CO4512 Risk Assessment: Information Security Management for Cloud XYZ
VerifiedAdded on 2023/06/13
|18
|3419
|275
Report
AI Summary
This report details a risk assessment conducted for Cloud XYZ, UK, focusing on securing storage and virtual services. It emphasizes mitigating data loss, preventing unauthorized access, and identifying personnel responsible for risk management. The assessment utilizes the organization's network diagram to analyze vulnerabilities and improve overall security, particularly within the server and demilitarized zone. Network resources are categorized into primary and secondary assets, with threats analyzed for their potential impact. The report also references ISO/IEC 27001 standards for information security management and includes recommendations for enhancing the network's security posture.

Running head: INFORMATION SECURITY MANAGEMENT
Information Security Management
Name of the Student
Name of the University
Author’s Note
Information Security Management
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY MANAGEMENT
Abstract
The report is prepared for the development of the security system for the Cloud XYZ, UK for securing
the storage and the virtual service for the customer connected with the organization. The loss of the
organization should be mitigated with the prevention of the malfunction and modification of the
data for prevention of the illegal user to access the resources of the organization. The personnel
responsible with the risk should be identified for the identification of the roles and responsibility for
the assessment of the risk. The network diagram of the organization is used for the analysis of the
risk and vulnerability such that the risk can be mitigated for the improvement of the security of the
current network framework. The security of the server and the demilitarized zone is analysed for
protecting the resources of the organization. The network resources are categorized as primary and
secondary assets and the threats for each of the asset are analysed for the identification of its
impact on the security of the organizational network.
INFORMATION SECURITY MANAGEMENT
Abstract
The report is prepared for the development of the security system for the Cloud XYZ, UK for securing
the storage and the virtual service for the customer connected with the organization. The loss of the
organization should be mitigated with the prevention of the malfunction and modification of the
data for prevention of the illegal user to access the resources of the organization. The personnel
responsible with the risk should be identified for the identification of the roles and responsibility for
the assessment of the risk. The network diagram of the organization is used for the analysis of the
risk and vulnerability such that the risk can be mitigated for the improvement of the security of the
current network framework. The security of the server and the demilitarized zone is analysed for
protecting the resources of the organization. The network resources are categorized as primary and
secondary assets and the threats for each of the asset are analysed for the identification of its
impact on the security of the organizational network.

2
INFORMATION SECURITY MANAGEMENT
Table of Contents
Introduction...........................................................................................................................................3
Risk Assessment....................................................................................................................................4
Owner Specification...........................................................................................................................5
Assets................................................................................................................................................6
Threats for each assets......................................................................................................................8
Vulnerability for each assets............................................................................................................11
Risk Likelihood.................................................................................................................................12
Risk Impact table.............................................................................................................................12
Risk Identification with level............................................................................................................13
Summary and Recommendations........................................................................................................15
Bibliography.........................................................................................................................................16
INFORMATION SECURITY MANAGEMENT
Table of Contents
Introduction...........................................................................................................................................3
Risk Assessment....................................................................................................................................4
Owner Specification...........................................................................................................................5
Assets................................................................................................................................................6
Threats for each assets......................................................................................................................8
Vulnerability for each assets............................................................................................................11
Risk Likelihood.................................................................................................................................12
Risk Impact table.............................................................................................................................12
Risk Identification with level............................................................................................................13
Summary and Recommendations........................................................................................................15
Bibliography.........................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY MANAGEMENT
Introduction
There are different ISO standards that are used as a baseline for the security of the
information in an organization. The ISO standards is used for avoiding breaches in the network,
reassuring the customers, gaining an edge and access new market opportunities. It is internationally
recognized and applied for management of the safety practices and used as a systematic approach
for increasing reliability and enforcement of the security controls. There are different standards of
IOS such as ISO/IEC 17025, ISO 9001, ISO/IEC 27001 and ISO 50001. The standards are used for
different purpose such as ISO/IEC 17025 is used for testing and calibration, ISO 9001 is used for
management of the quality, ISO/IEC 27001 is used for management of the information security and
ISO 50001 is used for the management of energy.
Thus for the analysis of the security of the CloudXYZ ISO/IEC 27001 is applied and it helps the
organization to securely store the information. The use if the ISO standard helps in increase the
security of the data residing in the cloud platform. For the development of the network framework
an authentication server should be used for permitting the user to connect with the database. The
user needs to authenticate with the system for the management of the virtual server and ISO/IEC
27001 is used for the identification of the potential risk associated with the system. The privacy
policy is assessed and the risk associated with it is eliminated for meeting the standard of the
information security management. For analysis of the risk the following steps are performed and are
given below:
Step#1: Analysis of the risk associated with the system
Step#2: Evaluation of the risk management system
Step#3: Selection of the risk management methodology
Step#4: Implementation of the risk management strategy and techniques
Step#5: Monitoring the current system and eliminate the errors for reducing the risk
INFORMATION SECURITY MANAGEMENT
Introduction
There are different ISO standards that are used as a baseline for the security of the
information in an organization. The ISO standards is used for avoiding breaches in the network,
reassuring the customers, gaining an edge and access new market opportunities. It is internationally
recognized and applied for management of the safety practices and used as a systematic approach
for increasing reliability and enforcement of the security controls. There are different standards of
IOS such as ISO/IEC 17025, ISO 9001, ISO/IEC 27001 and ISO 50001. The standards are used for
different purpose such as ISO/IEC 17025 is used for testing and calibration, ISO 9001 is used for
management of the quality, ISO/IEC 27001 is used for management of the information security and
ISO 50001 is used for the management of energy.
Thus for the analysis of the security of the CloudXYZ ISO/IEC 27001 is applied and it helps the
organization to securely store the information. The use if the ISO standard helps in increase the
security of the data residing in the cloud platform. For the development of the network framework
an authentication server should be used for permitting the user to connect with the database. The
user needs to authenticate with the system for the management of the virtual server and ISO/IEC
27001 is used for the identification of the potential risk associated with the system. The privacy
policy is assessed and the risk associated with it is eliminated for meeting the standard of the
information security management. For analysis of the risk the following steps are performed and are
given below:
Step#1: Analysis of the risk associated with the system
Step#2: Evaluation of the risk management system
Step#3: Selection of the risk management methodology
Step#4: Implementation of the risk management strategy and techniques
Step#5: Monitoring the current system and eliminate the errors for reducing the risk
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
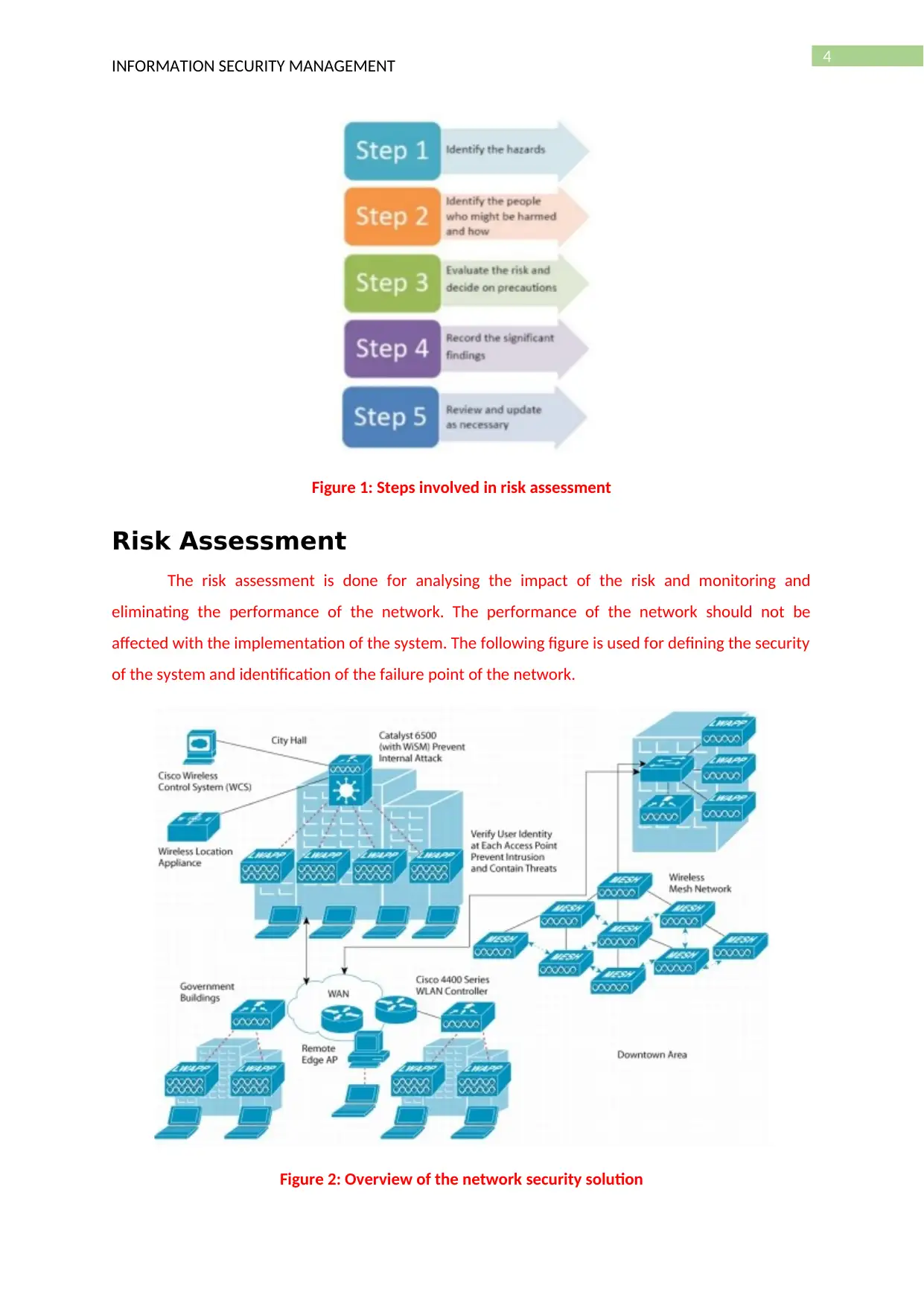
4
INFORMATION SECURITY MANAGEMENT
Figure 1: Steps involved in risk assessment
Risk Assessment
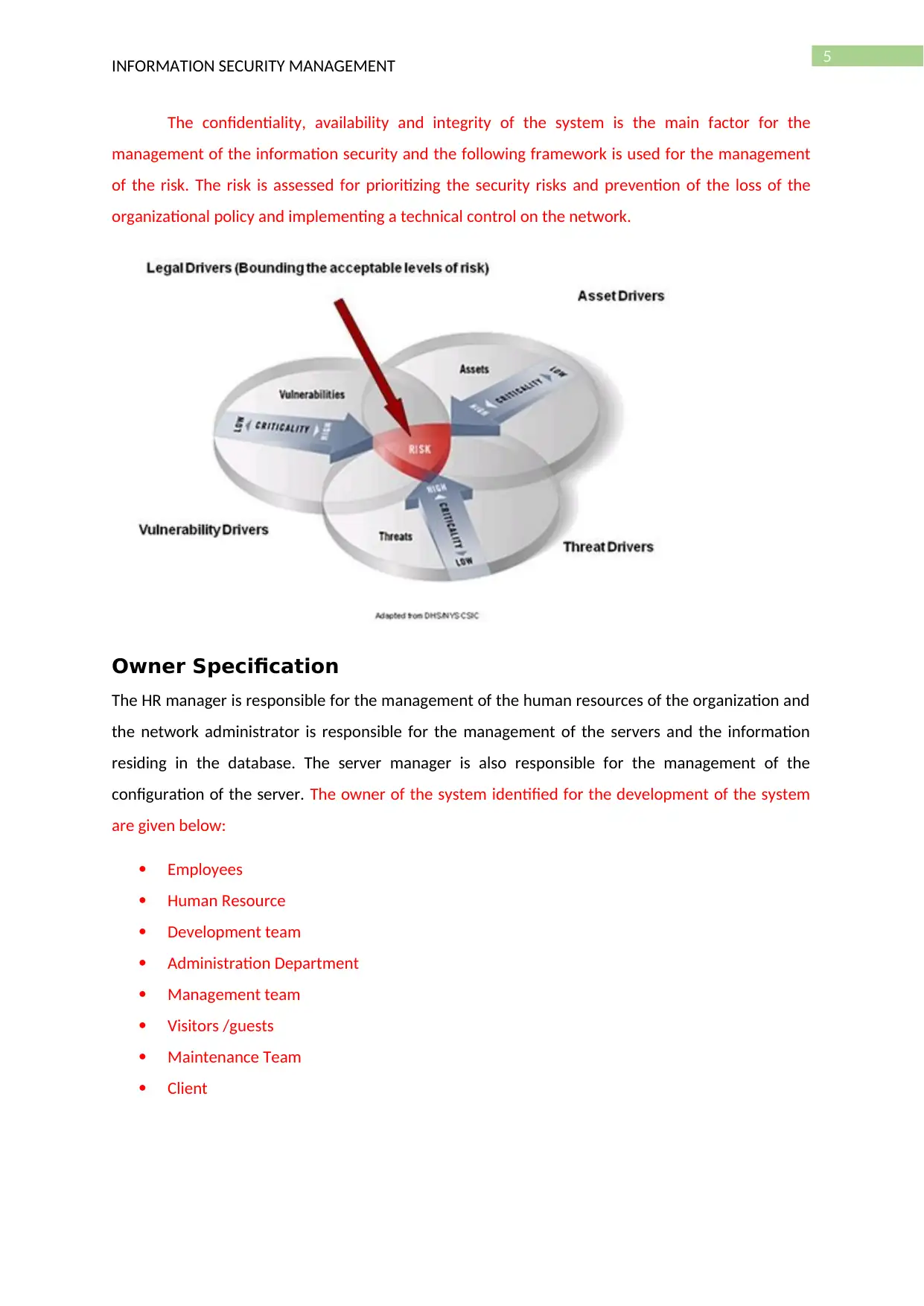
The risk assessment is done for analysing the impact of the risk and monitoring and
eliminating the performance of the network. The performance of the network should not be
affected with the implementation of the system. The following figure is used for defining the security
of the system and identification of the failure point of the network.
Figure 2: Overview of the network security solution
INFORMATION SECURITY MANAGEMENT
Figure 1: Steps involved in risk assessment
Risk Assessment
The risk assessment is done for analysing the impact of the risk and monitoring and
eliminating the performance of the network. The performance of the network should not be
affected with the implementation of the system. The following figure is used for defining the security
of the system and identification of the failure point of the network.
Figure 2: Overview of the network security solution
5
INFORMATION SECURITY MANAGEMENT
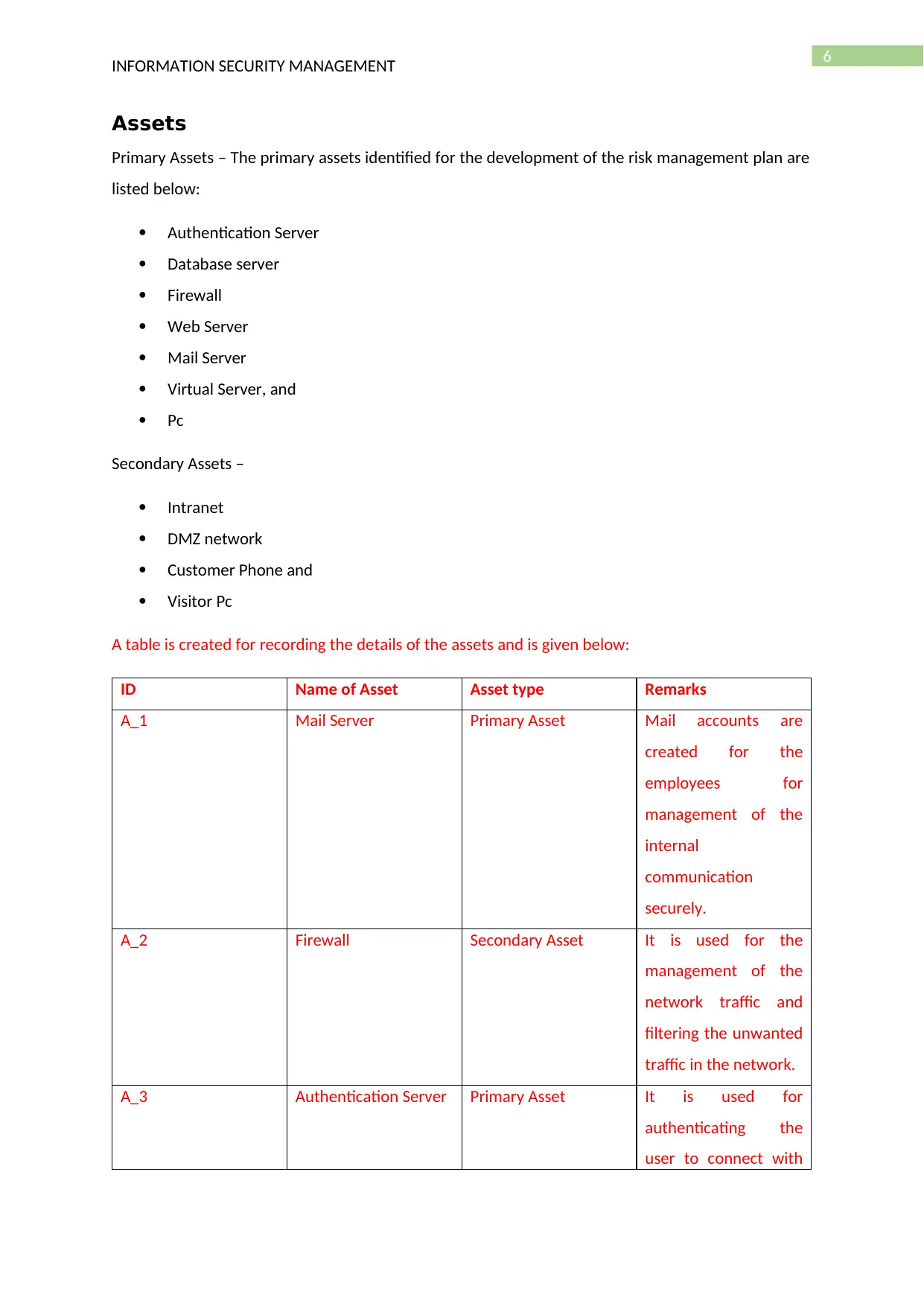
The confidentiality, availability and integrity of the system is the main factor for the
management of the information security and the following framework is used for the management
of the risk. The risk is assessed for prioritizing the security risks and prevention of the loss of the
organizational policy and implementing a technical control on the network.
Owner Specification
The HR manager is responsible for the management of the human resources of the organization and
the network administrator is responsible for the management of the servers and the information
residing in the database. The server manager is also responsible for the management of the
configuration of the server. The owner of the system identified for the development of the system
are given below:
Employees
Human Resource
Development team
Administration Department
Management team
Visitors /guests
Maintenance Team
Client
INFORMATION SECURITY MANAGEMENT
The confidentiality, availability and integrity of the system is the main factor for the
management of the information security and the following framework is used for the management
of the risk. The risk is assessed for prioritizing the security risks and prevention of the loss of the
organizational policy and implementing a technical control on the network.
Owner Specification
The HR manager is responsible for the management of the human resources of the organization and
the network administrator is responsible for the management of the servers and the information
residing in the database. The server manager is also responsible for the management of the
configuration of the server. The owner of the system identified for the development of the system
are given below:
Employees
Human Resource
Development team
Administration Department
Management team
Visitors /guests
Maintenance Team
Client
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INFORMATION SECURITY MANAGEMENT
Assets
Primary Assets – The primary assets identified for the development of the risk management plan are
listed below:
Authentication Server
Database server
Firewall
Web Server
Mail Server
Virtual Server, and
Pc
Secondary Assets –
Intranet
DMZ network
Customer Phone and
Visitor Pc
A table is created for recording the details of the assets and is given below:
ID Name of Asset Asset type Remarks
A_1 Mail Server Primary Asset Mail accounts are
created for the
employees for
management of the
internal
communication
securely.
A_2 Firewall Secondary Asset It is used for the
management of the
network traffic and
filtering the unwanted
traffic in the network.
A_3 Authentication Server Primary Asset It is used for
authenticating the
user to connect with
INFORMATION SECURITY MANAGEMENT
Assets
Primary Assets – The primary assets identified for the development of the risk management plan are
listed below:
Authentication Server
Database server
Firewall
Web Server
Mail Server
Virtual Server, and
Pc
Secondary Assets –
Intranet
DMZ network
Customer Phone and
Visitor Pc
A table is created for recording the details of the assets and is given below:
ID Name of Asset Asset type Remarks
A_1 Mail Server Primary Asset Mail accounts are
created for the
employees for
management of the
internal
communication
securely.
A_2 Firewall Secondary Asset It is used for the
management of the
network traffic and
filtering the unwanted
traffic in the network.
A_3 Authentication Server Primary Asset It is used for
authenticating the
user to connect with
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INFORMATION SECURITY MANAGEMENT
the database and
store the log details
for the user accessing
the resources of the
organization.
A_4 Web Server Primary Asset It is used for hosting
the website of the
organization and
storing the details of
the organization.
A_5 Admin PC Primary Asset The Admin Pc is used
for the management
of the server and the
service used for the
configuration of the
network solution.
A_6 Customer DB Primary Asset The customer
database is used for
recording the details
of the customer and
use it for
improvement of the
current business
process.
A_7 HR PC Primary Asset It is used for the
management of the
employees and the
customer information.
A_8 Virtual Server Secondary Asset It is used for the
management of the
loads and serve more
request from the
users.
A_9 Cloud Storage Primary Asset The cloud storage is
INFORMATION SECURITY MANAGEMENT
the database and
store the log details
for the user accessing
the resources of the
organization.
A_4 Web Server Primary Asset It is used for hosting
the website of the
organization and
storing the details of
the organization.
A_5 Admin PC Primary Asset The Admin Pc is used
for the management
of the server and the
service used for the
configuration of the
network solution.
A_6 Customer DB Primary Asset The customer
database is used for
recording the details
of the customer and
use it for
improvement of the
current business
process.
A_7 HR PC Primary Asset It is used for the
management of the
employees and the
customer information.
A_8 Virtual Server Secondary Asset It is used for the
management of the
loads and serve more
request from the
users.
A_9 Cloud Storage Primary Asset The cloud storage is
8
INFORMATION SECURITY MANAGEMENT
used for uploading the
data in the cloud
servers and provide
access to the users to
access the data from
remote location.
A_10 Visitor PC Secondary Asset It is used for allowing
the visitors to give
access to the core
network and
recording the details.
A_11 Mobile Device Secondary Device It is used for
connecting with the
wireless network of
the organization and
access the information
stored in the server of
the organization.
A_12 Staff PC Primary Asset The staff PC are used
for the management
of the technical works,
data of the enterprise
and management of
the information.
Threats for each assets
Name of the Asset Threat Level Source
Mail Server Malware High level Receiving malicious
emails from unknown
sources
Spam Medium level Outside source is used
for implementation of
the spam mails
Social Engineering Low level It is used for getting
INFORMATION SECURITY MANAGEMENT
used for uploading the
data in the cloud
servers and provide
access to the users to
access the data from
remote location.
A_10 Visitor PC Secondary Asset It is used for allowing
the visitors to give
access to the core
network and
recording the details.
A_11 Mobile Device Secondary Device It is used for
connecting with the
wireless network of
the organization and
access the information
stored in the server of
the organization.
A_12 Staff PC Primary Asset The staff PC are used
for the management
of the technical works,
data of the enterprise
and management of
the information.
Threats for each assets
Name of the Asset Threat Level Source
Mail Server Malware High level Receiving malicious
emails from unknown
sources
Spam Medium level Outside source is used
for implementation of
the spam mails
Social Engineering Low level It is used for getting
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
INFORMATION SECURITY MANAGEMENT
the login credentials
of the user by the
hackers
Firewall Shared secret High level The system can be
hacked from outside
sources
Phishing attack Medium level It can occur from
hacker for duplicating
the identity of the
user
Domain Hijacking Low level It is used for getting
the access of the data
traffic by the
outsiders.
Authentication Server Dictionary attack High level It is used by the
hacker for trying
different combination
of password
Password
authentication
Medium level Outsiders accessing
the server from
remote location.
Brute force attack Medium level Outsider from remote
location
Web Server Open relay attacks High level Outsider from any
place
Cross Site Scripting Medium level Outsider from any
place
SQL injection attacks Low level Outsider from any
place
Admin PC Ransomware High level From external device
and internet
Malware Medium level From external device
and internet
Spam Low level From external device
INFORMATION SECURITY MANAGEMENT
the login credentials
of the user by the
hackers
Firewall Shared secret High level The system can be
hacked from outside
sources
Phishing attack Medium level It can occur from
hacker for duplicating
the identity of the
user
Domain Hijacking Low level It is used for getting
the access of the data
traffic by the
outsiders.
Authentication Server Dictionary attack High level It is used by the
hacker for trying
different combination
of password
Password
authentication
Medium level Outsiders accessing
the server from
remote location.
Brute force attack Medium level Outsider from remote
location
Web Server Open relay attacks High level Outsider from any
place
Cross Site Scripting Medium level Outsider from any
place
SQL injection attacks Low level Outsider from any
place
Admin PC Ransomware High level From external device
and internet
Malware Medium level From external device
and internet
Spam Low level From external device
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
INFORMATION SECURITY MANAGEMENT
and emails
Customer DB Rainbow table High level
Passphrase, and Medium level
Ownership factor Low level
HR PC Ransomware High level From external device
and internet
Malware High level From external device
and internet
Spam Low level From external device
and emails
Virtual Server Lack of integration of
application
High level Internal sources and
hackers
Inadequate recovery
point
Low level Internal sources and
hackers
Restoring granularity Low level Internal sources and
hackers
Cloud Storage Hacking High level Outside hackers for
accessing the sensitive
information
Visitor PC Ransomware Low level From external device
and internet
Malware Low level From external device
and internet
Spam High level From external device
and emails
Mobile Device System hacking High level hackers
Virus High level Internet and external
sources
Spoofing attack High level Hacker and external
sources
Staff PC Ransomware High level From external device
and internet
Malware Medium level From external device
and internet
INFORMATION SECURITY MANAGEMENT
and emails
Customer DB Rainbow table High level
Passphrase, and Medium level
Ownership factor Low level
HR PC Ransomware High level From external device
and internet
Malware High level From external device
and internet
Spam Low level From external device
and emails
Virtual Server Lack of integration of
application
High level Internal sources and
hackers
Inadequate recovery
point
Low level Internal sources and
hackers
Restoring granularity Low level Internal sources and
hackers
Cloud Storage Hacking High level Outside hackers for
accessing the sensitive
information
Visitor PC Ransomware Low level From external device
and internet
Malware Low level From external device
and internet
Spam High level From external device
and emails
Mobile Device System hacking High level hackers
Virus High level Internet and external
sources
Spoofing attack High level Hacker and external
sources
Staff PC Ransomware High level From external device
and internet
Malware Medium level From external device
and internet

11
INFORMATION SECURITY MANAGEMENT
Spam Low level From external device
and emails
Vulnerability for each assets
Virtual Server
CVE-Modified – The JSON vulnerability and the XML vulnerability are analysed for analysing the
security flaws that are used as a link for the reference and identification of the weakness of the
network configuration.
Mail server
CVE-Recent – It is used for interaction with the security standard practice and it differs from the
traditional attacks for the exploitation of the system and the software. The social engineering attacks
are used by the hackers to gain the access of the confidential information. It consists of baiting,
phasing, pretexting and spear phasing. False communication is created with the victim using chats,
phone calls, spoofed website for gathering personal information and using it for illegal use.
PC
CVE-2018 – The dictionary attacks can be used by the attacker to determine the decryption or the
passphrase key and gain the access of the computer. The brute force attack are used for searching
password systematically and rainbow table are used for reducing the preparation time by analysing
the pre computerised dictionary and reducing the storage requirement.
Web server
CVE-2017 – cross site scripting are used for identification of the flaws in the network and
identification of the web application uses. The cookies can be accessed by the malicious codes for
rewriting the content and using sql injection attacks for modification of the content of the servers.
Firewall
CVE-2016 – It is used as a cryptography for securing the communication and establishing the
communication between the different users. The key agreement protocol and the use of the
symmetric key cryptography are used for authentication. Unique session should be used for the
authentication and responding against the challenges for derivation of the unique key for each of the
transaction. The domain hijacking are used for the changing the permission and abusing the
privileged for the domain hosting. The hijacker can use the domain name for implementing illegal
activity and gain the access of the private information for logging into the servers.
INFORMATION SECURITY MANAGEMENT
Spam Low level From external device
and emails
Vulnerability for each assets
Virtual Server
CVE-Modified – The JSON vulnerability and the XML vulnerability are analysed for analysing the
security flaws that are used as a link for the reference and identification of the weakness of the
network configuration.
Mail server
CVE-Recent – It is used for interaction with the security standard practice and it differs from the
traditional attacks for the exploitation of the system and the software. The social engineering attacks
are used by the hackers to gain the access of the confidential information. It consists of baiting,
phasing, pretexting and spear phasing. False communication is created with the victim using chats,
phone calls, spoofed website for gathering personal information and using it for illegal use.
PC
CVE-2018 – The dictionary attacks can be used by the attacker to determine the decryption or the
passphrase key and gain the access of the computer. The brute force attack are used for searching
password systematically and rainbow table are used for reducing the preparation time by analysing
the pre computerised dictionary and reducing the storage requirement.
Web server
CVE-2017 – cross site scripting are used for identification of the flaws in the network and
identification of the web application uses. The cookies can be accessed by the malicious codes for
rewriting the content and using sql injection attacks for modification of the content of the servers.
Firewall
CVE-2016 – It is used as a cryptography for securing the communication and establishing the
communication between the different users. The key agreement protocol and the use of the
symmetric key cryptography are used for authentication. Unique session should be used for the
authentication and responding against the challenges for derivation of the unique key for each of the
transaction. The domain hijacking are used for the changing the permission and abusing the
privileged for the domain hosting. The hijacker can use the domain name for implementing illegal
activity and gain the access of the private information for logging into the servers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




