Computer Networks and Cybersecurity: Threats and Controls
Describe and classify the type of controls that should be put in place in an organization for various threat categories in computer networks and cybersecurity.
13 Pages1739 Words446 Views
Added on 2023-06-03
About This Document
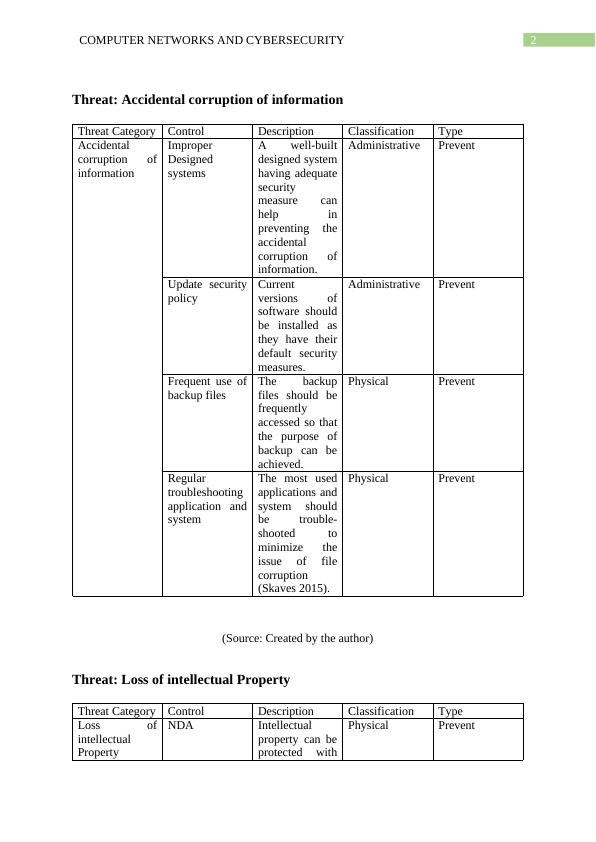
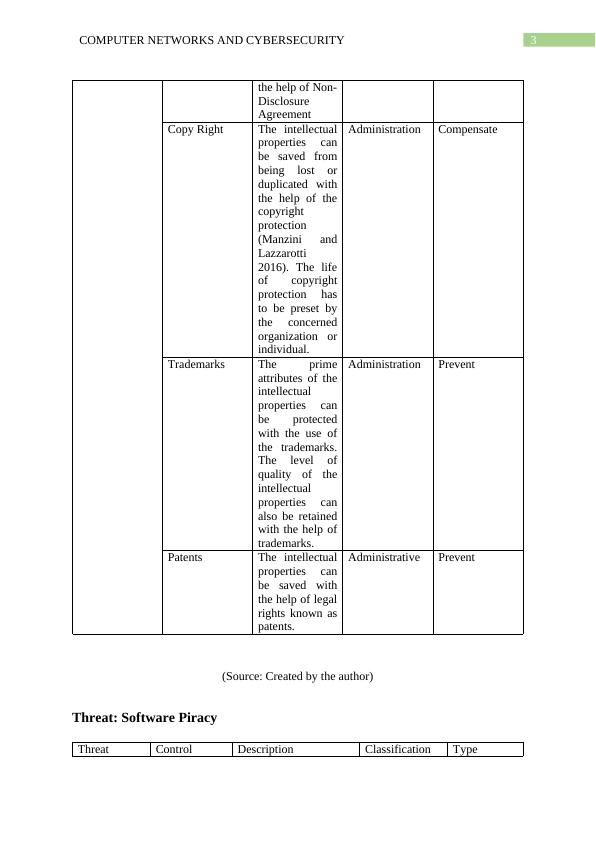
This article discusses the various threats and controls in Computer Networks and Cybersecurity. It covers topics such as accidental corruption of information, loss of intellectual property, software piracy, theft of information, website defacement, theft of equipment, viruses, worms, Trojan horses, elevation of privilege, and fire/flood. The article provides detailed descriptions of each threat and suggests preventive measures to protect against them.
Computer Networks and Cybersecurity: Threats and Controls
Describe and classify the type of controls that should be put in place in an organization for various threat categories in computer networks and cybersecurity.
Added on 2023-06-03
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Network and Security - Threats and Controls
|14
|1843
|104
Threat Categories for Information Security: Prevention and Detection Techniques
|13
|1796
|257
Network and Security: Threats and Controls
|10
|1781
|75
Network and Security: Threat Control
|14
|1775
|486
Network and Cybersecurity: Threats and Control Measures
|13
|1909
|314
ENGR8762 Computer Networks and Cybersecurity
|8
|1020
|164