Cloud Privacy and Security: Threats and Solutions
Added on 2023-06-10
12 Pages2587 Words159 Views
Running head: Cloud privacy and security
Cloud privacy and security
Name of the Student
Name of the University
Author note
Cloud privacy and security
Name of the Student
Name of the University
Author note

2
Cloud privacy and security
Table of Contents
1. Security of Employee Data....................................................................................................3
1.1 Security threat impact:.....................................................................................................4
2. Privacy of Employee Data.....................................................................................................4
3. Digital Identity Issues:...........................................................................................................5
4. Provider Solution Issues:........................................................................................................6
4.1 Security issues with SaaS:................................................................................................6
4.2. Privacy issues with SaaS:................................................................................................7
4.2.1. Impact of privacy issue:...........................................................................................8
5. Data Sensitivity......................................................................................................................8
Cloud privacy and security
Table of Contents
1. Security of Employee Data....................................................................................................3
1.1 Security threat impact:.....................................................................................................4
2. Privacy of Employee Data.....................................................................................................4
3. Digital Identity Issues:...........................................................................................................5
4. Provider Solution Issues:........................................................................................................6
4.1 Security issues with SaaS:................................................................................................6
4.2. Privacy issues with SaaS:................................................................................................7
4.2.1. Impact of privacy issue:...........................................................................................8
5. Data Sensitivity......................................................................................................................8

3
Cloud privacy and security
1. Security of Employee Data
While considering the in-house HR database for storing the employee data there are
two major threats for the security of the data:
Data backup:
The data backup is a major issue when considering the security of the data. When the
data is stored in the database there should be a proper data backup. Now the problem with the
local host is that it comes with a limited storage as the cost of storage is quite huge. Due to
limitation in storage, the data is often kept as it is without proper backup. Now the data stored
into the database is subject to corruption due to data hack and several other issue (Cai et al.,
2018). Now if anyhow the data is corrupted and if there is not proper backup for the data,
then the data is not possible to retrieve. Hence it process a strong security threat to the
database.
Email phishing:
The user of the database might be tweaked into accessing email that might contain
malicious code, which when run on the system will provide the hacker full administration on
the system (Jackson, 2016). Once the administrative access is provided, it is possible to
modify the system setting on which the database and the server is running. Now due to less
technical expertise, this kind of things happens as it becomes difficult for the users to identify
which email is malicious or not. Hence this a security challenge for the system.
SQL injection:
Cloud privacy and security
1. Security of Employee Data
While considering the in-house HR database for storing the employee data there are
two major threats for the security of the data:
Data backup:
The data backup is a major issue when considering the security of the data. When the
data is stored in the database there should be a proper data backup. Now the problem with the
local host is that it comes with a limited storage as the cost of storage is quite huge. Due to
limitation in storage, the data is often kept as it is without proper backup. Now the data stored
into the database is subject to corruption due to data hack and several other issue (Cai et al.,
2018). Now if anyhow the data is corrupted and if there is not proper backup for the data,
then the data is not possible to retrieve. Hence it process a strong security threat to the
database.
Email phishing:
The user of the database might be tweaked into accessing email that might contain
malicious code, which when run on the system will provide the hacker full administration on
the system (Jackson, 2016). Once the administrative access is provided, it is possible to
modify the system setting on which the database and the server is running. Now due to less
technical expertise, this kind of things happens as it becomes difficult for the users to identify
which email is malicious or not. Hence this a security challenge for the system.
SQL injection:

4
Cloud privacy and security
SQL injection is one of the common threats for the database running on SQL server. It
is a common method for gaining access to the database server. The SQL injection is aimed
for stealing user name and password that helps to modify the database and the contained data
(Jukic, 2016). The access to the database include permission for both read and write. The
SQL injection is quite popular among the hackers as it is easier to implement and often works
well with database where the security methods are not that strong.
Timely update:
Timely update is another major issue with the database security. The problems with
the in-house database is that the servers are not updated timely. Without updated security
patches the server becomes vulnerable to hacks (Grycuk, 2015).
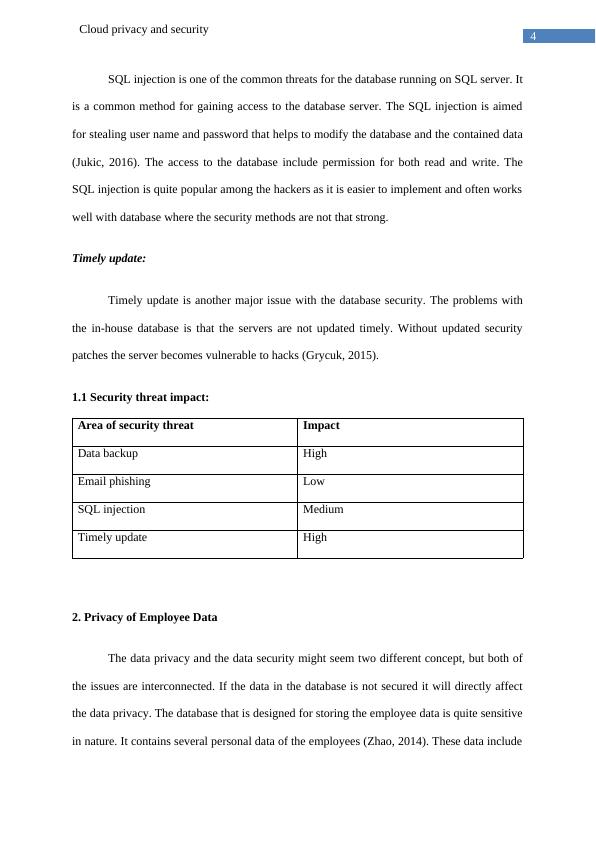
1.1 Security threat impact:
Area of security threat Impact
Data backup High
Email phishing Low
SQL injection Medium
Timely update High
2. Privacy of Employee Data
The data privacy and the data security might seem two different concept, but both of
the issues are interconnected. If the data in the database is not secured it will directly affect
the data privacy. The database that is designed for storing the employee data is quite sensitive
in nature. It contains several personal data of the employees (Zhao, 2014). These data include
Cloud privacy and security
SQL injection is one of the common threats for the database running on SQL server. It
is a common method for gaining access to the database server. The SQL injection is aimed
for stealing user name and password that helps to modify the database and the contained data
(Jukic, 2016). The access to the database include permission for both read and write. The
SQL injection is quite popular among the hackers as it is easier to implement and often works
well with database where the security methods are not that strong.
Timely update:
Timely update is another major issue with the database security. The problems with
the in-house database is that the servers are not updated timely. Without updated security
patches the server becomes vulnerable to hacks (Grycuk, 2015).
1.1 Security threat impact:
Area of security threat Impact
Data backup High
Email phishing Low
SQL injection Medium
Timely update High
2. Privacy of Employee Data
The data privacy and the data security might seem two different concept, but both of
the issues are interconnected. If the data in the database is not secured it will directly affect
the data privacy. The database that is designed for storing the employee data is quite sensitive
in nature. It contains several personal data of the employees (Zhao, 2014). These data include
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
ITC568 - Cloud Privacy and Securitylg...
|18
|2193
|34
Analysis of It Security And Managementlg...
|8
|832
|14
Ways of Attacking a Web Application in PHP: SQL Injection, XSS, Session Hijacking, Directory Traversal, and Remote File Inclusionlg...
|9
|1493
|176
Security and Privacy of Employee Data - Deskliblg...
|25
|6301
|272
Cyber Security: Vulnerabilities, Exploitation, and Security Controlslg...
|10
|2384
|453
Security threats in cloud computing and preventive methodslg...
|9
|2288
|116
