Computer Organization and Network Analysis Report - Semester 1
VerifiedAdded on 2022/09/02
|27
|5085
|18
Report
AI Summary
This report provides a comprehensive analysis of computer organization and network analysis. It begins with an overview of the Harvard and Von Neumann architectures, discussing their advantages and disadvantages, along with the role of virtualization. The report then delves into networking protocols such as TCP/IP, HTTP, FTP, and SMTP, examining their security implications and intrusion prevention techniques. It further explores ethical and legal issues surrounding computers and networks, including cybercrime. The practical section includes circuit simulations for half and full adders, demonstrating fundamental computer arithmetic operations, and a discussion on virtual machines. Overall, the report offers a detailed examination of the core concepts and challenges in computer organization and network security.

Running head: COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Computer Organization and Network Analysis
Name of the Student
Name of the University
Author Note
Computer Organization and Network Analysis
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Executive Summary
Over the last two decades computing has come a long way. Today’s processors can easily
process virtualization workloads as they continue to become more powerful and virtualization
instruction sets like AVX keep evolving. The report takes a look at the core architecture
based on which these processors are made. Then the respective advantages and disadvantages
of these architecture types and virtualization offered by Linux operating systems is to be
discussed. Then the report is to go through the ethical and legal issues that can arise among
computers and networks powered by these processors. The architecture of the processors are
found to be the Harvard and Von Neumann architectures. The layout of CPUs based on each
architecture type gets discussed by the report in the background section. The report
investigates the different networking protocols being used and how secure a network these
protocols can provide. These are mostly the TCP/IP, HTTP, FTP and SMTP protocols.
Detailed study of TCP/IP, HTTP and FTP are to be provided in the background section along
with a thorough analysis of intrusion prevention. Network security is mostly ensured by the
networking protocols and the security solutions offered by third party vendors. To provide
additional security, intrusion prevention systems can be implemented. These systems monitor
the entire network traffic and detects malicious attacks that other security solutions cannot.
After this the report ends with concluding notes.
Executive Summary
Over the last two decades computing has come a long way. Today’s processors can easily
process virtualization workloads as they continue to become more powerful and virtualization
instruction sets like AVX keep evolving. The report takes a look at the core architecture
based on which these processors are made. Then the respective advantages and disadvantages
of these architecture types and virtualization offered by Linux operating systems is to be
discussed. Then the report is to go through the ethical and legal issues that can arise among
computers and networks powered by these processors. The architecture of the processors are
found to be the Harvard and Von Neumann architectures. The layout of CPUs based on each
architecture type gets discussed by the report in the background section. The report
investigates the different networking protocols being used and how secure a network these
protocols can provide. These are mostly the TCP/IP, HTTP, FTP and SMTP protocols.
Detailed study of TCP/IP, HTTP and FTP are to be provided in the background section along
with a thorough analysis of intrusion prevention. Network security is mostly ensured by the
networking protocols and the security solutions offered by third party vendors. To provide
additional security, intrusion prevention systems can be implemented. These systems monitor
the entire network traffic and detects malicious attacks that other security solutions cannot.
After this the report ends with concluding notes.

2COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Table of Contents
Introduction................................................................................................................................4
Evaluation 1...............................................................................................................................4
Background............................................................................................................................4
Advantages.............................................................................................................................5
Harvard Architecture..........................................................................................................5
Von Neumann Architecture...............................................................................................5
Virtualization......................................................................................................................6
Disadvantages........................................................................................................................6
Harvard Architecture..........................................................................................................6
Von Neumann Architecture...............................................................................................7
Virtualization......................................................................................................................7
Ethical and Legal Issues.............................................................................................................8
Computers as targets..............................................................................................................8
Computers as storage devices................................................................................................8
Computers as communication tools.......................................................................................8
Law Enforcement...................................................................................................................8
Practical......................................................................................................................................9
Half Adder..............................................................................................................................9
Full Adder............................................................................................................................10
Virtual Machines..................................................................................................................12
Evaluation 2.............................................................................................................................13
Table of Contents
Introduction................................................................................................................................4
Evaluation 1...............................................................................................................................4
Background............................................................................................................................4
Advantages.............................................................................................................................5
Harvard Architecture..........................................................................................................5
Von Neumann Architecture...............................................................................................5
Virtualization......................................................................................................................6
Disadvantages........................................................................................................................6
Harvard Architecture..........................................................................................................6
Von Neumann Architecture...............................................................................................7
Virtualization......................................................................................................................7
Ethical and Legal Issues.............................................................................................................8
Computers as targets..............................................................................................................8
Computers as storage devices................................................................................................8
Computers as communication tools.......................................................................................8
Law Enforcement...................................................................................................................8
Practical......................................................................................................................................9
Half Adder..............................................................................................................................9
Full Adder............................................................................................................................10
Virtual Machines..................................................................................................................12
Evaluation 2.............................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Background..........................................................................................................................13
Advantages...........................................................................................................................15
Internet protocols.............................................................................................................15
Intrusion Prevention.........................................................................................................16
Disadvantages......................................................................................................................16
Internet protocols.............................................................................................................16
Intrusion Prevention.........................................................................................................17
Legal and Ethical Issues.......................................................................................................17
Practical....................................................................................................................................18
Router Configuration...........................................................................................................18
Internet Tools & Protocols...................................................................................................20
Conclusion................................................................................................................................21
Bibliography.............................................................................................................................23
Background..........................................................................................................................13
Advantages...........................................................................................................................15
Internet protocols.............................................................................................................15
Intrusion Prevention.........................................................................................................16
Disadvantages......................................................................................................................16
Internet protocols.............................................................................................................16
Intrusion Prevention.........................................................................................................17
Legal and Ethical Issues.......................................................................................................17
Practical....................................................................................................................................18
Router Configuration...........................................................................................................18
Internet Tools & Protocols...................................................................................................20
Conclusion................................................................................................................................21
Bibliography.............................................................................................................................23
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Introduction
The following report provides a study of the architectures based on which these
processors are designed. The associated advantages and disadvantages of these architecture
types and that of virtualization offered by alternate operating systems then get discussed.
Then the report is to go through the ethical and legal issues that computers and networks
powered by these processors can face. After that the report ends with concluding notes.
Evaluation 1
Background
The digital computer organization or computer architecture provides design and
description of computer systems. This serves as the art and science of selection and
interconnection of computing hardware that is required in the creation of computer systems
such that they meet the desired performance and functionalities within the allocated cost. The
two main methods by which computer architectures are being designed today are the Harvard
architecture and the Von Neumann architecture (Parhami 2019). CPUs based on these
architecture also have a specific set of instruction that enables systems to conduct
virtualization by hosting hypervisor-based virtual machines.
As per Hernandez Zavala et al. 2015, the Harvard architecture comprises separate
program memory and data memory with independent bus connection. On top of this
architectural techniques like pipelining and parallelism are applied to improve compute
performance.
According to Fu et al. 2016, the quantum plane of the processor is divided to specific
sections for processing, communication as also for storing quantum states. When applying the
Von Neumann architecture, in computing systems, various challenges can be introduced
Introduction
The following report provides a study of the architectures based on which these
processors are designed. The associated advantages and disadvantages of these architecture
types and that of virtualization offered by alternate operating systems then get discussed.
Then the report is to go through the ethical and legal issues that computers and networks
powered by these processors can face. After that the report ends with concluding notes.
Evaluation 1
Background
The digital computer organization or computer architecture provides design and
description of computer systems. This serves as the art and science of selection and
interconnection of computing hardware that is required in the creation of computer systems
such that they meet the desired performance and functionalities within the allocated cost. The
two main methods by which computer architectures are being designed today are the Harvard
architecture and the Von Neumann architecture (Parhami 2019). CPUs based on these
architecture also have a specific set of instruction that enables systems to conduct
virtualization by hosting hypervisor-based virtual machines.
As per Hernandez Zavala et al. 2015, the Harvard architecture comprises separate
program memory and data memory with independent bus connection. On top of this
architectural techniques like pipelining and parallelism are applied to improve compute
performance.
According to Fu et al. 2016, the quantum plane of the processor is divided to specific
sections for processing, communication as also for storing quantum states. When applying the
Von Neumann architecture, in computing systems, various challenges can be introduced

5COMPUTER ORGANIZATION AND NETWORK ANALYSIS
because of parallelization. One of the major issue is the memory wall issue which quite
difficult to solve through conventional methods.
Based on the study of Li and Kanso 2015, the two main ways of achieving
virtualization can be the hypervisor-based or container-based virtualization. The hypervisor-
based virtualization includes virtual machines like the ones made available by Microsoft
Hyper-V, VMware or Citrix XenServer while container-based virtualizations can be the OS
level virtualizations of Linux systems like LXC or Linux Containers. Linux is the alternate
family of operating systems available for computer users. There exist several branches of
Linux based operating systems. Among them, Ubuntu is the most user friendly OS for the
mainstream users while Kali Linux can be used by attackers and system administrators.
Unlike hypervisor-based VMs, Container-based virtualization do not emulate entire hardware
environments.
Advantages
Harvard Architecture
The Harvard architecture based processor architectures contain very efficient pipelining
where it is possible for overlapping the instruction fetch and the operand fetch.
The CPUs based on the Harvard architecture contain different independent buses for
instructions and data of programs.
These kind of CPUs are fine tuned to process the FPGA specific workloads.
The architecture layout enables the CPU to execute the programs much faster. The actual
execution time is directly proportional to the complexity of the hardware.
because of parallelization. One of the major issue is the memory wall issue which quite
difficult to solve through conventional methods.
Based on the study of Li and Kanso 2015, the two main ways of achieving
virtualization can be the hypervisor-based or container-based virtualization. The hypervisor-
based virtualization includes virtual machines like the ones made available by Microsoft
Hyper-V, VMware or Citrix XenServer while container-based virtualizations can be the OS
level virtualizations of Linux systems like LXC or Linux Containers. Linux is the alternate
family of operating systems available for computer users. There exist several branches of
Linux based operating systems. Among them, Ubuntu is the most user friendly OS for the
mainstream users while Kali Linux can be used by attackers and system administrators.
Unlike hypervisor-based VMs, Container-based virtualization do not emulate entire hardware
environments.
Advantages
Harvard Architecture
The Harvard architecture based processor architectures contain very efficient pipelining
where it is possible for overlapping the instruction fetch and the operand fetch.
The CPUs based on the Harvard architecture contain different independent buses for
instructions and data of programs.
These kind of CPUs are fine tuned to process the FPGA specific workloads.
The architecture layout enables the CPU to execute the programs much faster. The actual
execution time is directly proportional to the complexity of the hardware.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Von Neumann Architecture
CPUs based on Von Neumann architecture store instructions and data in the same memory
space
These kind of processors are simpler to design and economical to manufacture.
It is also simpler to manage a single common memory block for both instructions and data.
The physical space consumed by the Von Neumann based CPUs is significantly less than
those of Harvard architecture type.
Virtualization
The numerous advantages that can be obtained from virtualization that Linux based operating
systems can offer are:
Capital expenses and the overall operating costs can be brought down significantly.
Agility, efficiency, productivity and responsiveness of IT services can greatly be increased.
Continuity of business processes can be maintained along with ensuring faster disaster
recovery.
Simpler and central management of data can be performed by the company.
Companies if wish can operate as a true software defined Data Centre.
Other benefits from virtualization can be the ability to run multiple OSs from the same
machine and dividing system resources among virtual machines through partitioning. Fault
and security isolation can be ensured at hardware level along with preserving of performance.
Disadvantages
Harvard Architecture
The Harvard architecture is not as widely used as the Von Neumann architecture.
Von Neumann Architecture
CPUs based on Von Neumann architecture store instructions and data in the same memory
space
These kind of processors are simpler to design and economical to manufacture.
It is also simpler to manage a single common memory block for both instructions and data.
The physical space consumed by the Von Neumann based CPUs is significantly less than
those of Harvard architecture type.
Virtualization
The numerous advantages that can be obtained from virtualization that Linux based operating
systems can offer are:
Capital expenses and the overall operating costs can be brought down significantly.
Agility, efficiency, productivity and responsiveness of IT services can greatly be increased.
Continuity of business processes can be maintained along with ensuring faster disaster
recovery.
Simpler and central management of data can be performed by the company.
Companies if wish can operate as a true software defined Data Centre.
Other benefits from virtualization can be the ability to run multiple OSs from the same
machine and dividing system resources among virtual machines through partitioning. Fault
and security isolation can be ensured at hardware level along with preserving of performance.
Disadvantages
Harvard Architecture
The Harvard architecture is not as widely used as the Von Neumann architecture.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Because of the significant hardware complexity, it is difficult to produce CPUs based on the
Harvard architecture.
Also as a result of the increased hardware complexity, there are substantially more pins in
CPUs of Harvard architecture.
Von Neumann Architecture
The shared memory for program instructions and data causes defective programs to overwrite
other programs thereby resulting in system crashes.
Sometimes there are defective programs which end up failing to empty the memory space
assigned to them even after having finished their execution.
The speed of the CPU is substantially faster than the data bus and thus it mostly has to sit
idling.
Though the instructions and data are sharing the same data bus, the fetch rate for both varies
widely.
Virtualization
The disadvantages of virtualization can be:
The cost of implementing virtualization within the company can be substantially high as
appropriate hardware and software need to be acquired or developed.
The limitations of virtualization can include incompatibility of several key applications which
can force the business to setup a hybrid system.
A major concern from virtualization is availability and there can be a serious problem if the
business is unable to access their data stored in the virtual environment.
Because of the significant hardware complexity, it is difficult to produce CPUs based on the
Harvard architecture.
Also as a result of the increased hardware complexity, there are substantially more pins in
CPUs of Harvard architecture.
Von Neumann Architecture
The shared memory for program instructions and data causes defective programs to overwrite
other programs thereby resulting in system crashes.
Sometimes there are defective programs which end up failing to empty the memory space
assigned to them even after having finished their execution.
The speed of the CPU is substantially faster than the data bus and thus it mostly has to sit
idling.
Though the instructions and data are sharing the same data bus, the fetch rate for both varies
widely.
Virtualization
The disadvantages of virtualization can be:
The cost of implementing virtualization within the company can be substantially high as
appropriate hardware and software need to be acquired or developed.
The limitations of virtualization can include incompatibility of several key applications which
can force the business to setup a hybrid system.
A major concern from virtualization is availability and there can be a serious problem if the
business is unable to access their data stored in the virtual environment.

8COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Virtualization requires multiple virtual machines to stay interconnected through appropriate
LAN and other system configurations so that they can operate as one environment such that
the client systems can seamlessly interact with one another.
Virtualization can also develop scalability issues among growing businesses.
Ethical and Legal Issues
Crimes regarding computers are broadly termed as cybercrime. These are criminal activities
which involves computers and networks as targets or centre of the criminal activity. The three
main categories of cybercrime are:
Computers as targets
These crimes target the computer systems for acquiring sensitive information from these
systems. This is done by the attacker so that they can ultimately gain control over these target
systems by bypassing the authentication mechanism.
Computers as storage devices
Unlawful activities can further be expanded through use of computers and storage devices.
An example of these can be storage of the stolen list of passwords and transaction details on
the affected computers and storage devices.
Computers as communication tools
The crimes related to communications over computers and network are the examples of
traditional that are committed online. These can be trading of drugs, child pornography,
gambling and fraud.
Law Enforcement
Proper investigation of cybercrime activities is not possible without fair understanding of the
technology involved. These crimes can have a global spread which makes it harder to tackle.
Virtualization requires multiple virtual machines to stay interconnected through appropriate
LAN and other system configurations so that they can operate as one environment such that
the client systems can seamlessly interact with one another.
Virtualization can also develop scalability issues among growing businesses.
Ethical and Legal Issues
Crimes regarding computers are broadly termed as cybercrime. These are criminal activities
which involves computers and networks as targets or centre of the criminal activity. The three
main categories of cybercrime are:
Computers as targets
These crimes target the computer systems for acquiring sensitive information from these
systems. This is done by the attacker so that they can ultimately gain control over these target
systems by bypassing the authentication mechanism.
Computers as storage devices
Unlawful activities can further be expanded through use of computers and storage devices.
An example of these can be storage of the stolen list of passwords and transaction details on
the affected computers and storage devices.
Computers as communication tools
The crimes related to communications over computers and network are the examples of
traditional that are committed online. These can be trading of drugs, child pornography,
gambling and fraud.
Law Enforcement
Proper investigation of cybercrime activities is not possible without fair understanding of the
technology involved. These crimes can have a global spread which makes it harder to tackle.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER ORGANIZATION AND NETWORK ANALYSIS
The source of the attack can also be remote from the target system. Hence, the initiative like
International Convention on Cybercrime is found to be a welcome step in dealing with the
threat.
Practical
Additions and Subtractions are simple functions when it comes to arithmetic
operations performed by the CPU. When it comes to tasks requiring subtractions, the value of
the second operand is inverted and then an addition operation is performed among the two
operands such that:
(a – b) = (a) + (-b)
The electronic circuits that are required to enable calculations of such logical
operations are called logic gates. These are circuits made of transistors, diodes and resistors.
The three basic logic gates are the AND, OR and NOT gates. These simple logic gates can be
combined to create compound logic gates like NAND, NOR, XOR, XNOR gates. Both the
basic and the compound logic gates are used to create adders which are digital circuits that
can perform addition of numbers.
The source of the attack can also be remote from the target system. Hence, the initiative like
International Convention on Cybercrime is found to be a welcome step in dealing with the
threat.
Practical
Additions and Subtractions are simple functions when it comes to arithmetic
operations performed by the CPU. When it comes to tasks requiring subtractions, the value of
the second operand is inverted and then an addition operation is performed among the two
operands such that:
(a – b) = (a) + (-b)
The electronic circuits that are required to enable calculations of such logical
operations are called logic gates. These are circuits made of transistors, diodes and resistors.
The three basic logic gates are the AND, OR and NOT gates. These simple logic gates can be
combined to create compound logic gates like NAND, NOR, XOR, XNOR gates. Both the
basic and the compound logic gates are used to create adders which are digital circuits that
can perform addition of numbers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Half Adder
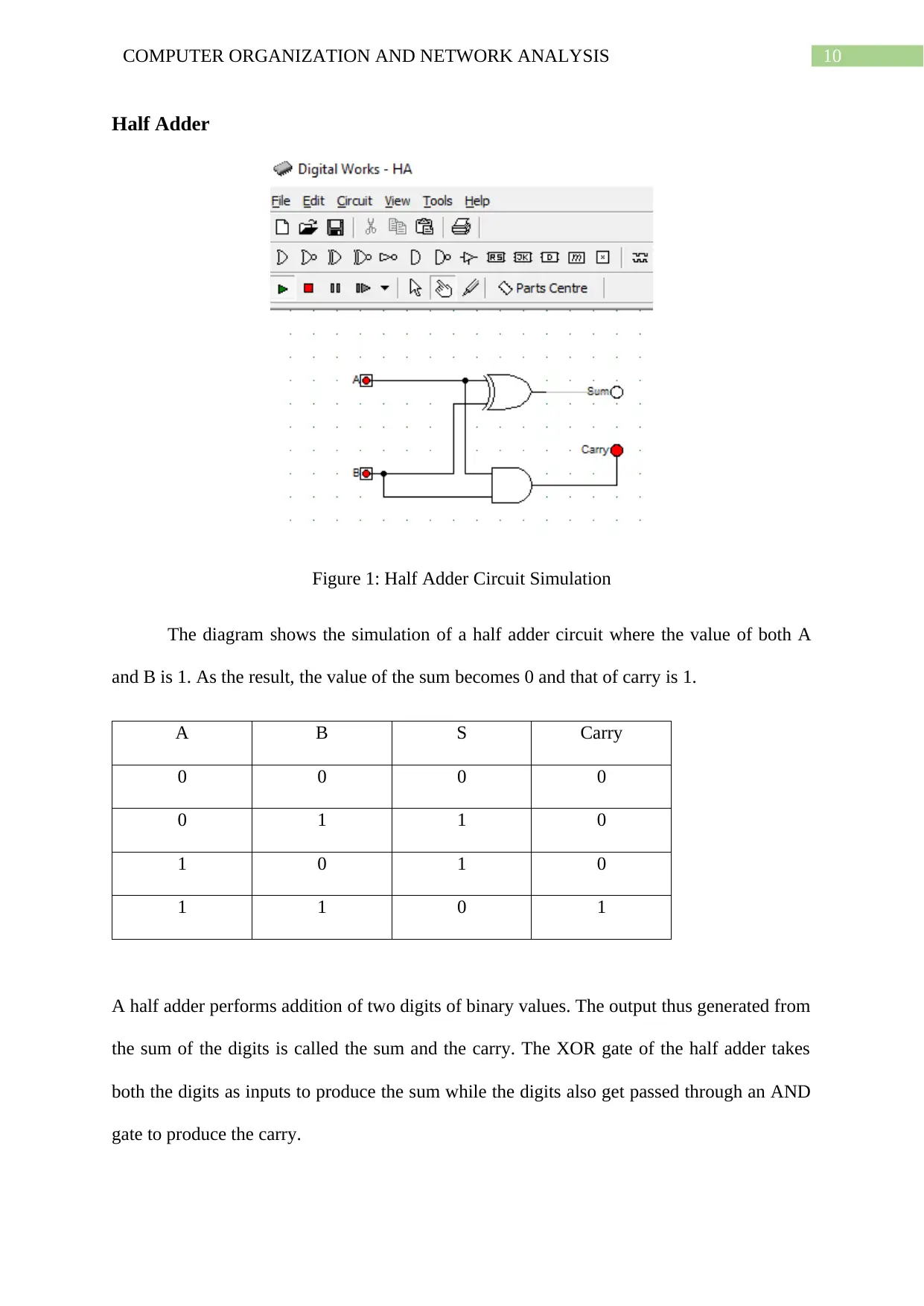
Figure 1: Half Adder Circuit Simulation
The diagram shows the simulation of a half adder circuit where the value of both A
and B is 1. As the result, the value of the sum becomes 0 and that of carry is 1.
A B S Carry
0 0 0 0
0 1 1 0
1 0 1 0
1 1 0 1
A half adder performs addition of two digits of binary values. The output thus generated from
the sum of the digits is called the sum and the carry. The XOR gate of the half adder takes
both the digits as inputs to produce the sum while the digits also get passed through an AND
gate to produce the carry.
Half Adder
Figure 1: Half Adder Circuit Simulation
The diagram shows the simulation of a half adder circuit where the value of both A
and B is 1. As the result, the value of the sum becomes 0 and that of carry is 1.
A B S Carry
0 0 0 0
0 1 1 0
1 0 1 0
1 1 0 1
A half adder performs addition of two digits of binary values. The output thus generated from
the sum of the digits is called the sum and the carry. The XOR gate of the half adder takes
both the digits as inputs to produce the sum while the digits also get passed through an AND
gate to produce the carry.
11COMPUTER ORGANIZATION AND NETWORK ANALYSIS
Full Adder
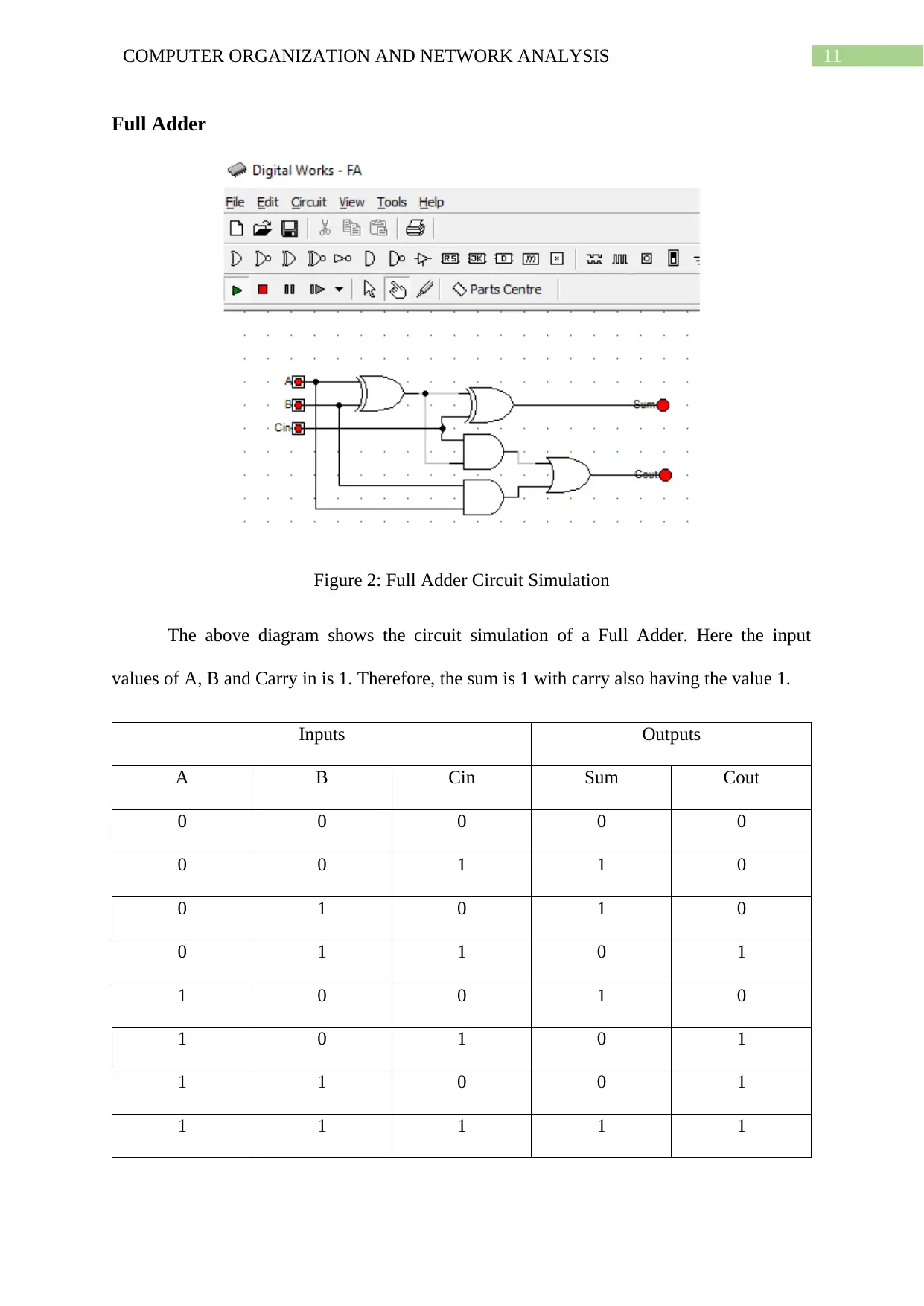
Figure 2: Full Adder Circuit Simulation
The above diagram shows the circuit simulation of a Full Adder. Here the input
values of A, B and Carry in is 1. Therefore, the sum is 1 with carry also having the value 1.
Inputs Outputs
A B Cin Sum Cout
0 0 0 0 0
0 0 1 1 0
0 1 0 1 0
0 1 1 0 1
1 0 0 1 0
1 0 1 0 1
1 1 0 0 1
1 1 1 1 1
Full Adder
Figure 2: Full Adder Circuit Simulation
The above diagram shows the circuit simulation of a Full Adder. Here the input
values of A, B and Carry in is 1. Therefore, the sum is 1 with carry also having the value 1.
Inputs Outputs
A B Cin Sum Cout
0 0 0 0 0
0 0 1 1 0
0 1 0 1 0
0 1 1 0 1
1 0 0 1 0
1 0 1 0 1
1 1 0 0 1
1 1 1 1 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




