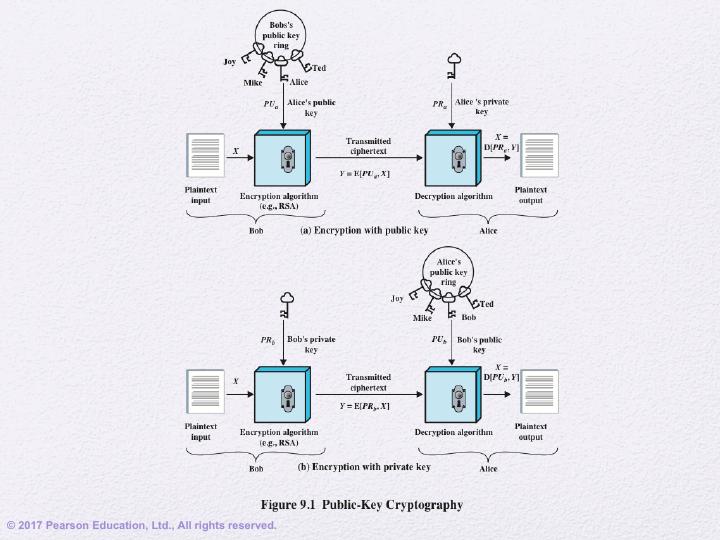
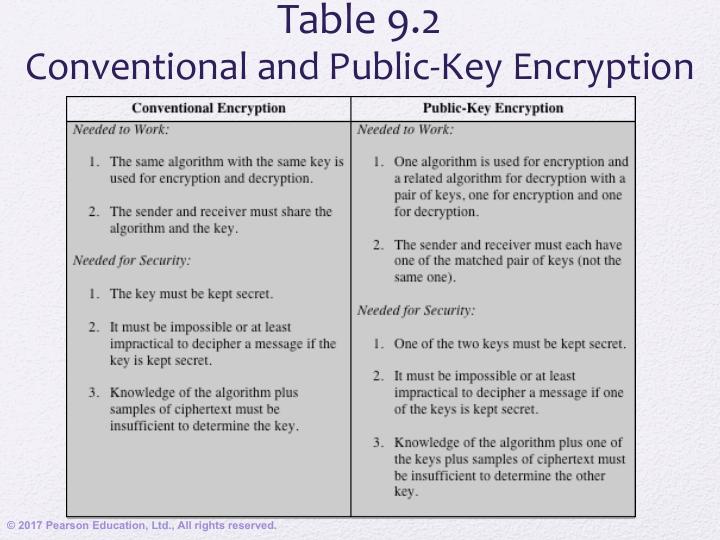
Public Key Cryptography and RSA pdf
44 Pages2675 Words91 Views
Added on 2022-01-21
Public Key Cryptography and RSA pdf
Added on 2022-01-21
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Symmetric Encryption Assignment
|5
|884
|175
Principle and Method in Cryptographic Security | Discussion
|4
|638
|19
Security in Information Technology | Assignments
|13
|3545
|119
Cryptography and System Security .
|7
|1528
|232
Cryptography Assignment 2022
|8
|559
|16
Network Security: Cryptography, Data in Transit and Rest, Cloud Computing
|10
|1928
|459