Course specification for CIS8008
33 Pages4258 Words30 Views
Added on 2021-06-14
Course specification for CIS8008
Added on 2021-06-14
ShareRelated Documents
CIS8008 Assessment 3Name of the Student Name of the University

Table of ContentsTask 1.............................................................................................................................3Task 1.1......................................................................................................................3Task 1.2......................................................................................................................3Task 2.............................................................................................................................4Task 2.1......................................................................................................................4Task 2.2......................................................................................................................8Task 2.3....................................................................................................................10Task 2.4....................................................................................................................11Task 3...........................................................................................................................16Task 3.1....................................................................................................................16Task 3.2....................................................................................................................17Task 3.3....................................................................................................................18Task 3.4....................................................................................................................19Task 3.5....................................................................................................................20References....................................................................................................................22Appendix......................................................................................................................22Decision tree Performance.......................................................................................22Weka logistic Performance.......................................................................................26

Task 1Task 1.1 The organization that is chosen to carry out this particular report is TelstraCorporation Ltd. Telstra is the leading provider of mobile devices, mobile phones, broadbandinternet or mobile phones in Australia. Telstra is the biggest Australian telecommunicationas well as media company that operates and builds networks of telecommunication, marketvoice, internet access, mobile as well as other services and products of entertainment as well(Thomas et al. 2016). Telstra Corporation Ltd. is located in Melbourne, Australia. FirstlyTelstra was combined with government department of Australia Post. But, now Telstraconverted itself to a privatised company and is undergoing to change its program forbecoming a company that mainly focuses on needs of customer. Telstra is also expecting toincrease its focus on growing its industry mainly in the international market. Telstra provides Australia with fixed line services including the home phones,businesses as well as other PSTN product. Telstra also outsource a part of networkmaintenance and network installation to private contractors as well as has joint ventures withABB Communications. Majority of the Australian public telephones are owned andmaintained by Telstra. In the year 2006, Telstra increased its services on mobile telephone(Moorhead 2016). Now, Telstra is largest service provider of mobile telephone in Australia,both in terms of coverage and subscription. The first company in Australia to provide serviceof mobile telephony is Telstra. Telstra Wholesale provides Australia products such as mobile,voice, data as well as other facilities to some other organizations and companies for re-sale(McDougal 2017). This particular company is selected to carry out this report is because thiscompany is using online platform for the payment method and all the uses several technologyto establish other payment options. Website: https://www.telstra.com.au/Task 1.2 In this section, the privacy as well as security policy of Telstra is analysed that makesthe company safe for using its service and products. The security and the privacy of data inTelstra mainly addresses the core principle of Australian Data Governance Draft Code ofPractice (Gerrand 2017). There are nine core principle that Telstra use to maintain its securityas well as privacy of data. The nine core principle are stated below.Principle 1:No Harm- In this principle, the entity is expected to use the best ventureto ensure the disclosure, collection, as well as use of the personal information should notharm the subject individual. Another no harm rule that is included in this principle includesthat the usage of data is not to be ethical (Stroyov, Patel and Ali 2017). There should be nodisclosure of personal information to some other parties and the situation for collecting thedata also should not be exploited. In respect to Telstra, the company should take step toensure that the data has privacy obligation and has confidentiality that is related to protectionof the personal information.

Principle 2: Honesty as well as Transparency- In this principle, the companyshould be honest to its customer while using their personal data, and while collecting as wellas disclosing the data. According to this principle, the company should ensure that the datathat is collected as the data that is disclosed are done according to the statement of privacypolicy as well as notification (Harris 2017). Enquiry that are made about any personalinformation are to be made with mechanism of individuals. The companies should raiseawareness regarding the disclosure of personal data to some other parties. The companyshould also take effort in promoting the data protection act and encourage codes for adoption,which protects the data from being disclosed to some other third parties (Fleisher andBensoussan 2015). Telstra can ensure honesty as well as transparency in collection of data byadhering all the updated practices. The information of the customer should be used by thecompany anytime, but that should not be disclosed to some other third parties. The customersare to be ensured about protection of their personal data by Telstra while providing theirpersonal details to the company. Telstra should provide their customer with the best customerexperience and this is bounded by Privacy Act 1988 in Australia. Principle 3: Fairness- According to this principle, the data that is collected from thecustomer should be collected in a fair way considering all factors that includes reasonableexpectation of community and the risk of harming the subject individual. This act should alsodetermine the exact time of retaining the personal information that are to be done (Ragsdale2014). The data should be collected from that particular subject individual that are needed forthe business purpose. The right that is used to access the personal information in Telstrashould be subjected to the exceptions as per the privacy of law. Telstra should maintain thefairness principle as per the privacy statement of law. Principle 4: Choice- A company should ensure a proper mechanism for proving thechoice of using as well as collecting the personal information within the company. Telstradoes not incorporate the principle of choice that is used in the company. Telstra should notuse external data without taking the permission of the individuals, unless and until it isrequired by the government. Principle 5: Accuracy- According to accuracy principle, the entity should reportsome reasonable steps to ensure the data that is shared is accurate and is not misleading.Development as well as adoption of standards in the industry is to be encouraged for helpingan effective code of implementation. This principle of accuracy is followed by Telstra as itcollects all the personal information from the customer personally and then deliverspersonalized content to the customers as well while paying for the services and products ofthe company. The data that is collected should be accessible and should be accurateaccording to the law of data protection act. Principle 6: Security, Safety and Re-Identification- A company should alwaysdesign the data security and organize the data security that fits best in the standard ofcompany. Telstra should also implement such standards of security measures and safetymeasure in the company that would address the data in case of any harm that is caused due todata breach in the company (Bednar, Sadok and Shiderova 2014). Telstra has implemented aparticular individual who entrusts the responsibility of the data security in the company. The

data sets that are collected and then storing of multiple data should be treated as personalinformation unless the company does not implement any appropriate security measures or re-identification technique that are needed in the organization. The process of re-identificationshould be robust, which includes updating as well as testing of the technique related to thestandard of the industry. Principle 7: Accountability- The organization should create a register as well asmaintain it, which includes personal information of the customers. This principle guidesTelstra to maintain such register. The information that are to be stored in the registers of thecompany should not be disclosed to any other third parties and information about how thedata is collected and about how they are used in the company should not be disclosed either.Telstra incorporates privacy obligations as well as confidentiality that helps to keep thepersonal data secured from any other third parties and from being the data being disclosed.The personal information is delivered to the customers only at the time of delivering theproduct or the service to the customer (Brijs 2016). The transactions that are done in Telstraare not only limited to process transaction, enquiries handling for supporting the customer,and transaction processing. The accountability principle ensures that the code is complied byTelstra so that it deals with the third parties properly. The statement of security policy shouldbe made clear within the organization to ensure compliance and the statement should adherewith the code of conduct that is already established. Principle 8: Stewardship: According to the principle of Stewardship, it is expectedfrom a company to appoint and official who looks on the fact that all the operation andservices goes well in the company. When the data is reviewed in Telstra, the company shouldimplement the factor of Stewardship. The compliance of Telstra should be created with thecode of Stewardship. The internal process in the organization should support as well asensure the compliance with code of Stewardship. The official should be provided with propertraining about how to handle the data in the organization. Principle 8: Enforcement- The enforcement principle of Telstra should be enforcedwithin the company from time to time. The guideline that is issued by enforcement is to beimplemented in a company that deals with security of data within the organization. Anyallegation in the company about data security is to be responded and reported by the officialsof the company (Aversa, Furnari and Haefliger 2015). To respond all such allegation, theofficials has to implement some enforcement principle to determine appropriate responsesregarded to data security in data breaches.

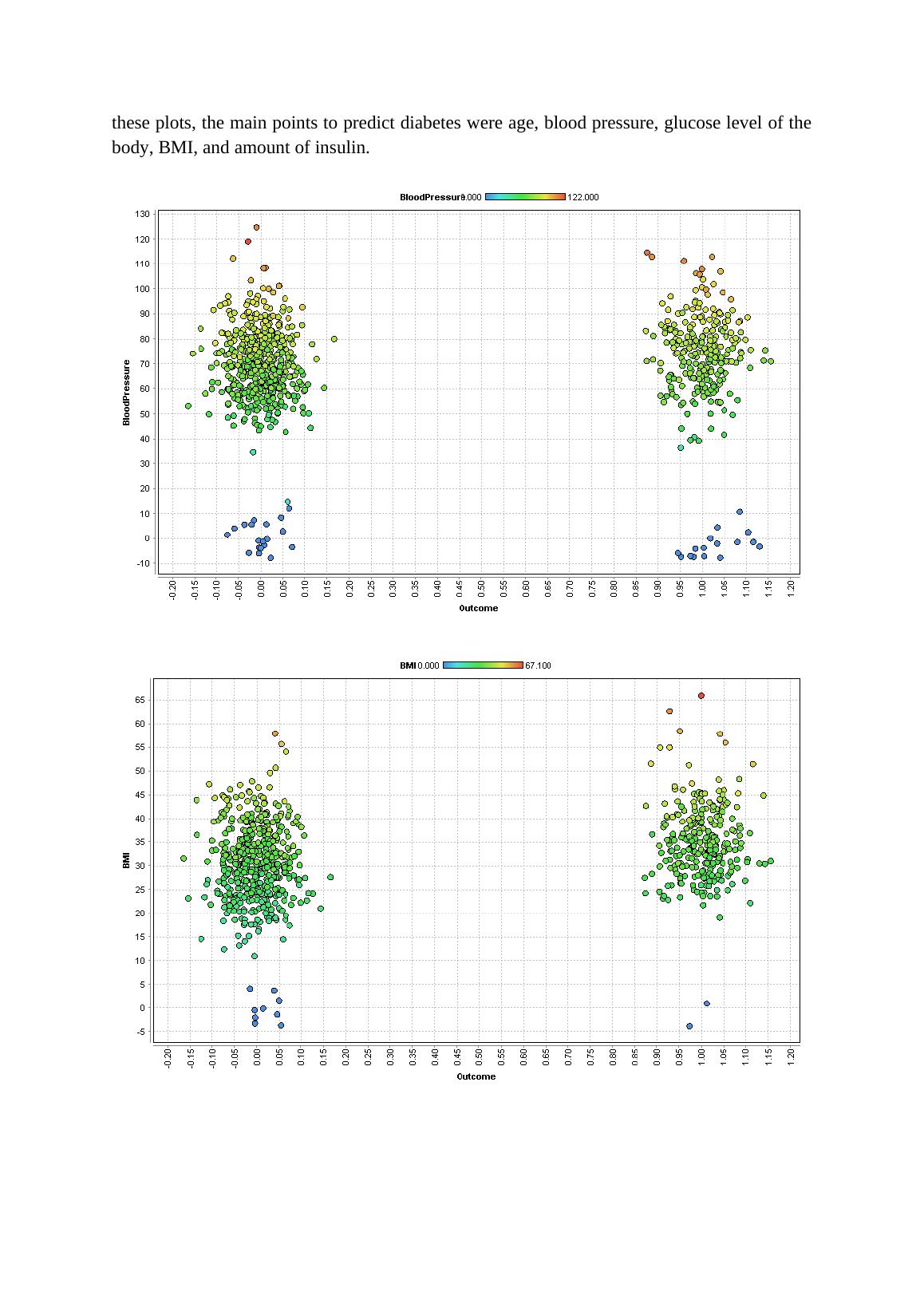
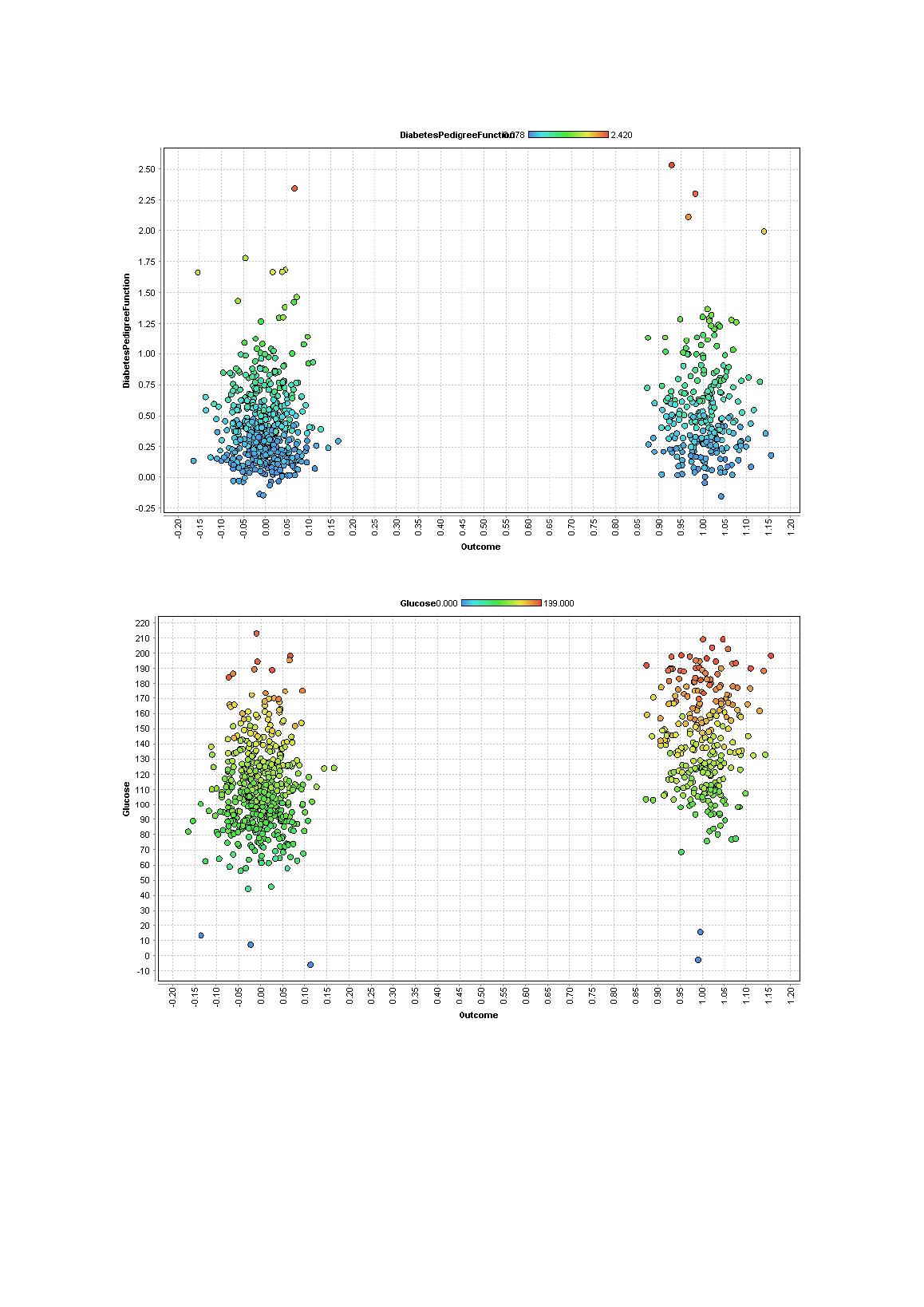
Task 2Task 2.1 To conduct the EDA (Exploratory Data Analysis) related to diabetes data, rapid minerstudio is basically required. For conducting this EDA, it is required to understand about howto fit the data in this miner studio software and how the processes are built. The process bywhich conducting of EDA starts is by importing the data in the software of rapid miner andthen save the data on the local storage (Grant 2016). After the data is stored, the next step isconducted by dragging the set of data in the process layout area and finally connects it withthe output port. After the dataset is dragged, the “run” button is pressed in the software,which returns the whole dataset and the primary statistics of the data. The primary statistics issummarized below.Figure 1: Summary Statistics TableThe analysis that is performed includes the cleaning process of the raw data that isincluded for further analysis. In this particular case, the dataset is taken from the diabetesdataset. There are a total of 8 independent variables as well as 1 dependent variable that isused in this analysis. All the variables that are used in this analysis are not such important formaking the prediction of the dependent variable. Maximum of five to six variable are actuallyneeded to predict all the independent variables in this analysis (Leppäaho, Plakoyiannaki andDimitratos 2016). The outcomes in this case is prediction of diabetes.To proceed with the analysis, the analyst has actually performed analysis in three step.Three step analysis that is performed in this analysis is done to identify the topmost fivevariable that are needed to predict diabetes. There are different research works that includesage, blood pressure, glucose level of the body, BMI, amount of insulin, and many more fordetermining the diabetes level. All such variable were used in this particular data set and bythis process, analyst has taken the top five variables. The first step of identifying the top fivevariable was done through plotting scatter diagram. The below diagrams shows the scatterplotting diagrams that does not give defective light in this particular case. By assuming all
these plots, the main points to predict diabetes were age, blood pressure, glucose level of thebody, BMI, and amount of insulin.
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Financial Analysis of Telecommunication Companies in Australialg...
|12
|1923
|186
IS Security and Risk Management: Telstra Corporationlg...
|12
|2941
|57
Telstra Financial Analysis Assignmentlg...
|16
|3025
|29
Marketing Analysis of Telstra TV: Strategies to Attract Targeted Customerslg...
|11
|2991
|238
CIS8008 Assessment 3 Name of the Student Name of the Universitylg...
|39
|4066
|267
Analysis of Digital Marketing Strategies for Telstra Companylg...
|5
|1126
|402
