Cloud Computing: Data Security Problems and Proposed Solutions Report
VerifiedAdded on 2023/01/20
|14
|2815
|29
Report
AI Summary
This report addresses the critical issue of data security within cloud computing environments. It begins by defining cloud computing and highlighting its reliance on the internet for shared resources like software, platforms, and information. The primary focus of the report is on data security, a significant concern for both consumers and cloud providers, and the potential solutions to this problem. The report examines the vulnerabilities associated with data storage and processing, and the need for protection against unauthorized access and data breaches. It delves into the challenges related to data security, including protecting confidential business and regulatory data, multi-tenant cloud service models, and legal and compliance issues. Furthermore, the report explores various cloud service models, including PaaS, SaaS, and IaaS, and their specific security concerns. The report proposes data lockdown, access policies, and security intelligence as potential solutions and offers an example of a security control plan. The conclusion emphasizes the limitations of current cloud computing systems in protecting user data confidentiality and the importance of implementing robust security measures.

Running head: CLOUD COMPUTING
CLOUD COMPUTING
Name of the Student
Name of the University
Author Note
CLOUD COMPUTING
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING 1
Abstract:
The purpose of this paper is to discuss the significant problem of cloud computing that is data
security, and this paper will also discuss the possible solution to this problem. Cloud
computing is a technology that is related to the computing that is based on the internet, in
cloud computing the shared resources like platform, software and the information that are
offered to the consumers on their demand. The technology of Cloud computing is one of the
cloud platforms, and the purpose of this is to share the resources which include software,
business processes, application and infrastructures. Confidentiality, availability, privacy,
authenticity and integrity are the major concerns for both the consumers as well as the cloud
providers as well. The concerns that are related to the security have given new life to the
immerging that is one of the most active areas of the research.
Abstract:
The purpose of this paper is to discuss the significant problem of cloud computing that is data
security, and this paper will also discuss the possible solution to this problem. Cloud
computing is a technology that is related to the computing that is based on the internet, in
cloud computing the shared resources like platform, software and the information that are
offered to the consumers on their demand. The technology of Cloud computing is one of the
cloud platforms, and the purpose of this is to share the resources which include software,
business processes, application and infrastructures. Confidentiality, availability, privacy,
authenticity and integrity are the major concerns for both the consumers as well as the cloud
providers as well. The concerns that are related to the security have given new life to the
immerging that is one of the most active areas of the research.

2CLOUD COMPUTING
Table of Contents
Introduction:...............................................................................................................................3
Problem:.....................................................................................................................................3
Data security:.........................................................................................................................4
PaaS:...................................................................................................................................6
SaaS:...................................................................................................................................6
IaaS:....................................................................................................................................6
Possible solution:.......................................................................................................................6
Conclusion:..............................................................................................................................10
Table of Contents
Introduction:...............................................................................................................................3
Problem:.....................................................................................................................................3
Data security:.........................................................................................................................4
PaaS:...................................................................................................................................6
SaaS:...................................................................................................................................6
IaaS:....................................................................................................................................6
Possible solution:.......................................................................................................................6
Conclusion:..............................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD COMPUTING
Introduction:
Cloud computing is a technology that is related to the computing that is based on the
internet, in cloud computing the shared resources like platform, software and the information
that are offered to the consumers on the demand of them (Chang & Ramachandran, 2016).
The actual definition of the cloud computing, that is a massive scale of paradigm of the
computing that is distributed, is also driven through the scales’ economics within that one
pool of the virtualized, abstract, dynamically scalable, storage, managed power of the
computing, services and platforms that have been delivered to the external consumers on their
demand over the internet. The primary purpose of this paper is to discuss the significant
problem of cloud computing that is data security, and this paper will also discuss the possible
solution of this problem (Hashizume et al., 2013). The present cloud computing systems are
able to pose limitations for the protection of confidentiality of the user data. Since the
sensitive data of the users is presented in the form of an unencrypted format for the remotely
controlled machines that are operated and owned by the third party providers. There are so
many techniques to protect the data of the users from hackers. An approach that is presented
for protection of the user data confidentiality from the providers of the services as well as it
ensures that the service providers are not able to collect the confidential data of the users
when the data has been stored and processed in the systems of the cloud computing. The
cloud computing offers different types of services and data storage that is based on the
internet.
Problem:
The major problem of cloud computing is, the data protection. The capabilities of the vendor
security are the key to the establishment of the strategic value (Arora, Parashar &
Transforming, 2013). When it is the matter of private, public and hybrid solutions of the
Introduction:
Cloud computing is a technology that is related to the computing that is based on the
internet, in cloud computing the shared resources like platform, software and the information
that are offered to the consumers on the demand of them (Chang & Ramachandran, 2016).
The actual definition of the cloud computing, that is a massive scale of paradigm of the
computing that is distributed, is also driven through the scales’ economics within that one
pool of the virtualized, abstract, dynamically scalable, storage, managed power of the
computing, services and platforms that have been delivered to the external consumers on their
demand over the internet. The primary purpose of this paper is to discuss the significant
problem of cloud computing that is data security, and this paper will also discuss the possible
solution of this problem (Hashizume et al., 2013). The present cloud computing systems are
able to pose limitations for the protection of confidentiality of the user data. Since the
sensitive data of the users is presented in the form of an unencrypted format for the remotely
controlled machines that are operated and owned by the third party providers. There are so
many techniques to protect the data of the users from hackers. An approach that is presented
for protection of the user data confidentiality from the providers of the services as well as it
ensures that the service providers are not able to collect the confidential data of the users
when the data has been stored and processed in the systems of the cloud computing. The
cloud computing offers different types of services and data storage that is based on the
internet.
Problem:
The major problem of cloud computing is, the data protection. The capabilities of the vendor
security are the key to the establishment of the strategic value (Arora, Parashar &
Transforming, 2013). When it is the matter of private, public and hybrid solutions of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD COMPUTING
cloud, the possibility of the information that is compromised is able to create tremendous
angst. Except for the third providers, the organizations, for managing the infrastructures of
the cloud however, it is not easy about to grant them the visibility into the data that are
sensitive (Wei et al., 2014). In the cloud based computing there comes data security
challenges which are complex:
The need for protecting the confidential business, regulatory data or government.
The models of the cloud services with having multiple tenants are sharing the
infrastructure that is the same (Rao & Selvamani, 2015).
The Legal issues as well as the data mobility that is related to some of the rules of the
government such as the directive of the EU data privacy.
Reporting, auditing and concern of compliance.
Operational intelligence and the loss of the critical security visibility that is not
available for feeding the enterprise of the information of the IT security as well as the
management of the risk (Hashem et al., 2015).
A type of an insider that is new and who even doesn't work for the particular
company; however it may be having the visibility and control into the data.
Data security:
It is able to focus on the protection of the hardware and software that is associated
with cloud computing (Rittinghouse & Ransome, (2017). This deals with the apt location of
the apt choosing for the data centres for protecting this from different types of conditions of
the weather, internal threats, physical and fire attacks which might able to destroy the
external threats and centre physically avoiding the break-ins and the unauthorised access
(Zhang et al., 2017).
cloud, the possibility of the information that is compromised is able to create tremendous
angst. Except for the third providers, the organizations, for managing the infrastructures of
the cloud however, it is not easy about to grant them the visibility into the data that are
sensitive (Wei et al., 2014). In the cloud based computing there comes data security
challenges which are complex:
The need for protecting the confidential business, regulatory data or government.
The models of the cloud services with having multiple tenants are sharing the
infrastructure that is the same (Rao & Selvamani, 2015).
The Legal issues as well as the data mobility that is related to some of the rules of the
government such as the directive of the EU data privacy.
Reporting, auditing and concern of compliance.
Operational intelligence and the loss of the critical security visibility that is not
available for feeding the enterprise of the information of the IT security as well as the
management of the risk (Hashem et al., 2015).
A type of an insider that is new and who even doesn't work for the particular
company; however it may be having the visibility and control into the data.
Data security:
It is able to focus on the protection of the hardware and software that is associated
with cloud computing (Rittinghouse & Ransome, (2017). This deals with the apt location of
the apt choosing for the data centres for protecting this from different types of conditions of
the weather, internal threats, physical and fire attacks which might able to destroy the
external threats and centre physically avoiding the break-ins and the unauthorised access
(Zhang et al., 2017).
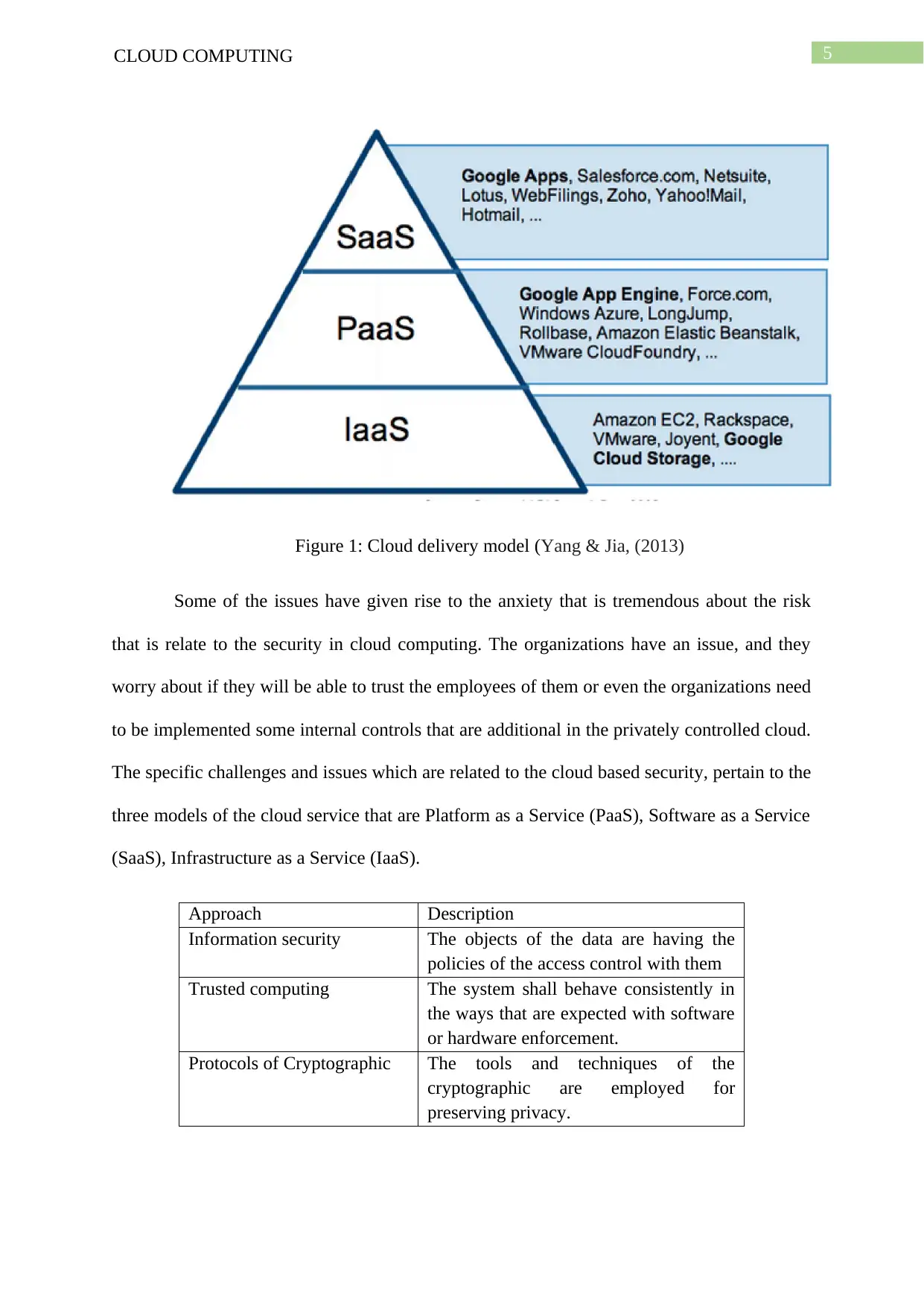
5CLOUD COMPUTING
Figure 1: Cloud delivery model (Yang & Jia, (2013)
Some of the issues have given rise to the anxiety that is tremendous about the risk
that is relate to the security in cloud computing. The organizations have an issue, and they
worry about if they will be able to trust the employees of them or even the organizations need
to be implemented some internal controls that are additional in the privately controlled cloud.
The specific challenges and issues which are related to the cloud based security, pertain to the
three models of the cloud service that are Platform as a Service (PaaS), Software as a Service
(SaaS), Infrastructure as a Service (IaaS).
Approach Description
Information security The objects of the data are having the
policies of the access control with them
Trusted computing The system shall behave consistently in
the ways that are expected with software
or hardware enforcement.
Protocols of Cryptographic The tools and techniques of the
cryptographic are employed for
preserving privacy.
Figure 1: Cloud delivery model (Yang & Jia, (2013)
Some of the issues have given rise to the anxiety that is tremendous about the risk
that is relate to the security in cloud computing. The organizations have an issue, and they
worry about if they will be able to trust the employees of them or even the organizations need
to be implemented some internal controls that are additional in the privately controlled cloud.
The specific challenges and issues which are related to the cloud based security, pertain to the
three models of the cloud service that are Platform as a Service (PaaS), Software as a Service
(SaaS), Infrastructure as a Service (IaaS).
Approach Description
Information security The objects of the data are having the
policies of the access control with them
Trusted computing The system shall behave consistently in
the ways that are expected with software
or hardware enforcement.
Protocols of Cryptographic The tools and techniques of the
cryptographic are employed for
preserving privacy.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD COMPUTING
Table 1: Privacy enforcement
PaaS:
It is a developing environment that is shaped like the Microsoft Windows Azure
where the deployed applications are controlled by the consumers; however it is not able to
manage the infrastructure that is underlying. The model of the cloud services requires strong
authentication for identification of the users, the ability for supporting the compliance
regulations, audit trail as well as the privacy mandates (Inukollu, Arsi & Ravuri, 2014).
SaaS:
The application of the providers that are running on the infrastructure of the
computing-based cloud is deployed by SaaS. The security risks are increased by it with the
service model. It is so much crucial for the implementation of the policies to identify the
management as well as for accessing the control of the applications.
IaaS:
It is the part the customer provision processing, networks, storage as well as other
resources of the fundamental computing as well as it controls to the storage, deployed an
application and operating systems.
Possible solution:
The traditional model regarding the protection of the data has focused often on the
perimeter and network centric security that is with the devices frequently with some of the
devices like the firewalls as well as the system that is able to detect intrusion (Rong, Nguyen
& Jaatun, 2013). However, this approach is unable to provide protection that is sufficient
against the privileged users, APTs and some of the other insidious security attack types.
Many of the organizations are currently using security and protection information, database
Table 1: Privacy enforcement
PaaS:
It is a developing environment that is shaped like the Microsoft Windows Azure
where the deployed applications are controlled by the consumers; however it is not able to
manage the infrastructure that is underlying. The model of the cloud services requires strong
authentication for identification of the users, the ability for supporting the compliance
regulations, audit trail as well as the privacy mandates (Inukollu, Arsi & Ravuri, 2014).
SaaS:
The application of the providers that are running on the infrastructure of the
computing-based cloud is deployed by SaaS. The security risks are increased by it with the
service model. It is so much crucial for the implementation of the policies to identify the
management as well as for accessing the control of the applications.
IaaS:
It is the part the customer provision processing, networks, storage as well as other
resources of the fundamental computing as well as it controls to the storage, deployed an
application and operating systems.
Possible solution:
The traditional model regarding the protection of the data has focused often on the
perimeter and network centric security that is with the devices frequently with some of the
devices like the firewalls as well as the system that is able to detect intrusion (Rong, Nguyen
& Jaatun, 2013). However, this approach is unable to provide protection that is sufficient
against the privileged users, APTs and some of the other insidious security attack types.
Many of the organizations are currently using security and protection information, database
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CLOUD COMPUTING
audit as well as the solutions that are related to the event management for gathering the
information together.
The strategy is to make sure at first that the data which cannot be read as well as
strong management of the key is offered by the solution (Rewagad & Pawar, 2013). The
solutions of the cloud security incorporate three capabilities that are, Data lockdown, Access
policies, Security intelligence (Zhao, Li & Liu, 2014). An example of the security control
plan is as follows:
Process Type Threat Vulnerability Control Monitoring
Record
FACILITY
and
OPERATIONS
Alarm
Monitoring
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorized
access to a
facility
Security
Procedure
Security
Inspection
Checklist
Motion-
Detection
Devices
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorized
access to the
facility
Security
Procedure
Security
Inspection
Checklist
Video
Surveillance
Facility Theft,
Property
Damage,
Unauthorized
access to a
Security
Procedure
Security
Inspection
audit as well as the solutions that are related to the event management for gathering the
information together.
The strategy is to make sure at first that the data which cannot be read as well as
strong management of the key is offered by the solution (Rewagad & Pawar, 2013). The
solutions of the cloud security incorporate three capabilities that are, Data lockdown, Access
policies, Security intelligence (Zhao, Li & Liu, 2014). An example of the security control
plan is as follows:
Process Type Threat Vulnerability Control Monitoring
Record
FACILITY
and
OPERATIONS
Alarm
Monitoring
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorized
access to a
facility
Security
Procedure
Security
Inspection
Checklist
Motion-
Detection
Devices
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorized
access to the
facility
Security
Procedure
Security
Inspection
Checklist
Video
Surveillance
Facility Theft,
Property
Damage,
Unauthorized
access to a
Security
Procedure
Security
Inspection
8CLOUD COMPUTING
Personal
Injury
facility Checklist
Access -
Employees
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorised
access to
specific areas
within the
facility
Security
Procedure,
Pre-hire
Screening,
Security
Inspection
Checklist
Access -
Visitors
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorized
access to
particular
areas within
the facility
Security
Procedure,
Visitor and
Contractor
Sign in Log,
Visitor and
Contractor
EH&S
Requirements,
Security
Inspection
Checklist
Access -
Contractors
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorized
access to
specific areas
within the
facility
Security
Procedure,
Visitor and
Contractor
Sign in Log,
Visitor and
Contractor
EH&S
Requirements,
Security
Inspection
Checklist
Personal
Injury
facility Checklist
Access -
Employees
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorised
access to
specific areas
within the
facility
Security
Procedure,
Pre-hire
Screening,
Security
Inspection
Checklist
Access -
Visitors
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorized
access to
particular
areas within
the facility
Security
Procedure,
Visitor and
Contractor
Sign in Log,
Visitor and
Contractor
EH&S
Requirements,
Security
Inspection
Checklist
Access -
Contractors
Facility Theft,
Property
Damage,
Personal
Injury
Unauthorized
access to
specific areas
within the
facility
Security
Procedure,
Visitor and
Contractor
Sign in Log,
Visitor and
Contractor
EH&S
Requirements,
Security
Inspection
Checklist
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9CLOUD COMPUTING
Storage of
confidential
documents
Business -
Confidential
Documents
Personal
(HR),
Business
other
Documents
were
stolen
Storage in an
unlocked
cabinet,
Human
Error,
Insufficiency
facility
security
Security
Procedure,
Employee
Handbook,
New Hire
Training
Security
Inspection
Checklist
Storage of
confidential
data
Business -
Confidential
Data on
(Company
Name)
Server
Personal,
Business
other Data
stolen
Storage in an
unlocked
cabinet,
Human
Error,
Insufficiency
facility
security
Security
Procedure,
Employee
Handbook,
New Hire
Training
Security
Inspection
Checklist
CUSTOMER
Storage of
confidential
data on data
bearing
devices
Customer -
Confidential
Data
Personal,
Business
other Data
stolen
Insufficiency
facility
security,
Human
Error,
Unauthorized
access
Security
Procedure
Security
Inspection
Checklist.
Monthly
Facility
Inspection
Checklist
Data Customer - Personal, Insufficiency Security Security
Storage of
confidential
documents
Business -
Confidential
Documents
Personal
(HR),
Business
other
Documents
were
stolen
Storage in an
unlocked
cabinet,
Human
Error,
Insufficiency
facility
security
Security
Procedure,
Employee
Handbook,
New Hire
Training
Security
Inspection
Checklist
Storage of
confidential
data
Business -
Confidential
Data on
(Company
Name)
Server
Personal,
Business
other Data
stolen
Storage in an
unlocked
cabinet,
Human
Error,
Insufficiency
facility
security
Security
Procedure,
Employee
Handbook,
New Hire
Training
Security
Inspection
Checklist
CUSTOMER
Storage of
confidential
data on data
bearing
devices
Customer -
Confidential
Data
Personal,
Business
other Data
stolen
Insufficiency
facility
security,
Human
Error,
Unauthorized
access
Security
Procedure
Security
Inspection
Checklist.
Monthly
Facility
Inspection
Checklist
Data Customer - Personal, Insufficiency Security Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10CLOUD COMPUTING
Sanitization of
confidential
data on data
bearing
devices
Confidential
Data
Business
other Data
stolen
data
sanitisation
procedure,
Human
Error,
insufficient
validation of
data
sanitization
Procedure,
Data
Sanitization
Procedure
Inspection
Checklist.
Monthly
Facility
Inspection
Checklist.
Data
Validation
Log
Physical
Destruction of
confidential
data on data
bearing
devices
Customer -
Confidential
Data
Personal,
Business
other Data
stolen
Insufficiency
data
destruction
procedure,
Human
Error,
insufficient
validation of
data
sanitisation
Security
Procedure,
Data
Destruction
Procedure
Security
Inspection
Checklist.
Monthly
Facility
Inspection
Checklist.
Data
Validation
Log
Conclusion:
The present cloud computing systems are able to pose limitations for the protection of
confidentiality of the user data. Since the sensitive data of the users is presented in the form
of an unencrypted format for the remotely controlled machines that are operated and owned
by the third-party providers. There are so many techniques to protect the data of the users
Sanitization of
confidential
data on data
bearing
devices
Confidential
Data
Business
other Data
stolen
data
sanitisation
procedure,
Human
Error,
insufficient
validation of
data
sanitization
Procedure,
Data
Sanitization
Procedure
Inspection
Checklist.
Monthly
Facility
Inspection
Checklist.
Data
Validation
Log
Physical
Destruction of
confidential
data on data
bearing
devices
Customer -
Confidential
Data
Personal,
Business
other Data
stolen
Insufficiency
data
destruction
procedure,
Human
Error,
insufficient
validation of
data
sanitisation
Security
Procedure,
Data
Destruction
Procedure
Security
Inspection
Checklist.
Monthly
Facility
Inspection
Checklist.
Data
Validation
Log
Conclusion:
The present cloud computing systems are able to pose limitations for the protection of
confidentiality of the user data. Since the sensitive data of the users is presented in the form
of an unencrypted format for the remotely controlled machines that are operated and owned
by the third-party providers. There are so many techniques to protect the data of the users

11CLOUD COMPUTING
from hackers. An approach that is presented for protection of the user data confidentiality
from the providers of the services as well as it ensures that the providers of the services are
not able to collect the confidential data of the users when the data has been stored and
processed in the systems of the cloud computing. When it is the matter of private, public and
hybrid solutions of the cloud, the possibility of the information that is compromised is able to
create tremendous angst. Except for the third providers, the organizations, for managing the
infrastructures of the cloud; however, it is not easy about to grant them the visibility into the
data that are sensitive. The organizations have an issue, and they worry about if they will be
able to trust the employees of them or even the organizations need to implement some
controls internally that are additional in the privately controlled cloud. This deals with the apt
location of the apt choice for the data centres for protecting this from different types of
conditions of the weather, internal threats, physical and fire attacks. If cloud computing is at
risk, then the privacy of the cloud will also be at risk.
from hackers. An approach that is presented for protection of the user data confidentiality
from the providers of the services as well as it ensures that the providers of the services are
not able to collect the confidential data of the users when the data has been stored and
processed in the systems of the cloud computing. When it is the matter of private, public and
hybrid solutions of the cloud, the possibility of the information that is compromised is able to
create tremendous angst. Except for the third providers, the organizations, for managing the
infrastructures of the cloud; however, it is not easy about to grant them the visibility into the
data that are sensitive. The organizations have an issue, and they worry about if they will be
able to trust the employees of them or even the organizations need to implement some
controls internally that are additional in the privately controlled cloud. This deals with the apt
location of the apt choice for the data centres for protecting this from different types of
conditions of the weather, internal threats, physical and fire attacks. If cloud computing is at
risk, then the privacy of the cloud will also be at risk.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




