SIT282 Computer Crime and Digital Forensics Investigation Report 2019
VerifiedAdded on 2022/09/27
|16
|3539
|20
Report
AI Summary
This report details a computer crime investigation, focusing on digital forensics procedures and outcomes. The investigation includes the examination of an email and a USB drive, with the goal of identifying and collecting evidence of potential cybercrime. The report outlines the digital forensic process, including evidence forms, workstation setup, and image downloading. It also covers the use of SHA-based hash functions for verifying data integrity. The report further describes the binary details of the evidence and the programs used for investigation, followed by the outcomes of the investigation, including the description and justification of keywords used, documented procedures, and technical tactics. Finally, the report addresses the legal implications of the cybercrime, referencing relevant legislation and the importance of evidence acquisition and examination. The report concludes with the findings and conclusions of the investigation, providing a comprehensive overview of the case and its handling.

TITLE: Computer Crime and Digital Forensics
Computer Crime and Digital Forensics
i
Computer Crime and Digital Forensics
i
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
Digital forensic is the rapidly growing field of investigations in the IT industry. Experts should be
able to collect the data, find evidence, collect the relevant evidence and also they should a team
inside of them are able to access all these steps using technology tools. By using the software, the
data in USB can be retrieved and also the viruses will be eliminated in the same case with the email.
All the malicious activities can be done just by the use of well build software to handle such issues
(Le‐Khac, Plunkett, Kechadi, & Chen, 2019). The research on the email clearly shows that it was
infected by the viruses. The emails can't be open with the normal software but after scanning using
Autopsy, the viruses can be seen. USB also contain sensitive financial files records of the balance
sheet. According to our investigations, the balance was found to mean he was planning to
manipulate the financial report of the company. In any investigation, acquiring evidence is the most
important part because no investigation will be carried if there is no evidence. The victim uses some
email to try and do crime because his contract was terminated and therefore the chance of him
trying to do the crime is very high. Also, USB found in his desk might be carrying some viruses
intended to infected computers or perhaps it contains stole files. Therefore, we will have to use legal
and ethics of judging and prosecuting digital crimes. We have all the evidence necessary for the
prosecution. We have also prepared a report which will be used as evidence against the victim.
ii
Digital forensic is the rapidly growing field of investigations in the IT industry. Experts should be
able to collect the data, find evidence, collect the relevant evidence and also they should a team
inside of them are able to access all these steps using technology tools. By using the software, the
data in USB can be retrieved and also the viruses will be eliminated in the same case with the email.
All the malicious activities can be done just by the use of well build software to handle such issues
(Le‐Khac, Plunkett, Kechadi, & Chen, 2019). The research on the email clearly shows that it was
infected by the viruses. The emails can't be open with the normal software but after scanning using
Autopsy, the viruses can be seen. USB also contain sensitive financial files records of the balance
sheet. According to our investigations, the balance was found to mean he was planning to
manipulate the financial report of the company. In any investigation, acquiring evidence is the most
important part because no investigation will be carried if there is no evidence. The victim uses some
email to try and do crime because his contract was terminated and therefore the chance of him
trying to do the crime is very high. Also, USB found in his desk might be carrying some viruses
intended to infected computers or perhaps it contains stole files. Therefore, we will have to use legal
and ethics of judging and prosecuting digital crimes. We have all the evidence necessary for the
prosecution. We have also prepared a report which will be used as evidence against the victim.
ii

TABLE OF CONTENTS
Page
TITLE................................................................................................................…………... ……..i
EXECUTIVE SUMMARY ....................................................................................................…..ii
TABLE OF CONTENTS .............................................................................................………….iii
INTRODUCTION ........................................................................................................................ iv
CHAPTER
1. DIGITAL FORENSIC PROCEDURE
1.1. Evidence Form (Figure 1-11 of the text)………………………………………………..1
1.2. Forensic Workstation and Image Downloading Procedure….……….………………...1
1.3. Two SHA-based Hash Function…………………………………...………………….. 2
1.4 Explanation of need for Multiple Hash Values ………………………………….……..3
1.5 Explanation of Procedure…………………………………………….………………..4
2. DESCRIPTION OF BINARY DETAILS
2.1. Table 1: Properties of the Undeleted Files………………………….………………...5
2.2. Description of Programs …………………………………...………………………...5
3. OUTCOMES OF DIGITAL FORENSIC INVESTIGATION
3.1. Description and Justification ………………………………………….……………..6
3.2. Document Procedure……………………………………………………..…………..6
3.3. Result and Conclusions…………………………………………….10
4. LEGAL IMPLICATIONS
4.1.Cybercrime Act 2001 and Crimes 1958…………………………………………………….1.1
4.2. Corporate or Criminal Investigation…….………………………………………………….11
References……………………………………………………………………………………12
iii
Page
TITLE................................................................................................................…………... ……..i
EXECUTIVE SUMMARY ....................................................................................................…..ii
TABLE OF CONTENTS .............................................................................................………….iii
INTRODUCTION ........................................................................................................................ iv
CHAPTER
1. DIGITAL FORENSIC PROCEDURE
1.1. Evidence Form (Figure 1-11 of the text)………………………………………………..1
1.2. Forensic Workstation and Image Downloading Procedure….……….………………...1
1.3. Two SHA-based Hash Function…………………………………...………………….. 2
1.4 Explanation of need for Multiple Hash Values ………………………………….……..3
1.5 Explanation of Procedure…………………………………………….………………..4
2. DESCRIPTION OF BINARY DETAILS
2.1. Table 1: Properties of the Undeleted Files………………………….………………...5
2.2. Description of Programs …………………………………...………………………...5
3. OUTCOMES OF DIGITAL FORENSIC INVESTIGATION
3.1. Description and Justification ………………………………………….……………..6
3.2. Document Procedure……………………………………………………..…………..6
3.3. Result and Conclusions…………………………………………….10
4. LEGAL IMPLICATIONS
4.1.Cybercrime Act 2001 and Crimes 1958…………………………………………………….1.1
4.2. Corporate or Criminal Investigation…….………………………………………………….11
References……………………………………………………………………………………12
iii
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
Cybercrime cases always shift because of the way technology is moving. When new cybercrime is
identified then new rules and regulations are set to strengthen the cybercrime laws. This intellectual
property troubles lawmakers because of how technical it is to set the rules and regulations. In most
cases, there is no clear or tangible proof of the theft because it is done in a magical way using
virtual environments. This problem, therefore, has given rise to new ways of process investigations
called IP forensic analysis. Investigative experts are assigned a task to perform valuations of
copyrights, patents, taxation, among others. Through digital forensics, investigations of a computer
have been dealt with accordingly (Moscato, Romeo, & Xhafa, 2019, February).
iv
Cybercrime cases always shift because of the way technology is moving. When new cybercrime is
identified then new rules and regulations are set to strengthen the cybercrime laws. This intellectual
property troubles lawmakers because of how technical it is to set the rules and regulations. In most
cases, there is no clear or tangible proof of the theft because it is done in a magical way using
virtual environments. This problem, therefore, has given rise to new ways of process investigations
called IP forensic analysis. Investigative experts are assigned a task to perform valuations of
copyrights, patents, taxation, among others. Through digital forensics, investigations of a computer
have been dealt with accordingly (Moscato, Romeo, & Xhafa, 2019, February).
iv
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1. DIGITAL FORENSIC PROCEDURE
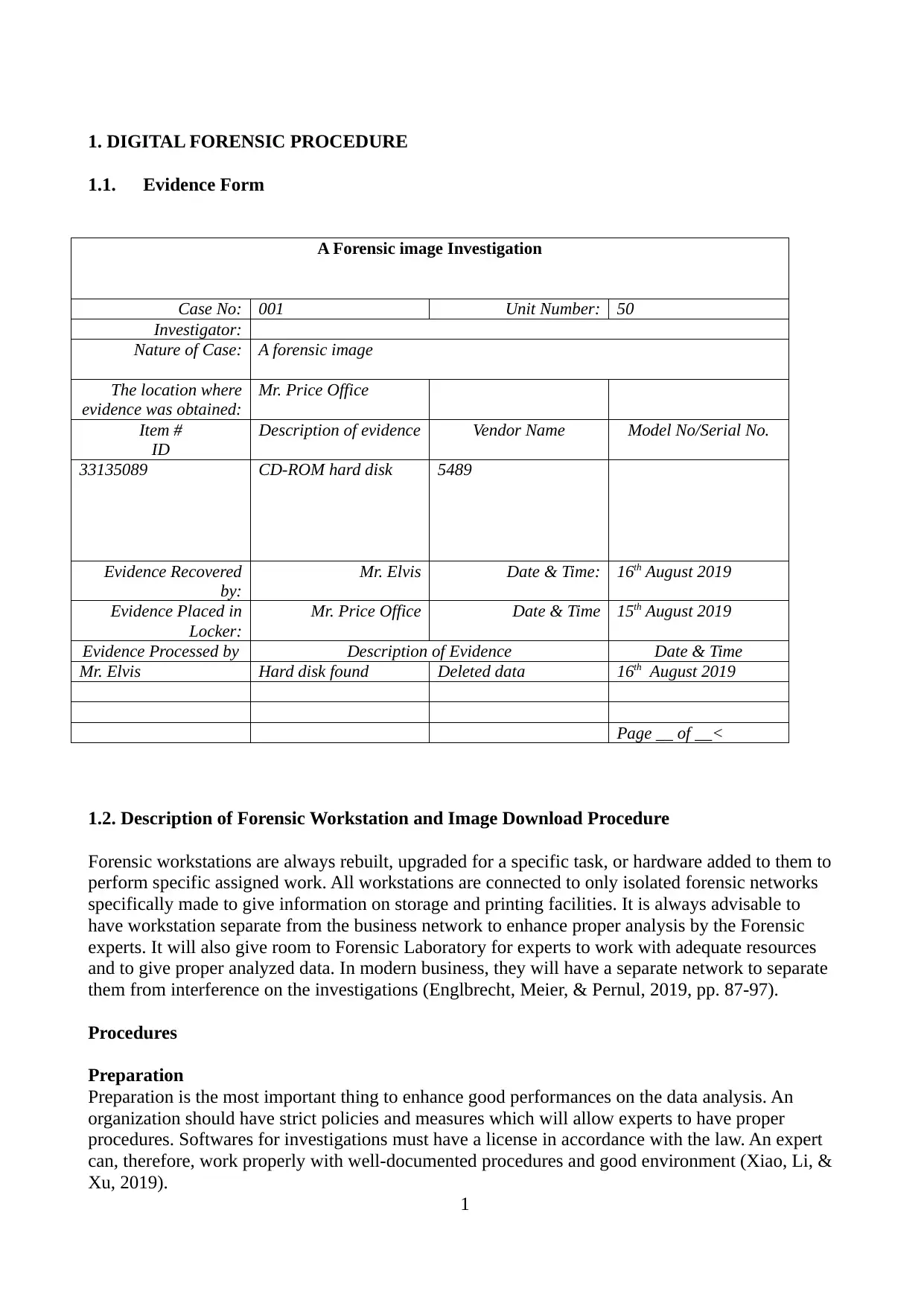
1.1. Evidence Form
A Forensic image Investigation
Case No: 001 Unit Number: 50
Investigator:
Nature of Case: A forensic image
The location where
evidence was obtained:
Mr. Price Office
Item #
ID
Description of evidence Vendor Name Model No/Serial No.
33135089 CD-ROM hard disk 5489
Evidence Recovered
by:
Mr. Elvis Date & Time: 16th August 2019
Evidence Placed in
Locker:
Mr. Price Office Date & Time 15th August 2019
Evidence Processed by Description of Evidence Date & Time
Mr. Elvis Hard disk found Deleted data 16th August 2019
Page __ of __<
1.2. Description of Forensic Workstation and Image Download Procedure
Forensic workstations are always rebuilt, upgraded for a specific task, or hardware added to them to
perform specific assigned work. All workstations are connected to only isolated forensic networks
specifically made to give information on storage and printing facilities. It is always advisable to
have workstation separate from the business network to enhance proper analysis by the Forensic
experts. It will also give room to Forensic Laboratory for experts to work with adequate resources
and to give proper analyzed data. In modern business, they will have a separate network to separate
them from interference on the investigations (Englbrecht, Meier, & Pernul, 2019, pp. 87-97).
Procedures
Preparation
Preparation is the most important thing to enhance good performances on the data analysis. An
organization should have strict policies and measures which will allow experts to have proper
procedures. Softwares for investigations must have a license in accordance with the law. An expert
can, therefore, work properly with well-documented procedures and good environment (Xiao, Li, &
Xu, 2019).
1
1.1. Evidence Form
A Forensic image Investigation
Case No: 001 Unit Number: 50
Investigator:
Nature of Case: A forensic image
The location where
evidence was obtained:
Mr. Price Office
Item #
ID
Description of evidence Vendor Name Model No/Serial No.
33135089 CD-ROM hard disk 5489
Evidence Recovered
by:
Mr. Elvis Date & Time: 16th August 2019
Evidence Placed in
Locker:
Mr. Price Office Date & Time 15th August 2019
Evidence Processed by Description of Evidence Date & Time
Mr. Elvis Hard disk found Deleted data 16th August 2019
Page __ of __<
1.2. Description of Forensic Workstation and Image Download Procedure
Forensic workstations are always rebuilt, upgraded for a specific task, or hardware added to them to
perform specific assigned work. All workstations are connected to only isolated forensic networks
specifically made to give information on storage and printing facilities. It is always advisable to
have workstation separate from the business network to enhance proper analysis by the Forensic
experts. It will also give room to Forensic Laboratory for experts to work with adequate resources
and to give proper analyzed data. In modern business, they will have a separate network to separate
them from interference on the investigations (Englbrecht, Meier, & Pernul, 2019, pp. 87-97).
Procedures
Preparation
Preparation is the most important thing to enhance good performances on the data analysis. An
organization should have strict policies and measures which will allow experts to have proper
procedures. Softwares for investigations must have a license in accordance with the law. An expert
can, therefore, work properly with well-documented procedures and good environment (Xiao, Li, &
Xu, 2019).
1

Collection
This is a phase where all the evidence are collected by the forensic experts. This is the most critical
stage since it involves collecting tangible evidence to assist in carrying out investigations. It can
include hard-rives, images among others evidence (Panchal, Yagnik, & Sharma, 2019, pp. 401-408).
Examination
During this phase, experts examine the first respondents. It includes detecting hidden, obscured and
encrypted data which are most important since they are required to provide an accurate and most
honest report (Montasari, Hill, Carpenter, & Hosseinian-Far, 2019, pp. 169-209).
Analysis
Analysis phase, the incident is determined exactly. All data collected is interpreted here hence it the
stage where it is determined whether the case is valid or not (Wong, Leung, New, & Ching, 2019,
pp. 181-199).
Reporting
The report is a summarized work of all the investigations. All the procedures and notes take are well
documented including all the discoveries and testimonies (Patel, & Sharma, 2019, pp. 447-456).
1.3. At Least Two SHA-based Hash Function Values of the ISO Image
1.3.1 Hash Cryptography Algorithm
It is a one-way hash which is mathematical functions used to convert variable to a binary sequence
of known length. It is impossible to reverse the process. It used when the 2 strings can produce the
same hash value. It will be used to trace the ISO image (Montasari, Hill, Carpenter, & Montaseri,
2019, 52-60).
1.3.2 Secure Hash Algorithm (SHA) 512
This hash explains how the cryptography algorithm can receive input in message form then converts
it to the 512-bit length message. This will help to find the ISO image on the hard-rive (Moscato,
Romeo, & Xhafa, 2019, February, Vol. 29, p. 170).
2
This is a phase where all the evidence are collected by the forensic experts. This is the most critical
stage since it involves collecting tangible evidence to assist in carrying out investigations. It can
include hard-rives, images among others evidence (Panchal, Yagnik, & Sharma, 2019, pp. 401-408).
Examination
During this phase, experts examine the first respondents. It includes detecting hidden, obscured and
encrypted data which are most important since they are required to provide an accurate and most
honest report (Montasari, Hill, Carpenter, & Hosseinian-Far, 2019, pp. 169-209).
Analysis
Analysis phase, the incident is determined exactly. All data collected is interpreted here hence it the
stage where it is determined whether the case is valid or not (Wong, Leung, New, & Ching, 2019,
pp. 181-199).
Reporting
The report is a summarized work of all the investigations. All the procedures and notes take are well
documented including all the discoveries and testimonies (Patel, & Sharma, 2019, pp. 447-456).
1.3. At Least Two SHA-based Hash Function Values of the ISO Image
1.3.1 Hash Cryptography Algorithm
It is a one-way hash which is mathematical functions used to convert variable to a binary sequence
of known length. It is impossible to reverse the process. It used when the 2 strings can produce the
same hash value. It will be used to trace the ISO image (Montasari, Hill, Carpenter, & Montaseri,
2019, 52-60).
1.3.2 Secure Hash Algorithm (SHA) 512
This hash explains how the cryptography algorithm can receive input in message form then converts
it to the 512-bit length message. This will help to find the ISO image on the hard-rive (Moscato,
Romeo, & Xhafa, 2019, February, Vol. 29, p. 170).
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
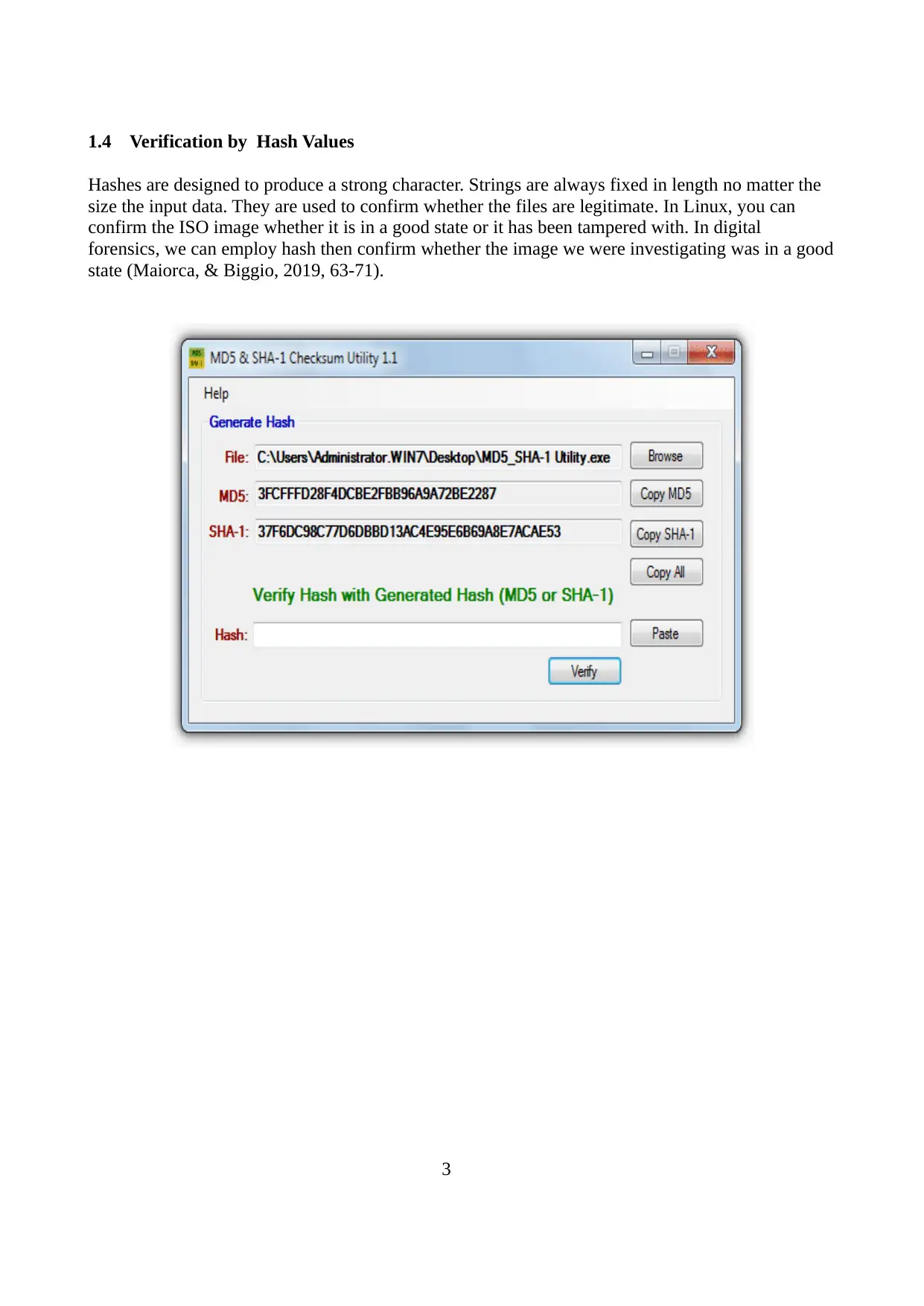
1.4 Verification by Hash Values
Hashes are designed to produce a strong character. Strings are always fixed in length no matter the
size the input data. They are used to confirm whether the files are legitimate. In Linux, you can
confirm the ISO image whether it is in a good state or it has been tampered with. In digital
forensics, we can employ hash then confirm whether the image we were investigating was in a good
state (Maiorca, & Biggio, 2019, 63-71).
3
Hashes are designed to produce a strong character. Strings are always fixed in length no matter the
size the input data. They are used to confirm whether the files are legitimate. In Linux, you can
confirm the ISO image whether it is in a good state or it has been tampered with. In digital
forensics, we can employ hash then confirm whether the image we were investigating was in a good
state (Maiorca, & Biggio, 2019, 63-71).
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
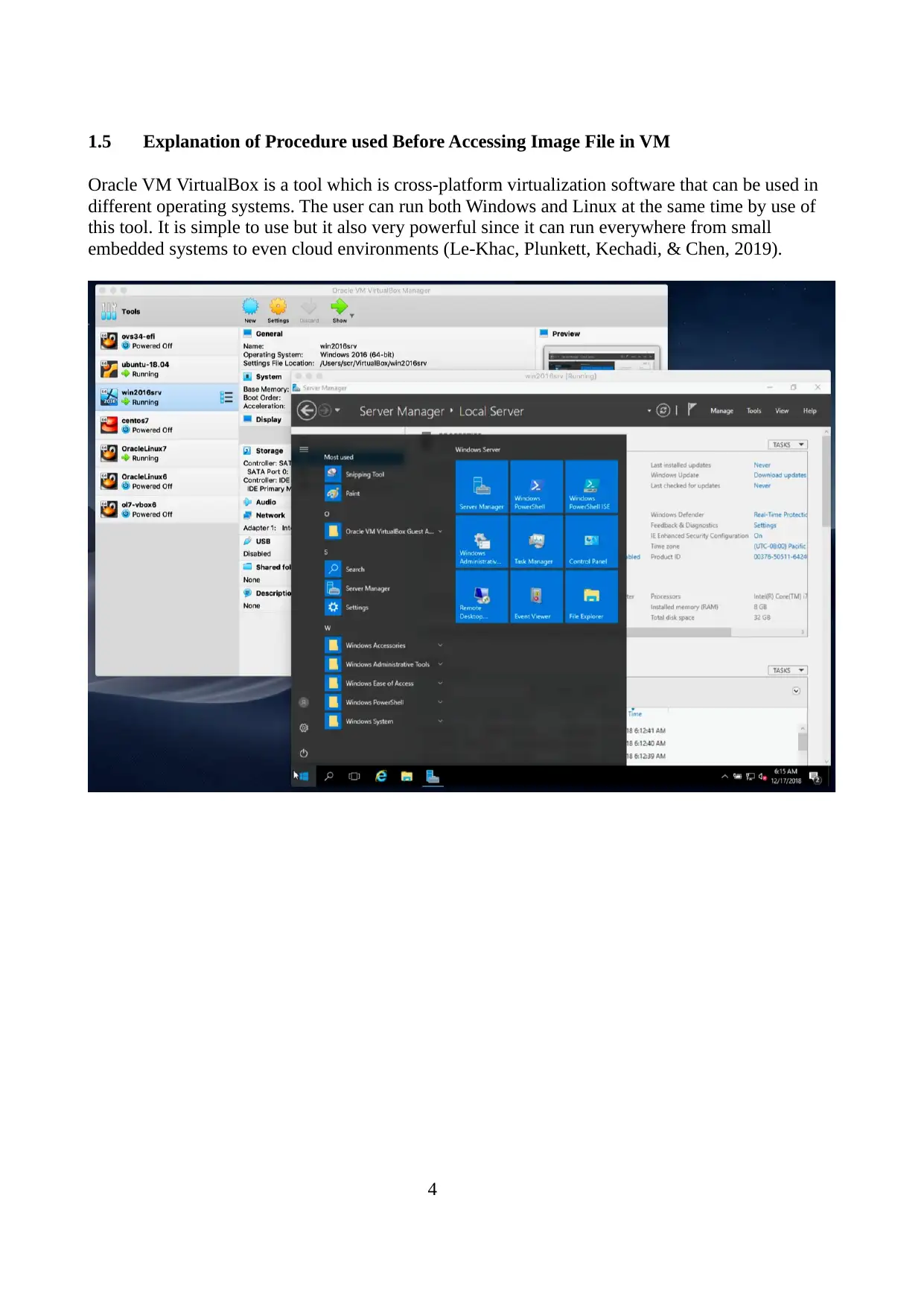
1.5 Explanation of Procedure used Before Accessing Image File in VM
Oracle VM VirtualBox is a tool which is cross-platform virtualization software that can be used in
different operating systems. The user can run both Windows and Linux at the same time by use of
this tool. It is simple to use but it also very powerful since it can run everywhere from small
embedded systems to even cloud environments (Le‐Khac, Plunkett, Kechadi, & Chen, 2019).
4
Oracle VM VirtualBox is a tool which is cross-platform virtualization software that can be used in
different operating systems. The user can run both Windows and Linux at the same time by use of
this tool. It is simple to use but it also very powerful since it can run everywhere from small
embedded systems to even cloud environments (Le‐Khac, Plunkett, Kechadi, & Chen, 2019).
4
2.DESCRIPTION OF BINARY DETAILS
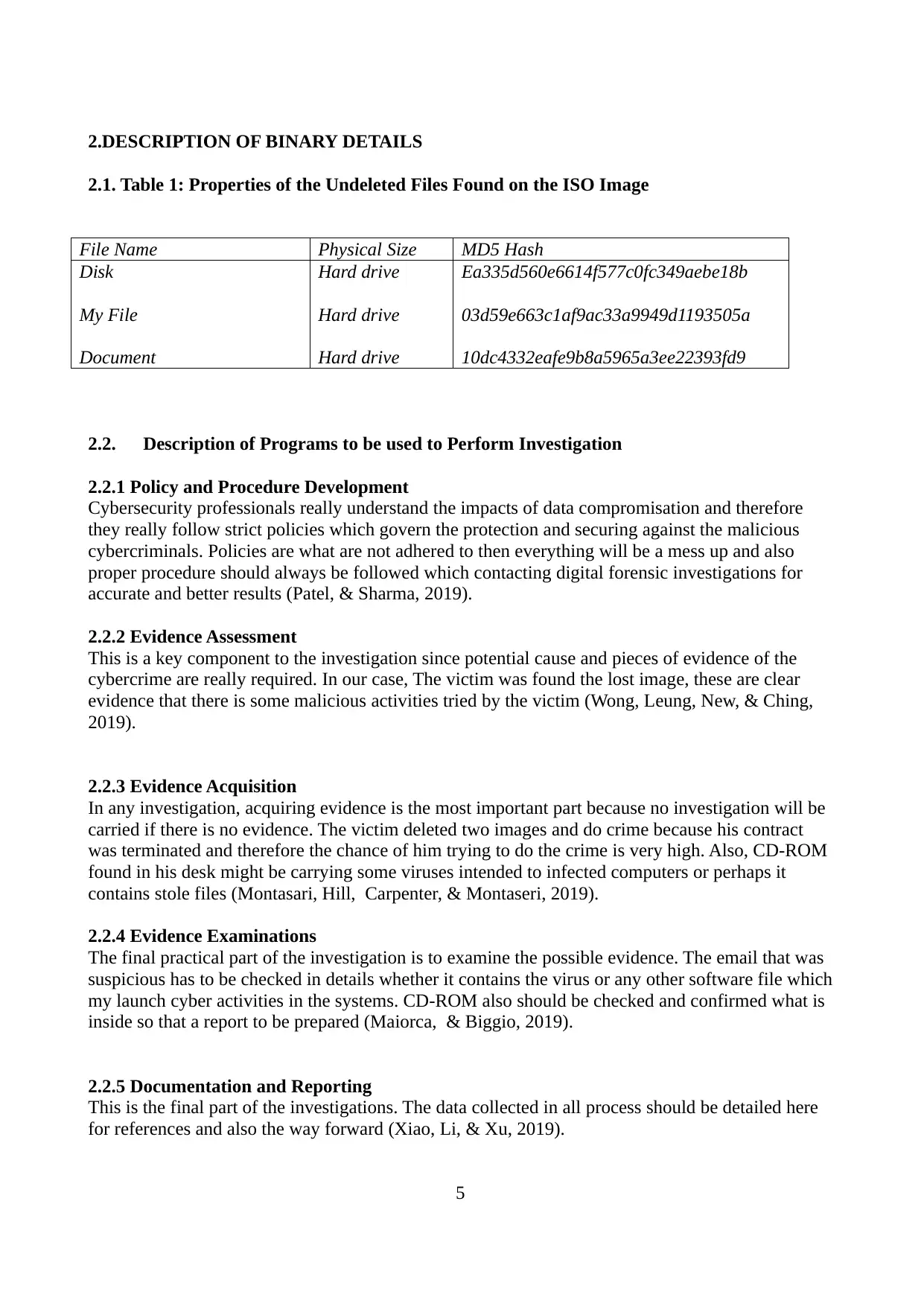
2.1. Table 1: Properties of the Undeleted Files Found on the ISO Image
File Name Physical Size MD5 Hash
Disk
My File
Document
Hard drive
Hard drive
Hard drive
Ea335d560e6614f577c0fc349aebe18b
03d59e663c1af9ac33a9949d1193505a
10dc4332eafe9b8a5965a3ee22393fd9
2.2. Description of Programs to be used to Perform Investigation
2.2.1 Policy and Procedure Development
Cybersecurity professionals really understand the impacts of data compromisation and therefore
they really follow strict policies which govern the protection and securing against the malicious
cybercriminals. Policies are what are not adhered to then everything will be a mess up and also
proper procedure should always be followed which contacting digital forensic investigations for
accurate and better results (Patel, & Sharma, 2019).
2.2.2 Evidence Assessment
This is a key component to the investigation since potential cause and pieces of evidence of the
cybercrime are really required. In our case, The victim was found the lost image, these are clear
evidence that there is some malicious activities tried by the victim (Wong, Leung, New, & Ching,
2019).
2.2.3 Evidence Acquisition
In any investigation, acquiring evidence is the most important part because no investigation will be
carried if there is no evidence. The victim deleted two images and do crime because his contract
was terminated and therefore the chance of him trying to do the crime is very high. Also, CD-ROM
found in his desk might be carrying some viruses intended to infected computers or perhaps it
contains stole files (Montasari, Hill, Carpenter, & Montaseri, 2019).
2.2.4 Evidence Examinations
The final practical part of the investigation is to examine the possible evidence. The email that was
suspicious has to be checked in details whether it contains the virus or any other software file which
my launch cyber activities in the systems. CD-ROM also should be checked and confirmed what is
inside so that a report to be prepared (Maiorca, & Biggio, 2019).
2.2.5 Documentation and Reporting
This is the final part of the investigations. The data collected in all process should be detailed here
for references and also the way forward (Xiao, Li, & Xu, 2019).
5
2.1. Table 1: Properties of the Undeleted Files Found on the ISO Image
File Name Physical Size MD5 Hash
Disk
My File
Document
Hard drive
Hard drive
Hard drive
Ea335d560e6614f577c0fc349aebe18b
03d59e663c1af9ac33a9949d1193505a
10dc4332eafe9b8a5965a3ee22393fd9
2.2. Description of Programs to be used to Perform Investigation
2.2.1 Policy and Procedure Development
Cybersecurity professionals really understand the impacts of data compromisation and therefore
they really follow strict policies which govern the protection and securing against the malicious
cybercriminals. Policies are what are not adhered to then everything will be a mess up and also
proper procedure should always be followed which contacting digital forensic investigations for
accurate and better results (Patel, & Sharma, 2019).
2.2.2 Evidence Assessment
This is a key component to the investigation since potential cause and pieces of evidence of the
cybercrime are really required. In our case, The victim was found the lost image, these are clear
evidence that there is some malicious activities tried by the victim (Wong, Leung, New, & Ching,
2019).
2.2.3 Evidence Acquisition
In any investigation, acquiring evidence is the most important part because no investigation will be
carried if there is no evidence. The victim deleted two images and do crime because his contract
was terminated and therefore the chance of him trying to do the crime is very high. Also, CD-ROM
found in his desk might be carrying some viruses intended to infected computers or perhaps it
contains stole files (Montasari, Hill, Carpenter, & Montaseri, 2019).
2.2.4 Evidence Examinations
The final practical part of the investigation is to examine the possible evidence. The email that was
suspicious has to be checked in details whether it contains the virus or any other software file which
my launch cyber activities in the systems. CD-ROM also should be checked and confirmed what is
inside so that a report to be prepared (Maiorca, & Biggio, 2019).
2.2.5 Documentation and Reporting
This is the final part of the investigations. The data collected in all process should be detailed here
for references and also the way forward (Xiao, Li, & Xu, 2019).
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
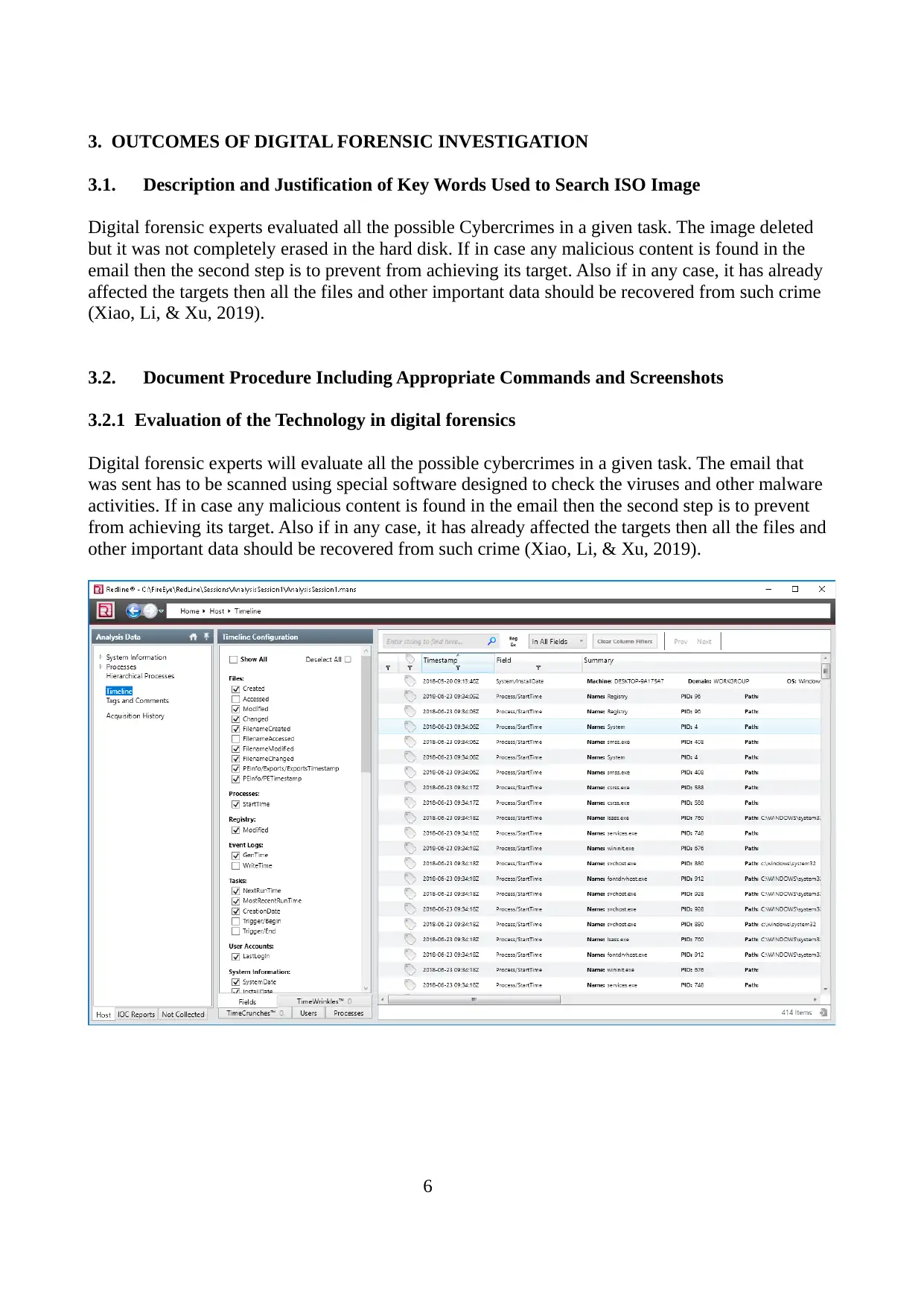
3. OUTCOMES OF DIGITAL FORENSIC INVESTIGATION
3.1. Description and Justification of Key Words Used to Search ISO Image
Digital forensic experts evaluated all the possible Cybercrimes in a given task. The image deleted
but it was not completely erased in the hard disk. If in case any malicious content is found in the
email then the second step is to prevent from achieving its target. Also if in any case, it has already
affected the targets then all the files and other important data should be recovered from such crime
(Xiao, Li, & Xu, 2019).
3.2. Document Procedure Including Appropriate Commands and Screenshots
3.2.1 Evaluation of the Technology in digital forensics
Digital forensic experts will evaluate all the possible cybercrimes in a given task. The email that
was sent has to be scanned using special software designed to check the viruses and other malware
activities. If in case any malicious content is found in the email then the second step is to prevent
from achieving its target. Also if in any case, it has already affected the targets then all the files and
other important data should be recovered from such crime (Xiao, Li, & Xu, 2019).
6
3.1. Description and Justification of Key Words Used to Search ISO Image
Digital forensic experts evaluated all the possible Cybercrimes in a given task. The image deleted
but it was not completely erased in the hard disk. If in case any malicious content is found in the
email then the second step is to prevent from achieving its target. Also if in any case, it has already
affected the targets then all the files and other important data should be recovered from such crime
(Xiao, Li, & Xu, 2019).
3.2. Document Procedure Including Appropriate Commands and Screenshots
3.2.1 Evaluation of the Technology in digital forensics
Digital forensic experts will evaluate all the possible cybercrimes in a given task. The email that
was sent has to be scanned using special software designed to check the viruses and other malware
activities. If in case any malicious content is found in the email then the second step is to prevent
from achieving its target. Also if in any case, it has already affected the targets then all the files and
other important data should be recovered from such crime (Xiao, Li, & Xu, 2019).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
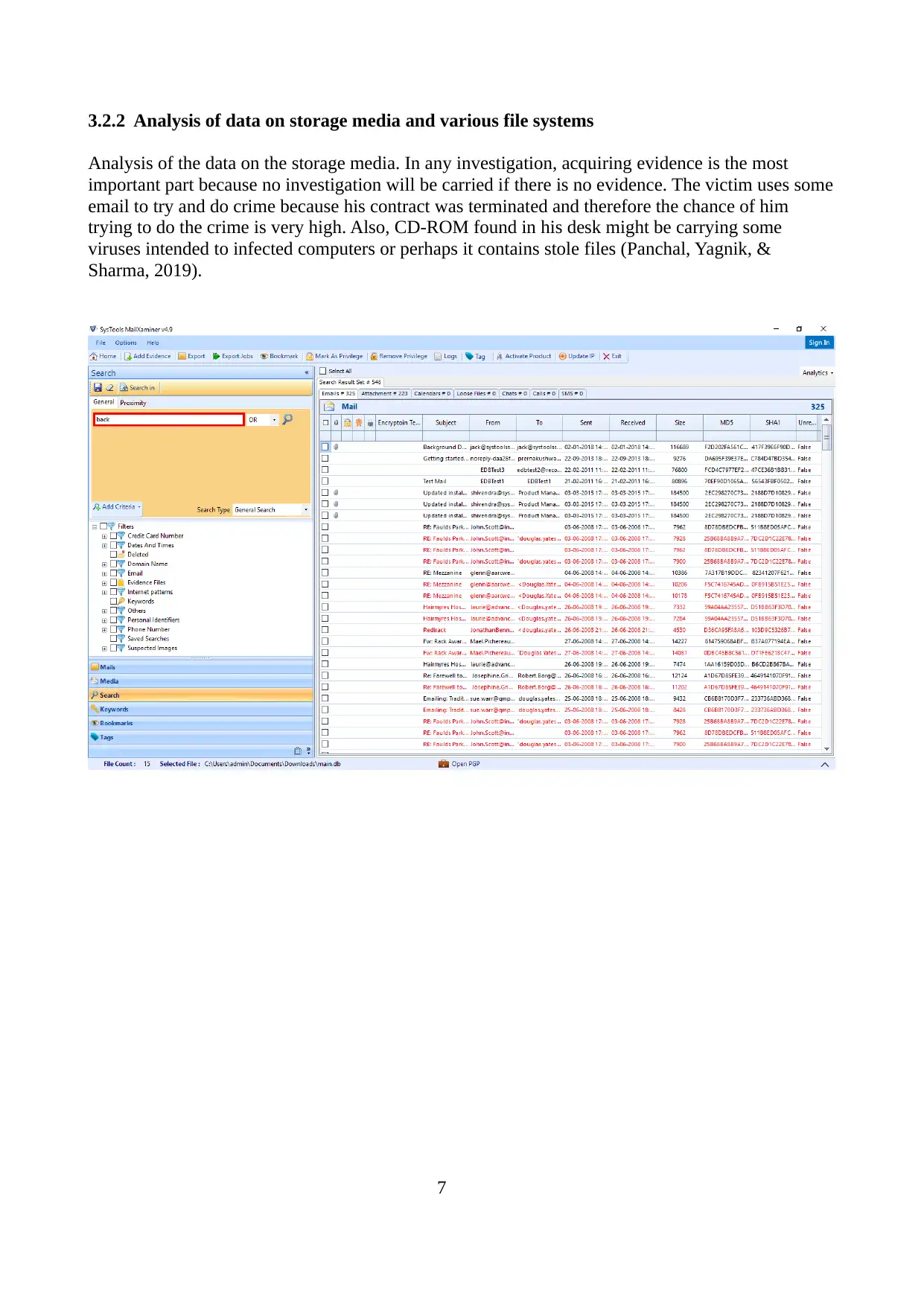
3.2.2 Analysis of data on storage media and various file systems
Analysis of the data on the storage media. In any investigation, acquiring evidence is the most
important part because no investigation will be carried if there is no evidence. The victim uses some
email to try and do crime because his contract was terminated and therefore the chance of him
trying to do the crime is very high. Also, CD-ROM found in his desk might be carrying some
viruses intended to infected computers or perhaps it contains stole files (Panchal, Yagnik, &
Sharma, 2019).
7
Analysis of the data on the storage media. In any investigation, acquiring evidence is the most
important part because no investigation will be carried if there is no evidence. The victim uses some
email to try and do crime because his contract was terminated and therefore the chance of him
trying to do the crime is very high. Also, CD-ROM found in his desk might be carrying some
viruses intended to infected computers or perhaps it contains stole files (Panchal, Yagnik, &
Sharma, 2019).
7
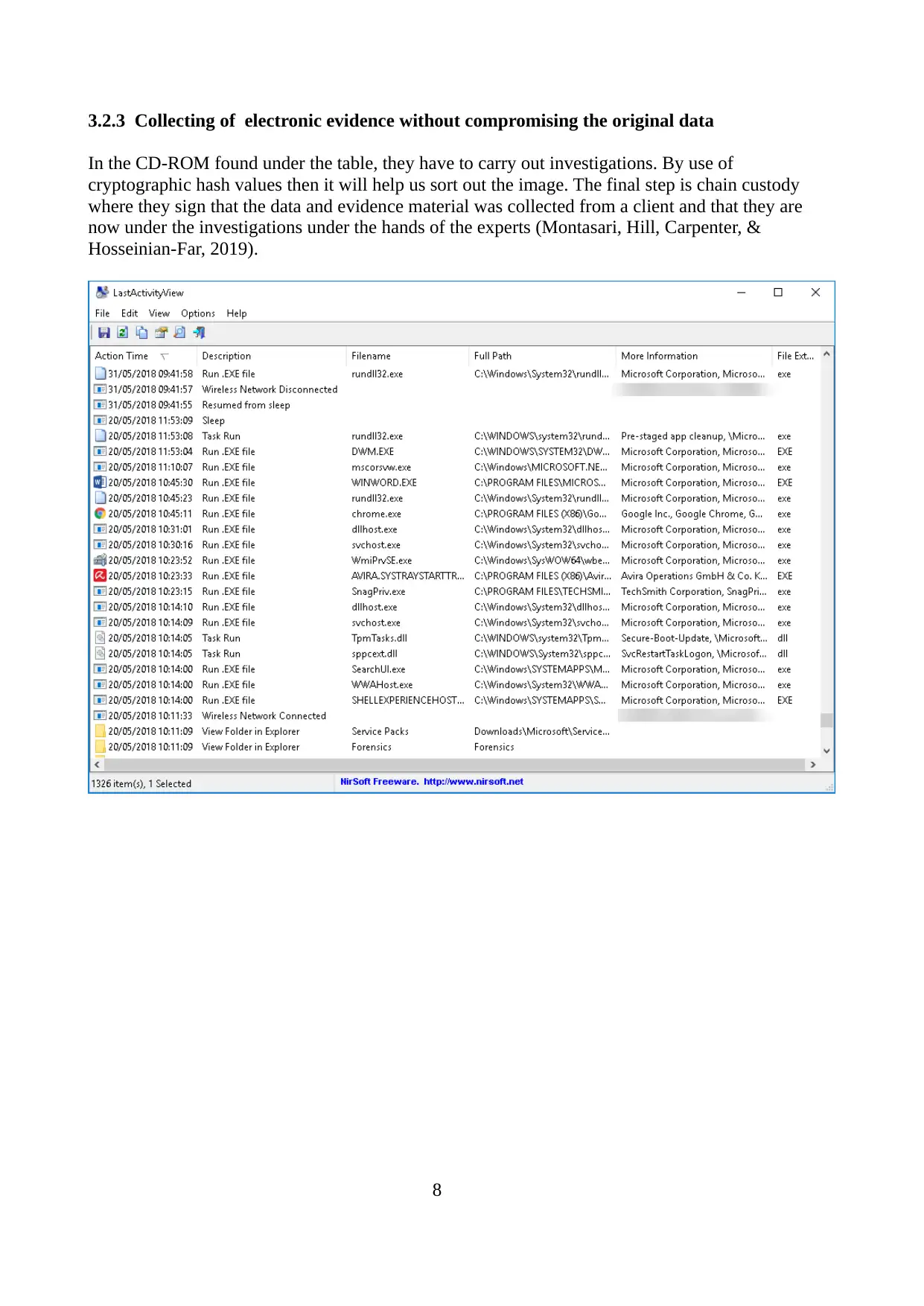
3.2.3 Collecting of electronic evidence without compromising the original data
In the CD-ROM found under the table, they have to carry out investigations. By use of
cryptographic hash values then it will help us sort out the image. The final step is chain custody
where they sign that the data and evidence material was collected from a client and that they are
now under the investigations under the hands of the experts (Montasari, Hill, Carpenter, &
Hosseinian-Far, 2019).
8
In the CD-ROM found under the table, they have to carry out investigations. By use of
cryptographic hash values then it will help us sort out the image. The final step is chain custody
where they sign that the data and evidence material was collected from a client and that they are
now under the investigations under the hands of the experts (Montasari, Hill, Carpenter, &
Hosseinian-Far, 2019).
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




