Cloud Computing Security: Threats, Issues and Mitigation Strategies
VerifiedAdded on 2023/01/19
|16
|3985
|85
Report
AI Summary
This report delves into the multifaceted realm of cloud computing security, recognizing its paramount importance in today's data-driven world. It begins by outlining fundamental security aspects, including confidentiality, authentication, authorization, non-repudiation, privacy, control, audit, and compliance. The report then dissects the major security issues and challenges inherent in cloud environments, categorizing them into general security challenges, security threats, privacy issues, application concerns, and specific threat issues such as data breaches, data loss, account hijacking, insecure APIs, and denial-of-service attacks. It further explores the threats posed by malicious insiders and the abuse of cloud services, underscoring the need for due diligence. The report concludes by presenting various security threats and the corresponding mitigation techniques to fortify cloud environments. This analysis emphasizes the critical need for robust security measures to safeguard data and ensure the reliable functioning of cloud-based systems.

Running head: CLOUD COMPUTING
Cloud Computing
[Name of the Student]
[Name of the University]
[Author note]
Cloud Computing
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD COMPUTING
Table of Contents
Introduction:....................................................................................................................................3
Cloud computing security aspects:..................................................................................................3
Confidentiality:............................................................................................................................3
Authentication and Authorization:..............................................................................................3
Non-repudiation:..........................................................................................................................4
Privacy and control:.....................................................................................................................4
Audit:...........................................................................................................................................4
Compliance:.................................................................................................................................5
Security issues in the cloud environment:.......................................................................................5
General Security challenges........................................................................................................5
Security threats:...........................................................................................................................5
Privacy issues:.............................................................................................................................6
Application issues:.......................................................................................................................7
Threat issues:...............................................................................................................................7
Breach of data:.............................................................................................................................7
Loss of Data:................................................................................................................................8
Hijacking of accounts:.................................................................................................................8
Insecure APIs:..............................................................................................................................9
Denial of Service or the DoS:......................................................................................................9
Table of Contents
Introduction:....................................................................................................................................3
Cloud computing security aspects:..................................................................................................3
Confidentiality:............................................................................................................................3
Authentication and Authorization:..............................................................................................3
Non-repudiation:..........................................................................................................................4
Privacy and control:.....................................................................................................................4
Audit:...........................................................................................................................................4
Compliance:.................................................................................................................................5
Security issues in the cloud environment:.......................................................................................5
General Security challenges........................................................................................................5
Security threats:...........................................................................................................................5
Privacy issues:.............................................................................................................................6
Application issues:.......................................................................................................................7
Threat issues:...............................................................................................................................7
Breach of data:.............................................................................................................................7
Loss of Data:................................................................................................................................8
Hijacking of accounts:.................................................................................................................8
Insecure APIs:..............................................................................................................................9
Denial of Service or the DoS:......................................................................................................9

2CLOUD COMPUTING
Malicious insider:........................................................................................................................9
Abuse of the cloud services:......................................................................................................10
Due diligence which are insufficient:........................................................................................10
Shared Technological issues:.....................................................................................................11
Security threats and Mitigation Techniques:.................................................................................11
Conclusion:....................................................................................................................................13
References:....................................................................................................................................14
Malicious insider:........................................................................................................................9
Abuse of the cloud services:......................................................................................................10
Due diligence which are insufficient:........................................................................................10
Shared Technological issues:.....................................................................................................11
Security threats and Mitigation Techniques:.................................................................................11
Conclusion:....................................................................................................................................13
References:....................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD COMPUTING
Introduction:
The cloud security is considered to be one of the most import issue which is to be taken
into consideration in today’s world and the reason behind this is that the security of the data is at
high risk. The risk faced by the data is mainly because of the safety and the security situations
which are not provided correctly for the transmission and function of the data [1]. Because of the
fact that the cloud computing is capable of providing a potential for an amount of consumers for
gaining access to the data that is saved and for this reason there remains an opportunity for the
obtaining of the high data risk. Due to all this reason there is an essential need of implementing
and identifying the security issues as well as the clarifications for the purpose of managing all the
issues.
Cloud computing security aspects:
Below are the listed major security aspects of cloud computing which needs to be focused
upon and this mainly includes the following:
Confidentiality:
This is mainly associated with including those areas which is associated with making sure
of the fact that the personal data are being presented as private, secure and in restricted form
anywhere around the users who are not authorized to access the data [2]. One of the most famous
and authentic way of maintaining the confidentiality includes the encryption of the data before
the data is hosted into the clouds.
Authentication and Authorization:
This is process which generally refers to the process of providing verification of the
identity of any individual along with verifying what an individual is authorized to do. In case of
Introduction:
The cloud security is considered to be one of the most import issue which is to be taken
into consideration in today’s world and the reason behind this is that the security of the data is at
high risk. The risk faced by the data is mainly because of the safety and the security situations
which are not provided correctly for the transmission and function of the data [1]. Because of the
fact that the cloud computing is capable of providing a potential for an amount of consumers for
gaining access to the data that is saved and for this reason there remains an opportunity for the
obtaining of the high data risk. Due to all this reason there is an essential need of implementing
and identifying the security issues as well as the clarifications for the purpose of managing all the
issues.
Cloud computing security aspects:
Below are the listed major security aspects of cloud computing which needs to be focused
upon and this mainly includes the following:
Confidentiality:
This is mainly associated with including those areas which is associated with making sure
of the fact that the personal data are being presented as private, secure and in restricted form
anywhere around the users who are not authorized to access the data [2]. One of the most famous
and authentic way of maintaining the confidentiality includes the encryption of the data before
the data is hosted into the clouds.
Authentication and Authorization:
This is process which generally refers to the process of providing verification of the
identity of any individual along with verifying what an individual is authorized to do. In case of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD COMPUTING
authentication, blocks related to the electric idea or a particular file is developed for identifying
in a proper way [3]. This is the process by which the data is kept secure and safe from any kind
of intentional or accidental modifications.
Non-repudiation:
This is generally associated with describing the capacity so as to make sure that a party
present in an agreement is not capable of rejecting the authenticity of the signature provided in a
document or in any transmission of message or email which has been stated by them previously.
Privacy and control:
Privacy is one of the problem which is highly important and is faced by the cloud
computing environment. Privacy is associated with considering each and every lawful agreement
along with the trust of the users at each and every single step of eth designing process [4].
Control generally refers to the best way of managing the utilization of the system such as the
applications or the infrastructure or the data.
Audit:
This generally refers to the facility which any business enterprise is having for the
purpose of monitoring the application users when being used in situations when be security as
the regulatory point of view is taken into consideration. This might be also associated with
including the extra layer present above the virtualized process system which are managed by the
virtual machine for the purpose of providing services related to observing the ways how this
happens in particular situations along with services for other factors which might be associated
with having an impact upon the availability needs of an system which needs to be audited.
authentication, blocks related to the electric idea or a particular file is developed for identifying
in a proper way [3]. This is the process by which the data is kept secure and safe from any kind
of intentional or accidental modifications.
Non-repudiation:
This is generally associated with describing the capacity so as to make sure that a party
present in an agreement is not capable of rejecting the authenticity of the signature provided in a
document or in any transmission of message or email which has been stated by them previously.
Privacy and control:
Privacy is one of the problem which is highly important and is faced by the cloud
computing environment. Privacy is associated with considering each and every lawful agreement
along with the trust of the users at each and every single step of eth designing process [4].
Control generally refers to the best way of managing the utilization of the system such as the
applications or the infrastructure or the data.
Audit:
This generally refers to the facility which any business enterprise is having for the
purpose of monitoring the application users when being used in situations when be security as
the regulatory point of view is taken into consideration. This might be also associated with
including the extra layer present above the virtualized process system which are managed by the
virtual machine for the purpose of providing services related to observing the ways how this
happens in particular situations along with services for other factors which might be associated
with having an impact upon the availability needs of an system which needs to be audited.

5CLOUD COMPUTING
Compliance:
Compliance issues is generally seen to be occurring whenever the cloud backup or
storage is used. While the data from the internal storage space is being shifted to the cloud
storage there is an essential need of conducting a strong analysis of the fact that how the data
would be stored and this is done so as to remain complaint with the laws and rules of the
industry.
Security issues in the cloud environment:
General Security challenges
Data which an organization is having and is based upon the cloud techniques are seen to be
exposed to different type of challenges. This challenges can be categorized into internal
challenges and external challenges the internal challenges might be faced when the data is being
transferred for the organization to the servers [5]. There also exists external risks such as the
DoS, malicious codes and many more. In order to ensure that the security level in an
organization dependent upon cloud computing it is very necessary to discover all the security
challenges which are related to the assets. Defining of the security challenges is very much
important. Some of the security challenges have been discussed below:
Security threats:
This are generally associated with referring to all those properties which are associated
with the exploitation of the vulnerabilities as well as the weakness of the points for the purpose
of causing a harm to the computer assets [6]. Threats might or might not be happening but still
they are having a high potential of damaging the data along with making the resources face a
huge amount of risk. Date kept at rest is one of the major issue which is faced by the cloud
Compliance:
Compliance issues is generally seen to be occurring whenever the cloud backup or
storage is used. While the data from the internal storage space is being shifted to the cloud
storage there is an essential need of conducting a strong analysis of the fact that how the data
would be stored and this is done so as to remain complaint with the laws and rules of the
industry.
Security issues in the cloud environment:
General Security challenges
Data which an organization is having and is based upon the cloud techniques are seen to be
exposed to different type of challenges. This challenges can be categorized into internal
challenges and external challenges the internal challenges might be faced when the data is being
transferred for the organization to the servers [5]. There also exists external risks such as the
DoS, malicious codes and many more. In order to ensure that the security level in an
organization dependent upon cloud computing it is very necessary to discover all the security
challenges which are related to the assets. Defining of the security challenges is very much
important. Some of the security challenges have been discussed below:
Security threats:
This are generally associated with referring to all those properties which are associated
with the exploitation of the vulnerabilities as well as the weakness of the points for the purpose
of causing a harm to the computer assets [6]. Threats might or might not be happening but still
they are having a high potential of damaging the data along with making the resources face a
huge amount of risk. Date kept at rest is one of the major issue which is faced by the cloud
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD COMPUTING
computing and the reason behind this is that the users might be associated with storing all their
common as well as the private and sensitive data in the clouds which are accessible from
anywhere and by anyone. Data theft is one of the common issue which is commonly being faced
by all the cloud service providers. Along with this there also exist some cloud service providers
who are not even provided with their own servers and the reason behind this is the cost
effectiveness and the flexibility [7]. Besides this there also exists certain incidents such as the
loss of data which might be associated with causing a very severe problem for the users. Beside
all this there also exists the natural disasters which might be associated with causing huge
damages to the data or might be responsible for making the data corrupted. For this reason the
physical data location can be considered to be one of the major security issue that is faced by the
cloud computing.
Privacy issues:
The cloud service providers are seen to be associated with enforcing the own policies that
they are having for the purpose of making sure that the data safety is ensured while the users are
indulged in storing of the data in the cloud model [8]. The service providers must be associated
with making sure of the fact that they are associated with recognizing the one who is actually
associated with accessing the data that is stored in the clouds along with making sure that only
the authorized persons are capable of maintaining the cloud service models. The security of the
cloud computing should be maintained from the service provider side as well as from the user
side. The cloud service providers should be associated with providing of a good layer of security
protection to the users and besides this the users should not be associated with the tampering of
the data of the other users [9]. Cloud computing is considered to be a good way of reducing the
cost as well as the good way of providing more storage. This is only to be done if and only if the
computing and the reason behind this is that the users might be associated with storing all their
common as well as the private and sensitive data in the clouds which are accessible from
anywhere and by anyone. Data theft is one of the common issue which is commonly being faced
by all the cloud service providers. Along with this there also exist some cloud service providers
who are not even provided with their own servers and the reason behind this is the cost
effectiveness and the flexibility [7]. Besides this there also exists certain incidents such as the
loss of data which might be associated with causing a very severe problem for the users. Beside
all this there also exists the natural disasters which might be associated with causing huge
damages to the data or might be responsible for making the data corrupted. For this reason the
physical data location can be considered to be one of the major security issue that is faced by the
cloud computing.
Privacy issues:
The cloud service providers are seen to be associated with enforcing the own policies that
they are having for the purpose of making sure that the data safety is ensured while the users are
indulged in storing of the data in the cloud model [8]. The service providers must be associated
with making sure of the fact that they are associated with recognizing the one who is actually
associated with accessing the data that is stored in the clouds along with making sure that only
the authorized persons are capable of maintaining the cloud service models. The security of the
cloud computing should be maintained from the service provider side as well as from the user
side. The cloud service providers should be associated with providing of a good layer of security
protection to the users and besides this the users should not be associated with the tampering of
the data of the other users [9]. Cloud computing is considered to be a good way of reducing the
cost as well as the good way of providing more storage. This is only to be done if and only if the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD COMPUTING
security is being ensured from the customer as well as the user side. There also exist regulatory
reforms which are very essential for the purpose of providing protection to the data which are
sensitive and the reason behind this is one of the most challenging aspect where the cloud
computing needs to make sure that the customers are having trust related to the privacy and
security of the data.
Application issues:
There always exists an essential need of monitoring and maintaining of the cloud
environment by the service providers and this is to be done so as to make sure of the fact that the
cloud remains secure and is not affected by any of the malicious codes which have been
uploaded by the hackers or by an attacker to the cloud for the purpose of stealing the information
which are sensitive and for damaging the information of specific users.
Threat issues:
Along with above discussed security and privacy issues there also exists other challenges
which are faced by the clouds and this security issues are seen to be used at a wide basis in
today’s world [10]. Below are the listed nine major threats which are being faced by cloud
computing environments in a frequent manner.
Breach of data:
The data which are stored in eth cloud by different users might seem to be very much
important or sensitive. All this data which are being stored in the cloud might be stolen by the
unauthorized users might be associated with posing some level of danger to the users as well
who have suffered from the attack [11]. This is one of the top threat which is faced by the cloud
computing and the reason behind this is that the hackers or the attackers are capable of having an
security is being ensured from the customer as well as the user side. There also exist regulatory
reforms which are very essential for the purpose of providing protection to the data which are
sensitive and the reason behind this is one of the most challenging aspect where the cloud
computing needs to make sure that the customers are having trust related to the privacy and
security of the data.
Application issues:
There always exists an essential need of monitoring and maintaining of the cloud
environment by the service providers and this is to be done so as to make sure of the fact that the
cloud remains secure and is not affected by any of the malicious codes which have been
uploaded by the hackers or by an attacker to the cloud for the purpose of stealing the information
which are sensitive and for damaging the information of specific users.
Threat issues:
Along with above discussed security and privacy issues there also exists other challenges
which are faced by the clouds and this security issues are seen to be used at a wide basis in
today’s world [10]. Below are the listed nine major threats which are being faced by cloud
computing environments in a frequent manner.
Breach of data:
The data which are stored in eth cloud by different users might seem to be very much
important or sensitive. All this data which are being stored in the cloud might be stolen by the
unauthorized users might be associated with posing some level of danger to the users as well
who have suffered from the attack [11]. This is one of the top threat which is faced by the cloud
computing and the reason behind this is that the hackers or the attackers are capable of having an

8CLOUD COMPUTING
easy access to the data which have been stored in the clouds by the users. Besides all this it is the
responsibility of the cloud service users to ensure the fact that the quality along with the
reliability and the performance of the cloud service providers are being negotiated between the
cloud service providers and the users by making use of the SLA or the Service Level Agreement.
For all this reason the data breach is considered to be the worst problem which is faced by the
cloud computing services.
Loss of Data:
The data which is stored in the cloud might be damaged or might also be corrupted
because of certain reasons like accidental or sudden shut down of the servers because of reasons
such as financial or legal problems, and along with this the natural disaster is another reason
which includes the events such as fire or earthquake [12]. Because of this events it might be
entirely impossible to recover because no backups are available and this in turn would be
associated with permanent loss of data of the users as there would not be existing any kind of
extra copies of the information which is lost.
Hijacking of accounts:
This threat mainly occurs when the account of the user is hijacked or is stolen by a hacker
and after having access of the account the attacker might be associated with impersonating of
user to conduct activities which are malicious and unauthorized and this in turn would be
associated with causing a harm to the users. Example of this particular incident is that the
hackers are associated with the manipulation of the data or is associated with providing of false
information and eavesdropping upon the transactions by making use of the accounts which they
have stolen [13]. Additionally there would also be no usage of native APIs so as to login and this
easy access to the data which have been stored in the clouds by the users. Besides all this it is the
responsibility of the cloud service users to ensure the fact that the quality along with the
reliability and the performance of the cloud service providers are being negotiated between the
cloud service providers and the users by making use of the SLA or the Service Level Agreement.
For all this reason the data breach is considered to be the worst problem which is faced by the
cloud computing services.
Loss of Data:
The data which is stored in the cloud might be damaged or might also be corrupted
because of certain reasons like accidental or sudden shut down of the servers because of reasons
such as financial or legal problems, and along with this the natural disaster is another reason
which includes the events such as fire or earthquake [12]. Because of this events it might be
entirely impossible to recover because no backups are available and this in turn would be
associated with permanent loss of data of the users as there would not be existing any kind of
extra copies of the information which is lost.
Hijacking of accounts:
This threat mainly occurs when the account of the user is hijacked or is stolen by a hacker
and after having access of the account the attacker might be associated with impersonating of
user to conduct activities which are malicious and unauthorized and this in turn would be
associated with causing a harm to the users. Example of this particular incident is that the
hackers are associated with the manipulation of the data or is associated with providing of false
information and eavesdropping upon the transactions by making use of the accounts which they
have stolen [13]. Additionally there would also be no usage of native APIs so as to login and this
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD COMPUTING
in turn would make anyone capable of getting registered as a cloud service user and for this
reason the chances related to account being hacked becomes very high.
Insecure APIs:
The software interfaces which exists for being used by the users so as to interact with the
cloud services is one of the crucial factor which is needed for making sure of the fact that the
security of the cloud is being maintained [14]. This can be understood with an example which is,
two stage access control mechanism can be proposed which would be done by usage of the Role
Based Access Control Model or the RBAC for the purpose of providing a strong API program.
Denial of Service or the DoS:
Hackers are associated with usage of this type of attack for the purpose of flooding the
machine or the network resources that a cloud service provider is having and this in turn would
be interrupting the users and would be preventing the users from getting connected to the
network access [15]. For this reason this is considered to be a major security issue which might
be associated with causing harm to the users and they might not be receiving the things when
they would be needing it.
Malicious insider:
Organizations which are associated with the usage of the cloud computing might be
facing a big threat because of the employees. The employees might be acting as an attacker
themselves or might be acting as the hacker’s partner. They would be having a better chance of
stealing of tampering the data present in the cloud model intentionally. These type of activities
are in turn associated with causing the sensitive data of the users to get leaked to eth other and
this would be responsible for causing a harm to the targeted users. Studies have been associated
in turn would make anyone capable of getting registered as a cloud service user and for this
reason the chances related to account being hacked becomes very high.
Insecure APIs:
The software interfaces which exists for being used by the users so as to interact with the
cloud services is one of the crucial factor which is needed for making sure of the fact that the
security of the cloud is being maintained [14]. This can be understood with an example which is,
two stage access control mechanism can be proposed which would be done by usage of the Role
Based Access Control Model or the RBAC for the purpose of providing a strong API program.
Denial of Service or the DoS:
Hackers are associated with usage of this type of attack for the purpose of flooding the
machine or the network resources that a cloud service provider is having and this in turn would
be interrupting the users and would be preventing the users from getting connected to the
network access [15]. For this reason this is considered to be a major security issue which might
be associated with causing harm to the users and they might not be receiving the things when
they would be needing it.
Malicious insider:
Organizations which are associated with the usage of the cloud computing might be
facing a big threat because of the employees. The employees might be acting as an attacker
themselves or might be acting as the hacker’s partner. They would be having a better chance of
stealing of tampering the data present in the cloud model intentionally. These type of activities
are in turn associated with causing the sensitive data of the users to get leaked to eth other and
this would be responsible for causing a harm to the targeted users. Studies have been associated
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CLOUD COMPUTING
with reveling the fact that the passwords along with other data which are confidential and might
be easily obtained by the malicious insiders [18]. And for this reason the studies have also been
associated with addressing all this problems which are faced because of the malicious insiders
and they have also been associated with claiming the fact that this should be studied in two
context which includes the insider threat in cloud provider and the insider threat in cloud
outsourcer.
Abuse of the cloud services:
Analysis of the cloud environments have shown that most of the cloud computing
systems are having a very weak registration system. Which means anyone who is having a valid
credit card might be associated with registering themselves and start using the cloud services
immediately[16]. So the attackers are often associated with conducting the malicious activities
by means of abusing the relative anonymity which the cloud registration systems are having.
Some of the areas of future concern is associated with including the passwords and cracking of
the keys, DDoS attacks, launch of the dynamic attack points and hosting of the malicious data.
Due diligence which are insufficient:
There exist many users who are associated with undertaking a little amount of due
diligence about their cloud service providers. Along with this there also exists users who are not
even associated with considering the basic due diligence like the assessing of the financial health
that the cloud service providers are having or without considering the timespan of existence of
the cloud service provider in the market [17]. So it is essentially to be made sure that the due
diligence is not being ignored and the reason behind this is that the cloud service providers might
not be secure enough and might not be associated with taking the responsibility of the data that is
stolen by the hackers from the clouds.
with reveling the fact that the passwords along with other data which are confidential and might
be easily obtained by the malicious insiders [18]. And for this reason the studies have also been
associated with addressing all this problems which are faced because of the malicious insiders
and they have also been associated with claiming the fact that this should be studied in two
context which includes the insider threat in cloud provider and the insider threat in cloud
outsourcer.
Abuse of the cloud services:
Analysis of the cloud environments have shown that most of the cloud computing
systems are having a very weak registration system. Which means anyone who is having a valid
credit card might be associated with registering themselves and start using the cloud services
immediately[16]. So the attackers are often associated with conducting the malicious activities
by means of abusing the relative anonymity which the cloud registration systems are having.
Some of the areas of future concern is associated with including the passwords and cracking of
the keys, DDoS attacks, launch of the dynamic attack points and hosting of the malicious data.
Due diligence which are insufficient:
There exist many users who are associated with undertaking a little amount of due
diligence about their cloud service providers. Along with this there also exists users who are not
even associated with considering the basic due diligence like the assessing of the financial health
that the cloud service providers are having or without considering the timespan of existence of
the cloud service provider in the market [17]. So it is essentially to be made sure that the due
diligence is not being ignored and the reason behind this is that the cloud service providers might
not be secure enough and might not be associated with taking the responsibility of the data that is
stolen by the hackers from the clouds.
11CLOUD COMPUTING
Shared Technological issues:
The IaaS vendors are associated with delivering the services in a scalable way by means
of shared infrastructure and it is generally not designed for offering a string isolation properties
for the architecture which is multi-tenant.
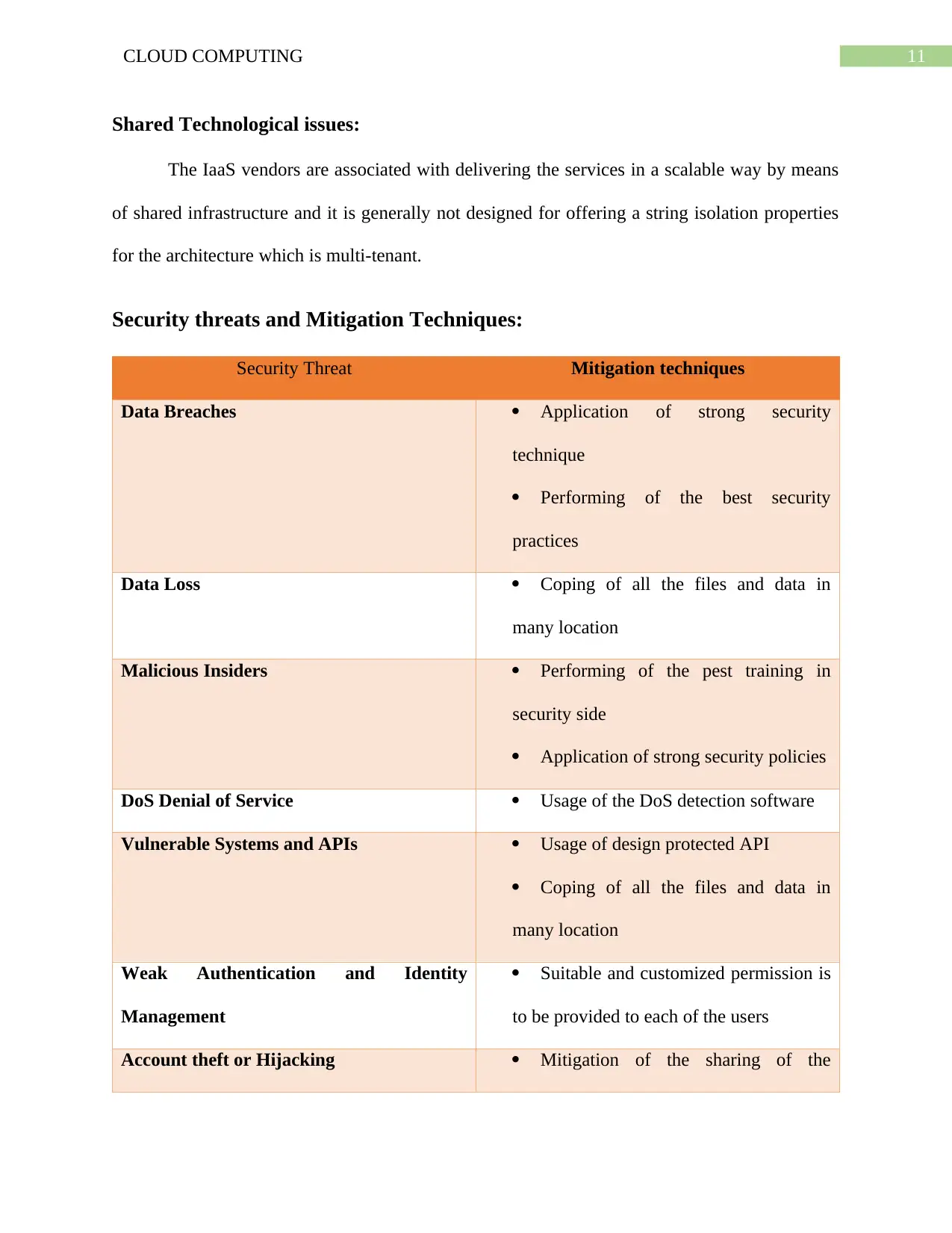
Security threats and Mitigation Techniques:
Security Threat Mitigation techniques
Data Breaches Application of strong security
technique
Performing of the best security
practices
Data Loss Coping of all the files and data in
many location
Malicious Insiders Performing of the pest training in
security side
Application of strong security policies
DoS Denial of Service Usage of the DoS detection software
Vulnerable Systems and APIs Usage of design protected API
Coping of all the files and data in
many location
Weak Authentication and Identity
Management
Suitable and customized permission is
to be provided to each of the users
Account theft or Hijacking Mitigation of the sharing of the
Shared Technological issues:
The IaaS vendors are associated with delivering the services in a scalable way by means
of shared infrastructure and it is generally not designed for offering a string isolation properties
for the architecture which is multi-tenant.
Security threats and Mitigation Techniques:
Security Threat Mitigation techniques
Data Breaches Application of strong security
technique
Performing of the best security
practices
Data Loss Coping of all the files and data in
many location
Malicious Insiders Performing of the pest training in
security side
Application of strong security policies
DoS Denial of Service Usage of the DoS detection software
Vulnerable Systems and APIs Usage of design protected API
Coping of all the files and data in
many location
Weak Authentication and Identity
Management
Suitable and customized permission is
to be provided to each of the users
Account theft or Hijacking Mitigation of the sharing of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



