Computer Forensics Investigation on Clown Content Offence in Western Australia
VerifiedAdded on 2023/06/03
|47
|6608
|329
AI Summary
This report presents the progress of a computer forensics investigation on a clown content offence in a workplace in Western Australia. The report includes the identification of ownership, intention of crime, file quantity, and software installed. The resources used in the investigation are also discussed.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Computer Forensics
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
1. Introduction.......................................................................................................................................2
2. Resources............................................................................................................................................2
3. Progress..............................................................................................................................................2
3.1 Issue-1 Presentation of contents.........................................................................................................2
3.2 Identification of ownership.........................................................................................................28
3.3 Intention of Crime.......................................................................................................................30
3.4 File Quantity................................................................................................................................30
3.5 Software installed........................................................................................................................31
4. Conclusion........................................................................................................................................33
5. References........................................................................................................................................34
Appendix I –Running Sheet....................................................................................................................38
Appendix II –Timeline of Events............................................................................................................42
Page 1 of 47
1. Introduction.......................................................................................................................................2
2. Resources............................................................................................................................................2
3. Progress..............................................................................................................................................2
3.1 Issue-1 Presentation of contents.........................................................................................................2
3.2 Identification of ownership.........................................................................................................28
3.3 Intention of Crime.......................................................................................................................30
3.4 File Quantity................................................................................................................................30
3.5 Software installed........................................................................................................................31
4. Conclusion........................................................................................................................................33
5. References........................................................................................................................................34
Appendix I –Running Sheet....................................................................................................................38
Appendix II –Timeline of Events............................................................................................................42
Page 1 of 47

1. Introduction
The offence is take place in a work place at Western Australia. The Clark who works at
there is involved in that offence. The other Clark may be involved in that offence. The Clark’s
statement is that he did not always take the computer home or locked it when he is away from his
desk ("Operating System Forensics | National Initiative for Cybersecurity Careers and Studies",
2018). The liability of the suspects or victims may cause delay in the investigation. The offence
of accessing or owning clown content will be investigated. In the investigation, Clark is a main
suspect. The computer related to the investigation is seized and that belongs to Clark. The hard
drive of the computer is wiped away ("Hacking & Digital Forensics & Autopsy - Stay lunix",
2018). But the forensic image is obtained. In the forensic image, the clown related contents will
be searched ("FTK Imager: Lesson 4: Mount Image File, Recover Deleted File", 2018). The
investigation will be completed by October 2018 (Zhao, Zong & Wu, 2014). The investigation
will start in first week of October 2018. The factors which may affect the completion time of
analysis are installation of appropriate tools, technical issues etc. ("FTK Imager and Custom
Content Images", 2018).
2. Resources
The forensic tools and a computer is the resources needed for this entire investigation.
And also the investigators, suspects are also included. The forensic tools are the important thing
in the investigation ("FTK Imager: Lesson 1: Install FTK Imager", 2018) (Pattnaik & Jana,
2005).
FTK Imager ("FTK Imager 3.2.0", 2018)
Autopsy
OS Forensics
Page 2 of 47
The offence is take place in a work place at Western Australia. The Clark who works at
there is involved in that offence. The other Clark may be involved in that offence. The Clark’s
statement is that he did not always take the computer home or locked it when he is away from his
desk ("Operating System Forensics | National Initiative for Cybersecurity Careers and Studies",
2018). The liability of the suspects or victims may cause delay in the investigation. The offence
of accessing or owning clown content will be investigated. In the investigation, Clark is a main
suspect. The computer related to the investigation is seized and that belongs to Clark. The hard
drive of the computer is wiped away ("Hacking & Digital Forensics & Autopsy - Stay lunix",
2018). But the forensic image is obtained. In the forensic image, the clown related contents will
be searched ("FTK Imager: Lesson 4: Mount Image File, Recover Deleted File", 2018). The
investigation will be completed by October 2018 (Zhao, Zong & Wu, 2014). The investigation
will start in first week of October 2018. The factors which may affect the completion time of
analysis are installation of appropriate tools, technical issues etc. ("FTK Imager and Custom
Content Images", 2018).
2. Resources
The forensic tools and a computer is the resources needed for this entire investigation.
And also the investigators, suspects are also included. The forensic tools are the important thing
in the investigation ("FTK Imager: Lesson 1: Install FTK Imager", 2018) (Pattnaik & Jana,
2005).
FTK Imager ("FTK Imager 3.2.0", 2018)
Autopsy
OS Forensics
Page 2 of 47
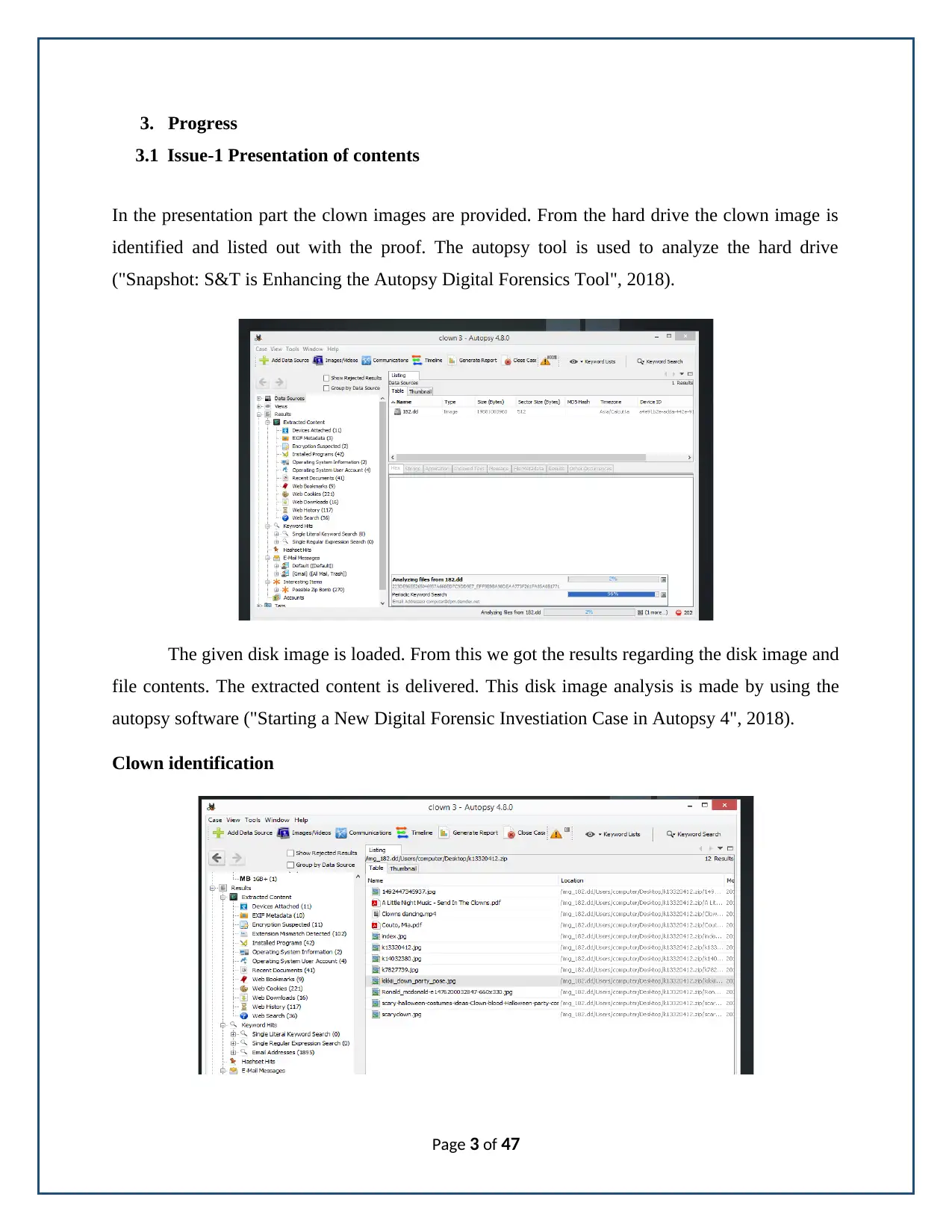
3. Progress
3.1 Issue-1 Presentation of contents
In the presentation part the clown images are provided. From the hard drive the clown image is
identified and listed out with the proof. The autopsy tool is used to analyze the hard drive
("Snapshot: S&T is Enhancing the Autopsy Digital Forensics Tool", 2018).
The given disk image is loaded. From this we got the results regarding the disk image and
file contents. The extracted content is delivered. This disk image analysis is made by using the
autopsy software ("Starting a New Digital Forensic Investiation Case in Autopsy 4", 2018).
Clown identification
Page 3 of 47
3.1 Issue-1 Presentation of contents
In the presentation part the clown images are provided. From the hard drive the clown image is
identified and listed out with the proof. The autopsy tool is used to analyze the hard drive
("Snapshot: S&T is Enhancing the Autopsy Digital Forensics Tool", 2018).
The given disk image is loaded. From this we got the results regarding the disk image and
file contents. The extracted content is delivered. This disk image analysis is made by using the
autopsy software ("Starting a New Digital Forensic Investiation Case in Autopsy 4", 2018).
Clown identification
Page 3 of 47
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

The desktop contents are analyzed. From the analysis we have found the clown images,
and the videos regarding the clown. The clown pdf such as a little night music is retrieved. Also
there are many images retrieved from the analysis regarding clown. The Clark downloaded the
clown images and stored in the computer desktop (Bell, 2018).
Clown image 1
Name /img_182.dd/Users/computer/Pictures/kikkii_clown_party_pose.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-19 05:20:05 AEST
Modified 2018-06-19 05:20:06 AEST
Size 50304
Accessed 2018-06-19 05:20:06 AEST
MD5 76e4975e5efc2a1268584fef7ade5f59
Internal ID 51651
Page 4 of 47
and the videos regarding the clown. The clown pdf such as a little night music is retrieved. Also
there are many images retrieved from the analysis regarding clown. The Clark downloaded the
clown images and stored in the computer desktop (Bell, 2018).
Clown image 1
Name /img_182.dd/Users/computer/Pictures/kikkii_clown_party_pose.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-19 05:20:05 AEST
Modified 2018-06-19 05:20:06 AEST
Size 50304
Accessed 2018-06-19 05:20:06 AEST
MD5 76e4975e5efc2a1268584fef7ade5f59
Internal ID 51651
Page 4 of 47

The clown image is identified. The name is ‘kikkii_clown_party_pose’. This clown
image is downloaded and stored in the pictures folder by the suspect. At the same time he made
the email to someone regarding the clown content. The device model is Canon EOS IOD. This
picture is taken by the device Canon. It is presented in the EXIF Meta data. From the file Meta
data we can able to find the creation time of the file. Based on this time the investigator required
to identify any suspicious activity during the same time (Galvao, 2006) (Imager & AccessData
Group, 2018).
Clown image 2
Name /img_182.dd/Users/computer/Desktop/k7827739.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:52:14 AEST
Modified 2018-07-02 06:52:15 AEST
Size 41284
Accessed 2018-07-02 06:52:14 AEST
MD5 39db918c4014d3a64fabbc17a2fe49a7
Internal ID 51461
From the Clark’s Laptop hard disk image file there are number of pictures and some
other files are founded (mannaza, 2018). Among the various pictures and videos some of them
Page 5 of 47
image is downloaded and stored in the pictures folder by the suspect. At the same time he made
the email to someone regarding the clown content. The device model is Canon EOS IOD. This
picture is taken by the device Canon. It is presented in the EXIF Meta data. From the file Meta
data we can able to find the creation time of the file. Based on this time the investigator required
to identify any suspicious activity during the same time (Galvao, 2006) (Imager & AccessData
Group, 2018).
Clown image 2
Name /img_182.dd/Users/computer/Desktop/k7827739.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:52:14 AEST
Modified 2018-07-02 06:52:15 AEST
Size 41284
Accessed 2018-07-02 06:52:14 AEST
MD5 39db918c4014d3a64fabbc17a2fe49a7
Internal ID 51461
From the Clark’s Laptop hard disk image file there are number of pictures and some
other files are founded (mannaza, 2018). Among the various pictures and videos some of them
Page 5 of 47

are related to the clown. The above illustrated picture is one of the clown picture retrieved from
the Clark’s laptop image file. The name of the file is “K7827739” and the file is founded on the
desktop. This picture file is a .jpeg format. And the files internal ID is 51461. In the above shown
table contains the various information about the file. The table contains the file meta details like
file type, MIME type, and file created time and modified time etc. these details are highly
helpful for find the person who download those files (Morrison & Petrisor, 2004). It also
provides the access log details. Here the access log is a set of information. The picture is
downloaded on (2018-07-02 06:52:14 AEST). So the investigator required to check whether
there is any noticeable actions are done by the suspect on the particular time period. From that
we may know about the person who created this file on Clark’s system.
Clown image 3
Name /img_182.dd/Users/computer/Desktop/k14032380.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:51:52 AEST
Modified 2018-07-02 06:51:52 AEST
Size 31837
Accessed 2018-07-02 06:51:52 AEST
MD5 913cb94539abfe8de858ce16c0a40e99
Page 6 of 47
the Clark’s laptop image file. The name of the file is “K7827739” and the file is founded on the
desktop. This picture file is a .jpeg format. And the files internal ID is 51461. In the above shown
table contains the various information about the file. The table contains the file meta details like
file type, MIME type, and file created time and modified time etc. these details are highly
helpful for find the person who download those files (Morrison & Petrisor, 2004). It also
provides the access log details. Here the access log is a set of information. The picture is
downloaded on (2018-07-02 06:52:14 AEST). So the investigator required to check whether
there is any noticeable actions are done by the suspect on the particular time period. From that
we may know about the person who created this file on Clark’s system.
Clown image 3
Name /img_182.dd/Users/computer/Desktop/k14032380.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:51:52 AEST
Modified 2018-07-02 06:51:52 AEST
Size 31837
Accessed 2018-07-02 06:51:52 AEST
MD5 913cb94539abfe8de858ce16c0a40e99
Page 6 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Internal ID 51458
Also another clown’s picture founded from the Clark’s Laptop image hard disk image
file. And the file name is k14032380. Similar to the previous picture it is also related to the
clown (Mudge, 2007). So this picture is also considered as the evidence for containing the
suspicious data in the Laptop. This picture clearly shows that suspect’s laptop contains the data
about the clown. Here also the created time, modified time as well as accessed time for the files
are founded form the file meta data. This particular picture file is created on 2018-07-02
06:51:52 AEST. Here also the investigator required to check any evidences regarding to the
suspects access during this time on other processes like sending mails, opening mails etc. From
the file Meta data also the various information like MIME type, size of the file etc are founded
and those information are tabulated.
Clown image 4
Name /img_182.dd/Users/computer/Desktop/k13320412.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:45:08 AEST
Modified 2018-07-02 06:45:08 AEST
Page 7 of 47
Also another clown’s picture founded from the Clark’s Laptop image hard disk image
file. And the file name is k14032380. Similar to the previous picture it is also related to the
clown (Mudge, 2007). So this picture is also considered as the evidence for containing the
suspicious data in the Laptop. This picture clearly shows that suspect’s laptop contains the data
about the clown. Here also the created time, modified time as well as accessed time for the files
are founded form the file meta data. This particular picture file is created on 2018-07-02
06:51:52 AEST. Here also the investigator required to check any evidences regarding to the
suspects access during this time on other processes like sending mails, opening mails etc. From
the file Meta data also the various information like MIME type, size of the file etc are founded
and those information are tabulated.
Clown image 4
Name /img_182.dd/Users/computer/Desktop/k13320412.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:45:08 AEST
Modified 2018-07-02 06:45:08 AEST
Page 7 of 47

Size 35546
Accessed 2018-07-02 06:45:08 AEST
MD5 e5ab36f6264d22714a88d53338469f95
Internal ID 51453
The clown image of “k13320412.jpg” is obtained from the analysis. It is retrieved from
the user desktop files. As similar to the above three images it is also related to clown. So this file
also considered as an evidence against suspect. As similar to other three pictures this file
also .jpeg format image file. It is created on 2018-07-02 06:45:08 AEST in suspect’s laptop. Also
the time of creation as well as time of modification are founded from the file Meta data. So the
investigator required to search about any noticeable actions on the above mentioned time. If any
actions are carried out by the suspect on the above mentioned time helps to prove that the suspect
having the system when the suspicious files creation.
Clown image 5
Name /img_182.dd/Users/computer/Pictures/scary-halloween-costumes-
ideas-Clown-blood-Halloween-party-costumes-e1410943909179.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-18 05:51:54 AEST
Modified 2018-06-18 05:51:55 AEST
Size 59178
Accessed 2018-06-18 05:51:54 AEST
Page 8 of 47
Accessed 2018-07-02 06:45:08 AEST
MD5 e5ab36f6264d22714a88d53338469f95
Internal ID 51453
The clown image of “k13320412.jpg” is obtained from the analysis. It is retrieved from
the user desktop files. As similar to the above three images it is also related to clown. So this file
also considered as an evidence against suspect. As similar to other three pictures this file
also .jpeg format image file. It is created on 2018-07-02 06:45:08 AEST in suspect’s laptop. Also
the time of creation as well as time of modification are founded from the file Meta data. So the
investigator required to search about any noticeable actions on the above mentioned time. If any
actions are carried out by the suspect on the above mentioned time helps to prove that the suspect
having the system when the suspicious files creation.
Clown image 5
Name /img_182.dd/Users/computer/Pictures/scary-halloween-costumes-
ideas-Clown-blood-Halloween-party-costumes-e1410943909179.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-18 05:51:54 AEST
Modified 2018-06-18 05:51:55 AEST
Size 59178
Accessed 2018-06-18 05:51:54 AEST
Page 8 of 47

MD5 51632444d9845cc6686adcf24e536f77
Internal ID 51664
The clown image is identified from the disk analysis. This image is presented in the
computer desktop. The suspect clerk only downloaded this image. History is presented in the
web bookmarks. This picture also related to clown. So it is also considered as the evidence for
the suspicious activity. Form the conducted DF analysis the Meta data of the file retrieved. From
the file Meta data we can able to identify the information like creation time etc. (Ochiai,
Yamakawa, Fukushima, Yamada & Hayashi, 2000).
Clown image 6
Name /img_182.dd/Users/computer/Pictures/s-l640.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-19 05:20:17 AEST
Modified 2018-06-19 05:20:17 AEST
Size 57620
Accessed 2018-06-19 05:20:17 AEST
MD5 dd42fe966af825567338e4f873cc2f6a
Page 9 of 47
Internal ID 51664
The clown image is identified from the disk analysis. This image is presented in the
computer desktop. The suspect clerk only downloaded this image. History is presented in the
web bookmarks. This picture also related to clown. So it is also considered as the evidence for
the suspicious activity. Form the conducted DF analysis the Meta data of the file retrieved. From
the file Meta data we can able to identify the information like creation time etc. (Ochiai,
Yamakawa, Fukushima, Yamada & Hayashi, 2000).
Clown image 6
Name /img_182.dd/Users/computer/Pictures/s-l640.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-19 05:20:17 AEST
Modified 2018-06-19 05:20:17 AEST
Size 57620
Accessed 2018-06-19 05:20:17 AEST
MD5 dd42fe966af825567338e4f873cc2f6a
Page 9 of 47
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Internal ID 51657
It is presented in the pictures folder. The modified time, change time and access time are
obtained regarding the clown image. The application sector is used to display the clown image.
As similar to the other founded pictures this picture also related to clown. So this picture also
considered as the evidence for the suspicious activity. File Meta data are retrieved from the
image file. From the retrieved file Meta data we can able to identify the information like
creation time etc. These details may helpful for prove the crime is done by the Clark. In the
given table the various Meta details about the file are given.
Clown image 7
Name /img_182.dd/Users/computer/Pictures/1492447345937.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-18 05:52:15 AEST
Modified 2018-06-18 05:52:15 AEST
Size 17134
Accessed 2018-06-18 05:52:15 AEST
MD5 3e58af33ebb789d5d81cb4ac613a76c9
Page 10 of 47
It is presented in the pictures folder. The modified time, change time and access time are
obtained regarding the clown image. The application sector is used to display the clown image.
As similar to the other founded pictures this picture also related to clown. So this picture also
considered as the evidence for the suspicious activity. File Meta data are retrieved from the
image file. From the retrieved file Meta data we can able to identify the information like
creation time etc. These details may helpful for prove the crime is done by the Clark. In the
given table the various Meta details about the file are given.
Clown image 7
Name /img_182.dd/Users/computer/Pictures/1492447345937.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-18 05:52:15 AEST
Modified 2018-06-18 05:52:15 AEST
Size 17134
Accessed 2018-06-18 05:52:15 AEST
MD5 3e58af33ebb789d5d81cb4ac613a76c9
Page 10 of 47
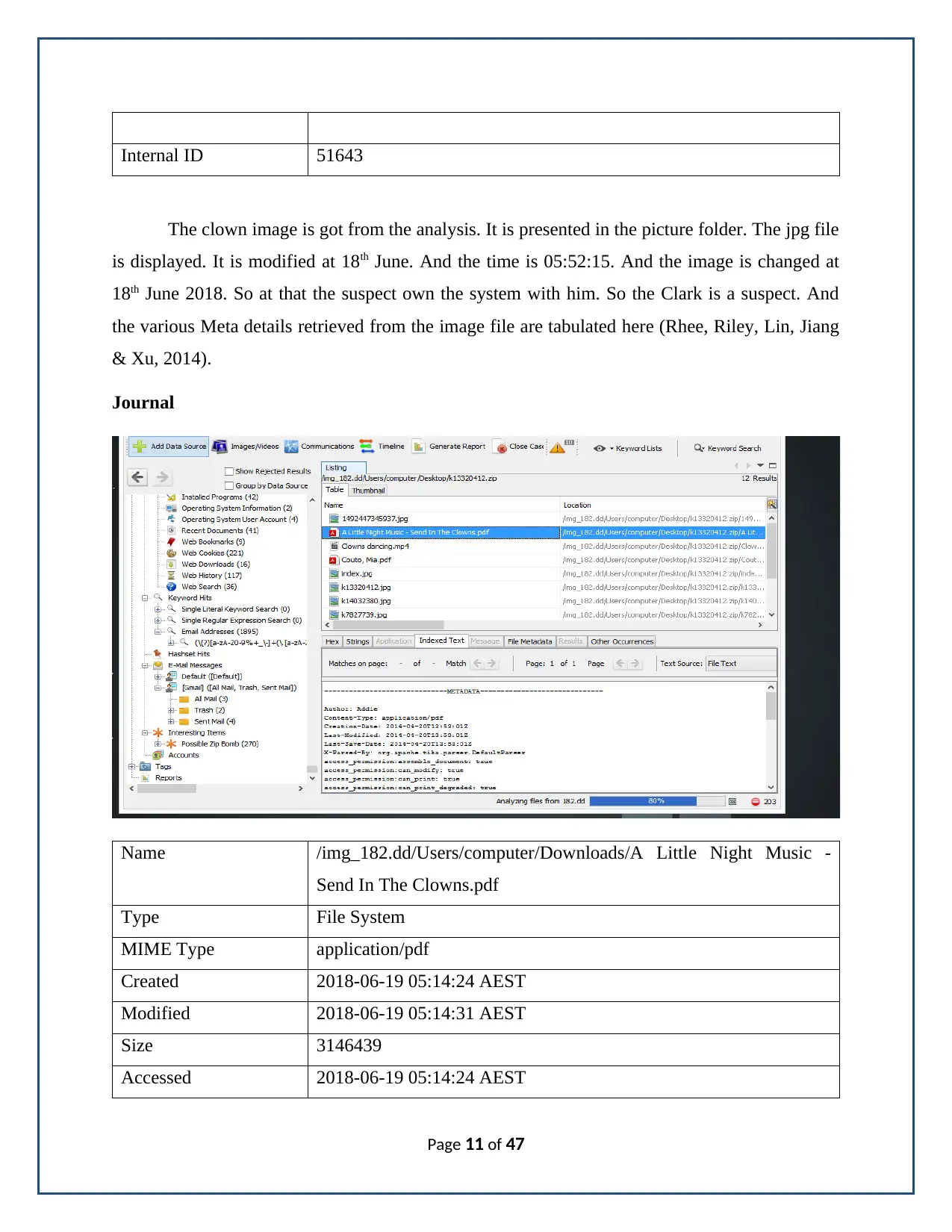
Internal ID 51643
The clown image is got from the analysis. It is presented in the picture folder. The jpg file
is displayed. It is modified at 18th June. And the time is 05:52:15. And the image is changed at
18th June 2018. So at that the suspect own the system with him. So the Clark is a suspect. And
the various Meta details retrieved from the image file are tabulated here (Rhee, Riley, Lin, Jiang
& Xu, 2014).
Journal
Name /img_182.dd/Users/computer/Downloads/A Little Night Music -
Send In The Clowns.pdf
Type File System
MIME Type application/pdf
Created 2018-06-19 05:14:24 AEST
Modified 2018-06-19 05:14:31 AEST
Size 3146439
Accessed 2018-06-19 05:14:24 AEST
Page 11 of 47
The clown image is got from the analysis. It is presented in the picture folder. The jpg file
is displayed. It is modified at 18th June. And the time is 05:52:15. And the image is changed at
18th June 2018. So at that the suspect own the system with him. So the Clark is a suspect. And
the various Meta details retrieved from the image file are tabulated here (Rhee, Riley, Lin, Jiang
& Xu, 2014).
Journal
Name /img_182.dd/Users/computer/Downloads/A Little Night Music -
Send In The Clowns.pdf
Type File System
MIME Type application/pdf
Created 2018-06-19 05:14:24 AEST
Modified 2018-06-19 05:14:31 AEST
Size 3146439
Accessed 2018-06-19 05:14:24 AEST
Page 11 of 47
MD5 4f640bc32c0ac35b585a814ee5235df4
Internal ID 51565
The clown pdf content is modified at 20th April 2014. The author of this pdf is Addie.
And the content type is application or pdf. It is parsed by default parser. This pdf is searched by
the suspect through the web. So we can decide the Clark is a suspect. The pdf name is A Little
Night Music- Send in the Clowns. Pdf. It is created by the suspect Clark. Because it is
downloaded at 16.09.2018. And the time is 05:14:29. But it is accessed by the Clark at 05:14:31
on the same day. So it must be accessed by the Clark (Petrisor, 2005) (Petrisor, 2007).
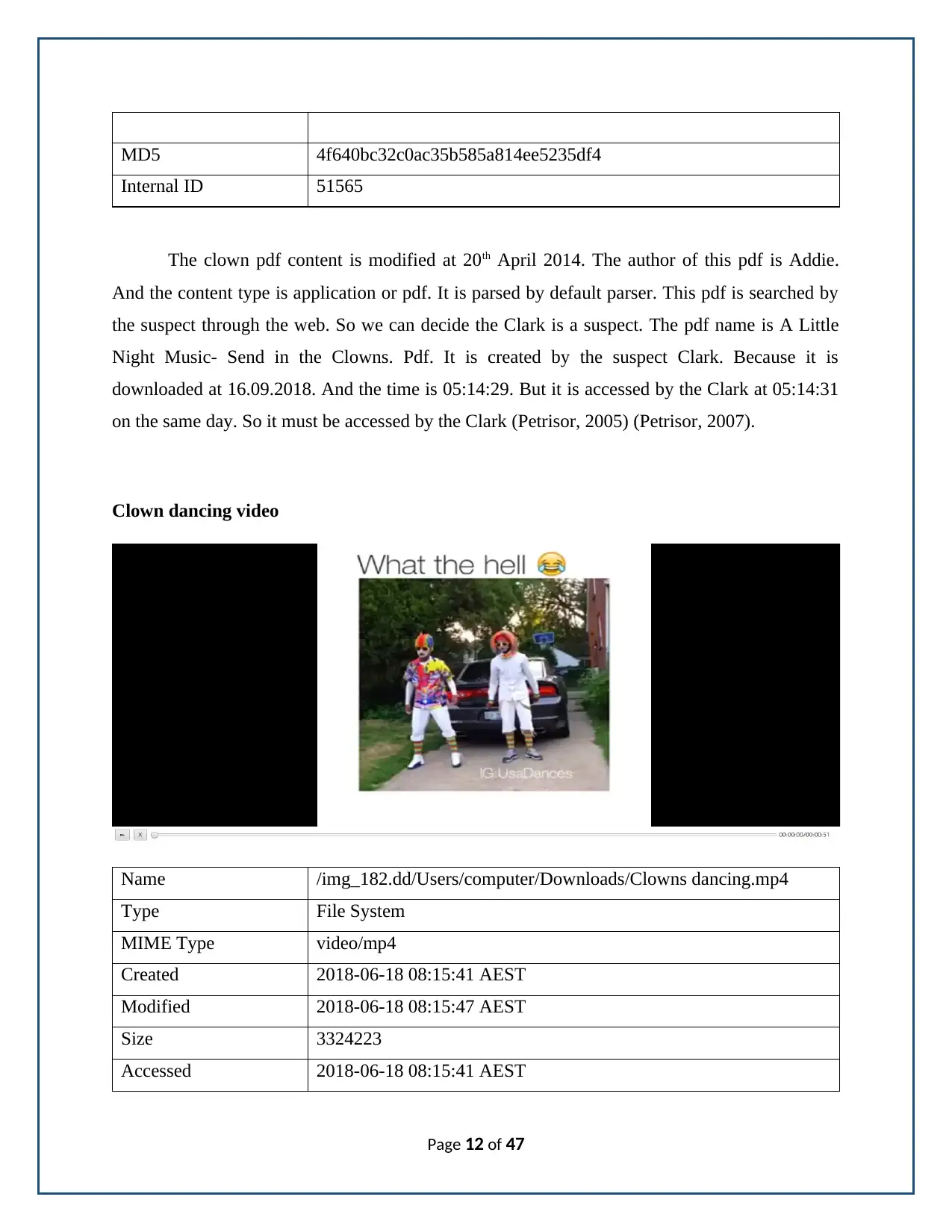
Clown dancing video
Name /img_182.dd/Users/computer/Downloads/Clowns dancing.mp4
Type File System
MIME Type video/mp4
Created 2018-06-18 08:15:41 AEST
Modified 2018-06-18 08:15:47 AEST
Size 3324223
Accessed 2018-06-18 08:15:41 AEST
Page 12 of 47
Internal ID 51565
The clown pdf content is modified at 20th April 2014. The author of this pdf is Addie.
And the content type is application or pdf. It is parsed by default parser. This pdf is searched by
the suspect through the web. So we can decide the Clark is a suspect. The pdf name is A Little
Night Music- Send in the Clowns. Pdf. It is created by the suspect Clark. Because it is
downloaded at 16.09.2018. And the time is 05:14:29. But it is accessed by the Clark at 05:14:31
on the same day. So it must be accessed by the Clark (Petrisor, 2005) (Petrisor, 2007).
Clown dancing video
Name /img_182.dd/Users/computer/Downloads/Clowns dancing.mp4
Type File System
MIME Type video/mp4
Created 2018-06-18 08:15:41 AEST
Modified 2018-06-18 08:15:47 AEST
Size 3324223
Accessed 2018-06-18 08:15:41 AEST
Page 12 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MD5 071f555cf58073ed4ebfb92915a8491a
Internal ID 51568
The clown dancing video is discovered from the analysis. It may be created by the Clark.
From the above details we can get the suspect. The Clark downloaded the image at 18th June
2018. And the time is 8:51:41. But it is modified by the client at 8:15:47. So within ten seconds
the clown image accessed. So the suspect would be a Clark (Tudorachi, 2014).
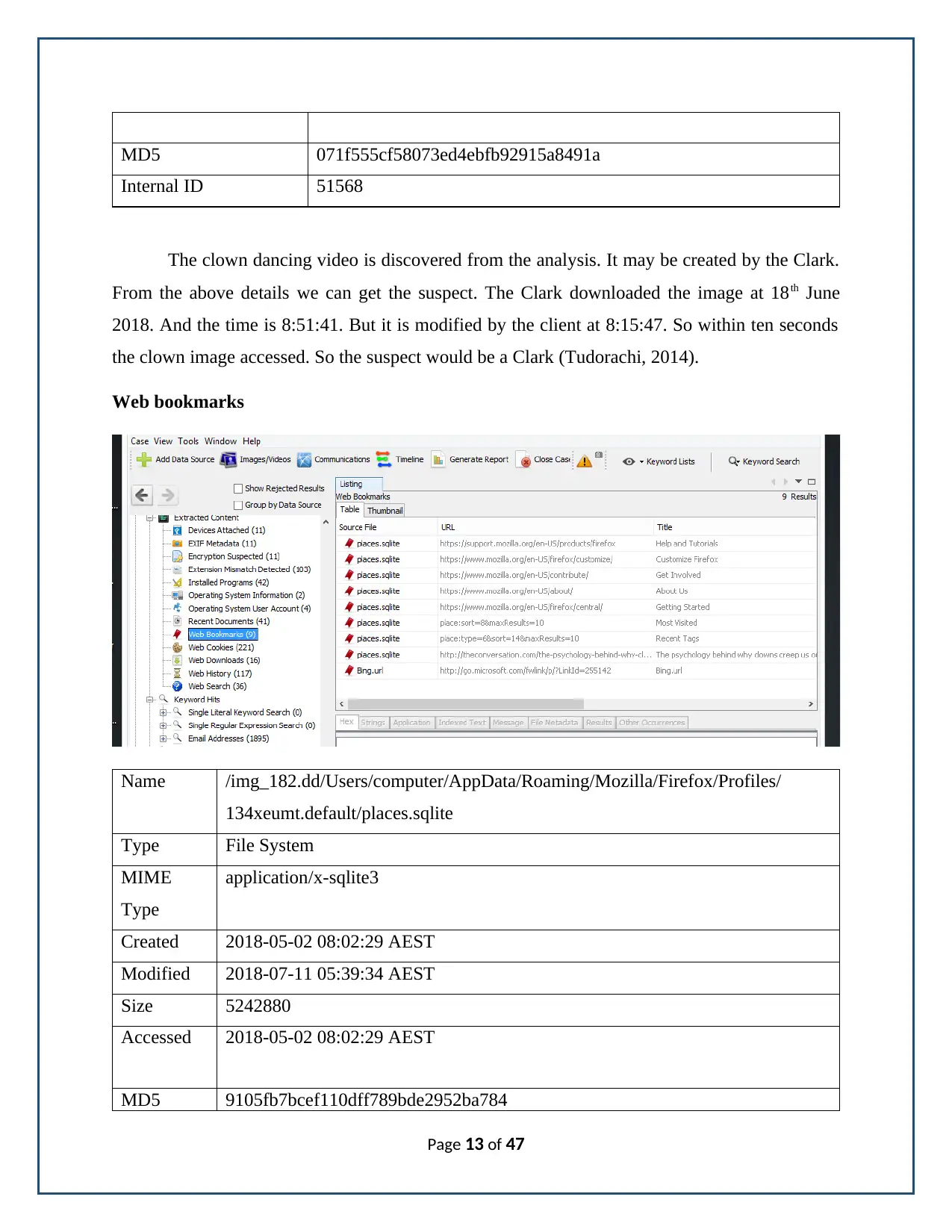
Web bookmarks
Name /img_182.dd/Users/computer/AppData/Roaming/Mozilla/Firefox/Profiles/
134xeumt.default/places.sqlite
Type File System
MIME
Type
application/x-sqlite3
Created 2018-05-02 08:02:29 AEST
Modified 2018-07-11 05:39:34 AEST
Size 5242880
Accessed 2018-05-02 08:02:29 AEST
MD5 9105fb7bcef110dff789bde2952ba784
Page 13 of 47
Internal ID 51568
The clown dancing video is discovered from the analysis. It may be created by the Clark.
From the above details we can get the suspect. The Clark downloaded the image at 18th June
2018. And the time is 8:51:41. But it is modified by the client at 8:15:47. So within ten seconds
the clown image accessed. So the suspect would be a Clark (Tudorachi, 2014).
Web bookmarks
Name /img_182.dd/Users/computer/AppData/Roaming/Mozilla/Firefox/Profiles/
134xeumt.default/places.sqlite
Type File System
MIME
Type
application/x-sqlite3
Created 2018-05-02 08:02:29 AEST
Modified 2018-07-11 05:39:34 AEST
Size 5242880
Accessed 2018-05-02 08:02:29 AEST
MD5 9105fb7bcef110dff789bde2952ba784
Page 13 of 47

Internal ID 50432
In the bookmark the URL is represented for the searching of ‘The psychology behind
why the clowns creeps us out’. It is searched by the suspect. Because it is created at 02/05/2018.
The time is 08:02:29. The file is contained in the computer user. So there is a chance for
searching the clown content by the Clark.
Web Cookies
From the analysis we have found the web cookies. 221 web cookies are found here. The
search URL links are Mozilla.org, yahoo.com and domex.com and etc. The time is 08:59. The
searches are made regarding the clown. So from the cookies we can ensure the Clark is a suspect
(Tabona, 2018).
Web Downloads
Page 14 of 47
In the bookmark the URL is represented for the searching of ‘The psychology behind
why the clowns creeps us out’. It is searched by the suspect. Because it is created at 02/05/2018.
The time is 08:02:29. The file is contained in the computer user. So there is a chance for
searching the clown content by the Clark.
Web Cookies
From the analysis we have found the web cookies. 221 web cookies are found here. The
search URL links are Mozilla.org, yahoo.com and domex.com and etc. The time is 08:59. The
searches are made regarding the clown. So from the cookies we can ensure the Clark is a suspect
(Tabona, 2018).
Web Downloads
Page 14 of 47
Name /img_182.dd/Users/computer/AppData/Roaming/Mozilla/Firefox/Profiles/
134xeumt.default/places.sqlite
Type File System
MIME
Type
application/x-sqlite3
Created 2018-05-02 08:02:29 AEST
Modified 2018-07-11 05:39:34 AEST
Size 5242880
Accessed 2018-05-02 08:02:29 AEST
MD5 9105fb7bcef110dff789bde2952ba784
Internal ID 50432
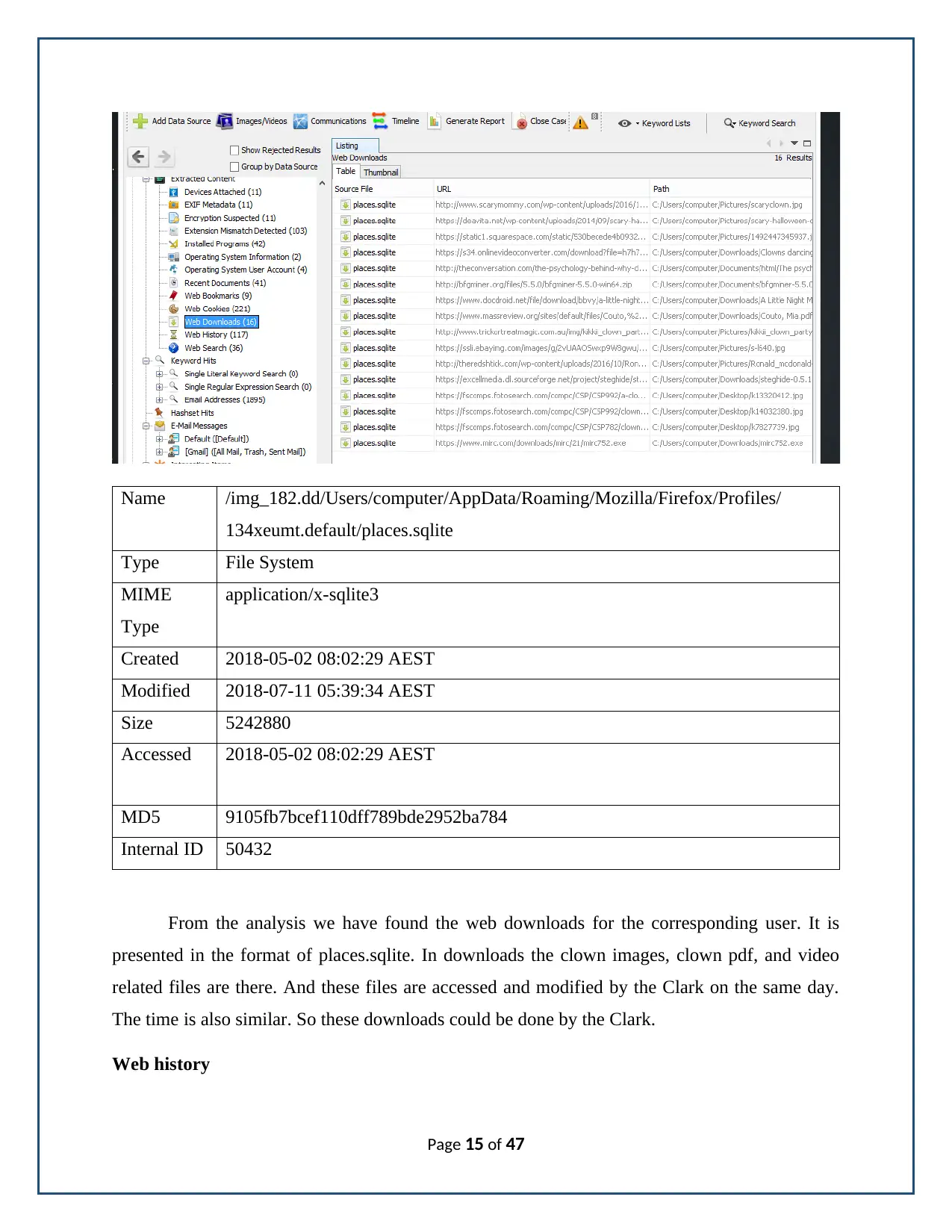
From the analysis we have found the web downloads for the corresponding user. It is
presented in the format of places.sqlite. In downloads the clown images, clown pdf, and video
related files are there. And these files are accessed and modified by the Clark on the same day.
The time is also similar. So these downloads could be done by the Clark.
Web history
Page 15 of 47
134xeumt.default/places.sqlite
Type File System
MIME
Type
application/x-sqlite3
Created 2018-05-02 08:02:29 AEST
Modified 2018-07-11 05:39:34 AEST
Size 5242880
Accessed 2018-05-02 08:02:29 AEST
MD5 9105fb7bcef110dff789bde2952ba784
Internal ID 50432
From the analysis we have found the web downloads for the corresponding user. It is
presented in the format of places.sqlite. In downloads the clown images, clown pdf, and video
related files are there. And these files are accessed and modified by the Clark on the same day.
The time is also similar. So these downloads could be done by the Clark.
Web history
Page 15 of 47
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
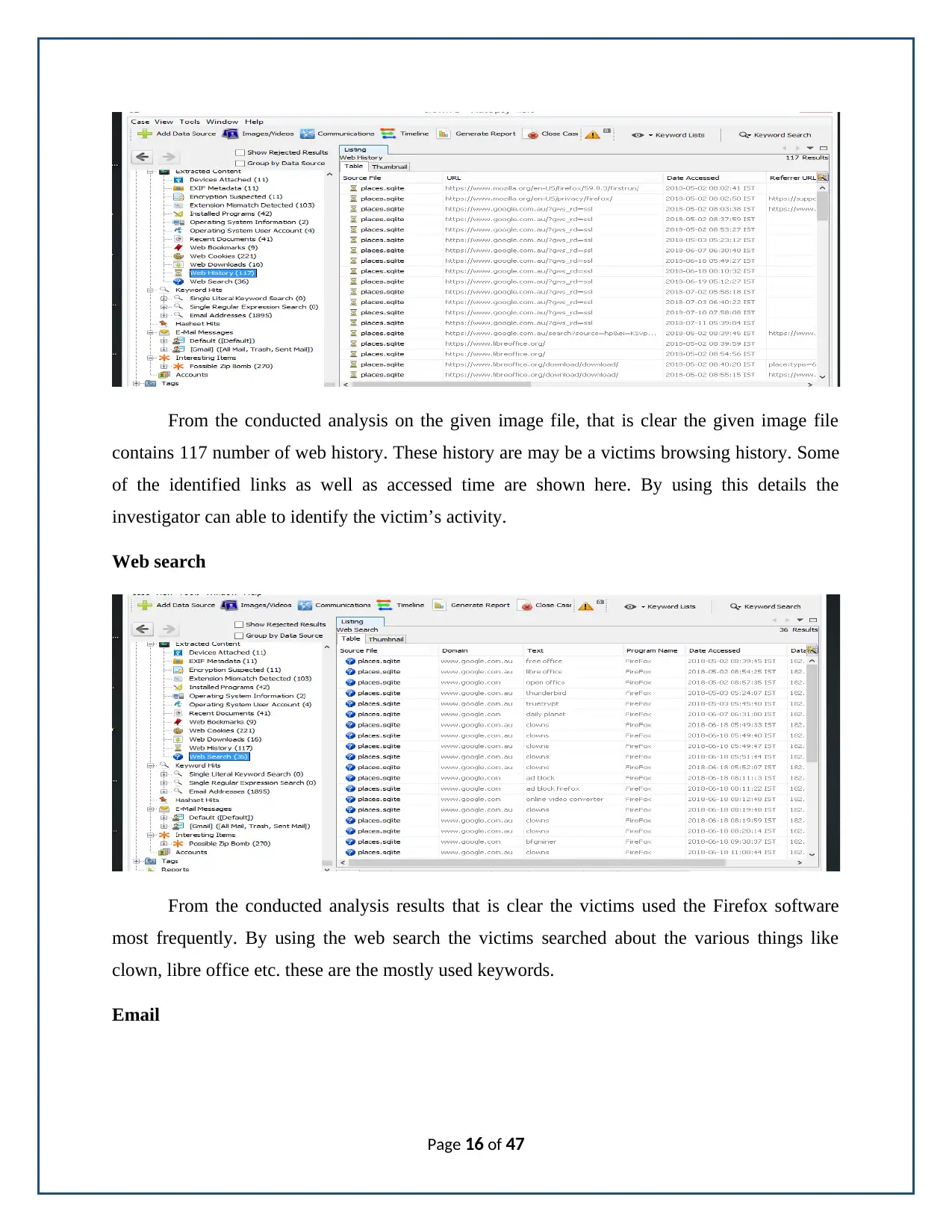
From the conducted analysis on the given image file, that is clear the given image file
contains 117 number of web history. These history are may be a victims browsing history. Some
of the identified links as well as accessed time are shown here. By using this details the
investigator can able to identify the victim’s activity.
Web search
From the conducted analysis results that is clear the victims used the Firefox software
most frequently. By using the web search the victims searched about the various things like
clown, libre office etc. these are the mostly used keywords.
Email
Page 16 of 47
contains 117 number of web history. These history are may be a victims browsing history. Some
of the identified links as well as accessed time are shown here. By using this details the
investigator can able to identify the victim’s activity.
Web search
From the conducted analysis results that is clear the victims used the Firefox software
most frequently. By using the web search the victims searched about the various things like
clown, libre office etc. these are the mostly used keywords.
Page 16 of 47

Name /img_182.dd/Users/computer/AppData/Roaming/Thunderbird/Profiles/
1cug4fub.default/ImapMail/imap.gmail.com/[Gmail].sbd/All Mail
Type File System
MIME
Type
application/mbox
Created 2018-06-19 05:19:41 AEST
Modified 2018-07-11 05:41:54 AEST
Page 17 of 47
1cug4fub.default/ImapMail/imap.gmail.com/[Gmail].sbd/All Mail
Type File System
MIME
Type
application/mbox
Created 2018-06-19 05:19:41 AEST
Modified 2018-07-11 05:41:54 AEST
Page 17 of 47
Size 3786
Accessed 2018-06-19 05:19:41 AEST
MD5 aa3afa26bc9f18b9cd12b48f5281aa31
Internal ID 51316
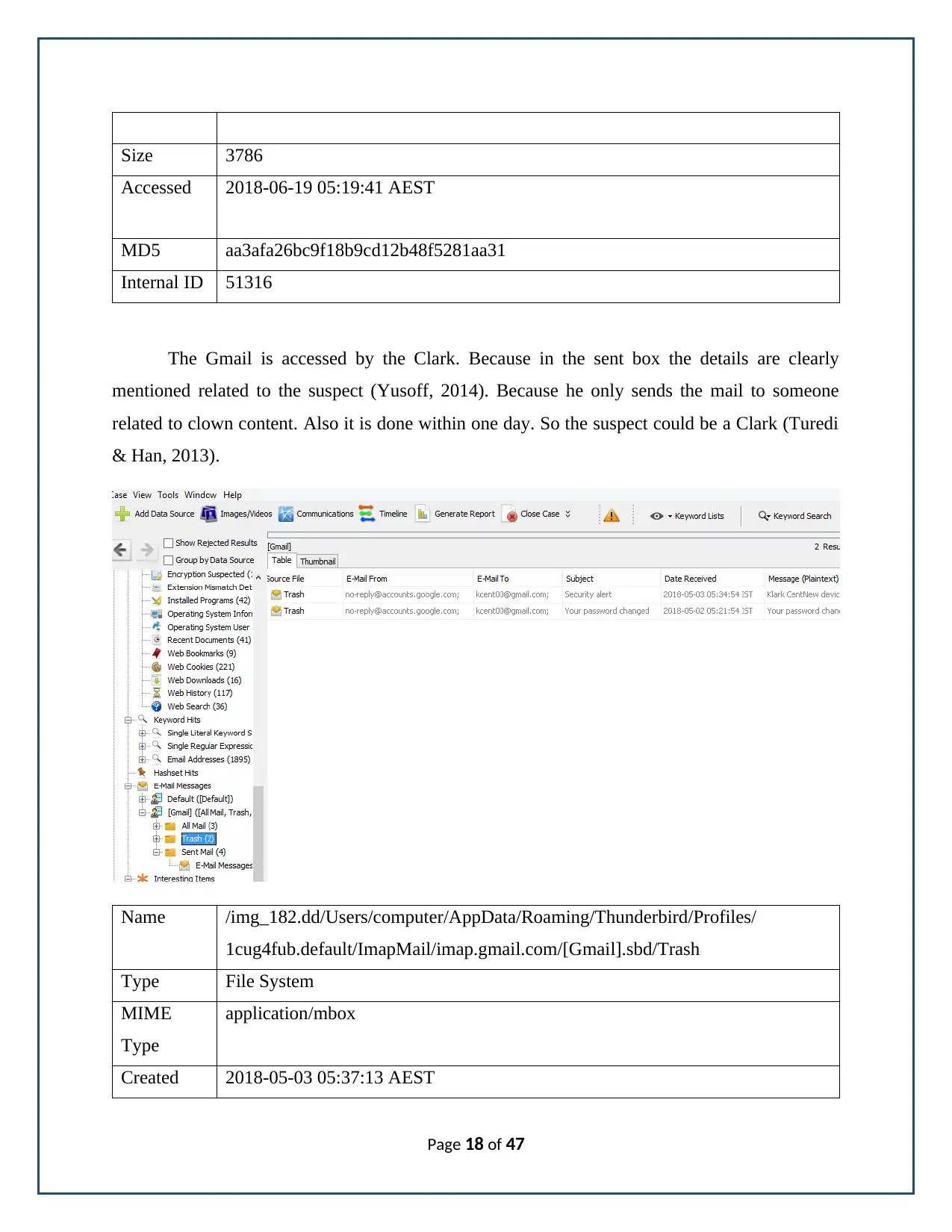
The Gmail is accessed by the Clark. Because in the sent box the details are clearly
mentioned related to the suspect (Yusoff, 2014). Because he only sends the mail to someone
related to clown content. Also it is done within one day. So the suspect could be a Clark (Turedi
& Han, 2013).
Name /img_182.dd/Users/computer/AppData/Roaming/Thunderbird/Profiles/
1cug4fub.default/ImapMail/imap.gmail.com/[Gmail].sbd/Trash
Type File System
MIME
Type
application/mbox
Created 2018-05-03 05:37:13 AEST
Page 18 of 47
Accessed 2018-06-19 05:19:41 AEST
MD5 aa3afa26bc9f18b9cd12b48f5281aa31
Internal ID 51316
The Gmail is accessed by the Clark. Because in the sent box the details are clearly
mentioned related to the suspect (Yusoff, 2014). Because he only sends the mail to someone
related to clown content. Also it is done within one day. So the suspect could be a Clark (Turedi
& Han, 2013).
Name /img_182.dd/Users/computer/AppData/Roaming/Thunderbird/Profiles/
1cug4fub.default/ImapMail/imap.gmail.com/[Gmail].sbd/Trash
Type File System
MIME
Type
application/mbox
Created 2018-05-03 05:37:13 AEST
Page 18 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Modified 2018-05-03 05:37:13 AEST
Size 24471
Accessed 2018-05-03 05:37:13 AEST
MD5 79241349ac5732b8dd37a3839bbf6c1e
Internal ID 51332
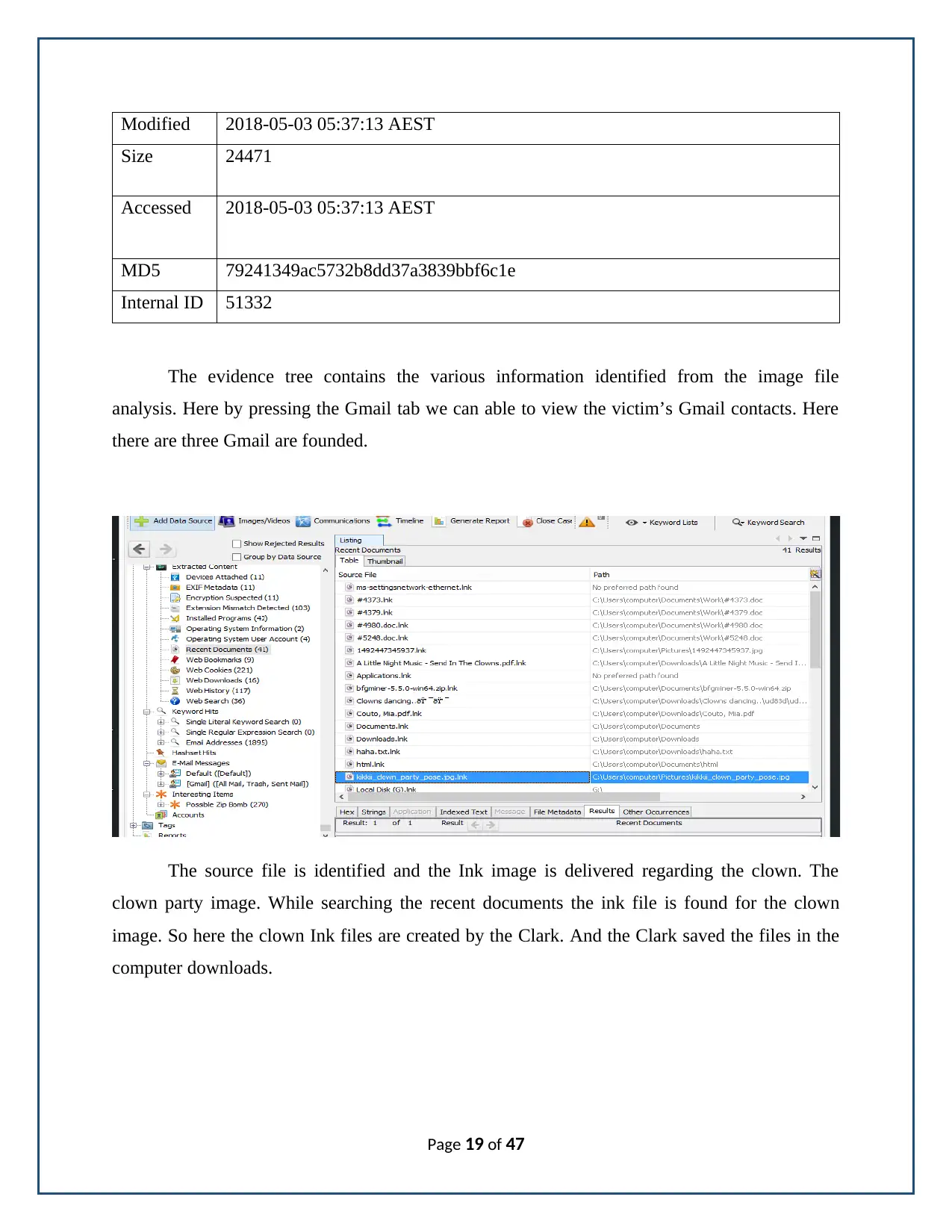
The evidence tree contains the various information identified from the image file
analysis. Here by pressing the Gmail tab we can able to view the victim’s Gmail contacts. Here
there are three Gmail are founded.
The source file is identified and the Ink image is delivered regarding the clown. The
clown party image. While searching the recent documents the ink file is found for the clown
image. So here the clown Ink files are created by the Clark. And the Clark saved the files in the
computer downloads.
Page 19 of 47
Size 24471
Accessed 2018-05-03 05:37:13 AEST
MD5 79241349ac5732b8dd37a3839bbf6c1e
Internal ID 51332
The evidence tree contains the various information identified from the image file
analysis. Here by pressing the Gmail tab we can able to view the victim’s Gmail contacts. Here
there are three Gmail are founded.
The source file is identified and the Ink image is delivered regarding the clown. The
clown party image. While searching the recent documents the ink file is found for the clown
image. So here the clown Ink files are created by the Clark. And the Clark saved the files in the
computer downloads.
Page 19 of 47
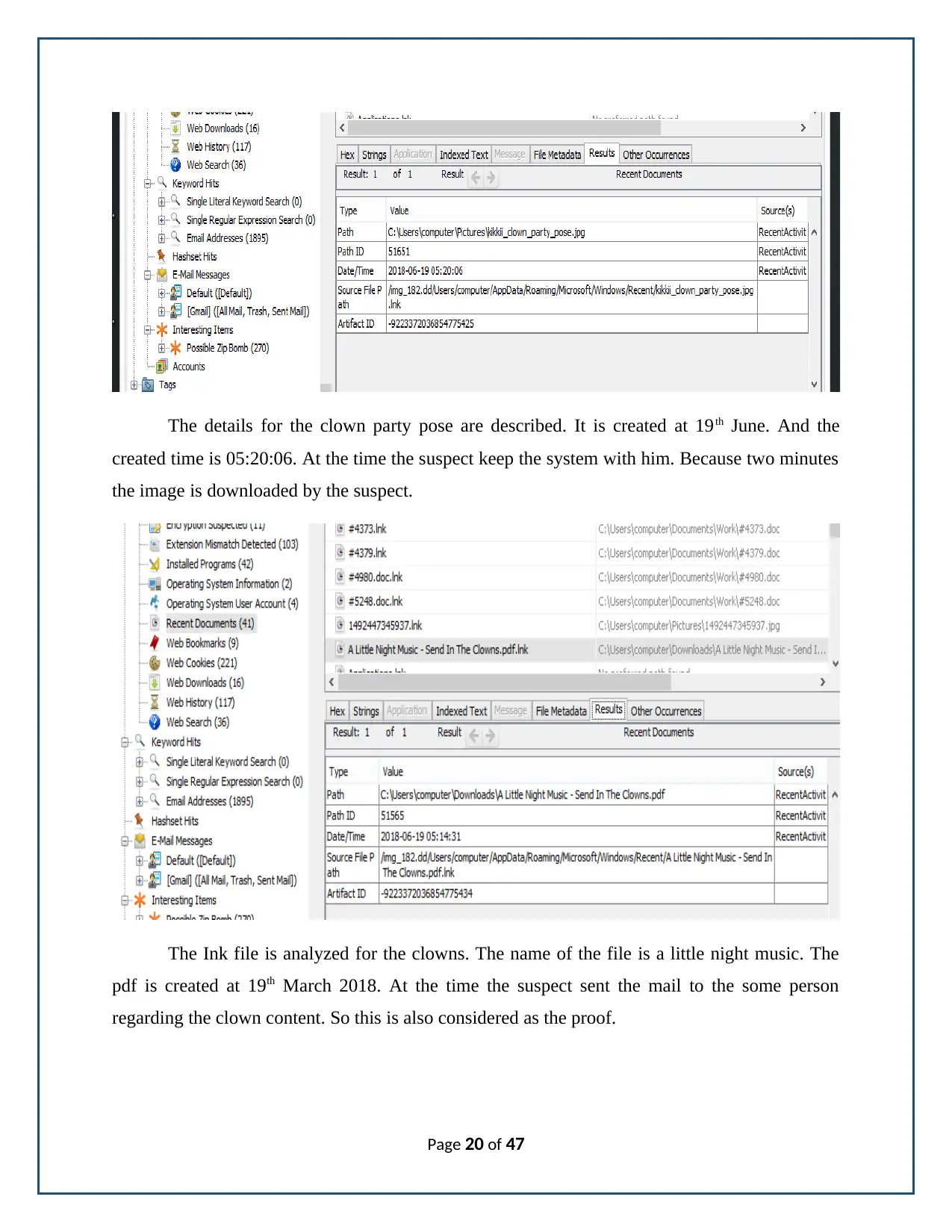
The details for the clown party pose are described. It is created at 19th June. And the
created time is 05:20:06. At the time the suspect keep the system with him. Because two minutes
the image is downloaded by the suspect.
The Ink file is analyzed for the clowns. The name of the file is a little night music. The
pdf is created at 19th March 2018. At the time the suspect sent the mail to the some person
regarding the clown content. So this is also considered as the proof.
Page 20 of 47
created time is 05:20:06. At the time the suspect keep the system with him. Because two minutes
the image is downloaded by the suspect.
The Ink file is analyzed for the clowns. The name of the file is a little night music. The
pdf is created at 19th March 2018. At the time the suspect sent the mail to the some person
regarding the clown content. So this is also considered as the proof.
Page 20 of 47
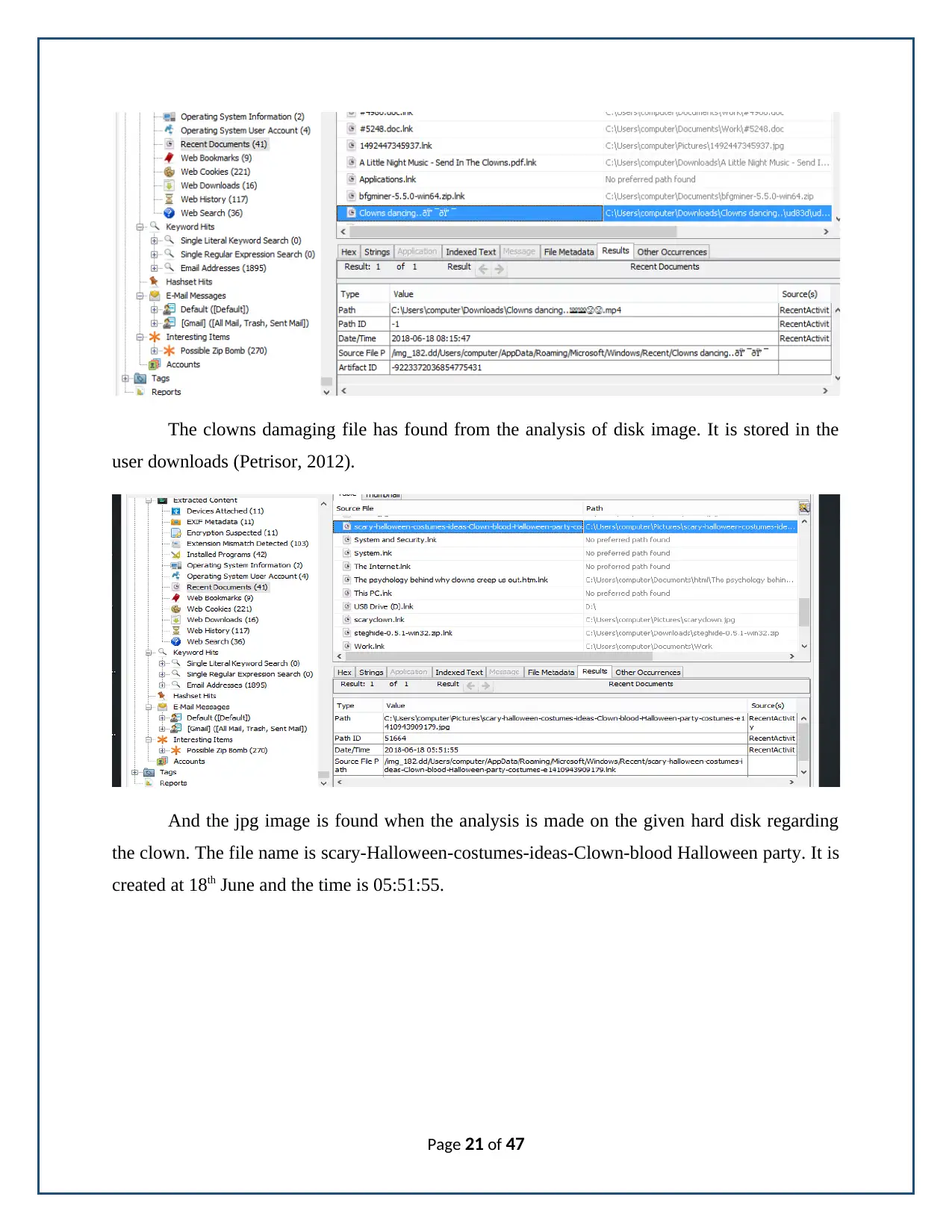
The clowns damaging file has found from the analysis of disk image. It is stored in the
user downloads (Petrisor, 2012).
And the jpg image is found when the analysis is made on the given hard disk regarding
the clown. The file name is scary-Halloween-costumes-ideas-Clown-blood Halloween party. It is
created at 18th June and the time is 05:51:55.
Page 21 of 47
user downloads (Petrisor, 2012).
And the jpg image is found when the analysis is made on the given hard disk regarding
the clown. The file name is scary-Halloween-costumes-ideas-Clown-blood Halloween party. It is
created at 18th June and the time is 05:51:55.
Page 21 of 47
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
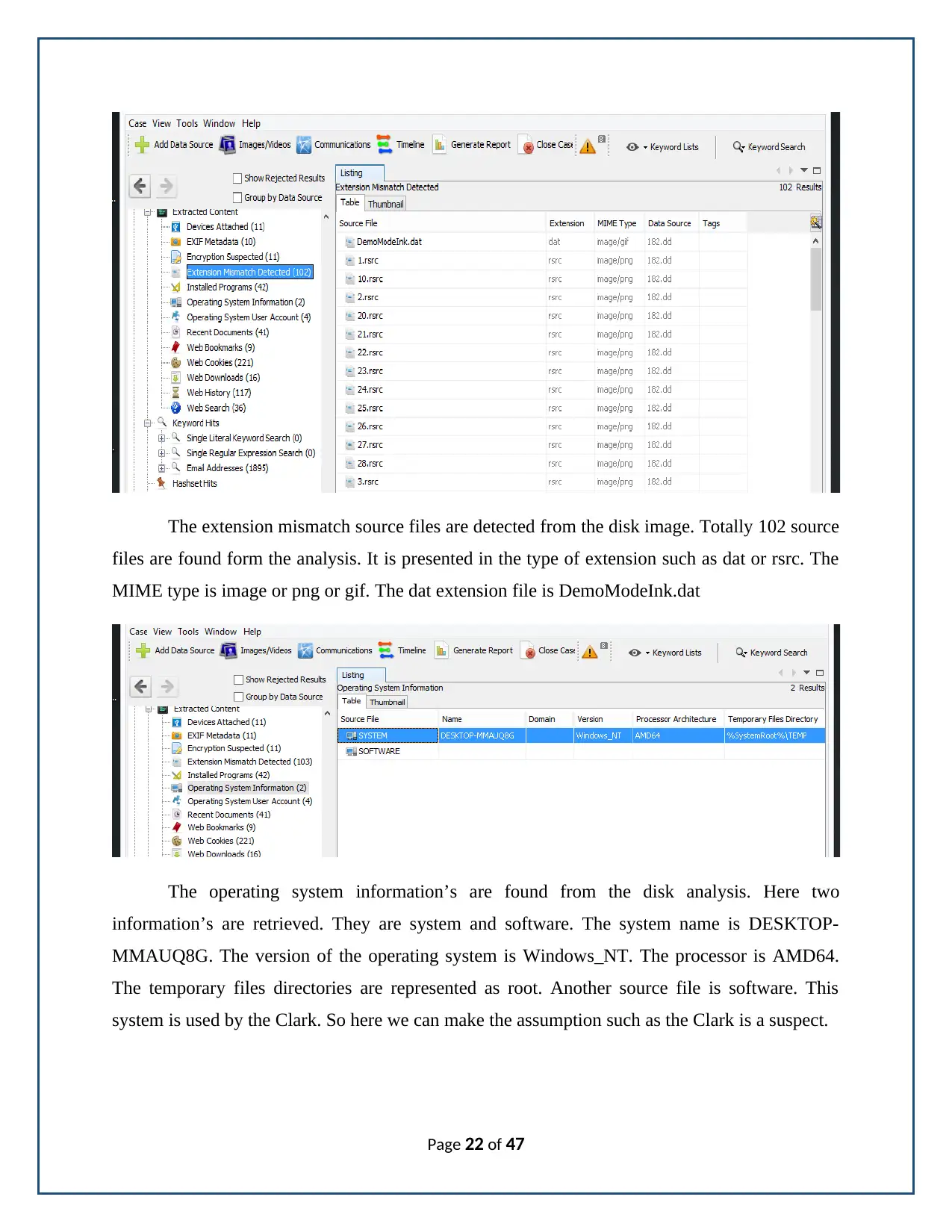
The extension mismatch source files are detected from the disk image. Totally 102 source
files are found form the analysis. It is presented in the type of extension such as dat or rsrc. The
MIME type is image or png or gif. The dat extension file is DemoModeInk.dat
The operating system information’s are found from the disk analysis. Here two
information’s are retrieved. They are system and software. The system name is DESKTOP-
MMAUQ8G. The version of the operating system is Windows_NT. The processor is AMD64.
The temporary files directories are represented as root. Another source file is software. This
system is used by the Clark. So here we can make the assumption such as the Clark is a suspect.
Page 22 of 47
files are found form the analysis. It is presented in the type of extension such as dat or rsrc. The
MIME type is image or png or gif. The dat extension file is DemoModeInk.dat
The operating system information’s are found from the disk analysis. Here two
information’s are retrieved. They are system and software. The system name is DESKTOP-
MMAUQ8G. The version of the operating system is Windows_NT. The processor is AMD64.
The temporary files directories are represented as root. Another source file is software. This
system is used by the Clark. So here we can make the assumption such as the Clark is a suspect.
Page 22 of 47
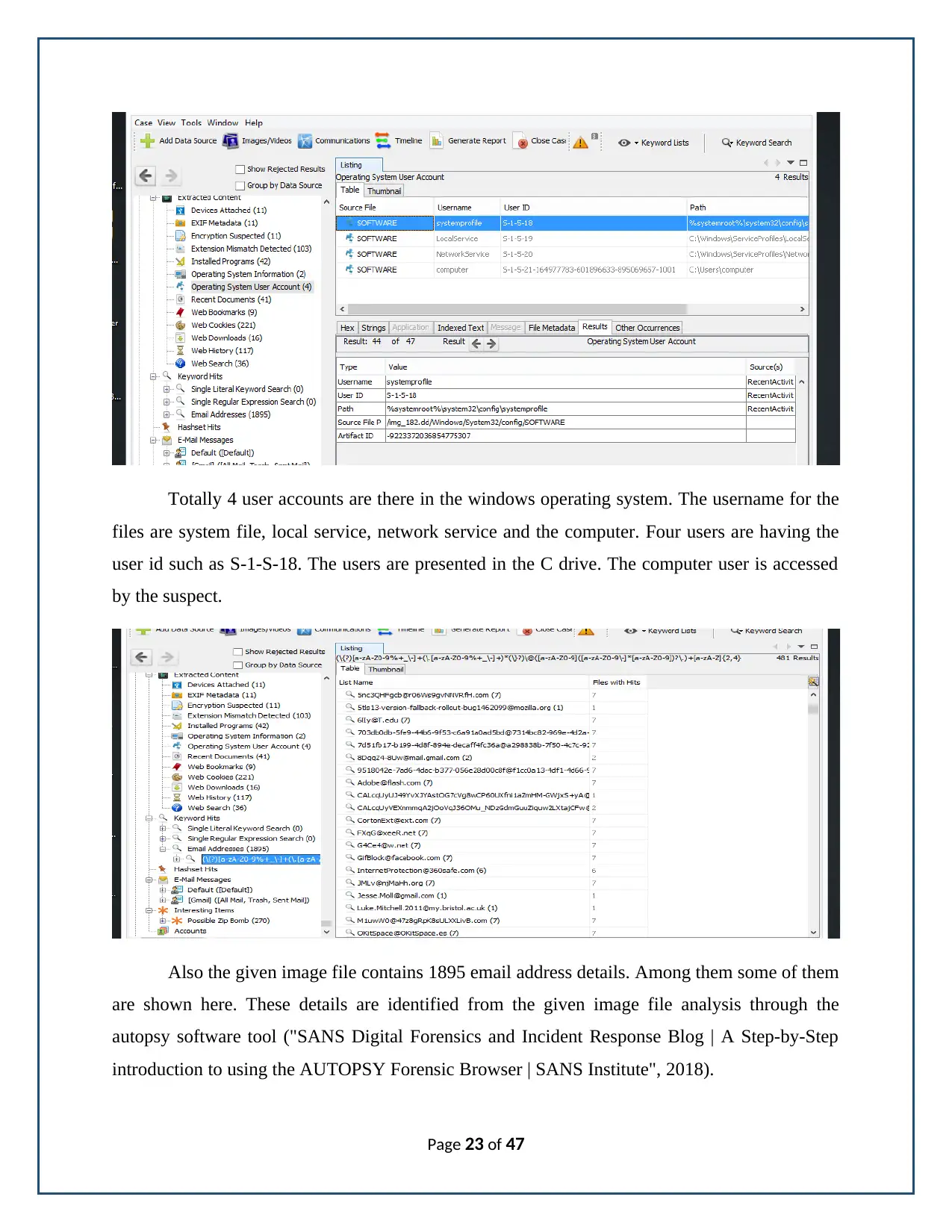
Totally 4 user accounts are there in the windows operating system. The username for the
files are system file, local service, network service and the computer. Four users are having the
user id such as S-1-S-18. The users are presented in the C drive. The computer user is accessed
by the suspect.
Also the given image file contains 1895 email address details. Among them some of them
are shown here. These details are identified from the given image file analysis through the
autopsy software tool ("SANS Digital Forensics and Incident Response Blog | A Step-by-Step
introduction to using the AUTOPSY Forensic Browser | SANS Institute", 2018).
Page 23 of 47
files are system file, local service, network service and the computer. Four users are having the
user id such as S-1-S-18. The users are presented in the C drive. The computer user is accessed
by the suspect.
Also the given image file contains 1895 email address details. Among them some of them
are shown here. These details are identified from the given image file analysis through the
autopsy software tool ("SANS Digital Forensics and Incident Response Blog | A Step-by-Step
introduction to using the AUTOPSY Forensic Browser | SANS Institute", 2018).
Page 23 of 47
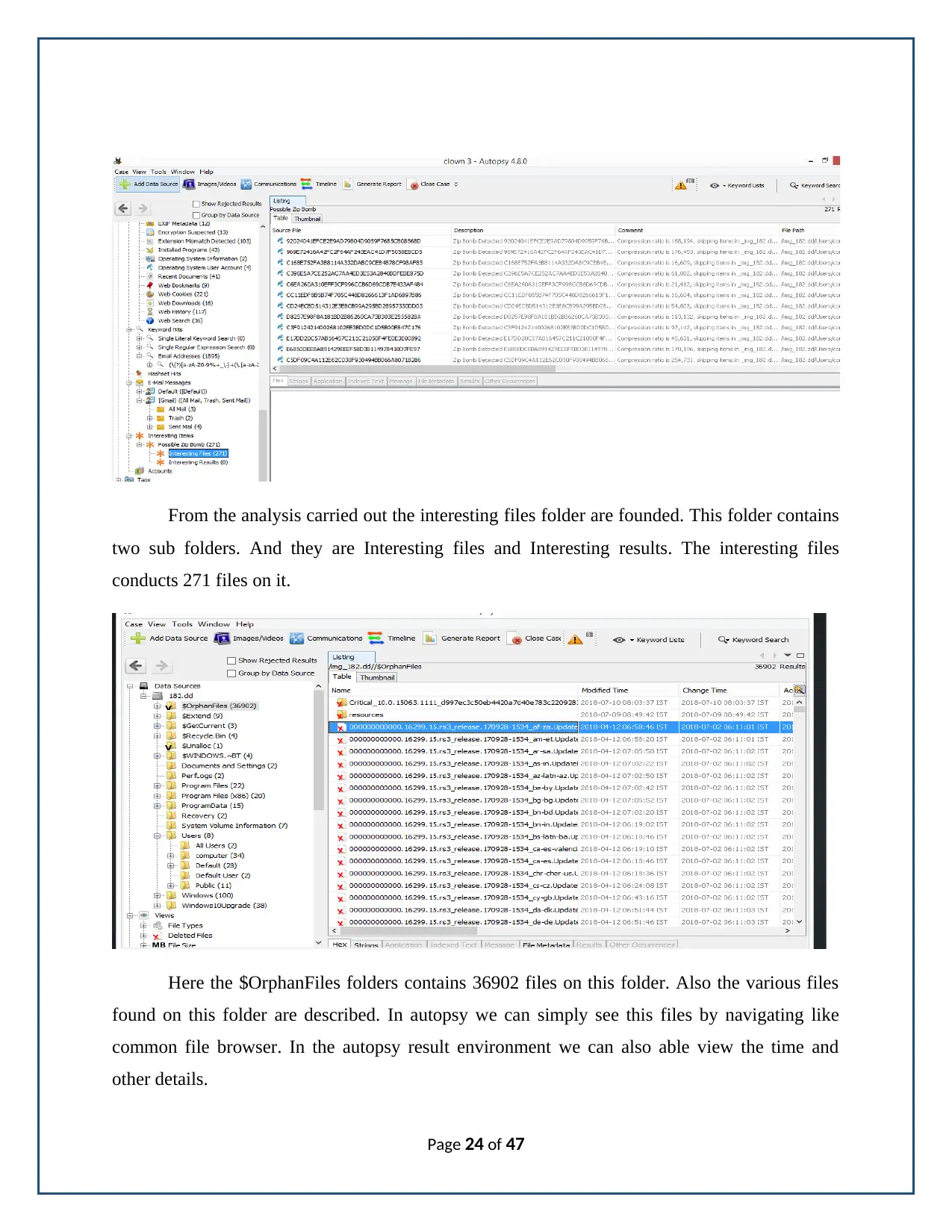
From the analysis carried out the interesting files folder are founded. This folder contains
two sub folders. And they are Interesting files and Interesting results. The interesting files
conducts 271 files on it.
Here the $OrphanFiles folders contains 36902 files on this folder. Also the various files
found on this folder are described. In autopsy we can simply see this files by navigating like
common file browser. In the autopsy result environment we can also able view the time and
other details.
Page 24 of 47
two sub folders. And they are Interesting files and Interesting results. The interesting files
conducts 271 files on it.
Here the $OrphanFiles folders contains 36902 files on this folder. Also the various files
found on this folder are described. In autopsy we can simply see this files by navigating like
common file browser. In the autopsy result environment we can also able view the time and
other details.
Page 24 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
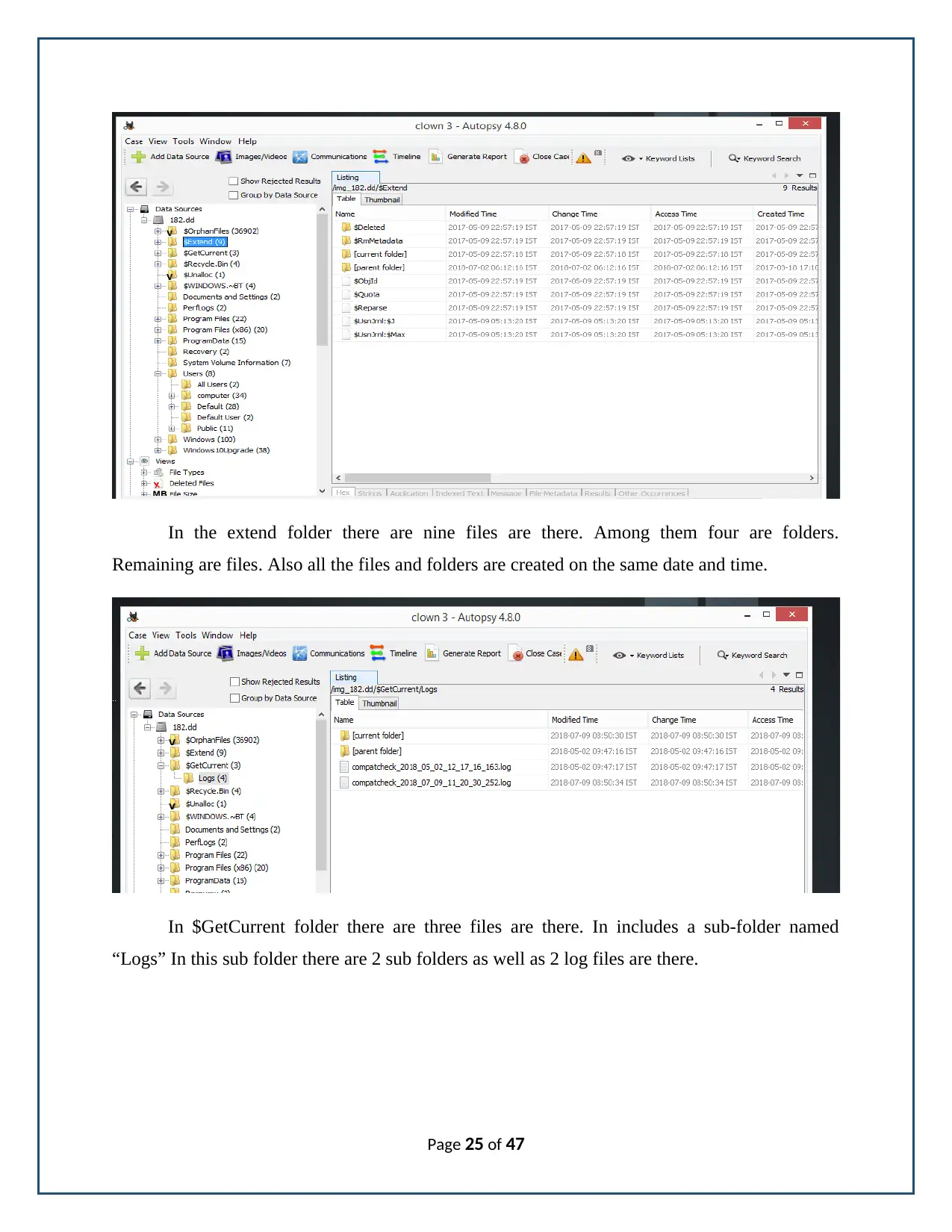
In the extend folder there are nine files are there. Among them four are folders.
Remaining are files. Also all the files and folders are created on the same date and time.
In $GetCurrent folder there are three files are there. In includes a sub-folder named
“Logs” In this sub folder there are 2 sub folders as well as 2 log files are there.
Page 25 of 47
Remaining are files. Also all the files and folders are created on the same date and time.
In $GetCurrent folder there are three files are there. In includes a sub-folder named
“Logs” In this sub folder there are 2 sub folders as well as 2 log files are there.
Page 25 of 47
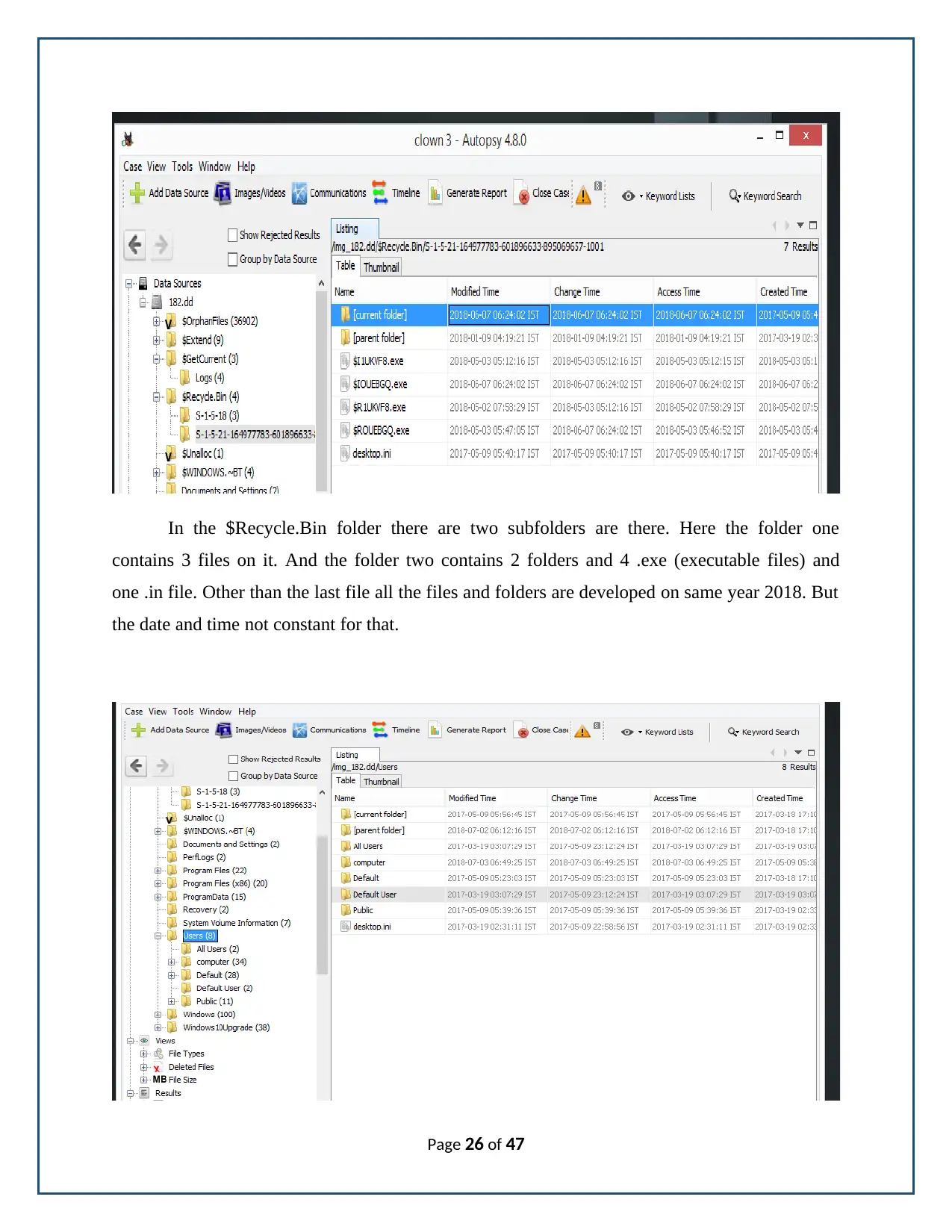
In the $Recycle.Bin folder there are two subfolders are there. Here the folder one
contains 3 files on it. And the folder two contains 2 folders and 4 .exe (executable files) and
one .in file. Other than the last file all the files and folders are developed on same year 2018. But
the date and time not constant for that.
Page 26 of 47
contains 3 files on it. And the folder two contains 2 folders and 4 .exe (executable files) and
one .in file. Other than the last file all the files and folders are developed on same year 2018. But
the date and time not constant for that.
Page 26 of 47
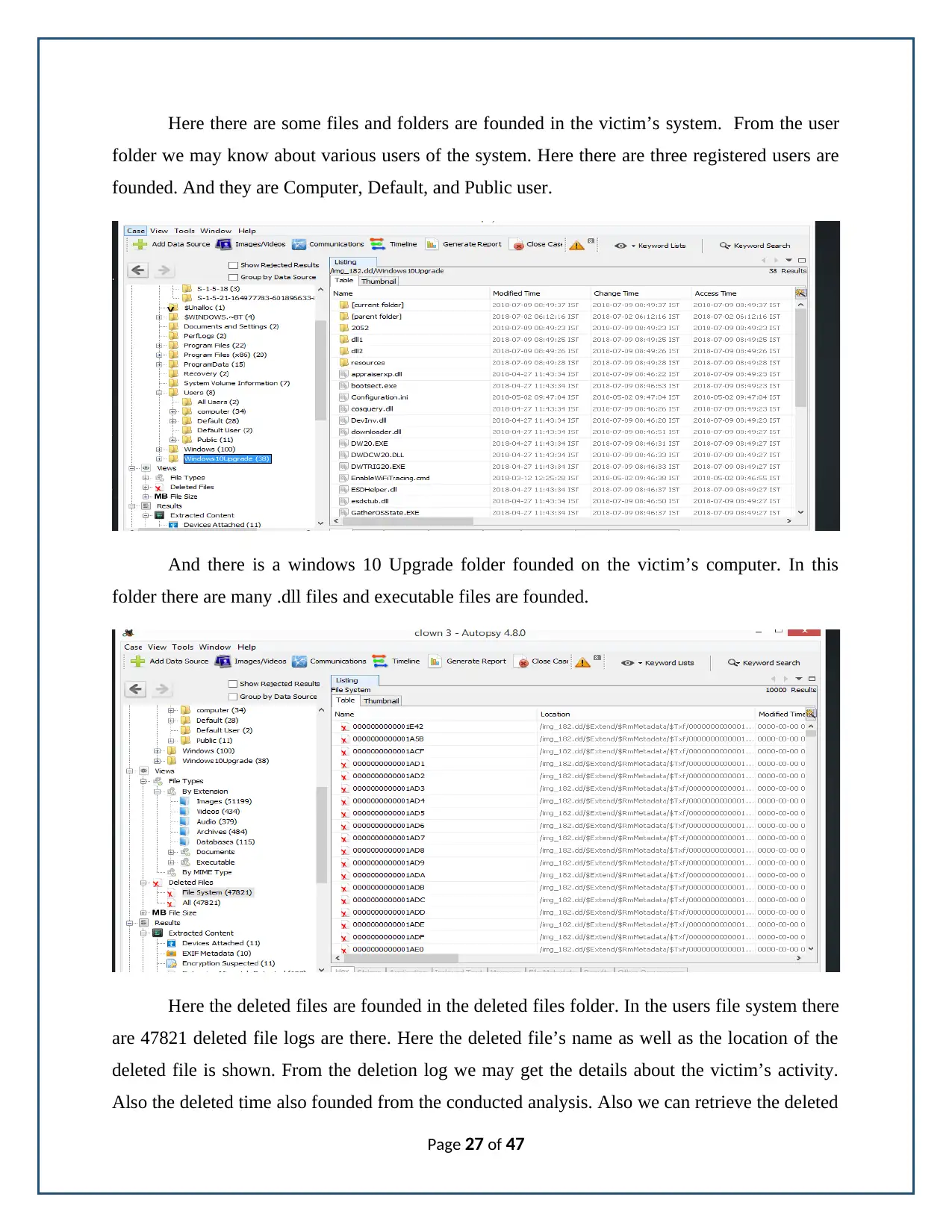
Here there are some files and folders are founded in the victim’s system. From the user
folder we may know about various users of the system. Here there are three registered users are
founded. And they are Computer, Default, and Public user.
And there is a windows 10 Upgrade folder founded on the victim’s computer. In this
folder there are many .dll files and executable files are founded.
Here the deleted files are founded in the deleted files folder. In the users file system there
are 47821 deleted file logs are there. Here the deleted file’s name as well as the location of the
deleted file is shown. From the deletion log we may get the details about the victim’s activity.
Also the deleted time also founded from the conducted analysis. Also we can retrieve the deleted
Page 27 of 47
folder we may know about various users of the system. Here there are three registered users are
founded. And they are Computer, Default, and Public user.
And there is a windows 10 Upgrade folder founded on the victim’s computer. In this
folder there are many .dll files and executable files are founded.
Here the deleted files are founded in the deleted files folder. In the users file system there
are 47821 deleted file logs are there. Here the deleted file’s name as well as the location of the
deleted file is shown. From the deletion log we may get the details about the victim’s activity.
Also the deleted time also founded from the conducted analysis. Also we can retrieve the deleted
Page 27 of 47
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
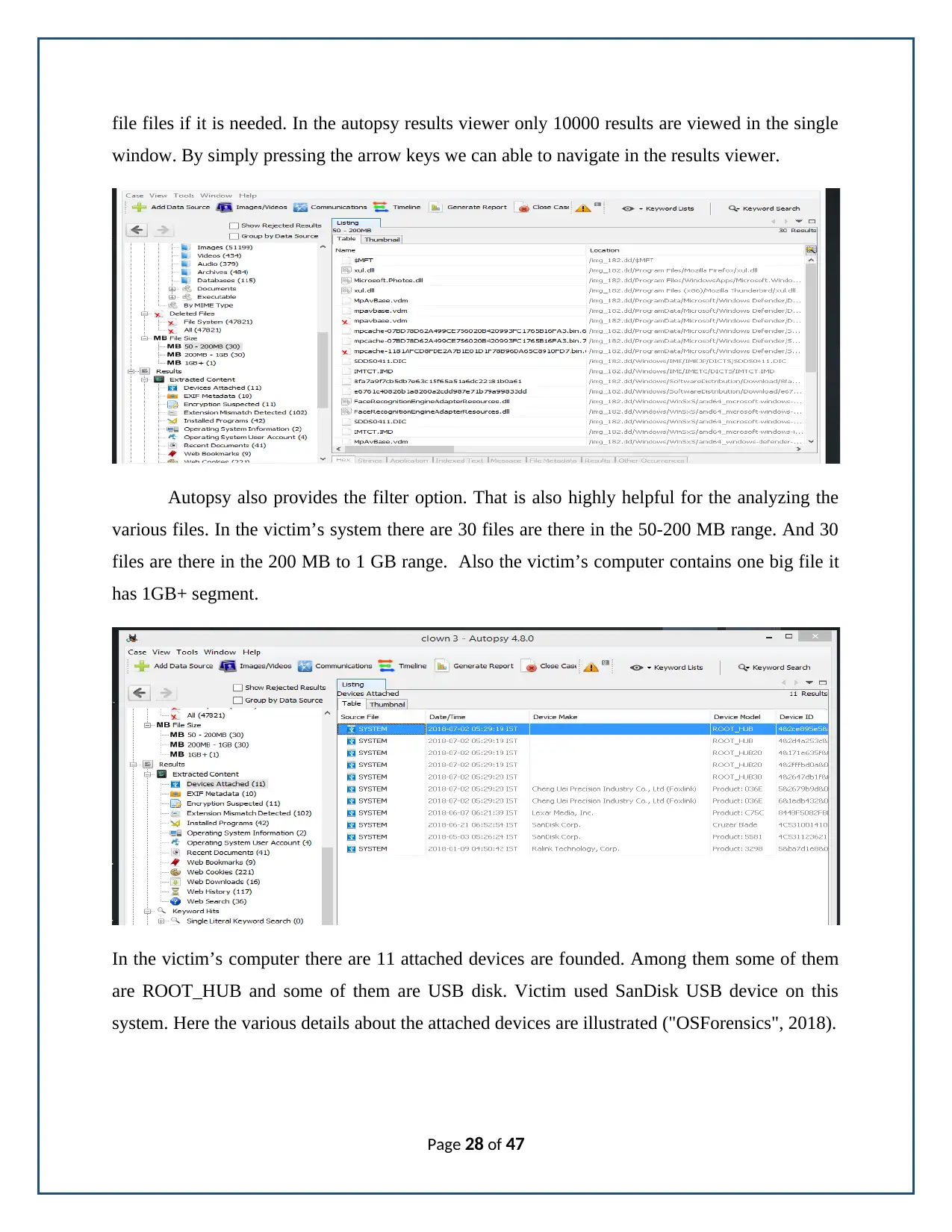
file files if it is needed. In the autopsy results viewer only 10000 results are viewed in the single
window. By simply pressing the arrow keys we can able to navigate in the results viewer.
Autopsy also provides the filter option. That is also highly helpful for the analyzing the
various files. In the victim’s system there are 30 files are there in the 50-200 MB range. And 30
files are there in the 200 MB to 1 GB range. Also the victim’s computer contains one big file it
has 1GB+ segment.
In the victim’s computer there are 11 attached devices are founded. Among them some of them
are ROOT_HUB and some of them are USB disk. Victim used SanDisk USB device on this
system. Here the various details about the attached devices are illustrated ("OSForensics", 2018).
Page 28 of 47
window. By simply pressing the arrow keys we can able to navigate in the results viewer.
Autopsy also provides the filter option. That is also highly helpful for the analyzing the
various files. In the victim’s system there are 30 files are there in the 50-200 MB range. And 30
files are there in the 200 MB to 1 GB range. Also the victim’s computer contains one big file it
has 1GB+ segment.
In the victim’s computer there are 11 attached devices are founded. Among them some of them
are ROOT_HUB and some of them are USB disk. Victim used SanDisk USB device on this
system. Here the various details about the attached devices are illustrated ("OSForensics", 2018).
Page 28 of 47
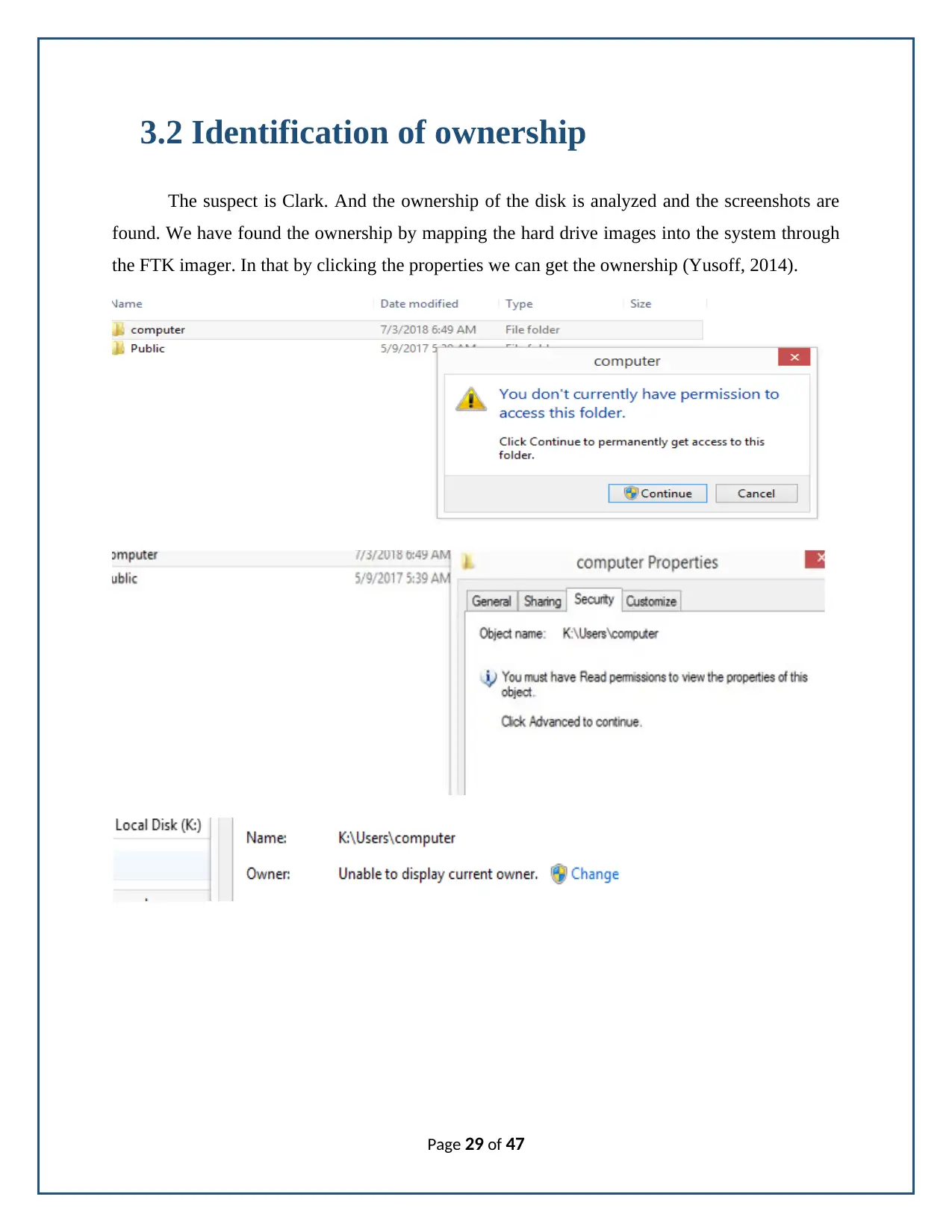
3.2 Identification of ownership
The suspect is Clark. And the ownership of the disk is analyzed and the screenshots are
found. We have found the ownership by mapping the hard drive images into the system through
the FTK imager. In that by clicking the properties we can get the ownership (Yusoff, 2014).
Page 29 of 47
The suspect is Clark. And the ownership of the disk is analyzed and the screenshots are
found. We have found the ownership by mapping the hard drive images into the system through
the FTK imager. In that by clicking the properties we can get the ownership (Yusoff, 2014).
Page 29 of 47
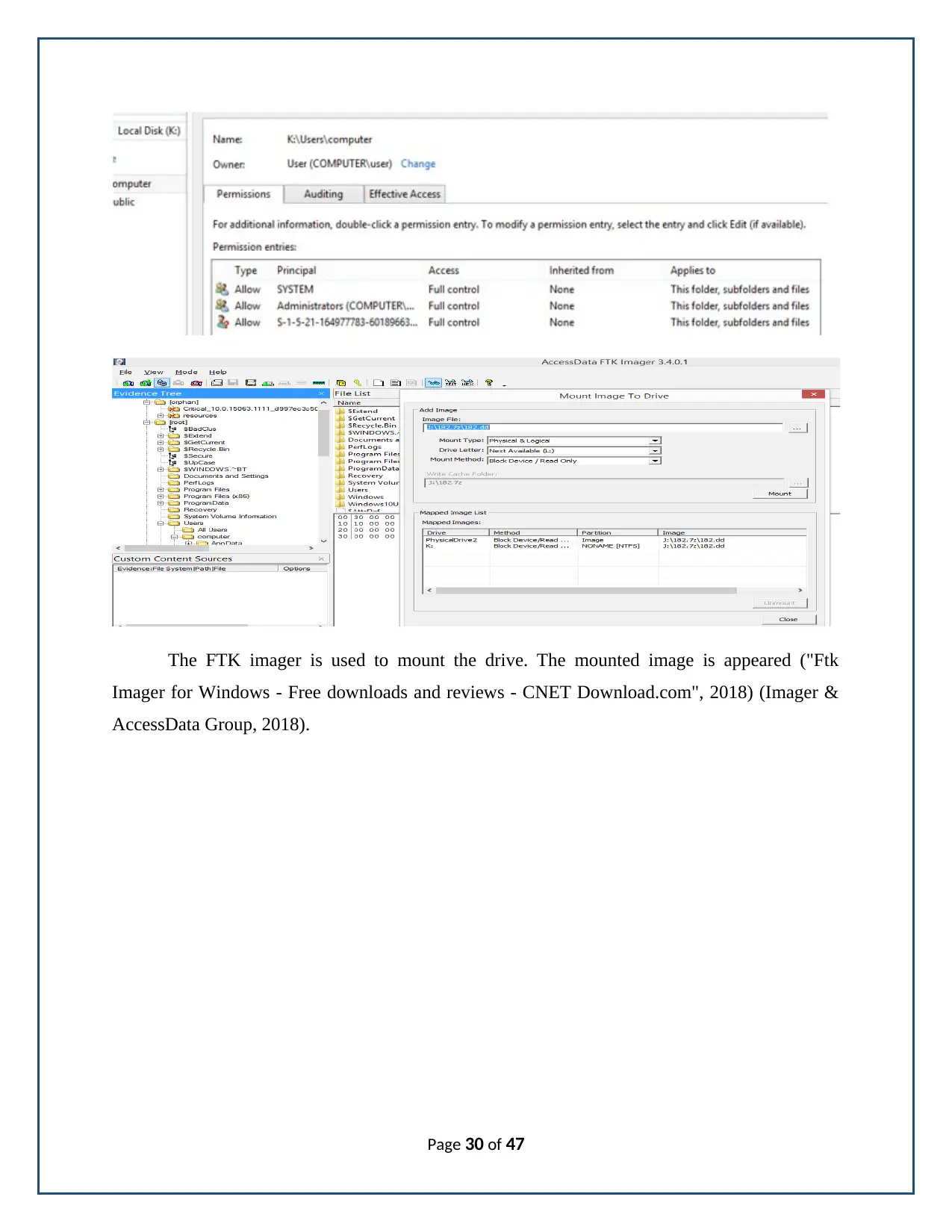
The FTK imager is used to mount the drive. The mounted image is appeared ("Ftk
Imager for Windows - Free downloads and reviews - CNET Download.com", 2018) (Imager &
AccessData Group, 2018).
Page 30 of 47
Imager for Windows - Free downloads and reviews - CNET Download.com", 2018) (Imager &
AccessData Group, 2018).
Page 30 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
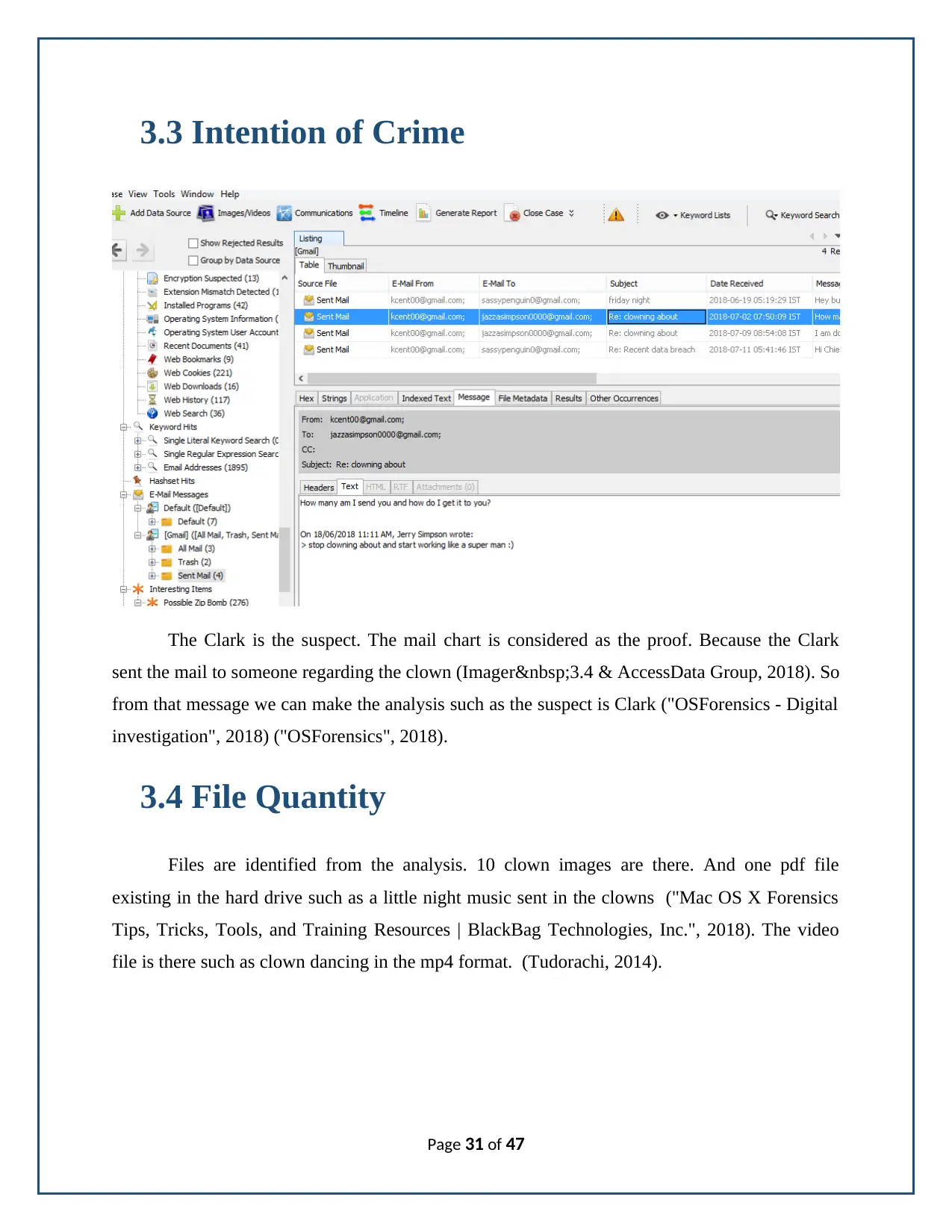
3.3 Intention of Crime
The Clark is the suspect. The mail chart is considered as the proof. Because the Clark
sent the mail to someone regarding the clown (Imager 3.4 & AccessData Group, 2018). So
from that message we can make the analysis such as the suspect is Clark ("OSForensics - Digital
investigation", 2018) ("OSForensics", 2018).
3.4 File Quantity
Files are identified from the analysis. 10 clown images are there. And one pdf file
existing in the hard drive such as a little night music sent in the clowns ("Mac OS X Forensics
Tips, Tricks, Tools, and Training Resources | BlackBag Technologies, Inc.", 2018). The video
file is there such as clown dancing in the mp4 format. (Tudorachi, 2014).
Page 31 of 47
The Clark is the suspect. The mail chart is considered as the proof. Because the Clark
sent the mail to someone regarding the clown (Imager 3.4 & AccessData Group, 2018). So
from that message we can make the analysis such as the suspect is Clark ("OSForensics - Digital
investigation", 2018) ("OSForensics", 2018).
3.4 File Quantity
Files are identified from the analysis. 10 clown images are there. And one pdf file
existing in the hard drive such as a little night music sent in the clowns ("Mac OS X Forensics
Tips, Tricks, Tools, and Training Resources | BlackBag Technologies, Inc.", 2018). The video
file is there such as clown dancing in the mp4 format. (Tudorachi, 2014).
Page 31 of 47
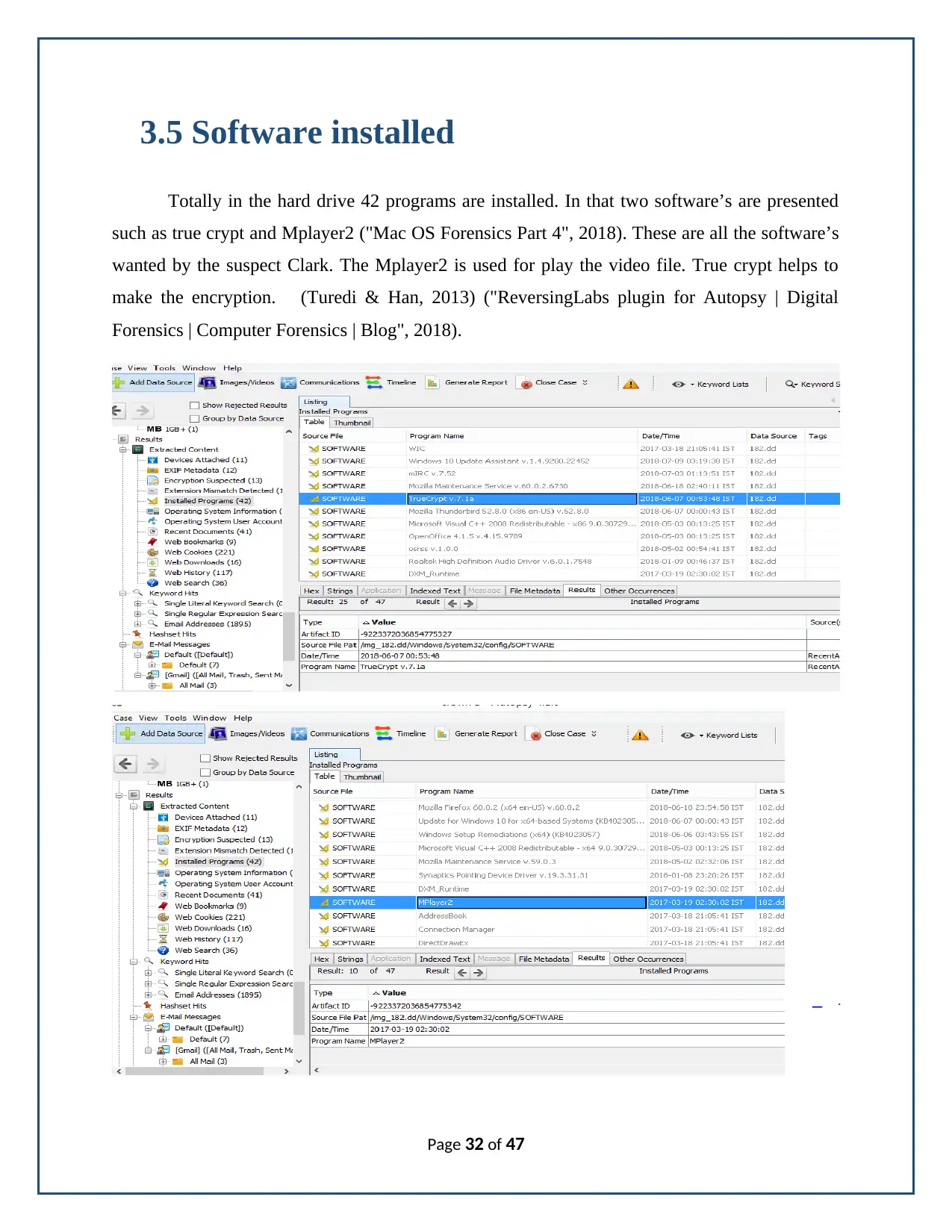
3.5 Software installed
Totally in the hard drive 42 programs are installed. In that two software’s are presented
such as true crypt and Mplayer2 ("Mac OS Forensics Part 4", 2018). These are all the software’s
wanted by the suspect Clark. The Mplayer2 is used for play the video file. True crypt helps to
make the encryption. (Turedi & Han, 2013) ("ReversingLabs plugin for Autopsy | Digital
Forensics | Computer Forensics | Blog", 2018).
Page 32 of 47
Totally in the hard drive 42 programs are installed. In that two software’s are presented
such as true crypt and Mplayer2 ("Mac OS Forensics Part 4", 2018). These are all the software’s
wanted by the suspect Clark. The Mplayer2 is used for play the video file. True crypt helps to
make the encryption. (Turedi & Han, 2013) ("ReversingLabs plugin for Autopsy | Digital
Forensics | Computer Forensics | Blog", 2018).
Page 32 of 47
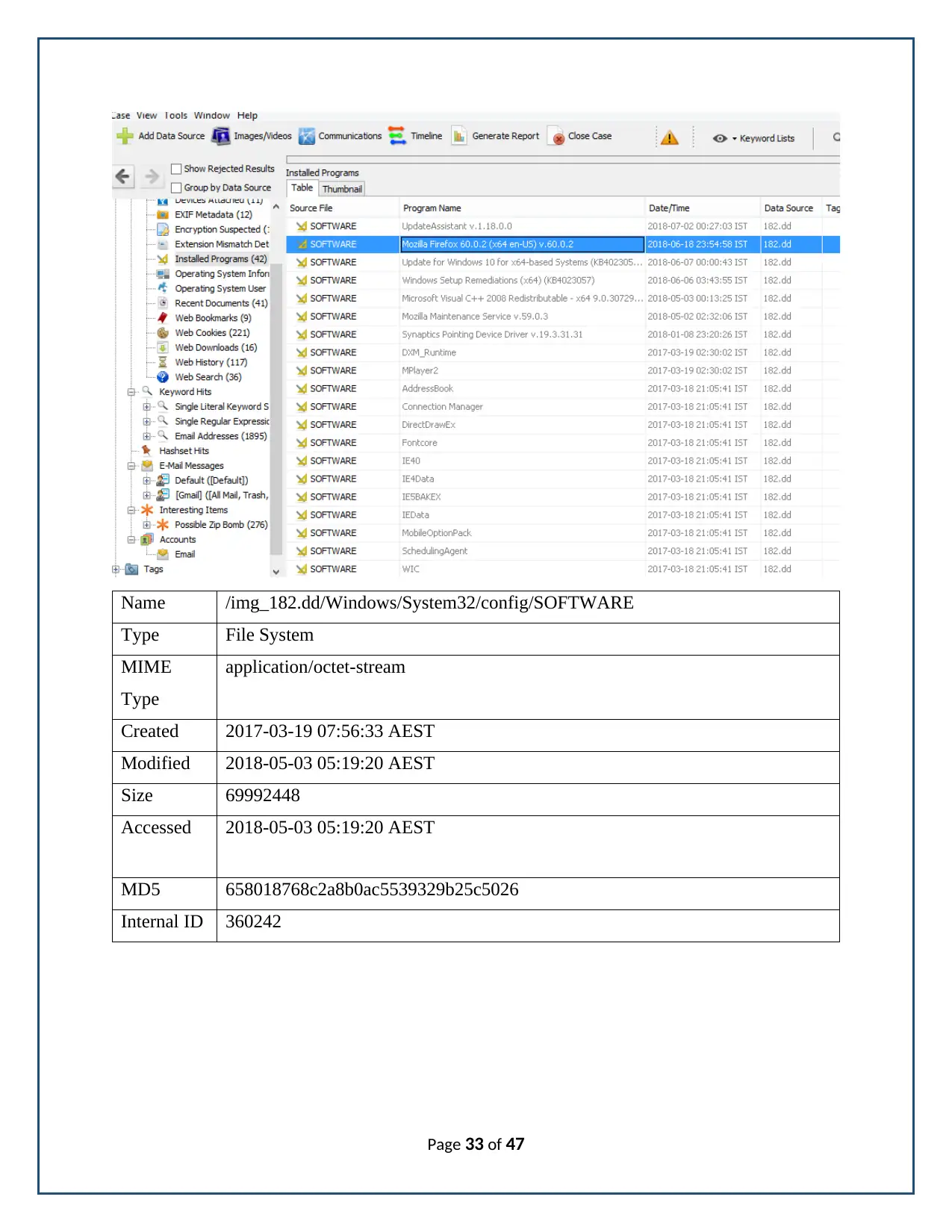
Name /img_182.dd/Windows/System32/config/SOFTWARE
Type File System
MIME
Type
application/octet-stream
Created 2017-03-19 07:56:33 AEST
Modified 2018-05-03 05:19:20 AEST
Size 69992448
Accessed 2018-05-03 05:19:20 AEST
MD5 658018768c2a8b0ac5539329b25c5026
Internal ID 360242
Page 33 of 47
Type File System
MIME
Type
application/octet-stream
Created 2017-03-19 07:56:33 AEST
Modified 2018-05-03 05:19:20 AEST
Size 69992448
Accessed 2018-05-03 05:19:20 AEST
MD5 658018768c2a8b0ac5539329b25c5026
Internal ID 360242
Page 33 of 47
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4.Conclusion
The offence of accessing or owning clown content is investigated. In the investigation,
the crime committed is analyzed ("Minnesota detectives crack the case with digital forensics",
2018). The computer related to the investigation is seized which belongs to Clark is investigated.
The forensic image of the hard drive is obtained. In the forensic image, the clown related
contents is searched with the help of forensic tools (James, 2018). The intention of the offence,
owner identification are done. And also the file quantity in the given forensic image is found.
The Clark is identified as a suspect. Because the mail chat and web bookmarks are presented
regarding the clown content. The installed software’s are analyzed. The web histories are found.
The images, pdf files and videos are discovered regarding the clown content.
Page 34 of 47
The offence of accessing or owning clown content is investigated. In the investigation,
the crime committed is analyzed ("Minnesota detectives crack the case with digital forensics",
2018). The computer related to the investigation is seized which belongs to Clark is investigated.
The forensic image of the hard drive is obtained. In the forensic image, the clown related
contents is searched with the help of forensic tools (James, 2018). The intention of the offence,
owner identification are done. And also the file quantity in the given forensic image is found.
The Clark is identified as a suspect. Because the mail chat and web bookmarks are presented
regarding the clown content. The installed software’s are analyzed. The web histories are found.
The images, pdf files and videos are discovered regarding the clown content.
Page 34 of 47

5.References
Bell, M. (2018). OS Forensics. Retrieved from https://lcdiblog.champlain.edu/2013/03/14/os-
forensics/
Firefox OS Forensics: Guidelines and Challenges. (2016). International Journal Of Science And
Research (IJSR), 5(6), 290-293. doi: 10.21275/v5i6.nov164047
FTK Imager and Custom Content Images. (2018). Retrieved from
https://salt4n6.com/2018/05/28/ftk-imager-custom-content-images/
Ftk Imager for Windows - Free downloads and reviews - CNET Download.com. (2018).
Retrieved from https://download.cnet.com/s/ftk-imager/windows/
FTK Imager: Lesson 1: Install FTK Imager. (2018). Retrieved from
https://www.computersecuritystudent.com/FORENSICS/FTK/IMAGER/FTK_IMG_313/
lesson1/index.html
FTK Imager: Lesson 4: Mount Image File, Recover Deleted File. (2018). Retrieved from
https://www.computersecuritystudent.com/FORENSICS/FTK/IMAGER/FTK_IMG_313/
lesson4/index.html
Hacking & Digital Forensics & Autopsy - Stay lunix. (2018). Retrieved from
https://www.youtube.com/channel/UCJLE73CGMx1PIu0gTHo9hOw
Imager 3.4, A., & AccessData Group, L. (2018). AccessData FTK Imager. Get the
software safe and easy. Retrieved from https://accessdata-ftk-imager.software.informer.com/
Imager, A., & AccessData Group, L. (2018). AccessData FTK Imager 3.2 Download (Free) -
FTK Imager.exe. Retrieved from https://accessdata-ftk-imager.software.informer.com/3.2/
Imager, A., & AccessData Group, L. (2018). AccessData FTK Imager (free) download Windows
version. Retrieved from https://en.freedownloadmanager.org/Windows-PC/AccessData-
FTK-Imager-FREE.html
Page 35 of 47
Bell, M. (2018). OS Forensics. Retrieved from https://lcdiblog.champlain.edu/2013/03/14/os-
forensics/
Firefox OS Forensics: Guidelines and Challenges. (2016). International Journal Of Science And
Research (IJSR), 5(6), 290-293. doi: 10.21275/v5i6.nov164047
FTK Imager and Custom Content Images. (2018). Retrieved from
https://salt4n6.com/2018/05/28/ftk-imager-custom-content-images/
Ftk Imager for Windows - Free downloads and reviews - CNET Download.com. (2018).
Retrieved from https://download.cnet.com/s/ftk-imager/windows/
FTK Imager: Lesson 1: Install FTK Imager. (2018). Retrieved from
https://www.computersecuritystudent.com/FORENSICS/FTK/IMAGER/FTK_IMG_313/
lesson1/index.html
FTK Imager: Lesson 4: Mount Image File, Recover Deleted File. (2018). Retrieved from
https://www.computersecuritystudent.com/FORENSICS/FTK/IMAGER/FTK_IMG_313/
lesson4/index.html
Hacking & Digital Forensics & Autopsy - Stay lunix. (2018). Retrieved from
https://www.youtube.com/channel/UCJLE73CGMx1PIu0gTHo9hOw
Imager 3.4, A., & AccessData Group, L. (2018). AccessData FTK Imager. Get the
software safe and easy. Retrieved from https://accessdata-ftk-imager.software.informer.com/
Imager, A., & AccessData Group, L. (2018). AccessData FTK Imager 3.2 Download (Free) -
FTK Imager.exe. Retrieved from https://accessdata-ftk-imager.software.informer.com/3.2/
Imager, A., & AccessData Group, L. (2018). AccessData FTK Imager (free) download Windows
version. Retrieved from https://en.freedownloadmanager.org/Windows-PC/AccessData-
FTK-Imager-FREE.html
Page 35 of 47

James, J. (2018). [How To] Introduction to Autopsy for Digital Forensics. Retrieved from
https://dfir.science/2017/02/how-to-introduction-to-autopsy-for-digital-forensics.html
Joyce, R., Powers, J., & Adelstein, F. (2008). MEGA: A tool for Mac OS X operating system
and application forensics. Digital Investigation, 5, S83-S90. doi: 10.1016/j.diin.2008.05.011
Larson, S. (2014). The Basics of Digital Forensics: The Primer for Getting Started in Digital
Forensics. Journal Of Digital Forensics, Security And Law. doi: 10.15394/jdfsl.2014.1165
Mac OS Forensics Part 4. (2018). Retrieved from
https://lcdiblog.champlain.edu/2015/04/02/mac-os-forensics/
Mac OS X Forensics Tips, Tricks, Tools, and Training Resources | BlackBag Technologies, Inc.
(2018). Retrieved from https://www.blackbagtech.com/resources/mac-forensics.html
Machemer, S., & Wang, Z. (2007). Environmental Forensics at Pacifichem 2005. Environmental
Forensics, 8(1-2), 75-76. doi: 10.1080/15275920601180594
mannaza, r. (2018). Retrieved from
https://www.dhs.gov/sites/default/files/publications/1491_508_Test%20Report_NIST_Disk
%20Imaging_FTK%20Imager%20v3.4.2.6_October_14_2016.pdf
Minnesota detectives crack the case with digital forensics. (2018). Retrieved from
http://www.startribune.com/when-teens-went-missing-digital-forensics-cracked-case/
278132541/
Morrison, R. (2001). Environmental Forensics: an International Forum. Environmental
Forensics, 2(4), 261. doi: 10.1006/enfo.2001.0067
Morrison, R., & Petrisor, L. (2004). Promoting Environmental Forensics Through ISEF
Workshops. Environmental Forensics, 5(1), 1-2. doi: 10.1080/15275920490426248
Morrison, R., & Petrisor, L. (2004). Promoting Environmental Forensics Through ISEF
Workshops. Environmental Forensics, 5(1), 1-2. doi: 10.1080/15275920490426248
Mudge, S. (2007). Multivariate Statistical Methods in Environmental Forensics. Environmental
Forensics, 8(1-2), 155-163. doi: 10.1080/15275920601180693
Page 36 of 47
https://dfir.science/2017/02/how-to-introduction-to-autopsy-for-digital-forensics.html
Joyce, R., Powers, J., & Adelstein, F. (2008). MEGA: A tool for Mac OS X operating system
and application forensics. Digital Investigation, 5, S83-S90. doi: 10.1016/j.diin.2008.05.011
Larson, S. (2014). The Basics of Digital Forensics: The Primer for Getting Started in Digital
Forensics. Journal Of Digital Forensics, Security And Law. doi: 10.15394/jdfsl.2014.1165
Mac OS Forensics Part 4. (2018). Retrieved from
https://lcdiblog.champlain.edu/2015/04/02/mac-os-forensics/
Mac OS X Forensics Tips, Tricks, Tools, and Training Resources | BlackBag Technologies, Inc.
(2018). Retrieved from https://www.blackbagtech.com/resources/mac-forensics.html
Machemer, S., & Wang, Z. (2007). Environmental Forensics at Pacifichem 2005. Environmental
Forensics, 8(1-2), 75-76. doi: 10.1080/15275920601180594
mannaza, r. (2018). Retrieved from
https://www.dhs.gov/sites/default/files/publications/1491_508_Test%20Report_NIST_Disk
%20Imaging_FTK%20Imager%20v3.4.2.6_October_14_2016.pdf
Minnesota detectives crack the case with digital forensics. (2018). Retrieved from
http://www.startribune.com/when-teens-went-missing-digital-forensics-cracked-case/
278132541/
Morrison, R. (2001). Environmental Forensics: an International Forum. Environmental
Forensics, 2(4), 261. doi: 10.1006/enfo.2001.0067
Morrison, R., & Petrisor, L. (2004). Promoting Environmental Forensics Through ISEF
Workshops. Environmental Forensics, 5(1), 1-2. doi: 10.1080/15275920490426248
Morrison, R., & Petrisor, L. (2004). Promoting Environmental Forensics Through ISEF
Workshops. Environmental Forensics, 5(1), 1-2. doi: 10.1080/15275920490426248
Mudge, S. (2007). Multivariate Statistical Methods in Environmental Forensics. Environmental
Forensics, 8(1-2), 155-163. doi: 10.1080/15275920601180693
Page 36 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ochiai, H., Yamakawa, Y., Fukushima, T., Yamada, H., & Hayashi, T. (2000). Primary
leiomyosarcoma of the cervical spine causing spontaneous compression fracture: Report of
an autospy case. Neuropathology, 20(1), 60-64. doi: 10.1046/j.1440-1789.2000.00279.x
Operating System Forensics | National Initiative for Cybersecurity Careers and Studies. (2018).
Retrieved from https://niccs.us-cert.gov/training/search/champlain-college-online/operating-
system-forensics
OSForensics - Digital investigation for a new era by PassMark Software®. (2018). Retrieved
from https://www.osforensics.com/
OSForensics - Digital investigation. (2018). Retrieved from
https://www.tritechforensics.com/osforensics
OSForensics - Extract forensic data from computers. (2018). Retrieved from
http://www.snapfiles.com/get/osforensics.html
Pattnaik, P., & Jana, A. (2005). Microbial Forensics: Applications in
Bioterrorism. Environmental Forensics, 6(2), 197-204. doi: 10.1080/15275920590952874
Petrisor, I. (2005). Sampling and Analyses—Key Steps of a Forensics
Investigation. Environmental Forensics, 6(1), 1-1. doi: 10.1080/15275920590913796
Petrisor, I. (2007). Background in Environmental Forensics: “Raising the
Awareness”?. Environmental Forensics, 8(3), 195-198. doi: 10.1080/15275920701505989
Petrisor, I. (2012). Emerging Environmental Forensics Applications and Case Studies: Review of
Environmental Forensics—Proceedings of the 2011 INEF Conference. Environmental
Forensics, 13(4), 285-288. doi: 10.1080/15275922.2012.738954
ReversingLabs plugin for Autopsy | Digital Forensics | Computer Forensics | Blog. (2018).
Retrieved from https://www.digitalforensics.com/blog/reversinglabs-plugin-for-autopsy/
Rhee, J., Riley, R., Lin, Z., Jiang, X., & Xu, D. (2014). Data-Centric OS Kernel Malware
Characterization. IEEE Transactions On Information Forensics And Security, 9(1), 72-87.
doi: 10.1109/tifs.2013.2291964
Page 37 of 47
leiomyosarcoma of the cervical spine causing spontaneous compression fracture: Report of
an autospy case. Neuropathology, 20(1), 60-64. doi: 10.1046/j.1440-1789.2000.00279.x
Operating System Forensics | National Initiative for Cybersecurity Careers and Studies. (2018).
Retrieved from https://niccs.us-cert.gov/training/search/champlain-college-online/operating-
system-forensics
OSForensics - Digital investigation for a new era by PassMark Software®. (2018). Retrieved
from https://www.osforensics.com/
OSForensics - Digital investigation. (2018). Retrieved from
https://www.tritechforensics.com/osforensics
OSForensics - Extract forensic data from computers. (2018). Retrieved from
http://www.snapfiles.com/get/osforensics.html
Pattnaik, P., & Jana, A. (2005). Microbial Forensics: Applications in
Bioterrorism. Environmental Forensics, 6(2), 197-204. doi: 10.1080/15275920590952874
Petrisor, I. (2005). Sampling and Analyses—Key Steps of a Forensics
Investigation. Environmental Forensics, 6(1), 1-1. doi: 10.1080/15275920590913796
Petrisor, I. (2007). Background in Environmental Forensics: “Raising the
Awareness”?. Environmental Forensics, 8(3), 195-198. doi: 10.1080/15275920701505989
Petrisor, I. (2012). Emerging Environmental Forensics Applications and Case Studies: Review of
Environmental Forensics—Proceedings of the 2011 INEF Conference. Environmental
Forensics, 13(4), 285-288. doi: 10.1080/15275922.2012.738954
ReversingLabs plugin for Autopsy | Digital Forensics | Computer Forensics | Blog. (2018).
Retrieved from https://www.digitalforensics.com/blog/reversinglabs-plugin-for-autopsy/
Rhee, J., Riley, R., Lin, Z., Jiang, X., & Xu, D. (2014). Data-Centric OS Kernel Malware
Characterization. IEEE Transactions On Information Forensics And Security, 9(1), 72-87.
doi: 10.1109/tifs.2013.2291964
Page 37 of 47

SANS Digital Forensics and Incident Response Blog | A Step-by-Step introduction to using the
AUTOPSY Forensic Browser | SANS Institute. (2018). Retrieved from https://digital-
forensics.sans.org/blog/2009/05/11/a-step-by-step-introduction-to-using-the-autopsy-
forensic-browser
Snapshot: S&T is Enhancing the Autopsy Digital Forensics Tool. (2018). Retrieved from
https://www.dhs.gov/science-and-technology/news/2017/12/12/snapshot-st-enhancing-
autopsy-digital-forensics-tool
Starting a New Digital Forensic Investiation Case in Autopsy 4. (2018). Retrieved from
https://www.youtube.com/watch?v=WB4xj8VYotk
Tabona, A. (2018). Top 20 Free Digital Forensic Investigation Tools for SysAdmins. Retrieved
from https://techtalk.gfi.com/top-20-free-digital-forensic-investigation-tools-for-sysadmins/
The Evolution of Environmental Forensics in the United States. (2001). Environmental
Forensics, 2(3), 177-177. doi: 10.1006/enfo.2001.0056
The International Society of Environmental Forensics Announces the Following Workshops for
2002. (2002). Environmental Forensics, 3(2), 1-1. doi: 10.1080/713848349
Tudorachi, L. (2014). Linking Chemistry to Law in Environmental Forensics. Environmental
Forensics, 15(3), 213-218. doi: 10.1080/15275922.2014.930938
Turedi, Z., & Han, L. (2013). Automatic forensic log file analysis for Mac OS X
systems. International Journal Of Electronic Security And Digital Forensics, 5(2), 124. doi:
10.1504/ijesdf.2013.055050
Yusoff, M. (2014). Advances of Mobile Forensic Procedures in Firefox OS. International
Journal Of Cyber-Security And Digital Forensics, 3(4), 183-199. doi: 10.17781/p001338
Yusoff, M. (2014). Performance Measurement for Mobile Forensic Data Acquisition in Firefox
OS. International Journal Of Cyber-Security And Digital Forensics, 3(3), 130-140. doi:
10.17781/p001333
Page 38 of 47
AUTOPSY Forensic Browser | SANS Institute. (2018). Retrieved from https://digital-
forensics.sans.org/blog/2009/05/11/a-step-by-step-introduction-to-using-the-autopsy-
forensic-browser
Snapshot: S&T is Enhancing the Autopsy Digital Forensics Tool. (2018). Retrieved from
https://www.dhs.gov/science-and-technology/news/2017/12/12/snapshot-st-enhancing-
autopsy-digital-forensics-tool
Starting a New Digital Forensic Investiation Case in Autopsy 4. (2018). Retrieved from
https://www.youtube.com/watch?v=WB4xj8VYotk
Tabona, A. (2018). Top 20 Free Digital Forensic Investigation Tools for SysAdmins. Retrieved
from https://techtalk.gfi.com/top-20-free-digital-forensic-investigation-tools-for-sysadmins/
The Evolution of Environmental Forensics in the United States. (2001). Environmental
Forensics, 2(3), 177-177. doi: 10.1006/enfo.2001.0056
The International Society of Environmental Forensics Announces the Following Workshops for
2002. (2002). Environmental Forensics, 3(2), 1-1. doi: 10.1080/713848349
Tudorachi, L. (2014). Linking Chemistry to Law in Environmental Forensics. Environmental
Forensics, 15(3), 213-218. doi: 10.1080/15275922.2014.930938
Turedi, Z., & Han, L. (2013). Automatic forensic log file analysis for Mac OS X
systems. International Journal Of Electronic Security And Digital Forensics, 5(2), 124. doi:
10.1504/ijesdf.2013.055050
Yusoff, M. (2014). Advances of Mobile Forensic Procedures in Firefox OS. International
Journal Of Cyber-Security And Digital Forensics, 3(4), 183-199. doi: 10.17781/p001338
Yusoff, M. (2014). Performance Measurement for Mobile Forensic Data Acquisition in Firefox
OS. International Journal Of Cyber-Security And Digital Forensics, 3(3), 130-140. doi:
10.17781/p001333
Page 38 of 47
Zhao, H., Zong, W., & Wu, G. (2014). Configuration Model Research Based on Product Family
Configuration Unit. Applied Mechanics And Materials, 635-637, 1981-1984. doi:
10.4028/www.scientific.net/amm.635-637.1981
Appendix I –Running Sheet
Date/Time Events Duration
11/10/2018 – 6:05 pm 182.dd hard disk image file
thoroughly examined by using
the appropriate digital forensics
examination tools. (Autopsy
Examination)
OUTCOME:
Laptop hard disk Image file
extracted into the autopsy
examination environment.
50 minutes
11/10/2018 – 6:55 pm Searching for the multimedia
file in the Clarks hard disk.
OUTCOME:
“kikki_down_party_pose.jpg”
image file founded.
5 minutes
11/10/2018 – 7:00 pm Searching for the multimedia
file in the Clarks hard disk.
OUTCOME:
“Clowns dancing.mp4” image
file founded.
10 minutes
11/10/2018 – 7:10 pm Searching for the multimedia
file in the Clarks hard disk.
5 minutes
Page 39 of 47
Configuration Unit. Applied Mechanics And Materials, 635-637, 1981-1984. doi:
10.4028/www.scientific.net/amm.635-637.1981
Appendix I –Running Sheet
Date/Time Events Duration
11/10/2018 – 6:05 pm 182.dd hard disk image file
thoroughly examined by using
the appropriate digital forensics
examination tools. (Autopsy
Examination)
OUTCOME:
Laptop hard disk Image file
extracted into the autopsy
examination environment.
50 minutes
11/10/2018 – 6:55 pm Searching for the multimedia
file in the Clarks hard disk.
OUTCOME:
“kikki_down_party_pose.jpg”
image file founded.
5 minutes
11/10/2018 – 7:00 pm Searching for the multimedia
file in the Clarks hard disk.
OUTCOME:
“Clowns dancing.mp4” image
file founded.
10 minutes
11/10/2018 – 7:10 pm Searching for the multimedia
file in the Clarks hard disk.
5 minutes
Page 39 of 47
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
OUTCOME:
“WelcomeScan.jpg” image file
founded.
11/10/2018 – 7:15 pm Searching for the malware files.
OUTCOME:
kikki_clown_party_pose.jpg.ink
file founded.
15 minutes
11/10/2018 – 7:30 pm Searching for find other
suspicious files.
OUTCOME:
A Little Night Music – Send In
The Clown.pdf.Ink file
founded.
13 minutes
11/10/2018 – 7:43 pm Searching for other malicious
files.
OUTCOME:
Clowns dancing file founded.
6 minutes
11/10/2018 – 7:49 pm Searching for the evidences.
OUTCOME:
“Scary-haloween-costumes-
ideas-Clown-blood-haloween-
party-costumes” file founded.
5 minutes
11/10/2018 – 7:54 pm Searching for multimedia files.
OUTCOME:
Clowns dancing.mp4 file
founded.
4 minutes
17/10/2018 – 7:58pm Searching for evidences against
suspect.
OUTCOME:
A Little Night Music – Send In
17 minutes
Page 40 of 47
“WelcomeScan.jpg” image file
founded.
11/10/2018 – 7:15 pm Searching for the malware files.
OUTCOME:
kikki_clown_party_pose.jpg.ink
file founded.
15 minutes
11/10/2018 – 7:30 pm Searching for find other
suspicious files.
OUTCOME:
A Little Night Music – Send In
The Clown.pdf.Ink file
founded.
13 minutes
11/10/2018 – 7:43 pm Searching for other malicious
files.
OUTCOME:
Clowns dancing file founded.
6 minutes
11/10/2018 – 7:49 pm Searching for the evidences.
OUTCOME:
“Scary-haloween-costumes-
ideas-Clown-blood-haloween-
party-costumes” file founded.
5 minutes
11/10/2018 – 7:54 pm Searching for multimedia files.
OUTCOME:
Clowns dancing.mp4 file
founded.
4 minutes
17/10/2018 – 7:58pm Searching for evidences against
suspect.
OUTCOME:
A Little Night Music – Send In
17 minutes
Page 40 of 47
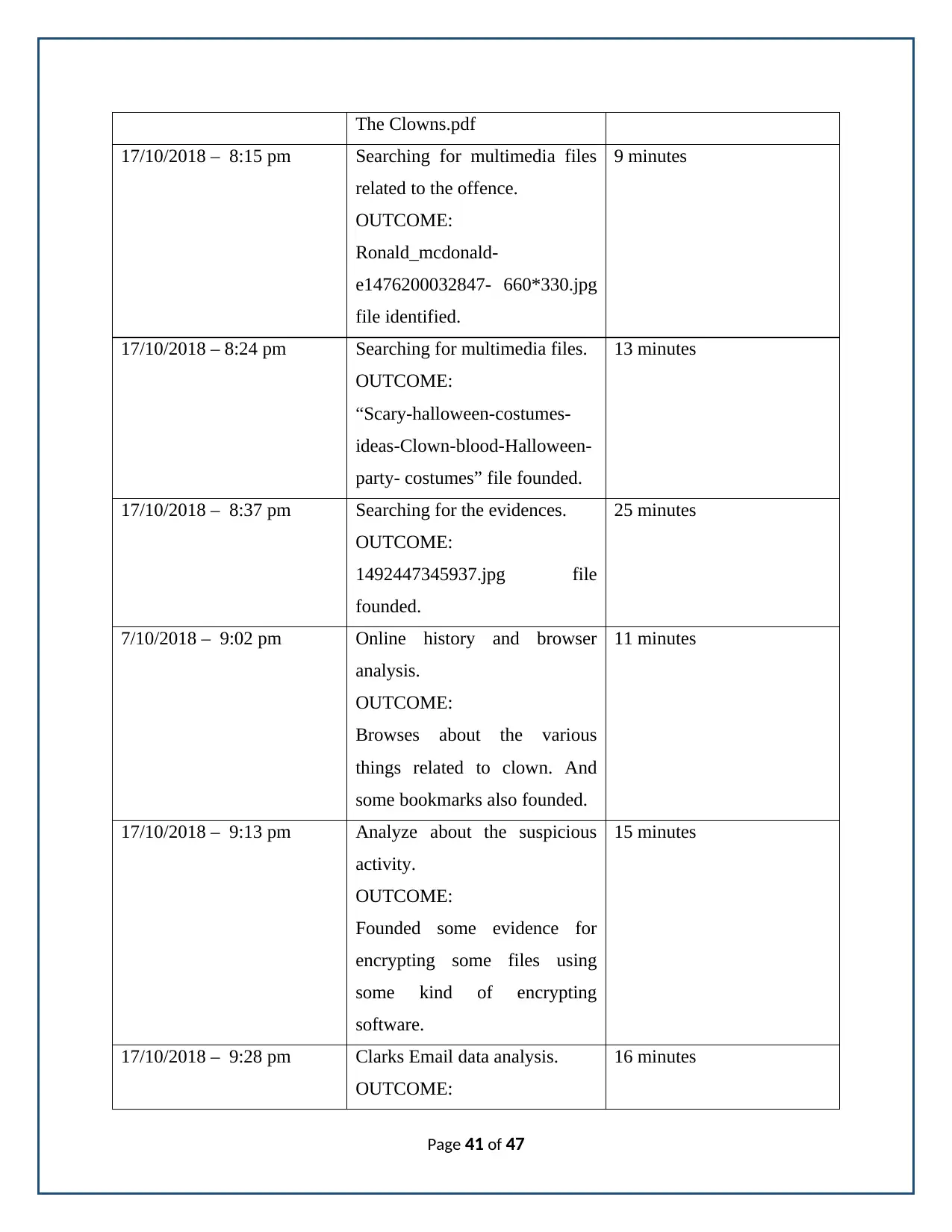
The Clowns.pdf
17/10/2018 – 8:15 pm Searching for multimedia files
related to the offence.
OUTCOME:
Ronald_mcdonald-
e1476200032847- 660*330.jpg
file identified.
9 minutes
17/10/2018 – 8:24 pm Searching for multimedia files.
OUTCOME:
“Scary-halloween-costumes-
ideas-Clown-blood-Halloween-
party- costumes” file founded.
13 minutes
17/10/2018 – 8:37 pm Searching for the evidences.
OUTCOME:
1492447345937.jpg file
founded.
25 minutes
7/10/2018 – 9:02 pm Online history and browser
analysis.
OUTCOME:
Browses about the various
things related to clown. And
some bookmarks also founded.
11 minutes
17/10/2018 – 9:13 pm Analyze about the suspicious
activity.
OUTCOME:
Founded some evidence for
encrypting some files using
some kind of encrypting
software.
15 minutes
17/10/2018 – 9:28 pm Clarks Email data analysis.
OUTCOME:
16 minutes
Page 41 of 47
17/10/2018 – 8:15 pm Searching for multimedia files
related to the offence.
OUTCOME:
Ronald_mcdonald-
e1476200032847- 660*330.jpg
file identified.
9 minutes
17/10/2018 – 8:24 pm Searching for multimedia files.
OUTCOME:
“Scary-halloween-costumes-
ideas-Clown-blood-Halloween-
party- costumes” file founded.
13 minutes
17/10/2018 – 8:37 pm Searching for the evidences.
OUTCOME:
1492447345937.jpg file
founded.
25 minutes
7/10/2018 – 9:02 pm Online history and browser
analysis.
OUTCOME:
Browses about the various
things related to clown. And
some bookmarks also founded.
11 minutes
17/10/2018 – 9:13 pm Analyze about the suspicious
activity.
OUTCOME:
Founded some evidence for
encrypting some files using
some kind of encrypting
software.
15 minutes
17/10/2018 – 9:28 pm Clarks Email data analysis.
OUTCOME:
16 minutes
Page 41 of 47
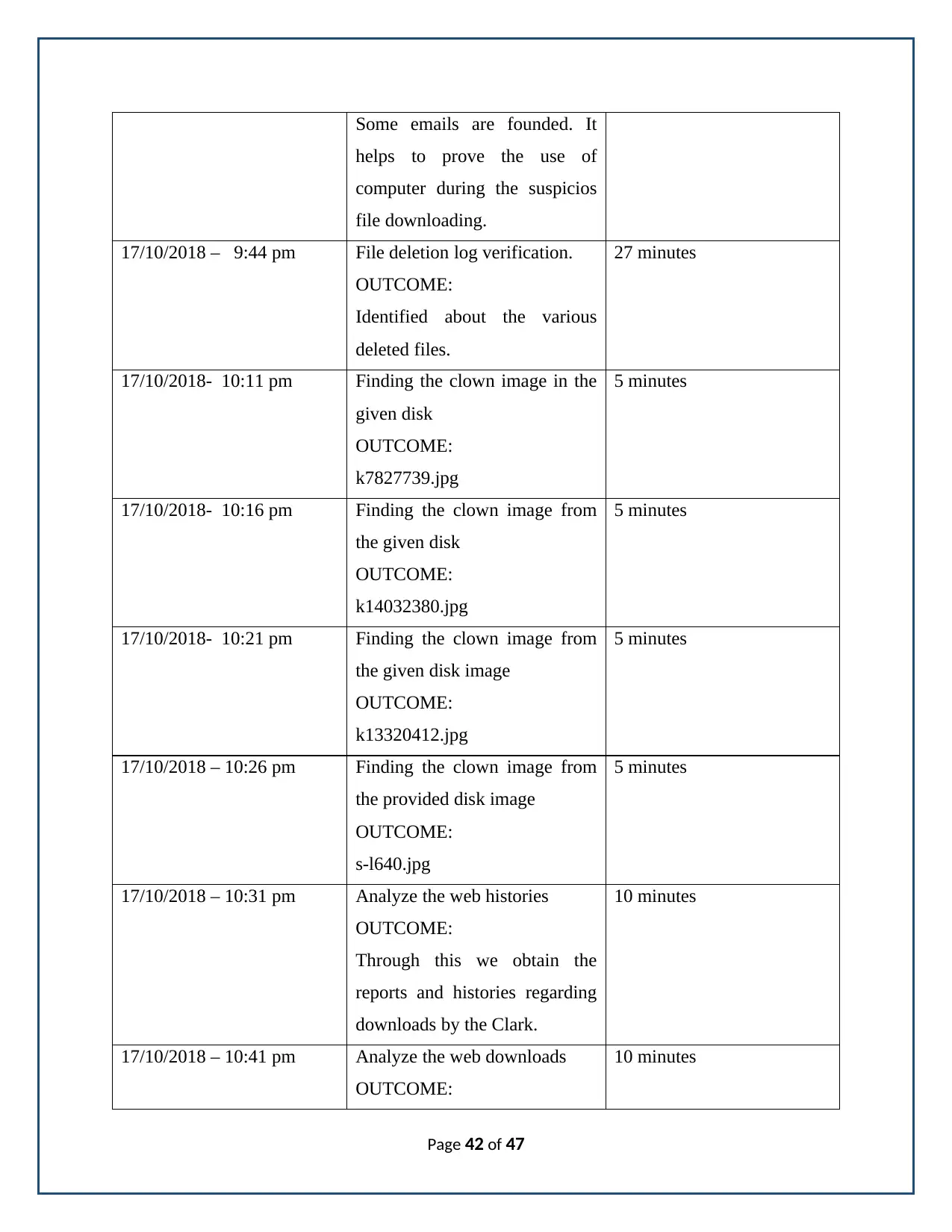
Some emails are founded. It
helps to prove the use of
computer during the suspicios
file downloading.
17/10/2018 – 9:44 pm File deletion log verification.
OUTCOME:
Identified about the various
deleted files.
27 minutes
17/10/2018- 10:11 pm Finding the clown image in the
given disk
OUTCOME:
k7827739.jpg
5 minutes
17/10/2018- 10:16 pm Finding the clown image from
the given disk
OUTCOME:
k14032380.jpg
5 minutes
17/10/2018- 10:21 pm Finding the clown image from
the given disk image
OUTCOME:
k13320412.jpg
5 minutes
17/10/2018 – 10:26 pm Finding the clown image from
the provided disk image
OUTCOME:
s-l640.jpg
5 minutes
17/10/2018 – 10:31 pm Analyze the web histories
OUTCOME:
Through this we obtain the
reports and histories regarding
downloads by the Clark.
10 minutes
17/10/2018 – 10:41 pm Analyze the web downloads
OUTCOME:
10 minutes
Page 42 of 47
helps to prove the use of
computer during the suspicios
file downloading.
17/10/2018 – 9:44 pm File deletion log verification.
OUTCOME:
Identified about the various
deleted files.
27 minutes
17/10/2018- 10:11 pm Finding the clown image in the
given disk
OUTCOME:
k7827739.jpg
5 minutes
17/10/2018- 10:16 pm Finding the clown image from
the given disk
OUTCOME:
k14032380.jpg
5 minutes
17/10/2018- 10:21 pm Finding the clown image from
the given disk image
OUTCOME:
k13320412.jpg
5 minutes
17/10/2018 – 10:26 pm Finding the clown image from
the provided disk image
OUTCOME:
s-l640.jpg
5 minutes
17/10/2018 – 10:31 pm Analyze the web histories
OUTCOME:
Through this we obtain the
reports and histories regarding
downloads by the Clark.
10 minutes
17/10/2018 – 10:41 pm Analyze the web downloads
OUTCOME:
10 minutes
Page 42 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

From this analysis we got
downloads by the Clark.
Through this we can proof the
victim as Clark.
17/10/2018 – 10:51 pm Analyze the web cookies and
web bookmarks
OUTCOME:
By this analysis we got the
searches made by the Clark.
Here the searches are made
related to the clown content.
10 minutes.
17/10/2018 – 11:01 pm Analyze the emails sent and
received by Clark.
Outcome:
By this analysis we got the
email content regarding the
clown content.
10 minutes.
Appendix II –Timeline of Events
Evidence Name Evidence
Type
Date of
Creation
(Year /
Month /
Date)
and Time
(Hour :
Minutes :
Seconds)
Date of
Modification
(Year /
Month /
Date)
and Time
(Hour :
Minutes :
Seconds)
Reason for
creations and
Creation method.
Clown dancing Video 16/06/2018
@ 8:15:41
16/06/2018 @
8:15:47
This file is created
by the victim. And
the source of the
image is online.
Page 43 of 47
downloads by the Clark.
Through this we can proof the
victim as Clark.
17/10/2018 – 10:51 pm Analyze the web cookies and
web bookmarks
OUTCOME:
By this analysis we got the
searches made by the Clark.
Here the searches are made
related to the clown content.
10 minutes.
17/10/2018 – 11:01 pm Analyze the emails sent and
received by Clark.
Outcome:
By this analysis we got the
email content regarding the
clown content.
10 minutes.
Appendix II –Timeline of Events
Evidence Name Evidence
Type
Date of
Creation
(Year /
Month /
Date)
and Time
(Hour :
Minutes :
Seconds)
Date of
Modification
(Year /
Month /
Date)
and Time
(Hour :
Minutes :
Seconds)
Reason for
creations and
Creation method.
Clown dancing Video 16/06/2018
@ 8:15:41
16/06/2018 @
8:15:47
This file is created
by the victim. And
the source of the
image is online.
Page 43 of 47
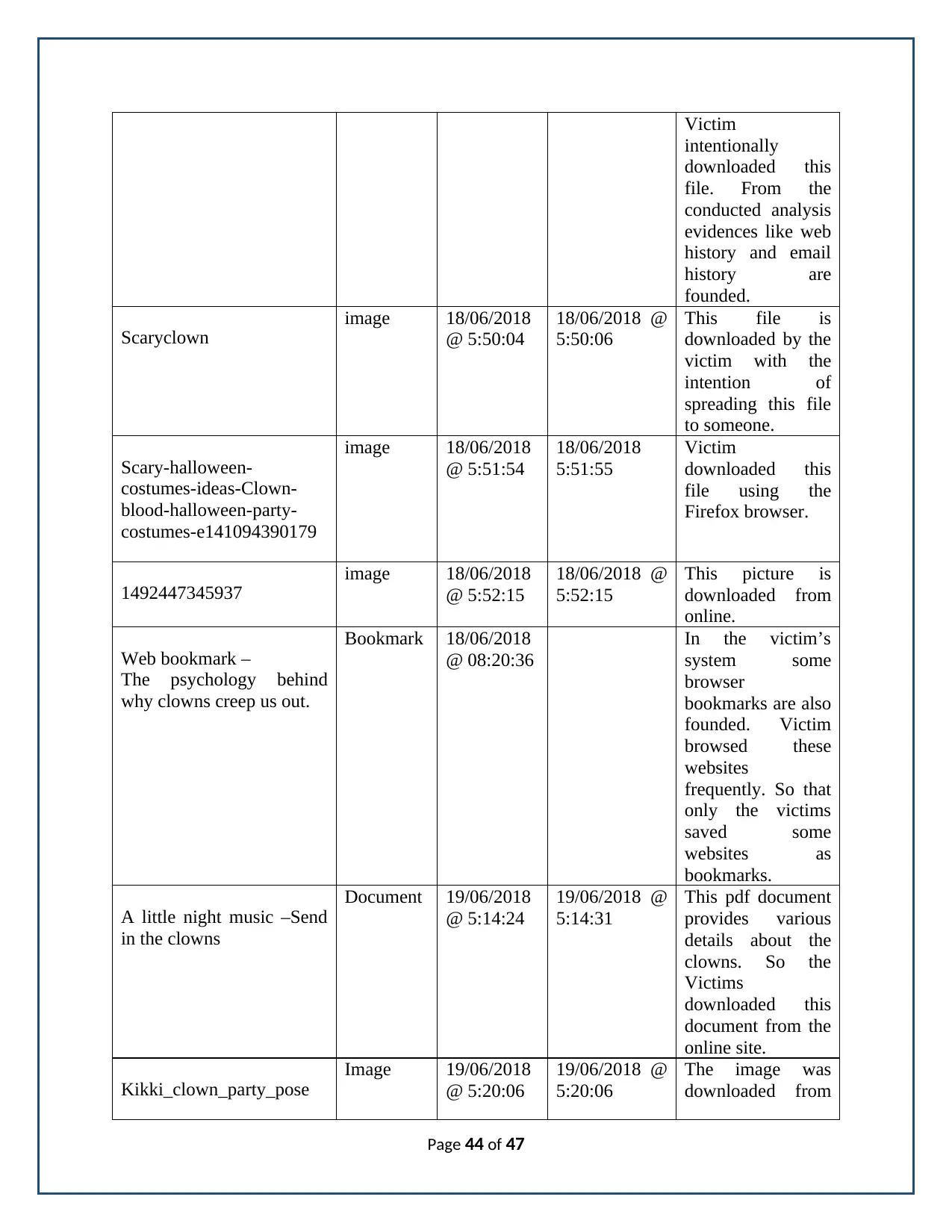
Victim
intentionally
downloaded this
file. From the
conducted analysis
evidences like web
history and email
history are
founded.
Scaryclown
image 18/06/2018
@ 5:50:04
18/06/2018 @
5:50:06
This file is
downloaded by the
victim with the
intention of
spreading this file
to someone.
Scary-halloween-
costumes-ideas-Clown-
blood-halloween-party-
costumes-e141094390179
image 18/06/2018
@ 5:51:54
18/06/2018
5:51:55
Victim
downloaded this
file using the
Firefox browser.
1492447345937
image 18/06/2018
@ 5:52:15
18/06/2018 @
5:52:15
This picture is
downloaded from
online.
Web bookmark –
The psychology behind
why clowns creep us out.
Bookmark 18/06/2018
@ 08:20:36
In the victim’s
system some
browser
bookmarks are also
founded. Victim
browsed these
websites
frequently. So that
only the victims
saved some
websites as
bookmarks.
A little night music –Send
in the clowns
Document 19/06/2018
@ 5:14:24
19/06/2018 @
5:14:31
This pdf document
provides various
details about the
clowns. So the
Victims
downloaded this
document from the
online site.
Kikki_clown_party_pose
Image 19/06/2018
@ 5:20:06
19/06/2018 @
5:20:06
The image was
downloaded from
Page 44 of 47
intentionally
downloaded this
file. From the
conducted analysis
evidences like web
history and email
history are
founded.
Scaryclown
image 18/06/2018
@ 5:50:04
18/06/2018 @
5:50:06
This file is
downloaded by the
victim with the
intention of
spreading this file
to someone.
Scary-halloween-
costumes-ideas-Clown-
blood-halloween-party-
costumes-e141094390179
image 18/06/2018
@ 5:51:54
18/06/2018
5:51:55
Victim
downloaded this
file using the
Firefox browser.
1492447345937
image 18/06/2018
@ 5:52:15
18/06/2018 @
5:52:15
This picture is
downloaded from
online.
Web bookmark –
The psychology behind
why clowns creep us out.
Bookmark 18/06/2018
@ 08:20:36
In the victim’s
system some
browser
bookmarks are also
founded. Victim
browsed these
websites
frequently. So that
only the victims
saved some
websites as
bookmarks.
A little night music –Send
in the clowns
Document 19/06/2018
@ 5:14:24
19/06/2018 @
5:14:31
This pdf document
provides various
details about the
clowns. So the
Victims
downloaded this
document from the
online site.
Kikki_clown_party_pose
Image 19/06/2018
@ 5:20:06
19/06/2018 @
5:20:06
The image was
downloaded from
Page 44 of 47
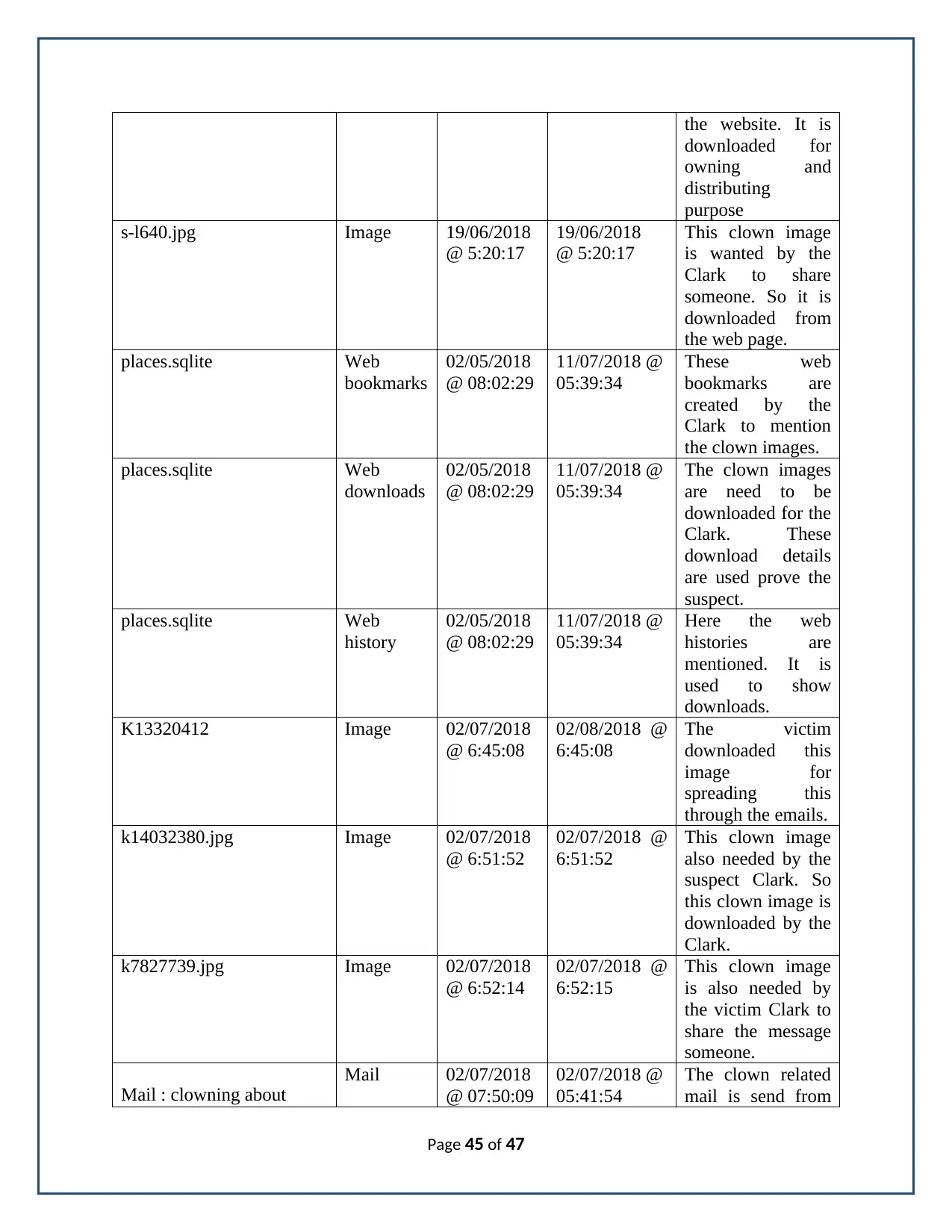
the website. It is
downloaded for
owning and
distributing
purpose
s-l640.jpg Image 19/06/2018
@ 5:20:17
19/06/2018
@ 5:20:17
This clown image
is wanted by the
Clark to share
someone. So it is
downloaded from
the web page.
places.sqlite Web
bookmarks
02/05/2018
@ 08:02:29
11/07/2018 @
05:39:34
These web
bookmarks are
created by the
Clark to mention
the clown images.
places.sqlite Web
downloads
02/05/2018
@ 08:02:29
11/07/2018 @
05:39:34
The clown images
are need to be
downloaded for the
Clark. These
download details
are used prove the
suspect.
places.sqlite Web
history
02/05/2018
@ 08:02:29
11/07/2018 @
05:39:34
Here the web
histories are
mentioned. It is
used to show
downloads.
K13320412 Image 02/07/2018
@ 6:45:08
02/08/2018 @
6:45:08
The victim
downloaded this
image for
spreading this
through the emails.
k14032380.jpg Image 02/07/2018
@ 6:51:52
02/07/2018 @
6:51:52
This clown image
also needed by the
suspect Clark. So
this clown image is
downloaded by the
Clark.
k7827739.jpg Image 02/07/2018
@ 6:52:14
02/07/2018 @
6:52:15
This clown image
is also needed by
the victim Clark to
share the message
someone.
Mail : clowning about
Mail 02/07/2018
@ 07:50:09
02/07/2018 @
05:41:54
The clown related
mail is send from
Page 45 of 47
downloaded for
owning and
distributing
purpose
s-l640.jpg Image 19/06/2018
@ 5:20:17
19/06/2018
@ 5:20:17
This clown image
is wanted by the
Clark to share
someone. So it is
downloaded from
the web page.
places.sqlite Web
bookmarks
02/05/2018
@ 08:02:29
11/07/2018 @
05:39:34
These web
bookmarks are
created by the
Clark to mention
the clown images.
places.sqlite Web
downloads
02/05/2018
@ 08:02:29
11/07/2018 @
05:39:34
The clown images
are need to be
downloaded for the
Clark. These
download details
are used prove the
suspect.
places.sqlite Web
history
02/05/2018
@ 08:02:29
11/07/2018 @
05:39:34
Here the web
histories are
mentioned. It is
used to show
downloads.
K13320412 Image 02/07/2018
@ 6:45:08
02/08/2018 @
6:45:08
The victim
downloaded this
image for
spreading this
through the emails.
k14032380.jpg Image 02/07/2018
@ 6:51:52
02/07/2018 @
6:51:52
This clown image
also needed by the
suspect Clark. So
this clown image is
downloaded by the
Clark.
k7827739.jpg Image 02/07/2018
@ 6:52:14
02/07/2018 @
6:52:15
This clown image
is also needed by
the victim Clark to
share the message
someone.
Mail : clowning about
Mail 02/07/2018
@ 07:50:09
02/07/2018 @
05:41:54
The clown related
mail is send from
Page 45 of 47
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
the Clark to Jazza
Simpson.
Page 46 of 47
Simpson.
Page 46 of 47
1 out of 47
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





