Cloud Security and Privacy Assignment 2022
26 Pages5018 Words14 Views
Added on 2022-10-11
Cloud Security and Privacy Assignment 2022
Added on 2022-10-11
ShareRelated Documents
Running head: CLOUD SECURITY AND PRIVACY
Cloud Security and Privacy
Name of the Student
Name of the University
Author’s Note:
Cloud Security and Privacy
Name of the Student
Name of the University
Author’s Note:

1
CLOUD SECURITY AND PRIVACY
Table of Contents
1. Introduction............................................................................................................................2
2. Security of Employee Data....................................................................................................2
3. Privacy of Employee Data...................................................................................................10
4. Digital Identity Issue............................................................................................................19
5. Conclusion............................................................................................................................20
References................................................................................................................................22
CLOUD SECURITY AND PRIVACY
Table of Contents
1. Introduction............................................................................................................................2
2. Security of Employee Data....................................................................................................2
3. Privacy of Employee Data...................................................................................................10
4. Digital Identity Issue............................................................................................................19
5. Conclusion............................................................................................................................20
References................................................................................................................................22

2
CLOUD SECURITY AND PRIVACY
1. Introduction
Cloud computing technology eventually is helpful for the on demand accessibility as
well as availability of all kinds of computer based resources. The accessibility is being
initiated with absolutely zero involvement of the direct users’ management. The respective
clouds majorly comprise of some of the most distinctive and important functionalities that are
being dispersed to different locations from the centralized users (Baron et al., 2019). Thee
clouds are also not restricted to any one organization or company and they are available to
numerous organizations. Digital identity is the type of information about any particular
person, enterprise as well as electronic devices that help in remaining online. These are
identifiers, which could be referred to as responsible to detect each and every device and
person involved.
The sensitive information is being needed to be kept safe and digital identity has the
capability of easily providing security to such information without any type of complexities
or issues (Singh & Chatterjee, 2017). DAS can easily provide several services and products to
the various different departments of the respective government. The main services of this
organization are payroll management, contractor, procurement management, HR
management and several others. Recently, the organizational management has taken the
decision of shifting to the approach of Shared Services so that they would be able to secure
their confidential information easily. The report will be describing about the privacy as well
as security issues that could be often faced within the company of DAS. Various mitigation
strategies would also be described for these threats.
2. Security of Employee Data
2.1 Existing security threats to Employee data
CLOUD SECURITY AND PRIVACY
1. Introduction
Cloud computing technology eventually is helpful for the on demand accessibility as
well as availability of all kinds of computer based resources. The accessibility is being
initiated with absolutely zero involvement of the direct users’ management. The respective
clouds majorly comprise of some of the most distinctive and important functionalities that are
being dispersed to different locations from the centralized users (Baron et al., 2019). Thee
clouds are also not restricted to any one organization or company and they are available to
numerous organizations. Digital identity is the type of information about any particular
person, enterprise as well as electronic devices that help in remaining online. These are
identifiers, which could be referred to as responsible to detect each and every device and
person involved.
The sensitive information is being needed to be kept safe and digital identity has the
capability of easily providing security to such information without any type of complexities
or issues (Singh & Chatterjee, 2017). DAS can easily provide several services and products to
the various different departments of the respective government. The main services of this
organization are payroll management, contractor, procurement management, HR
management and several others. Recently, the organizational management has taken the
decision of shifting to the approach of Shared Services so that they would be able to secure
their confidential information easily. The report will be describing about the privacy as well
as security issues that could be often faced within the company of DAS. Various mitigation
strategies would also be described for these threats.
2. Security of Employee Data
2.1 Existing security threats to Employee data

3
CLOUD SECURITY AND PRIVACY
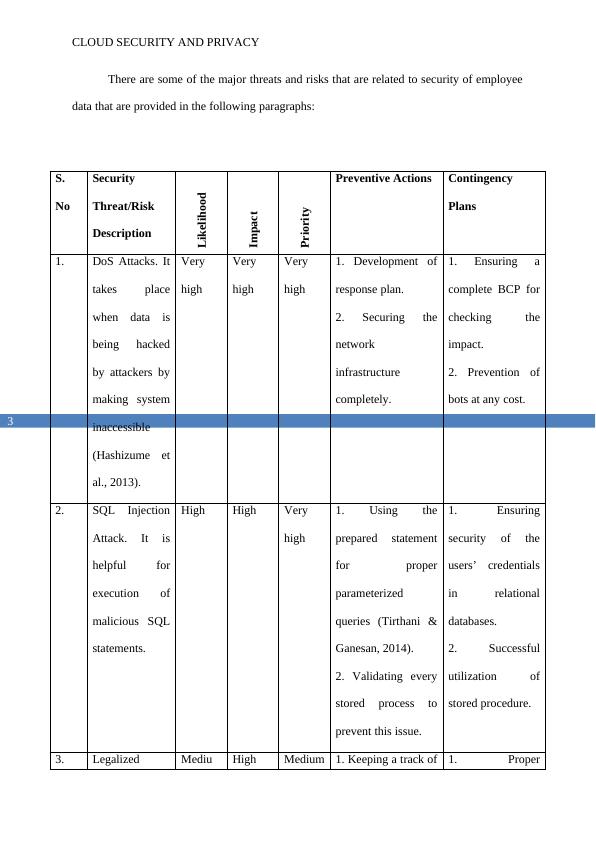
There are some of the major threats and risks that are related to security of employee
data that are provided in the following paragraphs:
S.
No
Security
Threat/Risk
Description
Likelihood
Impact
Priority
Preventive Actions Contingency
Plans
1. DoS Attacks. It
takes place
when data is
being hacked
by attackers by
making system
inaccessible
(Hashizume et
al., 2013).
Very
high
Very
high
Very
high
1. Development of
response plan.
2. Securing the
network
infrastructure
completely.
1. Ensuring a
complete BCP for
checking the
impact.
2. Prevention of
bots at any cost.
2. SQL Injection
Attack. It is
helpful for
execution of
malicious SQL
statements.
High High Very
high
1. Using the
prepared statement
for proper
parameterized
queries (Tirthani &
Ganesan, 2014).
2. Validating every
stored process to
prevent this issue.
1. Ensuring
security of the
users’ credentials
in relational
databases.
2. Successful
utilization of
stored procedure.
3. Legalized Mediu High Medium 1. Keeping a track of 1. Proper
CLOUD SECURITY AND PRIVACY
There are some of the major threats and risks that are related to security of employee
data that are provided in the following paragraphs:
S.
No
Security
Threat/Risk
Description
Likelihood
Impact
Priority
Preventive Actions Contingency
Plans
1. DoS Attacks. It
takes place
when data is
being hacked
by attackers by
making system
inaccessible
(Hashizume et
al., 2013).
Very
high
Very
high
Very
high
1. Development of
response plan.
2. Securing the
network
infrastructure
completely.
1. Ensuring a
complete BCP for
checking the
impact.
2. Prevention of
bots at any cost.
2. SQL Injection
Attack. It is
helpful for
execution of
malicious SQL
statements.
High High Very
high
1. Using the
prepared statement
for proper
parameterized
queries (Tirthani &
Ganesan, 2014).
2. Validating every
stored process to
prevent this issue.
1. Ensuring
security of the
users’ credentials
in relational
databases.
2. Successful
utilization of
stored procedure.
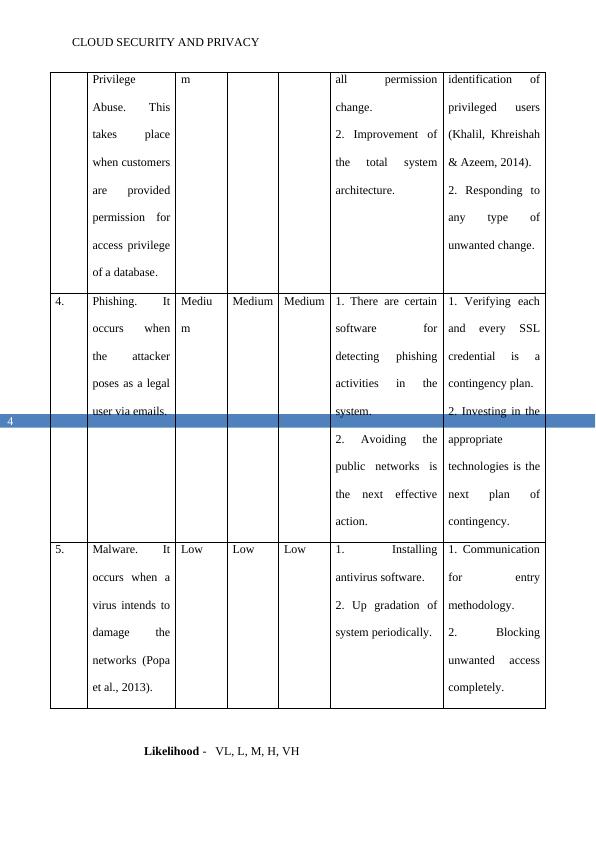
3. Legalized Mediu High Medium 1. Keeping a track of 1. Proper
4
CLOUD SECURITY AND PRIVACY
Privilege
Abuse. This
takes place
when customers
are provided
permission for
access privilege
of a database.
m all permission
change.
2. Improvement of
the total system
architecture.
identification of
privileged users
(Khalil, Khreishah
& Azeem, 2014).
2. Responding to
any type of
unwanted change.
4. Phishing. It
occurs when
the attacker
poses as a legal
user via emails.
Mediu
m
Medium Medium 1. There are certain
software for
detecting phishing
activities in the
system.
2. Avoiding the
public networks is
the next effective
action.
1. Verifying each
and every SSL
credential is a
contingency plan.
2. Investing in the
appropriate
technologies is the
next plan of
contingency.
5. Malware. It
occurs when a
virus intends to
damage the
networks (Popa
et al., 2013).
Low Low Low 1. Installing
antivirus software.
2. Up gradation of
system periodically.
1. Communication
for entry
methodology.
2. Blocking
unwanted access
completely.
Likelihood - VL, L, M, H, VH
CLOUD SECURITY AND PRIVACY
Privilege
Abuse. This
takes place
when customers
are provided
permission for
access privilege
of a database.
m all permission
change.
2. Improvement of
the total system
architecture.
identification of
privileged users
(Khalil, Khreishah
& Azeem, 2014).
2. Responding to
any type of
unwanted change.
4. Phishing. It
occurs when
the attacker
poses as a legal
user via emails.
Mediu
m
Medium Medium 1. There are certain
software for
detecting phishing
activities in the
system.
2. Avoiding the
public networks is
the next effective
action.
1. Verifying each
and every SSL
credential is a
contingency plan.
2. Investing in the
appropriate
technologies is the
next plan of
contingency.
5. Malware. It
occurs when a
virus intends to
damage the
networks (Popa
et al., 2013).
Low Low Low 1. Installing
antivirus software.
2. Up gradation of
system periodically.
1. Communication
for entry
methodology.
2. Blocking
unwanted access
completely.
Likelihood - VL, L, M, H, VH
5
CLOUD SECURITY AND PRIVACY
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
A detailed description of these threats is provided in the following paragraphs:
a) DoS Attacks: It causes subsequent destruction by allowing the hacker to get into
the machine and eventually access the databases.
b) Legalized Privilege Abuses: The customers get the opportunity of exploiting
numerous kinds of privileges for malicious purposes (Chang, Kuo & Ramachandran, 2016).
c) SQL Injection Attack: Code injections take place within the databases through text
message or email.
d) Phishing: A hacker gets himself as the legal user through text message or email.
e) Malware: This risk can cause subsequent destructions in the systems, servers or
even networks.
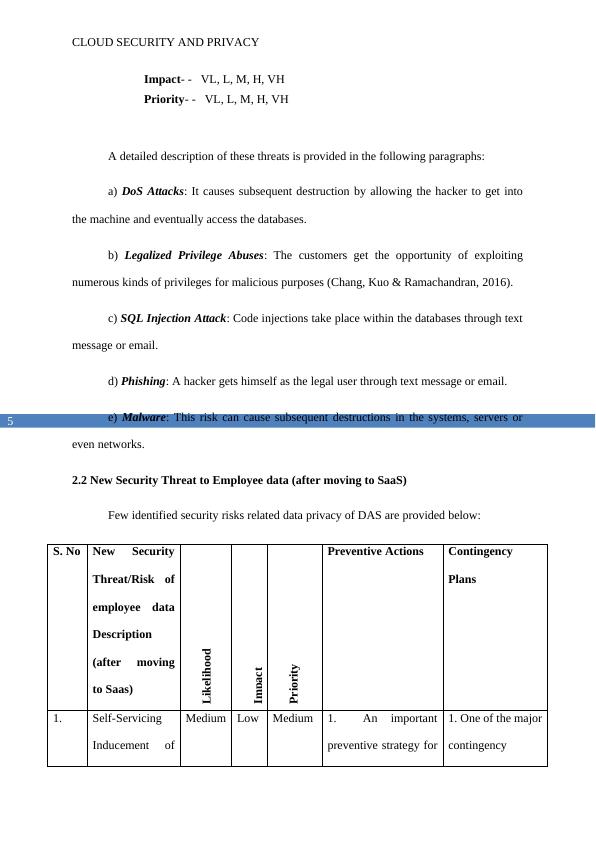
2.2 New Security Threat to Employee data (after moving to SaaS)
Few identified security risks related data privacy of DAS are provided below:
S. No New Security
Threat/Risk of
employee data
Description
(after moving
to Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency
Plans
1. Self-Servicing
Inducement of
Medium Low Medium 1. An important
preventive strategy for
1. One of the major
contingency
CLOUD SECURITY AND PRIVACY
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
A detailed description of these threats is provided in the following paragraphs:
a) DoS Attacks: It causes subsequent destruction by allowing the hacker to get into
the machine and eventually access the databases.
b) Legalized Privilege Abuses: The customers get the opportunity of exploiting
numerous kinds of privileges for malicious purposes (Chang, Kuo & Ramachandran, 2016).
c) SQL Injection Attack: Code injections take place within the databases through text
message or email.
d) Phishing: A hacker gets himself as the legal user through text message or email.
e) Malware: This risk can cause subsequent destructions in the systems, servers or
even networks.
2.2 New Security Threat to Employee data (after moving to SaaS)
Few identified security risks related data privacy of DAS are provided below:
S. No New Security
Threat/Risk of
employee data
Description
(after moving
to Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency
Plans
1. Self-Servicing
Inducement of
Medium Low Medium 1. An important
preventive strategy for
1. One of the major
contingency
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Cloud Security and Privacylg...
|27
|5040
|357
Cloud Privacy and Security: Threats and Solutionslg...
|12
|2587
|159
Security and Privacy of Employee Data | Reportlg...
|34
|6311
|63
Security of Employee Data Question 2022lg...
|16
|5147
|28
Security and Privacy of Employee Data - Deskliblg...
|25
|6301
|272
Cloud Security Report 2022lg...
|23
|6412
|11
