Comparative Analysis of CDN Security: New Model vs. Old Model
VerifiedAdded on 2020/03/16
|3
|670
|41
Report
AI Summary
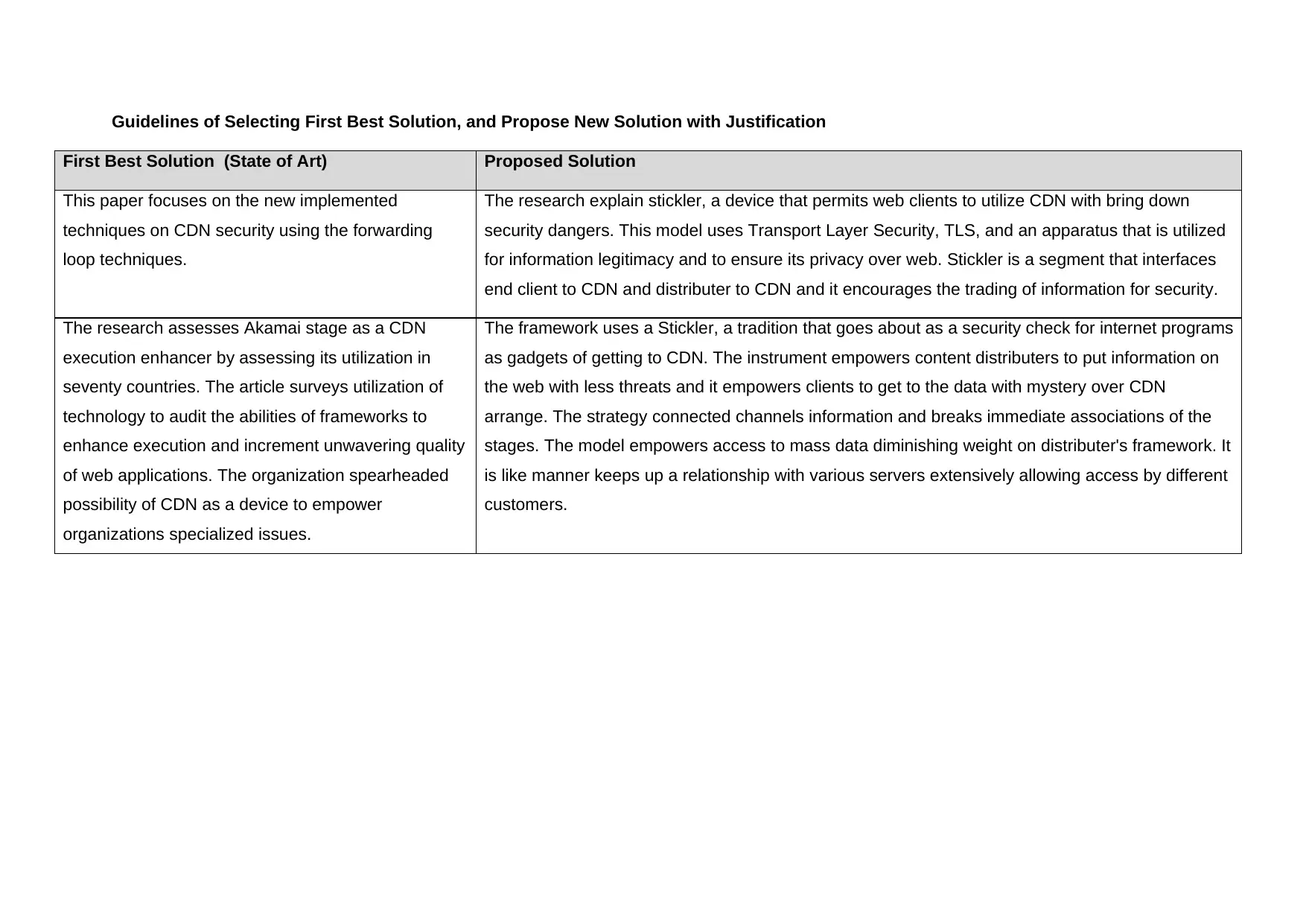
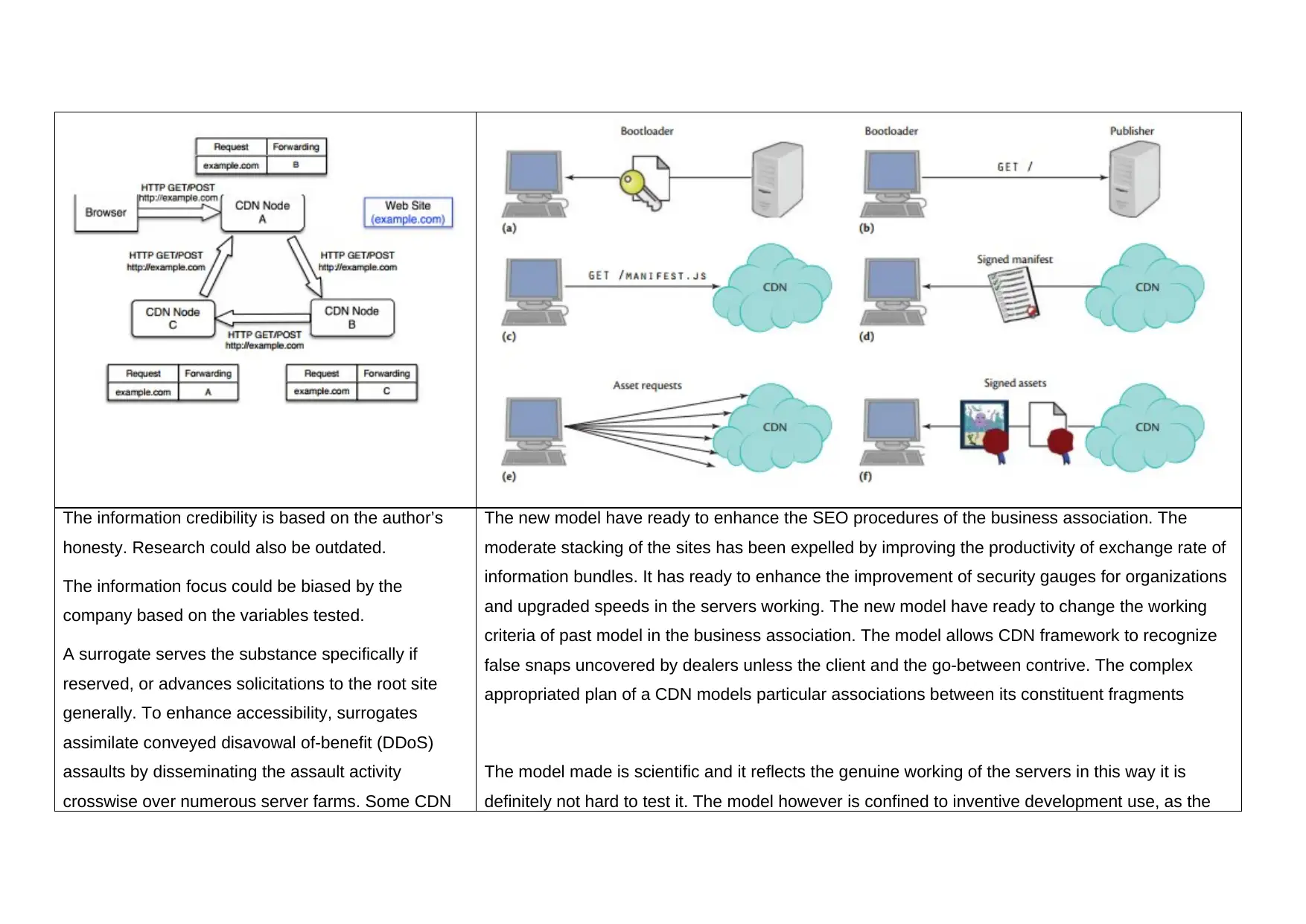
This report analyzes Content Delivery Network (CDN) security, focusing on a new implemented technique utilizing forwarding loop methods. The study examines a model using Transport Layer Security (TLS) to enhance data privacy and integrity, comparing it with existing CDN technologies, such as those used by Akamai. The report evaluates the impact of the new model on business organizations, highlighting improvements in website loading speed, enhanced security protocols, and the ability to identify fraudulent clicks. It also acknowledges the limitations of the new model, such as the need for further refinement to handle high data rates. The analysis includes a comparison of the bandwidth and delivery network enhancements of the new model, as well as the use of caching proxy arrays and web application firewalls (WAF) to mitigate DDoS attacks and improve overall web application performance. The report offers a comprehensive overview of the advancements in CDN security and its implications for modern web applications.
1 out of 3






![[object Object]](/_next/static/media/star-bottom.7253800d.svg)