Adapting Social Spam Infrastructure for Political Censorship
VerifiedAdded on 2022/11/25
|3
|1106
|379
AI Summary
This research evaluates and analyzes the use of social spam infrastructure for political censorship. It discusses the impact of cyber-attacks and fraudulent accounts on computer networks and the personal information of consumers. The study also examines a specific cyber-attack that compromised thousands of consumer accounts.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
COMPUTER NETWORKS 1
Abstract
Aim: To evaluate and understand social spam infrastructure for political censorship.
Methods: in order to understand the key aspects of spam infrastructure the authors included various kinds of
methodologies such as qualitative design, inductive approach, secondary and primary data gathering techniques and
content analysis method.
Results: it is observed that a social network is an effective tool for political engagement and dissent. A miscreant is a
common issue which spams the computer service and accounts used by consumers and the findings of this paper
identified the impact of malicious and other cyber-attacks on computer infrastructure.
Conclusion: in this research, the authors analyzed and evaluated how criminals adapted fraudulent accounts for
performing malicious processes on computer networks. Moreover, the authors examined a cyber-attack developed
by miscreants which hacked around 25,860 accounts of consumers.
Keywords: spam infrastructure, computer services, cyber-attacks and spam.
Introduction
In the last few years, social networks have emerged
as an effective system for dissent and political
discussion. It is observed that the use of Facebook,
Twitter and Google+ are growing very that drive
public discourse and hacking is a common problem
for every country [1]. While the nation stated has the
capability to control and manage social spams and
cyber-attacks and Twitter is the best example of
social spam in which hackers collected data of
consumers. In this research, the author provides in-
depth analysis about social spams and also examines
the user’s accounts and infrastructure which impact
on the personal information of consumers. The
previous investigation evaluated cyber-attacks and
Sybil accounts but current research focuses on social
spam and their significance in political censorship. It
is observed that in the last few years Twitter has
suffered from a data breach in which hacked
collected data of 25,860 consumers and stakeholders
[2].
Background
This section of this research identifies how hackers
can attempt to censor twitter by using fraud accounts
and spams. It is observed that most of the hackers use
fraud accounts and unauthorized networks for
performing data breach related activities and
malicious software help hackers for obtaining data of
consumers. In Twitter Hashtag is defined as a
mechanism used to organize communication around
topics happen outside the social network of
consumers. In the case of cyber-attacks, such kinds of
automated Sybil produce conflict in the system and
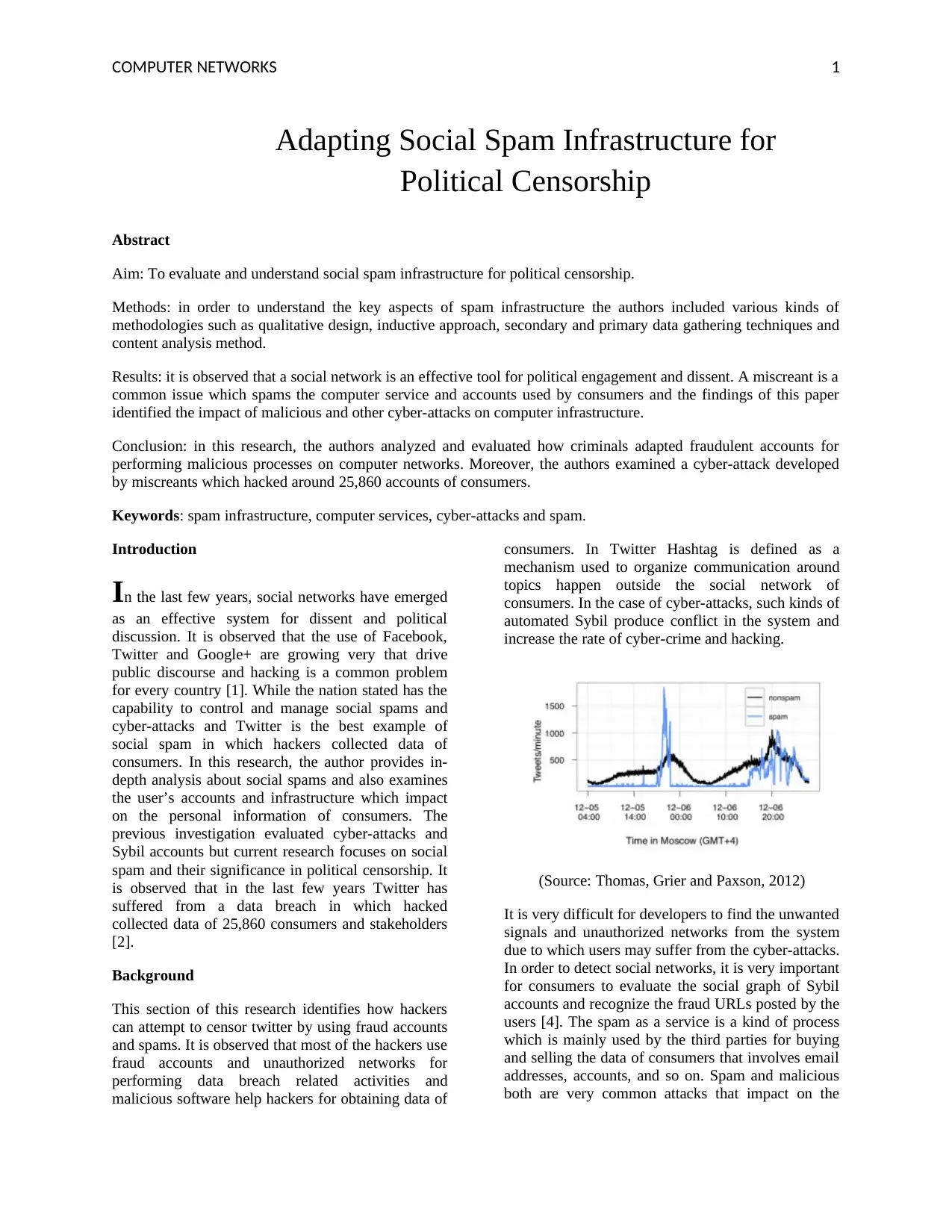
increase the rate of cyber-crime and hacking.
(Source: Thomas, Grier and Paxson, 2012)
It is very difficult for developers to find the unwanted
signals and unauthorized networks from the system
due to which users may suffer from the cyber-attacks.
In order to detect social networks, it is very important
for consumers to evaluate the social graph of Sybil
accounts and recognize the fraud URLs posted by the
users [4]. The spam as a service is a kind of process
which is mainly used by the third parties for buying
and selling the data of consumers that involves email
addresses, accounts, and so on. Spam and malicious
both are very common attacks that impact on the
Adapting Social Spam Infrastructure for
Political Censorship
Abstract
Aim: To evaluate and understand social spam infrastructure for political censorship.
Methods: in order to understand the key aspects of spam infrastructure the authors included various kinds of
methodologies such as qualitative design, inductive approach, secondary and primary data gathering techniques and
content analysis method.
Results: it is observed that a social network is an effective tool for political engagement and dissent. A miscreant is a
common issue which spams the computer service and accounts used by consumers and the findings of this paper
identified the impact of malicious and other cyber-attacks on computer infrastructure.
Conclusion: in this research, the authors analyzed and evaluated how criminals adapted fraudulent accounts for
performing malicious processes on computer networks. Moreover, the authors examined a cyber-attack developed
by miscreants which hacked around 25,860 accounts of consumers.
Keywords: spam infrastructure, computer services, cyber-attacks and spam.
Introduction
In the last few years, social networks have emerged
as an effective system for dissent and political
discussion. It is observed that the use of Facebook,
Twitter and Google+ are growing very that drive
public discourse and hacking is a common problem
for every country [1]. While the nation stated has the
capability to control and manage social spams and
cyber-attacks and Twitter is the best example of
social spam in which hackers collected data of
consumers. In this research, the author provides in-
depth analysis about social spams and also examines
the user’s accounts and infrastructure which impact
on the personal information of consumers. The
previous investigation evaluated cyber-attacks and
Sybil accounts but current research focuses on social
spam and their significance in political censorship. It
is observed that in the last few years Twitter has
suffered from a data breach in which hacked
collected data of 25,860 consumers and stakeholders
[2].
Background
This section of this research identifies how hackers
can attempt to censor twitter by using fraud accounts
and spams. It is observed that most of the hackers use
fraud accounts and unauthorized networks for
performing data breach related activities and
malicious software help hackers for obtaining data of
consumers. In Twitter Hashtag is defined as a
mechanism used to organize communication around
topics happen outside the social network of
consumers. In the case of cyber-attacks, such kinds of
automated Sybil produce conflict in the system and
increase the rate of cyber-crime and hacking.
(Source: Thomas, Grier and Paxson, 2012)
It is very difficult for developers to find the unwanted
signals and unauthorized networks from the system
due to which users may suffer from the cyber-attacks.
In order to detect social networks, it is very important
for consumers to evaluate the social graph of Sybil
accounts and recognize the fraud URLs posted by the
users [4]. The spam as a service is a kind of process
which is mainly used by the third parties for buying
and selling the data of consumers that involves email
addresses, accounts, and so on. Spam and malicious
both are very common attacks that impact on the
Adapting Social Spam Infrastructure for
Political Censorship
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
COMPUTER NETWORKS 2
personal data files and many companies are suffering
from such kinds of crimes. Twitter is an example
where hackers performed malicious and spam
activities and numbers of users lost their personal
information [3].
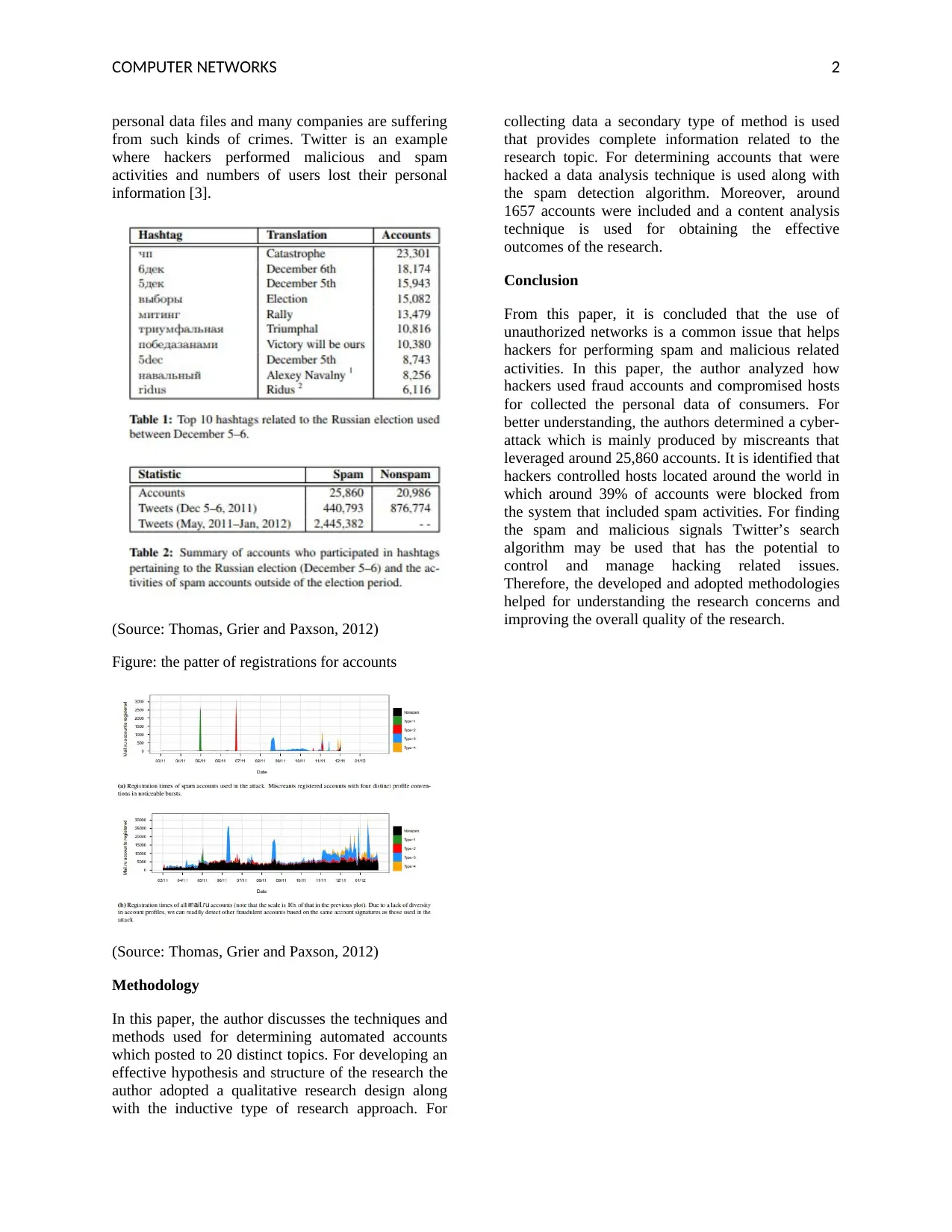
(Source: Thomas, Grier and Paxson, 2012)
Figure: the patter of registrations for accounts
(Source: Thomas, Grier and Paxson, 2012)
Methodology
In this paper, the author discusses the techniques and
methods used for determining automated accounts
which posted to 20 distinct topics. For developing an
effective hypothesis and structure of the research the
author adopted a qualitative research design along
with the inductive type of research approach. For
collecting data a secondary type of method is used
that provides complete information related to the
research topic. For determining accounts that were
hacked a data analysis technique is used along with
the spam detection algorithm. Moreover, around
1657 accounts were included and a content analysis
technique is used for obtaining the effective
outcomes of the research.
Conclusion
From this paper, it is concluded that the use of
unauthorized networks is a common issue that helps
hackers for performing spam and malicious related
activities. In this paper, the author analyzed how
hackers used fraud accounts and compromised hosts
for collected the personal data of consumers. For
better understanding, the authors determined a cyber-
attack which is mainly produced by miscreants that
leveraged around 25,860 accounts. It is identified that
hackers controlled hosts located around the world in
which around 39% of accounts were blocked from
the system that included spam activities. For finding
the spam and malicious signals Twitter’s search
algorithm may be used that has the potential to
control and manage hacking related issues.
Therefore, the developed and adopted methodologies
helped for understanding the research concerns and
improving the overall quality of the research.
personal data files and many companies are suffering
from such kinds of crimes. Twitter is an example
where hackers performed malicious and spam
activities and numbers of users lost their personal
information [3].
(Source: Thomas, Grier and Paxson, 2012)
Figure: the patter of registrations for accounts
(Source: Thomas, Grier and Paxson, 2012)
Methodology
In this paper, the author discusses the techniques and
methods used for determining automated accounts
which posted to 20 distinct topics. For developing an
effective hypothesis and structure of the research the
author adopted a qualitative research design along
with the inductive type of research approach. For
collecting data a secondary type of method is used
that provides complete information related to the
research topic. For determining accounts that were
hacked a data analysis technique is used along with
the spam detection algorithm. Moreover, around
1657 accounts were included and a content analysis
technique is used for obtaining the effective
outcomes of the research.
Conclusion
From this paper, it is concluded that the use of
unauthorized networks is a common issue that helps
hackers for performing spam and malicious related
activities. In this paper, the author analyzed how
hackers used fraud accounts and compromised hosts
for collected the personal data of consumers. For
better understanding, the authors determined a cyber-
attack which is mainly produced by miscreants that
leveraged around 25,860 accounts. It is identified that
hackers controlled hosts located around the world in
which around 39% of accounts were blocked from
the system that included spam activities. For finding
the spam and malicious signals Twitter’s search
algorithm may be used that has the potential to
control and manage hacking related issues.
Therefore, the developed and adopted methodologies
helped for understanding the research concerns and
improving the overall quality of the research.

COMPUTER NETWORKS 3
References
[1]. K., Thomas, C. Grier and, V., Paxson,
“Adapting social spam infrastructure for
political censorship,” In Presented as part of
the 5th {USENIX} Workshop on Large-
Scale Exploits and Emergent Threats, vol. 5,
no. 2, pp. 2-8, 2012.
[2]. H., Gao, J., Hu, C., Wilson, Z., Li, Y. Chen
and, B.Y., Zhao, “Detecting and
characterizing social spam campaigns,”
In Proceedings of the 10th ACM SIGCOMM
conference on Internet measurement, vol. 5,
no. 2, pp. 35-47, 2010.
[3]. C., Grier, K., Thomas, V. Paxson and, M.,
Zhang, “@ spam: the underground on 140
characters or less,” In Proceedings of the
17th ACM conference on Computer and
communications security, vol. 12, no. 6, pp.
27-37, 2010.
[4]. N. Jindal and, B., Liu, “Opinion spam and
analysis,” In Proceedings of the 2008
international conference on web search and
data mining, vol. 12, no. 6, pp. 219-230,
2008.
References
[1]. K., Thomas, C. Grier and, V., Paxson,
“Adapting social spam infrastructure for
political censorship,” In Presented as part of
the 5th {USENIX} Workshop on Large-
Scale Exploits and Emergent Threats, vol. 5,
no. 2, pp. 2-8, 2012.
[2]. H., Gao, J., Hu, C., Wilson, Z., Li, Y. Chen
and, B.Y., Zhao, “Detecting and
characterizing social spam campaigns,”
In Proceedings of the 10th ACM SIGCOMM
conference on Internet measurement, vol. 5,
no. 2, pp. 35-47, 2010.
[3]. C., Grier, K., Thomas, V. Paxson and, M.,
Zhang, “@ spam: the underground on 140
characters or less,” In Proceedings of the
17th ACM conference on Computer and
communications security, vol. 12, no. 6, pp.
27-37, 2010.
[4]. N. Jindal and, B., Liu, “Opinion spam and
analysis,” In Proceedings of the 2008
international conference on web search and
data mining, vol. 12, no. 6, pp. 219-230,
2008.
1 out of 3
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





