Computer & Network Security: Vulnerabilities and Mitigation Report
VerifiedAdded on 2019/09/30
|10
|810
|122
Report
AI Summary
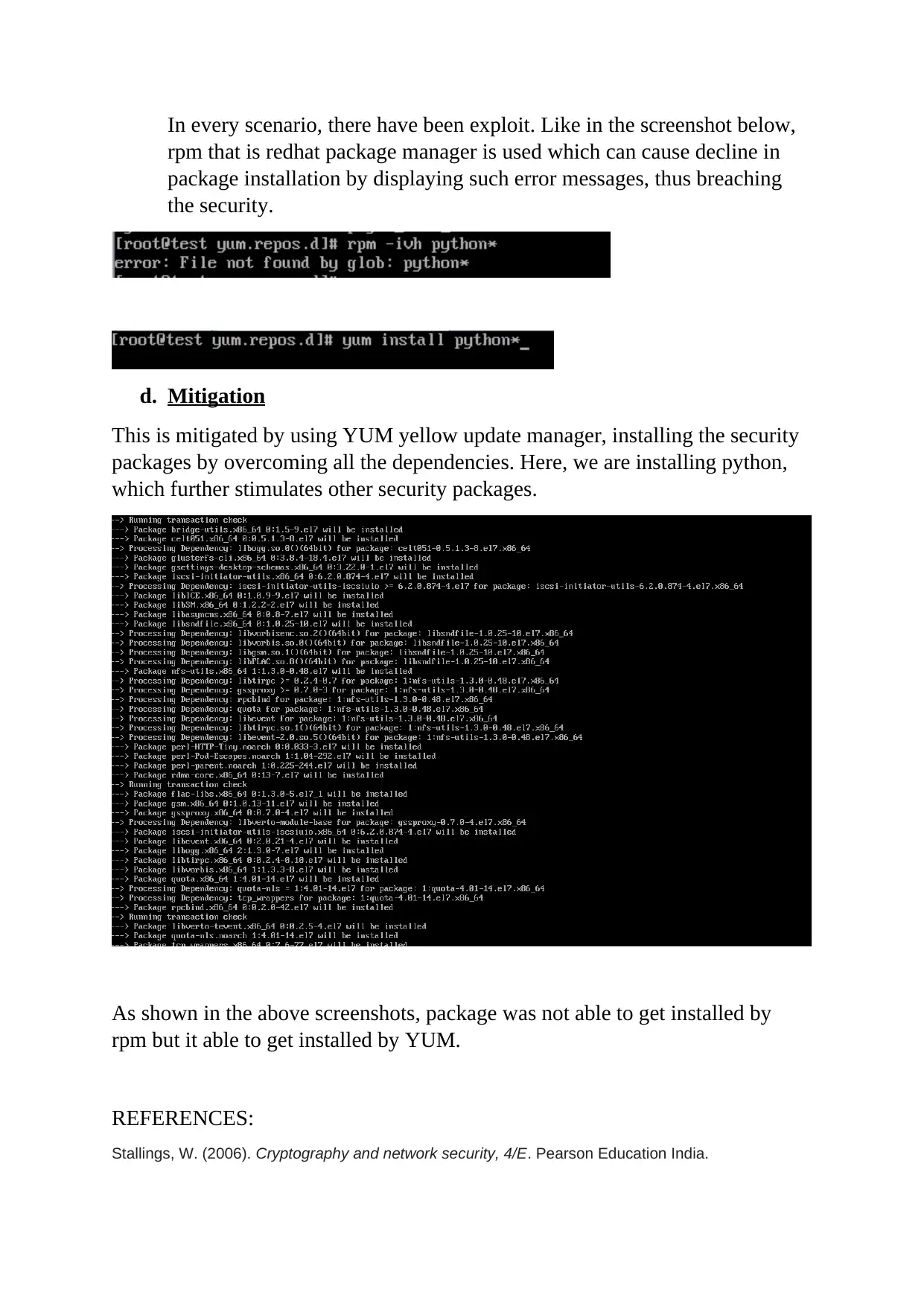
This report provides a comprehensive analysis of computer and network security, emphasizing the critical importance of data protection within organizations. It details various vulnerabilities, including firewall rule weaknesses, sudo user misconfigurations, insecure Telnet usage, and Yum server configuration issues, all of which can lead to significant security breaches. The report utilizes a Unix environment for security analysis and demonstrates how these vulnerabilities can be exploited. For each vulnerability scenario, the report offers specific mitigation strategies, such as modifying firewall rules, disabling direct root login, replacing Telnet with SSH, and using YUM for package installations. The report underscores the need for robust security measures before deploying systems into production environments and references several key sources in the field of cryptography and network security. The report provides practical steps for strengthening system security and preventing potential data loss or unauthorized access.
1 out of 10












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)