Network and Security: Comprehensive Threat Control Strategies Report
VerifiedAdded on 2023/06/03
|14
|1775
|486
Report
AI Summary
This report presents a comprehensive analysis of network and security threat control, addressing various threat categories and recommending appropriate control measures. The report categorizes controls as Administrative, Product, or Physical, and classifies them as Prevent, Detect, Correct, or Compensate. The threat categories covered include accidental corruption of information, loss of intellectual property, software piracy, theft of information (hacker and employee), website defacement, theft of equipment, viruses, worms, Trojan horses, elevation of privilege, and fire/flood. For each threat, the report suggests specific control descriptions, such as regular backups, access control, antivirus protection, and the use of firewalls, detailing their classification and type. Furthermore, the report emphasizes the importance of incident response planning, security policies, and regular audits to mitigate risks and maintain a secure network environment. The report concludes by providing a bibliography of relevant academic sources.

Running head: NETWORK AND SECURITY
Network and Security
Name of the Student
Name of the University
Author Note
Network and Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
NETWORK AND SECURITY
Threat Control
It is essential to identify the threats and set accurate controls for the identified threats. This eliminates the risks of business
loss. The recommendations for control to certain threat categories are represented in the following table-
Threat Category Control Description Classification Type
Accidental
corruption of
information
Regular Backup Regular backup will eliminate the
chances of data loss even if the
information stored is accidentally
corrupted
Administrative Compensate
Protection against Power
disturbances
One of the significant reasons of data
corruption is power disturbances. If
that can be fixed, the probability of
data corruption can be reduced.
Administrative Prevent
Ensuring proper shutting down
of the system after use
Data can be corrupted with improper
handling of information system and
therefore, it needs to be prevented
Administrative Prevent
Use of Proper antivirus and
spyware protection
Another significant reason behind
data corruption might be because of
Product Detect
NETWORK AND SECURITY
Threat Control
It is essential to identify the threats and set accurate controls for the identified threats. This eliminates the risks of business
loss. The recommendations for control to certain threat categories are represented in the following table-
Threat Category Control Description Classification Type
Accidental
corruption of
information
Regular Backup Regular backup will eliminate the
chances of data loss even if the
information stored is accidentally
corrupted
Administrative Compensate
Protection against Power
disturbances
One of the significant reasons of data
corruption is power disturbances. If
that can be fixed, the probability of
data corruption can be reduced.
Administrative Prevent
Ensuring proper shutting down
of the system after use
Data can be corrupted with improper
handling of information system and
therefore, it needs to be prevented
Administrative Prevent
Use of Proper antivirus and
spyware protection
Another significant reason behind
data corruption might be because of
Product Detect
2
NETWORK AND SECURITY
malware infection which can be
eliminated by making use of proper
antivirus and spyware protection.
Loss of
intellectual
property
Ensuring confidentiality by
enforcing access control
Access control can possibly ensure
confidentiality of intellectual
property thereby preventing the loss
of the same.
Administrative Detect
Maintaining good records of
data
This is important for prevention of
loss of intellectual property.
Administrative Compensate
The contacts and grant of rights
for the property access should
be checked.
The grant of rights should be wise in
order to prevent the loss of
intellectual property.
Administrative Prevent
Incoming trade secretes should
be restricted
Certain incoming trade secrets can
be risky for the intellectual property
and thus should be restricted.
Administrative Prevent
Regular Intellectual property
Audits
Regular audits will be able to
identify the risks associated with the
Administrative Prevent
NETWORK AND SECURITY
malware infection which can be
eliminated by making use of proper
antivirus and spyware protection.
Loss of
intellectual
property
Ensuring confidentiality by
enforcing access control
Access control can possibly ensure
confidentiality of intellectual
property thereby preventing the loss
of the same.
Administrative Detect
Maintaining good records of
data
This is important for prevention of
loss of intellectual property.
Administrative Compensate
The contacts and grant of rights
for the property access should
be checked.
The grant of rights should be wise in
order to prevent the loss of
intellectual property.
Administrative Prevent
Incoming trade secretes should
be restricted
Certain incoming trade secrets can
be risky for the intellectual property
and thus should be restricted.
Administrative Prevent
Regular Intellectual property
Audits
Regular audits will be able to
identify the risks associated with the
Administrative Prevent
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORK AND SECURITY
intellectual property.
Software piracy Development of software
policy statement
Having a clear software piracy
statement will help in explaining
how employees can legally acquire a
software thus preventing its piracy.
Product Prevent
Make employees accept and
sign an anti piracy statement
This will prevent the processing of
the information without permission.
Administrative Prevent
Ensuring regular software
inventories
If the staffs of an organization make
sure that the product name, version
number and the serial number for
each piece of software installed on
every computer is documented, the
issue can be prevented. Furthermore,
it is necessary for an organization to
perform unannounced audits.
Administrative Detect
An accurate knowledge of It is essential to keep all the licenses Administrative Prevent
NETWORK AND SECURITY
intellectual property.
Software piracy Development of software
policy statement
Having a clear software piracy
statement will help in explaining
how employees can legally acquire a
software thus preventing its piracy.
Product Prevent
Make employees accept and
sign an anti piracy statement
This will prevent the processing of
the information without permission.
Administrative Prevent
Ensuring regular software
inventories
If the staffs of an organization make
sure that the product name, version
number and the serial number for
each piece of software installed on
every computer is documented, the
issue can be prevented. Furthermore,
it is necessary for an organization to
perform unannounced audits.
Administrative Detect
An accurate knowledge of It is essential to keep all the licenses Administrative Prevent
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORK AND SECURITY
what the software licenses
allow
in one place to prevent the risk of
software piracy.
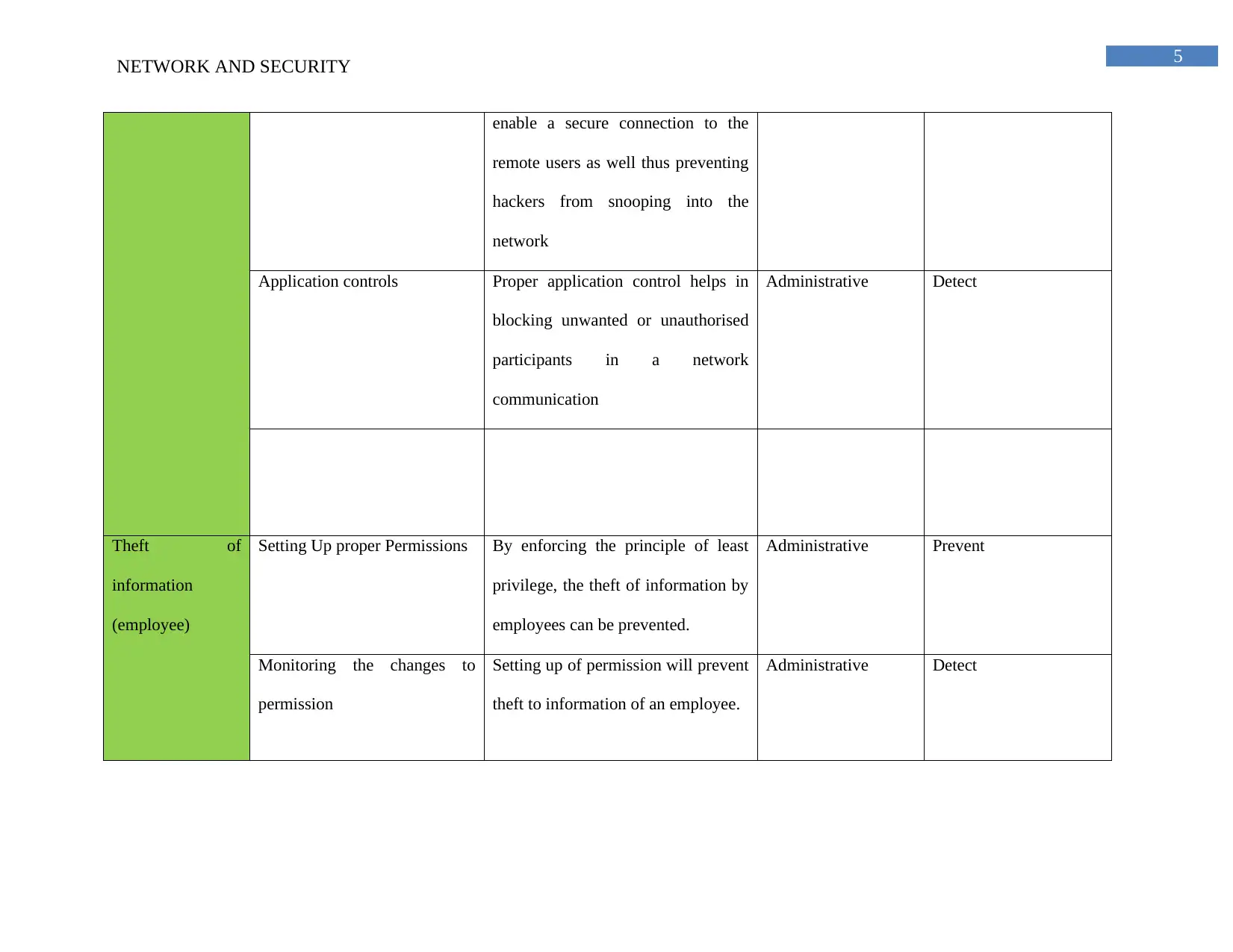
Theft of
information
(hacker)
Use of proxy services Use of proxy services will block the
revealing details of internal IP
addressing on networks
Product Detect
Stateful packet inspection It will help in distinguishing the
legitimate network communication
from the malicious forms of
communication thus saving from
information threat
Administrative Detect
Real time packet decryption Real time packet decryption helps an
organization to apply content level
control to the data for policy
compliance and malware filtering.
Administrative Detect
Email Handling Email handling is a control since it
includes malware detection, removal
of spam filtering and content check.
Administrative Prevent
Use of Virtual private network Use of virtual private network will Product Prevent
NETWORK AND SECURITY
what the software licenses
allow
in one place to prevent the risk of
software piracy.
Theft of
information
(hacker)
Use of proxy services Use of proxy services will block the
revealing details of internal IP
addressing on networks
Product Detect
Stateful packet inspection It will help in distinguishing the
legitimate network communication
from the malicious forms of
communication thus saving from
information threat
Administrative Detect
Real time packet decryption Real time packet decryption helps an
organization to apply content level
control to the data for policy
compliance and malware filtering.
Administrative Detect
Email Handling Email handling is a control since it
includes malware detection, removal
of spam filtering and content check.
Administrative Prevent
Use of Virtual private network Use of virtual private network will Product Prevent
5
NETWORK AND SECURITY
enable a secure connection to the
remote users as well thus preventing
hackers from snooping into the
network
Application controls Proper application control helps in
blocking unwanted or unauthorised
participants in a network
communication
Administrative Detect
Theft of
information
(employee)
Setting Up proper Permissions By enforcing the principle of least
privilege, the theft of information by
employees can be prevented.
Administrative Prevent
Monitoring the changes to
permission
Setting up of permission will prevent
theft to information of an employee.
Administrative Detect
NETWORK AND SECURITY
enable a secure connection to the
remote users as well thus preventing
hackers from snooping into the
network
Application controls Proper application control helps in
blocking unwanted or unauthorised
participants in a network
communication
Administrative Detect
Theft of
information
(employee)
Setting Up proper Permissions By enforcing the principle of least
privilege, the theft of information by
employees can be prevented.
Administrative Prevent
Monitoring the changes to
permission
Setting up of permission will prevent
theft to information of an employee.
Administrative Detect
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
NETWORK AND SECURITY
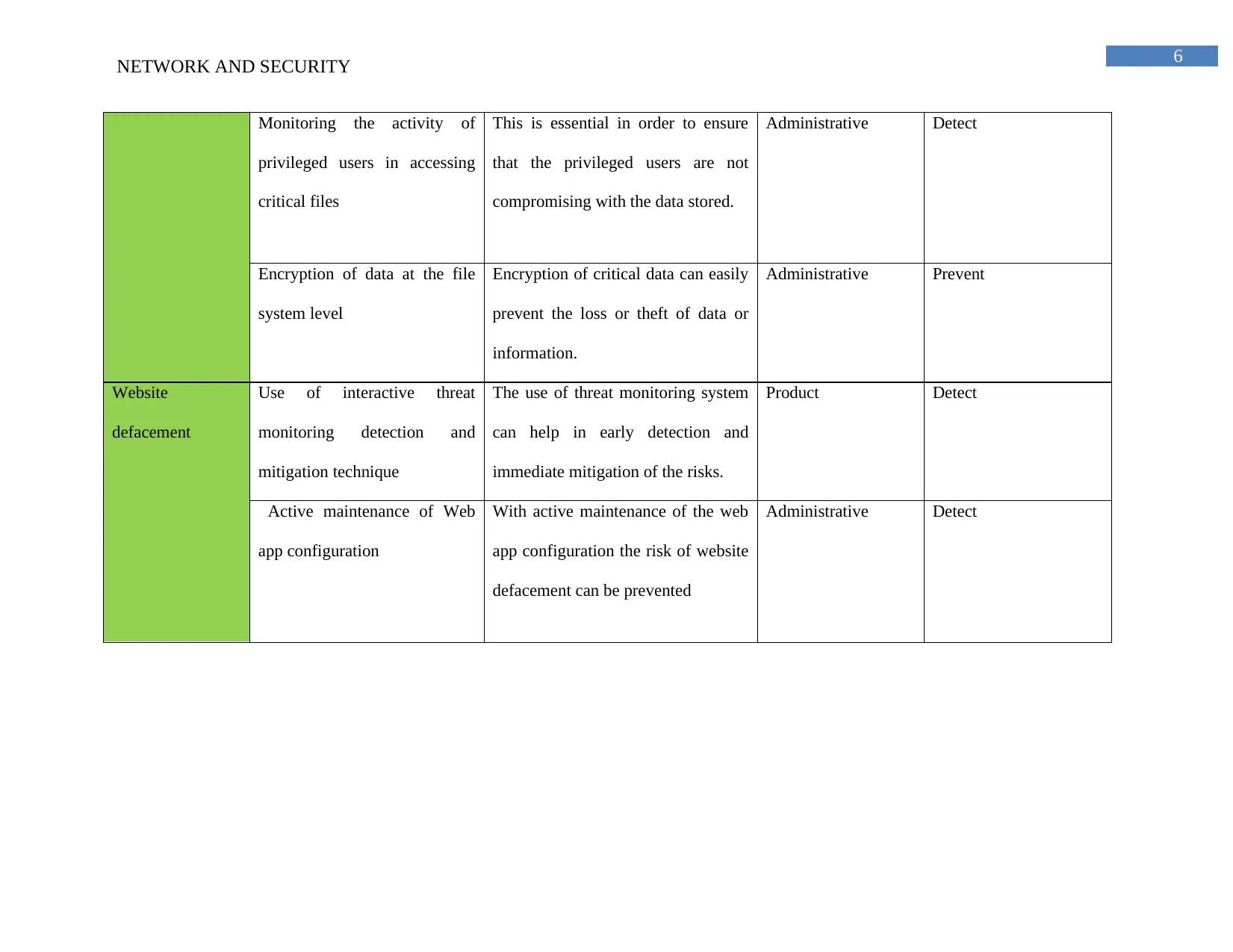
Monitoring the activity of
privileged users in accessing
critical files
This is essential in order to ensure
that the privileged users are not
compromising with the data stored.
Administrative Detect
Encryption of data at the file
system level
Encryption of critical data can easily
prevent the loss or theft of data or
information.
Administrative Prevent
Website
defacement
Use of interactive threat
monitoring detection and
mitigation technique
The use of threat monitoring system
can help in early detection and
immediate mitigation of the risks.
Product Detect
Active maintenance of Web
app configuration
With active maintenance of the web
app configuration the risk of website
defacement can be prevented
Administrative Detect
NETWORK AND SECURITY
Monitoring the activity of
privileged users in accessing
critical files
This is essential in order to ensure
that the privileged users are not
compromising with the data stored.
Administrative Detect
Encryption of data at the file
system level
Encryption of critical data can easily
prevent the loss or theft of data or
information.
Administrative Prevent
Website
defacement
Use of interactive threat
monitoring detection and
mitigation technique
The use of threat monitoring system
can help in early detection and
immediate mitigation of the risks.
Product Detect
Active maintenance of Web
app configuration
With active maintenance of the web
app configuration the risk of website
defacement can be prevented
Administrative Detect
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK AND SECURITY
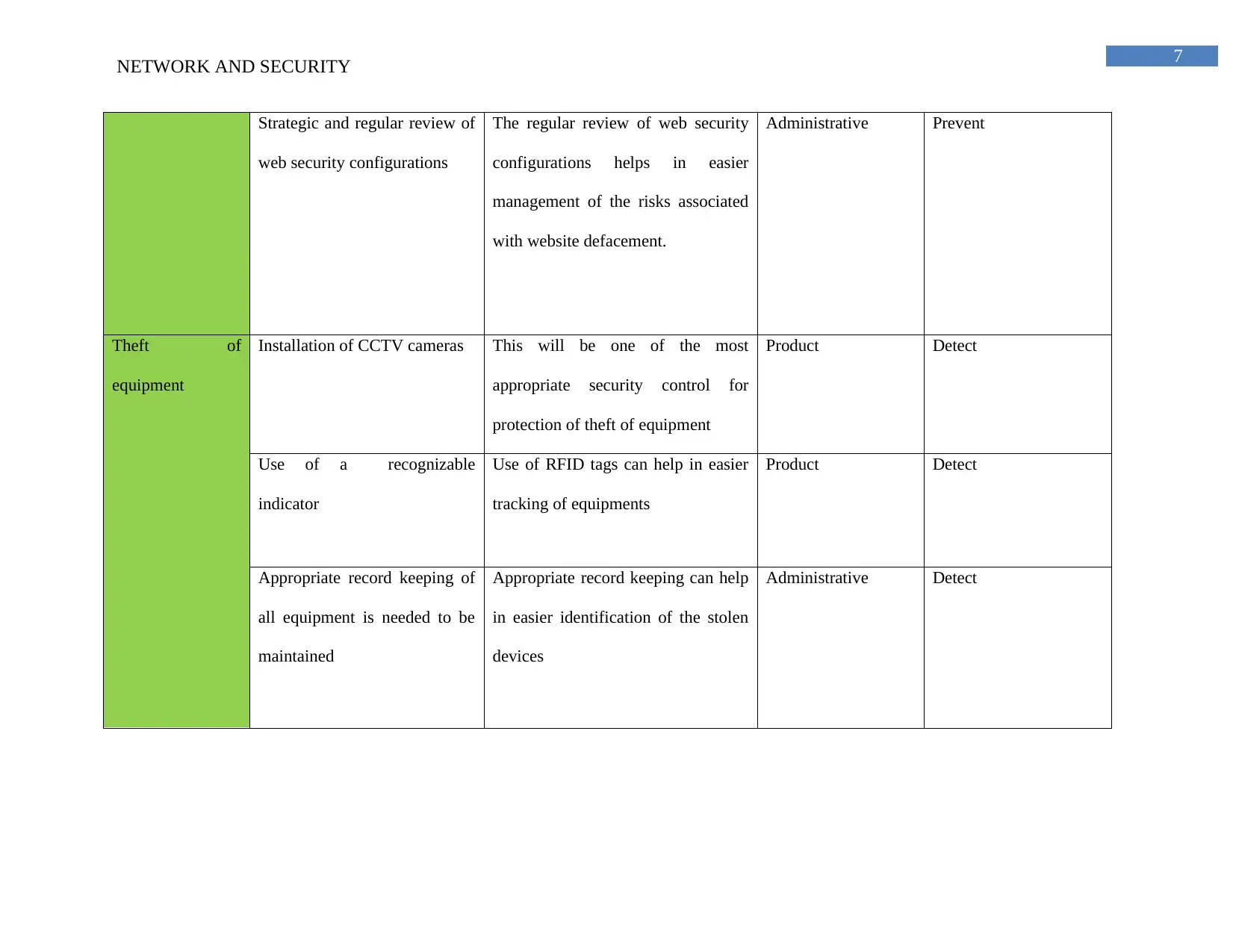
Strategic and regular review of
web security configurations
The regular review of web security
configurations helps in easier
management of the risks associated
with website defacement.
Administrative Prevent
Theft of
equipment
Installation of CCTV cameras This will be one of the most
appropriate security control for
protection of theft of equipment
Product Detect
Use of a recognizable
indicator
Use of RFID tags can help in easier
tracking of equipments
Product Detect
Appropriate record keeping of
all equipment is needed to be
maintained
Appropriate record keeping can help
in easier identification of the stolen
devices
Administrative Detect
NETWORK AND SECURITY
Strategic and regular review of
web security configurations
The regular review of web security
configurations helps in easier
management of the risks associated
with website defacement.
Administrative Prevent
Theft of
equipment
Installation of CCTV cameras This will be one of the most
appropriate security control for
protection of theft of equipment
Product Detect
Use of a recognizable
indicator
Use of RFID tags can help in easier
tracking of equipments
Product Detect
Appropriate record keeping of
all equipment is needed to be
maintained
Appropriate record keeping can help
in easier identification of the stolen
devices
Administrative Detect
8
NETWORK AND SECURITY
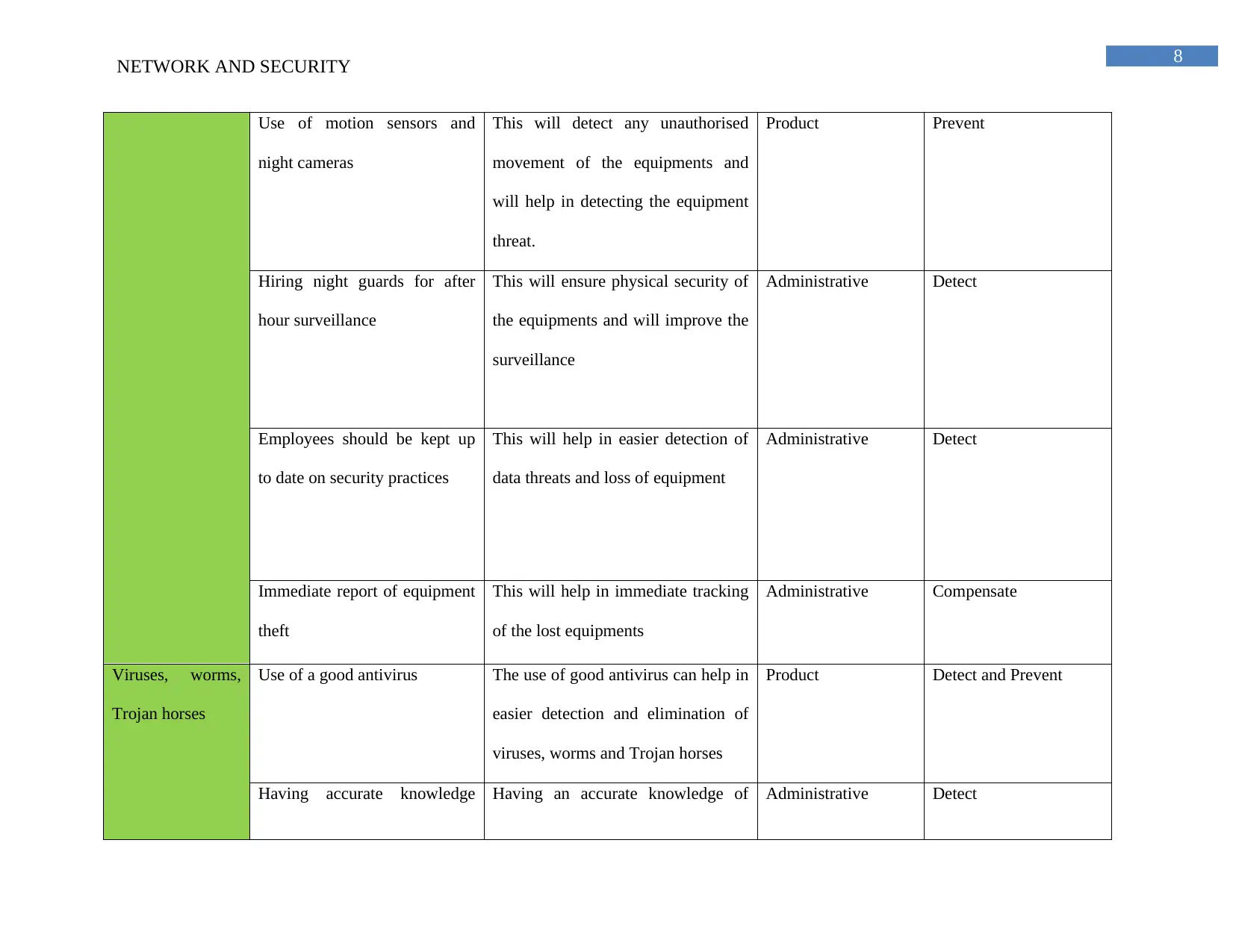
Use of motion sensors and
night cameras
This will detect any unauthorised
movement of the equipments and
will help in detecting the equipment
threat.
Product Prevent
Hiring night guards for after
hour surveillance
This will ensure physical security of
the equipments and will improve the
surveillance
Administrative Detect
Employees should be kept up
to date on security practices
This will help in easier detection of
data threats and loss of equipment
Administrative Detect
Immediate report of equipment
theft
This will help in immediate tracking
of the lost equipments
Administrative Compensate
Viruses, worms,
Trojan horses
Use of a good antivirus The use of good antivirus can help in
easier detection and elimination of
viruses, worms and Trojan horses
Product Detect and Prevent
Having accurate knowledge Having an accurate knowledge of Administrative Detect
NETWORK AND SECURITY
Use of motion sensors and
night cameras
This will detect any unauthorised
movement of the equipments and
will help in detecting the equipment
threat.
Product Prevent
Hiring night guards for after
hour surveillance
This will ensure physical security of
the equipments and will improve the
surveillance
Administrative Detect
Employees should be kept up
to date on security practices
This will help in easier detection of
data threats and loss of equipment
Administrative Detect
Immediate report of equipment
theft
This will help in immediate tracking
of the lost equipments
Administrative Compensate
Viruses, worms,
Trojan horses
Use of a good antivirus The use of good antivirus can help in
easier detection and elimination of
viruses, worms and Trojan horses
Product Detect and Prevent
Having accurate knowledge Having an accurate knowledge of Administrative Detect
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
NETWORK AND SECURITY
about malicious programs malicious programs can prevent its
use or can help in easier detection of
the same
Avoiding third party
downloads
Third party downloads can be a
source of Viruses, worms and Trojan
horses and therefore it is needed to
be prevented.
Administrative Prevent
Use of a hardware based
firewalls
Use of firewalls can help in easier
detection of Viruses, worms and
Trojan horses
Product Detect and Prevent
SLL should be checked prior to
any online transaction
Regular Data backup
The use of secure website can
prevent the threats associated with
Viruses, worms and Trojan horses
Administrative Prevent
Elevation of Segmentation Segmentation of the network helps in Administrative Prevent
NETWORK AND SECURITY
about malicious programs malicious programs can prevent its
use or can help in easier detection of
the same
Avoiding third party
downloads
Third party downloads can be a
source of Viruses, worms and Trojan
horses and therefore it is needed to
be prevented.
Administrative Prevent
Use of a hardware based
firewalls
Use of firewalls can help in easier
detection of Viruses, worms and
Trojan horses
Product Detect and Prevent
SLL should be checked prior to
any online transaction
Regular Data backup
The use of secure website can
prevent the threats associated with
Viruses, worms and Trojan horses
Administrative Prevent
Elevation of Segmentation Segmentation of the network helps in Administrative Prevent
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORK AND SECURITY
privilege applying filtering rules at the
network level
Blocking the traffic to internet Blocking the internet traffic should
not hold direct access to internet
Administrative Prevent
Use of firewalls in operating
system
Use of proper firewalls can help in
easier management of traffic and
communication thus preventing this
affect
Product Prevent and Detect
Execution blocking Execution blocking can possibly
help in mitigation of the risks that
can arise due to elevation of
privilege.
Administrative Prevent
Fire/Flood Ensuring a fire security Fire insurance can reduce the
damage caused by fire and flood.
Thus presence of proper fire security
can help in easier management of
this risk. The fire insurance should
cover maximum damage
Administrative Compensate
NETWORK AND SECURITY
privilege applying filtering rules at the
network level
Blocking the traffic to internet Blocking the internet traffic should
not hold direct access to internet
Administrative Prevent
Use of firewalls in operating
system
Use of proper firewalls can help in
easier management of traffic and
communication thus preventing this
affect
Product Prevent and Detect
Execution blocking Execution blocking can possibly
help in mitigation of the risks that
can arise due to elevation of
privilege.
Administrative Prevent
Fire/Flood Ensuring a fire security Fire insurance can reduce the
damage caused by fire and flood.
Thus presence of proper fire security
can help in easier management of
this risk. The fire insurance should
cover maximum damage
Administrative Compensate
11
NETWORK AND SECURITY
Prompt action in case of fire In case of fire or flood, prompt
action can be taken for management
of the problems faced fire or flood.
Proper training can be provided to
the employees for acting promptly in
this situation
Administrative Prevent and Compensate
Regular data back up Regular data backup can reduce the
problems and the damage caused by
fire or flood. Easy recovery of data
can be ensured by regular data back
up
Administrative Compensate
Appropriate disaster recovery
system
Presence of a proper disaster
recovery system can help in better
management of this type of risks.
Administrative Compensate
NETWORK AND SECURITY
Prompt action in case of fire In case of fire or flood, prompt
action can be taken for management
of the problems faced fire or flood.
Proper training can be provided to
the employees for acting promptly in
this situation
Administrative Prevent and Compensate
Regular data back up Regular data backup can reduce the
problems and the damage caused by
fire or flood. Easy recovery of data
can be ensured by regular data back
up
Administrative Compensate
Appropriate disaster recovery
system
Presence of a proper disaster
recovery system can help in better
management of this type of risks.
Administrative Compensate
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





