedures to become implemented, however, when feasible,
these rules apply:
o Security passwords will be required to be considered a minimum of 8 characters
lengthy, which has at least one (1) numeric character.
o Security passwords will certainly expire in the more 90 instances.
o Security passwords will be deactivated if not employed for a period of 60 days.
o Account details for a given consumer should not be used again in a twelve thirty day’s
period.
INFORMATION ACCESSIBILITY
o Information availability will be the responsibility of the website hosting Condition
Agency. Access to information is going to be granted as needed to all of State
Agencies to support their own required functions, timelines and processes.
o Required accessibility will vary with normal series of use (I. e. info is used throughout
the period continuously, but is only accessed throughout the evening by a backup
procedure periodically, becomes archival following the backup is complete).
SECURITY PROGRAM ADMINISTRATION
o Managing information safety within the State can be split into three components:
o Central organization (OMES IS) is responsible for direction and command in all
factors of information safety.
o Agencies that sponsor info services are responsible for producing system specific
suggestions plus policies to complement, but not confront those issued by the main
organization.
o All institutions are required to develop procedures particular to their information and
procedure flows to protect the sincerity of information and guard towards misuse or
decrease. This is simply not limited to, but includes personal computer based
information systems.
AWARENESS/TRAINING
o Awareness is not really training. The purpose of awareness delivering presentations
are basically to focus interest on security and are meant to allow individuals to
recognize THIS security concerns and react accordingly. Attention relies on achieving
broad audiences, whereas education is more formal, having the particular goal of
building info plus skills to help work performance.
o Effective THIS security awareness delivering presentations should be designed.
Interest presentations should be on-going, creative and motivational, with the
objective of focusing interest so that the learning will be included into conscious
decision-making.
10 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Potential Risks
The following activities may help you monitor the particular control measures risks which
have implemented and ensure that they stay effective:
o Accountability regarding health and safety - Accountability ought to be clearly
allocated to ensure methods are implemented and managed. Managers and supervisors
must be provided with the authority plus resources to implement and keep control
measures effectively.
o Maintenance of plant and devices - This will involve normal examination and testing,
restoration or even replacement of damaged or even worn equipment and flower. It
includes checking that any kind of control measures are ideal for the time period and
character of used correctly, work and are set up.
o Up dated competency and training: Control measures, particularly reduced level
controls, depend on all of employees and supervisors getting the appropriate
competencies to do the work safely. Training should be offered to maintain
competencies and to assure new workers are capable of functioning correctly.
o Up-to-date risk details - Information about risks, such as substances and herb, may be
up to date by producers and companies and should become checked to make sure
controls continue to be relevant. New technology may offer more effective solutions
than had been available previously. Changes in order to operating conditions or the
method activities are transported out there may also mean that control actions need to
be updated.
o Normal review and visit -- Control measures are more efficient where there is regular
overview of work procedures and visit with your workers and their particular
representatives.
Disaster Recovery
In any recovery plan you will have a wide array of disaster possibilities plus recovery
procedures to consider. To slice the problem down to size, consequently, preliminary
assumptions are created as guidelines. For the recuperation effort to be successful, all
included personnel are required to assure that these types of presumptions are current and
appropriate.
The Disaster Recovery Program is based on the following assumptions:
o Administrators will keep all employees affected by this plan aware of the current
procedures and procedures
o All personnel impacted simply by this plan are accountable for understanding their
component under a disaster situation
o This plan shall be continually managed.
o The recovery procedure documented in the plan must be tested annually
o Most personnel must respond plus effectively during the recovery procedure quickly
11 | P a g e
The following activities may help you monitor the particular control measures risks which
have implemented and ensure that they stay effective:
o Accountability regarding health and safety - Accountability ought to be clearly
allocated to ensure methods are implemented and managed. Managers and supervisors
must be provided with the authority plus resources to implement and keep control
measures effectively.
o Maintenance of plant and devices - This will involve normal examination and testing,
restoration or even replacement of damaged or even worn equipment and flower. It
includes checking that any kind of control measures are ideal for the time period and
character of used correctly, work and are set up.
o Up dated competency and training: Control measures, particularly reduced level
controls, depend on all of employees and supervisors getting the appropriate
competencies to do the work safely. Training should be offered to maintain
competencies and to assure new workers are capable of functioning correctly.
o Up-to-date risk details - Information about risks, such as substances and herb, may be
up to date by producers and companies and should become checked to make sure
controls continue to be relevant. New technology may offer more effective solutions
than had been available previously. Changes in order to operating conditions or the
method activities are transported out there may also mean that control actions need to
be updated.
o Normal review and visit -- Control measures are more efficient where there is regular
overview of work procedures and visit with your workers and their particular
representatives.
Disaster Recovery
In any recovery plan you will have a wide array of disaster possibilities plus recovery
procedures to consider. To slice the problem down to size, consequently, preliminary
assumptions are created as guidelines. For the recuperation effort to be successful, all
included personnel are required to assure that these types of presumptions are current and
appropriate.
The Disaster Recovery Program is based on the following assumptions:
o Administrators will keep all employees affected by this plan aware of the current
procedures and procedures
o All personnel impacted simply by this plan are accountable for understanding their
component under a disaster situation
o This plan shall be continually managed.
o The recovery procedure documented in the plan must be tested annually
o Most personnel must respond plus effectively during the recovery procedure quickly
11 | P a g e

Plans and Objectives
The following organizational goals could be pursued.
o Assignment associated with Internal Staff for Preparing and Training
o Obtaining the Interest and support of Administrators
o Getting Co-operation from the User Departments
o Concerning all Related Sections each internal and external
o Establishing Priorities for the Planning Hard work
o Taking a look at the Plan throughout The Development
Disaster Recuperation Program
All departments and types should develop, workout and maintain recovery plans for your
business functions and digesting operations as necessary for the particular protection of
University/Department details and firm activities.
Types of tragedy to consider
o Natural problems: Floods, Storms, Fires, Earthquakes, Lightning, Reduction of a
Storage Pc or Drive Program, etc.
o Man-made unfortunate occurrences: Fire, Transportation Accidents, Chemical
substance Situations, Sabotage or Willful Damage, Bomb Threats, Burst open Pipes,
Electrical Outage, Lack of Environmental Controls, etc .
o Political disasters: Riots, General public Demonstrations, Civil Disturbances, and so
forth
o Electronic Warfare: Cyber-terrorist, Cyber terrorism, Computer Bacterial infections,
Intrusion Detection, Denial associated with Service, etc.
Recovery Group Plans
Separate Coordination groups responsible for all actions in your department that will manage
the particular healing process. This large of teams enables the particular accounts activation
of any or all of the department’s employees and/or programs so that the recovery process may
scale appropriately based on the necessity.
The Disaster Recovery Plan may require updates when problems or changes consist of some
or any of the subsequent:
- Mid-Range and Mainframe Damage Recovery Test outcomes
- New critical apps or perhaps critical customers
: Increased application complexity
-- New equipment acquisitions
: Changes to:
- Equipment
- Software
- System
- Applications
12 | P a g e
The following organizational goals could be pursued.
o Assignment associated with Internal Staff for Preparing and Training
o Obtaining the Interest and support of Administrators
o Getting Co-operation from the User Departments
o Concerning all Related Sections each internal and external
o Establishing Priorities for the Planning Hard work
o Taking a look at the Plan throughout The Development
Disaster Recuperation Program
All departments and types should develop, workout and maintain recovery plans for your
business functions and digesting operations as necessary for the particular protection of
University/Department details and firm activities.
Types of tragedy to consider
o Natural problems: Floods, Storms, Fires, Earthquakes, Lightning, Reduction of a
Storage Pc or Drive Program, etc.
o Man-made unfortunate occurrences: Fire, Transportation Accidents, Chemical
substance Situations, Sabotage or Willful Damage, Bomb Threats, Burst open Pipes,
Electrical Outage, Lack of Environmental Controls, etc .
o Political disasters: Riots, General public Demonstrations, Civil Disturbances, and so
forth
o Electronic Warfare: Cyber-terrorist, Cyber terrorism, Computer Bacterial infections,
Intrusion Detection, Denial associated with Service, etc.
Recovery Group Plans
Separate Coordination groups responsible for all actions in your department that will manage
the particular healing process. This large of teams enables the particular accounts activation
of any or all of the department’s employees and/or programs so that the recovery process may
scale appropriately based on the necessity.
The Disaster Recovery Plan may require updates when problems or changes consist of some
or any of the subsequent:
- Mid-Range and Mainframe Damage Recovery Test outcomes
- New critical apps or perhaps critical customers
: Increased application complexity
-- New equipment acquisitions
: Changes to:
- Equipment
- Software
- System
- Applications
12 | P a g e

- Information
The eight R’s associated with the particular successful recovery program
o Reason for planning
o Recognition
o Reaction
o Recovery
o Restoration
o Return To Normal
o Relaxation and Relax
o Re-evaluate and Re-document
o
Failure Recuperation Plan is a great on-going process and should be executed with the
following points in your mind:
o Disaster Scenarios
o Procedures to recover from a catastrophe are written for the majority of severe
occurrence; for factors like formalizing the plan the following had been considered.
CONCLUSION
Organization’s information highlights and program the importance of applying a broad
method of data security none, encompassing both technical and protection-technical options.
Understanding the vast array of risks is the first step in ensuring adequate protection of
delicate data. All networks are usually vulnerable to cyber security hazards. An extensive
data protection program is vital for mitigating these dangers and preventing an information
breach. A holistic approach to information security begins with comprehending the network,
the particular architecture, consumer population, and mission specifications. For example,
security dangers for networks with huge user populations and systems connected to the
internet are specifically high. Once the risks are actually organizational and assessed safety
policies specified, a security structures should be designed and the particular security plan
implemented. Continuous implementation of the basic safety strategy will reduce
susceptibility in order to cyber threats and raise the overall safety of an organization’s
information.
Reference
U.S. safe harbor framework. http://www.export.gov/safeharbor/.
Dutch ministry of health, welfare and sport - wet op degeneeskundige ehandelingsovereenkomst
(wgbo), 1994. http://www.hulpgids.nl/wetten/wgbo.htm.
R. Alfieri et al. Voms, an authorization system for virtual organizations. In European Across Grids
Conf., volume 2970 of LNCS, pages 33–40. Springer, 2004.
U. Congress. Health insurance portability and accountability act, 1996.
S. Erberich et al. Globus medicus - federation of dicom medical imaging devices into healthcare grids.
Studies in Health Technology and Informatics, 126:269–278, 2007.
13 | P a g e
The eight R’s associated with the particular successful recovery program
o Reason for planning
o Recognition
o Reaction
o Recovery
o Restoration
o Return To Normal
o Relaxation and Relax
o Re-evaluate and Re-document
o
Failure Recuperation Plan is a great on-going process and should be executed with the
following points in your mind:
o Disaster Scenarios
o Procedures to recover from a catastrophe are written for the majority of severe
occurrence; for factors like formalizing the plan the following had been considered.
CONCLUSION
Organization’s information highlights and program the importance of applying a broad
method of data security none, encompassing both technical and protection-technical options.
Understanding the vast array of risks is the first step in ensuring adequate protection of
delicate data. All networks are usually vulnerable to cyber security hazards. An extensive
data protection program is vital for mitigating these dangers and preventing an information
breach. A holistic approach to information security begins with comprehending the network,
the particular architecture, consumer population, and mission specifications. For example,
security dangers for networks with huge user populations and systems connected to the
internet are specifically high. Once the risks are actually organizational and assessed safety
policies specified, a security structures should be designed and the particular security plan
implemented. Continuous implementation of the basic safety strategy will reduce
susceptibility in order to cyber threats and raise the overall safety of an organization’s
information.
Reference
U.S. safe harbor framework. http://www.export.gov/safeharbor/.
Dutch ministry of health, welfare and sport - wet op degeneeskundige ehandelingsovereenkomst
(wgbo), 1994. http://www.hulpgids.nl/wetten/wgbo.htm.
R. Alfieri et al. Voms, an authorization system for virtual organizations. In European Across Grids
Conf., volume 2970 of LNCS, pages 33–40. Springer, 2004.
U. Congress. Health insurance portability and accountability act, 1996.
S. Erberich et al. Globus medicus - federation of dicom medical imaging devices into healthcare grids.
Studies in Health Technology and Informatics, 126:269–278, 2007.
13 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

S. Fischer-Huebner. IT-security and privacy: design and use of privacy-enhancing security
mechanisms. Springer-Verlag, New York, NY, USA, 2001.
I. Foster, C. Kesselman, G. Tsudik, and S. Tuecke. A security architecture for computational grids.
5th ACM Conf. on Computer and Communication Security, pages 83–92, November 2-5 1998.
I. Foster, C. Kesselman, and S. Tuecke. The anatomy of the grid: Enabling scalable virtual
organizations. Int’l J. Supercomputer Applications, 15(3), 2001.
14 | P a g e
mechanisms. Springer-Verlag, New York, NY, USA, 2001.
I. Foster, C. Kesselman, G. Tsudik, and S. Tuecke. A security architecture for computational grids.
5th ACM Conf. on Computer and Communication Security, pages 83–92, November 2-5 1998.
I. Foster, C. Kesselman, and S. Tuecke. The anatomy of the grid: Enabling scalable virtual
organizations. Int’l J. Supercomputer Applications, 15(3), 2001.
14 | P a g e

REFERENCES
References should refer to a list at the end of the article, ordered alphabetically by first
author, and referenced in the text by names and year (i.e. Anderson 1992; Whitman &
Mattord 2009). You need to include the location of conferences and the exact date. Example
references are provided using the References style.
Anderson, R. 1992, ‘Social impacts of computing: Codes of professional ethics’, Social
Science Computing Review, vol.10, iss.2, pp. 453-469.
Whitman, M.and Mattord, H. 2009, Principles of Information Security 3rd Edition, Course
Technology, Canada.
15 | P a g e
References should refer to a list at the end of the article, ordered alphabetically by first
author, and referenced in the text by names and year (i.e. Anderson 1992; Whitman &
Mattord 2009). You need to include the location of conferences and the exact date. Example
references are provided using the References style.
Anderson, R. 1992, ‘Social impacts of computing: Codes of professional ethics’, Social
Science Computing Review, vol.10, iss.2, pp. 453-469.
Whitman, M.and Mattord, H. 2009, Principles of Information Security 3rd Edition, Course
Technology, Canada.
15 | P a g e
APPENDIXES
Allocation Roles and Tasks
Our group hastwo highly qualified ICT professionals and are competent in
handling ICT scoping report. In order to keep this report run smoothly,
specific task were allocated to each member.
Each member has responsibility to complete his/her tasks that has being
allocated. In this case, we used RACI chart to show allocation tasks and
responsibility of each member.
Tasks
Searching about the topic
Abstract
Introduction
Data storage infrastructure
Network infrastructure
Privacy and security protection
mechanisms
Policies that ensure operations
security
Potential risks
Disaster recovery
Conclusion
References
Report editing
RACI
R Responsible
A Assisted
C Consulted
I Informed
16 | P a g e
Allocation Roles and Tasks
Our group hastwo highly qualified ICT professionals and are competent in
handling ICT scoping report. In order to keep this report run smoothly,
specific task were allocated to each member.
Each member has responsibility to complete his/her tasks that has being
allocated. In this case, we used RACI chart to show allocation tasks and
responsibility of each member.
Tasks
Searching about the topic
Abstract
Introduction
Data storage infrastructure
Network infrastructure
Privacy and security protection
mechanisms
Policies that ensure operations
security
Potential risks
Disaster recovery
Conclusion
References
Report editing
RACI
R Responsible
A Assisted
C Consulted
I Informed
16 | P a g e
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





