Comprehensive Report on Computer and Network Security Vulnerabilities
VerifiedAdded on 2019/09/30
|10
|902
|247
Report
AI Summary
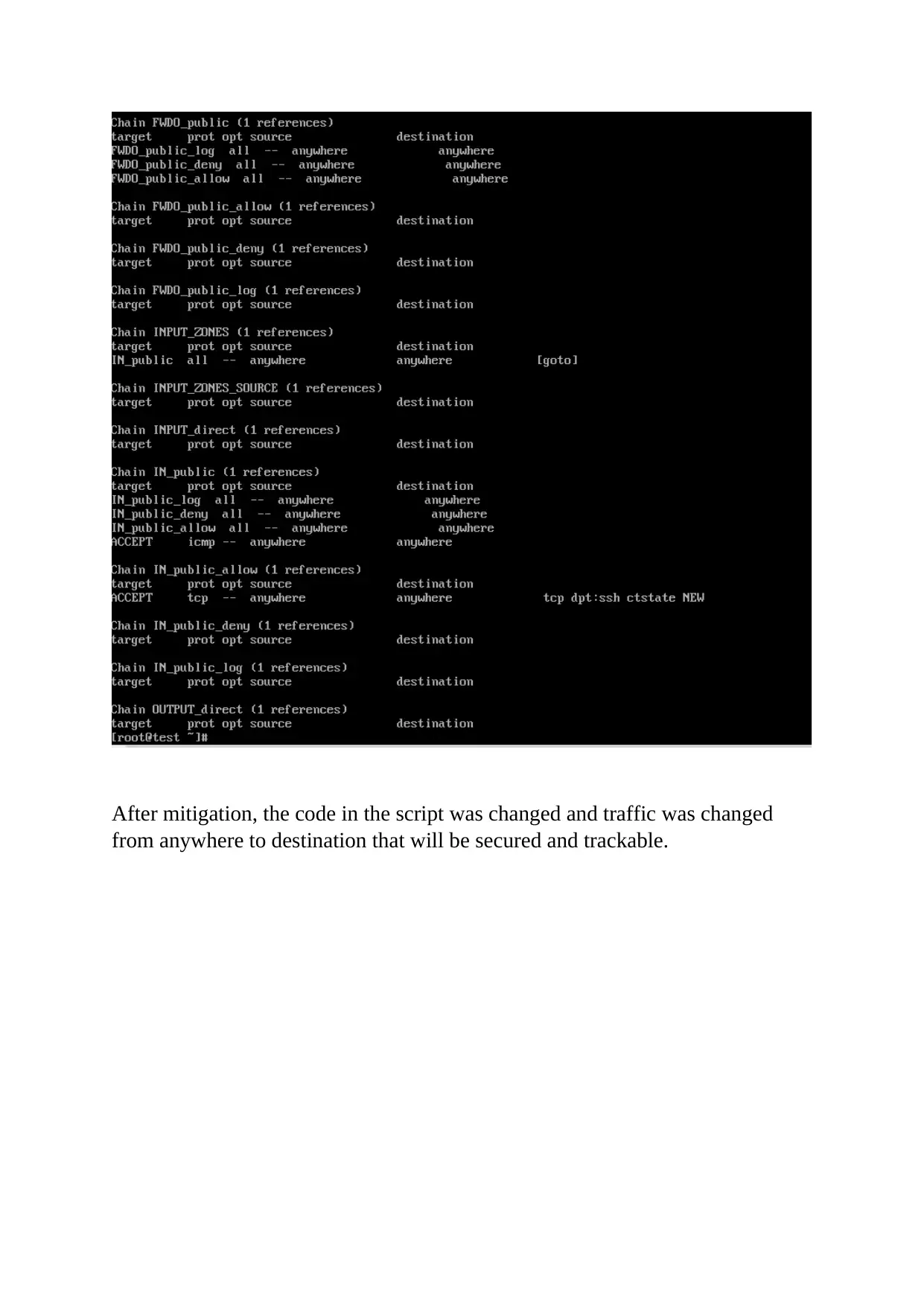
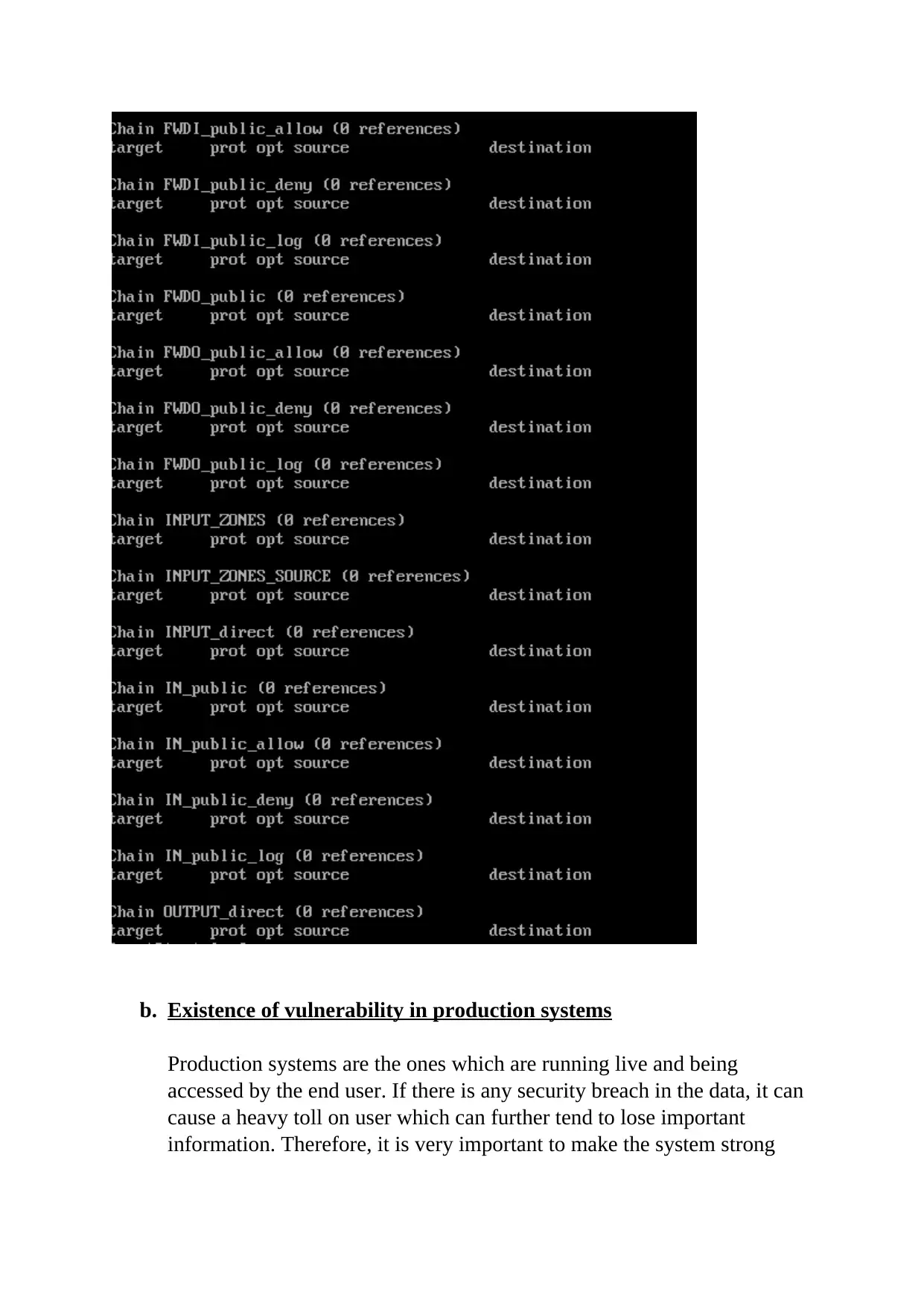
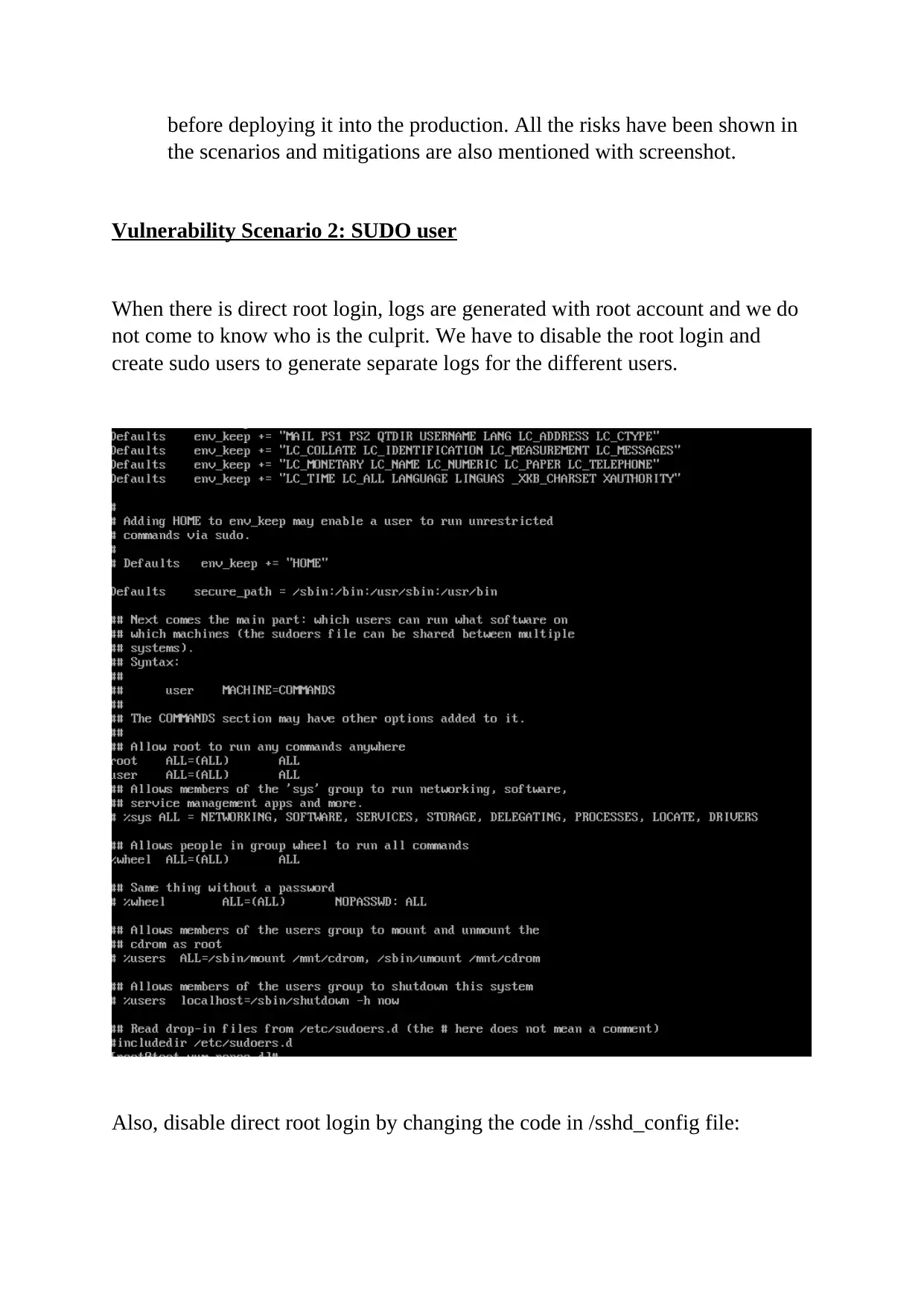
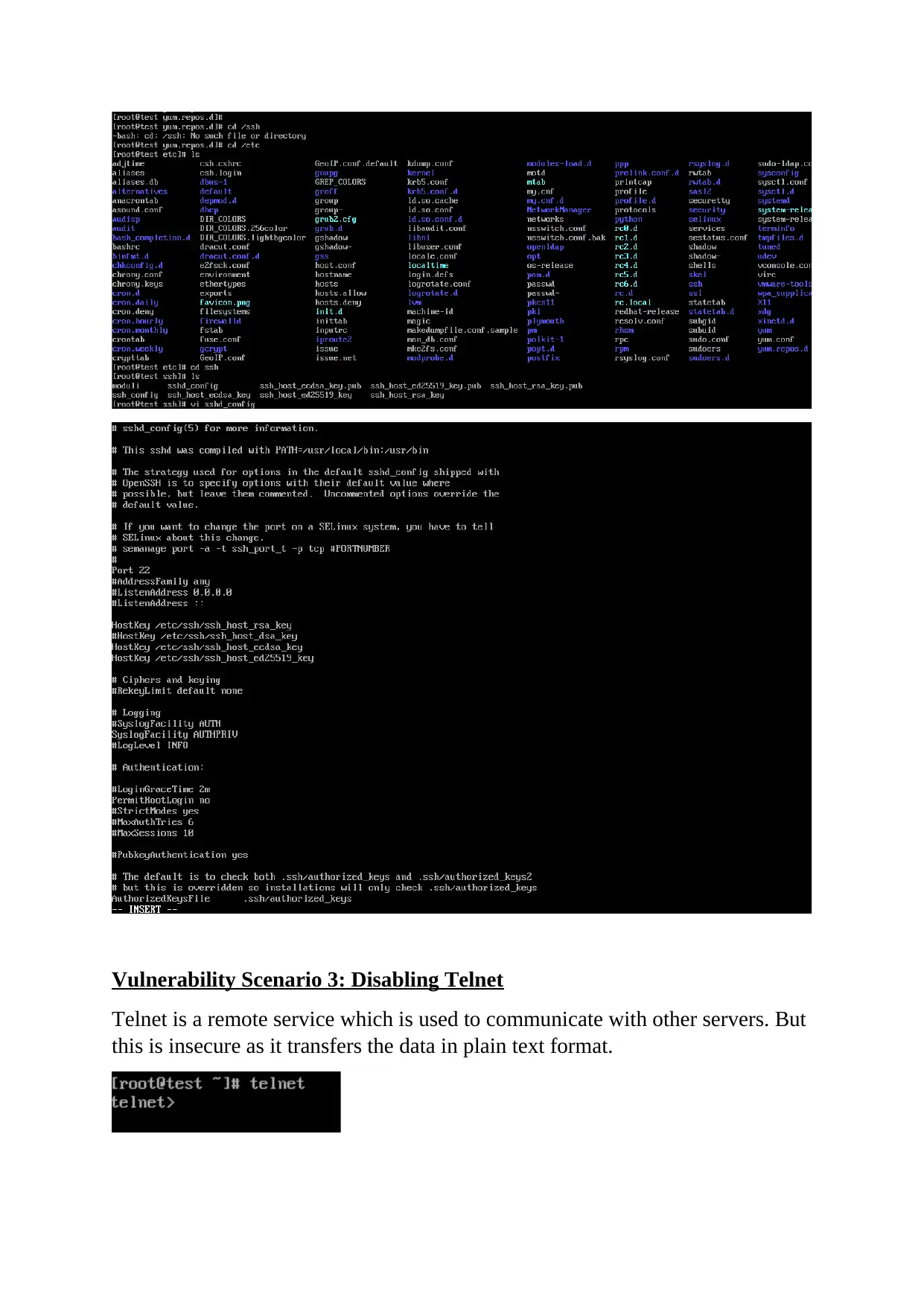
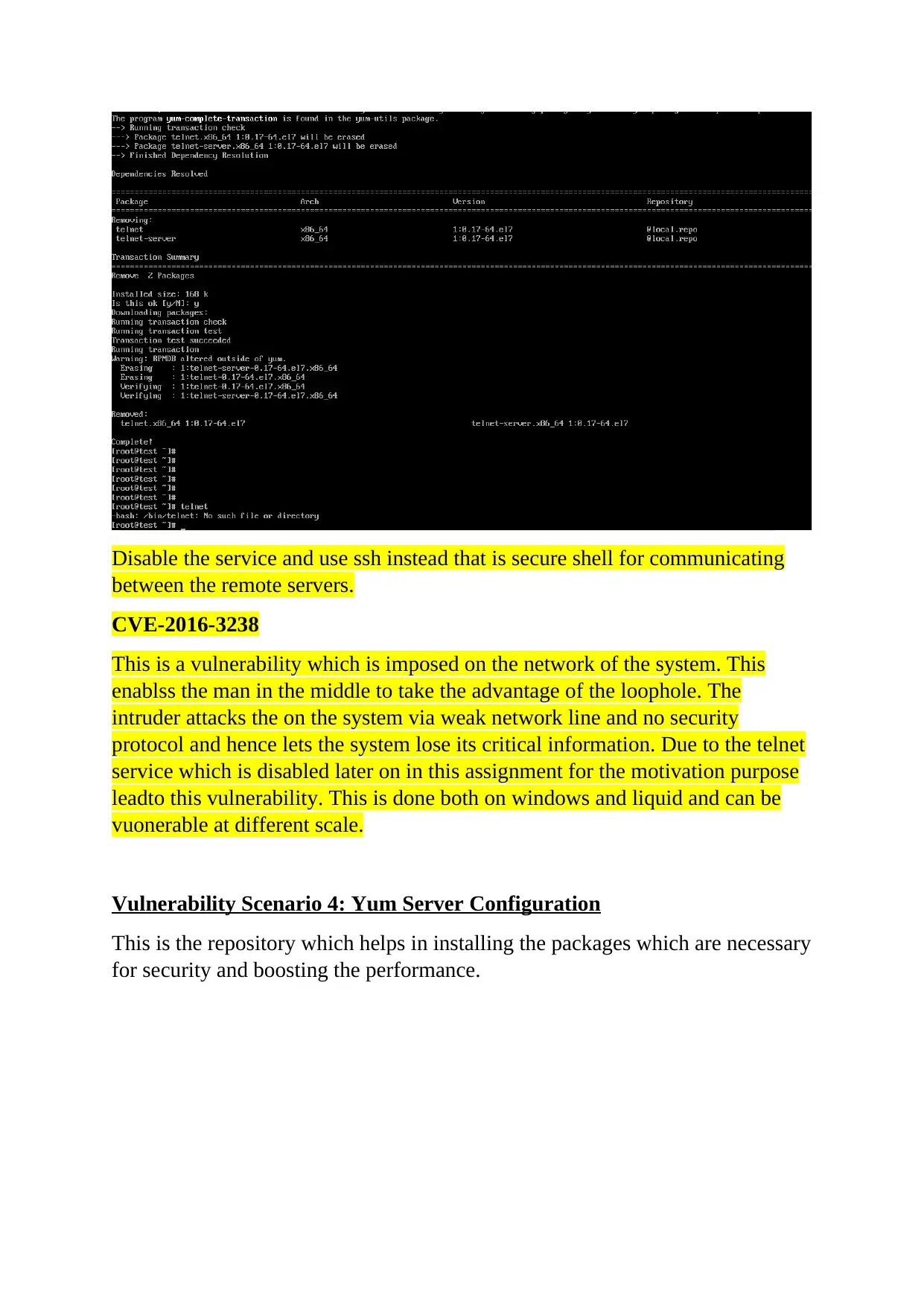
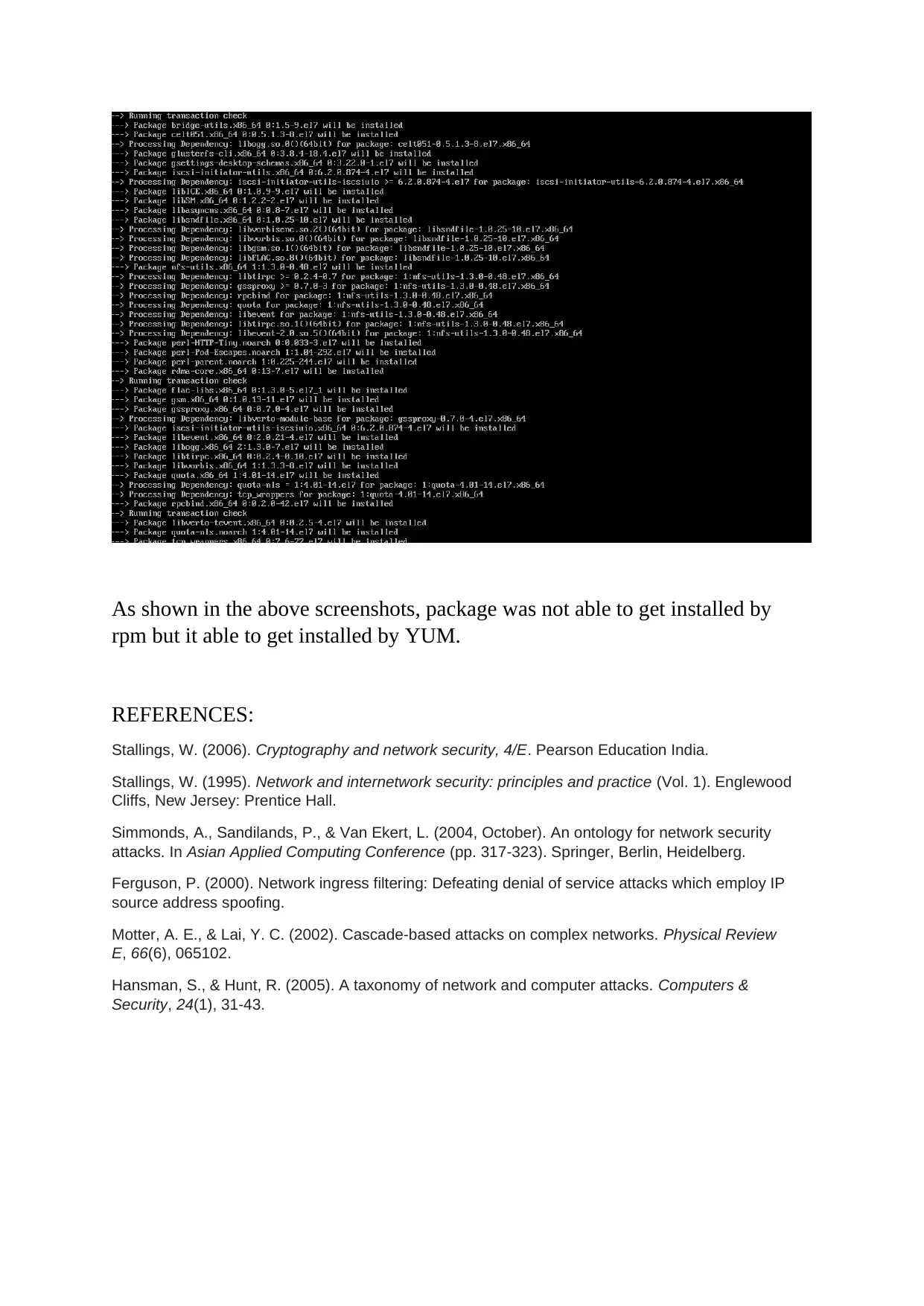
This report delves into the critical realm of computer and network security, focusing on various vulnerabilities and their corresponding mitigation strategies. It begins with an abstract emphasizing the significance of data security and system hardening. The report then meticulously details several vulnerabilities, including firewall rule misconfigurations, the risks associated with direct root login and the use of Telnet, and the impact of Yum server configuration. Each vulnerability is thoroughly explained with specific scenarios and potential attack vectors. The report also provides practical mitigation steps, such as adjusting firewall rules with IPTABLES, disabling direct root login and utilizing sudo users for enhanced logging, and replacing Telnet with SSH for secure remote communication. Furthermore, the report addresses CVE-2016-3238, highlighting the dangers of man-in-the-middle attacks facilitated by network vulnerabilities. Finally, the report illustrates the importance of using YUM for package installation to avoid security breaches, referencing relevant academic literature to support the analysis.
1 out of 10











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)