COIT20262 - Advanced Network Security Assignment 1 Submission
VerifiedAdded on 2024/07/12
|8
|1721
|330
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
COIT20262 Assignment 1 Submission Term 2, 2018
COIT20262 - Advanced Network Security, Term 2, 2018
Assignment 1 Submission
Due date: 5 pm Friday 24 August 2018 (Week 6) ASSESSMENT
Weighting: 40% 1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 8
COIT20262 - Advanced Network Security, Term 2, 2018
Assignment 1 Submission
Due date: 5 pm Friday 24 August 2018 (Week 6) ASSESSMENT
Weighting: 40% 1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
COIT20262 Assignment 1 Submission Term 2, 2018
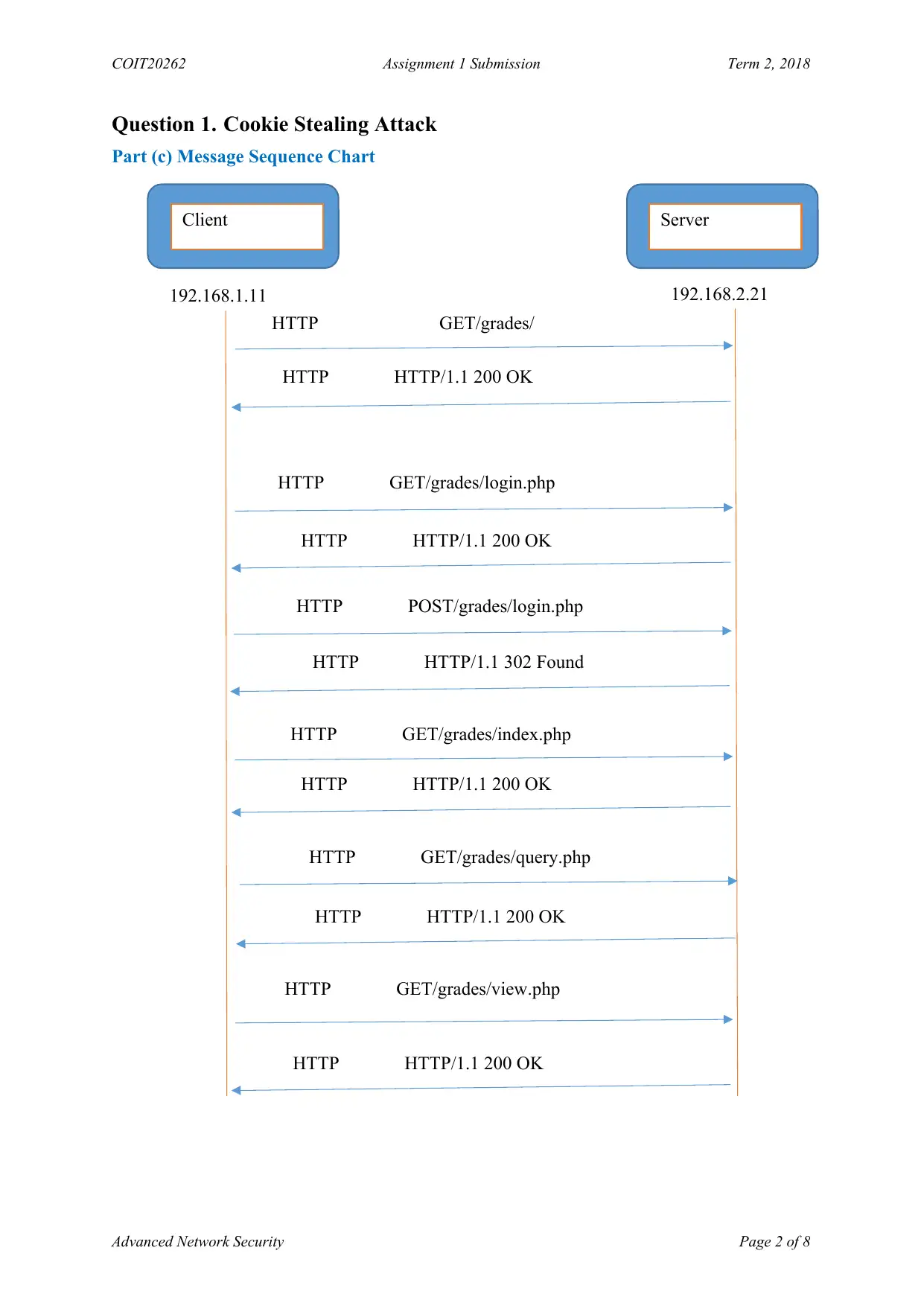
Question 1. Cookie Stealing Attack
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 8
Client Server
192.168.1.11 192.168.2.21
HTTP GET/grades/
HTTP HTTP/1.1 200 OK
HTTP GET/grades/login.php
HTTP HTTP/1.1 200 OK
HTTP POST/grades/login.php
HTTP HTTP/1.1 302 Found
HTTP GET/grades/index.php
HTTP HTTP/1.1 200 OK
HTTP GET/grades/query.php
HTTP HTTP/1.1 200 OK
HTTP GET/grades/view.php
HTTP HTTP/1.1 200 OK
Question 1. Cookie Stealing Attack
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 8
Client Server
192.168.1.11 192.168.2.21
HTTP GET/grades/
HTTP HTTP/1.1 200 OK
HTTP GET/grades/login.php
HTTP HTTP/1.1 200 OK
HTTP POST/grades/login.php
HTTP HTTP/1.1 302 Found
HTTP GET/grades/index.php
HTTP HTTP/1.1 200 OK
HTTP GET/grades/query.php
HTTP HTTP/1.1 200 OK
HTTP GET/grades/view.php
HTTP HTTP/1.1 200 OK

COIT20262 Assignment 1 Submission Term 2, 2018
Part (d) Information from Packets
Information Answer
Packet number from normal-student.pcap that contains the normal
students’ password
4
Packet number from normal-student.pcap in which the server
originally sends the cookie to the browser
6
Last 4 HEX digits of the id_hash in the cookie (give the value of the last
4 digits, not the packet number)
36 36 35 31
Packet number from malicious-student.pcap that contains the
normal student's grade for coit20262.
36
Packet number from malicious-student.pcap in which the client
originally sends the stolen cookie
4
Part (e)
For id_hash calculation, we have used the MD5 hash algorithm. The id_hash calculation which
we have used is basically a type of PHP. This hash algorithm sends the hash to the browser as a
cookie. This hash calculation algorithm is applying for password encryption. The browser
automatically saves this cookie generated by hash calculation algorithm.
Part (f)
The id_hash provides security in this assignment. The security is fully encrypted in this
assignment. Only one user at a time can log in in this grading web application. In the grading
web application, the user 12032177 can log in as a single user at a single time. The id_hash
provides single authentication in this web application.
Part (g)
When user login in the grading application first time, at that time the username and password go
into plain text. After login into the system, the PHP server starts and then the username and
password go into the browser and save as a cookie. At that time the login information is not
secure. This login and password can be stolen,
Part (h)
At the security level the login password was going through plaintext but if we provide client-
side encryption then the only hash will be verified. This encryption method is more secure. This
security function will perform in JavaScript. JavaScript is browsing language if the browser
turns off then the encryption method will be interrupted at that time.
Advanced Network Security Page 3 of 8
Part (d) Information from Packets
Information Answer
Packet number from normal-student.pcap that contains the normal
students’ password
4
Packet number from normal-student.pcap in which the server
originally sends the cookie to the browser
6
Last 4 HEX digits of the id_hash in the cookie (give the value of the last
4 digits, not the packet number)
36 36 35 31
Packet number from malicious-student.pcap that contains the
normal student's grade for coit20262.
36
Packet number from malicious-student.pcap in which the client
originally sends the stolen cookie
4
Part (e)
For id_hash calculation, we have used the MD5 hash algorithm. The id_hash calculation which
we have used is basically a type of PHP. This hash algorithm sends the hash to the browser as a
cookie. This hash calculation algorithm is applying for password encryption. The browser
automatically saves this cookie generated by hash calculation algorithm.
Part (f)
The id_hash provides security in this assignment. The security is fully encrypted in this
assignment. Only one user at a time can log in in this grading web application. In the grading
web application, the user 12032177 can log in as a single user at a single time. The id_hash
provides single authentication in this web application.
Part (g)
When user login in the grading application first time, at that time the username and password go
into plain text. After login into the system, the PHP server starts and then the username and
password go into the browser and save as a cookie. At that time the login information is not
secure. This login and password can be stolen,
Part (h)
At the security level the login password was going through plaintext but if we provide client-
side encryption then the only hash will be verified. This encryption method is more secure. This
security function will perform in JavaScript. JavaScript is browsing language if the browser
turns off then the encryption method will be interrupted at that time.
Advanced Network Security Page 3 of 8
COIT20262 Assignment 1 Submission Term 2, 2018
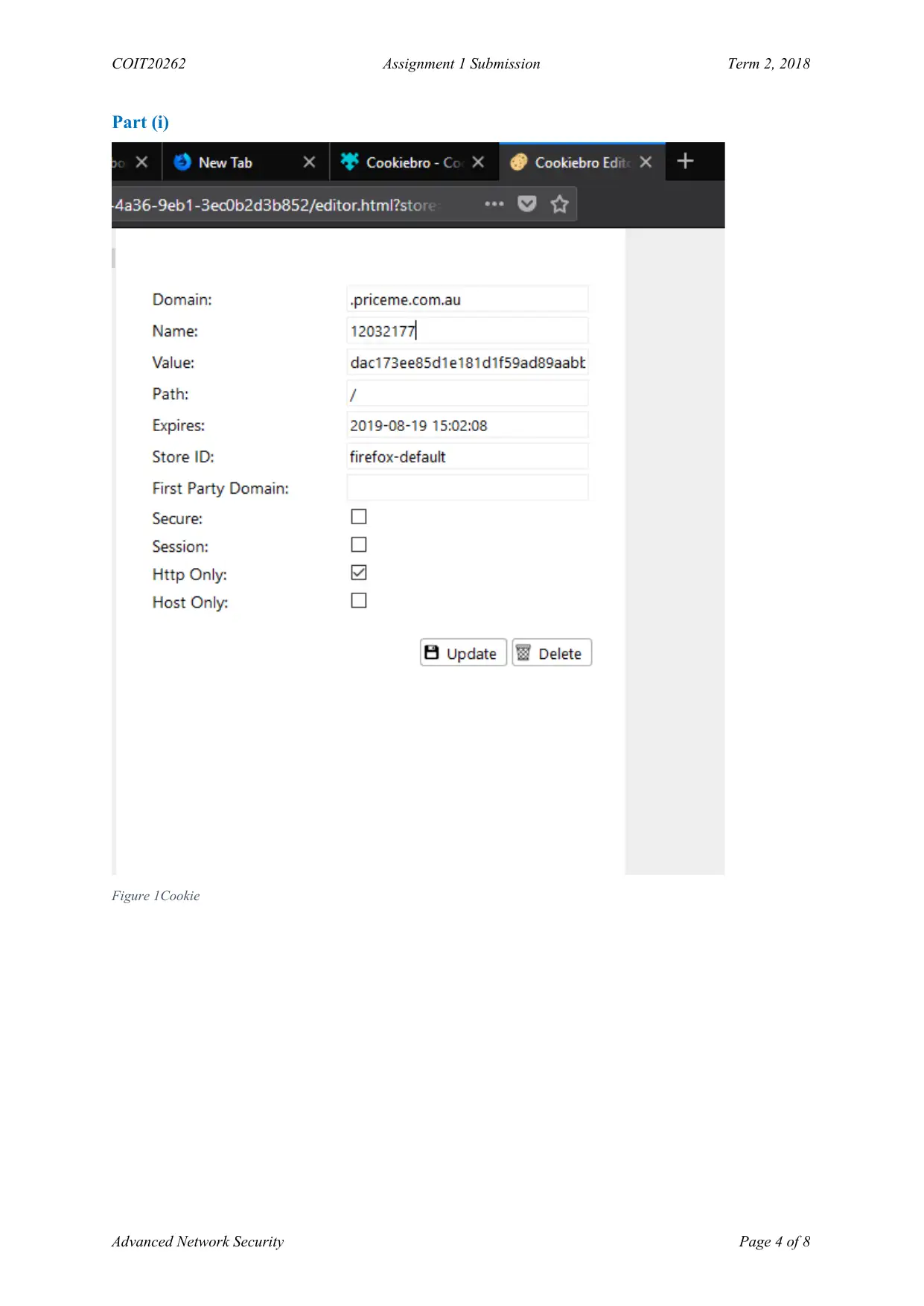
Part (i)
Figure 1Cookie
Advanced Network Security Page 4 of 8
Part (i)
Figure 1Cookie
Advanced Network Security Page 4 of 8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

COIT20262 Assignment 1 Submission Term 2, 2018
Question 2. Cryptography
Part (c)
If we use AES-256-CBC encryption key than the possible combination of the key will be
maximum and this encryption is unbreakable. But if we use alphabetical numeric in the capital
and small like a-A, Z-Z and so on then at that time the possible combination of the key will be
minimum and the security could be hack easily.
Part (d)
IV is a most secure feature in a plaintext process. This provides high security and high
encryption functionality. If we removed the IV security in the error will be generated and the
error will be irremovable at a particular time. We should not remove the IV encryption from the
browser. This IV generate a security key in the client-server browsing process. The security of
the IV prevents the SSH to generate security.
Advanced Network Security Page 5 of 8
Question 2. Cryptography
Part (c)
If we use AES-256-CBC encryption key than the possible combination of the key will be
maximum and this encryption is unbreakable. But if we use alphabetical numeric in the capital
and small like a-A, Z-Z and so on then at that time the possible combination of the key will be
minimum and the security could be hack easily.
Part (d)
IV is a most secure feature in a plaintext process. This provides high security and high
encryption functionality. If we removed the IV security in the error will be generated and the
error will be irremovable at a particular time. We should not remove the IV encryption from the
browser. This IV generate a security key in the client-server browsing process. The security of
the IV prevents the SSH to generate security.
Advanced Network Security Page 5 of 8

COIT20262 Assignment 1 Submission Term 2, 2018
Question 3. Ransomware Research
Overview of Ransomware
Overview
Software apps and malicious email attachments are the examples of ransomware malware
which changes the login credentials of the victim and infects the device by encryption. It locked
data on the victim’s computer and before decrypting the data they demand payment. To hide the
identity the payment demanded in a virtual currency such as bitcoin.
How it works
Cybercriminals can easily purchase the ransomware kit and create ransomware to generate
malware for their own distribution. It is easy for the non-technical field to purchase inexpensive
ransomware as a service and with no efforts can encrypt the files of the infected device.
attackers use several approaches to demand digital currency from the victim. The victim
receives a pop-up message or emails in which attacker demands money and warn the victim that
if the victim will not pay on the specified date then the decrypt data will be destroyed.
Prevention of ransomware
To control the ransomware malware attack antivirus software plays an important role. Users
should not click on links or open the emails which are unfamiliar. We can’t stop the
ransomware but reduce the effects of ransomware and recover the data quickly. There are some
strategies which can be used to minimize the effects of ransomware such as
compartmentalizing authentication domains and systems, by updating storage snapshots and
sets limits on who can access the data.
What are the common methods of infection?
Today time malware attackers use the complex technique to spread their malware virus.
Commonly there is three type of ransomware malware spread; malicious email attachment,
untrusted download website, Remote desktop protocol.
Malicious email attachment: Attackers attach a malicious file with a link, this file capable of
destroying your computer data or can send the personal data to a hacker. This file can be a word,
PDF, Zip, and RAR. , Video, Image.
Untrusted download website: There is some duplicated website which attacks the computer
user to download the software from there website. When a user downloads the file from this
website, a malicious software will download automatically in your computer. This malicious
software will this your data or may access your computer function.
Remote desktop protocol: Hacker use this service to access the user desktop. There is so
many software by which hacker can control the user computer from a remote area. Hacker can
see all that a user is doing in computer remotely.
What are common payloads?
Advanced Network Security Page 6 of 8
Question 3. Ransomware Research
Overview of Ransomware
Overview
Software apps and malicious email attachments are the examples of ransomware malware
which changes the login credentials of the victim and infects the device by encryption. It locked
data on the victim’s computer and before decrypting the data they demand payment. To hide the
identity the payment demanded in a virtual currency such as bitcoin.
How it works
Cybercriminals can easily purchase the ransomware kit and create ransomware to generate
malware for their own distribution. It is easy for the non-technical field to purchase inexpensive
ransomware as a service and with no efforts can encrypt the files of the infected device.
attackers use several approaches to demand digital currency from the victim. The victim
receives a pop-up message or emails in which attacker demands money and warn the victim that
if the victim will not pay on the specified date then the decrypt data will be destroyed.
Prevention of ransomware
To control the ransomware malware attack antivirus software plays an important role. Users
should not click on links or open the emails which are unfamiliar. We can’t stop the
ransomware but reduce the effects of ransomware and recover the data quickly. There are some
strategies which can be used to minimize the effects of ransomware such as
compartmentalizing authentication domains and systems, by updating storage snapshots and
sets limits on who can access the data.
What are the common methods of infection?
Today time malware attackers use the complex technique to spread their malware virus.
Commonly there is three type of ransomware malware spread; malicious email attachment,
untrusted download website, Remote desktop protocol.
Malicious email attachment: Attackers attach a malicious file with a link, this file capable of
destroying your computer data or can send the personal data to a hacker. This file can be a word,
PDF, Zip, and RAR. , Video, Image.
Untrusted download website: There is some duplicated website which attacks the computer
user to download the software from there website. When a user downloads the file from this
website, a malicious software will download automatically in your computer. This malicious
software will this your data or may access your computer function.
Remote desktop protocol: Hacker use this service to access the user desktop. There is so
many software by which hacker can control the user computer from a remote area. Hacker can
see all that a user is doing in computer remotely.
What are common payloads?
Advanced Network Security Page 6 of 8

COIT20262 Assignment 1 Submission Term 2, 2018
Payload means a malicious virus that does malicious activity in the computer. A virus with
more payload that means more harmful. There is a different type of virus. Some virus can
multiply themselves, some can access your data, and some can destroy your computer file.
Some of the ways to execute a payload include:
1 By executing an infected program
2 computer without an anti-virus installed
3 By opening an infected file
What are cryptographic techniques commonly used?
The whole world run on code and software like ATM, mobile, online shopping, industries,
airlines etc. In fact today we can’t live with code and software. Cryptography is a technique for
the communication of data in an encryption mode. The encryption is done in such a way that no
third person can decrypt the data.
Triple DES is used to replace the old DES algorithm. Earlier Des is using 56 bits key for
encryption, so a hacker can hack this code so now Triple DES is used up to 168 bits for
encryption.
Blowfish is also designed to replace the old DES algorithm. Blowfish is known for his
effectiveness and speed. As many say that to crack the blowfish is very difficult. Blowfish work
on variable length means from 32 bits to 448 bits. Blowfish used in e-commerce and database
security.
RSA is known for his an asymmetric key encryption technique. In this technique, the
encryption key is different than decryption key which is kept private. RSA key is increase by
encryption of data.
What technologies are used to obtain ransoms?
Ransomware hacker uses payment in form of cryptocurrency. Cryptocurrency is a virtual
currency that uses cryptography technique for security. Cryptocurrency is different from
countries currency like Dollar, Euro, and Rupees, due to his different security features.
Cryptocurrency uses blockchain technology. blockchain technology uses decentralized for all
transition. By using theses technology user can confirm their transition without the approval of
central bank authority.
Why is some ransomware very hard to break?
Now day’s hackers using higher bits keys to make ransomware virus more complex so it’s
difficult to break by anti-virus industries. Ransomware uses malicious code to gain control over
user file, data, and computer. These viri use RSA, Blowfish and Triple DES algorithm to make
a complex virus structure. Nowadays we can break the code or decrypt up to 600 bits key in a
short period of time, but above that keys are hard to break.
Recommendation
Advanced Network Security Page 7 of 8
Payload means a malicious virus that does malicious activity in the computer. A virus with
more payload that means more harmful. There is a different type of virus. Some virus can
multiply themselves, some can access your data, and some can destroy your computer file.
Some of the ways to execute a payload include:
1 By executing an infected program
2 computer without an anti-virus installed
3 By opening an infected file
What are cryptographic techniques commonly used?
The whole world run on code and software like ATM, mobile, online shopping, industries,
airlines etc. In fact today we can’t live with code and software. Cryptography is a technique for
the communication of data in an encryption mode. The encryption is done in such a way that no
third person can decrypt the data.
Triple DES is used to replace the old DES algorithm. Earlier Des is using 56 bits key for
encryption, so a hacker can hack this code so now Triple DES is used up to 168 bits for
encryption.
Blowfish is also designed to replace the old DES algorithm. Blowfish is known for his
effectiveness and speed. As many say that to crack the blowfish is very difficult. Blowfish work
on variable length means from 32 bits to 448 bits. Blowfish used in e-commerce and database
security.
RSA is known for his an asymmetric key encryption technique. In this technique, the
encryption key is different than decryption key which is kept private. RSA key is increase by
encryption of data.
What technologies are used to obtain ransoms?
Ransomware hacker uses payment in form of cryptocurrency. Cryptocurrency is a virtual
currency that uses cryptography technique for security. Cryptocurrency is different from
countries currency like Dollar, Euro, and Rupees, due to his different security features.
Cryptocurrency uses blockchain technology. blockchain technology uses decentralized for all
transition. By using theses technology user can confirm their transition without the approval of
central bank authority.
Why is some ransomware very hard to break?
Now day’s hackers using higher bits keys to make ransomware virus more complex so it’s
difficult to break by anti-virus industries. Ransomware uses malicious code to gain control over
user file, data, and computer. These viri use RSA, Blowfish and Triple DES algorithm to make
a complex virus structure. Nowadays we can break the code or decrypt up to 600 bits key in a
short period of time, but above that keys are hard to break.
Recommendation
Advanced Network Security Page 7 of 8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 1 Submission Term 2, 2018
There are several ways to handle the ransomware such as to clean the ransomware from the
machine use anti-malware or anti-virus; the user should not open the stranger email
attachments. GPO restrictions restrict the ransomware or malware to install on the device and
perform a regular back up. The user should not open the spam emails or the open attachments in
email from unknown origin.
Advanced Network Security Page 8 of 8
There are several ways to handle the ransomware such as to clean the ransomware from the
machine use anti-malware or anti-virus; the user should not open the stranger email
attachments. GPO restrictions restrict the ransomware or malware to install on the device and
perform a regular back up. The user should not open the spam emails or the open attachments in
email from unknown origin.
Advanced Network Security Page 8 of 8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



